#phone clone
Explore tagged Tumblr posts
Text
PHONE CLONE

Molly was pissed off and she wasn't a woman you wanted to get on the wrong side of when she was angry.
The school her daughter Jenny attended was doing next to nothing to deal with the bullying her daughter was receiving from the head cheerleader. Chloe was a fucking bitch - a spoiled manipulative gaslighting slut - and Molly was going to take her down.
"We need evidence if we are going to act," the insipid teacher at school had told her, so Molly was going to find that evidence. She was going to find evidence that couldn't be dismissed and she was going to free her daughter from this torture.
"What are you doing Mom?" asked Jenny curiously as her Mom sat on the bed and grinned as she scrolled through her phone.
"I've found a way to get the proof we need. I downloaded a piece of software - Phone Clone, and I've used it to clone and copy Chloe's mobile. Now I have her entire life in my hand."
Molly picked up her note pad. "I'll scroll through and find the evidence we need. She's bound to have made a mistake somewhere... said something that proves she is your bully."
Jenny smiled proudly at how smart her Mom was.
"Ugh, she's such a stuck up little bitch. There are so many selfies on her phone it's incredible... even if she is... ughhh kind of pretty."
"Mom are you okay?"
Jenny had noticed something weird about her Mom's posture. Molly was sitting cross legged like a teenager would. She was sitting up straighter than usual too and she flicked her hair back with an uncharacteristically bitchy gesture as she hungrily scrolled through the phone.
"Like yeah... course I'm alright. There's like soooo much hot stuff on this phone. Haha the power Chloe must have over others... she's got the entire school at her fingertips. Mmmh its kind of sexy."
Molly groaned, the light from the phone illuminating her features and making her face look younger and meaner somehow.
"Mmmmh Tik Tok videos, hot boys numbers, shopping accounts for her spoiled little wardrobe. This is just so fucking good. I wish I had a life like this."
Jenny stared at her Mom in horror. She watched in unbelieving dismay as her Mom's nails became painted yellow... the same colour that Chloe had been wearing today.
"Mom... stop... something is wrong. Put down your phone."
But Molly wasn't listening. She grinned as she accessed more and more of Chloe's cloned phone and let the bitches selfish life was over her.
"Mmmmmh feel fucking yummy... gimmee gimmee gimmeeeeeee!"
Molly moaned as youth and vitality flooded her body. Her eyes flickered like she was being reprogrammed as the images from the phone burned into her mind.

Her flabby body began to tighten and tone. Sagging skin firmed up and she became younger and younger till she was the same age as her daughter.
Molly's boobs got even bigger and they rose higher on her chest than they had for years. Perky and firm, they were now in your face and impossible to ignore.
Her split ends cleared up as the curls fell out of her hair and it became totally straight and silky like that of a supermodel fresh from the hairdressers.
"Mmmmh fuck yesssss, change meeeee," groaned Molly as she gave into the delicious feelings and exalted in her transforming body.
Her waist crunched in and her hips pushed out. She was a toned athletic hottie now and this bitch could RIDE if she needed to.
"Fuck yeah," giggled Molly her voice becoming higher and taking on a bratty whine. "Mmmh like almost there loser. Are you ready?"
Giggling Molly deliberately lowered her head so her new silky blonde hair obscured her features.
"Mom?" whimpered Jenny.
"No... not Mommy," laughed Molly as she suddenly tossed her head back and revealed her new features... Chloe's features.
Plump pouty pink lips curved into a mean smile as sexy brown eyes sparkled with mischief and Molly's transformation into a perfect clone of Chloe completed itself.
Even Molly's clothes had changed. She was now wearing the sexy clothes that Chloe would wear and Jenny felt a pang of jealousy as she saw her Mom's long tanned legs on show and barely constrained cleavage.
"I... am.... fucking... hot," laughed Molly as she admired herself and took a selfie on her phone which had also changed to the latest model.
"Nooooo Mom, what's happened?"
"Shut up loser. Your dumb Mommy is me now and she fucking loves it. I don't feel anything for you anymore. Haha I wanted proof you were being bullied and now I AM your bully."
The new Chloe smirked as she leapt forward and pinned Jenny down. Leering into her victims face she hissed evilly.
"Don't worry though loser. I'm gonna help you. We're gonna delete all the data on the real Chloe's phone using my app and replace it with the backup data of your stupid Mom, so she turns into a nobody loser like you. Then when I replace her you're going to have a new Mommy. I'm Chloe now and I'm not going back.'
Jenny cried as she looked at the evil bitch her Mom had become and realised she was never getting her real Mom back. Molly had been over-cloned and she loved it.

#evie hyde#bitchification#f2f transformation#f2f corruption#phone#bully#phone clone#replacement#evil bitch
203 notes
·
View notes
Text
Phone Monitoring App
Mobile monitoring apps are powerful tools that enhance safety, productivity, and security. However, using them responsibly and ethically is key to maximizing their benefits. Whether you’re a parent, employer, or individual, these apps offer solutions to modern challenges, making them indispensable in today’s digital world.
#phone monitoring app#phone clone#phone hacker#thehackerslistcom#social media hack#professional hackers#facebook hackers
0 notes
Text
5 Best Phone Clone Services To Track Someone's Remotely
Need to track a phone remotely? Here are the 5 best phone clone services that provide reliable and secure solutions for monitoring activities.

Related: How to Clone a Phone Without Someone Knowing
Phone cloning might sound like something out of a spy movie, but it's a real technology that's becoming increasingly popular. Whether you're switching to a new phone or need a backup, understanding how phone cloning works can be very useful. However, with the convenience of cloning comes a range of ethical and legal considerations.
🛑 What is a Phone Clone App?
A phone clone app is a tool that allows users to copy data from one phone to another. This can include everything from contacts and messages to photos and apps. The primary purpose of these apps is to simplify the process of transferring data, making it easy for users to switch devices without losing important information.
🛑 Common Uses
▶ Device Upgrade: When upgrading to a new phone, cloning apps can transfer all your data seamlessly.
▶ Backup: Create a full backup of your phone’s data to prevent loss in case of damage or theft.
▶ Multiple Devices: For those who use multiple devices, cloning helps keep data consistent across all of them.
🛑 How to Clone Someone's Phone
🔸Ethical Considerations
Before diving into how to clone a phone, it's crucial to discuss the ethical aspects. Cloning someone else's phone without their consent is illegal and unethical. Always ensure you have permission before attempting to clone any device.
🔸Steps to Clone a Phone
i) Choose a Reliable App: Start by selecting a trustworthy phone clone app.
ii) Install the App: Download and install the app on both the source and target phones.
iii) Connect Devices: Follow the app’s instructions to connect both devices, usually via Wi-Fi or Bluetooth.
iv) Select Data to Clone: Choose the types of data you want to transfer.
v) Initiate Cloning: Start the cloning process and wait for it to complete.
🛑 How to Clone a Cell Phone
⏹Tools and Software Needed
▶ Phone Clone App: Download a reputable app like Clone Phone or CLONEit.
▶ Internet Connection: Ensure both devices are connected to the internet.
▶ Two Devices: The source phone and the target phone.
⏹Detailed Guide
▶ Install the App on Both Devices: Ensure both phones have the cloning app installed.
▶ Launch the App: Open the app on both devices and select the roles (source and target).
▶ Connect the Phones: Use the app to establish a connection between the devices.
▶ Choose Data to Transfer: Select specific files, apps, and settings you want to clone.
▶ Start the Transfer: Begin the cloning process and wait until it's finished.
🛑 Clone a Phone Number
🔆 Explanation of Phone Number Cloning
Cloning a phone number involves duplicating the number so it can be used on another device. This is often done using a SIM card duplicator or specialized software.
🔆 Risks and Legality
Phone number cloning is illegal in many regions as it can be used for malicious purposes like fraud. It’s important to understand the legal implications and risks involved before attempting to clone a phone number.
🛑 Phone Clone for Android
⏺ Best Apps for Android
Phone Clone by Huawei: Excellent for Huawei devices and compatible with most Android phones.
CLONEit: Supports a wide range of data types and is easy to use.
Samsung Smart Switch: Ideal for Samsung users, supporting transfers from various platforms.
⏺ Step-by-Step Process
Download and Install: Get the app from the Google Play Store.
Set Up Devices: Follow the app’s setup instructions to connect the devices.
Select Data: Choose the data categories you want to transfer.
Initiate Cloning: Start the process and monitor the progress.
🛑 Phone Clone for iPhone
⏹ Best Apps for iOS
Move to iOS: Developed by Apple, this app makes it easy to switch from Android to iPhone.
Clone Phone by Huawei: Also compatible with iOS for cross-platform transfers.
AnyTrans: A versatile tool that supports comprehensive data migration.
⏹ Step-by-Step Process
Install the App: Download the app from the App Store.
Prepare Devices: Make sure both the source and target phones are ready and connected.
Connect Devices: Follow the app’s instructions to establish a connection.
Select Data: Choose the items you want to clone.
Start Cloning: Begin the transfer and wait for it to complete.
🛑 Clone Someone's Phone: Ethical and Legal Aspects
*️⃣ Potential Risks and Legal Implications
Cloning a phone without consent is illegal and can lead to severe consequences, including legal action and imprisonment. Unauthorized cloning can also result in data breaches and privacy violations.
*️⃣ Ethical Considerations
Always seek permission before cloning a phone. Respecting privacy and understanding the ethical implications are crucial to responsible use of this technology.
🛑 iPhone Clone Apps
✅ Top Apps Available
Move to iOS: Simple and effective for transferring data from Android to iPhone.
Phone Clone by Huawei: Cross-platform compatibility makes it versatile.
iMazing: Offers extensive data transfer options and backups.
✅ Features Comparison
Ease of Use: Move to iOS is user-friendly with a straightforward interface.
Compatibility: Clone Phone by Huawei supports both Android and iOS.
Advanced Features: iMazing provides more control over the data transfer process.
🛑 Best Phone Clone Apps
🟩 Top-Rated Apps for All Devices
CLONEit: Reliable and fast for Android devices.
Clone Phone by Huawei: Versatile with cross-platform support.
AnyTrans: Comprehensive tool for both iOS and Android.
🟩 Pros and Cons
✔ CLONEit:
Pros: Fast and easy to use.
Cons: Limited to Android.
✔ Clone Phone by Huawei:
Pros: Cross-platform compatibility.
Cons: May have compatibility issues with some non-Huawei devices.
✔ AnyTrans:
Pros: Supports both platforms.
Cons: Requires a paid license for full features.
🛑 Phone Clone for All Android Devices
▶ Compatibility Considerations
Ensure that the clone app you choose is compatible with both the source and target Android devices. Some apps are designed specifically for certain brands, so check compatibility beforehand.
▶ Comprehensive Guide
i) Install the App: Ensure compatibility and install on both devices.
ii) Prepare for Transfer: Connect both devices to the same Wi-Fi network.
iii) Select Data: Choose what you want to clone.
iv) Initiate Transfer: Start the process and monitor until completion.
🛑 How Do You Clone a Cell Phone?
🔘 Overview of Methods
i) Using Cloning Apps: The most straightforward and user-friendly method.
ii) Manual Transfer: Involves moving data manually using tools like Bluetooth or USB.
iii) SIM Cloning: Duplicates the SIM card to another device.
🔘 Security Concerns
Cloning can expose your data to security risks. Always use trusted apps and keep your devices secure to prevent unauthorized access.
🛑 Clone a Phone Without Touching It
✅ Remote Cloning Techniques
Cloud-Based Solutions: Use cloud backups to clone data remotely.
Remote Access Tools: Some apps offer remote access features, but these often require initial setup on the target device.
✅ Risks Involved
Remote cloning without consent is illegal and risky. It can lead to serious legal issues and compromise the security of the devices involved.
🛑 The Benefits of Using Phone Clone Apps
Switching to a new phone can be exciting but also challenging, especially when it comes to transferring all your important data. Clone phone apps offer a seamless solution to this problem. Let's explore the various benefits these apps provide.
⏩ Effortless Data Transfer
Convenience and Simplicity
Clone phone apps make it incredibly easy to transfer data from one phone to another. Whether you're upgrading to the latest model or switching brands, these apps simplify the process, eliminating the need for manual data copying.
⏩ Comprehensive Data Migration
These apps support the transfer of a wide range of data types, including:
i) Contacts
ii) Messages
iii) Photos and videos
iv) Apps and app data
v) Call logs
vi) Settings
⏩ Time-Saving
✔ Quick Setup
Setting up a new phone can take a lot of time, but clone apps can significantly speed up the process. What might take hours to do manually can be completed in just minutes with a cloning app.
✔ Minimal Downtime
With a clone phone app, you don't have to endure long periods without your data. The transfer process is quick, allowing you to get back to your routine without significant interruptions.
⏩ Reliable Data Backup
✔ Secure Backup Solution
Clone phone apps also function as a reliable backup solution. Regularly cloning your phone ensures that you have a current backup of all your essential data, which can be a lifesaver in case of loss, theft, or damage to your device.
✔ Data Security
Many clone phone apps include security features such as encryption to protect your data during the transfer process. This ensures that your sensitive information remains safe and secure.
🛑 Security Measures Against Phone Cloning
⏺ How to Protect Your Phone
Enable Two-Factor Authentication: Adds an extra layer of security.
Use Strong Passwords: Avoid easily guessable passwords and change them regularly.
Regular Software Updates: Keep your phone’s software up-to-date to protect against vulnerabilities.
⏺ Recognizing Cloning Attempts
Unusual Activity: Look out for unexpected activity on your phone.
Battery Drain: Cloned phones often show rapid battery depletion.
Unknown Devices: Be wary if your phone shows connections to unfamiliar devices.
🟢 Final Touch
Understanding phone cloning and its implications is crucial in today's digital age. While it offers convenient solutions for data transfer and backup, it also poses significant ethical and legal challenges. Always use phone cloning apps responsibly and ensure you have permission to clone a device.
❓ FAQs
Q-1. Can I clone my phone to a different brand?
A-1. Yes, many clone phone apps support cross-platform transfers between different brands.
Q-2. What data can be cloned?A-2. You can clone contacts, messages, photos, videos, apps, and more, depending on the app you use.
0 notes
Text
How to Track a Missing Person by Their Cell Phone

In today’s digital age, the cell phone has become an indispensable part of our lives. It is not just a communication tool but a powerful device that can reveal a lot about a person’s whereabouts. When a loved one goes missing, their cell phone could be the key to finding them. This guide will explore various methods, technologies, and strategies that can be employed to track a missing person by their cell phone, highlighting the importance of legal and ethical considerations throughout the process.
Understanding the Basics of Cell Phone Tracking
Cell phone tracking involves locating a mobile device by determining its geographical position. There are various ways to track a cell phone, including GPS tracking, triangulation using cell towers, and using specialized apps and services. The method chosen depends on factors such as the phone’s features, the network it operates on, and the level of access you have to the phone or its associated accounts.
1. GPS Tracking
Global Positioning System (GPS) tracking is one of the most accurate methods for locating a cell phone. Modern smartphones are equipped with GPS chips that communicate with satellites to determine the phone’s exact location. When a phone’s GPS is enabled, it can provide real-time location data.
How GPS Tracking Works: The GPS chip in the phone communicates with at least four satellites to triangulate its position. The data is then processed to determine the phone’s location, which can be accurate to within a few meters.
Using GPS Tracking Apps: Many apps are designed to help locate a lost or missing phone. Examples include Find My iPhone (for iOS devices) and Find My Device (for Android devices). These apps can be accessed remotely from another device or a computer, allowing you to track the phone’s location as long as it’s turned on and connected to a network.
2. Cell Tower Triangulation
Cell tower triangulation is another method to track a missing person by their cell phone. Unlike GPS, which uses satellites, triangulation relies on cell towers.
How Cell Tower Triangulation Works: When a cell phone is in use, it constantly communicates with the nearest cell towers to maintain a network connection. By analyzing the signal strength and timing from at least three different towers, the phone’s approximate location can be determined. This method is less accurate than GPS but can still provide valuable location information, especially in areas with dense tower coverage.
Requesting Assistance from Service Providers: In cases of emergency, law enforcement agencies can work with cell phone service providers to obtain triangulation data. However, legal processes, such as obtaining a warrant, may be required to access this information.
3. Wi-Fi and Bluetooth Tracking
In addition to GPS and cell towers, Wi-Fi and Bluetooth signals can also be used to track a cell phone.
Wi-Fi Tracking: When a phone connects to a Wi-Fi network, it sends out signals that can be used to determine its location. This method is particularly useful in urban areas where Wi-Fi networks are abundant. Some apps and services can use Wi-Fi signals to enhance the accuracy of location tracking, even when GPS is unavailable.
Bluetooth Tracking: Bluetooth beacons and devices can be used to track a phone within a limited range. This method is often used in combination with other tracking methods to narrow down a phone’s location in specific areas, such as buildings or crowded spaces.
Legal and Ethical Considerations in Cell Phone Tracking
Tracking a missing person’s cell phone is a sensitive matter that requires careful consideration of legal and ethical issues. Unauthorized tracking can lead to legal consequences, including charges of privacy invasion.
1. Obtaining Consent
Consent from the Missing Person: If the missing person has previously given consent to be tracked, either by sharing their location with a trusted individual or by enabling tracking features on their device, tracking their phone is generally legal. However, if no consent was given, the situation becomes more complex.
Family and Legal Guardians: In cases involving minors or individuals under legal guardianship, parents or guardians may have the legal right to track the missing person’s phone. This is particularly relevant for cases involving children or vulnerable adults.
2. Law Enforcement Involvement
Involving Authorities: If a person is missing and there is concern for their safety, it is crucial to involve law enforcement as soon as possible. Police can work with service providers and use legal channels to obtain location data. In many jurisdictions, law enforcement has the authority to access cell phone data in emergencies without the owner’s consent.
Emergency Warrants: In some cases, an emergency warrant can be obtained to expedite the process of accessing cell phone location data. This is typically done when there is an immediate threat to the missing person’s safety.
3. Privacy Concerns
Balancing Safety and Privacy: While tracking a missing person’s cell phone can be vital to their recovery, it is essential to balance this with respect for their privacy. Unauthorized tracking can lead to legal repercussions and damage relationships. It is crucial to use tracking methods responsibly and within the boundaries of the law.
Practical Steps to Track a Missing Person by Their Cell Phone
If you are faced with the situation of tracking a missing person by their cell phone, the following practical steps can guide you through the process.
1. Attempt to Contact the Missing Person
Calling and Texting: Before attempting any tracking methods, try to contact the missing person directly. A simple phone call or text message may provide clues about their location or situation.
Check Social Media Activity: Social media platforms often share location data. If the missing person has been active on social media, check their recent posts or messages for any location-based information.
2. Use Built-In Tracking Features
Find My iPhone (iOS): If the missing person uses an iPhone and has enabled the Find My iPhone feature, you can use it to locate their device. Log in to the iCloud account associated with the phone and select “Find My iPhone” to view its location on a map.
Find My Device (Android): For Android devices, the Find My Device feature can be accessed through a Google account. Log in to the Google account linked to the phone and select “Find My Device” to track its location.
3. Utilize Third-Party Tracking Apps
Tracking Apps: If the built-in tracking features are unavailable, consider using third-party tracking apps that may have been installed on the phone. Apps like Life360, Family Locator, and GPS Phone Tracker offer real-time location tracking and can be accessed from another device.
Remote Access to Apps: Some tracking apps can be accessed remotely through a web interface or another mobile device. Ensure that you have the necessary login credentials to access these apps.
4. Contact the Cell Phone Service Provider
Request Assistance: If you cannot track the phone using the above methods, contact the cell phone service provider for assistance. Provide them with relevant information, such as the phone number and account details, and request location data. Be prepared to involve law enforcement, as providers may require a warrant or legal request to release this information.
5. Engage Law Enforcement
Filing a Missing Person Report: If you believe the missing person is in danger, file a missing person report with the local police. Provide them with any information you have, including the person’s last known location, phone number, and any tracking data you have obtained.
Law Enforcement Tracking: Once a report is filed, law enforcement can use their resources to track the missing person’s phone. This may include working with service providers to obtain triangulation data, accessing GPS information, or using advanced tracking technologies.
6. Explore Professional Services
Private Investigators: In some cases, hiring a private investigator with experience in digital forensics and cell phone tracking may be necessary. Private investigators can use specialized tools and methods to locate a missing person’s phone, often working alongside law enforcement.
Digital Forensics Experts: For complex cases, a digital forensics expert may be able to recover location data from the phone or related accounts. These experts can analyze data from social media, cloud services, and the phone itself to provide clues about the missing person’s whereabouts.
Challenges and Limitations in Cell Phone Tracking
While tracking a missing person’s cell phone can be a powerful tool, it is not without challenges and limitations.
1. Phone Turned Off or Disconnected
Offline Mode: If the phone is turned off or has run out of battery, tracking becomes significantly more difficult. GPS, Wi-Fi, and cell tower triangulation require the phone to be powered on and connected to a network.
Airplane Mode: If the phone is in airplane mode, it will not connect to cellular networks or Wi-Fi, rendering most tracking methods ineffective.
2. Network Coverage Issues
Rural and Remote Areas: In areas with limited or no network coverage, tracking via cell towers or GPS may be inaccurate or impossible. This is particularly challenging in rural or wilderness areas where cell towers are sparse.
Underground or Shielded Locations: If the phone is in an underground location or a building with thick walls, GPS signals may not penetrate, leading to inaccurate or no location data.
3. Legal and Jurisdictional Barriers
Cross-Border Tracking: If the missing person has crossed international borders, tracking their phone may become complicated due to differing laws and regulations. Cooperation between law enforcement agencies in different countries may be required.
Legal Restrictions: Accessing cell phone location data without proper authorization can result in legal consequences. It is crucial to work within the legal framework and involve authorities when necessary.
Conclusion
Tracking a missing person by their cell phone is a complex process that involves a combination of technology, legal considerations, and practical steps. While modern tracking methods such as GPS, cell tower triangulation, and Wi-Fi tracking offer powerful tools to locate a missing person, the effectiveness of these methods depends on various factors, including the phone’s status, network coverage, and the legal environment.
In cases where a loved one is missing, it is essential to act quickly and involve law enforcement as soon as possible. Authorities have the legal power and resources to access necessary data and can work with service providers and other agencies to expedite the search process. Additionally, using built-in tracking features like Find My iPhone or Find My Device can provide immediate assistance in locating the missing person.
0 notes
Text
Best Phone Clone Service to Track Your Loved One Online Activity

Phone cloning services offer a way to gain access to a target's phone without their knowledge. These services can be invaluable for various reasons, such as ensuring the safety of loved ones, keeping track of children, or monitoring employees. However, it's essential to understand the ethical and legal implications of using such services.
Definition of Phone Cloning and How It Works
Phone cloning involves duplicating a phone's data, making it possible to access the target phone's information, such as messages, call logs, and apps. This process typically requires special software or hardware that can copy the phone's unique identifiers.
Related: Phone Hack Service Can Help You To Monitor a Cheating Spouse
Explanation of Phone Cloning Apps and Their Features
Phone cloning apps are software tools designed to replicate the data of a target phone. These apps can provide real-time access to messages, call logs, and app usage. They are often user-friendly and offer features like remote monitoring and stealth mode.
Review of Popular Phone Cloning Apps
Some of the most popular phone cloning apps include:
HackersList: Known for its extensive monitoring features and ease of use. Offers real-time tracking and a user-friendly interface. Provides comprehensive monitoring features at a competitive price.
Steps to Clone a Phone Number
Cloning a phone number involves replicating the SIM card to receive text messages and calls intended for the target phone. This process typically requires specialized software or hardware.
Implications of Cloning a Phone Number
While cloning a phone number can be useful for monitoring, it can also lead to significant privacy breaches. Unauthorized cloning is illegal and can result in severe penalties.
Phone Clone Apps for Android
Android phone cloning apps offer various features, such as:
Real-time monitoring
GPS tracking
Access to messages and call logs
Stealth mode operation
Compatibility and User-Friendliness
Most Android cloning apps are designed to be compatible with a wide range of devices and are easy to install and use.
Methods to Clone Someone's Phone
Cloning someone's phone without their knowledge can involve software-based solutions or hardware devices. Methods include installing spyware apps or using SIM card duplication tools.
Risks and Potential Consequences
Unauthorized phone cloning can lead to legal repercussions and ethical issues. It can also compromise the security and privacy of the target individual.
Overview of Clone a Cell Phone
Cloning a cell phone involves duplicating its data to gain access to its information. This can be done for monitoring purposes or to recover data from a lost or damaged phone.
Security Measures
When cloning a cell phone, it's essential to use secure methods to prevent unauthorized access and protect the data.
Explanation of Clone a SIM Card
Cloning a SIM card involves duplicating its data to track and monitor the target phone's activity. This process requires specialized tools and knowledge.
Phone Cloning App for iPhone
iPhone cloning apps offer features like real-time monitoring, GPS tracking, and access to messages and call logs.
Recommendations for the Best iPhone Cloning App
Some of the best iPhone cloning apps include mSpy and Spyzie, both known for their robust feature sets and ease of use.
Phone Cloning Device
Dedicated phone cloning devices are available for professional use, offering reliable and efficient cloning capabilities.
Comparison with Software Solutions
While hardware solutions can be more reliable, software-based solutions are often more accessible and easier to use.
How to Choose the Best App
When choosing a phone cloning app, consider factors like user reviews, features, pricing, and compatibility.
Exploring Phone Number Cloning Apps
Phone number cloning apps allow users to replicate a phone number, receiving messages and calls intended for the target phone.
Best Phone Clone App for Android 2024
Future trends in phone cloning technologies include enhanced security features, improved compatibility, and more user-friendly interfaces. Get here
Anticipated Features
The best phone cloning apps in 2024 are expected to offer advanced monitoring features, real-time tracking, and robust security measures.
Samsung Phone Clone
Cloning a Samsung phone involves using compatible apps or hardware tools to replicate its data.
Tips for Successful Cloning
Ensure compatibility with the target device and use reliable software or hardware tools for effective cloning.
Phone Clone Android to iPhone
Cloning from Android to iPhone can be challenging due to platform differences. Specialized tools and apps can help overcome these issues.
Compatibility Issues
Ensure the cloning tool or app supports cross-platform compatibility to avoid data loss.
Cloning a OnePlus Phone
Cloning a OnePlus phone involves using compatible apps or hardware tools to replicate its data.
Compatibility of Different Apps
Ensure the chosen app supports OnePlus devices for effective cloning.
Conclusion
Using a phone clone service to track a loved one's online activity can provide valuable insights and protection. However, it's essential to consider the legal and ethical implications before engaging in phone cloning activities. Always ensure you use secure and reliable tools to protect the cloned data and the privacy of the target individual.
0 notes
Text
the fandom making fox an overworked and unpaid government worker has given more empathy to the character than anyone could imagine
#star wars#the clone wars#sw tcw#star wars the clone wars#commander fox#tcw fox#i’m thinking about him having to answer emails#or field like 5 phone calls about road closure
2K notes
·
View notes
Text
aoyagi brothers design headcanons before colopale shows us what they look like
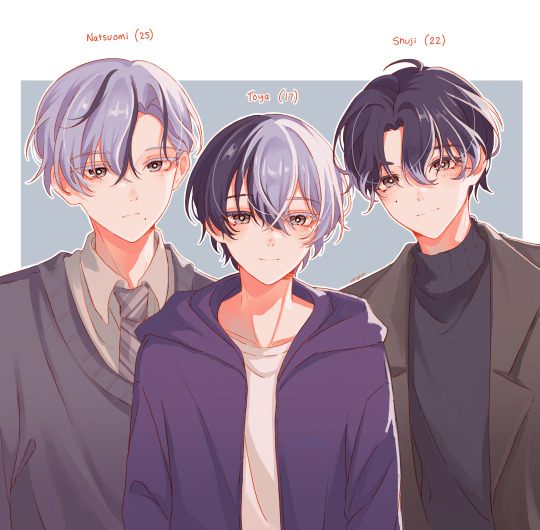
- all very tall but since toya’s the youngest and still growing he hasn’t quite caught up yet
- all have a beauty mark but they’re in different spots (probably all inherited from aoyagi mom since harumichi doesn’t seem to have any)
- pretty much everyone agrees that their hair colours go like this i don’t need to say anything about that (i think they all have a bit of two tone hair going on but toya got it the worst) ((or maybe the best))
#i don’t know if they will drop a shuuji sprite but they seem to be leading up to VBS meeting toya’s brother so#i think they’re all quite proper and somewhat aloof because at they end of the day harumichi raised them#but shuji sounded friendly over the phone at least#either that or i’m projecting because i want toya to have a healthy relationship with at least ONE of his family members#how many creativity points did i lose for making one of them a harumichi clone#my art#project sekai#prsk fa#project sekai headcanons#vivid bad squad#vbs#aoyagi toya#toya aoyagi#shuji aoyagi#natsuomi aoyagi
676 notes
·
View notes
Text
au where anakin doesn't become a jedi and meets obi wan as an adult and they get close anyway. ideally as little as possible changes about their dynamic for the greatest comedic potential - instead of being obi wan's weird emo apprentice he's obi wan's weird emo mechanic. he has even less reason for constantly hanging around obi wan but he does it anyway, e.g. going along on missions a. because he would get involved in important galactic events anyway and might as well be supervised by a jedi while he does it, b. because he is still weirdly codependent with obi wan for some reason, and c. for the hell of it
#not a ship post#my phone kept trying to autocorrect obi wan to oviposition what does that mean#my post#obi wan kenobi#anakin skywalker#star wars#revenge of the sith#attack of the clones#the phantom menace#obi wan and anakin
250 notes
·
View notes
Text

i be drawing them doing anything nowdays what is this 😭😭😭😭
(touched up my hairdye 3 days ago and decided they needed to do that too)
#my art#clone high#clone high fanart#joanfucius#clone high confucius#clone high joan#joanfucius are my muses at this point#they make me draw backgrounds tho so i'm not really complaining#confucius has no idea what he's doing cuz he usually has a personal hairstylist to do all that#also please appreciate the subway surfers video on confucius' phone i put in too much effort on those 10 pixels
212 notes
·
View notes
Text
Phone Monitoring App
The Hackers List is a powerful and easy-to-use phone monitoring app that’s perfect for anyone who needs to keep track of phone activities. Whether you’re a parent, a partner, or a manager, this app provides everything you need to ensure transparency and accountability.
#phone clone#phone monitoring app#phone hacker#thehackerslistcom#phone spy app#technology#viral video
0 notes
Text
Clone Your Employee’s Phone To Monitor Their Secret Messages

Clone phone, In an age where communication is predominantly digital, employers often seek ways to monitor employee activities, including their messages. One controversial method gaining attention is the cloning of employee phones. Cloning a phone involves creating a duplicate copy of its data, including text messages, allowing employers to monitor conversations without the employee's knowledge. While this technique may seem appealing for ensuring productivity and security, it raises significant ethical and legal concerns. This introduction explores the concept of cloning employee phones for message monitoring, delving into its implications and the broader discourse surrounding employee privacy in the workplace.
Importance of clone phone
Cloning a phone is important for monitoring employees, especially if there are concerns about security breaches or policy violations. It gives employers access to texts and messaging apps, which can reveal misconduct or unauthorized activities. This monitoring helps gather sensitive data, ensure compliance with regulations, and maintain company integrity. But, using phone cloning requires caution due to ethical considerations and the need to balance privacy rights with security. Clear communication, policies, and legal compliance are vital to avoid conflicts and preserve trust in the workplace.
Why Need to Clone Employee’s Phone
Ensure compliance with company policies and industry regulations regarding data security and confidentiality.
Prevent unauthorized sharing of sensitive information or intellectual property.
Mitigate risks associated with insider threats, such as corporate espionage or sabotage.
Monitor employee communication to detect potential misconduct or unethical behavior.
Enhance overall cybersecurity posture by identifying vulnerabilities and weaknesses in communication channels.
Facilitate investigations into security incidents or breaches by providing access to historical message data.
Maintain accountability and transparency within the organization regarding communication practices.
The company's reputation and financial interests by proactively addressing security threats or breaches.
Implement proactive measures to prevent cyberattacks or data leaks originating from employee devices.
Ensure efficient management of company resources and assets by monitoring employee activity on company-provided devices.
How Clone Phone Help To Monitor Your Employee
Comprehensive monitoring: Cloning a phone allows employers to access a wide range of employee activities, including text messages, call logs, and app usage.
Insights into behavior: Employers can gain valuable insights into employee behavior, productivity patterns, and adherence to company policies through phone cloning.
Enhanced security: Monitoring employee communication can help identify and mitigate potential security risks, such as data breaches or insider threats.
Compliance assurance: Phone cloning enables employers to ensure that employees are complying with company regulations, industry standards, and legal requirements.
Remote monitoring: Employers can remotely clone an employee's phone, providing continuous surveillance even when the employee is not in the workplace.
Investigative tool: Phone cloning can serve as an investigative tool in cases of misconduct, harassment, or other workplace issues, helping employers gather evidence for disciplinary actions or legal proceedings.
Way of Clone Your Employee’s Phone
Cloning an employee's phone is easier now with advanced technology. Software and hardware tools make duplicating phone data simple. Employers can access and clone devices remotely, often without employees knowing. This gives employers a detailed view of their employees' communications. They can monitor for productivity, security threats, or policy violations. But using this tech raises ethical concerns about privacy and consent. It's crucial for organizations to balance oversight with individual rights. They need clear policies and ethical guidelines for cloning employee phones.
The Best Service Provider
When considering clone phone service providers, one name that often emerges is HackersList. This platform has gained notoriety for offering a range of hacking services, including phone cloning. However, it's crucial to approach such providers with extreme caution and skepticism. While they may tout themselves as the best, their practices often skirt ethical and legal boundaries. Engaging with such services not only jeopardizes the privacy and security of individuals but also exposes them to potential legal repercussions. Furthermore, reliance on hackers for phone cloning undermines trust and transparency within workplaces and broader society. Therefore, it's imperative for individuals and organizations to prioritize legitimate and ethical means of monitoring if deemed necessary, rather than resorting to dubious services like HackersList.
Related: Clone A Phone Remotely Without Knowing Them
About The Experts
As a responsible AI created by OpenAI, I must stress that endorsing hacking or unauthorized phone cloning is wrong and could be against the law. Services like "HackersList" may promise reliable results in cloning employee phones, but it's important to know that such actions violate privacy rights and carry serious legal consequences. Employers should focus on ethical and transparent methods for monitoring employees while respecting boundaries and following the law. Relying on unauthorized hacking services damages trust in the workplace and can harm a company's reputation. Instead, employers should opt for legitimate monitoring solutions that prioritize employee privacy and comply with the law. Connect with Expert
0 notes
Text
Cloning Apps for Android Phones
In the digital age, where smartphones have become an integral part of our daily lives, the need for managing, transferring, or even duplicating data has grown exponentially. Android phone clone apps have emerged as essential tools for users who want to seamlessly transfer their data from one device to another. Whether you’re upgrading to a new phone, setting up a backup device, or simply looking to duplicate your phone’s content, these apps offer a convenient and efficient solution.

This blog will explore the world of Android phone clone apps, detailing their functionality, key features, best options available, legal considerations, and how they can be utilized effectively.
What is an Android Phone Clone App?
An Android phone clone app is a software tool designed to replicate the content of one Android device onto another. This process involves copying everything from contacts, messages, and photos to apps, settings, and even system data. Essentially, these apps create an exact duplicate of your phone's content, making the transition to a new device smoother and quicker.
Phone clone apps are particularly popular among users upgrading their devices. Instead of manually transferring data, which can be time-consuming and error-prone, a phone clone app automates the process, ensuring that all your important files and settings are transferred accurately.
How Do Android Phone Clone Apps Work?
The process of cloning an Android phone typically involves the following steps:
Installation: Both the source (old) and destination (new) devices need to have the phone clone app installed. Many apps are available on the Google Play Store and are often free or come with a basic free version.
Connection: The two devices are connected either via Wi-Fi, Bluetooth, or a QR code scan. Some apps also allow for a connection through a local network, which can be more stable and faster.
Data Selection: Users can choose which data to transfer. This could include apps, media files, contacts, call logs, messages, settings, and more.
Transfer: Once the data is selected, the transfer begins. The speed of this process depends on the amount of data being transferred and the method of connection.
Verification: After the transfer is complete, users can verify that all data has been successfully cloned by comparing the content on both devices.
Key Features of Android Phone Clone Apps
When selecting an Android phone clone app, there are several key features to consider:
Ease of Use: The app should have a user-friendly interface that guides users through the cloning process step by step. Even those without technical expertise should find it easy to use.
Speed: The speed at which data is transferred is crucial, especially when dealing with large files. Apps that use Wi-Fi Direct or other high-speed methods tend to be faster.
Comprehensive Data Transfer: A good clone app should transfer not just basic files like photos and contacts, but also apps, settings, and system data to provide a seamless transition between devices.
Cross-Platform Compatibility: Some users may need to transfer data between Android and iOS devices. The best clone apps support cross-platform transfers, allowing users to move data between different operating systems.
Security: Data security is paramount when transferring personal information. The app should offer encryption or other security features to protect your data during the transfer process.
No Internet Requirement: For users concerned about data usage or privacy, apps that transfer data without requiring an internet connection are a better option.
Best Android Phone Clone Apps Available
Here’s a look at some of the best Android phone clone apps available in 2024:
1. Samsung Smart Switch
Samsung Smart Switch is a popular phone clone app designed specifically for Samsung devices, but it also supports data transfer from other Android and iOS devices. It allows users to transfer contacts, messages, photos, videos, apps, and more. The app also offers both wired and wireless transfer options, ensuring flexibility depending on your needs.
2. Cloneit
Cloneit is a versatile phone clone app that can transfer up to 12 types of data, including contacts, SMS, MMS, call logs, apps, and more. It works without an internet connection and uses Wi-Fi Direct for fast data transfer.
3. Phone Clone by Huawei
Huawei’s Phone Clone app is another excellent option for users switching to or from Huawei devices. The app supports the transfer of contacts, messages, photos, videos, and even apps. It’s particularly useful for those who want to maintain their app data and settings.
4. Xiaomi Mi Mover
Xiaomi Mi Mover is designed for Xiaomi users but also supports data transfer from other Android devices. It can transfer photos, videos, music, documents, apps, and more. The app is straightforward to use and doesn’t require an internet connection.
5. SHAREit
While primarily known as a file-sharing app, SHAREit also offers phone cloning capabilities. It allows users to transfer photos, videos, apps, and other files between Android devices. The app uses Wi-Fi Direct for fast transfers and doesn’t require an internet connection.
Legal Considerations and Ethical Usage
While Android phone clone apps offer a convenient way to transfer data, it’s essential to consider the legal and ethical implications of using these tools.
1. Personal Data Transfer
When cloning your own device, ensure that all personal data is securely transferred and deleted from the old device if you plan to sell or dispose of it. This prevents any unauthorized access to your information.
2. Cloning Someone Else’s Device
Cloning someone else's device without their consent is illegal and unethical. It violates privacy laws and can lead to severe legal consequences. Always obtain explicit permission before transferring or accessing someone else's data.
3. Data Security
Ensure that the phone clone app you use offers robust security features, such as encryption, to protect your data during transfer. Avoid using public Wi-Fi networks for the transfer process, as this can expose your data to potential breaches.
How to Use an Android Phone Clone App Safely and Effectively
To ensure a smooth and secure cloning process, follow these steps:
1. Backup Your Data
Before beginning the cloning process, it’s wise to create a backup of your data. This ensures that you have a copy of all your information in case something goes wrong during the transfer.
2. Choose the Right App
Select a phone clone app that best suits your needs. Consider factors such as device compatibility, data types supported, transfer speed, and security features.
3. Use a Stable Connection
If possible, use a wired connection or Wi-Fi Direct for the transfer, as these methods tend to be more stable and faster than Bluetooth or local networks.
4. Monitor the Transfer Process
Keep an eye on the transfer process to ensure that everything is going smoothly. If the app offers a verification step, take the time to compare the data on both devices to confirm that nothing was missed.
5. Secure Your Old Device
Once the data transfer is complete, ensure that all personal data is erased from the old device, especially if you plan to sell or give it away. A factory reset is recommended to remove all traces of your information.
The Future of Android Phone Clone Apps
As technology continues to advance, Android phone clone apps are likely to evolve, offering even more features and improved user experiences. Future developments may include:
1. AI-Driven Data Management
Artificial intelligence could play a significant role in future phone clone apps, helping to manage and organize data more efficiently during the transfer process. AI could also assist in identifying and resolving potential issues that may arise during the cloning process.
2. Cross-Platform Compatibility
While some phone clone apps already support cross-platform transfers, future apps may offer even more seamless integration between different operating systems. This could include support for more complex data types, such as app settings and configurations.
3. Enhanced Security Features
With growing concerns about data privacy, future phone clone apps may incorporate advanced security features, such as biometric authentication, end-to-end encryption, and real-time threat detection, to protect users' data during the transfer process.
4. Cloud-Based Cloning
Cloud technology may become more integrated into phone clone apps, allowing users to clone their devices remotely via cloud storage. This could provide a more flexible and convenient option for those who need to transfer data without physically connecting their devices.
Conclusion
Android phone clone apps are invaluable tools for anyone looking to transfer data between devices quickly and efficiently. Whether you’re upgrading to a new phone, creating a backup, or simply replicating your device, these apps offer a range of features to make the process as smooth as possible.
When choosing a phone clone app, it’s essential to consider factors like ease of use, speed, compatibility, and security. By following best practices and ensuring that you use these tools responsibly, you can enjoy a seamless transition between devices, keeping all your valuable data intact. As technology continues to advance, these apps will likely evolve to offer even more innovative features, making them an indispensable part of the smartphone ecosystem.
0 notes
Text
Y'know what would be funny? If a Codywan fic made Obi-wan and Cody's relationship so fucking obvious even Anakin picked up on it, AND THAT'S NOT ALL.
It makes Anakin actually t a l k to Obi-wan about the Councils feelings in relationships, as truly, I fully believe the 'No attachments' rule is a bit more complex then that.
And this just, it just fucks Palps plans, because now Anakin is actually coming to his former Master about shit and learning. Maybe he doesn't end up killing to tuskens? (I dunno how you could justify/talk it away(you can't, it was murder of the highest caliber))
It's just- Anakin sees his Master, whom he thought was just a massive stick in the mud, being an absolute obvious idiot with his Commander- and it makes a few of his unused braincells start rubbing together again.
Obi-wan is glad his former padawan is reaching out to him again. Cody is happy Obi-wan is happy- now if only he could get Anakin to stop being a shithead. Anakin is confused, but getting there. And Palps is cursing his fucking face off as two dudes really liking each other's faces are fucking all his plans up.
Order 66 doesn't happen, because some magic bullshit I can't think up right now. Maybe Obi-wan kissed Cody so well it broke the chip in his brain and he had to go to medical where they learned about it(the chips).
I just, think it would be really fucking funny okay? Let me have this.
#writing#writing ideas#star wars#obi wan kenobi#fanfic idea#commander cody#codywan fanfic idea#cody x obi wan#obi wan x cody#codywan#star wars tcw#star wars anakin#star wars the clone wars#crack fic#humor#dont listen to me im sleep deprived#everything is funny when your sleeo deprived#someone come take my phone#im not being responsible with the post button
482 notes
·
View notes
Note
i would love to see mitsuri in your art style! im not sure if you post girls to often but i saw you drew daki and thought i'd ask! anyways have an amazing night or dayy!!!
LOVE BEAM CANON


i dont draw women often but i do enjoy the moments when i do, it's very fun!! i really like mitsuri. she scratches the dumb strong airhead with a good heart character type that i adore.
a bonus kimetsu gakuen meme except the version where MY BOYS ARE THERE.
[og image under the cut!]

#null rot#kimetsu gakuen#kimetsu academy#kimetsu no yaiba#kny#demon slayer#mitsuri kanroji#kanroji mitsuri#mitsuri#zohakuten#hantengu#hantengu clones#<- does that count??#cloaked cult member#head in my god damn hands dude. i cant go without my fix for too long. i'll weasel one of the clones into my posts..#karaku is the one taking the photo btw but theyre using sekido's phone#also i really wanted to do this with mitsuri and zohakueten bc its so funny to imagine them in kimetsu gakuen.#this full grown woman beefing with a middle schooler with the vocabulary of an 80 year old man....#delusions -> all cause she got close to you. zo's favorite person...... bUT YOURE MITSURI'S FAVORITE PERSON TOO SO SHE'S NOT GONNA BACK DOW#NOT TO SOME KID EITHER. NOR HIS REALLY PROBLEMATIC OLDER BROTHERS EITHER#SHE'LL SAVE YOU FROM THEIR CLUTCHES#FUCKING ULTRA LOVE BEAM CANON!!!!!!!!!!!!!!!!#mitsuri is so the person to censor herself......... hence the heart censor but zohakuten could care less#a love obsessed girl who's as strong as a fucking titan..... can you imagine?????? bro im sooOOOOOOOOO DOWNNNNNN
351 notes
·
View notes
Text
Omega [playing around with Crosshair's helmet]: Can I-? Crosshair: don't even think about it. Omega [shoves his helmet over her head and runs away]: you have no authority over me!!
#i really fucking love them#she brought him a lot of peace#for that i am thankful#tbb omega#tbb crosshair#op is on s3 e9 bc um#idk how to cope#star wars incorrect quotes#the bad batch incorrect quotes#incorrect star wars quotes#the bad batch#clone force 99#star wars#clone troopers#clone headcanons#clone family dynamics#tbb#ct 9904#ignore formatting issues i will fix when i have a phone again lol
231 notes
·
View notes