#Phone Hacking
Explore tagged Tumblr posts
Text
💥 The Duke of Sussex, Sir Elton John and Baroness Doreen Lawrence can continue their unlawful information gathering claims against the publisher of the Daily Mail, after it lost a bid to have the cases thrown out at the High Court 💥
39 notes
·
View notes
Text


Prince Harry's uncle, Charles Spencer, shows his support for Harry's case. Charles Spencer, brother of Princess Diana, shared former Labour adviser Alistair Campbell's tweets about the case via Twitter & Instagram.
One of the tweets was about the dangers of reading about Harry's case via UK media sources, which clearly have an agenda against Prince Harry.
#prince harry#the duke of sussex#duke of sussex#brf#british royals#the british monarchy#british tabloids#british royal family#uk royals#uk royal family#uk tabloids#phone hacking#harry and meghan#charles spencer#princess diana#diana spencer#toxic media
84 notes
·
View notes
Text


96 notes
·
View notes
Text
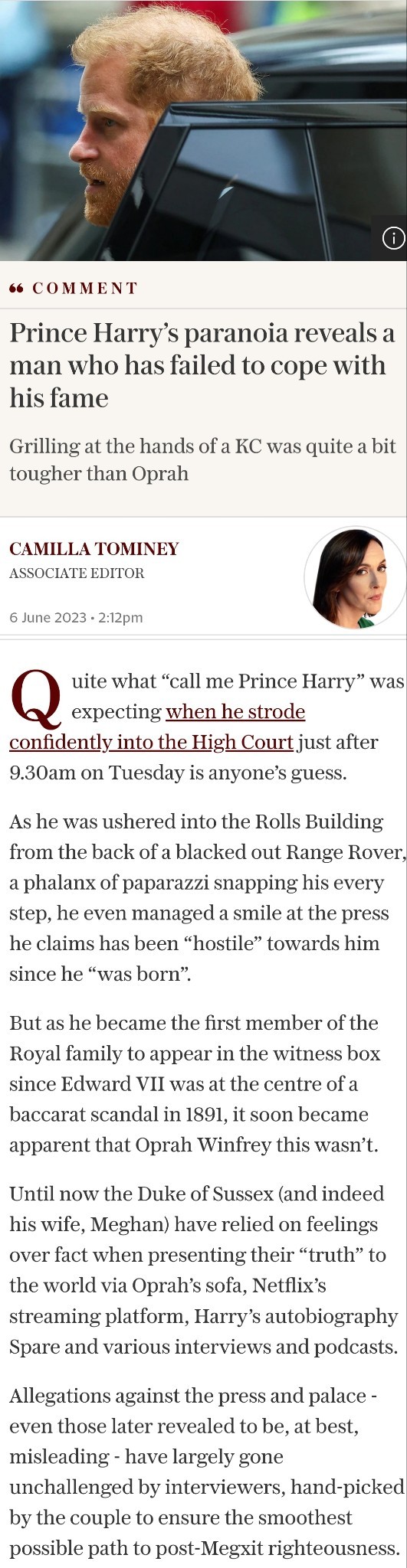
Prince Harry: decision to take on tabloids contributed to family ‘rift’
Duke of Sussex tells ITV documentary that legal battles against newspapers ‘central’ to deterioration in relations
Caroline Davies

Wed 24 Jul 2024 16.46 BST
The Duke of Sussex believes his determination to take on tabloid newspapers in the courts was a “central piece” in the deterioration of relations between him and his family in the UK.
Speaking about his legal battles against newspapers over privacy, Prince Harry told an ITV documentary Tabloids on Trial that his decision to fight contributed to the “rift” with the royal family.
Asked if his decision destroyed the relationship, Harry says: “Yeah, that’s certainly a central piece to it. But, you know, that’s a hard question to answer because anything I say about my family results in a torrent of abuse from the press.”
He continues: “I’ve made it very clear that this is something that needs to be done. It would be nice if we, you know, did it as a family. I believe that, again, from a service standpoint and when you are in a public role, that these are the things that we should be doing for the greater good. But, you know, I’m doing this for my reasons.”
Asked what he thought of the royal family’s decision not to fight in the way he has done, he replies: “I think everything that has played out has shown people what the truth of the matter is. For me, the mission continues, but it has, it has, yes. It’s caused, yeah, as you say, part of a rift.”
Harry has long despaired of the royal family’s failure to take on the press, and has previously revealed that his father, King Charles, told him it would be a “suicide mission”.
In his memoir, Spare, he wrote of what he saw as the royal family’s connivance with the media through alleged leaking, believing himself to be collateral damage. In the book Harry was withering about his father’s failure to take on the media, writing that “the same shoddy bastards who’d portrayed [Charles] as a clown” were now “tormenting and bullying” him and his wife, Meghan.
In December 2023, after he won damages in his hacking case against Mirror Group Newspapers, Harry made clear he felt vindication for his long-running legal battles against sections of the British media. He said in the statement at the time that he had “been told that slaying dragons will get you burned”, adding a defiant: “The mission continues.”
Speaking for the first time about the case, he told the documentary: “To go in there and come out and have the judge rule in our favour was obviously huge … a monumental victory.”
He also spoke about fears that his mother, the late Diana, Princess of Wales, may have been an early victim of phone hacking.
The duke, who is one of several celebrities appearing in the documentary which airs on ITV1 and ITVX at 9pm on Thursday, is also involved in continuing legal actions over privacy against News Group Newspapers and Associated Newspapers.
9 notes
·
View notes
Text
Fuck a doodle do.
In a statement, Prince Harry said the ruling was "vindicating and affirming" and took aim at senior executives and editors including Piers Morgan - who was in charge at the Daily Mirror from 1995 to 2004.
Judge Mr Justice Fancourt found Morgan knew about phone hacking at the paper.
He said the Duke's phone was probably only hacked to a modest extent and was "carefully controlled by certain people" from the end of 2003 to April 2009.
Jesus -- this is.... unbelievable.
When asked what he thought the way forward was, he said to scrap the current press regulator, the Independent Press Standards Organisation, which he likened to a "poodle".
"You have to get independent regulation as Leveson called for, which we haven't got because, there's a self regulator poodle, not a watchdog," he said.
"You also need to have the Leveson Inquiry restarted or completed... which the government cancelled at the request of those being investigated."
The Tory government should hang its head in shame. I mean -- it won't, but seriously -- this is appalling.
The government has failed to find the courage to hold the press accountable, a media lawyer has said.
Jonathan Coad said that despite Prince Harry's victory, only politicians can bring about real change.
However, it has never ensured the press regulated itself according to the principles set out in the Leveson Inquiry, he said.
"If you're going to be accountable, someone has got to have the courage to hold you accountable," he told Sky News.
"Harry has fought the battle and said it needs to change, but it is only going to change if politicians have the courage to take on Fleet Street.
"At the moment, they have shown a complete lack of intention of doing so.
What was the Leveson Inquiry and why is it relevant?
In 2011, Judge Sir Brian Leveson led a public inquiry after it was revealed News Of The World journalists had hacked the phone of murdered school girl Milly Dowler.
Initially intended to be carried out in two sections, the first part of the inquiry looked at the culture, practices and ethics of the press. It involved celebrities including Hugh Grant, Sienna Miller, Steve Coogan and Charlotte Church.
Part two of the Leveson Inquiry was meant to investigate the relationship between journalists and the police, but never took place. There have since been calls to re-open it.
#phone hacking#hacked off#fleet street#daily mirror#mirror group#piers morgan#prince harry#gentlemen of the press#leveson inquiry
19 notes
·
View notes
Text
Mirror Group in-house lawyer knew about phone hacking, rules court in Prince Harry judgment | Law Gazette


If these people don't go to jail. Hacking someone's phone at least 13 times feels jailable but we'll have to see. I hope Piers Morgan goes to prison. He's such a creature
I hope the payout he gets breaks them. He's taking other newspapers to court for hacking his phone and I think other people are a part of those cases as well. British newspapers are so corrupt and have ruined people's lives. It's wishful thinking but maybe this will be the crack that breaks Murdoch's grip on the media.
16 notes
·
View notes
Text
Been thinking about if I had a secret hacker/stalker friend. Some close with a little bit of a crush. Maybe when we were hanging out one day and I was away from my phone they installed some spyware on my phone. It wouldn’t be too hard. I trust my friends with my passcode.
We continue to hangout, me being completely oblivious to any changes. We are just sitting on the couch together playing on our phones. being the horny guy I am, I look at something nsfw. Maybe it’s my twitter, here on tumblr, or one of my many online fanfics and bl mangas. While they are finishing setting up the bug on their phone, ready to live watch my every move with a recording feature for when they are too busy to live view.
They watch my every move over a couple of weeks, maybe even a month or two. Keeping track of all of the deprived and horny thing I look at. Taking notes on the most interesting and embarrassing kink and quirks.
Suddenly I get a message on here. “I know who you are.”
I laugh it off, pretending that paranoia hasn’t already started to eat away at me. I respond quickly so as to not overthink it. I play it coy and respond: “oh yeah, what do you know about then?” ”I can’t just take your word for it��
They take a moment, maybe 10-15 minutes. They know that this will increase my anxiety, make me more malleable. Suddenly they start typing and it take a while but they finally send the message.
“How do you want me to prove to you then? I have so many options for you! I could just send you a photo of yourself. Simple and effective but I don’t think that would excite either of us enough now would it? You like so many disgusting things ‘Issac’. Though we both know that isn’t your real name. Just one of your several allies to keep your anonymity. I’m proud of you for at least trying to keep your info safe but you really need to switch up your passwords and start adding 2 -factor to more of your apps. Not that that could protect you from me. mmm let me see… I could quote one of your favorite post, one of the one you won’t reblog out of fear. Or how about I tell you where you work? Maybe you’d like that one. It’s scary to think someone could connect this blog to you and your job. You’d get fired for sure. Oh and I’ll give you one more option. I’ll login here and post something. Whatever i want, I’ll respect you wish for privacy but maybe I’ll slip something small in just for me.”
I panic reading their message. I try to reply, i haven’t decided what to say but I start typing and suddenly I’m kick out of tumblr. More panic sets in as I try to open the app, it won’t let me. 2 minutes pass as I am frantically trying to get in and my screen turn black. Text appears on the screen.
Go ahead and open it up again
Go and see what I have done
My screen returns to normal. I hesitantly open tumblr, afraid of what i might find. I look at my posts, there is a new one from just 50 seconds ago. Just one word. My deadname.
#ftm ns/fw#ftm nsft#send r3pe threats#hacking#stalking fantasy#stalking k!nk#phone hacker#phone hacking#threats#paranoia#paranoia play#fear#fear k!nk#fear kink#deadname
2 notes
·
View notes
Text
11 notes
·
View notes
Text
How Do Private Investigators Track Cell Phones?
Private investigators (PIs) are known for their resourcefulness and ability to uncover information that may seem out of reach for the average person. Among their many skills, tracking cell phones has become a critical tool in modern investigations. Whether working on cases involving missing persons, fraud, infidelity, or corporate espionage, PIs often rely on cell phone tracking to collect crucial evidence.

But how do private investigators track cell phones? This blog explores the techniques, tools, and ethical considerations involved in this sensitive process.
1. The Basics of Cell Phone Tracking
Cell phone tracking involves determining the location of a device by utilizing the technology it relies on to function—cell towers, GPS, and Wi-Fi networks. Smartphones emit signals that can be intercepted or analyzed to pinpoint their location. While law enforcement agencies have sophisticated tools and legal authority for tracking, private investigators often use alternative methods that stay within legal boundaries.
2. Common Techniques Used by Private Investigators
a. GPS Tracking
GPS (Global Positioning System) tracking is one of the most accurate ways to locate a cell phone. Many modern devices come equipped with built-in GPS chips that constantly communicate with satellites to determine their location. Private investigators might use the following approaches to access GPS data:
Authorized Access: If a private investigator has legal permission (e.g., from the device owner), they can use GPS tracking apps to monitor the phone's location. This is common in cases of missing persons or parental tracking of children.
Location-Sharing Apps: Some apps, like Find My iPhone or Google Find My Device, allow users to share their location. A PI might assist clients in accessing these features, provided they have the right credentials or consent.
b. Cell Tower Triangulation
Cell phones connect to nearby towers for communication, and the distance to these towers can be used to approximate the device's location. By analyzing signal strength from multiple towers, a process known as triangulation can determine the phone's general whereabouts.
Private investigators might collaborate with telecommunications providers to request such data, but this typically requires proper legal justification, such as a subpoena or court order.
c. Wi-Fi Positioning Systems (WPS)
Many modern devices use Wi-Fi signals for location tracking when GPS is unavailable. By identifying the networks a phone connects to, investigators can narrow down the location. This technique is particularly useful in urban areas, where Wi-Fi networks are abundant.
d. Mobile Applications
Private investigators may use third-party apps designed for tracking. These apps often require installation on the target device, making their use legally and ethically complex. Popular tracking apps include:
mSpy: Often marketed for parental control, this app can monitor a phone’s location, messages, and activity.
FlexiSPY: Offers advanced tracking features, but its use must comply with local laws.
Such software is generally legal only if used with the consent of the device owner.
e. Social Engineering
In some cases, private investigators might rely on social engineering techniques to gain access to location data. For example, they might trick the target into sharing their location via a deceptive message or link. While this is less common among reputable PIs, it highlights the importance of staying vigilant against such tactics.
3. Advanced Tracking Methods
a. IMEI and SIM Tracking
Every mobile device has a unique International Mobile Equipment Identity (IMEI) number. Similarly, SIM cards have unique identifiers that can be traced through the network. Private investigators may use IMEI or SIM tracking to locate a device if they have access to the necessary records or tools.
b. Stingray Devices
A Stingray is a portable device that mimics a cell tower, tricking nearby phones into connecting to it. Law enforcement agencies commonly use this technology, but private investigators typically avoid it due to its invasive nature and legal restrictions.
c. Geofencing
Geofencing creates a virtual perimeter around a specific area. If a device enters or exits this area, it triggers an alert. This technique can be used with GPS or mobile app tracking and is often employed in cases involving surveillance or asset protection.
4. Legal and Ethical Considerations
Tracking cell phones is a highly regulated activity due to privacy concerns. Private investigators must adhere to strict legal and ethical guidelines to avoid violating rights or committing crimes.
a. Consent
In most jurisdictions, private investigators can track a cell phone only with the consent of the device owner. For example, a parent might authorize tracking of their child’s phone, or an employer might monitor company-owned devices used by employees.
b. Privacy Laws
Privacy laws vary by country and region but generally prohibit unauthorized tracking. In the United States, the Electronic Communications Privacy Act (ECPA) regulates the interception of electronic communications, including location data. Similarly, the General Data Protection Regulation (GDPR) in the EU sets strict rules on personal data collection.
c. Ethical Practices
Reputable private investigators follow ethical practices to maintain professionalism and protect client interests. This includes:
Avoiding illegal tracking methods.
Respecting the privacy of non-consenting individuals.
Providing clear disclosures about the methods used.
Unethical practices, such as installing spyware without consent, can lead to legal repercussions and damage the investigator’s reputation.
5. The Role of Technology
Technology plays a central role in cell phone tracking. From software solutions to hardware tools, PIs have access to a wide range of resources that make their work more efficient. Some commonly used technologies include:
Tracking Apps: As mentioned earlier, these apps offer location-sharing features for authorized users.
Surveillance Tools: Tools like GPS trackers or geofencing systems allow investigators to monitor movement discreetly.
Data Analysis Software: PIs often use software to analyze call records, SMS logs, or app usage patterns, which can provide indirect clues about a person’s location.
6. Challenges in Cell Phone Tracking
Despite advancements, cell phone tracking comes with its challenges:
a. Legal Barriers
Obtaining location data without proper authorization can lead to legal consequences, limiting the methods available to private investigators.
b. Technological Limitations
Signal Interference: GPS tracking may not work in areas with poor satellite coverage, such as tunnels or densely packed buildings.
Device Security: Modern smartphones are equipped with advanced security features that prevent unauthorized access to location data.
c. Ethical Dilemmas
Balancing client demands with ethical considerations can be tricky. Investigators must ensure they don’t overstep boundaries while fulfilling their obligations.
7. Real-World Applications
Private investigators use cell phone tracking in various scenarios:
a. Missing Persons
Cell phone location data can provide vital clues in locating missing individuals, especially in time-sensitive cases.
b. Infidelity Investigations
PIs often track cell phones to gather evidence of infidelity. For example, GPS data might reveal that a spouse visited a suspicious location.
c. Corporate Investigations
In cases of corporate fraud or espionage, tracking company-owned devices can help identify rogue employees or uncover unauthorized activities.
d. Stalking and Harassment Cases
Cell phone tracking can help victims of stalking or harassment by identifying the perpetrator’s movements and providing evidence for legal action.
8. How to Protect Yourself from Unwanted Tracking
While private investigators are bound by legal and ethical guidelines, not everyone operates within the law. To protect yourself from unauthorized tracking:
Disable Location Services: Turn off GPS and location-sharing features when not needed.
Secure Your Device: Use strong passwords, enable two-factor authentication, and regularly update your phone’s software.
Avoid Suspicious Links: Be cautious about clicking on unknown links or downloading apps from unverified sources.
Use Anti-Spyware Apps: These can detect and remove tracking software from your device.
9. Conclusion
Private investigators play an essential role in uncovering the truth, and cell phone tracking is one of the many tools they use to achieve their goals. However, this practice requires a delicate balance of skill, technology, and adherence to legal and ethical standards.
For individuals and organizations seeking the services of a PI, it’s crucial to ensure they work with professionals who operate transparently and within the law. At the same time, understanding the methods and limitations of cell phone tracking can help protect your privacy and make informed decisions when hiring an investigator.
By staying informed about the capabilities and boundaries of cell phone tracking, you can better navigate the complexities of this modern investigative tool.
#private investigator#finding a hacker#spy phone#phone hacking tools#phone hacking service#phone hacking
1 note
·
View note
Text
“Two of Fleet Street’s biggest news organisations carried on using unlawful methods—including the hacking of voicemail—for at least five years after they claimed to have stopped, according to evidence disclosed in court.”
2 notes
·
View notes
Text
Judge rules 15 of the 33 articles were obtained by Unlawful Information Gathering by Mirror Group Newspapers from 2006 to 2011. He’s awarded £140,600 in damages.
#i'm aware i'm basically never here anymore sorry about that#but a win for h today ig#prince harry#duke of sussex#phone hacking#this is and always will be bigger than harry folks
29 notes
·
View notes
Text


Charles Spencer calling out Amanda Platell was not on my bingo card today
#prince harry#the duke of sussex#duke of sussex#brf#british royals#the british monarchy#british tabloids#british royal family#uk royals#uk royal family#uk tabloids#phone hacking#harry and meghan#charles spencer#princess diana#diana spencer#toxic media
69 notes
·
View notes
Link
Lessons in British libel law:
Grant had said he had wanted to fight the case and go to trial, where the Sun’s top executives could be called to give evidence. But he has concluded he cannot afford to turn down the payout from the Rupert Murdoch-owned newspaper, which he will be donating to press regulation charities.
This is because of a quirk in the way the English legal system encourages both sides to settle cases before trial or risk financial oblivion owing to the legal costs involved.
It all hinges on a technical piece of civil law procedure known as a “Part 36 offer”.
The Sun has used this provision to offer Grant what he has called an “enormous” amount of money to settle the case. The actor’s lawyers have advised him that this is more money than he is likely to be awarded in damages by a judge after a trial, even if his case were completely successful.
As a result, under the Part 36 rules, even if he were victorious at trial, Grant could find himself having to pay the enormous legal costs for both sides.
As Grant wrote on X: “If I proceed to trial and the court awards me damages that are even a penny less than the settlement offer, I would have to pay the legal costs of both sides.”
This is because, in the eyes of the court, he would have wasted everyone’s time by fighting the case when he could have accepted more money at a much earlier date.
2 notes
·
View notes
Text
Go Harry!

15 notes
·
View notes
Text
Hugh Grant and Piers Morgan Clash Over Murdoch Connections in Fiery Twitter Exchange
The digital corridors of Twitter have become the battleground for a renewed feud between Hugh Grant and Piers Morgan, two figures who have never shied away from public spats. This latest skirmish, however, delves into the murky waters of media ethics, government influence, and personal history, with Rupert Murdoch at the epicentre of their argument. The spark that lit this particular fire was…
#British politics#Hugh Grant#Leveson Inquiry#media ethics#phone hacking#Piers Morgan#Rupert Murdoch#Twitter
0 notes
Text
Best Phone Tracker Apps to Track Your Partner Phone - 2024
Nowadays phone tracker apps have gained popularity in many ways and is often used for tracking the activities of close ones. If you are planning to track your partner’s phone, then it is highly advisable to use the best phone tracker. They not only give a sense of relief by being able to keep an eye on your partner’s safety but also contribute positively to enhancing trust in relationships. Now, shall we focus on the most prominent phone tracker apps to track your partner’s phone in 2024?

Phone Tracker Apps: A Necessity in 2024
Thanks to the steadily developing technology, the availability of smartphones, and the ability to share information via digital means, tracking applications for phones are needed by many people. From tracking the partner’s location to providing safety to personal security, these apps come with a number of monitoring attributes that can make the connections gratifying. As people are getting more demanding and independent, hence the enforcing the use of phone tracker app may help one to know what his or her partner is up to.
Best Phone Tracker Apps for Tracking Your Partner's Phone
In this context, we would like to present some of the top phone tracker apps permitting to track your partner’s phone. Some of the top-rated apps include: Some of the top-rated apps include:
Mobile Tracker Apps: These apps have features such as GPS tracking, phone call intercept, and message interception.
GPS Tracker Apps: There are tracker apps available in the market that come in handy when it comes to tracking the location of your partner with the help of GPS on their mobile.
Partner Phone Tracker: Bespoke applications developed with the intention of monitoring partner phones discreetly.
If you're looking for a more comprehensive solution, consider using phone monitoring and surveillance apps like
Phone Monitoring Apps: The following are the applications that enable one to spy on your partner’s phone usage such as calls, texts, and history on the phone.
Phone Surveillance Apps: Some of the spying apps are more sophisticated in their functionality, for instance, one can have full access to the target’s device and tap into the feeds from its camera in real-time.
How Phone Tracker Helps You
Having been explained above, using a phone tracker is beneficial in accessing any signs of unfaithfulness in a relationship. Through discreet surveillance, it will be easy to see changed behavior through phone and other gadget movements late at night or calls to unknown people thinking that they are cheating. Such information may be useful in handling any issues, and even in navigating areas of misunderstandings in the relation. Phone trackers enable both parties to be more understanding and documented, and provide a professional ground and approach towards handling shaky scenarios and assuring safety for all the parties.
Why Need Phone Tracker Service
The availability of a good phone tracker also does have a huge value in professional practice, especially when one needs to spy on a cheating partner. Using such a service, a person can spy on his or her partner’s social media usage as well as other activities that take place online. This data may also aid in external observations and confirm the possibility of infidelity that a partner could only guess at through their communication behavior.
Where trust has been breached, the possibility of monitoring a partner’s internet activity becomes a significant avenue towards confirming the truth so that everyone in the relationship can proceed to the next level in a clean manner. This smooth surveillance feature assists individuals who wish to hold their psychological condition and arrive at sound decision on relationship issues without being pressured to make rash decisions.
Key Features of Phone Tracker Apps
Thus, while deciding to monitor your partner’s phone with the help of a phone tracker application, it is necessary to pay attention to such options: Some essential features to consider include: Some essential features to consider include:
GPS Tracking: To do so, the app must provide proper GPS location tracking features to the users.
Call Recording: Self, it would be wise to seek apps that can record calls and play them back.
Messaging Monitoring: Supplement questions to establish if the app is capable of monitoring messages and social media interactions.
Getting Professional Phone Tracker Service
The task of hiring a professional phone tracker service to monitor a cheating partner needs to be approached carefully, especially when it comes to choosing the right people to help with this job, as their work should be based on personal privacy and adherence to facts rather than on manipulation and lies. HackersList is a site that aims at providing people with performers who will be able to spy on their partner’s phone effectively and secretively. Contact With Experts
Through their services, you can monitor communications that your partner has and where he or she is, information that is useful in relationships. However, it is always important not to violate the privacy and legal rights of people in such circumstances, so availing help of a reliable service like HackersList can offer appropriate assistance alongside the proof you may require.
Related: Best Social Media Hacks to Track Partner’s Activity
Ensuring Privacy and Security
However, when you intend on using phone tracker apps to track your partner's phone then you should think twice since the practice comes with said ethical issues besides the invasion of privacy. To ensure privacy and security, follow these tips: To ensure privacy and security, follow these tips:
Communication: Since the use of a phone tracker app is contentious, it is recommended that partners talk to each other about it.
Consent: It’s important that you inform your partner that you want to monitor their phone activities and then gain their permission to do so.
Data Security: Select an excellent app that is attentive to these aspects among its priorities, namely reliability and data encryption.
Conclusion
Thus, the tracking of your partner’s phone through a phone tracker app is very important in 2024. Using the most effective tracking apps for phones, you can always guarantee the well-being of the person you love and, at the same time, the need to trust and be trusted back. As with any technology that facilitates communication between two or more parties, it is crucial to keep it private and secure while at the same time being open so as not to harm the existing and developing relationship between the individuals.
#best phone tracker apps#phone tracker apps#phone tracker#phone hack#phone hacks#phone hacking#phone hacker#hackerslist
0 notes