#mobile tracker tool
Explore tagged Tumblr posts
Text

ONEMONITAR is the all-in-one mobile tracker for real-time GPS tracking, geofencing, and activity monitoring. Perfect for parents, employers, and anyone focused on safety, ONEMONITAR is easy to use, secure, and affordable. Start tracking with peace of mind—visit onemonitar.com today!
#mobile tracker#mobile tracking app#mobile tracking software#mobile tracking application#mobile tracker tool#tracker for mobile
0 notes
Text
Stay Ahead with Reliable GPS Update Services
Tired of outdated routes and incorrect navigation? Upgrade your GPS system today! With our Latest GPS & Maps update services, Improved route accuracy, Seamless navigation. Don't let old maps slow you down—get your GPS updated now.

Stay Ahead with Reliable GPS Update Services
#GPS update services#how to update GPS devices#Garmin map update#Latest GPS & Maps update services#how to renew gps tracker#how to update garmin gps device#how to update tomtom navigation device#how do I udapte my garmin gps device#how can i update my gps for free#can i update my garmin gps for free#how to update gps in mobile#Navigation#garmin gps update maps free#GPS Update#Travel Tools#Accurate Maps
0 notes
Text
Tobii Pro Eye Tracking Tools for Marketing and User Research, India
Authorized Reseller, Dealer & Distributor of Tobii Pro Eye Tracker, Tobii Pro Eye Tracking Glasses and Tobii Pro Eye Tracking Software for Marketing and User Research, Mumbai, India.
Tobii Pro, Eye Tracker, Tobii Pro Eye Tracking Equipments, Eye Tracking Tools, Eye Tracking Tools for Marketing and User Research, Tobii Pro Eye Tracker Reseller, Tobii Pro Eye Tracker Dealer, Tobii Pro Eye Tracker Distributor, Tobii Pro Eye Tracking Glasses, Tobii Pro Eye Tracking Software, Tobii Pro Glasses 3 Eye Tracker, Tobii Pro Nano Eye Tracker, Tobii Pro Fusion Eye Tracker, Tobii Pro Spectrum Eye Tracker Hardware, Tobii Pro Lab Software, MTA Eye Tracker, Mobile Testing Accessory, Reseller, Dealer, Distributor, Mumbai, India.
#Tobii Pro#Eye Tracker#Tobii Pro Eye Tracking Equipments#Eye Tracking Tools#Eye Tracking Tools for Marketing and User Research#Tobii Pro Eye Tracker Reseller#Tobii Pro Eye Tracker Dealer#Tobii Pro Eye Tracker Distributor#Tobii Pro Eye Tracking Glasses#Tobii Pro Eye Tracking Software#Tobii Pro Glasses 3 Eye Tracker#Tobii Pro Nano Eye Tracker#Tobii Pro Fusion Eye Tracker#Tobii Pro Spectrum Eye Tracker Hardware#Tobii Pro Lab Software#MTA Eye Tracker#Mobile Testing Accessory#Reseller#Dealer#Distributor#Mumbai#India
0 notes
Text
How Can I Improve My Diet with Technology?
In today’s fast-paced world, maintaining a healthy diet can be challenging. However, technology has made it easier than ever to manage and improve our eating habits. From smart appliances to mobile apps, there are numerous tools available to help you achieve your dietary goals. According to a recent study, 75% of people who used diet-tracking apps reported improved eating habits within three…
#Apple Watch#calorie tracking#diet#diet apps#diet improvement#diet technology#diet tips#dietary goals#dietary tools#digital health#Fitbit#fitness technology#fitness trackers#food apps#food technology#food tracking#Fooducate#Garmin#health apps#health monitoring#health tech#healthy choices#Healthy Eating#healthy habits#healthy tech#kitchen gadgets#meal planning#Meal Prep#Mealime#mobile apps
0 notes
Text
here's a list of mozilla add-ons for all of you tumblrinas out there to have a better internet experience
also, if you like my post, please reblog it. Tumblr hates links but i had to put them so you adhd bitches actually download them <3 i know because i am also adhd bitches
BASIC STUFF:
AdGuard AdBlocker / uBlock Origin : adguard is a basic adblock and with origin you can also block any other element you want. for example i got rid of the shop menu on tumblr

Privacy Badger : this add on will block trackers. if an element contains a tracker it will give you the option to use it or not
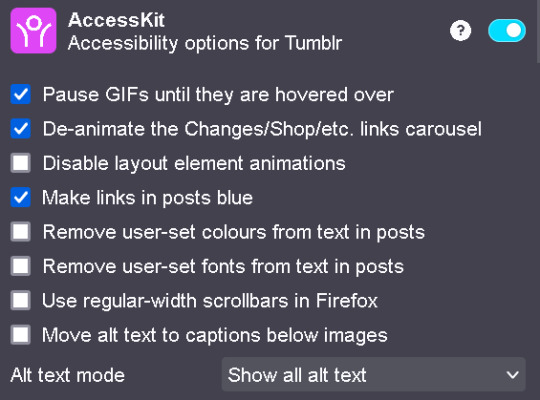
Shinigami Eyes: this will highlight transphobic and trans friendly users and sites using different colors by using a moderated database. perfect to avoid terfs on any social media. i will explain how to use this and other add-ons on android as well under the read more cut
THINGS YOU TUMBLINAS WANT:
Xkit: the best tumblr related add on. with many customizable options, xkit not only enhances your experience from a visual standpoint, but provides some much needed accessibility tools

bonus: if you are into tf2 and wanna be a cool cat, you can also get the old version to add cool reblog icons

AO3 enhancer: some basic enhancements including reading time and the ability to block authors and tags
YOUTUBE
Return of the YouTube Dislike : pretty self explanatory
Youtube non-stop: gets rid of the annoying "Video paused. Continue watching?" popup when you have a video in the background
SponsorBlock: gives you options to skip either automatically or manually sponsors, videoclip non music sectors and discloses other type of sponsorships/paid partnerships
Enhancer for YouTube: adds some useful options such as custom play speed, let's you play videos in a window and most important of all, it allows you to make the youtube interface as ugly as your heart desires. I can't show a full image of what it looks like because i've been told its eye strainy and i want this post to be accessible but look at this <3

PocketTube: allows you to organize your subscriptions into groups
YouTube Comment Search: what it says
FINDING STUFF
WayBack Machine: you probably know about this site and definitely should get the add on. this allows you to save pages and access older versions with the click of a button. while you can search wayback using web archives, please get this one as well as it allows you to easily save pages and contribute to the archive.
Web Archives: it allows you to search through multiple archives and search engines including WayBack Machine, Google, Yandex and more.
Search by Image: allows you to reverse image search using multiple search engines (in my experience yandex tends to yield the best results)
Image Search Options: similar to the last one
this next section is pretty niche but... STEAM AND STEAM TRADING
SteamDB: adds some interesting and useful statistics
Augmented Steam: useful info specially for browsing and buying games
TF2 Trade Helper: an absolute godsend, lets you add items in bundles, keeps track of your keys and metal and your recent trades, displays links to the backpack tf page next to users profiles and more. look it tells me how much moneys i have and adds metal to trades without clicking one by one oh may god

IN CONCLUSION: oooooh you want to change to firefox so badly, you want to delete chrome and all the chrome clones that are actually just spyware and use firefox
HOW TO USE MOZILLA ADD-ONS ON YOUR PHONE
if you already use firefox on android, you'll know there are certain add-ons compatible with the app, some of them even being made just for the mobile version such as Video Background Play FIx. while most of them are pretty useful, some more specific ones aren't available on this version of the browser, but there's a way of getting some of them to work
you need to download the firefox nightly app, which is basically the same as the regular firefox browser but with the ability of activating developer mode. you can find how to do that here. once you've enabled it, you need to create a collection with all the add ons you want. i wouldn't recommend adding extensions if the creators haven't talked about phone compatibility, but XKit and Shinigami Eyes should work
also, don't tell the government this secret skater move, but you can try using both the regular firefox browser and nightly so you can have youtube videos in a floating box while you browse social media.
see? i can block this terf while Rick Rolling the people following this tutorial. isn't that tubular?
#zezo talks#firefox#internet safety#accessibility#id in alt text#this will get tagged as tf2 because mine heart desires and its mentioned like twice#tf2#long post#but it's worth it i promise#tumblr
3K notes
·
View notes
Note
https://www.tumblr.com/olderthannetfic/766611758459879424/youtube-just-showed-me-the-most-dumb-video-essay?source=share
Youtube fed you that swill and you actually watched it? And then you read the comments?? That's why the algorithm is like this. Feeding people hateful garbage makes them stick around.
Log out (If you very much like features that are only available logged in, just make a second google account to use for youtube and nothing else)
Download Firefox https://www.mozilla.org/en-US/firefox/windows/
Go into the privacy settings and set Enhanced Tracking Protection to "strict"
Install an adblocker, I like ublock origin https://ublockorigin.com/
Optionally, install some more anti-track addons, like Privacy Badger or Duckduckgo's privacy essentials
Install the container addon and set one up to qurantine youtube away from everything else https://addons.mozilla.org/en-US/firefox/addon/multi-account-containers/
Now what you have is a box that has youtube in it and literally nothing else. No ads, no personal information, no creepy stalkerware, no ability for other websites to see in the box, or for youtube to see out of it.
And now the fun part. Use the adblocker to nuke the entire sidebar and endcard overlays. Just select these with the eyedropper from the adblock extension, preview it to make sure you're not blocking more than you mean to, and bam, it's like three clicks and and you'll never see it again, it's beautiful.
Do this and you can watch all the videos you please and will NEVER have the algorithm shove some misogynistic garbage in your face because it crunched some math and knows that users with your profile are stasticsally likely to spend time on the side when served that sort of trash.
You can also use the adblocker to get rid of the entire comments section, or to nuke any design element or feature that you find annoying or ugly. It's called an adblocker, but it blocks anything based on URLs and HTML strings. The posibilites are endless, freeing, and beautiful. I use adblockers for aesthetics and accesibility at least as much as for actual ads.
I do this with every website I use regularily, including tumblr (though only the worst few [including youtube] have dedicated quarantine containers). It's a few steps to set up, but once you have the extensions installed and know how to use them, nuking algorithmic feeds and making sure that you only see what you actually want to see takes like ten seconds.
And no, before you say you have to use the app, this does work on mobile. Download Firefox for mobile, install the adblocker, install the anti-trackers, and use youtube in the browser instead of the app because taking an extra three seconds to load and having a slightly less optimized layout is worth not being unundated with advertisements and hate.
You can also root your phone and install adblockers that work with apps, but that's a more involved process and takes more effort and knowledge than simply installing a new browser and using an eyedropper tool to select a sidebar.
--
73 notes
·
View notes
Text
Stop! Have you checked your phone’s ad privacy settings recently? No? Here’s a guide. It’s from 2022 but I can confirm that as of November 2024 the Apple stuff is still correct.
Android:
Settings —> Privacy —> ads —> delete advertising ID
On older versions you might not be able to delete the ID, but can reset it and there should still be a toggle to opt out: do both of those things!
iOS:
Two things to take care of, here. One) Apple already makes each app ask permission, but you can still tell it to just not even let them ask:
Settings —> privacy —> Tracking —> toggle off ‘allow apps to request to track’.
Two) settings —> privacy —> scroll riiiiiight down —> Apple advertising —> toggle off personalised ads.
Samsung:
Settings —> privacy —> Customisation services —> ‘stop customising all devices’
Xiaomi:
Settings —> passwords and security —> Authorisation & revocation —> toggle off ‘MSA’
Why it Matters
‘The ad identifier is a string of letters and numbers that uniquely identifies your phone, tablet, or other smart device. It exists for one purpose: to help companies track you.
Third-party trackers collect data via the apps on your device. The ad ID lets them link data from different sources to one identity you. In addition, since every app and tracker sees the same ID, it lets data brokers compare notes about you. Broker A can buy data from broker B, then use the ad identifier to link those two datasets together. Simply, the ad ID is the key that enables a whole range of privacy harms: invasive 3rd-party profiling by Facebook and Google, pseudoscientific psychographic targeting by political consultants like Cambridge Analytica, and location tracking by the U.S. military.
Sometimes, participants in the data pipeline will argue that the ad ID is anonymous or pseudo-anonymous, not “personally identifying” information, and imply that it does not pose a serious privacy threat. This is not true in practice. First, the ad ID is commonly used to help collect data that is obviously personally identifiable, like granular location data. If you can see where a person works, sleeps, studies, socializes, worships, and seeks medical care, you don’t need their email address to help identify them. And second, an entire industry exists to help trackers link ad IDs to more directly identifying information, like email addresses and phone numbers. In a vacuum, the ad ID may be anonymous, but in the context of the tracking industry, it is a ubiquitous and effective identifier.
Disabling this ID makes it substantially harder for most advertisers and data brokers to track you. These industries process data from millions or billions of users every day, and they rely on convenient technologies like the ad ID to make that kind of scale possible. Removing this tool from their toolbox will result in substantially less data that can be associated with you in the wild. It is not only beneficial to your privacy, it also makes the surveillance advertising industry less profitable.‘
9 notes
·
View notes
Note
okay so, ever since I've first read about Lucas I loved him but there's just one question I can't get out of my head: Lucas is very much against any sort of new tech so he'd ban it all from the house but what about any sort or styling things? Like a flat iron? I'd look a mess without it. Would he get me one? Probably only if I'm very well behaved, I bet. Or is it something he wouldn't even consider buying me?
Honestly; yes, if you've been well-behaved he'd probably get a straightener or a flat iron for you, but it's going to be low-tech, probably not overly expensive or with all kinds of fancy tools. You want it to do one thing, he's getting one that does one thing.
He hasn't entirely gone off the idea of new technology - he's using a television, after all! - but the whole idea of a technology that connects you too much to the world . . . Things like the internet and mobile phones and trackers? Those freak him out.
If you make a good enough case for it, if you've been sweet and well-behaved and such, he might even get you an old handheld games console or something. It's mostly the connectivity thing that he absolutely cannot be having.
He is reassuring you that you're beautiful exactly the way you are and have no need at all for the flat iron, though. Making an extra effort to twirl your hair around his fingers and kiss the top of your head. Fussing about your appearance has actually endeared you to him, just a bit: if you didn't like him back, why would you care about how you looked?
6 notes
·
View notes
Note
I'm desperately trying to remember an rpg that focused on living with chronic pain and migraines - do you know any that fit the bill?
THEME: Chronic Pain, Migraines, Disability
Hello friend, I was able to find a few! Some of these games focus on chronic pain or migraines specifically, while others are expanded to talk about a broader range of disability or illness. A few aren’t full games, but rather supplements that can be integrated into more generic rulesets.







Chronic Migraines for 5e, by Cat Elm.
Chronic Migraine Mechanics For 5e is a set of rules and guidance to enable player characters to experience chronic migraines, which additional feats related to migraine experience and rules on deciding migraine occurrence and suggested side effects.
Designed to allow players to explore real-world disability and experiences in a safe, controlled environment, Chronic Migraine Mechanics For 5E gives players and DMs to the tools to expand their in-game options and representation.
This is a supplement for D&D 5e, not a game in and of itself. If you are looking for ways to express disability in a game that you’ve already established, this supplement might be worth looking into.
You’re Sick (And it’s your fault), by David Moskowitz.
Were they a smoker? Not wear sunscreen? Eat a lot of red meat?
Did they have unprotected sex? Share needles?
Who were they with? How long have they had that cough? Who might have they infected?
This is a solo-journaling game that’s an exploration of guilt and internalized stigma related to illness, with cancer, AIDS, and tuberculosis as the foundational afflictions informing the game.
Designed after the Wretched & Alone engine, this is a solo-ttrpg that is designed to be realistic. Living with illness is heavily stigmatized, and this game guides you, the player, through the physical and emotional toll that this stigma places upon you. Victory in this game means not that you will be “cured”, but rather, that you have the tools you need to make life liveable.
This game doesn’t focus on chronic pain specifically, but much of the prompts in the oracle seem to experience some overlap, such as having better days and worse days, irritating conversations with folks who don’t understand, and the way your situation drains you of money and time. If you’re looking for a solo experience that explores different facets of living with an illness that might not kill you, but won’t let up either, this might be worth checking out.
I AM FUCKING TIRED, by Tia Let | Hydromer
I AM FUCKING TIRED is a one-page solo journaling game about having an undiagnosed fatigue condition and trying to manage your day-to-day.
Even when your day-to-day might not be as certain as you think.
You have a body that loses it’s energy quite quickly; you have a condition that constantly drains you, but has no official diagnosis. Doing your day-to-day at home is difficult, but you do your best. Today is another day.
A simple game with a few rules, I AM FUCKING TIRED is a solo journaling game so grab a pen and paper. You roll a d20 to see what memory comes to mind, and write about it. If you roll the same number as a previous roll, the Memory Twists - you remembered it falsely, had insufficient information, or someone lied to you. Finally, you also have an Energy tracker. During a Twist, you roll against that energy to see if you can continue.
This game is free, and emphasizes self care before and after play. While this is about undiagnosed fatigue, I would not be surprised if much of the experiences of folks with chronic pain overlap with some of the events that appear in this game.
We Are Still Here, by Ennis Rook Bashe.
use a cane or a walker or braces. stab people. take meds. exist. survive.
we are still here.
This is a way to incorporate disability into Apocalypse World, and might work as inspiration for other PbtA games about how to include disability or illness.
You can include a mobility aid that gives you both benefits and drawbacks - such as doubling as a weapon, or requiring frequent repairs. Alternatively or additionally, you can include medication, which provides benefits such as helping you concentrate or focus, while also threatening your well-being if you run out of stock, need a special storage environment, or have difficulties with your supplier.
This is a perfect add-on for players who desire more representation of disabled folks surviving (and thriving) in post-apocalyptic fiction.
Pieces of Me, by Mothworks.
You are young and newly disabled. Try your best to learn your limits, find new ways of doing things, and rest as you can as you tear and repair your character sheet.
Pieces of Me uses an index card, a pen, tape, and ten coins. Your character sheet (index card) will contain a number of boxes to indicate your ability to complete certain tasks. Whenever you push yourself to accomplish a task, you must flip your coins to see how many heads you get. Not enough heads? You have to rip off a piece of your sheet. Too few heads and you destroy a piece of your character sheet forever.
Torn pieces of the sheet can be taped back on or redrawn, and fresh scraps of paper represent new aids or methods of doing things. At the end of the game, you will have a memento of your game experience.
This game has a standard and a dyslexic-friendly font. If you’re looking for a personal game with a tactile experience, this might be a game for you.
Inkeeryn’s irritating insidious incurringible incessant illness, by cosmicbeagle.
Inkeeryn's Irritating Insidious Incorrigible Incessant Illness is a storytelling duet that uses a six-sided die and a deck of standard playing cards. One player plays someone who is afflicted or cursed or hexed, and the other plays the affliction itself. Over the course of four rounds -- representing stages of life -- you take turns narrating about the afflicted person and the curse that torments them.
The exact nature of the affliction -- its effects, symptoms, and expressions -- are determined by you. You describe how the curse affects the character, and how the character treats, copes with, and maybe even transcends it.
This game gives you the freedom to decide how exactly your illness manifests, as well as the power to decide how your character responds to that illness. As a duet game, this provides for an intimate, personal experience, good for exploring a topic that can weigh heavily on many folks.
Microservice, by Ponder Games.
You are a human going shopping with your service dog.
Microservice is a single-page tabletop roleplaying game. It is intended for solo play, or for play with 1 player and 1 GM.
This is a salty, tongue-in-cheek commentary on what it is like to navigate North America with a service dog, complete with a roll table of unhelpful NPCs that almost certainly drain your energy. You have the ability to play this solo, or with one other person, so it’s best for a quick little game with one other person, most likely someone that you’re comfortable gaming with.
172 notes
·
View notes
Note
what's the deal with firefox
Boy howdy, am I glad you asked! I'll be comparing Firefox to Chrome and Edge.
Firefox uses fewer resources than Chrome or Edge, meaning that your browser and other apps will run faster and your battery will last longer on mobile/laptop.
Firefox is privacy-focused, meaning the browser doesn't gather data unless you opt into it, and by default it blocks third-party cookies, trackers, and other things that track you across the web. You can choose between standard, strict, and custom blocking, plus install privacy tools from the add-on store. This will protect your personal data and help websites load more quickly.
Speaking of ad blocking, Firefox supports ad-blocking extensions on Android devices, unlike the other Big 3 browsers. I don't even use the YouTube app on my phone anymore because if I watch via Firefox, I get no ads. I can actually read articles on news sites without being spammed by ads! It's amazing!
Firefox has equivalent add-ons for almost all Chrome extensions, so you won't lose functionality when you switch.
Firefox accounts allow you to sync across devices, just like Google accounts allow Chrome settings to sync, so moving from desktop to mobile or vice versa is very simple.
The Mozilla Foundation, Firefox's parent company, is a non-profit which advocates for online transparency and users' rights to keep the internet usable for everyone.
Firefox is free, open source, and non-proprietary, and allows you to opt out of all sponsored content, unlike Chrome or Edge.
Firefox does not tie you down to a particular product or corporation, such as Microsoft or Apple. It works on any platform.
Cutest mascot by far.

#i should make an infographic about this#or find one that an actual designer made lol#firefox#answers.txt
30 notes
·
View notes
Text
ONEMONITAR Spy Phone Tracker

Gain a competitive edge in surveillance with ONEMONITAR's advanced spy phone tracker. By harnessing the power of cutting-edge technology, ONEMONITAR allows you to monitor real-time GPS locations, call logs, and multimedia files remotely, giving you unparalleled visibility into your target's activities. Whether you're tracking a loved one's whereabouts or monitoring employee productivity, ONEMONITAR provides the precision and reliability you need to achieve your objectives. With its intuitive interface and robust performance, ONEMONITAR is the ultimate solution for anyone seeking to enhance security and streamline surveillance efforts.
Start Monitoring Today!
#Phone spy software#Cell phone spy app#Spy phone tracker#Mobile phone spy tool#Phone spyware detection#Hidden phone spy#Remote phone spy#Undetectable phone spy#Stealth phone spy#Phone spy monitoring
0 notes
Text
GPS update services for accurate navigation
Avoid getting lost, learn how to update GPS devices and keep your GPS Up-to-Date visit our official website to schedule regular updates for seamless navigation.
#GPS update services#how to update GPS devices#Garmin map update#Latest GPS & Maps update services#how to renew gps tracker#how to update garmin gps device#how to update tomtom navigation device#how do I udapte my garmin gps device#how can i update my gps for free#can i update my garmin gps for free#how to update gps in mobile#Navigation#garmin gps update maps free#GPS Update#Travel Tools#Accurate Maps
0 notes
Text
We should ban TikTok('s surveillance)

With the RESTRICT Act, Congress is proposing to continue Trump’s war on Tiktok, enacting a US ban on the Chinese-owned service. How will they do this? Congress isn’t clear. In practice, banning stuff on the internet is hard, especially if you don’t have a national firewall:
https://doctorow.medium.com/theyre-still-trying-to-ban-cryptography-33aa668dc602
If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/03/30/tik-tok-tow/#good-politics-for-electoral-victories
My guess is that they’re thinking of ordering the mobile duopoly of Google and Apple to nuke the Tiktok app from their app stores. That’s how they do it in China, after all: when China wanted to ban VPNs and other privacy tools, they just ordered Apple to remove them from the App Store, and Apple rolled over:
https://pluralistic.net/2022/11/11/foreseeable-consequences/#airdropped
That’s the completely foreseeable consequence of arrogating the power to decide which software every mobile user on earth is entitled to use — as Google and Apple have done. Once you put that gun on the mantelpiece in Act I, you damn betcha that some strong-man backed by a powerful state is going to come along and shoot it by Act III.
The same goes for commercial surveillance: once you collect massive, nonconsensual dossiers on every technology user alive, you don’t get to act surprised when cops and spies show up and order your company to serve as deputies for a massive, off-the-books warrantless surveillance project.
Hell, a cynic might even say that commercial surveillance companies are betting on this. The surveillance public-private partnership is a vicious cycle: corporations let cops and spies plunder our data; then the cops and spies lobby against privacy laws that would prevent these corporations from spying on us:
https://pluralistic.net/2023/01/25/nationalize-moderna/#hun-sen
Which makes the RESTRICT Act an especially foolish project. If the Chinese state wants to procure data on Americans, it need not convince us to install Tiktok. It can simply plunk down a credit card with any of the many unregulated data-brokers who feed the American tech giants the dossiers that the NSA and local cops rely on.
Every American tech giant is at least as bad for privacy as Tiktok is — yes, even Apple. Sure, Apple lets its users block Facebook spying with a single tap — but even if you opt out of “tracking,” Apple still secretly gathers exactly the same kinds of data as Facebook, and uses it to power its own ad product:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
There is no such thing as a privacy-respecting tech giant. Long before Apple plastered our cities with lying billboards proclaiming its reverence for privacy, Microsoft positioned itself as the non-spying alternative to Google, which would be great, except Microsoft spies on hundreds of millions of people and sells the data:
https://pluralistic.net/2020/11/25/the-peoples-amazon/#clippys-revenge
Tech’s surveillance addiction means that Tiktok’s own alternative to the RESTRICT Act is also unbelievably stupid. The company has proposed to put itself under Oracle’s supervision, letting Oracle host its data and audit its code. You know, Oracle, the company that built the Great Firewall of China 1.0:
https://www.eff.org/deeplinks/2010/01/selling-china-surveillance
We should not trust Tiktok any more than we trust Apple, Facebook, Google or Microsoft. Tiktok lied about whether it was sending data to China before:
https://www.buzzfeednews.com/article/emilybakerwhite/tiktok-tapes-us-user-data-china-bytedance-access
And even if it keeps its promise not to send user data to China, that promise is meaningless — it can still send the vectors and models it creates with that data to China — these being far more useful for things like disinformation campaigns and population-scale inferences than the mere logs from your Tiktok sessions.
There are so many potentially harmful ways to process commercial surveillance data that trying to enumerate all the things that a corporation is allowed to do with the data it extracts from us is a fool’s errand. Instead, we should ban companies from spying on us, whether they are Chinese or American.
Corporations are remorseless, paperclip-maximizing colony organisms that perceive us as inconvenient gut-flora, and they lack any executive function (as do their “executives”), and they cannot self-regulate. To keep corporations from harming us, we must make it illegal for them to enact harm, and punish them when they break the law:
https://doctorow.medium.com/small-government-fd5870a9462e
After all, the problem with Tiktok isn’t the delightful videos or the fact that it’s teaching a generation of children to be expert sound- and video-editors. The problem with Tiktok is that it spies on us. Just like the problem with Facebook isn’t that it lets us communicate with our friends, and the problem with Google isn’t that it operates a search engine.
Now, these companies will tell you that the two can’t be separated, that a bearded prophet came down off a mountain with two stone tablets, intoning, “Larry, Sergey, thou shalt stop rotating thine logfiles and, lo, thou wilt data-mine them for actionable market intelligence.” But it’s nonsense. Google ran for years without surveillance. Facebook billed itself as the privacy-forward alternative to Myspace and promised never to spy on us:
https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3247362
The inevitabilist narrative that says that corporations must violate our rights in order to make the products we love is unadulterated Mr Gotcha nonsense: “Yet you participate in society. Curious. I am very intelligent”:
https://thenib.com/mister-gotcha/
Of course, corporations push this narrative all the time, which is why American Big Tech has been quietly supporting a ban on Tiktok, which (coincidentally) has managed to gain a foothold in the otherwise impregnable, decaying, enshittified oligarchy that US companies have created.
They have conspicuously failed to call for any kind of working solution, like a federal privacy law that would ban commercial surveillance, and extend a “private right of action,” so people could sue tech giants and data-brokers who violated the law, without having to convince a regulator, DA or Attorney General to bestir themselves:
https://www.eff.org/deeplinks/2019/01/you-should-have-right-sue-companies-violate-your-privacy
Instead, the tech giants have the incredible gall to characterize themselves as the defenders of our privacy — at least, so long as the Chinese government is the adversary, and so long as its privacy violations come via an app, and not buy handing a credit card to the data-brokers that are the soil bacteria that keeps Big Tech’s ecosystem circulating. In the upside-down land of Big Tech lobbying, privacy is a benefit of monopoly — not something we have to smash monopolies to attain:
https://www.eff.org/wp/interoperability-and-privacy
Not everyone in Congress is onboard with the RESTRICT Act. AOC has come out for a federal privacy law that applies to all companies, rather than a ban on an app that tens of millions of young Americans love:
https://www.businessinsider.com/aoc-first-tiktok-congress-ban-without-being-clued-in-2023-3
You know who agrees with AOC? Rand Paul. Yes, that absolute piece of shit. Paul told his caucusmates in the GOP that banning an app that millions of young American voters love is bad electoral politics. This fact is so obvious that even Rand fucking Paul can understand it:
https://gizmodo.com/rand-paul-opposes-tiktok-ban-warns-republicans-1850278167
Paul is absolutely right to call a Tiktok ban a “national strategy to permanently lose elections for a generation.” The Democrats should listen to him, because the GOP won’t. As between the two parties, the GOP is far more in thrall to the Chamber of Commerce and the rest of the business lobby. They are never going to back a policy that’s as good for the people and as bad for big business as a federal privacy law.
The Democrats have the opportunity to position themselves as “the party that wants to keep Tiktok but force it to stop being creepy, along with all the other tech companies,” while the GOP positions itself as “the party of angry technophobes who want to make sure that any fun you have is closely monitored by Mark Zuckerberg, Sundar Pinchai and Tim Cook and their pale imitations of the things you love about Tiktok.”
That’s not just good electoral politics — it’s good policy. Young voters aren’t going to turn out to the polls for performative Cold War 2.0 nonsense, but they will be pissed as hell at whoever takes away their Tiktok.
And if you do care about Cold War 2.0, then you should be banning surveillance, not Tiktok; the Chinese government has plenty of US dollars at its disposal to spend in America’s freewheeling, unregulated data markets — as do criminals, petty and organized, and every other nation-state adversary of the USA.
The RESTRICT Act is a garbage law straight out of the Clinton era, a kind of King Canute decree that goes so far as to potentially prohibit the use of VPNs to circumvent its provisions. America doesn’t need a Great Firewall to keep itself safe from tech spying — it needs a privacy law.
Have you ever wanted to say thank you for these posts? Here’s how you can: I’m kickstarting the audiobook for my next novel, a post-cyberpunk anti-finance finance thriller about Silicon Valley scams called Red Team Blues. Amazon’s Audible refuses to carry my audiobooks because they’re DRM free, but crowdfunding makes them possible.
Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
[Image ID: A modified vintage editorial cartoon. Uncle Sam peeks out over a 'frowning battlement' whose cannon-slots are filled with telescopes from which peer the red glaring eyes of HAL 9000 from '2001: A Space Odyssey.' Topping the battlements in a row are Uncle Sam and three business-suited figures with dollar-sign-bags for heads. The three dollar-bag men have corporate logos on their breasts: Facebook, Google, Apple. Standing on the strand below the battlements, peering up, is a forlorn figure with a Tiktok logo for a head. The fortress wall bears the words 'RESTRICT Act.']
#rand paul is right actually ugh ugh ugh#politics#oracle#restrict act#privacy#privacy without monopoly#tiktok#commercial surveillance#trade war#bytedance#apple#google#facebook#meta#usausausa#generational warfare#electoral strategy#pluralistic#aoc
117 notes
·
View notes
Text
Tales of Bloody Bug and Chat Noir - Chapter 60 - Bird's Nest
Beginning || Previous || Next
Bloody Bug stood atop the Eiffel Tower as she waited for Chat Noir. Night had fallen and the city had quieted, though was still buzzed in the night light. Unease clawed at her as she looked at the empty sky filled with the wanning full moon. She took several deep breaths as she calmed herself and prepared for the hunt before her. They would find Mayura today. They would put an end to all this.
“You ready?” Chat Noir asked.
Bloody Bug’s breath caught. She turned to look at Chat Noir when her eye caught the black cat ring. It shimmered and shone white with a prismatic gleam in a mesmerizing, fractured light. She turned back to the city and nodded.
“I’m ready. Let’s go,” Bloody Bug said.
Bloody Bug and Chat Noir activated the trackers in their tools. The other heroes were on standby and ready to mobilize while the few scheduled to be out were. They split up and covered different sections of the city. They ran along the rooftops and hopped between them while doing anything to draw eyes to them. Chat Noir twirled and mimicked poses from the shows he watched with Porcelet while Bloody Bug swung around before she skated along the side of buildings and in the streets.
Bloody Bug’s focus was broken by a ping from her yo-yo. She leapt out of the street onto a rooftop. She opened her tool to see Chat Noir deterred off course in pursuit. She sent a signal with her yo-yo before she hurried to join Chat Noir. She watched the lively city fade away to dark neighborhoods and abandoned buildings. She pursed her lips as she stopped to look around for Chat Noir. She eyed the green fluff of his coat on a nearby rooftop. She jumped over to him and knelt.
“What do we have here?” Bloody Bug asked.
“I’m not sure. I saw Mayura, or rather, a shadow of her. I followed and it led me here.”
“Well, let’s wait. We need most the team, if not all before we head in.”
“Perhaps, though we could go in now, couldn’t we? Look around?”
“Cat, this could be a trap if she led you here. She’s likely prepared something for us. And given her mental state, I can’t imagine it’ll be pleasant.”
“But how long before people arrive? How long before Mayura just attacks us out here? We should at least go in to distract, right?”
“Absolutely not. That bitch wanted to skip right to the kill when she found me yesterday. If we step in there without everyone, we’re as good as dead. We aren’t tempting fate.”
Chat Noir grumbled and sat down. Bloody Bug and him watched for their team to arrive. Their team trickled in one by one. Gallic Chick, Outlaw, Porcelet, and Bomb Bee were the first ones to arrive. Bloody Bug filled them in as Badb, Pom Pom, Hydra, and Crimson Tiger showed up. The patrolling heroes, Minotaur, Apollo, and the newest hero, Serow, joined them. The last ones to arrive were Fennec, Ouroboros, and Llameri.
“Alright, looks like everyone is here. Divide into your teams and get into positions,” Bloody Bug instructed.
Everyone nodded and moved. Bomb Bee, Badb, Apollo, and Pom Pom stood with Bloody Bug while Gallic Chick, Porcelet, Llameri, and Serow stood with Chat Noir. Ouroboros found a place to hide with Fennec guarding him. Hydra, Crimson Tiger, Minotaur, and Outlaw patrolled the immediate area.
Bloody Bug and Chat Noir moved into the building with their teams. They busted down the door and surveyed the immediate room. The room was clear of debris, random clutter, and cleared away of spiderwebs and dust expected in abandoned buildings. Various tables with equipment lined the middle of the room with the walls covered in scraps of notes. They all cautiously approached the tables and notes to inspect them.
The instruments on the table were akin to the tools that Eve had laying around her home the second time Bloody Bug and Chat Noir met her. Amongst them was the tool that Mayura had used to liberate Tikki, Plagg, and Fluff from the Order’s tampering. Alchemy and chemistry tools were littered around the space with notes on how to make the serums with different combinations striked out and the right ones circled.
The notes on the wall were a mix. There were ones on fresh, white paper with flawless cursive, while the others were old, yellowed paper written in an old language that looked like Sanskrit. Alongside the old parchment were loosely translated pieces of fragmented information that was all that Eve had left after she was betrayed. Bloody Bug and Apollo skimmed over the notes to find most were research results and several mentions of betrayal.
“I see why Mayura thought there was some sort of ancient wrong now. All this mention of betrayal and no context,” Bloody Bug muttered.
“Indeed. And you told her the truth?” Apollo asked.
“Sure did, but in her mental state, she didn’t believe me.”
Apollo grimaced. “Well, if you don’t mind, I’m going to collect these. They may be useful.”
“Knock yourself out.”
Bloody Bug moved as Apollo gathered notes. She stopped before a large locked door. She destroyed the lock and slid open the door. She froze as she stared in horror seeing Emilie Agreste’s body hung up in chains like a decoration. She staggered back and was caught by Chat Noir. He opened his mouth to ask what was wrong when he looked up and screamed. He turned his back as Porcelet rushed to his side to comfort him. Everyone gathered and gawked at the sight.
Bloody Bug took a deep breath before she ran in and removed Emilie’s body from the chains. She put Emilie down as laughter filled the space. She rushed out and looked around as everyone stood ready. She narrowed her eyes as she eyed Nathalie silhouetted up in the rafters.
“Marvelous, isn’t she? Oh, yes, she is, yes she is,” Nathalie cooed.
“What the hell is wrong with you? Why did you do this?” Chat Noir roared.
“So many plans. So many, so many. All gone, up in flames. Because of you. You stupid cat!” Nathalie hissed.
“Enough of this. Mayura, Nathalie, whatever, let this end. It’s not too late to stop,” Bloody Bug pressed.
“Indeed. You are an incredible mind with research anyone of credibility would go crazy over. You can still abandon this path and pursue other methods,” Apollo added.
“Please, let this end amicability,” Pom Pom begged.
Silence passed for a moment before Nathalie snickered that grew into manic laughter. Everyone cringed away when Nathalie floated down from the rafters. She grinned at them with a manic smile, pained, crazy eyes, and horrid black cracked lines on her skin. Bloody Bug blinked several times as Nathalie’s entire body had a white glow and the fractured prismatic light as a miraculous did.
“Too late. Far too late. Too broken. Far too broken. Tried to save, but only one option. Yes, there was. Yes, there was,” Nathalie cooed.
“You took the final step, didn’t you?” Bloody Bug demanded.
Nathalie snickered. “Had to help my darling brother, yes, I did. Too broken, too lost. Didn’t want to be away, wanted to save him. Oh, the pain, oh the pain, but he was saved. But no need to save him if not for you, wretched cat. You used Father’s power to hurt my brother. You abused his power so much like your wretched father. Like so many others. Like so many others.”
“That’s not true, and you know it. There are many that still treat the kwamis right. There are those that don’t abuse their powers,” Bloody Bug argued.
“And who are you to speak? You’ve done nothing but abuse your powers and hurt people. You are no better than Gabriel or Eve!” Chat Noir yelled.
“Oh. Oh, dear. Have I? I may have. But there’s a remedy for that. A remedy for all. Quick and easy. Fast and simple. Over and done. Good, very good. No time. Out of time,” Nathalie rambled.
“Mayura, please. Whatever you’re thinking, you don’t need to do it,” Bloody Bug attempted.
“That’s where you’re wrong, little Bug. Oh so wrong. Something must be done. Always be done. If no one else will do it, then I shall be the one. Yes, I will. Yes, I will.”
“Nathalie, wait!”
Nathalie’s snickering grew into manic laughter. Her pale skin changed to the light blue it was as Mayura’s, but with the black veins a bright fuchsia. Her sclera black and blood shot with the fuchsia veins. Her pristine hair a ragged mess and her dress ripped and torn. The ombre gloves and boots that faded into her skin receded closer to the wrists and ankles, making more of the veins visible.
“What the hell-?” Bloody Bug breathed.
Mayura laughed. “Clock’s ticking. Tic tok. Tic tok. Death’s a-calling. Do you hear its crow? No time left. Must act now. Must correct all wrongs. Must cleanse all.”
“Cleanse? What do you mean-?”
Mayura unfurled her fan as all the feathers lit up. Pom Pom reached for her ball as Mayura turned the blades to steel and struck Pom Pom across the chest, leaving a large, deep gash. Bloody Bug and Badb screamed out as Mayura was engulfed in dark blue light. Bloody Bug scooped up Pom Pom and grabbed Badb before Badb could use Uproar.
“What are you doing? Let me go!” Badb yelled.
“No! Bitch is already crazy. Don’t make things worse. Go! Retreat! All of you!” Bloody Bug roared.
Bloody Bug threw Pom Pom into Badb’s arms and pushed them towards the exit. Bloody Bug lingered behind with Chat Noir as they watched hideous monsters were born from the light. They shared a worried look before they ran off with the rest of their team. They all retreated several blocks away as the warehouse was destroyed as monsters poured out of it. They all watched in horror as the monsters roared and rampaged. A handful headed for the city while all the others teleported away and Mayura charged forward in Primal form, ignoring heroes.
“Oh fuck! Where did they go?” Minotaur yelled.
“How the fuck are we supposed to know?” Bloody Bug retorted.
“Well, what are supposed to do, oh fearless leaders?”
“I don’t… fuck!”
Chat Noir put a hand on Bloody Bug’s shoulder. “Focus on protecting the people. About three monsters and Mayura headed into the city, putting them in immediate danger. Keep them safe at all costs.”
“What about Mayura?” Bomb Bee asked.
“Leave her to Bug and I. We’ll hand her. Everyone move out!”
Everyone exchanged worried glances before they headed off. Chat Noir took a breath as he looked at Bloody Bug.
“What’s the plan for us if we’re facing crazy?” Bloody Bug demanded.
“Well, I guess, we go primal. Meet her on even footing.”
“Are you insane? Even footing? She’s at the final stage. She consumed her kwami. You saw it too, didn’t you?”
“I… I did.”
“Then what makes you think this will be on even footing? Just because we go primal doesn’t mean we’ll be able to stop her.”
“I know, but we can keep her busy. You saw as well as I did. She’s broken, damaged. And, going off her ramblings, she knows her death is close at hand. If we can keep her busy, she’ll die from the exertion of her powers. Just like the one mentioned in the grimoire.”
“Or, and hear me out, we kill her ourselves.”
Chat Noir’s ears pinned back as he looked away.
“Cat, the longer she’s left alive, the more damage she’s going to cause. If we end her now, we can save more lives that way because this bitch is going for the kill. If we don’t end her, everyone will pay the price. Finish what you started by damaging her miraculous.”
“But-! I didn’t mean to-!”
“Bullshit! I saw you. You went right for that brooch. You brought this onto her. You’ve already condemned her to death by damaging that brooch. Whatever you were thinking, you are far from innocent in this, Cat. Whatever you choose at this point, you are the cause of her death, and the longer we wait, the deaths of many more. So, what will it be?”
“I… I can’t. I just… I can’t. I… I’m sor-.”
“Fuck you’re so naïve, but I can’t fault you for that. Not completely. If you cannot, then allow me. If you cannot carry that burden, allow me to carry this one for you.”
“I-.”
“Don’t say anything. I’ve lived with the fact that, in another life, I erased an entire universe. It was difficult coming to terms with that fact. Something I’ve still not fully accepted, and it still haunts me from time to time, but not the way it did before. If anyone is able to carry this burden, let it be me. What’s one more to the tally?”
Chat Noir grimaced. “Are you sure?”
“No, but we don’t have time to hesitate. We need to act. I’ve made my choice. Will you stand at my side?”
Chat Noir considered and sighed. “Very well. I’ll be there at your side to support you. End this nightmare.”
Bloody Bug nodded. “Then let’s not waste anymore time.”
Patreon || Discord || Ko-Fi
#miraculous ladybug#miraculous#miraculoustalesofladybugandcatnoir#miraculous au#au#alternate universe#fanfiction writer#fanfiction#fanfic#bloody bug au#bloody bug#chat noir#mayura
5 notes
·
View notes
Text
So, I'm on Redfin trying to get a feel for the housing market and what kind of house I might get once I have the money for it, and there's a pop-up that will not close. It's got this little QR code and right next to that is "download the app so you can have new houses at your fingertips!" I think I'm clicking on the X for a minute before it finally disappears.
One thing about the constant push towards "download the app" is just how little control you have over an .exe program on your mobile phone.
You can't block ads, you can't stop trackers, and you can't alter the appearance of the site via the app. You're at the mercy of the company whereas on a desktop, which has similar issues (esp with the monopoly that Microsoft has on non-Apple PCs), a lot of those problems can be at least mitigated or minimized with browser extensions or .exe programs on your desktop.
Twitter, Reddit, YouTube, Tumblr, Instagram, and Facebook are a quagmire of privacy violations, particularly through ads, and their want to push you towards using their less-than-stellar apps says more about how much the companies dislike how much control the user can exert through their choice-of-browser with extensions. Extensions created by people who want a basic user experience and not one controlled by algorithms.
Fandom, formerly Wikia, continues to push the narrative that "we have more mobile users than desktop users!" to justify making the website, already bogged down and redesigned with invasive advertisements in mind, worse and worse.
And they know they can get away with it because, at the moment, it costs money to escape that void and create an Independent Wiki. There is no Paizo-type non-profit platform where people tired of Fandom (dot com)'s shit can migrate away from them, and vibe as a fan-run Wikipedia. (And when there was one, it got consumed by the Fandom monopoly.)
I wouldn't be surprised if the push towards "download the app" was just the start of retiring desktop computers (among consumers) in the same way Video on Demand (digital downloads and purchases), and the practical death of Special Features (BTS Documentaries, and Audio Commentary), has become another tool for minimizing the necessity of physical media like DVDs and CDs.
None of this was at the request of the consumer, but damn if corporations and companies don't want people to accept that as the true narrative.
22 notes
·
View notes
Text
Scannero Phone Tracker: Empowering Personal Security and Connectivity
Scannero Phone Tracker is a cutting-edge mobile application designed to provide users with enhanced security and improved connectivity. With its array of features, this innovative tool offers peace of mind to individuals seeking to safeguard their loved ones and streamline their communication experiences.
Key Features:
Real-Time Location Tracking: Scannero Phone Tracker employs advanced GPS technology to offer real-time location tracking for smartphones. Whether you're keeping an eye on your family members or ensuring the safety of your personal device, this feature lets you pinpoint exact locations instantly.
Geofencing Alerts: Set up virtual boundaries with geofencing alerts. Receive notifications whenever a tracked device enters or exits a designated area. This feature is invaluable for parents, enabling them to monitor their children's movements and safety.
Lost or Stolen Phone Recovery: In the unfortunate event of a lost or stolen phone, Scannero Phone Tracker can assist in locating your device. The app's precise tracking capabilities can aid in the recovery process, minimizing data loss and potential security breaches.
Emergency SOS Button: Prioritize safety with the built-in emergency SOS button. With a single press, users can send out distress signals to pre-selected contacts, sharing their real-time location and ensuring swift assistance during critical situations.
Family Connectivity: Strengthen family bonds with the app's group tracking feature. Stay connected with loved ones by sharing locations and coordinating activities, all while respecting individual privacy preferences.
User-Friendly Interface: Scannero Phone Tracker boasts an intuitive interface that makes navigation effortless. The user-friendly design ensures that users of all ages can benefit from its features without encountering any technological barriers.
Privacy Controls: Protecting user privacy is a priority for Scannero Phone Tracker. The app provides customizable privacy settings, allowing users to determine who can access their location information and when.

Why Choose Scannero Phone Tracker:
In an increasingly connected world, personal security and effective communication are paramount. Scannero Phone Tracker offers a comprehensive solution that combines both elements seamlessly. Whether you're a concerned parent, an individual looking to safeguard their device, or someone interested in maintaining constant contact with their family, Scannero Phone Tracker caters to diverse needs with its array of features and commitment to user privacy.
Cost Per Trial
#PhoneTracker#GPSTracking#MobileTracking#CellPhoneTracker#PhoneMonitoring#FamilySafety#LostPhoneTracker#ChildTracking#EmployeeMonitoring
19 notes
·
View notes