#software vendor selection
Explore tagged Tumblr posts
Text
Integrating New Software: Tips for a Smooth Transition
Introduction
In today’s fast-paced technological landscape, businesses often find themselves integrating new software to stay competitive and efficient. However, the process can be daunting, fraught with potential disruptions and challenges. At TechtoIO, we understand the importance of a smooth transition when implementing new software. This guide provides essential tips to help you integrate new software seamlessly, minimizing downtime and maximizing productivity. Read to Continue
#addressing software resistance#business software implementation#continuous software improvement#data migration tools#effective software rollout#ensuring data integrity#Integrating new software#minimizing downtime in software integration#new software adoption#performance metrics for software integration#post-implementation software review#selecting new business software#smooth software transition#software compatibility considerations#software implementation roadmap#software integration tips#software migration strategies#software vendor selection#successful software integration#training for software integration#software solutions
1 note
·
View note
Text
I haven’t really seen any of the more recent U.S. election news hitting tumblr yet so here’s some updates (now edited with sources added):
There’s evidence of Trump cheating and interfering with the election.
Possible Russian interference.
Mail-in ballots are not being counted or “recognized” in multiple (notably swing) states.
30+ bomb threats were called in and shut down polling stations on Election Day.
20+ million votes are still unaccounted for, and that’s just to have the same voter turnout as 2020.
There was record voter turnout and new/first-time voter registration this year. We definitely should be well over the turnout in 2020.
U.S. citizens are using this site to demand, not only a recount, but a complete investigation into election fraud and interference for the reasons stated above:
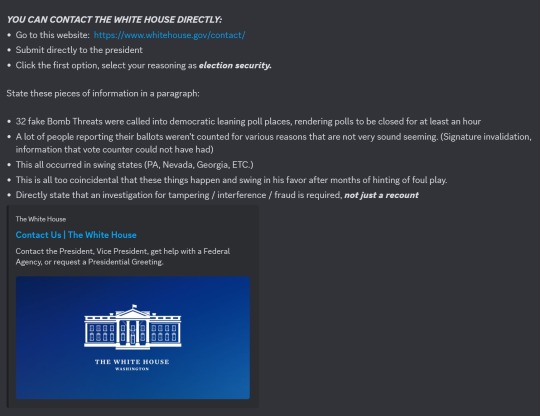
Here is what I submitted as an example:
An investigation for election interference and fraud is required. We desperately need a recount or even a revote. The American people deserve the right to a free and fair election. There has been evidence unveiled of Trump cheating and committing election fraud which is illegal. There is some evidence of possible Russian interference. At least 30+ bomb threats were called in to polling places. Multiple, notably swing states, have ballots unaccounted for and voting machines not registering votes. Ballots and ballot boxes were tampered with and burned. Over 20 million votes that we know of are unaccounted for. With record turnout and new voter registration this year, there should be no possibility that there are less votes than even in the 2020 election.
Sources (working on finding more links but if anyone wants to add info, it’s appreciated):
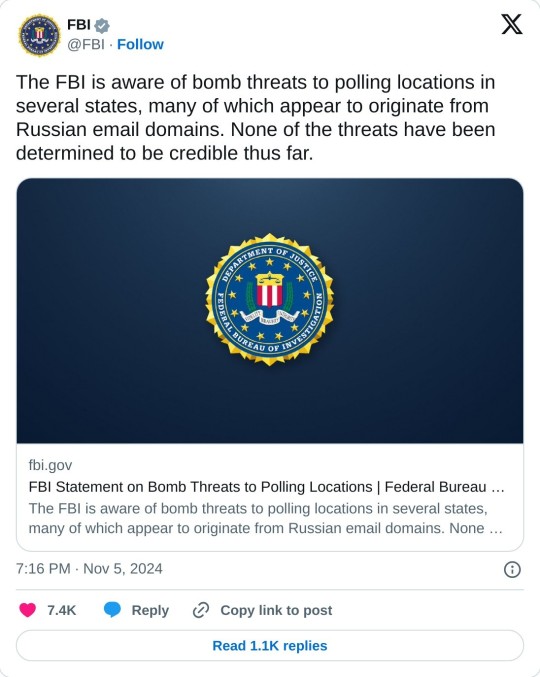
FBI addressing Russian interference and bomb threats:
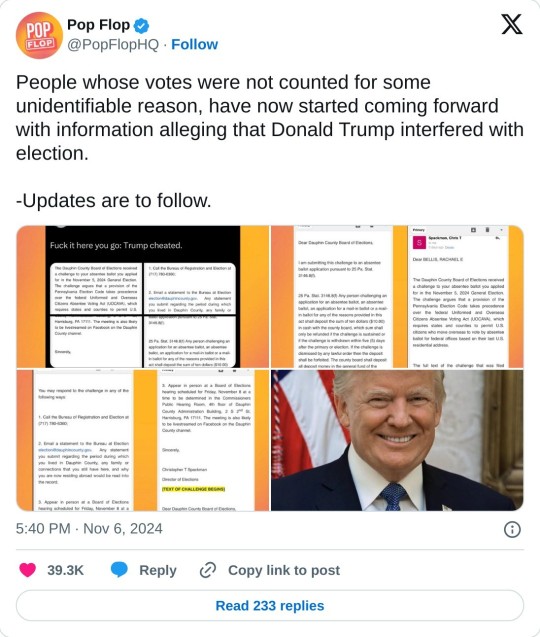
Emails released by Rachael Bellis (private account, can’t share original tweet) confirming Trump committing election fraud:
Pennsylvania's Centre County officials say they are working with their ballot scanner vendor to figure out why the county's mail-in ballot data is "not being recognized when uploaded to the elections software:”

Wisconsin recount:
[ID:
Multiple screenshots and images.
The first is a screenshot with a link and information for contacting the White House directly regarding election fraud. The instructions include choosing to leave a comment to President Joe Biden directly and to select election security as the reason.
The screenshot then instructs people to include any or all of the following information in a paragraph as a comment to the president:
32 fake bomb threats were called into Democratic leaning poll places, rendering polling places closed for at least an hour.
A lot of people reporting their ballots were not counted for various reasons.
This all occurred in swing states.
This is too coincidental that these things happen and swing in his favor after months of hinting at foul play.
Directly state that an investigation for tampering, interference, fraud is required, not just a recount.
The second image is from the FBI Twitter account that reads:
The FBI is aware of bomb threats to polling locations in several states, many of which appear to originate from Russian email domains. None of the threats have been determined to be credible thus far. https://t.co/j3YfajVK1m — FBI (@FBI) November 5, 2024
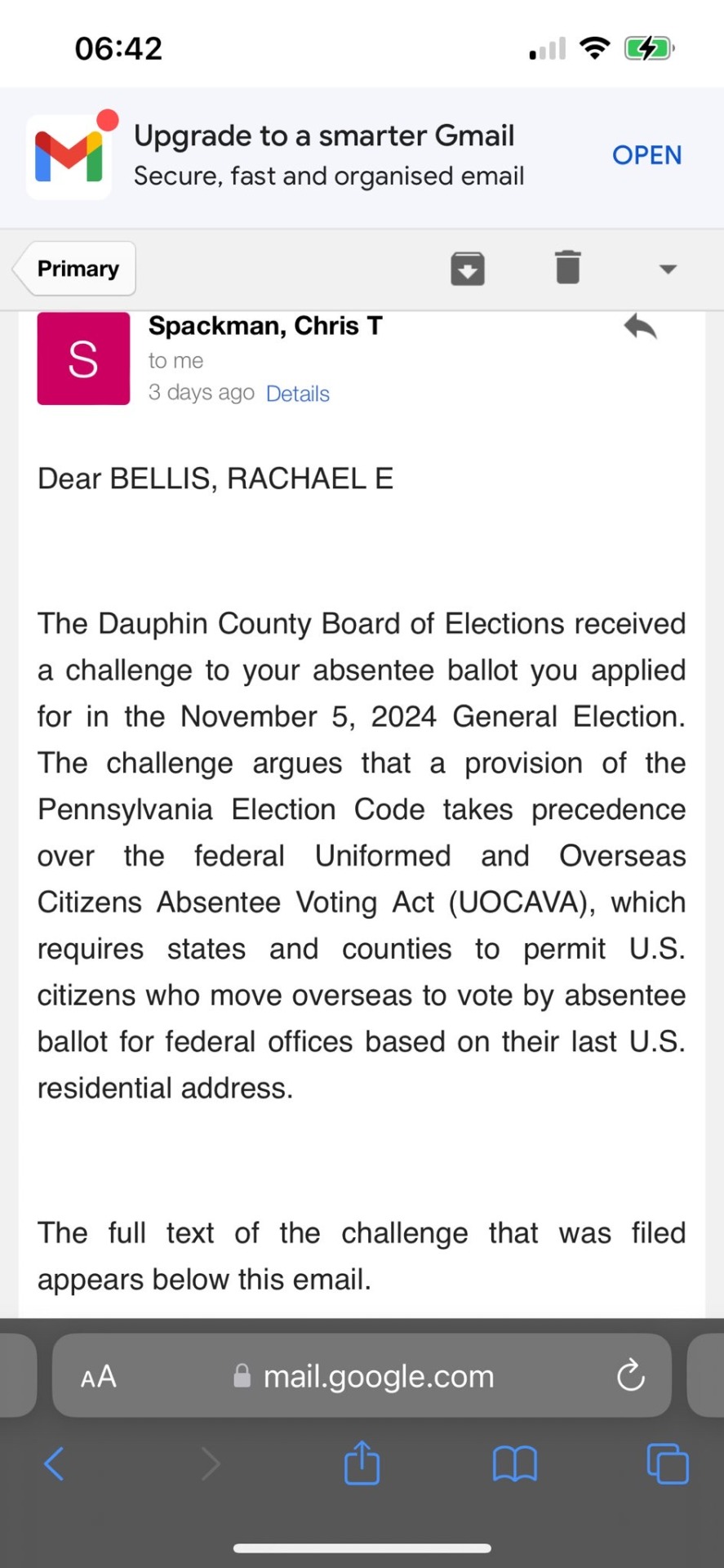
The next four Gmail screenshots of an email sent to Rachael Bellis from Chris T. Spackman that read together as follows:
Dear BELLIS, RACHAEL E., The Dauphin County Board of Elections received a challenge to your absentee ballot you applied for in the November 5, 2024 General Election. The challenge argues that a provision of the Pennsylvania Election Code takes precedence over the federal Uniformed and Overseas Citizens Absentee Voting Act (UOCAVA), which requires states and counties to permit U.S. citizens who move overseas to vote by absentee ballot for federal offices based on their last U.S. residential address.
The full text of the challenge that was filed appears below this email.
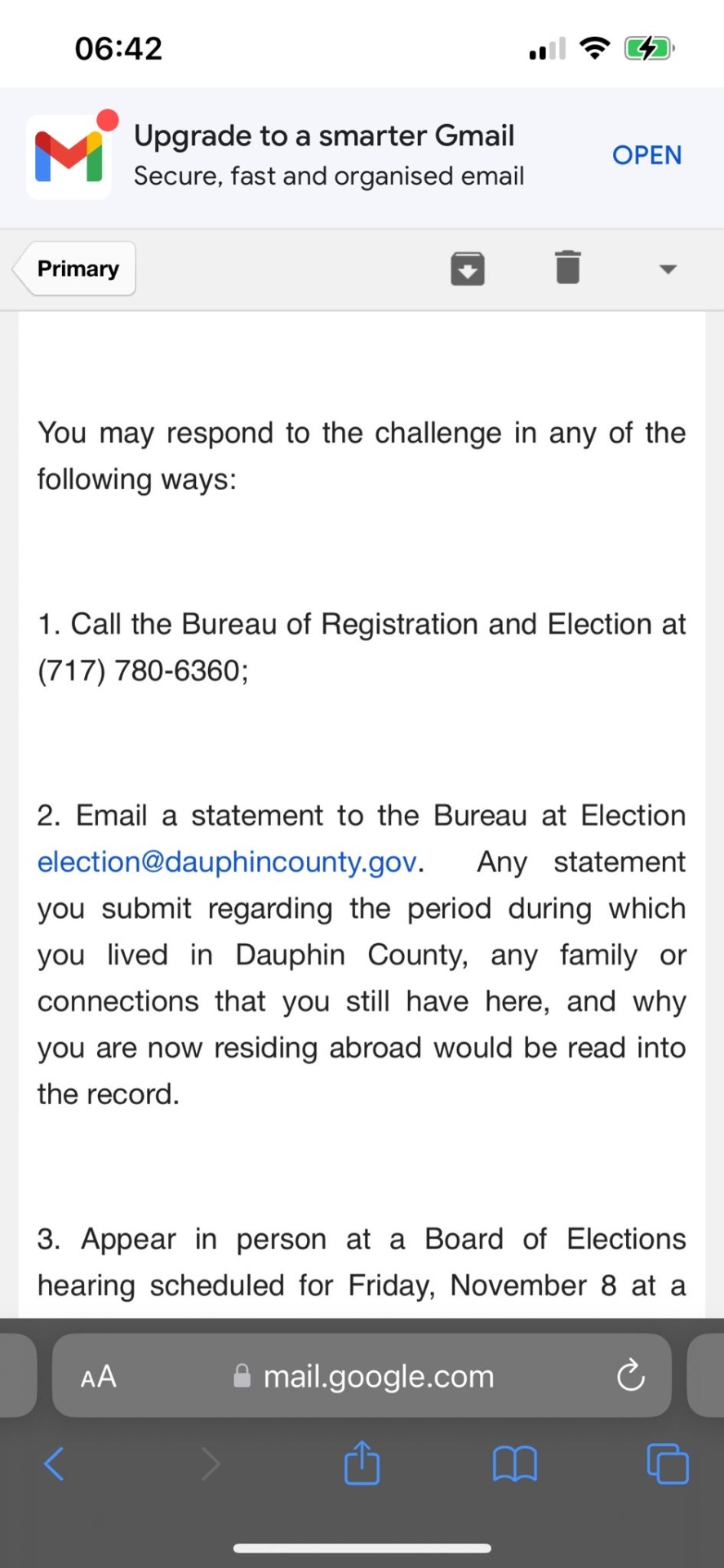
You may respond to the challenge in any of the following ways:
1. Call the Bureau of Registration and Election at (717) 780-6360;
2. Email a statement to the Bureau at Election [email protected]. Any statement you submit regarding the period during which you lived in Dauphin County, any family or connections that you still have here, and why you are now residing abroad would be read into the record.
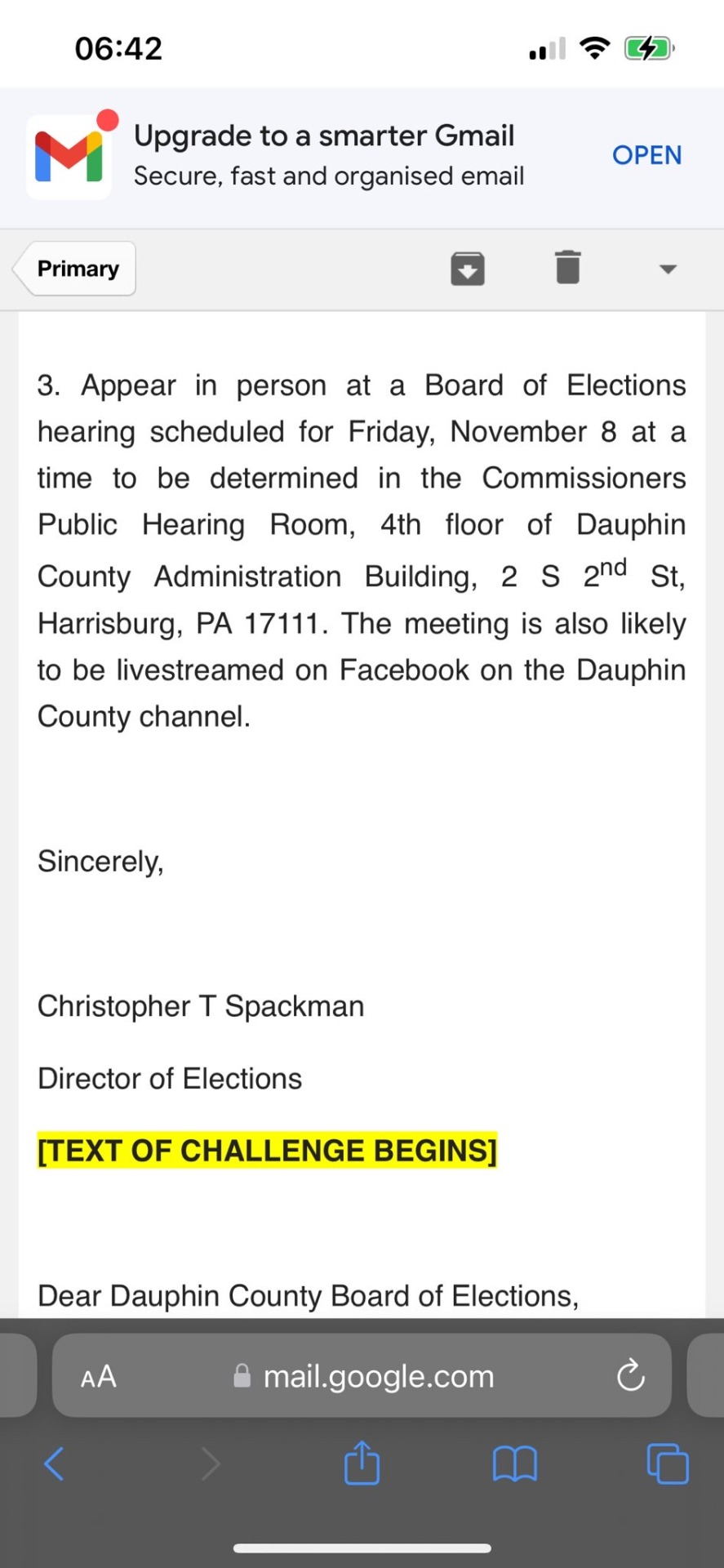
3. Appear in person at a Board of Elections hearing scheduled for Friday, November 8 at a time to be determined in the Commissioners Public Hearing Room, 4th floor of Dauphin County Administration Building, 2 S 20d St, Harrisburg, PA 17111. The meeting is also likely to be livestreamed on Facebook on the Dauphin County channel.
Sincerely,
Christopher T Spackman
TEXT OF CHALLENGE BEGINS
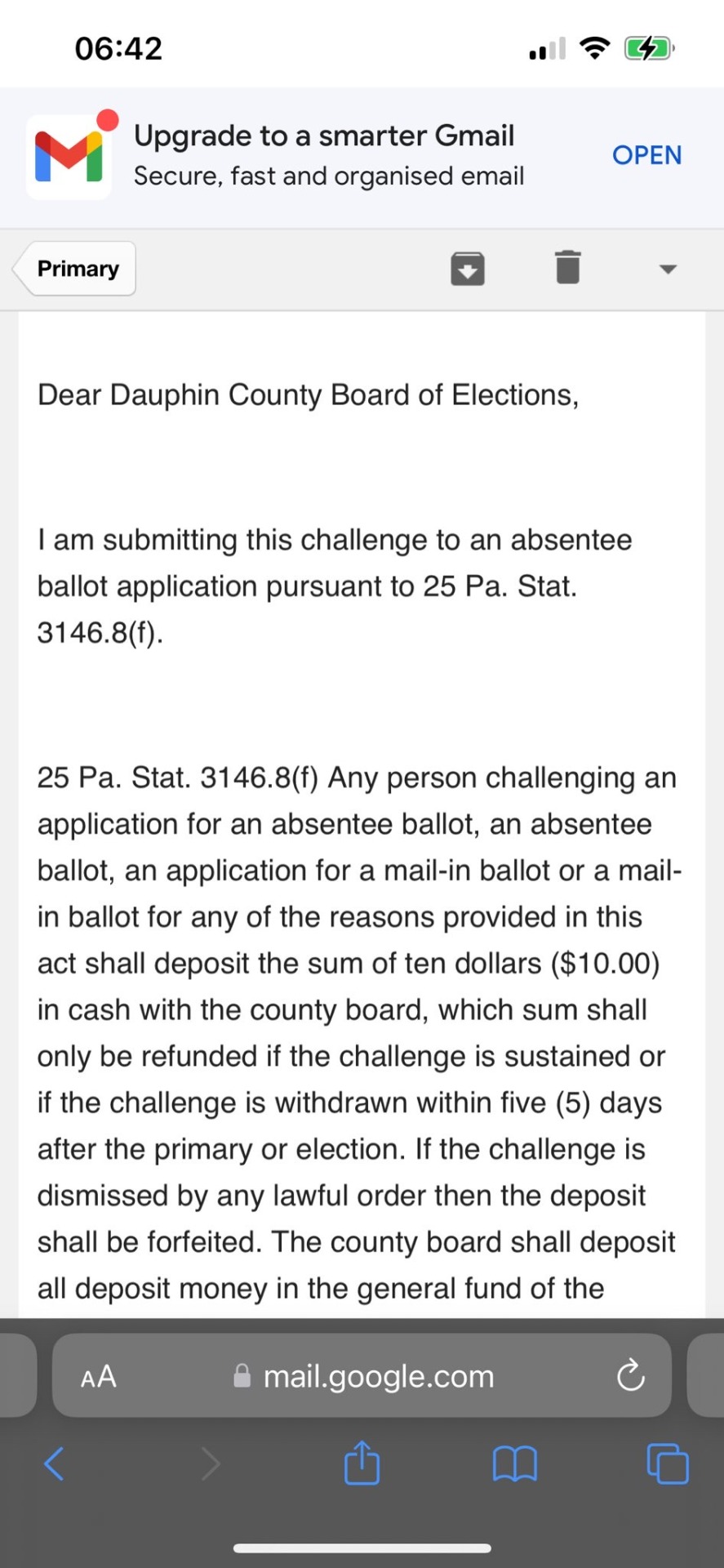
Dear Dauphin County Board of Elections,
I am submitting this challenge to an absentee ballot application pursuant to 25 Pa. Stat.
3146.8(f).
25 Pa. Stat. 3146.8(f) Any person challenging an application for an absentee ballot, an absentee ballot, an application for a mail-in ballot or a mail-in ballot for any of the reasons provided in this act shall deposit the sum of ten dollars ($10.00) in cash with the county board, which sum shall only be refunded if the challenge is sustained or if the challenge is withdrawn within five (5) days after the primary or election. If the challenge is dismissed by any lawful order then the deposit shall be forfeited. The county board shall deposit all deposit money in the general fund of the…
The rest of the forwarded email is cut off.
The last image is a screenshot of the official statement from the Centre County, Pennsylvania Board of Commissioners released on November 6, 2024 that states:
Centre County Working with Ballot Scanner Vendor to Export Election Results.
(Bellefonte, PA) -Centre County Elections Office is working continuously to provide mail-in ballot data in order to post unofficial results.
To this point, all ballots have been scanned, including all mail-in ballots.
Centre County's Election team and IT team have identified that the data are successfully being exported from the mail-in ballot scanners, but that the data is not being recognized when uploaded to the elections software.
Centre County's Administrator, John Franek, Jr. stated, "We have not stopped working, and we will continue to work until unofficial results are posted and reported to the Pennsylvania Department of State."
As a next step, Centre County has begun working with the equipment vendor to adjust configurations to make the two systems-the mail-in ballot scanner and the elections software where data are uploaded -compatible with one another.
We will provide updates as we make progress.
/end ID]
#sources added#us politics#us election#presidential election#2024 presidential election#election interference#election integrity#election security#image described#image description in alt#image description included#image description added#described#kamala harris#kamala 2024#us news#us presidents#updated id
36K notes
·
View notes
Text
ERP Implementation Success: Key Steps for a Smooth Transition
Embarking on an ERP Implementation Success journey is both exciting and challenging for any organization. To achieve ERP Implementation Success, businesses must follow key steps, anticipate potential challenges, and apply effective strategies. From planning and vendor selection to data migration and training, this article explores the essential aspects of ERP implementation to ensure a smooth and…
#Business Efficiency#Business Transformation#change management#Data Migration#Digital Transformation#Enterprise Software#ERP Best Practices#ERP Challenges#ERP Implementation#ERP Success#Process Optimization#Project Management#System Integration#User Training#Vendor Selection
0 notes
Text

🕵️♂️ Diving deep into the testing trenches! 🚀 Unmasking the Bug Brigade's Top 4 Most Common Intruders:
1️⃣ UI Issues – Where pixels tell tales of visual challenges. 2️⃣ Functionality Issues – Unraveling the labyrinth of feature hiccups. 3️⃣ Security Issues – Guarding the digital fortress against potential breaches. 4️⃣ Performance Issues – Navigating the speed bumps in the quest for seamless operation.
Join us on this bug-busting adventure as we shine a spotlight on the quirks and quarks of software testing! 🐛🔍
#software testing vendor#software testing company#software testing outsource#Top Testing Company to hire#testing company#Automation Testing Company#Top 5 software testing company#How to select software testing vendor/services#software testing vendor list#Top 10 software testing company#Top 15 software testing company
0 notes
Text
An Independent Review of the Industry's Top ERP Vendors!
ERP Advisors Group works with vendors across the entire #erp space, vetting and selecting the right solutions for businesses throughout multiple industries. Follow the link below for a unique look into the industry's top ERP vendors from the independent consultants at EAG!
0 notes
Link

#erp#erp system#ERP Software#erpsolutions#erp selection#erp vendors in chennai#erpdevelopment#erp dubai#erp implementation#erp integration#printing and packaging#business#technology
0 notes
Text
Immigration and Customs Enforcement is paying software company Palantir $30 million to provide the agency with “near real-time visibility” on people self-deporting from the United States, according to a contract justification published in a federal register on Thursday. The tool would also help ICE choose who to deport, giving special priority to “visa overstays,” the document shows.
Palantir has been an ICE contractor since 2011, but the document published Thursday indicates that Palantir wants to provide brand-new capabilities to ICE. The agency currently does not have any publicly known tools for tracking self-deportation in near real-time. The agency does have a tool for tracking self-reported deportations, but Thursday’s document, which was first reported by Business Insider, does not say to what degree this new tool may rely on self-reported data. ICE also has “insufficient technology” to detect people overstaying their visas, according to the Department of Homeland Security. This is particularly due to challenges in collecting "biographic and biometric" data from departing travelers, especially if they leave over land, according to Customs and Border Protection.
The agency says in the document that these new capabilities will be under a wholly new platform called the Immigration Lifecycle Operating System, or ImmigrationOS. Palantir is expected to provide a prototype of ImmigrationOS by September 25, 2025, and the contract is scheduled to last at least through September 2027. ICE’s update to the contract comes as the Trump administration is demanding that thousands of immigrants “self-deport,” or leave the US voluntarily.
ICE and Palantir did not respond for comment.
According to the document, ImmigrationOS is intended to have three core functions. Its “Targeting and Enforcement Prioritization” capability would streamline the “selection and apprehension operations of illegal aliens.” People prioritized for removal, ICE says, should be “violent criminals,” gang members, and “visa overstays.”
Its “Self-Deportation Tracking” function would have “near real-time visibility into instances of self-deporation,” the document says. The document does not say what data Palantir would use for such a system, but ICE says it aims to “accurately report metrics of alien departures from the United States.” The agency stipulates that this tool should also integrate with “enforcement prioritization systems to inform policy” but does not elaborate on these systems or policies.
Meanwhile, the “Immigration Lifecycle Process” function would streamline the “identification” of aliens and their “removal” from the United States, with the goal of making "deportation logistics” more efficient.
In a “rationale” section, ICE claims that it has an “urgent and compelling” need for ImmigrationOS’s capabilities. Without them, ICE claims, it would be “severely” limited in its ability to target the gangs MS-13 and Tren de Aragua, and abide by President Donald Trump’s executive order to expedite deportations.
Palantir, ICE claims, is “the only source that can provide the required capabilities and prototype of ImmogrationOS [sic] without causing unacceptable delays.” ICE says the company has developed “deep institutional knowledge of the agency’s operations over more than a decade of support.”
“No other vendor could meet these timeframes of having the infrastructure in place to meet this urgent requirement and deliver a prototype in less than six months,” ICE says in the document.
ICE’s document does not specify the data sources Palantir would pull from to power ImmigrationOS. However, it says that Palantir could “configure” the case management system that it has provided to ICE since 2014.
Palantir has done work at various other government agencies as early as 2007. Aside from ICE, it has worked with the US Army, Air Force, Navy, Internal Revenue Service, and Federal Bureau of Investigation. As reported by WIRED, Palantir is currently helping Elon Musk’s so-called Department of Government Efficiency (DOGE) build a brand-new “mega API” at the IRS that could search for records across all the different databases that the agency maintains.
Last week, 404 Media reported that a recent version of Palantir’s case-management system for ICE allows agents to search for people based on “hundreds of different, highly specific categories,” including how a person entered the country, their current legal status, and their country of origin. It also includes a person’s hair and eye color, whether they have scars or tattoos, and their license-plate reader data, which would provide detailed location data about where that person travels by car.
These functionalities have been mentioned in a government privacy assessment published in 2016, and it’s not clear what new information may have been integrated into the case management system over the past four years.
This week’s $30 million award is an addition to an existing Palantir contract penned in 2022, originally worth about $17 million, for work on ICE’s case management system. The agency has increased the value of the contract five times prior to this month; the largest was a $19 million increase in September 2023.
The contract’s ImmigrationOS update was first documented on April 11 in a government-run database tracking federal spending. The entry had a 248-character description of the change. The five-page document ICE published Thursday, meanwhile, has a more detailed description of Palantir’s expected services for the agency.
The contract update comes as the Trump administration deputizes ICE and other government agencies to drastically escalate the tactics and scale of deportations from the US. In recent weeks, immigration authorities have arrested and detained people with student visas and green cards, and deported at least 238 people to a brutal megaprison in El Salvador, some of whom have not been able to speak with a lawyer or have due process.
As part of its efforts to push people to self-deport, DHS in late March revoked the temporary parole of more than half a million people and demanded that they self-deport in about a month, despite having been granted authorization to live in the US after fleeing dangerous or unstable situations in Cuba, Haiti, Nicaragua, and Venezuela under the so-called “CHNV parole programs.”
Last week, the Social Security Administration listed more than 6,000 of these people as dead, a tactic meant to end their financial lives. DHS, meanwhile, sent emails to an unknown number of people declaring that their parole had been revoked and demanding that they self-deport. Several US citizens, including immigration attorneys, received the email.
On Monday, a federal judge temporarily blocked the Trump administration’s move to revoke people’s authorization to live in the US under the CHNV programs. White House spokesperson Karoline Leavitt called the judge’s ruling “rogue.”
5 notes
·
View notes
Text

The Modular Guarantee
(transcription)
It's what you can withstand. Like all of our software suites, licensed copies of Mareware Interactive's Extensions for Microsoft Windows NT 4.0™ include "The Modular Guarantee" - A New and Innovative solution that is custom-fit to suit your needs. We hear you crying out - "Not me!", and you might follow-up with the inquiry: "to what degree can we extend our coverage?". This is where we help. Bugs happen, often three at a time, but rest assured that we understand you and your plea. As 1995 carries on, Mareware Interactive continues pushing updates and improvements to our Operating System Extensions via our Monthly disk service, and as part of The Modular Guarantee.
You can reap all of these benefits for only $6.95 per month. Our monthly disk service includes new software, updates to our Operating System Extensions, and more. Be polite, comply, and try today. You can sign-up by contacting our sales department. Have you lost your line of site? Do you feel your chest tightening? Are you suffering from the consequences of your actions? You can also sign-up through select software vendors. Contact your local software vendor today and ask about Mareware Interactive's Modular Guarantee mail-order system. Disorientation has never been easier. The key is in your hands, and Mareware Interactive can walk you through it. Our words are clear, our terminology is clearer. Doesn't it feel sick? Do you feel sick? Don't ask.
#microsoft sam#arg#mareware interactive#malwareministry#themalwareministry#1995#retro computing#retro advertising#mulehorse#art#photoshop#photomanip#mockup#fake ads#alternate reality game
7 notes
·
View notes
Text
Complete Guide to Mobile Recharge Software

In the digital age, smartphone recharge apps are essential for successful prepaid and postpaid mobile top-ups. Consumers, retailers, and businesses all use this technology to fast recharge mobile phones. Companies that want to provide robust and effective mobile services must have mobile recharge software in order to meet rising demand. This article discusses the cost, features, and benefits of smartphone recharge applications, as well as tips on how to choose the best one.

Knowledge about Mobile Recharge Programs
Advanced digital mobile recharging systems enable consumers to charge mobile numbers from a variety of telecom carriers. This scheme enables retailers, distributors, and telecommunications firms to quickly recharge mobile phones. Access is also available via online, smartphone, and SMS apps.
Using mobile recharge software, a store can allow clients to swiftly reload their smartphone balances without having to visit multiple telecom providers. The application automates recharge transactions, which simplifies and accelerates the procedure.

Different Mobile Recharge Software Types
Single SIM Recharge Software allows users to charge several telecom operators with a single SIM card. It's frequent in smaller stores.
Integrates with multiple telecom operators, providing mobile recharge functionality using multi-recharge API software.
White label recharging software is ideal for entrepreneurs starting a smartphone recharge business. Their name and logo will help to establish the initiative's brand.

Features of an Excellent Mobile Recharge Program
The initiative should assist several telecom carriers with simple recharges across different providers.
A simple design makes it easier for organizations and retailers to access platforms.
Companies can connect to external APIs to expand their recharge offers and add bill payments, among other features.
The program should accept UPI, credit and debit cards, and digital wallets to offer a variety of payment options.
Encrypted data exchanges preserve user safety and prevent fraud, hence improving security and dependability.
Users should have live access to their recharge transactions to avoid errors and anomalies.
Good software should record all transactions and provide analysis for corporate expansion.

Mobile Recharge Systems Benefit Companies:
1. Offers cellphone recharging services, which increases income.
Client retention is boosted by providing prompt and courteous service; automation and API integration help to reduce operating costs.
Customers have various operators that offer quick and easy recharging options, as well as a variety of payment ways and secure transactions.
2. Mobile Recharge Software Selection Advice
Make sure the program supports many telecom carriers for convenience.
3. Evaluate Security:
Choose programs with strong fraud prevention and encryption capabilities.
Companies looking for scalability should ensure that their systems support API integration.
4. Analyze Customer Service:
Reliable assistance provides a speedy resolution of technical issues.
5. Compare Features and Cost:
Different software vendors offer different features and pricing. Examine various choices before making a decision.

Transfer of Money for Business
Effective money transmission is required in commercial operations to ensure smooth financial transactions. Companies can safely transmit and accept money using digital methods. Real-time transaction processing, enabled by technology, helps to reduce delays and improve cash flow control. A consistent money transfer system reduces transaction errors, improves security, and increases financial transparency, which benefits organizations of all sizes.
Money transfer operator facilitate computerized financial transactions between individuals and businesses. On secure platforms, these operators handle both domestic and foreign transactions quickly. They increase financial inclusion by providing easy money transfers. A reliable money transfer agency ensures that transactions are completed quickly and safely in accordance with the requirements.

About Our Offerings
Our innovative mobile recharge mechanism ensures secure transactions while remaining simple. Our products are dependable and rapid, making them ideal for merchants looking for customer satisfaction or businesses looking for a multi-operator recharge system. Companies can benefit from safe money transfer for business, which simplify and expand the accessibility of financial transactions.

FAQs
1. Explain the cellphone recharge software?
Customers can use digital mobile recharging devices to charge their prepaid and postpaid phones from a variety of telecom operators. Businesses, retailers, and phone carriers employ fast, safe recharges.
2. How does the smartphone recharging program operate?
The app uses APIs provided by numerous telecom companies to recharge mobile phones instantaneously. Users can access the system through SMS, mobile, or internet.
3. What are the commercial benefits of mobile recharge software?
Automating recharge procedures in mobile recharge systems improves revenue, customer satisfaction, and efficiency. It also allows them to provide several services from a single platform.
4. How can one find the greatest cellphone recharge app?
Select mobile recharge software based on multi-operator compatibility, security, API integration, customer service, and pricing range. Check if the program is straightforward to use and matches your company's needs.
5. Is it possible to customize smartphone charging programs?
Indeed, several cellphone recharge apps offer business-specific customization options. If necessary, you may include money transfers and bill payments.

Final Words
Companies that use the correct smartphone recharge program can improve their efficiency and service quality. Long-term success and customer involvement improve with a consistent recharging method.
2 notes
·
View notes
Text
How to Choose the Best ERP for Engineering and Manufacturing Industry
In today’s fast-paced world, engineering and manufacturing companies face increasing pressure to deliver high-quality products while maintaining efficiency and cost-effectiveness. Implementing the right Enterprise Resource Planning (ERP) software can significantly enhance operations, streamline workflows, and boost productivity. However, with numerous options available, selecting the best ERP software for the engineering and manufacturing industry can be challenging. This guide will help you navigate this decision-making process and choose the most suitable solution for your business.

Why ERP is Crucial for Engineering and Manufacturing
ERP software integrates various business processes, including production, inventory management, supply chain, finance, and human resources. For engineering and manufacturing companies, ERP solutions are particularly vital because they:
Facilitate real-time data sharing across departments.
Enhance supply chain management.
Optimize production planning and scheduling.
Ensure compliance with industry standards.
Reduce operational costs.
Partnering with the right Engineering ERP software company ensures that your organization leverages these benefits to stay competitive in a dynamic market.
Steps to Choose the Best ERP for Engineering and Manufacturing
1. Understand Your Business Needs
Before exploring ERP solutions, evaluate your company’s specific requirements. Identify the pain points in your current processes and prioritize the features you need in an ERP system. Common features for engineering and manufacturing companies include:
Bill of Materials (BOM) management
Production planning and scheduling
Inventory control
Quality management
Financial reporting
Consulting with a reputed ERP software company can help you match your needs with the right features.
2. Look for Industry-Specific Solutions
Generic ERP software might not address the unique needs of the engineering and manufacturing sector. Opt for an ERP software in India that offers modules tailored to your industry. Such solutions are designed to handle specific challenges like multi-level BOM, project costing, and shop floor management.
3. Check Vendor Expertise
Choosing a reliable vendor is as important as selecting the software itself. Research ERP solution providers with a strong track record in serving engineering and manufacturing companies. Look for reviews, case studies, and client testimonials to gauge their expertise.
4. Evaluate Scalability and Flexibility
Your business will grow, and so will your operational requirements. Ensure that the ERP system you choose is scalable and flexible enough to accommodate future needs. The top 10 ERP software providers in India offer scalable solutions that can adapt to changing business demands.
5. Assess Integration Capabilities
An ERP system must integrate seamlessly with your existing tools, such as Computer-Aided Design (CAD) software, Customer Relationship Management (CRM) systems, and IoT devices. A well-integrated system reduces redundancies and enhances efficiency.
6. Prioritize User-Friendliness
A complex system with a steep learning curve can hinder adoption. Choose an ERP software with an intuitive interface and easy navigation. This ensures that your employees can use the system effectively without extensive training.
7. Consider Customization Options
No two businesses are alike. While standard ERP solutions offer core functionalities, some companies require customization to align with specific workflows. A trusted ERP software company in India can provide custom modules tailored to your unique needs.
8. Focus on Data Security
Engineering and manufacturing companies often deal with sensitive data. Ensure that the ERP solution complies with the latest security standards and offers robust data protection features.
9. Compare Pricing and ROI
While cost is an important factor, it should not be the sole criterion. Evaluate the long-term return on investment (ROI) offered by different ERP software. A slightly expensive but feature-rich solution from the best ERP software provider in India may deliver better value than a cheaper alternative with limited functionalities.
10. Test Before You Commit
Most ERP software companies offer free trials or demo versions. Use these opportunities to test the software in a real-world scenario. Gather feedback from your team and ensure the solution meets your expectations before finalizing your decision.
Benefits of Partnering with the Best ERP Software Providers in India
India is home to some of the leading ERP software providers in India, offering state-of-the-art solutions for the engineering and manufacturing sector. Partnering with a reputable provider ensures:
Access to advanced features tailored to your industry.
Reliable customer support.
Comprehensive training and implementation services.
Regular updates and enhancements to the software.
Companies like Shantitechnology (STERP) specialize in delivering cutting-edge ERP solutions that cater specifically to engineering and manufacturing businesses. With years of expertise, they rank among the top 10 ERP software providers in India, ensuring seamless integration and exceptional performance.
Conclusion
Selecting the right ERP software is a critical decision that can impact your company’s efficiency, productivity, and profitability. By understanding your requirements, researching vendors, and prioritizing features like scalability, integration, and security, you can find the perfect ERP solution for your engineering or manufacturing business.
If you are looking for a trusted ERP software company in India, consider partnering with a provider like STERP. As one of the best ERP software providers in India, STERP offers comprehensive solutions tailored to the unique needs of engineering and manufacturing companies. With their expertise, you can streamline your operations, improve decision-making, and stay ahead in a competitive market.
Get in touch with STERP – the leading Engineering ERP software company – to transform your business with a reliable and efficient ERP system. Take the first step toward a smarter, more connected future today!
#Manufacturing ERP software company#ERP solution provider#Engineering ERP software company#ERP software company#ERP software companies
6 notes
·
View notes
Text
High-Ticket Affiliate Programs: A Comprehensive Guide for 2025
High-ticket affiliate marketing represents a strategic approach to generating substantial commissions through the promotion of premium products and services.
Unlike traditional affiliate marketing that focuses on high-volume, low-commission items, high-ticket affiliate programs offer significantly larger earnings per sale, often ranging from $500 to several thousand dollars per transaction.
The primary advantage of pursuing high-ticket affiliate programs lies in their potential for generating meaningful income with fewer sales. For instance, promoting a $2,000 product with a 40% commission yields $800 per sale, equivalent to selling eighty $10 products at a 10% commission rate.
Top High-Ticket Affiliate Programs for Serious Marketers
When evaluating high-ticket affiliate marketing opportunities, several programs stand out for their exceptional earning potential and professional support structures:
Digital Education Platforms
Commission rates: 30-50% per sale
Average product value: $1,000-$3,000
Comprehensive training materials included
Enterprise Software Solutions
Commission rates: 20-40% per sale
Average product value: $2,500-$10,000
Recurring commission opportunities
Enterprise Software Solutions
Commission rates: 15-30% per sale
Average booking value: $5,000-$15,000
Exclusive partnership opportunities
Essential Steps to Start High-Ticket Affiliate Marketing Successfully
Success in high-ticket affiliate marketing requires a strategic approach:
Market Research and Selection Begin by identifying your target audience and understanding their specific needs. High-ticket products require a more sophisticated approach to market analysis, focusing on demographics with substantial purchasing power.
Platform Development Establish a professional online presence through:
A professionally designed website
Authoritative content development
Strategic social media positioning
Relationship Building Develop strong relationships with:
Program vendors
Industry influencers
Potential customers through value-driven content
Advanced Strategies for Promoting High-Ticket Affiliate Products
To maximize success in high-ticket affiliate marketing, implement these advanced strategies:
Content Marketing Excellence Create comprehensive content that demonstrates expertise and builds trust. This includes:
Detailed product reviews
Case studies
Expert interviews
Educational webinars
Email Marketing Automation Develop sophisticated email sequences that:
Nurture potential customers
Provide valuable insights
Build credibility over time
Guide prospects through the decision-making process
Personal Brand Development Establish yourself as an authority in your chosen niche by:
Speaking at industry events
Publishing thought leadership content
Participating in professional networks
Showcasing successful case studies
Success in high-ticket affiliate marketing stems from building genuine relationships and providing substantial value to your audience. Focus on understanding your target market's needs and consistently delivering solutions that address their specific challenges. Remember that while the commission potential is significant, the responsibility to provide accurate, valuable information to your audience is paramount.
2 notes
·
View notes
Text
What Are the Best Payout Solutions for Your Business?

In today’s fast-paced digital economy, businesses of all sizes need efficient and secure payout solutions to manage their financial transactions. Whether you're running a small e-commerce store, a large enterprise, or providing services in the gig economy, selecting the right payout solution is crucial. From disbursing salaries to paying vendors or customers, a seamless payout process can enhance trust and streamline operations.
In this article, we will explore the best payout solutions for businesses, focusing on their features, benefits, and how they cater to diverse business needs. We’ll also touch upon the importance of working with a reliable micro ATM service provider and highlight Xettle Technologies as an example of innovation in this space.
Understanding Payout Solutions
Payout solutions refer to systems or platforms that facilitate the transfer of funds from a business to its employees, partners, customers, or vendors. These solutions are essential for ensuring smooth financial transactions and reducing manual intervention. Modern payout solutions are designed to be flexible, secure, and capable of handling high transaction volumes with ease.
The best payout solution for your business will depend on several factors, including the size of your company, the frequency of payouts, and the geographical location of your recipients. Let’s dive into the key elements to consider when selecting the right solution.
Features of Effective Payout Solutions
Multi-Channel Accessibility A good payout solution should support multiple payment channels, such as bank transfers, mobile wallets, UPI, and cards. This ensures that your business can cater to the diverse preferences of your recipients.
Scalability As your business grows, your payout needs will evolve. A scalable solution can accommodate increasing transaction volumes without compromising on speed or security.
Security and Compliance Protecting sensitive financial data is paramount. Choose a payout solution that complies with industry standards and regulatory requirements, ensuring the safety of your transactions.
Integration Capabilities Seamless integration with your existing systems, such as accounting software or enterprise resource planning (ERP) tools, can simplify operations and improve efficiency.
Real-Time Processing In today’s competitive environment, real-time payouts can be a game-changer. Recipients value quick access to their funds, making this a must-have feature.
Types of Payout Solutions
1. Bank Transfers
This is one of the most common methods, offering a direct and secure way to transfer funds to recipients' bank accounts. However, it may not be ideal for real-time payouts due to processing times.
2. Digital Wallets
Digital wallets like Paytm, Google Pay, and others provide a convenient and fast way to transfer funds. They are particularly popular in regions with high mobile penetration.
3. Prepaid Cards
Prepaid cards are a versatile option that allows businesses to load funds for employees or customers. They can be used for shopping or cash withdrawals.
4. Micro ATM Services
For businesses operating in rural or remote areas, a micro ATM service provider can be a game-changer. These services enable cash disbursements even in areas with limited banking infrastructure, bridging the financial inclusion gap.
How Micro ATM Service Providers Add Value
Micro ATM service providers are transforming the way businesses manage payouts in underbanked regions. These portable devices allow users to perform basic banking functions, such as cash withdrawals, balance inquiries, and fund transfers. By partnering with a reliable micro ATM service provider, businesses can expand their reach and cater to rural audiences effectively.
For instance, a small-scale retailer or a government agency can use micro ATM services to disburse payments to beneficiaries without requiring them to travel long distances to access banking facilities. This enhances convenience and boosts trust among recipients.
A Spotlight on Xettle Technologies
Xettle Technologies has emerged as a leader in the payout solutions space, offering innovative platforms that cater to diverse business needs. Their solutions are designed to enhance operational efficiency and provide a seamless experience for businesses and recipients alike. By leveraging advanced technology, Xettle Technologies ensures secure, real-time payouts while simplifying the integration process for businesses.
Choosing the Right Payout Solution
Selecting the best payout solution requires careful consideration of your business’s specific needs. Here are some steps to guide you:
Assess Your Requirements Determine the frequency and volume of payouts your business handles. This will help you identify a solution that matches your operational scale.
Evaluate Security Measures Ensure the platform offers robust encryption, fraud detection, and compliance with financial regulations.
Test for User-Friendliness The solution should be easy to use for both your team and your recipients. Look for platforms with intuitive interfaces and reliable customer support.
Consider Costs Compare the transaction fees, setup costs, and other charges associated with different solutions. Opt for one that offers value for money without compromising on quality.
Final Thoughts
Choosing the right payout solution is not just about facilitating transactions; it’s about building trust and ensuring smooth financial operations. Whether you’re looking for traditional methods like bank transfers or innovative options like micro ATM services, the key lies in understanding your business needs and selecting a partner that aligns with your goals.
From scalability to security, modern payout solutions offer a range of features that can empower your business to operate efficiently in a competitive landscape. By leveraging the right tools and technologies, such as those offered by Xettle Technologies, you can simplify your payout processes and focus on growing your business.
2 notes
·
View notes
Text
CompTIA Certifications: Your Gateway to IT Success

Introduction
In today's technology-driven world, IT professionals play a crucial role in driving innovation and business growth. To validate their skills and stand out in the competitive job market, many individuals seek industry-recognized certifications. CompTIA certifications have emerged as a popular choice, offering a comprehensive pathway to IT success.
What are CompTIA Certifications?
CompTIA, the Computing Technology Industry Association, is a non-profit trade association that develops and delivers vendor-neutral IT certifications. These certifications are designed to assess an individual's knowledge and skills in various IT domains, including networking, cybersecurity, and cloud computing.
Benefits of CompTIA Certifications
Enhanced Career Prospects: CompTIA certifications are highly valued by employers worldwide. Earning a CompTIA certification can significantly boost your job prospects and open doors to new opportunities.
Increased Earning Potential: Certified IT professionals often command higher salaries compared to their non-certified counterparts. CompTIA certifications can directly contribute to your financial growth.
Industry Recognition: CompTIA certifications are recognized and respected throughout the IT industry. They serve as a testament to your expertise and professionalism.
Skill Development: Preparing for and passing a CompTIA certification requires a deep understanding of the relevant IT concepts and technologies. This process helps you develop valuable skills that can be applied in your daily work.
Vendor Neutrality: Unlike vendor-specific certifications, CompTIA certifications are vendor-neutral. This means they are not tied to a particular product or technology, making them more versatile and adaptable to various IT environments.
Popular CompTIA Certifications
CompTIA A+: This entry-level certification is ideal for IT professionals who want to build a solid foundation in computer hardware and software.
CompTIA Network+: This certification validates your knowledge of networking fundamentals, including network infrastructure, protocols, and troubleshooting.
CompTIA Security+: This certification focuses on cybersecurity and equips you with the skills to protect systems and data from threats.
CompTIA PenTest+: This certification validates your skills in penetration testing, a crucial aspect of cybersecurity.
CompTIA Data+: This certification focuses on data analysis and validates your ability to collect, analyze, and interpret data.
How to Prepare for a CompTIA Certification
Identify Your Goals: Determine which CompTIA certification aligns with your career aspirations and current skill level.
Choose Study Materials: Select high-quality study materials, such as textbooks, practice exams, and online courses.
Create a Study Plan: Develop a structured study plan that covers all the exam objectives.
Practice Regularly: Take advantage of practice exams to assess your knowledge and identify areas for improvement.
Join Study Groups: Connect with other candidates to share knowledge and motivation.
Opting certification courses: Enroll the CompTIA courses from Xaltius Academy.
Conclusion
CompTIA certifications offer a valuable pathway to IT success. By earning a CompTIA certification, you can enhance your career prospects, increase your earning potential, and gain recognition as a skilled IT professional. If you're looking to advance your IT career, consider pursuing a CompTIA certification.
2 notes
·
View notes
Text
Importance of Dental software
Feeling overwhelmed managing appointments, patient records, billing, and insurance on top of providing excellent patient care? Dental practice management software (DPMS) can be your secret weapon!
Think of DPMS as your digital assistant, streamlining these tasks and freeing up valuable time for what matters most: focusing on your patients' smiles.
Here's how DPMS can revolutionize your dental practice:
Boost Efficiency: DPMS automates tasks like scheduling, billing, and recordkeeping, allowing you and your staff to dedicate more time to patient interaction.
Ditch the Paperwork: Say goodbye to overflowing file cabinets! Electronic records save space and make patient information readily accessible.
Enhanced Patient Communication: Improve communication with features like automated appointment reminders and online patient portals.
Smoother Financial Management: Streamline billing with automated processes and insurance verification, leading to faster and easier collections.
Inventory Management Made Easy: DPMS helps you track dental supplies and equipment, reducing waste and ensuring you have what you need when you need it.
Data-Driven Decisions: Generate insightful reports on patient demographics, treatment trends, and practice performance, empowering you to make informed decisions for your practice.
Choosing the Right DPMS: Cloud-Based vs. On-Premise
There are two main types of DPMS: cloud-based and on-premise. Understanding the differences is crucial for selecting the best fit for your practice.
Cloud-Based Dental Practice Management Software:
Imagine accessing software through the internet. Your data is securely stored on the vendor's servers and is accessible from any device with an internet connection.
Benefits:
Easy Setup and Maintenance: No software installation or server management needed. Updates are automatic.
Scalability: Grows with your practice – easily add users or features as needed.
Accessibility: Access patient information and manage your practice from anywhere, anytime.
Ideal for: Smaller practices, solo practitioners, or those who value flexibility and remote access.
On-Premise DPMS:
Traditional software installed directly on your practice computers. You have complete control over the data stored on your servers.
Benefits:
Customization: May offer more customization options for specific workflows.
Data Security: Some dentists prefer having complete control over their data on-site.
Drawbacks:
Higher Upfront Costs: Requires purchasing software licenses and server hardware.
IT Maintenance: Relies on in-house IT expertise or external support for updates and maintenance.
Scalability: Scaling up can be complex and requires additional hardware and software licenses.
Ideal for: Larger practices with dedicated IT staff or those who prioritize complete on-site data control.
The Bottom Line:
The best DPMS choice depends on your practice size, budget, and IT capabilities. Cloud-based solutions offer ease of use and scalability, while on-premise systems provide more customization and potential data control. Consider your priorities and consult with DPMS vendors to find the perfect fit for your dental practice.
Ready to explore how DPMS can transform your practice? Try this
2 notes
·
View notes
Text
This Week in Rust 534
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
Announcing Rust 1.76.0
This Development-cycle in Cargo: 1.77
Project/Tooling Updates
zbus 4.0 released. zbus is a pure Rust D-Bus crate. The new version brings a more ergonomic and safer API. Release: zbus4
This Month in Rust OSDev: January 2024
Rerun 0.13 - real-time kHz time series in a multimodal visualizer
egui 0.26 - Text selection in labels
Hello, Selium! Yet another streaming platform, but easier
Observations/Thoughts
Which red is your function?
Porting libyaml to Safe Rust: Some Thoughts
Design safe collection API with compile-time reference stability in Rust
Cross compiling Rust to win32
Modular: Mojo vs. Rust: is Mojo 🔥 faster than Rust 🦀 ?
Extending Rust's Effect System
Allocation-free decoding with traits and high-ranked trait bounds
Cross-Compiling Your Project in Rust
Kind: Our Rust library that provides zero-cost, type-safe identifiers
Performance Roulette: The Luck of Code Alignment
Too dangerous for C++
Building an Uptime Monitor in Rust
Box Plots at the Olympics
Rust in Production: Interview with FOSSA
Performance Pitfalls of Async Function Pointers (and Why It Might Not Matter)
Error management in Rust, and libs that support it
Finishing Turborepo's migration from Go to Rust
Rust: Reading a file line by line while being mindful of RAM usage
Why Rust? It's the safe choice
[video] Rust 1.76.0: 73 highlights in 24 minutes!
Rust Walkthroughs
Rust/C++ Interop Part 1 - Just the Basics
Rust/C++ Interop Part 2 - CMake
Speeding up data analysis with Rayon and Rust
Calling Rust FFI libraries from Go
Write a simple TCP chat server in Rust
[video] Google Oauth with GraphQL API written in Rust - part 1. Registration mutation.
Miscellaneous
The book "Asynchronous Programming in Rust" is released
January 2024 Rust Jobs Report
Chasing a bug in a SAT solver
Rust for hardware vendors
[audio] How To Secure Your Audio Code Using Rust With Chase Kanipe
[audio] Tweede Golf - Rust in Production Podcast
[video] RustConf 2023
[video] Decrusting the tracing crate
Crate of the Week
This week's crate is microflow, a robust and efficient TinyML inference engine for embedded systems.
Thanks to matteocarnelos for the self-suggestion!
Please submit your suggestions and votes for next week!
Call for Participation; projects and speakers
CFP - Projects
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
* Hyperswitch - [FEATURE]: Setup code coverage for local tests & CI * Hyperswitch - [FEATURE]: Have get_required_value to use ValidationError in OptionExt
If you are a Rust project owner and are looking for contributors, please submit tasks here.
CFP - Speakers
Are you a new or experienced speaker looking for a place to share something cool? This section highlights events that are being planned and are accepting submissions to join their event as a speaker.
Devoxx PL 2024 | CFP closes 2024-03-01 | Krakow, Poland | Event date: 2024-06-19 - 2024-06-21
RustFest Zürich 2024 CFP closes 2024-03-31 | Zürich, Switzerland | Event date: 2024-06-19 - 2024-06-24
If you are an event organizer hoping to expand the reach of your event, please submit a link to the submission website through a PR to TWiR.
Updates from the Rust Project
466 pull requests were merged in the last week
add armv8r-none-eabihf target for the Cortex-R52
add lahfsahf and prfchw target feature
check_consts: fix duplicate errors, make importance consistent
interpret/write_discriminant: when encoding niched variant, ensure the stored value matches
large_assignments: Allow moves into functions
pattern_analysis: gather up place-relevant info
pattern_analysis: track usefulness without interior mutability
account for non-overlapping unmet trait bounds in suggestion
account for unbounded type param receiver in suggestions
add support for custom JSON targets when using build-std
add unstable -Z direct-access-external-data cmdline flag for rustc
allow restricted trait impls under #[allow_internal_unstable(min_specialization)]
always check the result of pthread_mutex_lock
avoid ICE in drop recursion check in case of invalid drop impls
avoid a collection and iteration on empty passes
avoid accessing the HIR in the happy path of coherent_trait
bail out of drop elaboration when encountering error types
build DebugInfo for async closures
check that the ABI of the instance we are inlining is correct
clean inlined type alias with correct param-env
continue to borrowck even if there were previous errors
coverage: split out counter increment sites from BCB node/edge counters
create try_new function for ThinBox
deduplicate tcx.instance_mir(instance) calls in try_instance_mir
don't expect early-bound region to be local when reporting errors in RPITIT well-formedness
don't skip coercions for types with errors
emit a diagnostic for invalid target options
emit more specific diagnostics when enums fail to cast with as
encode coroutine_for_closure for foreign crates
exhaustiveness: prefer "0..MAX not covered" to "_ not covered"
fix ICE for deref coercions with type errors
fix ErrorGuaranteed unsoundness with stash/steal
fix cycle error when a static and a promoted are mutually recursive
fix more ty::Error ICEs in MIR passes
for E0223, suggest associated functions that are similar to the path
for a rigid projection, recursively look at the self type's item bounds to fix the associated_type_bounds feature
gracefully handle non-WF alias in assemble_alias_bound_candidates_recur
harmonize AsyncFn implementations, make async closures conditionally impl Fn* traits
hide impls if trait bound is proven from env
hir: make sure all HirIds have corresponding HIR Nodes
improve 'generic param from outer item' error for Self and inside static/const items
improve normalization of Pointee::Metadata
improve pretty printing for associated items in trait objects
introduce enter_forall to supercede instantiate_binder_with_placeholders
lowering unnamed fields and anonymous adt
make min_exhaustive_patterns match exhaustive_patterns better
make it so that async-fn-in-trait is compatible with a concrete future in implementation
make privacy visitor use types more (instead of HIR)
make traits / trait methods detected by the dead code lint
mark "unused binding" suggestion as maybe incorrect
match lowering: consistently lower bindings deepest-first
merge impl_polarity and impl_trait_ref queries
more internal emit diagnostics cleanups
move path implementations into sys
normalize type outlives obligations in NLL for new solver
print image input file and checksum in CI only
print kind of coroutine closure
properly handle async block and async fn in if exprs without else
provide more suggestions on invalid equality where bounds
record coroutine kind in coroutine generics
remove some unchecked_claim_error_was_emitted calls
resolve: unload speculatively resolved crates before freezing cstore
rework support for async closures; allow them to return futures that borrow from the closure's captures
static mut: allow mutable reference to arbitrary types, not just slices and arrays
stop bailing out from compilation just because there were incoherent traits
suggest [tail @ ..] on [..tail] and [...tail] where tail is unresolved
suggest less bug-prone construction of Duration in docs
suggest name value cfg when only value is used for check-cfg
suggest pattern tests when modifying exhaustiveness
suggest turning if let into irrefutable let if appropriate
suppress suggestions in derive macro
take empty where bounds into account when suggesting predicates
toggle assert_unsafe_precondition in codegen instead of expansion
turn the "no saved object file in work product" ICE into a translatable fatal error
warn on references casting to bigger memory layout
unstably allow constants to refer to statics and read from immutable statics
use the same mir-opt bless targets on all platforms
enable MIR JumpThreading by default
fix mir pass ICE in the presence of other errors
miri: fix ICE with symbolic alignment check on extern static
miri: implement the mmap64 foreign item
prevent running some code if it is already in the map
A trait's local impls are trivially coherent if there are no impls
use ensure when the result of the query is not needed beyond its Resultness
implement SystemTime for UEFI
implement sys/thread for UEFI
core/time: avoid divisions in Duration::new
core: add Duration constructors
make NonZero constructors generic
reconstify Add
replace pthread RwLock with custom implementation
simd intrinsics: add simd_shuffle_generic and other missing intrinsics
cargo: test-support: remove special case for $message_type
cargo: don't add the new package to workspace.members if there is no existing workspace in Cargo.toml
cargo: enable edition migration for 2024
cargo: feat: add hint for adding members to workspace
cargo: fix confusing error messages for sparse index replaced source
cargo: fix: don't duplicate comments when editing TOML
cargo: relax a test to permit warnings to be emitted, too
rustdoc: Correctly generate path for non-local items in source code pages
bindgen: add target mappings for riscv64imac and riscv32imafc
bindgen: feat: add headers option
clippy: mem_replace_with_default No longer triggers on unused expression
clippy: similar_names: don't raise if the first character is different
clippy: to_string_trait_impl: avoid linting if the impl is a specialization
clippy: unconditional_recursion: compare by Tys instead of DefIds
clippy: don't allow derive macros to silence disallowed_macros
clippy: don't lint incompatible_msrv in test code
clippy: extend NONMINIMAL_BOOL lint
clippy: fix broken URL in Lint Configuration
clippy: fix false positive in redundant_type_annotations lint
clippy: add autofixes for unnecessary_fallible_conversions
clippy: fix: ICE when array index exceeds usize
clippy: refactor implied_bounds_in_impls lint
clippy: return Some from walk_to_expr_usage more
clippy: stop linting blocks_in_conditions on match with weird attr macro case
rust-analyzer: abstract more over ItemTreeLoc-like structs
rust-analyzer: better error message for when proc-macros have not yet been built
rust-analyzer: add "unnecessary else" diagnostic and fix
rust-analyzer: add break and return postfix keyword completions
rust-analyzer: add diagnostic with fix to replace trailing return <val>; with <val>
rust-analyzer: add incorrect case diagnostics for traits and their associated items
rust-analyzer: allow cargo check to run on only the current package
rust-analyzer: completion list suggests constructor like & builder methods first
rust-analyzer: improve support for ignored proc macros
rust-analyzer: introduce term search to rust-analyzer
rust-analyzer: create UnindexedProject notification to be sent to the client
rust-analyzer: substitute $saved_file in custom check commands
rust-analyzer: fix incorrect inlining of functions that come from MBE macros
rust-analyzer: waker_getters tracking issue from 87021 for 96992
rust-analyzer: fix macro transcriber emitting incorrect lifetime tokens
rust-analyzer: fix target layout fetching
rust-analyzer: fix tuple structs not rendering visibility in their fields
rust-analyzer: highlight rustdoc
rust-analyzer: preserve where clause when builtin derive
rust-analyzer: recover from missing argument in call expressions
rust-analyzer: remove unnecessary .as_ref() in generate getter assist
rust-analyzer: validate literals in proc-macro-srv FreeFunctions::literal_from_str
rust-analyzer: implement literal_from_str for proc macro server
rust-analyzer: implement convert to guarded return assist for let statement with type that implements std::ops::Try
Rust Compiler Performance Triage
Relatively balanced results this week, with more improvements than regressions. Some of the larger regressions are not relevant, however there was a real large regression on doc builds, that was caused by a correctness fix (rustdoc was doing the wrong thing before).
Triage done by @kobzol. Revision range: 0984becf..74c3f5a1
Summary:
(instructions:u) mean range count Regressions ❌ (primary) 2.1% [0.2%, 12.0%] 44 Regressions ❌ (secondary) 5.2% [0.2%, 20.1%] 76 Improvements ✅ (primary) -0.7% [-2.4%, -0.2%] 139 Improvements ✅ (secondary) -1.3% [-3.3%, -0.3%] 86 All ❌✅ (primary) -0.1% [-2.4%, 12.0%] 183
6 Regressions, 5 Improvements, 8 Mixed; 5 of them in rollups 53 artifact comparisons made in total
Full report here
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
eRFC: Iterate on and stabilize libtest's programmatic output
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
RFC: Rust Has Provenance
Tracking Issues & PRs
Rust
[disposition: close] Implement Future for Option<F>
[disposition: merge] Tracking Issue for min_exhaustive_patterns
[disposition: merge] Make unsafe_op_in_unsafe_fn warn-by-default starting in 2024 edition
Cargo
[disposition: merge] feat: respect rust-version when generating lockfile
New and Updated RFCs
No New or Updated RFCs were created this week.
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
RFC: Checking conditional compilation at compile time
Testing steps
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Upcoming Events
Rusty Events between 2024-02-14 - 2024-03-13 💕 🦀 💕
Virtual
2024-02-15 | Virtual (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn
2024-02-15 | Virtual + In person (Praha, CZ) | Rust Czech Republic
Introduction and Rust in production
2024-02-19 | Virtual (Melbourne, VIC, AU)| Rust Melbourne
(Hybrid - in person & online) February 2024 Rust Melbourne Meetup - Day 1
2024-02-20 | Virtual (Melbourne, VIC, AU) | Rust Melbourne
(Hybrid - in person & online) February 2024 Rust Melbourne Meetup - Day 2
2024-02-20 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful
2024-02-20 | Virtual | Rust for Lunch
Lunch
2024-02-21 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
Rust for Rustaceans Book Club: Chapter 2 - Types
2024-02-21 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2024-02-22 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-02-27 | Virtual (Dallas, TX, US) | Dallas Rust
Last Tuesday
2024-02-29 | Virtual (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup | Mirror: Berline.rs page
2024-02-29 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Surfing the Rusty Wireless Waves with the ESP32-C3 Board
2024-03-06 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2024-03-07 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-03-12 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2024-03-12 | Hybrid (Virtual + In-person) Munich, DE | Rust Munich
Rust Munich 2024 / 1 - hybrid
Asia
2024-02-17 | New Delhi, IN | Rust Delhi
Meetup #5
Europe
2024-02-15 | Copenhagen, DK | Copenhagen Rust Community
Rust Hacknight #2: Compilers
2024-02-15 | Praha, CZ - Virtual + In-person | Rust Czech Republic
Introduction and Rust in production
2024-02-21 | Lyon, FR | Rust Lyon
Rust Lyon Meetup #8
2024-02-22 | Aarhus, DK | Rust Aarhus
Rust and Talk at Partisia
2024-02-29 | Berlin, DE | Rust Berlin
Rust and Tell - Season start 2024
2024-03-12 | Munich, DE + Virtual | Rust Munich
Rust Munich 2024 / 1 - hybrid
North America
2024-02-15 | Boston, MA, US | Boston Rust Meetup
Back Bay Rust Lunch, Feb 15
2024-02-15 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2024-02-20 | New York, NY, US | Rust NYC
Rust NYC Monthly Mixer (Moved to Feb 20th)
2024-02-20 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2024-02-21 | Boston, MA, US | Boston Rust Meetup
Evening Boston Rust Meetup at Microsoft, February 21
2024-02-22 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
2024-02-28 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
2024-03-07 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
Oceania
2024-02-19 | Melbourne, VIC, AU + Virtual | Rust Melbourne
(Hybrid - in person & online) February 2024 Rust Melbourne Meetup - Day 1
2024-02-20 | Melbourne, VIC, AU + Virtual | Rust Melbourne
(Hybrid - in person & online) February 2024 Rust Melbourne Meetup - Day 2
2024-02-27 | Canberra, ACT, AU | Canberra Rust User Group
February Meetup
2024-02-27 | Sydney, NSW, AU | Rust Sydney
🦀 spire ⚡ & Quick
2024-03-05 | Auckland, NZ | Rust AKL
Rust AKL: Introduction to Embedded Rust + The State of Rust UI
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
For some weird reason the Elixir Discord community has a distinct lack of programmer-socks-wearing queer furries, at least compared to Rust, or even most other tech-y Discord servers I’ve seen. It caused some weird cognitive dissonance. Why do I feel vaguely strange hanging out online with all these kind, knowledgeable, friendly and compassionate techbro’s? Then I see a name I recognized from elsewhere and my hindbrain goes “oh thank gods, I know for a fact she’s actually a snow leopard in her free time”. Okay, this nitpick is firmly tongue-in-cheek, but the Rust user-base continues to be a fascinating case study in how many weirdos you can get together in one place when you very explicitly say it’s ok to be a weirdo.
– SimonHeath on the alopex Wiki's ElixirNitpicks page
Thanks to Brian Kung for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
3 notes
·
View notes
Text
Unmasking the Invisible: Ethical Hackers and the Art of Vulnerability Hunting

In today's digital age, our reliance on technology has created a vast and interconnected landscape. While this interconnectedness offers undeniable benefits, it also introduces vulnerabilities – chinks in the armor that can be exploited by malicious actors. Imagine a grand castle, its walls seemingly impenetrable. But what if there were hidden weaknesses, unseen passages known only to a select few? This is where ethical hackers, the unsung heroes of cybersecurity, come in. They are the vulnerability hunters, the digital detectives on a relentless quest to identify and expose these weaknesses before they can be used for malicious purposes.
This blog delves into the fascinating world of vulnerability hunting, exploring the role of ethical hackers in safeguarding our digital assets. We'll uncover the techniques they employ, the challenges they face, and the importance of cyber security training Mumbai for fostering a skilled workforce of ethical hackers.
The Invisible Threat: Unveiling Vulnerabilities
Imagine a digital thief attempting to break into a bank vault. They wouldn't simply smash through the front door; they'd meticulously search for weaknesses – a faulty security system, a hidden ventilation shaft. Similarly, vulnerabilities in software, hardware, and network configurations act as those hidden access points for malicious hackers. These vulnerabilities can be:
Software Bugs: Errors in the code that can be exploited to gain unauthorized access or cause unexpected behavior.
Misconfigurations: Improper settings in network devices or software applications that create security gaps.
Zero-Day Attacks: Previously unknown vulnerabilities that attackers exploit before software vendors have a chance to issue a patch.
These vulnerabilities are often invisible to the untrained eye. This is where ethical hackers, also known as white hats, step in. They act as the security guardians, wielding specialized tools and techniques to hunt for these hidden weaknesses.
The Art of the Hunt: Techniques of a Vulnerability Hunter
Ethical hackers employ a diverse arsenal of techniques in their pursuit of vulnerabilities. Here are some of the most common methods which you can learn in cyber security training mumbai :
Network Scanning: Ethical hackers use specialized tools to scan networks and identify devices, open ports, and potential security weaknesses.
Penetration Testing: This involves simulating a cyberattack to identify vulnerabilities that could be exploited by malicious actors. Ethical hackers attempt to gain unauthorized access to systems using various techniques, mimicking the methods black hats might employ.
Social Engineering Testing: This involves testing the organization's security awareness by attempting to trick employees into revealing sensitive information or clicking on malicious links.
Code Review: Ethical hackers meticulously examine the code of software applications to identify potential vulnerabilities and bugs.
These techniques require a deep understanding of cybersecurity principles, programming languages, and hacking methodologies. Cyber security training Mumbai can equip individuals with the necessary skills and knowledge to become proficient vulnerability hunters.
The Challenges of the Hunt: A Constant Cat-and-Mouse Game
The world of vulnerability hunting is a constant cat-and-mouse game. As technology evolves, so do the vulnerabilities that ethical hackers need to identify. Here are some of the key challenges they face:
The Ever-Expanding Attack Surface: With the increasing use of cloud computing, mobile devices, and the Internet of Things (IoT), the attack surface – the potential points of entry for attackers – is constantly expanding. This makes it more challenging for ethical hackers to identify all potential vulnerabilities.
Zero-Day Attacks: The constant threat of zero-day attacks, where attackers exploit previously unknown vulnerabilities, keeps ethical hackers on their toes. They need to be constantly researching and developing new methods to identify these vulnerabilities before they can be used in real-world attacks.
Staying Ahead of Black Hats: Malicious hackers are constantly innovating and developing new attack techniques. Ethical hackers need to stay up-to-date on the latest hacking trends and methodologies to ensure they can identify vulnerabilities before they are exploited.
The Value of the Hunt: Why Vulnerability Hunting Matters
Vulnerability hunting plays a critical role in safeguarding our digital infrastructure. By proactively identifying and patching vulnerabilities, ethical hackers can significantly reduce the risk of successful cyberattacks. Here are some of the key benefits of vulnerability hunting:
Reduced Risk of Cyberattacks: By identifying and patching vulnerabilities, ethical hackers make it more difficult for malicious actors to gain unauthorized access to systems and data.
Improved Security Posture: The process of vulnerability hunting helps organizations identify and address weaknesses in their overall security posture, leading to a more robust defense.
Enhanced Compliance: Many regulations require organizations to conduct regular vulnerability assessments. Ethical hacking helps organizations meet these compliance requirements.
Cyber security training Mumbai can equip individuals with the skills to become ethical hackers, contributing to a safer digital landscape. These courses can provide valuable knowledge on vulnerability hunting methodologies, penetration testing techniques, and ethical hacking best practices.
2 notes
·
View notes