#privacyshield
Explore tagged Tumblr posts
Text
𝐅𝐚𝐬𝐭, 𝐑𝐞𝐥𝐢𝐚𝐛𝐥𝐞, 𝐒𝐞𝐜𝐮𝐫𝐞: 𝐂𝐡𝐨𝐨𝐬𝐞 𝐈𝐒𝐏 𝐏𝐫𝐨𝐱𝐲 𝐟𝐨𝐫 𝐚 𝐒𝐮𝐩𝐞𝐫𝐢𝐨𝐫 𝐈𝐧𝐭𝐞𝐫𝐧𝐞𝐭 𝐂𝐨𝐧𝐧𝐞𝐜𝐭𝐢𝐨𝐧

Step into the digital landscape, where the synergy of connectivity and security molds our online interactions. This blog post takes an immersive dive into the realm of ISP proxy servers, revealing how they can elevate your online presence. At VPS Proxies, we serve as your premier source for cutting-edge proxy, RDP, and VPS solutions, guiding you through the nuances of ISP proxy servers to equip you with valuable insights and expertise.
𝐖𝐡𝐚𝐭 𝐢𝐬 𝐚𝐧 𝐈𝐒𝐏 𝐩𝐫𝐨𝐱𝐲 𝐬𝐞𝐫𝐯𝐞𝐫❓
In the intricate web of online connectivity, an ISP Proxy Server, or “Internet Service Provider Proxy Server,” stands as a bridge between a user’s device and the vast digital landscape. This unique server serves as a facilitator, orchestrating seamless communication between the user and various online resources. Its pivotal role extends to fortifying privacy, bolstering security measures, and ensuring unrestricted access to a spectrum of digital content.
𝐖𝐡𝐲 𝐃𝐨 𝐈 𝐍𝐞𝐞𝐝 𝐈𝐒𝐏 𝐏𝐫𝐨𝐱𝐢𝐞𝐬❓
Unlocking a multitude of applications, Internet Service Provider (ISP) proxies cater to diverse user needs. Whether it’s safeguarding anonymity, overcoming geo-restrictions, or enhancing security, these proxies seamlessly adapt to the unique requirements of individuals and businesses navigating the digital landscape.
🌐 𝐀𝐧𝐨𝐧𝐲𝐦𝐢𝐭𝐲 𝐚𝐧𝐝 𝐏𝐫𝐢𝐯𝐚𝐜𝐲 𝐒𝐡𝐢𝐞𝐥𝐝 : Embarking on the digital journey, ISP proxies serve as guardians of user anonymity by cloaking IP addresses. This protective veil not only safeguards personal privacy but also thwarts websites from tracking and monitoring user activities in the vast expanse of the internet.
🌍 𝐆𝐞𝐨-𝐫𝐞𝐬𝐭𝐫𝐢𝐜𝐭𝐢𝐨𝐧 𝐋𝐢𝐛𝐞𝐫𝐚𝐭𝐢𝐨𝐧 : Empowering users to transcend geographical boundaries, ISP proxies become the key to unlocking restricted content. By adopting an ISP proxy located in a different region, users effortlessly access content otherwise confined by geo-restrictions, whether it be streaming services, websites, or online platforms.
💻🔄 𝐖𝐞𝐛 𝐒𝐜𝐫𝐚𝐩𝐢𝐧𝐠 𝐚𝐧𝐝 𝐃𝐚𝐭𝐚 𝐌𝐢𝐧𝐢𝐧𝐠 𝐃𝐲𝐧𝐚𝐦𝐨 : In the realm of business and research, ISP proxies emerge as indispensable tools for web scraping and data mining endeavors. A strategic dance of regularly switching IP addresses ensures uninterrupted access to valuable online information, sidestepping potential obstacles like rate-limiting or anti-scraping measures.
👁️ 𝐀𝐝 𝐕𝐞𝐫𝐢𝐟𝐢𝐜𝐚𝐭𝐢𝐨𝐧 𝐒𝐞𝐧𝐭𝐢𝐧𝐞�� : For advertisers and marketers, ISP proxies act as vigilant sentinels ensuring the accurate placement and display of online ads. This instrumental tool aids in verifying that ads reach their intended audience and appear in the right locations across the digital landscape.
🔍📈 𝐒𝐄𝐎 𝐌𝐨𝐧𝐢𝐭𝐨𝐫𝐢𝐧𝐠 𝐌𝐚𝐞𝐬𝐭𝐫𝐨 : In the world of SEO, ISP proxies transform into monitoring maestros, allowing professionals to assess search engine rankings from diverse locations. This strategic perspective enables SEO experts to optimize website visibility by understanding and addressing regional variations in ranking.
🔄⚖️ 𝐋𝐨𝐚𝐝 𝐁𝐚𝐥𝐚𝐧𝐜𝐢𝐧𝐠 𝐕𝐢𝐫𝐭𝐮𝐨𝐬𝐨 : Enterprises strategically deploy ISP proxies for load balancing, directing internet traffic through multiple proxies to optimize resource usage. This virtuoso maneuver ensures a stable and reliable connection, enhancing the overall efficiency of online operations.
🛡️🔍 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐓𝐞𝐬𝐭𝐢𝐧𝐠 𝐒𝐨𝐫𝐜𝐞𝐫𝐞𝐫 : For security professionals and ethical hackers, ISP proxies become sorcerers, enabling the simulation of attacks and security testing from diverse IP addresses. This dynamic approach enhances the robustness of network, application, and website security.
🏠🔗 𝐑𝐞𝐬𝐢𝐝𝐞𝐧𝐭𝐢𝐚𝐥 𝐈𝐏 𝐂𝐡𝐚𝐫𝐦 : Certain ISP proxies offer the charm of residential IP addresses, mimicking real user interactions. This subtle yet valuable distinction proves crucial in online activities where websites treat traffic differently based on whether it originates from residential or data center IPs.
𝐇𝐨𝐰 𝐝𝐨 𝐈 𝐮𝐬𝐞 𝐚𝐧 𝐈𝐒𝐏 𝐩𝐫𝐨𝐱𝐲❓
Leveraging the prowess of an ISP (Internet Service Provider) proxy involves fine-tuning your device or network settings. This configuration not only empowers efficient internet traffic routing but also guarantees a smooth journey through the ISP-supplied proxy server, with step-by-step instructions tailored to your device or operating system:
🖥️🔧 𝐖𝐢𝐧𝐝𝐨𝐰𝐬 𝐂𝐨𝐧𝐟𝐢𝐠𝐮𝐫𝐚𝐭𝐢𝐨𝐧 𝐆𝐞𝐚𝐫 :
To harness the power of an ISP (Internet Service Provider) proxy on Windows, navigate through the digital landscape with these essential steps:
1. 𝐎𝐩𝐞𝐧 𝐈𝐧𝐭𝐞𝐫𝐧𝐞𝐭 𝐒𝐞𝐭𝐭𝐢𝐧𝐠𝐬: Head to the Control Panel. 2. 𝐅𝐢𝐧𝐝 ❞𝐈𝐧𝐭𝐞𝐫𝐧𝐞𝐭 𝐎𝐩𝐭𝐢𝐨𝐧𝐬❞: Uncover and open this crucial menu. 3. 𝐀𝐜𝐜𝐞𝐬𝐬 𝐭𝐡𝐞 𝐂𝐨𝐧𝐧𝐞𝐜𝐭𝐢𝐨𝐧𝐬 𝐓𝐚𝐛: Delve into the “Connections” tab. 4. 𝐂𝐨𝐧𝐟𝐢𝐠𝐮𝐫𝐞 𝐋𝐀𝐍 𝐬𝐞𝐭𝐭𝐢𝐧𝐠𝐬: Click on “LAN settings,” enabling the proxy. 5. 𝐄𝐧𝐭𝐞𝐫 𝐈𝐒𝐏 𝐃𝐞𝐭𝐚𝐢𝐥𝐬: Check the box for “Use a proxy server for your LAN” and input the ISP’s IP address and port number. 6. 𝐒𝐚𝐯𝐞 𝐒𝐞𝐭𝐭𝐢𝐧𝐠𝐬: Seal the deal by clicking “OK” to secure these configuration changes.
🍏🌐 𝐌𝐚𝐜 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐍𝐚𝐯𝐢𝐠𝐚𝐭𝐨𝐫 :
For Mac users embarking on the ISP proxy journey, chart your course with these intuitive steps:
1. 𝐎𝐩𝐞𝐧 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐏𝐫𝐞𝐟𝐞𝐫𝐞𝐧𝐜𝐞𝐬: Navigate to the Apple menu and choose “System Preferences.” 2. 𝐀𝐜𝐜𝐞𝐬𝐬 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐒𝐞𝐭𝐭𝐢𝐧𝐠𝐬: Click on “Network” to open up connectivity options. 3. 𝐒𝐞𝐥𝐞𝐜𝐭 𝐲𝐨𝐮𝐫 𝐜𝐨𝐧𝐧𝐞𝐜𝐭𝐢𝐨𝐧: Choose the active network connection, be it Wi-Fi or Ethernet. 4. 𝐂𝐨𝐧𝐟𝐢𝐠𝐮𝐫𝐞 𝐏𝐫𝐨𝐱𝐲 𝐒𝐞𝐭𝐭𝐢𝐧𝐠𝐬: Click “Advanced” and navigate to the “Proxies” tab. 5. 𝐂𝐡𝐞𝐜𝐤 𝐭𝐡𝐞 𝐏𝐫𝐨𝐱𝐲 𝐁𝐨𝐱𝐞𝐬: Activate “Web Proxy (HTTP)” or “Secure Web Proxy (HTTPS)” as needed. 6. 𝐈𝐧𝐩𝐮𝐭 𝐈𝐒𝐏 𝐃𝐞𝐭𝐚𝐢𝐥𝐬: Enter the provided IP address and port number from your ISP. 7. 𝐒𝐚𝐯𝐞 𝐂𝐡𝐚𝐧𝐠𝐞𝐬: Click “OK” and then “Apply” to anchor these proxy settings securely.
⚓🌐 𝐁𝐫𝐨𝐰𝐬𝐞𝐫-𝐬𝐩𝐞𝐜𝐢𝐟𝐢𝐜 𝐒𝐚𝐢𝐥𝐢𝐧𝐠 :
Navigate the vast ocean of the internet with ISP proxies using these browser-specific settings:
🌐🔍 𝐆𝐨𝐨𝐠𝐥𝐞 𝐂𝐡𝐫𝐨𝐦𝐞 𝐄𝐱𝐩𝐥𝐨𝐫𝐚𝐭𝐢𝐨𝐧 :
1. Open Chrome and access “Settings.” 2. Scroll and click “Advanced.” 3. Under “System,” click “Open your computer’s proxy settings.” 4. In the Internet Properties window, click the “Connections” tab and navigate to “LAN settings.” 5. Configure proxy settings as guided by your ISP.
𝐇𝐨𝐰 𝐝𝐨 𝐈 𝐠𝐞𝐭 𝐭𝐡𝐞 𝐛𝐞𝐬𝐭 𝐈𝐒𝐏 𝐩𝐫𝐨𝐱𝐲 𝐢𝐧 𝐭𝐡𝐞 𝐔𝐒𝐀❓
Embarking on the quest for the best ISP (Internet Service Provider) proxy in the USA requires a strategic approach tailored to your unique needs. Here’s a roadmap to guide you through the process:
🧐 𝐑𝐞𝐬𝐞𝐚𝐫𝐜𝐡 𝐑𝐞𝐩𝐮𝐭𝐚𝐛𝐥𝐞 𝐏𝐫𝐨𝐯𝐢𝐝𝐞𝐫𝐬 : When seeking a trustworthy proxy provider, it’s crucial to explore well-established options with a proven track record. Take the time to peruse reviews and testimonials to assess the reliability and performance of their services, where VPS Proxies Inc emerges as the premier and top-level choice in the current landscape.
📋 𝐃𝐞𝐟𝐢𝐧𝐞 𝐘𝐨𝐮𝐫 𝐑𝐞𝐪𝐮𝐢𝐫𝐞𝐦𝐞𝐧𝐭𝐬 : Clearly outline your needs, considering factors like the number of required IP addresses, preferred geographical locations, anonymity levels, and specific features such as rotating IPs or session control.
🌐🔒 𝐕𝐞𝐫𝐢𝐟𝐲 𝐈𝐏 𝐐𝐮𝐚𝐥𝐢𝐭𝐲 : Ensure that the provider offers top-notch residential IP addresses, crucial for avoiding detection by websites that blacklist data center IPs. Quality is paramount for a seamless proxy experience.
🗺️ 𝐂𝐡𝐞𝐜𝐤 𝐋𝐨𝐜𝐚𝐭𝐢𝐨𝐧 𝐂𝐨𝐯𝐞𝐫𝐚𝐠𝐞 : Confirm that the provider covers the specific USA locations you require. A broader network gives you flexibility in selecting proxy locations that align with your objectives.
📈 𝐀𝐬𝐬𝐞𝐬𝐬 𝐒𝐜𝐚𝐥𝐚𝐛𝐢𝐥𝐢𝐭𝐲 : Choose a provider capable of scaling services to accommodate your growing needs. Scalability ensures sustained performance even as your usage expands over time.
⚡🚀 𝐏𝐫𝐢𝐨𝐫𝐢𝐭𝐢𝐳𝐞 𝐑𝐞𝐥𝐢𝐚𝐛𝐢𝐥𝐢𝐭𝐲 𝐚𝐧𝐝 𝐒𝐩𝐞𝐞𝐝 : Opt for a provider offering low-latency and high-speed connections. This is particularly vital for applications like web scraping, where quick response times are imperative for success.
🔄💰 𝐄𝐱𝐩𝐥𝐨𝐫𝐞 𝐓𝐫𝐢𝐚𝐥 𝐏𝐞𝐫𝐢𝐨𝐝𝐬 𝐚𝐧𝐝 𝐑𝐞𝐟𝐮𝐧𝐝 𝐏𝐨𝐥𝐢𝐜𝐢𝐞𝐬 : Take advantage of trial periods or money-back guarantees to test the proxies firsthand. This allows you to assess their suitability and performance in alignment with your requirements.
📜⚖️ 𝐄𝐧𝐬𝐮𝐫𝐞 𝐋𝐞𝐠𝐚𝐥 𝐂𝐨𝐦𝐩𝐥𝐢𝐚𝐧𝐜𝐞 : Prioritize providers that adhere to relevant laws and regulations. Unethical or illegal proxy usage can lead to severe consequences, so ensure your chosen provider operates within legal boundaries.
🛠️🤝 𝐄𝐯𝐚𝐥𝐮𝐚𝐭𝐞 𝐂𝐮𝐬𝐭𝐨𝐦𝐞𝐫 𝐒𝐮𝐩𝐩𝐨𝐫𝐭 : A responsive and knowledgeable customer support team is invaluable. Check if the provider offers support through various channels and has a reputation for swiftly addressing issues.
💸 𝐂𝐨𝐧𝐬𝐢𝐝𝐞𝐫 𝐂𝐨𝐬𝐭 𝐅𝐚𝐜𝐭𝐨𝐫𝐬 : Compare pricing plans, keeping an eye on the balance between features and performance. Be cautious of excessively low-cost options, as they may compromise on the quality of service.
🔄🔄 𝐀𝐬𝐬𝐞𝐬𝐬 𝐏𝐫𝐨𝐱𝐲 𝐑𝐨𝐭𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐒𝐞𝐬𝐬𝐢𝐨𝐧 𝐂𝐨𝐧𝐭𝐫𝐨𝐥 𝐅𝐞𝐚𝐭𝐮𝐫𝐞𝐬 : Depending on your use case, evaluate whether the provider offers features like IP rotation or session control. These functionalities enhance your ability to avoid detection and prevent IP bans.
𝐖𝐡𝐚𝐭 𝐢𝐬 𝐭𝐡𝐞 𝐝𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐜𝐞 𝐛𝐞𝐭𝐰𝐞𝐞𝐧 𝐚 𝐝𝐚𝐭𝐚 𝐜𝐞𝐧𝐭𝐞𝐫 𝐚𝐧𝐝 𝐚𝐧 𝐈𝐒𝐏 𝐩𝐫𝐨𝐱𝐲❓
In the intricate web of internet connectivity, data centers and ISP proxies play distinct yet complementary roles. Data centers take center stage in the digital orchestra, orchestrating the storage, processing, and management of colossal data volumes. On the other hand, ISP proxies, denoting Internet Service Provider proxies, don the mantle of intermediaries, fostering a secure bridge between users and the expansive realm of the Internet.
In the foundational landscape of the internet, data centers stand tall as the architectural pillars, hosting websites and applications to ensure their seamless availability. Meanwhile, ISP proxies weave a dynamic tapestry of online communication, efficiently directing internet traffic through their servers to enhance both privacy and security. To distill the essence, data centers command the domain of data storage and processing, while ISP proxies emerge as adept navigators, optimizing internet connections to elevate the overall user experience.
𝐅𝐢𝐧𝐚𝐥 𝐭𝐡𝐨𝐮𝐠𝐡𝐭:
The incorporation of VPS Proxies Inc.’s ISP proxy server signifies a revolutionary change in our online interactions and navigation. In essence, integrating this cutting-edge technology into your online arsenal becomes a strategic decision, promising a multitude of advantages. Above all, VPS Proxies Inc.’s ISP proxy server stands out for its capacity to elevate privacy, bolster security measures, and optimize overall online connectivity.
ℂ𝕠𝕟𝕥𝕒𝕔𝕥 𝕦𝕤:-: 👉🏻 Web: www.vpsproxies.com 👉🏻 Telegram: https://t.me/vpsproxiesinc 👉 Gmail: [email protected] 👉🏻 Skype: live:.cid.79b1850cbc237b2a
#ProxyPower#InternetFreedom#ProxyPerfection#SecureSurfing#ISPProxyMagic#BrowseSmart#UnlockTheWeb#PrivacyShield#SpeedyProxy#ProxyAdvantage#OnlinePrivacyGuard#BrowseAnonymous#WebWithoutLimits#ProxyInnovations#ProxyPerformance#DigitalPrivacy#FastAndSecure#ProxySolutions#BeyondBoundaries#VirtualPrivateSurfing
0 notes
Text
Come implementare Privacy Shield per non bloccare domini leciti

Perché il Piracy Shield non funziona e come sarebbe dovuto essere implementato. Nell’era digitale, la gestione della proprietà intellettuale e la lotta contro la pirateria online rappresentano sfide cruciali per i regolatori, le industrie creative e i fornitori di servizi internet. Il “Piracy Shield”, un’iniziativa dell’Autorità per le Garanzie nelle Comunicazioni (AGCOM), rappresenta un tentativo significativo di affrontare il problema della pirateria digitale in Italia. Questo strumento è stato ideato per identificare e bloccare l’accesso ai siti web che violano i diritti di proprietà intellettuale, sfruttando tecnologie di filtraggio degli “FQDN e degli indirizzi IP” (citando testualmente AGCOM). Nonostante le sue nobili intenzioni, il Piracy Shield ha suscitato non poche controversie e dibattiti riguardo la sua efficacia e le implicazioni per la libertà di espressione e il diritto alla privacy. In questo articolo tecnico-scientifico, si intende esplorare e discutere le ragioni per cui il Privacy Shield non ha raggiunto pienamente i suoi obiettivi, mettendo in luce le difficoltà tecniche, legali e etiche incontrate.

Sarà inoltre illustrato come, attraverso un approccio innovativo basato sulla configurazione di record CNAME, sia possibile distinguere tra servizi legittimi e illeciti associati allo stesso indirizzo IPv4. Questa dimostrazione pratica non solo evidenzierà le potenzialità di tali tecniche, ma anche come esse potrebbero essere integrate efficacemente in un framework rinnovato per la lotta alla pirateria, suggerendo modifiche e migliorie al sistema attuale del Piracy Shield. Le Content Delivery Network Le Content Delivery Networks (CDN) sono infrastrutture distribuite di server progettate per ottimizzare la consegna di contenuti web agli utenti finali. Le CDN migliorano la velocità e l’affidabilità di accesso ai dati riducendo la distanza fisica tra il server e l’utente, distribuendo il contenuto su diversi server posizionati in varie località geografiche. Funzionamento delle CDN Quando un utente accede a un sito web che utilizza una CDN, la richiesta di dati non viene inviata direttamente al server principale del sito, ma viene reindirizzata al server della CDN più vicino all’utente. Questo server “edge” contiene copie dei contenuti del sito, come file HTML, immagini, video e altri tipi di dati. Grazie a questa architettura, il tempo di caricamento delle pagine si riduce notevolmente, migliorando l’esperienza dell’utente e riducendo il carico sui server centrali. Mascheramento dell��IP reale Un effetto importante dell’uso delle CDN è il mascheramento dell’indirizzo IP pubblico reale del server di origine dei contenuti. Quando un servizio online adotta una CDN, gli indirizzi IP visibili al pubblico sono quelli dei server della rete CDN. Questo significa che l’IP percepito come fonte del servizio è in realtà quello della CDN, non del server originale. Questo ha implicazioni per la sicurezza, la privacy e la gestione del traffico, ma può anche complicare alcune operazioni di controllo e filtraggio del contenuto. Implicazioni per il filtraggio di contenuti Se un’autorità come AGCOM implementa misure per bloccare l’accesso a contenuti ritenuti illegali (come quelli piratati) mediante il filtraggio degli indirizzi IP attraverso strumenti come il Piracy Shield, si potrebbero verificare problemi significativi. Poiché un singolo indirizzo IP di una CDN può essere utilizzato per trasmettere i contenuti di numerosi servizi diversi, il blocco di quell’IP potrebbe avere l’effetto collaterale di interrompere l’accesso a servizi legittimi e non solo a quelli illegali. Questo scenario potrebbe portare a interruzioni di servizio per utenti che non sono coinvolti nella fruizione di contenuti piratati. Facciamo chiarezza con un esempio pratico Per comprendere meglio come funziona la navigazione su internet e l’interazione con una Content Delivery Network (CDN), prendiamo come esempio il processo di collegamento a un sito web, come “www.libero.it”. Questo esempio ci permetterà di osservare come, durante la navigazione, il nome di dominio inizialmente richiesto possa in realtà essere servito da un dominio completamente diverso, come “d31d9gezsyt1z8.cloudfront.net”, che appartiene a una CDN. DNS Query Il processo inizia quando l’utente digita “www.libero.it” nel browser. Il browser deve risolvere questo nome di dominio in un indirizzo IP per poter stabilire una connessione. Questo avviene tramite una richiesta DNS (Domain Name System). Il browser consulta i server DNS configurati (tipicamente forniti dal provider di servizi internet o specificati manualmente dall’utente) per ottenere l’indirizzo IP associato al nome di dominio. (Si vede evidenziata la richiesta) Ricezione della risposta DNS I server DNS eseguono la ricerca e, una volta trovato l’indirizzo IP, lo restituiscono al browser. Se il dominio è ospitato su una CDN, l’IP restituito sarà quello di uno dei server edge della CDN più vicino all’utente, non l’IP del server originale di “libero.it”. (Si vede evidenziata la risposta Apertura della connessione (Handshake) Con l’indirizzo IP in mano, il browser inizia un handshake TCP con il server al fine di stabilire una connessione affidabile. Questo include la sincronizzazione dei numeri di sequenza per garantire che i pacchetti di dati vengano inviati e ricevuti in ordine. Durante l’handhsake il client invia un segmento SYN , il server risponde con un SYN + ACK , il client termina l’handshake con un ACK. (Si vede in figura nella riga evidenziata l’inizio dell’handshake verso la CDN di libero).
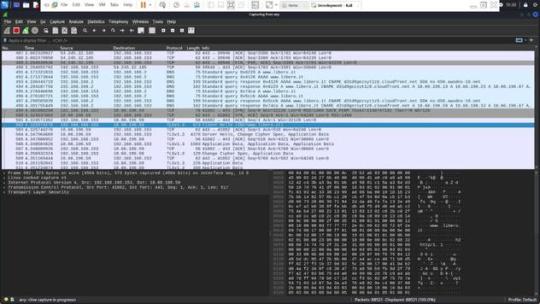
Negoziazione TLS (Transport Layer Security) Dopo aver stabilito una connessione TCP, il browser inizia una negoziazione TLS per assicurare che la comunicazione sia sicura e criptata. Questo processo inizia con l’invio del “ClientHello”, che include la versione di TLS supportata, i metodi di cifratura proposti, e altri dettagli necessari per la sicurezza.

Il server risponde con un “ServerHello”, che conferma i dettagli della crittografia che sarà utilizzata, seleziona un metodo di cifratura tra quelli proposti dal client e prosegue con l’invio dei certificati, la verifica della chiave, e la conferma finale di inizio della cifratu Comunicazione sicura Una volta completata la negoziazione TLS, tutte le trasmissioni successive tra il browser e il server sono completamente criptate. Il browser può ora richiedere le risorse web da “www.libero.it”, che in realtà potrebbero essere servite dal dominio della CDN, come “d31d9gezsyt1z8.cloudfront.net”. Questo esempio mostra come, nella pratica, un sito che l’utente intende visitare possa essere effettivamente distribuito attraverso una rete CDN, rendendo il nome del dominio CDN visibile nelle comunicazioni di rete, anche se l’utente potrebbe non essere immediatamente consapevole di tale fatto. Considerazioni Questa architettura farà in modo che www.libero.it avrà una serie di IP associati all’ASN di cloudfront che vengono usati per far funzionare la CDN. Questi IP saranno associati non solo a www.libero.it ma anche a molti altri FQDN (Altre web app) che usano la CDN. Ricordiamo che questi servizi vengono distinti fra loro grazie ai record CNAME che puntano a FQDN univoci come questo: d31d9gezsyt1z8.cloudfront.net.
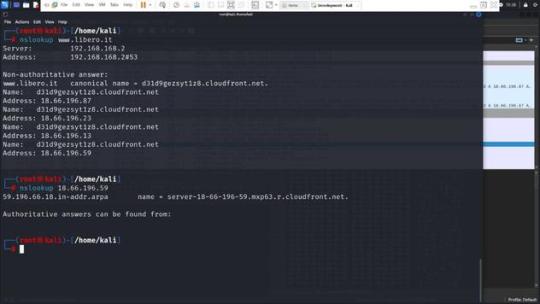
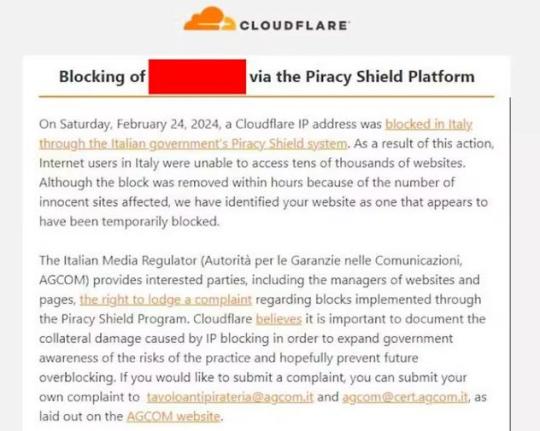
Dimostrazione del problema Con l’esempio precedente abbiamo quindi dimostrato che quando un servizio è integrato ad una CDN la corrispondenza servizio – IP non è più della cardinalità 1:1 , ma bensì N:1. Quindi se viene filtrato un indirizzo IP, N servizi vengono oscurati, pur non essendo tutti illegali. Lo abbiamo visto con l’esempio precedente in cui libero viene deliberatamente associato a diversi IP, condivisi con altri servizi della CDN cloudFront. Infatti una delle CDN che ha lamentato proprio questo problema è la nota Cloudflare che ha emesso un comunicato ad alcuni suoi clienti, esortandoli all’invio di una lettera di richiamo alla stessa AGCOM chiedendo di annullare l’ingiusto provvedimento.
Non si può quindi pensare di bloccare il traffico IP semplicemente filtrando un indirizzo IPv4/IPv6. Come si potrebbe procedere Per affrontare efficacemente le sfide poste dal filtraggio di contenuti attraverso indirizzi IP in un ambiente dove sono ampiamente utilizzate le Content Delivery Networks (CDN), è essenziale adottare metodi più sofisticati che prendano in considerazione le peculiarità tecniche delle CDN stesse. Una strategia più mirata e meno suscettibile di causare danni collaterali può essere implementata analizzando in dettaglio le proprietà di rete associate agli indirizzi IP, in particolare l’Autonomous System Number (ASN). Analisi dell’ASN Prima di procedere al blocco di un indirizzo IP sospettato di veicolare contenuti piratati, è cruciale determinare a quale sistema autonomo appartiene quel determinato IP. Se l’IP è associato all’ASN di una CDN nota, questo indica che potrebbe essere utilizzato per servire una moltitudine di clienti e servizi, molti dei quali legittimi. Il blocco diretto di tali IP potrebbe quindi interrompere l’accesso a servizi legittimi, causando interruzioni non necessarie e potenzialmente estese. Blocco basato su FQDN della CDN Invece di bloccare indiscriminatamente gli indirizzi IP, si dovrebbe valutare l’opzione di filtrare specifici Fully Qualified Domain Names (FQDN) direttamente legati a contenuti illeciti. Un metodo più mirato consiste nell’analizzare i record CNAME, che collegano un FQDN a un altro dominio, spesso usato per identificare contenuti specifici all’interno di una CDN. Il sistema attuale del Piracy Shield già applica il blocco agli FQDN e agli indirizzi IP, ma non estende questo trattamento ai FQDN univoci usati dalle CDN. Ad esempio, bloccando il dominio pubblico www.libero.it ed i suoi indirizzi IP, si impedisce anche l’accesso agli IP come 18.66.196.87, 18.66.196.23, 18.66.196.13 e 18.66.196.59. Tali indirizzi, associati a una CDN, vengono utilizzati anche da altri servizi che sarebbero ingiustamente bloccati. Soluzione proposta Quando viene rilevato che un servizio usa una CDN, la strategia corretta sarebbe quella di bloccare esclusivamente gli FQDN specifici alla CDN, come d31d9gezsyt1z8.cloudfront.net e www.libero.it, senza intervenire sugli indirizzi IP. In questo modo gli altri servizi che usano la CDN non saranno bloccati. Conclusioni Adottando queste pratiche migliorate, AGCOM e altre autorità simili potrebbero ottimizzare le loro strategie di enforcement senza suscitare controversie legate a interruzioni di servizio ingiustificate o a violazioni dei diritti alla privacy e alla libertà di espressione. Questo equilibrio tra l’efficacia del blocco e il rispetto per i diritti degli utenti è essenziale per mantenere la fiducia nel regolamento digitale e nella protezione della proprietà intellettuale nel contesto globale e interconnesso di oggi Read the full article
#AgCom#CDNcloudFront#contentdeliverynetwork#dnsquery#filtering#FQDN#indirizziIP#ipaddress#PrivacyShield
0 notes
Text

Trainiert MS ihre KI mit unseren Daten?
Wohin gehen unsere Daten?
AGBs lesen ist mühsam, entweder sie sind viele Seiten lang und man findet die wichtige Sätze nicht oder sie sind so kryptisch formuliert, dass man alles mögliche darunter verstehen kann. Die Mozilla Foundation, das ist die Stiftung, die den Firefox Browser und das Mailprogramm Thunderbird unterstützt, hat 9 ExpertInnen beauftragt, die AGBs von Microsoft daraufhin zu untersuchen, ob Microsoft die Daten seiner Nutzer zum Training von KI verwendet.
Die ExpertInnen konnten Mozilla keine klare Antwort geben. Nun hat Mozilla eine Webseite aufgemacht, wo man Microsoft direkt fragen kann. Die Annahme ist, dass Microsoft zu einer Antwort gedrängt wird, wenn genügend Menschen danach fragen. Mozilla sagt dort:
"Trainiert ihr eure KI mit unseren persönlichen Daten?
Wir haben 4 Jurist*innen, 3 Datenschutzexpert*innen und 2 Aktivist*innen beauftragt, den neuen Servicevertrag von Microsoft unter die Lupe zu nehmen. Keinem der Profis gelang es, dem Dokument zu entnehmen, ob Microsoft plant, Ihre persönlichen Daten – darunter Audio- und Videodaten, Chatprotokolle und Dateianhänge aus 130 Produkten wie Office, Skype, Teams und Xbox – zum Training seiner KI-Modelle zu nutzen.
Wenn 9 Datenschutzexpert*innen nicht verstehen, wie Microsoft Ihre Daten nutzen wird – wie sollen Normalverbraucher*innen da durchblicken? Wahrscheinlich gar nicht. Deshalb fordern wir Microsoft auf, Klartext zu reden, ob das Unternehmen persönliche Daten zu KI-Trainingszwecken einsetzt."
Auf der verlinkten Seite kann sich der Frage an Microsoft anschließen. Wir sind auf eine Antwort gespannt ...
Mehr dazu bei https://foundation.mozilla.org/de/campaigns/microsoft-ai/?utm_source=newtab&utm_campaign=23-MS-AI&utm_medium=firefox-desktop&utm_term=de&utm_content=banner_I2-C1 und alle unsere Artikel zu Microsoft und Datenverlusten https://www.aktion-freiheitstattangst.org/cgi-bin/searchart.pl?suche=microsoft+verlust&sel=meta
Kategorie[21]: Unsere Themen in der Presse Short-Link dieser Seite: a-fsa.de/d/3yA Link zu dieser Seite: https://www.aktion-freiheitstattangst.org/de/articles/8661-20240125-trainiert-ms-ihre-ki-mit-unseren-daten.html
#Anfrage#KI#BigBrother#Gefahren#Microsoft365#Teams#Skype#Lauschangriff#Überwachung#Videoüberwachung#Verbraucherdatenschutz#Datenschutz#Datensicherheit#Ergonomie#Datenpannen#Datenskandale#PrivacyShield#SafeHarbor#USA#Big5#Apps#Privatsphäre#Verluste
1 note
·
View note
Text
#balconynetting#balconysafety#balconyprivacy#balconyprotection#balconysecurity#balconyenhancement#outdoorliving#balconydesign#safetyfirst#privacyshield#netting for balconies#custom netting for balconies
0 notes
Text
Ciao ciao AirVPN, grazie Piracy Shield
Friday rant del mercoledì:#fridayrant #quellidelfascicolop #quellascemenzadellaseraio comprendo la esigenza di bloccare la pirateria dei contenuti legittimamente offerti dalle piattaforme che li hanno acquistati, ma talvolta la cura proposta è semplicemente aberrante.Ogni riferimento al nostro #PrivacyShield, creata dalla mai doma #AGICOM (ica) è dovuto: l’ennesimo esempio di come implementare…

View On WordPress
0 notes
Link

#privacyshield#shieldapps#ransomwaredefender#shieldantivirus#identitytheftpreventer#mobileidentitytheftpreventer
1 note
·
View note
Link
#PrivacyShield mal anders herum. Mit einen Unterschied.. man kümmert sich drum und nutzt es nicht nur als..

0 notes
Text
RiskPro provides the services on the Privacy Shield Framework. To know more, please visit our website.
#PrivacyShield#GDPR#InternationalTradeAdministration#EU-USPrivacyshield#self-assessment#privacyframework#InternalAudit#riskmanagement#riskassessment#riskproservices#cybersecurity#dataprivacy#incidentmanagement#gapassessment#risk assessment#riskadvisory#internal audit#internalaudit
0 notes
Photo



Kritisches Bewusstsein bezüglich Regulierung von Tech-Konzernen wächst @SnowSoftware https://netzpalaver.de/2020/11/04/kritisches-bewusstsein-bezueglich-regulierung-von-tech-konzernen-waechst/
#Compliance#Cybersecurity#Cybersicherheit#Datenschutz#Doomscrolling#DSGVO#Internetgiganten#ITPrioritiesReport#PrivacyShield#Regulierung
0 notes
Text
Privacy Shield e trasferimento dati in USA: il punto della situazione

Il 16 luglio 2020 è certamente una data destinata a restare negli annali della storia della Privacy e della protezione dei dati: si tratta infatti del giorno in cui la Corte di Giustizia dell’Unione Europea, nel suo pronunciamento sulla causa C‑311/18 “Schrems II”, ha invalidato la decisione di adeguatezza della Commissione UE sul Privacy Shield relativa al trasferimento di dati tra l’Unione Europea e gli Stati Uniti. In conseguenza di questa decisione, è ragionevole affermare che il Privacy Shield non può più costituire una valida base per il trasferimento di dati personali verso gli USA. Questa storica sentenza è destinata ad avere una serie di conseguenze immediate e significative su tutte le imprese italiane ed Europee che, utilizzando servizi e/o fornitori negli Stati Uniti e/o aventi realtà infragruppo extra-UE, hanno basato il trasferimento estero dei dati sul Privacy Shield. In questo articolo faremo del nostro meglio per fornire una serie di consigli pratici per la gestione del trasferimento dei dati negli Stati Uniti a seguito della sentenza Schrems II, nella speranza di poter essere d'aiuto ai tanti responsabili privacy e DPO che si troveranno a dover gestire questa scomoda e complessa "gatta da pelare": prima di addentrarci nelle modalità operative, però, è utile spendere qualche minuto per ricordare la genesi del Privacy Shield e l'utilità di questo dispositivo (fino a pochi giorni fa). Read the full article
0 notes
Text
𝐈𝐧𝐯𝐢𝐬𝐢𝐛𝐥𝐞 𝐏𝐨𝐰𝐞𝐫, 𝐔𝐧𝐛𝐞𝐚𝐭𝐚𝐛𝐥𝐞 𝐏𝐞𝐫𝐟𝐨𝐫𝐦𝐚𝐧𝐜𝐞: 𝐁𝐚𝐜𝐤𝐜𝐨𝐧𝐧𝐞𝐜𝐭 𝐏𝐫𝐨𝐱𝐢𝐞𝐬 𝐑𝐞𝐝𝐞𝐟𝐢𝐧𝐢𝐧𝐠 𝐂𝐨𝐧𝐧𝐞𝐜𝐭𝐢𝐯𝐢𝐭𝐲

𝐈𝐧𝐭𝐫𝐨𝐝𝐮𝐜𝐭𝐢𝐨𝐧 𝐭𝐨 𝐁𝐚𝐜𝐤𝐜𝐨𝐧𝐧𝐞𝐜𝐭 𝐏𝐫𝐨𝐱𝐢𝐞𝐬:
In the ever-evolving landscape of online activities, maintaining anonymity, security, and unrestricted access is crucial. One innovative solution that addresses these needs is the Backconnect Proxy. This dynamic proxy server introduces a unique approach by assigning users a random IP address from a pool with each connection request. This rotation of IP addresses proves instrumental for tasks demanding frequent changes, such as web scraping or circumventing IP-based restrictions.
𝐇𝐨𝐰 𝐁𝐚𝐜𝐤𝐜𝐨𝐧𝐧𝐞𝐜𝐭 𝐏𝐫𝐨𝐱𝐢𝐞𝐬 𝐖𝐨𝐫𝐤 ❓
At the core of Backconnect proxies is the ability to dynamically allocate IP addresses. Upon each connection request, users are provided a random IP from a pre-established pool. This rotation ensures that the user’s identity remains concealed, making it challenging for websites or online services to track or restrict their activities.
𝐄𝐬𝐬𝐞𝐧𝐭𝐢𝐚𝐥 𝐅𝐞𝐚𝐭𝐮𝐫𝐞𝐬:
𝐃𝐲𝐧𝐚𝐦𝐢𝐜 𝐈𝐏 𝐑𝐨𝐭𝐚𝐭𝐢𝐨𝐧 🔄 Automatically rotates IP addresses from a pool, preventing tracking and enhancing anonymity.
𝐄𝐧𝐡𝐚𝐧𝐜𝐞𝐝 𝐏𝐫𝐢𝐯𝐚𝐜𝐲 🔒 Acts as an intermediary to shield user identity, providing an additional layer of privacy and security.
𝐁𝐲𝐩𝐚𝐬𝐬 𝐑𝐞𝐬𝐭𝐫𝐢𝐜𝐭𝐢𝐨𝐧𝐬 🌐 Enables users to bypass IP-based restrictions and access content or services that may be otherwise restricted.
𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐌𝐞𝐚𝐬𝐮𝐫𝐞𝐬 🛡️ Offers a secure connection for users by masking their original IP address, reducing the risk of cyber threats.
𝐆𝐥𝐨𝐛𝐚𝐥 𝐏𝐫𝐨𝐱𝐲 𝐏𝐫𝐞𝐬𝐞𝐧𝐜𝐞 🌍 Access to a diverse range of IP addresses worldwide, allowing users to appear as if they are connecting from different geographic locations.
𝐇𝐢𝐠𝐡-𝐒𝐩𝐞𝐞𝐝 𝐂𝐨𝐧𝐧𝐞𝐜𝐭𝐢𝐯𝐢𝐭𝐲 🚀 Maintains fast and reliable connections, ensuring efficient data transfer and optimal performance.
𝐒𝐞𝐚𝐦𝐥𝐞𝐬𝐬 𝐈𝐧𝐭𝐞𝐠𝐫𝐚𝐭𝐢𝐨𝐧 🔧 Easily integrates with various applications and software, making it versatile for different online tasks.
𝐀𝐮𝐭𝐨𝐦𝐚𝐭𝐞𝐝 𝐈𝐏 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭 🤖 Streamlines the process with automatic IP address management, eliminating the need for manual configuration.
𝐏𝐫𝐨𝐱𝐲 𝐃𝐢𝐯𝐞𝐫𝐬𝐢𝐭𝐲 🔄 Offers a diverse pool of proxies, reducing the likelihood of IP blocks and improving overall reliability.
𝐒𝐜𝐚𝐥𝐚𝐛𝐢𝐥𝐢𝐭𝐲 📈 Scales effectively to accommodate increased demand, making it suitable for both individual users and businesses with varying needs.
𝐀𝐝𝐯𝐚𝐧𝐭𝐚𝐠𝐞𝐬 𝐨𝐟 𝐁𝐚𝐜𝐤𝐜𝐨𝐧𝐧𝐞𝐜𝐭 𝐏𝐫𝐨𝐱𝐢𝐞𝐬
𝐀𝐧𝐨𝐧𝐲𝐦𝐢𝐭𝐲 𝐑𝐞𝐢𝐧𝐟𝐨𝐫𝐜𝐞𝐦𝐞𝐧𝐭 Backconnect proxies excel in providing users with a cloak of anonymity. The constant rotation of IP addresses makes it exceedingly difficult for websites to trace user activities back to a single source.
𝐃𝐚𝐭𝐚 𝐒𝐜𝐫𝐚𝐩𝐢𝐧𝐠 𝐄𝐟𝐟𝐢𝐜𝐢𝐞𝐧𝐜𝐲 For web scraping activities, where frequent IP changes are essential to avoid detection and bans, Backconnect proxies prove invaluable. The dynamic IP rotation enables seamless data extraction without interruptions.
𝐀𝐜𝐜𝐞𝐬𝐬 𝐭𝐨 𝐑𝐞𝐬𝐭𝐫𝐢𝐜𝐭𝐞𝐝 𝐂𝐨𝐧𝐭𝐞𝐧𝐭 Geographical restrictions or content limitations based on IP addresses can be circumvented effortlessly with Backconnect proxies. Users can appear as if they are accessing the internet from different locations, unlocking content that might be region-restricted.
𝐄𝐧𝐡𝐚𝐧𝐜𝐞𝐝 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐌𝐞𝐚𝐬𝐮𝐫𝐞𝐬 By acting as an intermediary, Backconnect proxies add an extra layer of security to online activities. The user’s original IP address remains hidden, reducing the risk of potential cyber threats, including hacking and identity theft.
𝐆𝐥𝐨𝐛𝐚𝐥 𝐂𝐨𝐧𝐧𝐞𝐜𝐭𝐢𝐯𝐢𝐭𝐲 The availability of a diverse range of IP addresses from different locations worldwide allows users to simulate connections from virtually anywhere. This global presence proves beneficial for various applications, such as localized marketing campaigns or content testing.
𝐇𝐢𝐠𝐡-𝐒𝐩𝐞𝐞𝐝 𝐂𝐨𝐧𝐧𝐞𝐜𝐭𝐢𝐨𝐧𝐬 Backconnect proxies are designed to maintain high-speed and reliable connections. This is essential for tasks that require efficient data transfer, ensuring optimal performance and user experience.
𝐒𝐞𝐚𝐦𝐥𝐞𝐬𝐬 𝐈𝐧𝐭𝐞𝐠𝐫𝐚𝐭𝐢𝐨𝐧 𝐰𝐢𝐭𝐡 𝐀𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 Versatility is a key feature of Backconnect proxies. They seamlessly integrate with various applications and software, making them suitable for a wide array of online tasks, from social media management to e-commerce activities.
𝐀𝐮𝐭𝐨𝐦𝐚𝐭𝐞𝐝 𝐈𝐏 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭 The automation of IP address management reduces the burden on users. The system takes care of the dynamic allocation of IP addresses, eliminating the need for manual configuration and allowing users to focus on their tasks.
𝐃𝐢𝐯𝐞𝐫𝐬𝐞 𝐏𝐫𝐨𝐱𝐲 𝐏𝐨𝐨𝐥 The availability of a diverse pool of proxies minimizes the risk of IP blocks. Users can switch between different proxies, ensuring a more reliable and uninterrupted online experience.
𝐒𝐜𝐚𝐥𝐚𝐛𝐢𝐥𝐢𝐭𝐲 𝐟𝐨𝐫 𝐕𝐚𝐫𝐢𝐞𝐝 𝐍𝐞𝐞𝐝𝐬 Whether an individual user with specific requirements or a business with varying demands, Backconnect proxies offer scalability. They can effectively handle increased demand, making them suitable for both personal and business use.
𝐄𝐥𝐞𝐯𝐚𝐭𝐞 𝐘𝐨𝐮𝐫 𝐎𝐧𝐥𝐢𝐧𝐞 𝐄𝐱𝐩𝐞𝐫𝐢𝐞𝐧𝐜𝐞 𝐰𝐢𝐭𝐡 𝐕𝐏𝐒 𝐏𝐫𝐨𝐱𝐢𝐞𝐬 𝐈𝐧𝐜. Your IP, Your Rules: VPS Proxies Inc. — Empowering Your Online Presence with Dynamic Backconnect Solutions.
In the ever-evolving digital realm, anonymity, security, and unrestricted access are paramount. VPS Proxies Inc. stands as your trusted source for Backconnect Proxies, offering dynamic IP rotation for ultimate anonymity, enhanced privacy, and seamless access to global content. Our high-speed, secure, and scalable solutions cater to diverse needs, ensuring a reliable and efficient online experience for individuals and businesses alike.
𝐖𝐡𝐲 𝐂𝐡𝐨𝐨𝐬𝐞 𝐕𝐏𝐒 𝐏𝐫𝐨𝐱𝐢𝐞𝐬 𝐈𝐧𝐜 ❓
𝐃𝐲𝐧𝐚𝐦𝐢𝐜 𝐈𝐏 𝐑𝐨𝐭𝐚𝐭𝐢𝐨𝐧: 🔄 Enjoy automatic IP rotation for unparalleled anonymity and privacy.
𝐄𝐧𝐡𝐚𝐧𝐜𝐞𝐝 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐌𝐞𝐚𝐬𝐮𝐫𝐞𝐬: 🛡️ Our proxies act as a shield, providing an additional layer of security for your online activities.
𝐆𝐥𝐨𝐛𝐚𝐥 𝐏𝐫𝐨𝐱𝐲 𝐏𝐫𝐞𝐬𝐞𝐧𝐜𝐞: 🌍 Access a diverse range of IP addresses worldwide, tailoring your online presence to different geographic locations.
𝐒𝐞𝐚𝐦𝐥𝐞𝐬𝐬 𝐈𝐧𝐭𝐞𝐠𝐫𝐚𝐭𝐢𝐨𝐧: 🔧 Easily integrate our proxies with various applications and software, ensuring versatility for your online tasks.
𝐀𝐮𝐭𝐨𝐦𝐚𝐭𝐞𝐝 𝐈𝐏 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭: 🤖 Say goodbye to manual configurations; our system takes care of automatic IP address management.
𝐃𝐢𝐯𝐞𝐫𝐬𝐞 𝐏𝐫𝐨𝐱𝐲 𝐏𝐨𝐨𝐥: 🔄 Benefit from a varied pool of proxies, minimizing the risk of IP blocks and improving overall reliability.
𝐒𝐜𝐚𝐥𝐚𝐛𝐢𝐥𝐢𝐭𝐲 𝐟𝐨𝐫 𝐀𝐥𝐥 𝐍𝐞𝐞𝐝𝐬: 📈 Whether an individual user or a business with varying demands, our proxies scale effectively to meet your requirements.
𝐘𝐨𝐮𝐫 𝐈𝐏, 𝐘𝐨𝐮𝐫 𝐑𝐮𝐥𝐞𝐬: At VPS Proxies Inc., we understand the importance of maintaining control over your online presence. Our Backconnect Proxies empower you with the flexibility to navigate the digital landscape on your terms. Enjoy the benefits of dynamic IP rotation, enhanced security, and global connectivity with our reliable and efficient proxy solutions.
𝐑𝐞𝐚𝐝𝐲 𝐭𝐨 𝐞𝐥𝐞𝐯𝐚𝐭𝐞 𝐲𝐨𝐮𝐫 𝐨𝐧𝐥𝐢𝐧𝐞 𝐞𝐱𝐩𝐞𝐫𝐢𝐞𝐧𝐜𝐞 ❓ Contact VPS Proxies Inc. today for dynamic Backconnect Proxies that put you in control of your digital journey.
𝑬𝒍𝒆𝒗𝒂𝒕𝒆 𝒚𝒐𝒖𝒓 𝒐𝒏𝒍𝒊𝒏𝒆 𝒂𝒄𝒕𝒊𝒗𝒊𝒕𝒊𝒆𝒔 𝒘𝒊𝒕𝒉 𝑽𝑷𝑺 𝑷𝒓𝒐𝒙𝒊𝒆𝒔 𝑰𝒏𝒄. — 𝒀𝒐𝒖𝒓 𝑻𝒓𝒖𝒔𝒕𝒆𝒅 𝑺𝒐𝒖𝒓𝒄𝒆 𝒇𝒐𝒓 𝑩𝒂𝒄𝒌𝒄𝒐𝒏𝒏𝒆𝒄𝒕 𝑷𝒓𝒐𝒙𝒊𝒆𝒔. 𝒀𝒐𝒖𝒓 𝑰𝑷, 𝒀𝒐𝒖𝒓 𝑹𝒖𝒍𝒆𝒔.
𝐂𝐨𝐧𝐜𝐥𝐮𝐬𝐢𝐨𝐧:
VPS Proxies Inc. offers unparalleled backconnect proxy services with round-the-clock support. Our commitment to providing reliable, high-speed connections ensures that your online activities remain secure and uninterrupted. Whether you’re a business seeking enhanced data privacy or an individual looking for seamless browsing experiences, our comprehensive suite of proxy solutions caters to all your needs. Trust VPS Proxies Inc. for dependable services backed by a dedicated support team, ensuring peace of mind and optimal performance for your online ventures.
ℂ𝕠𝕟𝕥𝕒𝕔𝕥 𝕦𝕤:-: 👉🏻 Web: www.vpsproxies.com 👉🏻 Telegram: https://t.me/vpsproxiesinc 👉 Gmail: [email protected] 👉🏻 Skype: live:.cid.79b1850cbc237b2a
#UnrestrictedAccess#InvisibleSurfing#StealthModeON#ProxyLife#OnlinePrivacyGuard#BeyondBoundaries#ProxyMagic#PrivacyFirst#SecureSurfing#AnonymousBrowsing#IPFreedom#DynamicProxy#WebPrivacy#ExploreSecurely#ProxyRevolution#PrivacyShield#WebFreedom#ProxyUniverse#HideMyIP#StayAnonymous
0 notes
Text

USA wollen angeblich EU DSGVO achten
Danke Max Schrems!
Schon vergessen? Nein, Max Schrems hat ja der EU der Reihe nach ein "Datenschutzabkommen" (Safe Harbor, Privacy Shield) nach dem anderen mit den USA wegprozessiert, und zwar nicht zuletzt weil wir seit unserem Ehrenmitglied Edward Snowden wissen, dass die Amis da hemmungslos in den Datentopf greifen, wenn sie können.
180° Wende - USA geben sich geläutert
Man glaubt es kaum - und sollte es auch nicht glauben - wenn der NSA Präsident öffentlich äußert:
Bei der bislang besonders eingreifenden Fernmeldeaufklärung ("Sigint") müsse berücksichtigt werden, "dass alle Personen mit Würde und Respekt behandelt werden sollten", ordnet NSA-Präsident Paul Nakasone in einer jetzt bekannt gewordenen Richtlinie zur Datensammlung vom 29. Juni an.
Dies habe "unabhängig von ihrer Nationalität oder ihrem Wohnort" zu gelten – also auch beim Ausspionieren von Gegnern wie dem russischen Präsidenten Wladimir Putin. Alle Menschen weltweit hätten "berechtigte Datenschutzinteressen", die zu wahren seien. Generell dürfen erhobene Daten über Ausländer nur noch gespeichert werden, wenn eine solche Befugnis auch bei US-Bürgern besteht, geht aus der Vorschrift hervor.
Der einzige Grund für dieses Kreide fressen ist Bidens Executive Order 14086, die Durchführungsverordnung 14086 vom Oktober 2022. In dieser beruft sich Biden auf das EU-U.S. Data Privacy Framework, den Nachfolger von Privacy Shield und stellt fest:
The Department of Justice welcomes the European Commission’s adoption on July 10, 2023 of an adequacy decision for the United States as part of the EU-U.S. Data Privacy Framework, to which President Biden and European Commission President von der Leyen agreed in March of 2022. ... eigentlich eine Null-Aussage außer, dass man sich einig sei ;-)
Nun muss Max Schrems - oder auch jede/r beliebige andere EU-BürgerIn - wieder ran und vor Gericht beweisen, dass den Worten keine Taten gefolgt sind und der Datenklau aus Europa wie vorher weiter geht.
Mehr dazu bei https://www.heise.de/news/Ueberwachung-NSA-soll-weltweit-mit-Wuerde-und-Respekt-spionieren-9286076.html und https://blog.fefe.de/
Kategorie[21]: Unsere Themen in der Presse Short-Link dieser Seite: a-fsa.de/d/3vU Link zu dieser Seite: https://www.aktion-freiheitstattangst.org/de/articles/8505-20230828-usa-wollen-angeblich-eu-dsgvo-achten.htm
#NSA#USA#EU#Big5#Verbraucherdatenschutz#Datenschutzabkommen#SafeHarbor#PrivacyShield#DataPrivacyFramework#Datensicherheit#Datenklau#Algorithmen#Cookies#Smartphone#Handy#sensibleDaten#Diskriminierung#Ungleichbehandlung
1 note
·
View note
Text
privacyshield replied:
the secret is i dont and then i end up with like 3 notebooks of just slow burn bc i like healthy romance too much dkjfg
that’s fair. i love healthy romance too much but also i need to fix what the new owners of my favorite franchises destroyed and i WILL give the characters i love the character development they Deserved
2 notes
·
View notes
Note
m-may i have a muppet...
the muppet random generator is generous today for you have received fozzie bear

4 notes
·
View notes
Link

#CyberSecurity#Cyberattacks#informationTechnologySecurity#ElectronicCyberSecurity#privacyshield#ransomwaredefender#shieldantivirus#identitytheftpreventer#mobileidentitytheftpreventer#networkprivacyshield#driversandshield
0 notes
Note
⅀⅀⅀ !!!
local teen deals with ancient family curse by eating shrubbery and cheating in horse races
spoiled rich kid’s life saved by passing eldritch being, you won’t believe what happens next!
whoever said adversity builds character should have set an upper limit bc this teenager built too much character and has commandeered a dangerous turnip
4 notes
·
View notes