#secure data backup
Explore tagged Tumblr posts
Text
#big data#file replication#data protection#file synchronization software#data management#cloud solutions#secure data backup#cloud software
0 notes
Text
Cybersecurity is a critical aspect of modern business operations. With the increasing digitization of processes and data, businesses face a range of cyber threats that can compromise sensitive information and disrupt operations.
0 notes
Text

118 notes
·
View notes
Text
Secure Configurations on your Technology

Ensuring secure configurations on your technology is crucial to protect against cyber threats and vulnerabilities. Here are some tips to make sure your configurations are secure:
-Change Default Settings: Always change default usernames and passwords on your devices.
-Enable Firewalls: Use firewalls to block unauthorized access to your network.
-Regular Updates: Keep your software and firmware up to date to patch any security holes.
-Strong Passwords: Use complex and unique passwords for all your accounts and devices.
-Disable Unnecessary Services: Turn off services and features you don't use to reduce potential entry points for attackers.
-Monitor and Audit: Regularly monitor and audit your configurations to ensure they remain secure.
Stay vigilant and keep your technology secure! #CyberSecurity #SecureConfigurations #StaySafe – www.centurygroup.net
#Cybersecurity#managed it services#data backup#Secured Configuration#cloud technology services#phishing
2 notes
·
View notes
Text
aside from directly dealing with The Agency's competitors/threats/etc, Antares also gets sent out for other jobs ranging from deliveries to acting as a bodyguard
this is so that i can get some flexibility here and also i think he should be able to run into the fivemind units more often aside from like...trying to destroy them and going to the grocery store and stuff
#[ out of circuits ]#(( sometimes he just acts as backup for whatever villain of the week or like security detail for larger evil plans ig#he can also petsit#if given the choice he always goes for shit like 'yeah i'll watch the shark tank :>'#[ data : antares ]
3 notes
·
View notes
Text
youtube
2 notes
·
View notes
Text
The above is not a great conclusion;
You shouldn't use flash drives for any important data at all, actually. This goes for all flash memory, so sd cards are out as well. Flash memory is really easy to corrupt, especially in active use. So use something more permanent like a hard disk or SSD. Disconnecting flash drives like OP suggest is good practice if you want them to last longer without corruption. I'll give them that.
Additionally, you should have at least one additional copy of stuff you want to keep. This can be on an external hard drive or SSD, cd's, dvd's, blurays, dedicated backup tape-recorders, in print, or on a cloud service.
Keep in mind though, cloud services have the side effect of your backup being at the mercy of corporations & their content crawlers with little to no possibility to appeal if you're banned. So like erroneous tumblr flags, but with your personal pictures and with way worse repercussions.
I'm not an expert on different types of storage but the advice of OP is really bad. Just don't use flash drives for anything you want to keep. Just to reiterate: your memories are not at all safe on a flash drive, whatever you do with the drive.
Devices break, keep multiple copies.
PSA- TAKE YOUR FLASHDRIVE OUT OF YOUR COMPUTER
If you are not using your flashdrive to actively back things up- TAKE IT OUT OF YOUR COMPUTER! DO IT NOW! RIGHT. NOW.
Yesterday one of my flashdrives stopped working. My mom took it to our local computer guy to find out what was wrong with it and the guy said the the ONLY way that it could POSSIBLY (not definitely, POSSIBLY) be recovered is by sending it to a FORENSICS COMPANY that charges NINE HUNDRED AND FIFTY DOLLARS ($950) as a flat rate for this service. IF the stuff can even be recovered.
The computer guy said that he has seen all types of flashdrives, no matter the quality, fail because people don't know that they need to take them out of their computers when they're not using them. A few of the things that can happen are the flashdrive can overheat or a virus could destroy it if your computer happens to pick up a virus.
I have thousands of pictures and videos on that flashdrive, precious, precious memories of kids I've worked with that I may never see again in my life and now I might have lost them because I didn't know to take my flashdrive out of my computer when I'm not using it. The cute pictures of my three new kittens I've been posting? On that flashdrive. Memories from holidays and birthdays and camping adventures might be lost forever.
TAKE. YOUR. FLASHDRIVE. OUT. OF. YOUR. COMPUTER!!!!!!
(please for the love of all that is good share this so other people don't have it happen too)
#I lost a lot of data because I thought i had a backup set up correctly but didn't and the hard disk died#hard disks are WAY more stable than flash drives. Like orders of magnitude more stable. And mine died after just two years and a bit#part of me not checking if the backups were running correctly was the false sense of security the relatively new hard drive gave me#the key to keeping your data safe isn't betting on devices to work forever but keeping multiple (physical) copies
6K notes
·
View notes
Text
Security and privacy issues in cloud computing
New Post has been published on https://thedigitalinsider.com/security-and-privacy-issues-in-cloud-computing/
Security and privacy issues in cloud computing

Cloud computing is the main support for many companies worldwide. More businesses are moving to cloud computing to improve how they work and compete.
It’s important to find the top security problems in cloud computing. Data leaks caused by cloud setup mistakes and past data leaks need to be watched. This is to avoid impact on the company.
What is cloud computing?
Cloud computing changes how we manage, access, and store data. This is done through internet services. This is different from the old way of using storage devices.

The new cloud-computing model means you do not have to worry about managing servers. Both companies and people can benefit. They get strong data security and flexible, low-cost, and easy-to-adapt data solutions in the cloud.
Why do you need cloud computing?
Companies can use secure data centers, lower infrastructure costs, and do operation optimization at full length. It increases efficiency, lowers costs, and empowers businesses.
With cloud computing, an organization can quickly adjust resources to match demand without requiring large initial hardware investments.
An organization needs to pay for only the resources it consumes, lowering expenses for infrastructure and upkeep.
You can access data and applications remotely with an internet connection, which increases accessibility to work and collaboration.
You can, however, enable fast deployment of new applications and services, eliminating the lengthy lead times of traditional IT methods.
In cloud computing, service providers take care of maintenance and updates, guaranteeing that you constantly receive the most up-to-date features and security.
Numerous cloud services provide strong backup and recovery options, reducing downtime in the event of data loss.
It streamlines IT resource management, enabling teams to concentrate on strategic projects instead of daily upkeep.
Cloud security issues
There are multiple security issues in cloud computing, and there are hurdles to overcome to secure data and still be able to maintain operational reliability. In this article, we explore the main security concerns in cloud computing and the extent to which they could possibly harm businesses.
Data loss
Data leakage has been a serious issue in cloud computing. Well, that is true, but only if our sensitive data is being taken care of by someone else whom we cannot trust absolutely, and just the opposite.
Therefore, if cloud service security is going to be baked by a hacker, then hackers can surely get a hold of our sensitive data or personal files.
Insecure APIs
APIs are the easiest way to talk about the Cloud and need protection. Moreover, as third-party access public clouds, they too can be vulnerabilities to a cloud.
To secure these APIs, implementing SSL certificates is crucial, as they encrypt data in transit, making it harder for hackers to intercept sensitive information. Without this layer of security, attackers can exploit weaknesses in the API, leading to unauthorized access or data loss.
Account hijacking
The most serious and pressing security threat out of myriads of cloud computing is account hijacking. Once a hacker compromises or hijacks the Account of a User or an Organization, he can access all unauthorized accounts and other activities.
Change of service provider
Change of service provider is also an important Security issue in Cloud Computing. Many organizations will face different problems like data shifting and different charges for each vendor while shifting from one vendor to another.
Skill gap
The biggest problem with IT Companies that do not have skilled Employees is the need to shift to another service provider while working, another feature required, how to use a feature, and so on. Therefore, it requires an extremely skilled person to work in cloud computing.
Insider threat
On the face of it, this would come out unlikely, but in reality, cloud security threats are those insiders that pose a serious threat to the organizations that avail cloud-based services.
These persons with authorized access to the most needed company resources may indulge in some forms of misconduct, either intentional or unintentional, which will lead to the misuse of their sensitive data. Sensitive data will include client accounts and all critical financial information.
The important fact to be considered is that the threats from within in cloud security are likely to come through either malicious intent or unintended and just plain negligence. Most such threats can mature into serious violations of security if they develop further and can thereby put sensitive data at risk.

To fight effectively such insider threats while maintaining, at the same time, the confidentiality of data being protected and stored in the cloud, access control must be proper, along with tight and strict access controls.
Moreover, full training courses including minute details about security should be provided to every member of the staff. In this regard also, monitoring should be done periodically. It is these aspects that have been the main reasons for protection against internal threats that may go about happening.
Malware injection
The most potent cloud security threats are malware injections. Evil code is concealed in the guise of legitimate code in cloud services. The attacks compromise data integrity because malignant options allow attackers to eavesdrop, modify information, and escape data without detection.
It has become essential to secure the data from eavesdropping in cloud computing and security is an essential aspect. This has become a serious threat to the security of the cloud environment; it should be counter-attacked through careful vigilance and robust security to avoid access to the cloud infrastructure.
Misconfiguration
Indeed, misconfigurations in cloud security settings have proved to be one of the leading and most common causes of data breaches in the present-day digital, and these incidents are mostly the offspring of less-than-perfect practices about managing an effective posture of security.
The user-friendly nature of cloud infrastructure, set up primarily to allow easy exchange and interaction of data, poses significant hurdles to directing access of the data to only a targeted entity or personnel.
Data storage issue
This distributed cloud infrastructure is spread all over the globe. Sometimes it tends to keep user data outside the jurisdictions of the legal frameworks of certain regions, raising the range of such data among local law enforcement and regulations. The user dreads its violation because the notion of a cloud makes it difficult to identify one server in the process of transferring data overseas.
Shared infrastructure security concerns
Multi-tenancy is the sharing of resources, storage, applications, and services from one platform with many at the cloud provider’s site. This tends to enable the provider to recoup high returns on investment but puts the customer at risk. Hence, an attacker can use multi-homing options to make a successful attack against the remaining co-tenants. This has a privacy problem.
Conclusion
The business world is changing rapidly, and the rise of cloud computing has created huge security and privacy concerns. In the cloud, there are many issues, such as multiple users sharing the same infrastructure and relying on third parties. These make data vulnerable.
Organizations must be proactive to protect data. They need strong encryption, controlled access, regular security audits, and a clear understanding of their shared responsibility with cloud providers.
#access control#Accessibility#Accounts#API#APIs#applications#Article#attackers#backup#backup and recovery#Business#certificates#change#Cloud#Cloud AI#cloud computing#cloud environment#cloud infrastructure#cloud providers#Cloud Security#cloud service#cloud services#clouds#code#Collaboration#Companies#compromise#computing#courses#data
0 notes
Text
सही Tally on Cloud प्रोवाइडर चुनने से पहले ये 7 सवाल ज़रूर पूछें!
आजकल कारोबार को बेहतर बनाने और कहीं से भी डेटा एक्सेस करने के लिए Tally on Cloud बहुत पॉपुलर हो गया है। लेकिन सही सर्विस का चुनाव करना थोड़ा मुश्किल हो सकता है। यह ब्लॉग उन मुश्किलों को आसान बनाने के लिए तैयार किया गया है। इसमें हम आपको 7 जरूरी सवाल बताएंगे, जो आपको Tally on Cloud सर्विस लेने से पहले पूछने चाहिए।

Tally on Cloud लेते समय सबसे पहले हमें सुरक्षा (Security) पर ध्यान देना चाहिए, खासकर वित्तीय डेटा (Financial Data)के लिए यह बहुत जरूरी है। इसलिए आपको यह पूछना चाहिए कि कंपनी आपके डेटा को सुरक्षित रखने के लिए क्या कदम उठाती है, जैसे डेटा एन्क्रिप्शन (Encryption) और मल्टी-फैक्टर ऑथेंटिकेशन (MFA)। इसके अलावा एक और महत्वपूर्ण चीज है सर्विस की विश्वसनीयता (Reliability)। यह सुनिश्चित करें कि कंपनी आपको हमेशा सर्विस प्रदान कर सके। अगर आपका व्यवसाय अलग-अलग टाइम ज़ोन में चलता है, तो यह और भी जरूरी हो जाता है।
इसके अलावा, कस्टमर सपोर्ट (Customer Support), डेटा बैकअप और रिकवरी (Data Backup and Recovery), छिपे हुए शुल्क (Hidden Charges), और कस्टमाइजेशन (Customization) के बारे में भी जरूर पूछें। हर बिजनेस की जरूरतें अलग होती हैं, इसलिए यह बेहतर होगा कि सर्विस को अपनी जरूरत के मुताबिक कस्टमाइज़ किया जा सके।
Antraweb Technologies एक ऐसी कंपनी है जो मजबूत और सुरक्षित Tally on Cloud सर्विस प्रदान करती है। यह कंपनी 24/7 सपोर्ट, बेहतरीन सुरक्षा, और कस्टमाइजेशन के विकल्प भी देती है। और सबसे अच्छी बात यह है कि यह सब कुछ किफायती दामों में उपलब्ध है।
अगर आप और ज्यादा जानना चाहते हैं, तो हमारे ब्लॉग पेज पर जाएं:
Blog Page: https://www.antraweb.com/blog/tally-on-cloud-hindi
हमारी वेबसाइट: https://www.antraweb.com/
#Tally on Cloud#Tally on AntraCloud#Tally on Cloud provider#AntraCloud#Tally Cloud solution#Tally Data security#Tally security#Tally backup#Tally cloud computing#Tally support#Tally customization#Tally software#Tally cloud solution#Tally Data Encryption#Antraweb Tally cloud
0 notes
Text
Learn effective Salesforce backup strategies to protect your business data and ensure seamless recovery in case of data loss.
#Salesforce backup#data recovery guide#Salesforce strategies#secure business data#Salesforce data protection
0 notes
Text
#data migration#data management#big data#data protection#file synchronization software#cloud solutions#linux#data orchestration#Government Data Management#file replication#Linux file transfer#secure data backup#cloud computing#cloud software
0 notes
Video
youtube
🌟 Protect Your Data & Earn Income with GotBackUp! 💼💰
Looking for a way to safeguard your digital files while creating a steady income? GotBackUp offers secure cloud storage and a powerful income opportunity!
Why GotBackUp? ✔ Protect your important files ✔ Build residual income with referrals ✔ Flexible, work-from-anywhere opportunity
💡 Perfect for network marketers, remote workers, and entrepreneurs!
🚀 Click below to start your journey today: 👉 bit.ly/3XNMpzO
#GotBackUp #PassiveIncome #DataSecurity #NetworkMarketing #WorkFromAnywhere #FinancialFreedom #ResidualIncome #BackupSolutions #DigitalProtection #EarnOnline
(via 🌟 Ready to Start Earning with GotBackUp? Here’s How! 💰)
#gotbackup#passive income#data security#network marketing#work from anywhere#financial freedom#residual income#backup solutions#digital protection#earn online
0 notes
Text
Hospitals IT Support
Century Solutions Group offers comprehensive Healthcare IT support and Medical IT services in Atlanta, GA tailored for medical practices to mitigate risks associated with migrating to Electronic Health Records (EHR) and intricate coding.
Contact us: https://centurygroup.net/industries/healthcare-medical-it-support/
#HealthcareIT #MedicalIT #AtlantaHospitals #AtlantaClinicsIT #HospitalIT #CenturyGroupIT #PatientCareITSupport #DigitalTransformation

#healthcare it services#medical it support#Hospitals IT support#Clinics IT Support#managed it services#cybersecurity#data backup#Secured Networking
1 note
·
View note
Text
How to create Synology Snapshot Replication
Snapshot Replication delivers an expert solution for data backup and recovery, offering near-instant data protection with flexible scheduling. This package safeguards your business data in shared folders and virtual machines stored in LUNs, ensuring quick access and availability in the event of a disaster. In this article, we shall learn the steps on how to create Synology Snapshot Replication.…
#check Snapshot Replication Status#Create Replication Job#Data Protection and Recovery#Disaster Recovery#Enable Synology Retention Policy#Enable the replication schedule#Perform Snapshot Recovery#Security and Compliance#Set Record Access time to Never#storage#Storage management#Synology#Synology NAS#Synology NAS backup
0 notes
Text
Folder Lock
If you have folders and files that you want to keep private, consider using Folder Lock. Unlike My Lockbox, it isn’t a free app, but it offers excellent configuration options and numerous methods to protect important and private documents from prying eyes. Folder Lock is a complete solution for keeping your personal files encrypted and locked, while automatically and in real-time backing up…
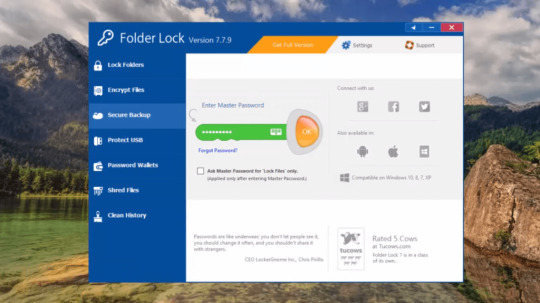
View On WordPress
#Data Encryption#Digital Wallets#Encryption Software#File Locking#File Management#File Security#File Shredding#password protection#Portable Security#privacy protection#Secure Backup#Windows Security
0 notes
Text
Global Cyber Resilience Report 2024: Overconfidence and Gaps in Cybersecurity Revealed
New Post has been published on https://thedigitalinsider.com/global-cyber-resilience-report-2024-overconfidence-and-gaps-in-cybersecurity-revealed/
Global Cyber Resilience Report 2024: Overconfidence and Gaps in Cybersecurity Revealed
The Global Cyber Resilience Report 2024 presents an in-depth analysis of the current state of cyber resilience across various industries worldwide. Based on a survey conducted by Cohesity and Censuswide, involving 3,139 IT and Security Operations (SecOps) decision-makers from eight countries, this report sheds light on the significant gaps between perceived and actual cyber resilience capabilities.
Survey Demographics and Scope
The survey, conducted in June 2024, covered both public and private organizations across several countries:
United States: ~500 respondents
United Kingdom: ~500 respondents
Australia: ~500 respondents
France: ~400 respondents
Germany: ~400 respondents
Japan: ~300 respondents
Singapore: ~300 respondents
Malaysia: ~200 respondents
Participants were evenly split between IT and SecOps professionals, providing a comprehensive overview of the current cyber resilience landscape.
Key Findings
1. Overestimation of Cyber Resilience
A striking revelation from the survey is the overestimation of cyber resilience capabilities among organizations. Only 2% of respondents indicated that they could recover their data and restore business processes within 24 hours of a cyberattack. This starkly contrasts with the confidence expressed by nearly 4 in 5 (78%) respondents in their organization’s cyber resilience strategy.
2. Ransom Payments: A Growing Concern
The willingness to pay ransoms has become alarmingly common. Approximately 75% of respondents indicated their organization would pay over $1 million to recover data and restore business operations, with 22% willing to pay over $3 million. In the past year, 69% of respondents admitted to paying a ransom, despite 77% having policies against such payments.
Slow Recovery Times
Recovery times reported by organizations reveal significant vulnerabilities:
Only 2% could recover within 24 hours.
18% could recover within 1-3 days.
32% required 4-6 days.
31% needed 1-2 weeks.
16% would need 3+ weeks.
These recovery times fall short of the targeted optimum recovery time objectives (RTO), with 98% aiming for recovery within one day and 45% targeting within two hours.
4. Insufficient Data Privacy Compliance
Just over 2 in 5 (42%) respondents claimed their organization could identify sensitive data and comply with applicable data privacy laws. This indicates a significant gap in necessary IT and security capabilities.
5. Zero Trust Security Deficiencies
Despite the availability of effective security measures, many organizations have not adopted them:
48% have not deployed multifactor authentication (MFA).
Only 52% have implemented MFA.
Quorum controls or administrative rules requiring multiple approvals are used by 49%.
Role-based access controls (RBAC) are deployed by 46%.
These deficiencies leave organizations vulnerable to both external and internal threats.
The Escalating Threat Landscape
The survey underscores the increasing threat of cyberattacks:
In 2022, 74% of respondents felt the threat of ransomware was rising. By 2023, this figure rose to 93%, and in 2024, it reached 96%.
Two-thirds (67%) of respondents reported being victims of ransomware in the past six months.
Industries Most Affected
The report identifies seven industries that have been hardest hit by cyberattacks:
IT & Technology (40%)
Banking & Wealth Management (27%)
Financial Services (27%)
Telecommunications & Media (24%)
Government & Public Services (23%)
Utilities (21%)
Manufacturing (21%)
Areas of Critical Concern
1. Confidence-Capability Paradox
The disparity between confidence in cyber resilience strategies and the actual capability to execute these strategies effectively is evident. While many organizations have a cyber resilience plan, their ability to recover quickly from attacks lags significantly behind their goals.
2. Rampant Ransom Payments
The prevalence of ransom payments, often in contradiction to organizational policies, highlights a reactive rather than proactive approach to cyber resilience. The financial impact of paying ransoms extends beyond the immediate cost, affecting downtime, lost opportunities, and reputational damage.
3. Zero Trust Security Deficiencies
The failure to implement robust data access controls like MFA and RBAC poses a significant risk to organizations. Effective security measures are essential for protecting critical data and ensuring business continuity.
Recommendations for Improvement
To address these critical issues, the report suggests several actionable strategies:
Engage in rigorous testing, drills, and simulations to ensure the effectiveness of backup and recovery processes.
Sign up for ransomware resilience workshops to enhance cyber incident response capabilities.
Automate testing of backup data to verify integrity and recoverability without manual intervention.
Maintain detailed documentation and recovery playbooks to ensure all stakeholders understand their roles during an incident.
Conclusion
The Global Cyber Resilience Report 2024 that was commissioned by Cohesity highlights the urgent need for organizations to bridge the gap between their perceived and actual cyber resilience capabilities. By identifying and addressing these vulnerabilities, organizations can enhance their ability to recover from cyberattacks and protect critical data, ensuring a more secure and resilient future.
The comprehensive data and insights from this report serve as a crucial resource for IT and SecOp professionals aiming to strengthen their cyber resilience strategies and safeguard their organizations against the evolving threat landscape.
#2022#2023#2024#amp#Analysis#approach#authentication#backup#backup and recovery#banking#bridge#Business#business continuity#comprehensive#Critical Issues#cyber#cyber security#cyberattack#Cyberattacks#cybersecurity#data#data privacy#decision-makers#documentation#financial#financial services#Future#gap#Global#Government
0 notes