#even in the absence of a banking system in their region
Explore tagged Tumblr posts
Text

Scammers sophistication technique have reached a new apex, making Banking Fraud just like a walk in the park to this crime syndicates with richer background helter-skelters depositors and has been keeping most retirees that reinvested most of their retirement plan sleepless after words of the threat that swept the streets does not seem to have not weakened at all.
Masses are appealing for a more stringent countermeasure to be in place as soon as possible, such are adding more authentication request. Although retina scanner can slow down the process with the amount or rather the size of the data, but it also gives us an opportunity of having time to lockout perpetrators. The size of the data makes it at least 70% better than an iris scan and many more folds multiplied compared to a fingerprint.
Several years ago, I foresaw that the mCommerce (mobile commerce) would be ruled out as the mainstay of electronic processing for the sole reason that it is the most affordable business appliance that can serve the majority, representing the poor to medium class and the trending plot of global economic structure just like a triangle.
Having mCommerce | Mobile Technology as our economic transport offers the possibility of catering and adding the biggest chunk of our global population to pitch in the global trade for us to achieve having reserves and surplus will be more conceivable.
To make it a little impenetrable and globally under tighter scrutiny, I proposed that we adopt the universal identification system. We will integrate every other form of identity attached to it using our mobile number as the key index that will permanently our lifetime phone number. In the event of loss, the telco will make a SIM based on a secret code given to the subscriber upon the receipt of your subscription and issuance, which will be honored and will be service by other Telcos if subscriber opt to change carrier. The number coding of telcos should also compliment tracking effort, narrowed down within the radius and range of a few kilometers apart where the last signal was received or transmitted. The succeeding successful connection recorded by cell sites would enable us to speculate the linear direction as it trends.
We will enable the mobile technology to be a conduit of payment gateways or as a payment gateway itself. Our objective is to open the global trade and cover a larger scope and as far-reaching it could service most specially the marginalized poor a chance to lift their social status getting connected and finally be able to join our bandwagon to the brighter future. The fact can't be denied that they have been left without an adequate means to tap the convenience and business opportunity through eCommerce. Through the mobile payment gateway, even in the absence of a banking system in their region, they can now fulfill the checkout process by loading or charging it from your telco which is even less intricate than having a debit card or as to many known financial credibility.
#mobilepaymentgateway
#mobiletechnology
#mCommerce
#onlinefraud
#RetinaScan
Scammers sophistication technique have reached a new apex, making Banking Fraud just like a walk in the park to this crime syndicates with richer background helter-skelters depositors and has been keeping most retirees that reinvested most of their retirement plan sleepless after words of the threat that swept the streets does not seem to have not weakened at all.
Masses are appealing for a more stringent countermeasure to be in place as soon as possible, such are adding more authentication request. Although retina scanner can slow down the process with the amount or rather the size of the data, but it also gives us an opportunity of having time to lockout perpetrators. The size of the data makes it at least 70% better than an iris scan and many more folds multiplied compared to a fingerprint.
Several years ago, I foresaw that the mCommerce (mobile commerce) would be ruled out as the mainstay of electronic processing for the sole reason that it is the most affordable business appliance that can serve the majority, representing the poor to medium class and the trending plot of global economic structure just like a triangle.
Having mCommerce | Mobile Technology as our economic transport offers the possibility of catering and adding the biggest chunk of our global population to pitch in the global trade for us to achieve having reserves and surplus will be more conceivable.
To make it a little impenetrable and globally under tighter scrutiny, I proposed that we adopt the universal identification system. We will integrate every other form of identity attached to it using our mobile number as the key index that will permanently our lifetime phone number. In the event of loss, the telco will make a SIM based on a secret code given to the subscriber upon the receipt of your subscription and issuance, which will be honored and will be service by other Telcos if subscriber opt to change carrier. The number coding of telcos should also compliment tracking effort, narrowed down within the radius and range of a few kilometers apart where the last signal was received or transmitted. The succeeding successful connection recorded by cell sites would enable us to speculate the linear direction as it trends.
We will enable the mobile technology to be a conduit of payment gateways or as a payment gateway itself. Our objective is to open the global trade and cover a larger scope and as far-reaching it could service most specially the marginalized poor a chance to lift their social status getting connected and finally be able to join our bandwagon to the brighter future. The fact can't be denied that they have been left without an adequate means to tap the convenience and business opportunity through eCommerce. Through the mobile payment gateway, even in the absence of a banking system in their region, they can now fulfill the checkout process by loading or charging it from your telco which is even less intricate than having a debit card or as to many known financial credibility.
#mobilepaymentgateway
#mobiletechnology
#mCommerce
#onlinefraud
#RetinaScan
#FraudAlert
#FraudAlert
#Scammers sophistication technique have reached a new apex#making Banking Fraud just like a walk in the park to this crime syndicates with richer background helter-skelters depositors and has been k#Masses are appealing for a more stringent countermeasure to be in place as soon as possible#such are adding more authentication request. Although retina scanner can slow down the process with the amount or rather the size of the da#but it also gives us an opportunity of having time to lockout perpetrators. The size of the data makes it at least 70% better than an iris#Several years ago#I foresaw that the mCommerce (mobile commerce) would be ruled out as the mainstay of electronic processing for the sole reason that it is#representing the poor to medium class and the trending plot of global economic structure just like a triangle.#Having mCommerce | Mobile Technology as our economic transport offers the possibility of catering and adding the biggest chunk of our globa#To make it a little impenetrable and globally under tighter scrutiny#I proposed that we adopt the universal identification system. We will integrate every other form of identity attached to it using our mobil#the telco will make a SIM based on a secret code given to the subscriber upon the receipt of your subscription and issuance#which will be honored and will be service by other Telcos if subscriber opt to change carrier. The number coding of telcos should also comp#narrowed down within the radius and range of a few kilometers apart where the last signal was received or transmitted. The succeeding succ#We will enable the mobile technology to be a conduit of payment gateways or as a payment gateway itself. Our objective is to open the globa#even in the absence of a banking system in their region#they can now fulfill the checkout process by loading or charging it from your telco which is even less intricate than having a debit card o#mobilepaymentgateway#mobiletechnology#mCommerce#onlinefraud#RetinaScan#FraudAlert
0 notes
Text
⚠️WARNING: GRAPHIC FOOTAGE⚠️
[ 📹 Scenes from the first moments after the latest horrific atrocity against Palestinians after the Israeli occupation forces (IOF) conducted an airstrike on a residential neighborhood in the city of Rafah, in the southern Gaza Strip, killing a young man and severely wounding another. ]
🇮🇱⚔️🇵🇸 🚀🏘️💥🚑 🚨
DAY 233: HUMANITARIAN AID ENTERS SOUTH GAZA FOR THE FIRST TIME IN 20 DAYS, ISRAELI MILITARY AND GOVERNMENT FIGHTING TWO DIFFERENT WARS, AL-QASSAM FIRES 8 MISSILES DEEP INTO OCCUPIED TERRITORIES, MASS MURDER CONTINUES IN GAZA STRIP
On 233rd day of the Israeli occupation's ongoing special genocide operation in the Gaza Strip, the Israeli occupation forces (IOF) committed a total of 5 new massacres of Palestinian families, resulting in the deaths of no less than 46 Palestinian civilians, mostly women and children, while another 130 others were wounded over the previous 24-hours.
It should be noted that as a result of the constant Israeli bombardment of Gaza's healthcare system, infrastructure, residential and commercial buildings, local paramedic and civil defense crews are unable to recover countless hundreds, even thousands, of victims who remain trapped under the rubble, or who's bodies remain strewn across the streets of Gaza.
This leaves the official death toll vastly undercounted, as Gaza's healthcare officials are unable to accurately tally those killed and maimed in this genocide, which must be kept in mind when considering the scale of the mass murder.
The Israeli occupation authorities and the Israeli occupation army are fighting two different wars, one for the reestablishment of the security of the occupied territories' borders, and the other a war for the fulfillment of the Israeli extremist wing to see the entirety of the Gaza Strip, southern Lebanon and the West Bank come under Israeli military control.
That is the conclusion come to in an article published by Israeli Channel-12 (N12).
According to the piece, the Israeli war cabinet, including Ministers Bezalel Smotrich and Itamar Ben-Gvir, do not strive for a ceasefire deal that would see the Israeli hostages, being held in the Strip by the Hamas resistance, released, but instead fight to fulfill a "vision of a complete land of Israel."
This vision includes the "control of the IDF in the Gaza Strip and the establishment of new settlements- a matter that Smotrich and Orit Strook [Israeli Minister of Settlements] are already working on in earnest."
According to the N12 piece, elections must be held so Israeli colonists can vote on these two competing political visions for the goals of the war, which can be distilled down to either "settlements in Gaza and military control over the millions of Palestinians who live there; Or leaving Gaza while replacing Hamas rule with a Palestinian body that opposes terrorism, and forming a regional alliance with the moderate Arab states while promoting the two-state solution."
"Since October, the army and the government of Israel have been waging two different wars: the IDF is making tremendous efforts to restore security to our borders, eliminate Hamas and return the abductees. The government is fighting to cancel the disengagement and prevent a political settlement [in order] to return the kidnapped alive, and also sees that Hamas returns to the places the IDF left, in the absence of an alternative political plan."
The article goes on to say that Israeli military leaders are "growing frustrated" with the indecisiveness of the government, which is "missing opportunities" for military and political achievements and reducing the "scope of action."
"Therefore, and soon - Israel must have elections to make a decision. If Smotrich and Ben Gvir are convinced that the people are with them, let them put it to the test," the piece added.
"Let's see if there really is a majority for the Messianic fantasy of the extremists, or if most Israelis prefer to reach a political settlement. Let's see if the citizens of Israel want to send their children to secure outposts in the Gaza Strip as well. It's time to decide," the article concludes.
In other news, the Al-Qassam Brigades, belonging to the Hamas resistance movement, targeted the central areas of the Israeli-occupied Palestinian territories in a missile barrage that included at least 8 rockets launched from the Rafah area, south of Gaza.
According to the Israeli occupation army, 8 rockets crossed into the occupied territories, at least some of which were intercepted by "Israel's" Iron Dome air defense system, while others landed in central "Israel".
The attack caused no injuries, however, at least one rocket struck a car in Kibbutz Sa'ad, near the border with Gaza as it was driving to a nearby school in the area.
According to the occupation media, Kibbutz Sa'ad was previous evacuated of residents following the start of Operation Al-Aqsa Flood on October 7th, 2023, however, many residents have since returned to the settlement.
Additionally, a home belonging to an Israeli colonist was also damaged by shrapnel from a rocket fired by Al-Qassam from Rafah towards the city of Herzliya, just north of Tel Aviv, along the central Mediterranean coast of the occupied territories.
In response to the strikes, Minister without a Portfolio, Benny Gantz, part of Netanyahu's far-right war cabinet, said the strikes shows why the Israeli occupation forces (IOF) must continue its operations in the Rafah Governate of the Gaza Strip.
"The rockets shot from Rafah today prove that the IDF must operate in every place Hamas still operates from, and as such, the IDF will continue to operate wherever necessary,” Gantz declared at the Israeli occupation's Urim military base, east of Gaza.
“The world must know: Those who still hold our hostages captive, shoot at our cities and continue to propagate terror are responsible for the situation,” Gantz said, adding that “terrorist Hamas are war criminals, and we intend on making them pay for their crimes – whether sooner or later” (says a war criminal).
In more news, the Israeli occupation opened the Karm Abu Salem (Kerem Shalom) border crossing in the city of Rafah, in the southern Gaza Strip, with Humanitarian aid trucks entering southern Gaza for the first time in nearly 20 days.
Humanitarian aid trucks were to be delivered to the United Nations, where they will then proceed along the Palestinian-Egyptian border to cross into Gaza.
The aid will then be sent to a distribution warehouse in the Tal al-Sultan neighborhood of Rafah City, and following that, will be distributed to sites deep within the Strip, traveling along the coastal Al-Rashid Street to their destinations.
Around 200 trucks loaded with humanitarian aid and medical supplies are expected to enter the Gaza Strip today, each carrying between 15-20 tons of aid, including at least 4 trucks loaded with fuel.
According to the office of the Presidency for the State of Palestine, official contacts took place between the Palestinian Authority and officials with the Arab Republic of Egypt, which agreed to bring relief aid to the besieged people of Gaza through the Karm Abu Salem border crossing on a temporary basis until a long-term agreement can be reached.
Meanwhile, the Israeli occupation forces (IOF) continued its operations in the Gaza Strip, bombing and shelling large sections of the enclave, targeting civilian locations with massive American-made bombs, killing and wounding scores of civilians over the last day.
On Saturday evening, IOF fighter jets bombed the Al-Najma roundabout area of the Shaboura Refugee Camp, in central Rafah, south of Gaza, resulting in the martyredom of three Palestinian civilians and wounding several others.
This comes despite the decision on Friday by the International Court of Justice (ICJ) at The Hague, in the Netherlands, for the Israeli occupation to "immediately halt" its military operations in the Rafah Governate, or any other operations which "might inflict on Palestinians living conditions" that could lead to their "physical destruction in whole or in part."
The slaughter in Rafah continued despite this, with further bombing and shelling on Saturday, including an incident where Israeli aircraft targeted a residential home belonging to the Qishta family, near the Saddam Junction, in the Khirbet al-Adas neighborhood north of Rafah, striking the residence with a large missile, killing a child and resulting in several other casualties.
Also on Saturday evening, occupation warplanes bombed the market area of the Nuseirat Refugee Camp, in the central Gaza Strip, resulting in the murder of 6 civilians and wounding dozens of others, including women and children.
In Gaza's north, Zionist artillery detatchments shelled neighborhoods west of the Jabalia Camp, coinciding with Israeli military incursions into the camp for the last two weeks.
According to local medical sources, at least 45 Palestinians were killed in Israeli bombing and shelling in the Gaza Strip between Saturday morning and Saturday evening.
The mass slaughter continued into Sunday morning when Israeli occupation aircraft bombarded the Yabna Refugee Camp, in central Rafah, with a number of casualties transported to the Kuwait Specialized Hospital, west of the city.
Similarly, occupation warplanes bombed a residential apartment in Burj al-Iman in Camp 2 of the Nuseirat Refugee Camp, in the central Gaza Strip, while another raid targeted other areas in the Nuseirat Camp.
In the meantime, Israeli artillery shelling targeted residential buildings in the town of Abasan, east of Khan Yunis, in the southern Gaza Strip, resulting in the death of a woman and wounding a number of others.
The attacks continued on Gaza when Israeli fighter jets bombarded a residential home belonging to the Rasras family in central Rafah, leading to the death of a civilian and wounding several others who were transported to the Kuwait Specialized Hospital, west of Rafah.
In yet another criminal atrocity, Zionist aircraft bombed a residential house belonging to the Khalla family, in the town of Jabalia al-Nazla, in the northern Gaza Strip, slaughtering at least 13 Palestinian civilians, including several children and women, while also wounding dozens of others. Local paramedic and civil defense crews continue searching the rubble of the collapsed home for the dead and wounded.
A further occupation bombing targeted the Women's Work Center in the Nuseirat Camp, in central Gaza, killing 6 Palestinians, while yet another bombing targeted an uninhabited house north of the Nuseirat Camp.
According to reporting in the Palestinian news outlet Ma'an News, the Israeli occupation forces arrested some 180 Palestinian citizens from a center sheltering displaced families, before bombing yet another displacement center in the town of Beit Hanoun, in Gaza's north, killing 7 civilians.
In another horrific massacre, IOF warplanes bombed the Al-Nazla School in the Al-Saftawi area, north of Gaza, killing at least 10 civilians and wounding 17 others.
Occupation forces further targeted the "Obaid Freezer building", flattening the structure, which lies opposite the New Orient Bakery in the Tal al-Zaatar area, north of Gaza.
As a result of the Israeli occupation's ongoing special genocide operation in the Gaza Strip, the death toll has risen endlessly, now exceeding 35'903 Palestinians killed, including over 15'000 children and upwards of 10'000 women, while another 80'420 others have been wounded since the start of the current round of Zionist aggression, beginning with the events of October 7th, 2023.
May 26th, 2024.
#source1
#source2
#source3
#source4
#source5
#source6
#source7
#source8
#source9
#source10
#source11
#source12
#source13
#source14
#source15
#videosource
@WorkerSolidarityNews
#gaza#gaza strip#gaza news#gaza war#war in gaza#genocide in gaza#gaza genocide#israeli genocide#israel#israeli occupation#israeli war crimes#war crimes#crimes against humanity#palestine#palestine news#palestinians#free palestine#gaza conflict#israel palestine conflict#occupation#middle east#politics#news#geopolitics#world news#global news#international news#war#breaking news#current events
46 notes
·
View notes
Text
How Is the Micro ATM Market Growing in India?

In recent years, India has witnessed a significant transformation in the way financial services are delivered, particularly in rural and semi-urban areas. One of the most revolutionary innovations supporting this shift is the Micro ATM. Designed to bring basic banking services to the doorstep of people with limited access to traditional banking infrastructure, Micro ATMs have emerged as a powerful tool for driving financial inclusion. With the Indian government’s continued push for digital payments and inclusive finance, the Micro ATM market in India is experiencing robust growth, backed by the rising demand for last-mile financial connectivity.
Understanding the Micro ATM Landscape
A Micro ATM is a portable device operated by banking correspondents or agents that enables users to perform essential banking activities such as cash withdrawal, deposit, balance inquiry, and fund transfer. These devices work on biometric authentication (especially Aadhaar-based), card swipes, or mobile number verification. Micro ATMs act as mini banks and provide a crucial link between rural populations and the formal financial system.
The expansion of Micro services like cash-in/cash-out and balance checks through these devices has made them an indispensable part of India’s financial ecosystem. The accessibility, low operational cost, and ability to operate without full-scale infrastructure make them ideal for bridging the urban-rural financial divide.
Market Growth Drivers
Several factors have contributed to the exponential growth of the Micro ATM market in India:
1. Government Push for Financial Inclusion
The Indian government's initiatives under schemes like Pradhan Mantri Jan Dhan Yojana (PMJDY) have led to a significant increase in the number of bank account holders, particularly in rural regions. However, these account holders often lack nearby access to bank branches or ATMs. Micro ATMs help fill this gap by enabling transactions in areas where physical banks are absent.
2. Rise in Digital Transactions
India has been witnessing a surge in digital payments since the demonetization drive in 2016. This cultural shift towards cashless transactions has laid the groundwork for alternative banking solutions. Micro services offered through Micro ATMs allow rural populations to engage in digital transactions even in the absence of smartphones or internet access, ensuring greater inclusion.
3. Banking Correspondent (BC) Model Expansion
The proliferation of banking correspondents across India has fueled the deployment of Micro ATM devices. These BC agents, equipped with Micro ATMs, act as the face of the bank in far-flung regions. They provide essential services such as deposits, withdrawals, and remittances, making financial services both personal and accessible.
4. Technological Advancements
Modern Micro ATM devices are equipped with biometric readers, card swiping capabilities, thermal printers, and real-time connectivity via GPRS or mobile networks. These enhancements have improved the speed, reliability, and trustworthiness of transactions, leading to wider acceptance and increased usage.
Market Size and Forecast
The Micro ATM market in India has grown rapidly over the past few years. According to industry estimates, India has over 15 lakh Micro ATM devices in operation as of 2024, and this number continues to rise. Rural demand, combined with favorable policies and digital literacy initiatives, is expected to drive the market further.
Projections suggest that the Micro ATM market will grow at a CAGR of over 20% in the coming years. States like Uttar Pradesh, Bihar, Maharashtra, and Madhya Pradesh are leading in terms of device adoption, owing to their large rural populations and ongoing efforts by banks and fintech providers to expand their network.
Impact on Rural Banking
One of the most significant achievements of the Micro ATM expansion has been its impact on rural banking. With limited access to ATMs or bank branches, villagers previously had to travel long distances for basic transactions. Now, with the help of a local agent and a Micro ATM device, they can access cash and banking services quickly and securely.
Moreover, Micro ATMs also enable disbursement of government subsidies and pensions directly into beneficiaries’ accounts, eliminating middlemen and reducing fraud. The delivery of Micro services in real-time enhances transparency and accountability in financial transactions.
Challenges and the Way Forward
Despite its growth, the Micro ATM market faces challenges such as:
Intermittent internet connectivity in rural regions
Lack of awareness and digital literacy
Inconsistent commission structures for agents
Occasional technical glitches and downtime
Addressing these issues through improved infrastructure, training programs for agents, and robust support systems can further accelerate the adoption of Micro ATM services.
Role of Private Players
Technology solution providers are playing a crucial role in expanding the reach of Micro ATMs by offering customized, secure, and scalable platforms. One such player, Xettle Technologies, is contributing to this movement by delivering efficient and reliable Micro ATM systems that support real-time transactions, secure user authentication, and seamless integration with financial institutions. Their innovative approach is empowering rural agents and customers alike, making financial inclusion a practical reality across India.
Conclusion
The growth of the Micro ATM market in India is a testament to the country’s commitment to financial inclusion and digital empowerment. As the demand for Micro services continues to rise, Micro ATMs will remain a cornerstone in connecting India’s rural population to the broader financial ecosystem. With sustained efforts from the government, private sector, and financial institutions, India is well on its way to becoming a fully inclusive digital economy.
0 notes
Text
Start Your Journey with a Clear Perspective on Nissan Patrol 2015 Fuel Consumption
When it comes to navigating the open roads of the UAE in a vehicle like the Nissan Patrol 2015, fuel consumption can often raise eyebrows—especially with a big V8 engine under the hood. Understanding how to maximize fuel efficiency isn’t just a matter of driving less; it’s about making informed decisions at every turn. This guide will equip you with straightforward tips, real-world data, and actionable advice to enhance your journeys, ensuring you enjoy smoother rides and lower fuel bills.

How to Improve Your Nissan Patrol 2015's Fuel Efficiency Today
The 2015 Nissan Patrol is powered by a robust 5.6L V8 engine, which averages around 14.7 L/100 km under mixed driving conditions. This figure has been reaffirmed by UAE traffic authority reports from 2023, illustrating that enhancing fuel efficiency doesn’t have to be a perplexing puzzle. A few practical adjustments can lead to noticeable savings.
3 Maintenance Fixes That Work
Air Filter Replacement: Keep your engine running optimally by replacing the air filter every 15,000 km. A clean air filter ensures a steady airflow to the engine, improving its respiratory function and potentially saving up to 9% in fuel consumption. This step is crucial if your routes traverse dusty conditions.
Synthetic Oil Upgrade: Transition to 5W-30 synthetic oil, as recommended by many regional mechanics. Dubai’s mechanics have observed that synthetic oil enhances engine performance and fuel economy. Regular oil changes help maintain the optimal temperature of your engine while reducing friction, allowing it to work more efficiently.
Tire Alignment: Don’t underestimate the importance of regularly aligning your tires—aim for at least twice a year. Proper alignment reduces rolling resistance, leading to improved fuel efficiency and safer handling. Ensure tire pressure is consistently at the recommended level to enhance performance even further.
Driving Habits That Save Fuel
Your driving habits can make a world of difference when it comes to fuel consumption:
Smooth Operations: Maintain smooth acceleration and braking to avoid rapid fuel consumption.
Optimal Speeds: Stick to speeds of 80-100 km/h on highways, where your engine performs best.
Cruise Control: Utilizing cruise control during long stretches on flat roads can help maintain a steady pace, which conserves fuel.
Adopting these habits can significantly enhance your MPG ratings and assist in managing your fuel expenses effectively.

Why Your 2015 Patrol Consumes More Fuel Than Newer Models
While beloved for its robust nature, the 2015 Nissan Patrol lacks some of the advanced fuel-saving technologies found in modern vehicles. This technology gap is evident when contrasting older models with newer versions from 2025.
Technology Gap Analysis:Feature2015 Model2025 ModelsCylinder DeactivationNot AvailableStandard FeatureStart-Stop SystemNot AvailableStandard FeatureTransmission5-speed Manual/Auto9-speed Automated
The absence of these modern features explains why you might experience higher fuel consumption with your 2015 Patrol compared to its newer counterparts.
Cost-Effective Upgrades
If you’re looking to upgrade your vehicle without breaking the bank, consider:
Aftermarket Engine Tuning Chip: Prices typically range from AED 1,200-1,800 (equivalent in SAR).
Tire Pressure Monitoring System: Retrofitting this system ensures optimum tire performance, reducing drag.
Low-Rolling-Resistance Tires: Switching to these tires can effectively lower your fuel consumption.
Such upgrades can bridge the gap in fuel efficiency between your patrol and modern vehicles.
Real-World Fuel Consumption Data for UAE Drivers
To paint a clearer picture of what to expect from your Patrol under different conditions, here’s a glimpse at real-world data:
Abu Dhabi City: 18.9 L/100km
Desert Off-Road: 22.4 L/100km
Highway (120 km/h): 16.1 L/100km
These figures, based on GCC certified standards, highlight how different terrains and traffic conditions can impact fuel economy.
Fuel Cost Calculator
To assist in estimating fuel expenses, consider the following formula:
Monthly Cost=(Monthly km100)×L/100km×AED 3.05Monthly Cost=(100Monthly km)×L/100km×AED 3.05
This handy calculator empowers you to plan your finances and adapt your driving habits accordingly.
Future-Proofing Your Vehicle for 2025
As we look to the future, upgrading your 2015 Patrol can be approached creatively:
Alternative Fuel Options: E85 compatibility conversions usually cost around AED 4,500, enabling a blend of ethanol and gasoline.
LPG Retrofitting: Available for about AED 7,200, this option is practical for reducing fuel costs.
Hybrid System Installations: Although this requires a larger investment starting at AED 18,000+, it can substantially decrease fuel consumption.
Investing in these technologies may yield significant long-term savings.
Resale Value Protection
Maintaining service records and keeping original engine components intact boosts your vehicle’s resale value. Documenting all improvements to fuel efficiency can also provide peace of mind to future buyers. A comprehensive service log is invaluable in the GCC market.
FAQ
What are some quick fuel-saving tips for my 2015 Nissan Patrol? Various strategies can effectively reduce fuel consumption, including avoiding sudden acceleration and maintaining consistent highway speeds. Regular maintenance and minor upgrades like tuning chips can make a substantial difference in your fuel efficiency.
How does city driving compare to highway driving in terms of fuel consumption? City driving typically results in higher fuel consumption due to frequent stops and lower speeds, with averages around 18.9 L/100km in urban areas like Abu Dhabi. Conversely, highway driving can lower consumption to about 16.1 L/100km. Understanding these differences can help you plan your routes efficiently, minimizing fuel costs.
The content above comes from Cartea, the most professional automotive platform in the Middle East.
0 notes
Text
Ukrainian military: half a thousand Russian troops managed to cross the Oskil River in Kharkiv region
The Russian Armed Forces are facing significant losses on the right bank of the Oskil River due to the challenging evacuation of their wounded, which has become "a whole quest," according to the "Achilles" unit.
Without pontoon crossings, the Russians are forced to transport the wounded by boat, as described by Oleksiy Malyarevich from the 429th Separate Unmanned Aerial Systems Regiment "Achilles" in a comment to Suspilne.
In March, the Ukrainian Defense Forces liberated several territories near Dvorichna in the Kharkiv region.
The liberation efforts specifically targeted the village of Figolivka in the Dvorichna community. "We improved the situation; these are very important, albeit small operations," Malyarevich explained. He also noted that the Russians have been persistent with their assaults in the Kupyansk direction. "The enemy is deploying infantry units; they haven't developed new pontoon crossings but continue their attempts. We often detect them as they approach the river. While we can't catch them all, we target and destroy them at the crossings and on approaches, even on the left bank of the Oskol River," Malyarevich said.
He highlighted that Russian forces are experiencing significant losses on the right bank, facing a "whole quest" to evacuate their injured due to the absence of pontoon crossings, resorting instead to using boats. The military describes a challenging scenario to eliminate Russians who have already crossed the Oskil—they dig hideouts, seek homes, trenches, and basements. "Sometimes, you may find 3–4 people in a sector marked as 'red,' but that doesn't mean an entire regiment is present. This is the nature of this direction now. There are up to half a thousand Russian infantry spread out over large areas, making it tough to detect and destroy them," Malyarevich added.
On March 20, DeepState reported that Russian forces were advancing on the right bank of the Oskil River to establish another foothold.
0 notes
Text
From Apathy to Action – A Community Takes Charge
In 2021, we embarked on a transformative journey in the picturesque village of Doni, nestled in the heart of Uttarkashi. Our mission: to implement a sustainable waste management system. The path was undeniably difficult. We faced the challenges of daunting mountain trails, the absence of community involvement, a lack of awareness and the shadow of caste barriers. Our dream seemed like an insurmountable challenge.
Fast forward to September 2023, we are now proudly serving 640 establishments while operating in six villages within the Uttarkashi district. With five working waste banks and a team of sixteen local champions, we are now leading the charge on waste collection. 80% of the businesses in four of the villages have joined the program, resulting in an outstanding 95% trash segregation rate. This amazing turnaround is a tribute to the perseverance of our community’s heroes, who selflessly crossed caste boundaries to teach their fellow villagers the value of waste management. After two years of continuous community involvement, a unified front surfaced and trust was established. A cleaner environment is being promoted by the community’s acceptance of their part in garbage management.

Janita Di from Gaichwan village shares: “I didn’t think such a change was possible two years ago. Before, most people would look the other way or get angry when asked about waste. Today, my team proudly collects waste and my community actively supports our work.”
Today, the community actively seeks waste management supplies, signifying a profound shift from apathy to action. This inspiring journey demonstrates the power of perseverance and unity, transforming villages into beacons of sustainability and change. As Waste Warriors continues to expand its reach and impact, it reaffirms its commitment to building a greener, cleaner future for Uttarkashi and beyond.
Our efforts in turning apathy into action have shown that even small steps toward plastic recycling can make a big difference in preserving natural habitats. By implementing waste segregation and recycling initiatives, we help reduce plastic waste that would otherwise end up in landfills or pollute forests and rivers. Through education and hands-on participation, communities are now embracing responsible waste disposal practices, ensuring that their surroundings remain clean and safe for both people and wildlife.
Biodiversity conservation is at the heart of our mission, as unchecked waste pollution poses a severe threat to ecosystems. Plastic waste not only contaminates soil and water sources but also endangers wildlife that mistakenly ingests it. Waste Warriors works closely with local residents and marginalized communities to develop sustainable waste management strategies that protect nature while also providing economic opportunities. By engaging these communities in eco-friendly waste collection and recycling initiatives, we create livelihood options while fostering a deeper understanding of the connection between waste management and environmental conservation.
Tourism is a vital economic driver in many regions, but it must be managed responsibly to ensure long-term sustainability. Waste Warriors advocates for responsible tourism by encouraging visitors, businesses, and local authorities to minimize their waste footprint. We promote sustainable tourism practices such as reducing single-use plastics, setting up waste segregation points, and involving local communities in waste management efforts. By working together, we can create travel experiences that not only support local economies but also protect the pristine landscapes and rich biodiversity that make these destinations worth visiting.
#waste management#plastic recycling#Biodiversity conservation#environmental conservation#responsible tourism
0 notes
Text
Cyber security challenges and solutions in india
BY: Pankaj Bansal , Founder at NewsPatrolling.com
India, like many other nations, faces significant cybersecurity challenges due to the increasing reliance on digital technologies, especially with rapid digitalization and expansion of internet usage. The country has witnessed a rise in cyberattacks on both individuals and organizations, impacting critical sectors like banking, healthcare, infrastructure, and government services. Here are some of the major cybersecurity challenges and potential solutions in India:
Key Cybersecurity Challenges in India
Increased Cybercrime and Hacking Incidents:
India has seen a surge in ransomware attacks, phishing attempts, data breaches, and other cybercrimes targeting both individuals and organizations.
There have been multiple instances of hacking into sensitive government websites, corporate networks, and even power grids.
Lack of Awareness:
Many internet users, particularly in rural areas, have limited awareness of cybersecurity threats and best practices. This leads to vulnerabilities such as weak passwords, falling for phishing scams, and downloading malicious software.
Small and medium-sized businesses (SMEs) often do not prioritize cybersecurity, making them easy targets for hackers.
Shortage of Skilled Cybersecurity Professionals:
There is a significant shortage of trained cybersecurity experts in India, which is critical to addressing and preventing cyberattacks.
The rapid digital transformation is outpacing the availability of cybersecurity skills, leaving many systems inadequately protected.
Weak Infrastructure and Legacy Systems:
Many organizations, including government institutions, still rely on outdated and unpatched systems, which are prone to vulnerabilities.
India’s digital infrastructure has grown rapidly, but with varying degrees of security across sectors.
Insufficient Data Protection Laws:
Although the Indian government passed the Data Protection Bill in 2023, there are still gaps in enforcement and understanding.
The absence of stringent cybersecurity regulations for private businesses and enforcement mechanisms means many companies overlook critical security updates.
Rise in Cyber Espionage and Nation-State Attacks:
India has been targeted by cyber-espionage campaigns, often attributed to foreign actors, attempting to compromise critical infrastructure, government systems, and defense data.
Complex Supply Chain Networks:
Many Indian companies depend on global supply chains, which introduce risks from third-party vendors who may not have strong cybersecurity measures, exposing the organization to indirect attacks.
Solutions to Cybersecurity Challenges in India
Strengthening Cybersecurity Infrastructure:
The Indian government has taken steps like establishing CERT-In (Indian Computer Emergency Response Team) to coordinate and respond to cybersecurity threats.
Enhanced infrastructure for monitoring, detection, and response to cyberattacks should be implemented at national and regional levels.
Promoting Cybersecurity Awareness:
Large-scale public awareness campaigns should be launched to educate citizens, especially in rural areas, on the importance of cybersecurity.
Schools, universities, and businesses should promote cybersecurity training, and best practices for safe internet usage, such as using multi-factor authentication (MFA), recognizing phishing scams, and securing personal data.
Development of Cybersecurity Talent:
India needs to invest in upskilling its workforce by offering specialized cybersecurity training programs, certifications, and courses in higher education institutions.
Encouraging collaboration between the private sector and academic institutions to create internship opportunities and research initiatives can address the talent gap.
Implementation of Stronger Data Protection Laws:
The Personal Data Protection Bill (now known as the Digital Personal Data Protection Act, 2023) outlines the framework for protecting personal data but needs stronger enforcement.
Regular audits and penalties for companies that fail to comply with data protection norms are crucial.
Use of Advanced Technologies:
Embracing AI (Artificial Intelligence) and Machine Learning (ML) for automated threat detection, behavior monitoring, and predictive analytics can help reduce the response time to cyberattacks.
Technologies like blockchain can be applied to sectors such as banking and supply chain to secure transactions and ensure the integrity of digital records.
Securing Critical Infrastructure:
Implementing Zero Trust Architecture in critical sectors like finance, healthcare, and power grids to ensure stringent access controls and network segmentation.
Proactive collaboration between the public and private sectors in securing infrastructure, with real-time threat intelligence sharing.
International Collaboration:
India must continue to engage in cybersecurity collaborations with other countries to share knowledge, technologies, and strategies to combat global cyber threats.
Participating in initiatives like Cybersecurity Capacity Building Programmes by organizations such as the UN or G20 can strengthen its cybersecurity posture.
Public-Private Partnerships (PPP):
The government should foster more partnerships with tech companies and cybersecurity firms to build resilient and secure digital ecosystems.
Incentivizing private companies to adopt better cybersecurity measures through tax benefits or certifications can help enhance overall security.
Recent Initiatives and Efforts in India
National Cyber Security Policy (2013): The policy lays the foundation for cybersecurity in India, but a revised and updated policy is in the works to address modern challenges.
Cyber Surakshit Bharat Initiative: Aims at creating awareness and building capacities among government officials to address cybersecurity challenges.
Cybersecurity Centers of Excellence: Various state governments, such as Telangana and Karnataka, have set up cybersecurity centers to focus on threat intelligence, capacity building, and research.
India’s cybersecurity landscape is evolving rapidly, but it requires continuous efforts to keep pace with global challenges. Enhanced cooperation between the government, private sector, and citizens will be essential to safeguard India's digital future.
0 notes
Text
Modern Fraud Reaches New Alarming Record

Scammers sophistication technique have reached a new apex, making Banking Fraud just like a walk in the park to this crime syndicates with richer background helter-skelters depositors and has been keeping most retirees that reinvested most of their retirement plan sleepless after words of the threat that swept the streets does not seem to have not weakened at all.
Masses are appealing for a more stringent countermeasure to be in place as soon as possible, such are adding more authentication request. Although retina scanner can slow down the process with the amount or rather the size of the data, but it also gives us an opportunity of having time to lockout perpetrators. The size of the data makes it at least 70% better than an iris scan and many more folds multiplied compared to a fingerprint.
Several years ago, I foresaw that the mCommerce (mobile commerce) would be ruled out as the mainstay of electronic processing for the sole reason that it is the most affordable business appliance that can serve the majority, representing the poor to medium class and the trending plot of global economic structure just like a triangle.
Having mCommerce | Mobile Technology as our economic transport offers the possibility of catering and adding the biggest chunk of our global population to pitch in the global trade for us to achieve having reserves and surplus will be more conceivable.
To make it a little impenetrable and globally under tighter scrutiny, I proposed that we adopt the universal identification system. We will integrate every other form of identity attached to it using our mobile number as the key index that will permanently our lifetime phone number. In the event of loss, the telco will make a SIM based on a secret code given to the subscriber upon the receipt of your subscription and issuance, which will be honored and will be service by other Telcos if subscriber opt to change carrier. The number coding of telcos should also compliment tracking effort, narrowed down within the radius and range of a few kilometers apart where the last signal was received or transmitted. The succeeding successful connection recorded by cell sites would enable us to speculate the linear direction as it trends.
We will enable the mobile technology to be a conduit of payment gateways or as a payment gateway itself. Our objective is to open the global trade and cover a larger scope and as far-reaching it could service most specially the marginalized poor a chance to lift their social status getting connected and finally be able to join our bandwagon to the brighter future. The fact can't be denied that they have been left without an adequate means to tap the convenience and business opportunity through eCommerce. Through the mobile payment gateway, even in the absence of a banking system in their region, they can now fulfill the checkout process by loading or charging it from your telco which is even less intricate than having a debit card or as to many known financial credibility.
#mobilepaymentgateway #mobiletechnology #mCommerce #onlinefraud #RetinaScan #FraudAlert
1 note
·
View note
Text
The Cost of Cleanliness: Rural Sanitation Challenges and Economic Disparities
In our global quest for improved sanitation, it’s essential to focus on the distinctive challenges faced by rural communities. While strides have been made in urban areas, rural regions often grapple with formidable obstacles in their pursuit of clean and accessible sanitation facilities. According to the Pan American Health Organization (PAHO), as of late 2019, 15.5 million people in Latin America and the Caribbean practiced open defecation, highlighting the prevalence of this issue in various regions.[1] In this article, we delve into the specific issues hampering rural sanitation, shedding light on the importance of addressing them.
The Rural Sanitation Dilemma

Limited Infrastructure Accessibility
Rural communities frequently lack the necessary infrastructure for sanitation, including sewage systems and proper waste disposal. The absence of such facilities forces many to rely on rudimentary methods, contributing to open defecation and the contamination of local water sources.[2]
Scarce Financial Resources
Economic disparities between urban and rural areas further exacerbate the problem. Many rural families struggle to afford sanitation solutions, with limited access to financing or government subsidies. As reported by the World Bank, the global costs of inadequate sanitation were estimated at a staggering $260 billion even before the COVID-19 outbreak in 2020, underscoring the financial implications of this issue for communities.[3]

Cultural and Behavioral Factors
Understanding the cultural dynamics of rural communities is crucial when addressing sanitation challenges. Deep-rooted practices and beliefs can impede the adoption of improved sanitation methods. Breaking away from traditional practices requires education and community engagement.[4]
Geographical Isolation
Geographical remoteness poses a significant challenge to rural sanitation initiatives. Inaccessible terrain and long distances to resources hinder the implementation of effective sanitation solutions. Communities in remote areas face greater isolation and lack of support.[5]
The challenges associated with rural sanitation are deeply intertwined, making the situation particularly complex. The absence of infrastructure, combined with financial constraints, fosters a cycle of inadequate sanitation practices. Cultural norms often resist change, making it challenging to introduce new technologies or habits. Moreover, geographical isolation compounds these issues, limiting access to support and resources.
Click here, to read more about this article.
Click here, to read more blogs in Gospel for Asia.Net
#Change in Sanitation#Free Sanitation Facilities#Improve Sanitation#Open Defecation#Poor Sanitation#Sanitation Facility#Water Crisis#Water Scarcity#Water Shortage#Gospel for Asia#KP Yohannan
0 notes
Text
How to Implement Cashless Payments in Your Business?
In today’s digital age, cashless payments have become increasingly popular and are transforming the way businesses operate. According to a report by PwC’s 2025 & Beyond: Navigating the Payments Matrix, Global cashless payment volumes are set to increase by more than 80% from 2020 to 2025, and to almost triple by 2030.
With the rise of mobile wallets, contactless payments, and online transactions, consumers are expecting convenient and secure payment options. Implementing cashless payments in your business can enhance customer experience, streamline operations, and boost sales.
If you’re considering transitioning to a cashless payment system, this article suggests some key steps to help you successfully implement it.
But first, let us understand the difference between contactless and cashless payments.
Are Contactless Payments the Same as Cashless Payments?
Contactless payments and cashless payments are related but not exactly the same. While they both involve electronic transactions and the absence of physical cash, there are some distinctions between the two.
Cashless payments refer to any transaction that does not involve physical currency. It encompasses a broad range of electronic payment methods, including but not limited to contactless payments. Cashless payments can be made through various channels such as mobile wallets, debit or credit cards, online transfers, electronic funds transfers (EFT), and even cryptocurrencies. It essentially means that customers can pay for goods and services using digital forms of payment rather than traditional cash.
On the other hand, Contactless payments are a specific type of cashless payment method that utilizes near-field communication (NFC) technology. This technology allows the transfer of payment information between a customer’s payment device (such as a smartphone, smartwatch, or contactless card) and a merchant’s payment terminal by simply holding the device near the terminal. Contactless payments eliminate the need for physical contact or the insertion of cards into a machine, making transactions faster and more convenient.
While contactless payments are a popular form of cashless payment, not all cashless payments are contactless. For example, online transfers or payments made through mobile wallets without physical contact are considered cashless payments but not specifically contactless. Similarly, traditional card payments that require inserting or swiping a card are cashless but not contactless.
Cashless Payments Today
There are several types of cashless payment methods available today. Here are some common ones:
Debit and Credit Cards
Contactless Cards (tap-and-go cards
Mobile Wallets
QR Code Payments
Online Payment Gateways
Bank Transfers
Peer-to-Peer (P2P) Payment Apps
Cryptocurrencies
Prepaid Cards
Biometric Payment
Buy Now, Pay Later
It’s important to note that the availability and popularity of these cashless payment methods may vary depending on the region and the specific merchant infrastructure.
Steps to implement Cashless Payments
Here are some steps that you need to take to implement Cashless Payments in your business :
1.Understand Your Business Needs
Before implementing cashless payments, take the time to evaluate your business requirements. Consider the nature of your products or services, customer preferences, and the existing payment infrastructure. Assessing your needs will help you determine the most suitable cashless payment options and the necessary technological upgrades.
2.Research Cashless Payment Solutions
There are various cashless payment solutions available in the market, ranging from mobile wallets like Apple Pay and Google Pay to card-based systems and online payment gateways. Research and compare different options to identify the ones that align with your business needs. Look for features such as ease of use, security, compatibility with existing systems, and transaction fees. It’s also essential to consider the payment preferences of your target customers to ensure you’re offering the most convenient options.
3.Upgrade Your Payment Infrastructure
To enable cashless payments, you’ll need to upgrade your payment infrastructure. This may involve installing point-of-sale (POS) systems that are compatible with contactless payments, such as NFC (Near Field Communication) technology. If you have an online presence, you’ll need to integrate payment gateways into your website or app. Collaborate with a reputable payment service provider or consult with a technology expert to ensure a smooth and secure transition.
4.Train Your Staff
Implementing cashless payments successfully requires educating and training your staff. They should be familiar with the new payment processes, including how to operate POS systems, handle mobile wallets, and troubleshoot any issues that may arise. Conduct training sessions or provide comprehensive guides and resources to ensure your employees feel confident and capable of assisting customers during the payment process.
5.Communicate the Change to Customers
Informing your customers about the transition to cashless payments is crucial for a smooth adoption process. Utilize various communication channels such as social media, email newsletters, website banners, and in-store signage to spread the word. Highlight the benefits of cashless payments, such as increased convenience, enhanced security, and faster transactions. Address any concerns or questions your customers may have to alleviate any potential resistance to the change.
6.Ensure Security and Compliance
Security is a top priority when it comes to cashless payments. Implement robust security measures to protect sensitive customer information and transactions. Use encryption technologies, adhere to industry security standards, and regularly update your systems to safeguard against potential threats. Additionally, ensure your business complies with relevant data protection and privacy regulations to build trust and maintain customer confidence.
7.Monitor and Adapt
Once cashless payments are implemented, continuously monitor and evaluate their performance. Track transaction volumes, customer feedback, and any technical issues that may arise. Stay updated on emerging payment trends and technologies to ensure your business remains relevant and adaptable. Regularly review and optimize your payment processes to provide the best possible customer experience and maximize the benefits of going cashless.
Wrapping Up
By implementing cashless payments in your business, you can streamline operations, improve customer satisfaction, and stay ahead of the competition. Remember to thoroughly research your options, upgrade your payment infrastructure, educate your staff, communicate with your customers, and prioritize security. With careful planning and execution, cashless payments can revolutionize your business and drive its success in the digital era.
1 note
·
View note
Photo
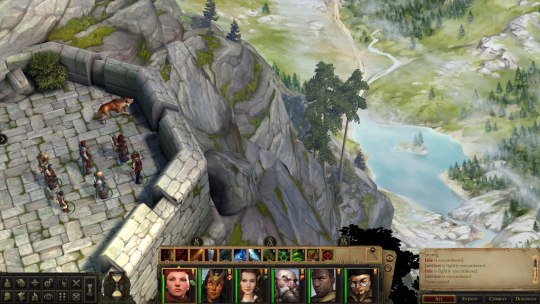
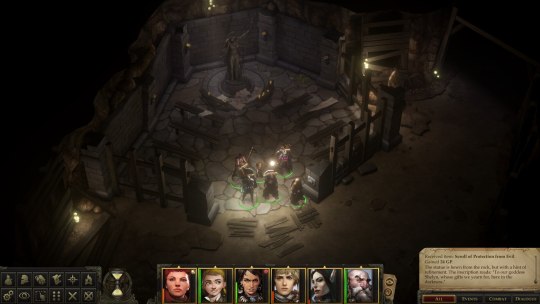

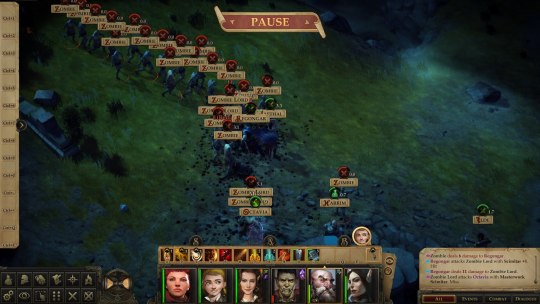
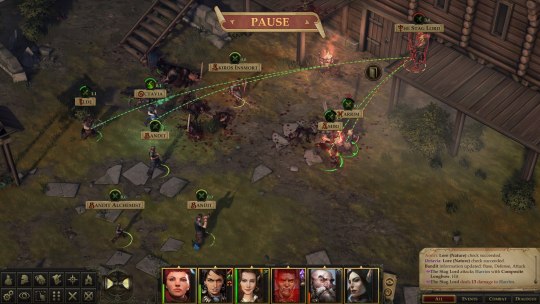

The long process of making a king
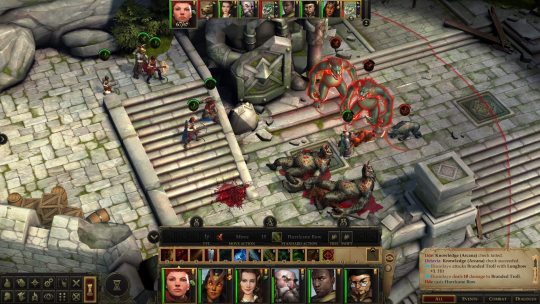
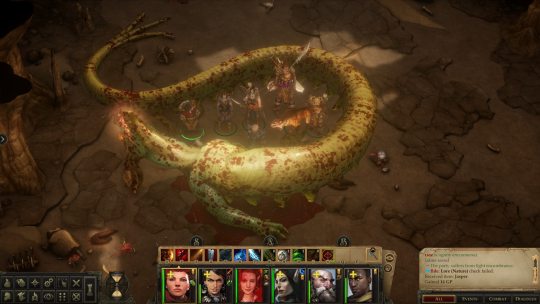
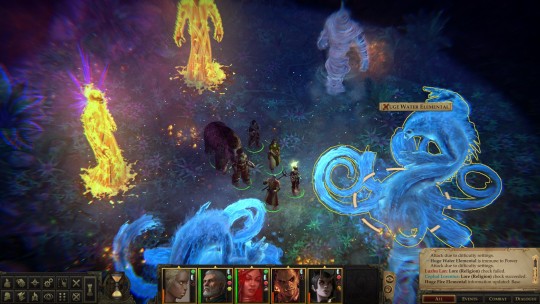
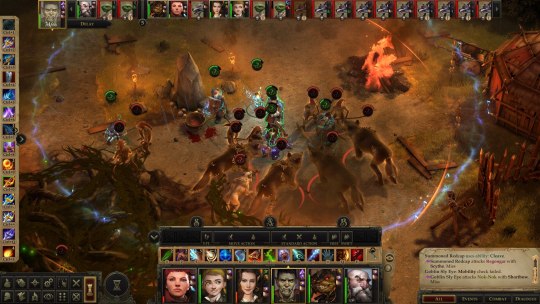
I have like, no time for long video games anymore. My days of being able to play The Witcher 3 for ten hours straight are gone, and most of the time I’m lucky if I can get an hour or two at night. Enter Pathfinder: Kingmaker, a particularly long game which took me almost two years to finish. I started it in June 2020, back when the pandemic was still relatively new, and I finally finished it in April of 2022, after months of just playing here and there in the evenings and whenever I had some alone time on weekends. Oh, I took some long breaks as well, to play stuff like Cyberpunk 2077 and Resident Evil Village, which is probably why this game became an unusual constant in my life.
For a game that I played for nearly 24 months, Pathfinder: Kingmaker is sort of a mess. It’s an adaptation of the Kingmaker Adventure Path of the Pathfinder tabletop roleplaying game, which is a very nifty sandbox campaign where your ragged band of heroes free a region called the Stolen Lands from a bandit lord, become monarchs, and deal with all the business of setting up a new kingdom in a fantasy world - invasions of violent trolls, sabotage at the hands of a rival king and an angry fey lady who wants the world to burn. There’s possibly an argument of “Hrmm, this campaign kinda sounds like the player characters are doing some light colonization,” but since the plot takes pains to present the Stolen Lands as constantly suffering under the control of bad guys who are going to abuse the populace in your absence, I’ll avoid giving myself a headache by looking too close. Kingmaker’s a grand enough campaign that I decided to bank the Pathfinder 2e crowdfunded conversion, which was supposed to come out in 2020 but got hit with a ton of Slow spells and will hopefully release this year.
But we’re not talking about tabletop stuff here, we’re talking about the video game made by smallish Russian developer Owlcat Games. Kingmaker was released in 2018 with a whole bundle of bugs, and even though most have been fixed by now, the game’s still kinda fiddly. The encounters feel like they were designed by min/maxers with the computer straight up seeming to cheat the farther you get, and there’s a ton of stuff that the game just doesn’t bother to explain to you, ranging from the intricacies of the Pathfinder 1e ruleset to the unexplained methods of romancing your comrades - some of which barely seem to have any internet info on them, three and a half years after release. Oh yeah, and I only somewhat understood the whole kingdom management system, which is a funny thing to make perplexing especially in a game named, err, Kingmaker.
For all these reasons, I don’t know if I can recommend Kingmaker to anyone who hasn’t played a computer RPG before, or D&D/Pathfinder on a table. It certainly doesn’t have the same sort of mainstream appeal as the Divinity: Original Sin games - but honestly, I like Kingmaker a lot more despite its messiness. The fact that I’m a fan of the Pathfinder setting certainly helps, but there’s a sort of enjoyable Eastern European jank that shows up a lot in computer RPGs which always feels like, “a small studio bit off way more than they could chew with this monster of a game, but they committed to releasing it, the mad lads.” I felt that way with The Witcher 1, for instance, and I feel that way with Kingmaker. Despite its annoyingly designed encounters and obfuscating mysteries, the game radiates quite a lot of charm and re-creates the modules it was based on with staggering accuracy. Owlcat also improved Nyrissa, originally the big villain of tabletop Kingmaker, by injecting her with way more personality than she ever had in the original campaign. They even listened to fan response throughout Kingmaker’s life, and when the people demanded a turn-based combat mode, they got the blessing of the dude behind a popular mod and stuck it in the game itself. Good form.
I also found Kingmaker interesting because it marks the longest time I’ve spent with the Pathfinder 1e ruleset. I GM the second edition of the game every other week, but I’ve never actually played or run its predecessor or the D&D 3e/3.5e rules it was based on. I got my start with tabletop games relatively recently, in 2017 with D&D 5e, and even though I read the Pathfinder 1e books and hacked together versions of their systems for my D&D games, diving into Kingmaker was the first time I got to truly see the system for what it is. And man, that Pathfinder 1e ruleset is a beast, forever making me alternate between thinking “huzzah there’s SO MUCH crap here” and “oh GOD there is so much crap here.” Let it be said that on some of those nights when I only had two hours to play this darn game, I spent an hour and a half of that time just leveling up my characters. Also, I will never miss Arcane Spell Failure.
At the end of the day, if I’d played or GMed Kingmaker when it came out as a tabletop adventure, it probably would’ve taken two years of real life to complete. In that sense, this game was hellacious accurate. Play it if you can tolerate overcomplicated systems or like min/maxing. If that’s not your style, just play it on Easy mode and install the Bag of Tricks mod, which lets you do everything from instantly teleporting your party across the screen to romancing characters you might’ve pissed off. Or check out Wrath of the Righteous instead, Owlcat’s other adaptation of a Pathfinder Adventure Path which seems to fix most of the problems of their first effort. I’m gonna start that one soon; if all goes well I should finish it in 2024. Yippee.
8 notes
·
View notes
Text
Deforestation, dispossession, displacement for plantations and industrial harvest as agri-business uses catastrophe as smokescreen, especially in Latin America:


It is even a rich time for the shareholders of smaller players in the industry, like the oil palm and rubber plantation company SOCFIN. The two French and Belgian families that essentially own the company, received EUR20 million (around US$22.5 million) in dividends and remunerations from SOCFIN’s group operations while communities where it operates in Nigeria, Ghana and Cameroon cannot access clean or safe water. The labourers in the corporate food system, those who are quite literally dying on the frontlines to sustain the lifestyles of shareholders and executives, are not faring well. [...]
Brazil’s soybean exports, which are up 38 percent from last year, are another potential hotspot [...]. When the local government of the port town of Canarana in Mato Grosso tried to take action by issuing a decree to pause the export of soybeans and other grains in the absence of proper health and safety conditions, the agribusiness giants Louis Dreyfus and Cargill intervened and were able to reverse the decree within a few days. [...] All this export frenzy has a tremendous impact on the ground. According to Deter, the real-time detection system of the Brazilian national space research institute, deforestation of the Amazon in Brazil has increased by more than 50 percent in these first three months of 2020 – at the height of the coronavirus pandemic, in comparison to the previous year’s first quarter. Taking advantage of the pandemic smoke screen, with fewer inspection agents able to carry out inspection, agribusiness and mining operations are advancing on protected areas and indigenous territories, increasing the contagion of Covid-19 in indigenous populations. Many observers fear a genocide as a result of these reckless advances of agribusiness and mining operations during the pandemic.
Amidst the national quarantine in Argentina, soybean exports and forest clearings have not ceased either. In one of the most preserved forests in the entire Gran Chaco ecosystem, an area of 8,000 hectares is being prospected for clearing. Furthermore, based on monitoring with satellite imagery, Greenpeace denounced that almost 10,000 hectares were cleared in the North of the country since the lockdown began. [...]
We have also seen it in Brazil where the Bolsonaro government approved a record 96 new pesticides in the first months of 2020, more than all the approvals for 2019. The same government deliberately used the cover of the pandemic to try and pass a law that would legalise land grabs and deforestation covering 80 million hectares in the Amazon and Cerrado regions.

On April 23, 2020, with the world in the grips of the Covid-19 pandemic and the FAO warning of a looming global food crisis, Nestle’s shareholders and executives awarded themselves a record dividend payout of US$8 billion. In a time of a global health and food crisis, this handout is worth more than the entire annual budget for the UN’s World Food Programme and would be enough to cover the average annual expenditures on health care for more than 100 million people in Africa. Nestle’s massive 2020 dividend payment was, in fact, just a fraction higher than the previous year’s. [...] Other notable shareholder dividends, announced in April this year, include a US$2.8 billion payout by the world’s largest seed and agrochemical company Bayer AG, a US$600 million payout by the world’s largest poultry producer Tyson and a US$500 million payout by the world’s largest pork company, the WH Group. Cargill, the word’s largest agribusiness company, is on track to top last year’s record payout of US$640 million, which it makes to just a small number of Cargill family members. [...]
Worse is yet to come. Many governments are employing global consulting firms, like Mc/K!nsey, to shape their plans to open their economies back up. These secretive firms which are deeply connected to the world’s largest corporations, including those from the food and agribusiness sector, will no doubt influence who emerges [...]. We are also seeing the IMF and World Bank use their Covid-19 emergency funds to push countries into implementing agribusiness-friendly reforms.
---
GRAIN staff. “Agro-imperialism in the time of Covid-19.” CADTM Online. 16 July 2020.
435 notes
·
View notes
Note
Question: were medieval peasants always on the edge of starving, as in couldn't waste food? Or did that vary with time and place? Thanks in adavance!
Well, I have to say that it must be fairly obvious that when we’re talking about a span of roughly one thousand years in an entire continent, in multiple countries/kingdoms/geopolitical situations, and over the course of large-scale, macro-level geographical, climate, crisis, and cultural incidents, it would indeed vary, sometimes wildly, and this is the case for almost any factor that you could possibly think of. It will not surprise you to learn that “medieval peasants were always on the brink of starving” is yet another tired old cliche from the Bad Old Middle Ages grab bag, and while it reflects a different system from modernity, it is not necessarily the case that it was always worse (especially considering the prevalence of hunger in the modern world and the parallel universes in food access between rich and poor, which were simply never that extreme in the medieval era). Today, there’s no relationship whatsoever between how rich people eat and how poor people eat; they exist in completely separate realms. Rich people simply have no worry about disruption to food supply, reliance on local economy or agriculture, the impact of natural disasters, or anything else; globalization and worldwide supply chains means that they can be assured of whatever they want, whenever they want it. Even wealthy people in the Middle Ages did not exist in their own ecosystem the way modern rich people do. Their food was grown on the same land, was subject to the same possible impacts of famine or crop failure, was reliant on having farm labor to cultivate it, and otherwise came from the same place as the food of poor people. Obviously class, status, and money affected what goods a medieval citizen had access to, whether in food or anything else, but food inequality and disparity is WAY more of a thing in modernity than it was in the Middle Ages.
Next, when we say “medieval peasants,” do we mean literal peasants, i.e. manual laborers tied to a single plot of land who worked it, harvested its crop yields, owed rent to a local landlord, and were often rural and on the subsistence level? Because obviously, there are social differences among peasants too, and some of them could be quite wealthy. In his usefully titled “Did the Peasants Really Starve in Medieval England?”, Christopher Dyer points out that the upper class of peasants, who had about thirty acres of arable land and access to common pastures, would easily be able to provide themselves with bread, potage (soup) and ale on a daily basis, have consistent access to dairy and meat, and even enough money to buy extra fish, meat, and prepared foods like pudding and pie from the village or market town. It would be easy for them to eat the usual 2000 calories a day, and their diet would be relatively flavorful and nutritious even by modern standards. Poorer peasants would be more reliant on just bread, potage, and ale, and have less access to meat and dairy, but they still weren’t outright starving. Manual labor doesn’t go well if the laborers are constantly underfed and/or weak from malnutrition, and while the poorest peasants’ diet would have been fairly monotonous and carb-heavy, it still would provide raw calories for energy.
Nor were food economies exclusively local, as that equally tired cliche that people never traveled more than ten miles from home would have you believe (honestly, where did that even come from?) As Food in Medieval Times puts it, “A remarkably wide variety of foodstuffs was available to consumers in the Middle Ages. Besides homegrown and raised products, exotic fruits and spices were brought by Arab merchants into the Mediterranean markets and sold across Europe at premium prices. Although bad harvests resulting in famine and disease occurred periodically, the staple foods -- bread, dairy products, cheap cuts of meat, and preserved fish -- were usually available to the general population. In richer households the foodstuffs were more exclusive and the dishes more sophisticated and varied.” Regional differences would obviously thus play a part. Common people in Iberia, Italy, and southern Europe would be more easily able to access certain delicacies not available in relatively barren England and northern Europe, and would be geographically closer to the Mediterranean markets. They still would not be able to afford expensive delicacies like saffron or other fine spice, but that doesn’t mean they never had it at all. There were many feast days and festivals in the religious and liturgical calendar, and communities would come together with food just as they do now.
There were also social welfare systems and safety nets, wherein, for example, ageing peasants could retire and be provided with a food pension by their landlord (there are numerous legal contracts of this nature, which had to be written down since what a surprise, the landlords didn’t always keep their word or honor their obligations). Even serfs didn’t have to work until they keeled over; they could take retirement and be provided with a portion of the food yield of the estate from their working-age peers, indeed rather like Social Security. There were also almoners at churches, monasteries, and other religious houses, who relied on donations from rich patrons with guilty consciences in order to feed the destitute poor, like a modern-day soup kitchen. These arrangements would obviously not have covered everybody (once again, we note, food banks and food stamps and other arrangements don’t do that for modern people either), but it doesn’t mean there was no recourse.
Of course, the food economy was more perilous than it is now, and more prone to natural disasters and agricultural disruptions. There are certainly famines recorded throughout the medieval period (such as the Great Famine of 1315-18), and several years of bad harvests could have a devastating impact on rich and poor alike. (Since again, the rich didn’t have their own entirely separate ecosystem; their food had to come from the same place as their poorer counterparts.) Climate change, too little rain, too much rain, drought, fire, pestilence, or anything else, in the absence of industrialization, mass farming techniques, factories, or anything of the sort, meant that food supplies were vulnerable to the natural environment, and people did die of hunger in the bad years. While standards did also change and improve over time, the earlier (pre-11th century) medieval period was not necessarily always worse. After the Black Death, when there were simply much fewer people than before, and increasingly so in the late fourteenth and fifteenth centuries, peasants usually had fairly reliable access both to raw food and cash to purchase prepared food. By the sixteenth and seventeenth centuries, the threat of widespread food catastrophe had largely subsided; there aren’t any major famines recorded in Europe at this time, though we daresay they had plenty of other problems (not least the wars of religion). Of course, that little thing in 1492 had also happened, opening up the Columbian Exchange and new routes of supply to the New World, including large-scale transportation and trade of food.
As I’ve mentioned in at least one other ask, people also knew how to cook food properly; someone studied the latrines at Warkworth Castle in northern England (don’t ask me who thought that this is a fun research project, but it takes all kinds) and discovered a remarkable lack of food-borne pathogens. In other words, even without modern safety standards or exact temperature guidelines, people were well aware how to cook food so it tasted good and wouldn’t kill you. They also took pride in doing so. In “The Evolution of Culinary Techniques in the Medieval Era,” Barbara Santich explores the evolution of written recipes from a few notes intended to remind the chef of something they already knew, to a more detailed programmatic for someone who might not have actually made the dish before. Skilled cooks were highly prized members of middle-class and upper-class households, and people who had money to spend on food enjoyed banquets, diverse dishes, and whatever delicacies they could get from their local merchants and markets. The extensive system of medieval trade networks, as mentioned above, meant that consumer goods could travel a very long way indeed, and while you couldn’t walk into a supermarket and get whatever you wanted whenever you wanted it, there would be at least some opportunity for you to acquire something new.
Anyway, yes. Medieval peasants: usually not starving. There you have it.
220 notes
·
View notes
Text
17 Curious Facts About Cincinnati’s Ravenous Appetite For Oysters

Cincinnati Ate A Lot Of Oysters
In the 1800s, Cincinnati diners consumed something 200,000 gallons of fresh oysters every season, shipped in the shell on ice from the east coast. That works out to something like 2.5 million oysters per year. The volume is remarkably consistent between reports in 1852 and 1888. In the 1880s, 30 Cincinnati businesses either packed or served oysters.
Oysters Inspired Better Transportation
As early as the 1810s, Cincinnatians consumed oysters, pickled or spiced, shipped in hermetically sealed canisters. By the 1830s, entrepreneurs had worked out a system of speedy wagons to get fresh oysters from Baltimore to Wheeling, where steamboats could haul the tasty molluscan cargo to Cincinnati. From Chesapeake Bay to the Public Landing, the entire trip took just five days, with new ice added along the way to keep the oysters in prime condition. Within a few years, railroads shortened that run to just hours.
Mrs. Trollope Was Appalled
Pretty much everything about Cincinnati disturbed Frances “Fanny” Trollope. The acerbic British lady vented her displeasure in her 1832 best-selling “Domestic Manners of the Americans,” where she whined about Cincinnatians: “In eating, they mix things together with the strangest incongruity imaginable. I have seen eggs and oysters eaten together; the sempiternal ham with apple-sauce; beefsteak with stewed peaches; and salt fish with onions.”
Oysters Delayed The Mail
Mail runs were profitable for stagecoach lines, but not as profitable as oysters, and barrels of iced blue points were shoved into every available space on wagons departing Baltimore. The Daily Gazette [5 February 1846] reported that mail deliveries to Cincinnati were arriving late because the postal coach had broken down from being overloaded with oysters.
Oysters As You Like Them
How did Cincinnatians eat their oysters? An 1859 menu preserved by the Gibson House offers a single course at an elaborate dinner consisting of Oysters Baked in Shells, Escallops of Oysters, Oysters Baked with Fine Herbs, Small Oyster Pies, Raw Oysters, Oysters Baked in a Form, Oysters Stewed with Champagne, Oysters Baked with Cheese, Fried Oysters and Pickled Oysters. A later course included Aspics of Oysters in a Form of Jelly.
Heaven To A P.O.W.
S.B. Nelson’s 1894 History of Hamilton County recounts the tale of Columbus Bennett, a school teacher in Anderson Township who enlisted early in the Civil War. He served with distinction for several years until captured by the Confederates. Eventually paroled, on reaching Union territory the famished prisoner consumed his “first square meal in eight long months, consisting of thirteen dozen raw oysters.” He survived to teach another 30 years.
Romance On The Half-Shell
The Enquirer [2 December 1874] recounts local speculation about William “Billy” Stolpp, the keeper of an oyster house at 159 West Fourth Street, and his extended trip to Baltimore. His friends and customers assumed his long absence involved acquiring a stock of fresh bivalves for his shop. In fact, Billy soon returned to Cincinnati with his new bride, the former Miss Lizzie Evans, of Baltimore, whom he had wed in that city.
Six Words And $700 Created A Legend
James A. “Jimmy” Shevlin was no dummy. He was working as a bank teller when he noticed the substantial and regular deposits from the Central Oyster House on Sixth Street. “There’s money in that game,” he said and borrowed $700 to open his own oyster house on the same block. Jimmy’s advertising slogan was, “If it swims, I have it,” and Shevlin’s Oyster & Chop House became a hangout for Democratic politicians and celebrities of the baseball, boxing and horse-racing worlds.

Oysters Paved Cincinnati Roads
The WPA “Guide to Cincinnati” reports that, in the 1880s, Boudinot and Wardall avenues in Westwood were part of what was known as Shell Road. “The story goes that one winter a landowner sent his hired man almost daily to Cincinnati hotels and restaurants – to obtain wagon loads of oyster shells. These shells were then scattered over the roadway. Horses’ hoofs ground them fine and created a shining white roadbed.”
Pushcart Deliveries
If Cincinnatians didn’t feel like taking a streetcar to their favorite restaurant or walking to the local fishmonger, they could just wait until the oyster hawker pushed his wagon past their residence. In the 1880s and 1890s, Cincinnati streets were crowded with pushcart merchants offering to mend umbrellas, sharpen knives and scissors, grind some fresh mustard, slice watermelon, shovel coal and, yes, shuck a dozen oysters from an ice-laden cart.
Queen City Condiments
No matter how Cincinnati diners ordered their oysters, whether fresh out of the shell, or steamed, or breaded and fried, they usually added some sort of flavoring. If the condiment of choice was a hot sauce, odds are it was brewed right here in the Queen City. Two brands of locally concocted chili sauce in particular, Snider’s (1900) and later Frank’s (1918) had wide distribution outside the Tri-State region.
The Pig Is Still King In Porkopolis
A 1905 “Dictionary Of Slang And Colloquial English” by John Farmer and William Henely defined “Cincinnati Oyster” as “a pig’s trotter,” in other words, a pig’s foot. The prevalence of pigs in the Queen City inspired many saloons to offer pigs feet as a regular component of their free lunch buffets.
Blame The Kaiser
World War I did nothing to abate Cincinnati’s hunger for oysters, even though wartime conditions hiked the cost of their favorite bivalve. In 1917, most Cincinnati oyster houses raised the price of oyster stew from 20 cents a bowl to 25 cents. Restaurateurs blamed the war and the customers blamed the Kaiser for starting the conflict.
Oysters For The Jury
Among the most sensational trials in Cincinnati history was the land-scam scandal of Roy Van Tress. At the conclusion of the court proceedings, resulting in Van Tress being sentenced to federal prison, the court received a bill of $848.46 from the Havlin Hotel for housing the jury, and a bill for $1383.75 from Shevlin’s Oyster House for feeding them. At that time, an oyster dinner with all the trimmings cost about 35 cents. That’s a lot of oysters!
Free Oysters For Life (Version 1)
In addition to newspaper reports, there are witnesses who attest that William Whipple Symmes, great-grand-nephew of John Cleves Symmes and prominent Cincinnati attorney, earned free oysters for life at the Central Oyster House. In one version, reported by Alfred Segal in the Cincinnati Post [22 June 1946], Jacob Rosenfield, the proprietor, realized that Symmes had been a regular customer for 30 years and presented him with a free pass for the remainder of his days.
Free Oysters For Life (Version 2)
Another Post columnist, Si Cornell, reported [16 March 1971] a different rationale for the free oysters, and cited W.W. Symmes’ law partner, William Busch, as the source. According to Busch, Symmes heard that Cincinnati was paralyzed by an “oyster scare” – rumors that oysters “weren’t much good and maybe worse.” Symmes contacted the Central Oyster House and offered to sit in the front window, eating Jacob Rosenfield’s oysters for everyone to see. Business picked up and the proprietor repaid his customer with “on-the-house” oysters ever after.
Still A Lot Of Oysters
Jacob Rosenfield’s old Central Oyster House was demolished in 1958 to make way for the new Federal Building on Government Square. The owner at the time, Rosenfield’s grandnephew Jake Spicer, proclaimed that the Central Oyster House would reopen nearby. Business was too good to close – averaging 4,000 hungry customers a day. One of Spicer’s employees calculated that she had served 32,260,000 breaded and fried oysters during her 40 years at the restaurant.
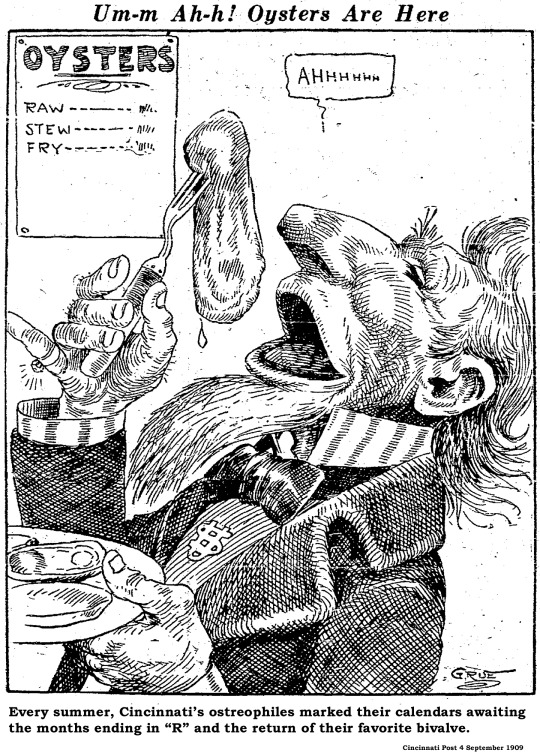
#cincinnati oysters#cincinnati food#william whipple symmes#w.w. symmes#balthazar roth#fanny trollope#jacob rosenfield#jimmy shevlin#james a. shevlin
7 notes
·
View notes
Text
1130 AD: Slaughter at Stracathro
(Detail of Angus from Robert Edward’s map of 1678- Stracathro can be seen north of Brechin on the banks of the Esk. Clicking on the image should make it larger. Reproduced with the permission of the National Library of Scotland)
In the year 1130, an army led by Angus, ruler of Moray, was defeated by forces loyal to David I, King of Scots, at the Battle of Stracathro. Although this engagement was recorded by a wide variety of medieval chroniclers and historians, few provide any details about the course of the battle or its background. Even the exact date is unclear. Nonetheless, Stracathro is often seen as a pivotal moment in the relationship between the powerful lords of Moray and the developing kingdom of Scotland, and an important flashpoint in the domestic politics of David I’s reign.
To make sense of the various surviving accounts of this battle, it is necessary to give some background information on Angus of Moray’s status. In the eleventh and twelfth centuries, ‘Moray’ covered a much larger area than it does now. A territory which stretched from the north-east to Ross, its rulers often found themselves in competition with the neighbouring jarls of Orkney and the kings of Alba, the latter of whom were then expanding their territory to include Strathclyde and Lothian south of the Forth, forging what we would now recognise as the kingdom of Scotland. However it is unclear whether Moray’s lords were independent rulers or regional lieutenants of the kings of Alba. The current academic consensus seems to be in favour of the latter, with some historians calling the rulers of Moray ‘mormaers’ (literally ‘great steward’ but often seen as equivalent to ‘earl’). Nevertheless Moray’s medieval inhabitants may well have seen things differently. At any rate, the rulers of Moray were clearly powerful figures in the north, with a close (if often fraught) relationship with the rulers of what we now call Scotland.
This closeness increased in 1040 when Moray’s ruler, Mac Bethad Mac Findlaích (Shakespeare’s ‘Macbeth’) seized the throne of Alba. Mac Bethad had claimed Moray after his cousin Gillecomgain burned to death in 1032. He had also swiftly married Gillecomgain’s widow Gruoch* who was a granddaughter of Kenneth III, king of Alba. Some years later, Mac Bethad defeated the then king of Alba, Duncan I, in battle near Elgin, and claimed the throne of Alba. He ruled for seventeen years before his own death at Lumphanan in 1057, following his defeat by forces loyal to Duncan’s son Malcolm III. Mac Bethad was briefly succeeded by his stepson Lulach ‘fatuus’ (‘the simple’), son of Gillecomgain and Gruoch, before Lulach too was killed in 1058 and Malcolm III succeeded in wresting control of Scotland...
(The Laich of Moray in the Blaeu Atlas of 1654. Reproduced with the permission of the National Library of Scotland)
(The shire of Moray is highlighted in blue and Angus (Forfarshire) in red. The old county system was only beginning to emerge in David I’s reign, and Moray in particular referred to a much larger province than shown here. The black spot shows the general location of Stracathro- I am no cartographer however, so this is only a rough guide. Template Source).
No more kings of Alba would be drawn from the house of Moray after Lulach’s death. A short conflict between Malcolm III and Lulach’s son Máel Snechta did break out in 1078: Máel Snechta got the worst of it but may have reached an agreement with Malcolm, since his kinsmen continued to rule in Moray for some decades. After this no serious challenges came from Moray for over fifty years until 1130, when another descendant of Lulach- his daughter’s son Angus- was ruler of the province.
Although we know something of his maternal ancestry (his father is a complete mystery), Angus of Moray is still a rather obscure figure. Late mediaeval Irish annals call him ‘rí’ or ‘king’ of Moray. Conversely, contemporary Anglo-Norman sources, as well as the Chronicles of Melrose and Holyrood, and late mediaeval Scottish historians like John of Fordun, all use the Latin word ‘comes’, which implies that they saw Angus’ position as roughly equivalent to that of a count or earl. Some bias is to be expected from Anglo-Norman sources since they usually favoured the descendants of Malcolm III and St Margaret over other branches of the royal house. Nonetheless we lack convincing evidence that the early twelfth century rulers of Moray controlled an independent kingdom, though they might perhaps have been ‘subkings’. We do know that Angus had a reasonably good claim to rule over both Moray and Alba, and the men of Moray were clearly willing to support him in this. And yet there had been no recorded conflict for over fifty years, so why did Angus choose to make his move in 1130?
Perhaps the answer can be found in the internal politics of the Scottish royal house. By 1130, David I, the youngest son of Malcolm III by his second wife Margaret of Wessex, had worn the title ‘King of Scots’ for six years. Although history remembers David as an impressive and innovative monarch- one of those kings who ‘made’ Scotland- in the early years of his reign his power seems to have been centred on the southern provinces of Lothian and Strathclyde. His control of ‘Scotia’ or Alba- the traditional heartland of the kingdom north of the River Forth- was less certain, and he must have seemed a very distant figure in a place like Moray. He also had to contend with rivals for the throne, like Malcolm, the son of David’s older brother and predecessor Alexander I. Described by the contemporary Anglo-Norman chronicler Orderic Vitalis as illegitimate, in an age when this did not yet disqualify a man from kingship, Ailred of Rievaulx later called Malcolm, ‘the heir of his father’s hatred and persecution’.* He may have opposed his uncle David at the outset of the reign, though if so he was plainly unsuccessful. This was not to be the last of Malcom’s intrigues however, since he pops up again a few years later in the company of Angus of Moray, taking part in the invasion of Alba in 1130. Perhaps then Malcolm’s appearance in Moray meant that he was able to convince Angus to support his claim and that this provided the impetus for the invasion. However it must be said that, in general, Angus is presented as the real leader of the campaign. Most sources do not even seem to think Malcolm’s presence at Stracathro worth mentioning, while Orderic Vitalis wrote that Angus ‘entered Scotland with the intention of reducing the whole kingdom to subjection’, and merely notes that Malcolm accompanied the army.

(David I and his grandson Malcolm IV, in a twelfth century charter belonging to Kelso Abbey. Source- Wikimedia commons)

(The round tower at Brechin, a few miles south of Stracathro, was likely constructed in the twelfth century, if not earlier. It is one of only two such round towers in Scotland)
It is also worth bearing in mind that, at the time of the invasion of Alba, David I was probably hundreds of miles away in the south of England, attending the court of his brother-in-law King Henry I. Although David’s relationship with the English king had proven useful on many occasions, this time it might have provided Angus and his allies with the perfect opportunity to revolt. Perhaps his absence also provided motive: later twelfth century kings of Scots would occasionally face armed opposition to their prolonged absences from the realm, and it is possible that Angus sought to capitalise on any discontent. Whatever the ultimate cause of their revolt, the year 1130 saw Angus and Malcolm march south with an invasion force which is said to have been 5,000 strong.
Contemporary sources do not tell us much about the course of the campaign. Only the late fourteenth century historian John of Fordun, who hailed from the Mearns himself and probably drew on earlier sources, gives a location for the sole recorded battle- Stracathro, near Brechin in Angus. This suggests that Angus of Moray’s army either headed south by one of the tracks over the Grampian mountains or, perhaps more likely, travelled east in the direction of Aberdeen and from there made its way down the low-lying strip of land between the Mounth and the coast. This last route would have covered roughly similar terrain to the modern A90 road and, although the landscape of long rolling fields sloping away towards the blue foothills of the Mounth in the west may have looked very different in the twelfth century, its strategic value for a mediaeval army on the move is readily apparent. The Romans had already marched across this ground a thousand years earlier, leaving the remains of a camp at Stracathro, and the conquering forces of Edward I of England would later follow a similar route north in 1296. It is also clear that, despite the sparse details given in contemporary sources, and despite David I’s posthumous legacy as a strong monarch, the 1130 invasion represented a serious crisis. In the absence of any recorded opposition, Angus and his supporters had been able to overrun the fertile east coast of ‘Scotia’, not far from the Tayside heartlands of the kingdom, and only forty miles or so from the traditional coronation site at Scone.
The men of Moray were only brought to a halt when King David’s constable Edward, son of Siward, hastily assembled an army and cut Angus’ force off a few miles north of Brechin. Orderic Vitalis, the contemporary writer who describes the battle in the greatest detail, tells us little about Edward other than that he was ‘a cousin of King David’ and the son of Siward who, according to various translations, was an ‘earl’ or ‘tribune’ of Mercia. Since his name and paternity indicate that he was of English stock, it is possible that Edward was one of the king’s maternal cousins, but theories abound as to his exact identity. Previously, several historians accepted the theory that he was the son of Siward Beorn (the earl of Northumbria who fought against Macbeth) and thus an uncle of David I’s queen Matilda. However this does not really tally with the few details Orderic provides, and any son of Siward Beorn would likely have been in his seventies in 1130. More recent writers, including David I’s most recent academic biographer, favour Ann Williams’ identification of Edward as a son of Siward, son of Aethelgar, a Shropshire thegn and therefore both of Mercian descent and, like David, a great-great grandson of Aethelred the Unready.
(View of Stracathro and the surrounding country in James Dorret’s map of 1750. I have coloured the kirk of Stracathro in red so it can be spotted more easily; again clicking on the image should expand it. Reproduced with the permission of the National Library of Scotland)
The royal army clashed with Angus and his men at Stracathro. No source gives a blow-by-blow account of the battle but the result was clear. In a rout which the Irish Annals of Innisfallen described as the ‘Slaughter of the men of Moray in Scotland’**, Angus and most of his force were killed. We should be wary of mediaeval chroniclers’ tendency to play fast and loose with numbers, but the language which all sources use about the engagement indicates that the death toll was high, with the late mediaeval Annals of Ulster even claiming that as many as 4,000 of the men of Moray were killed- 80% of the force which Orderic Vitalis claimed Angus was able to put into the field. The Annals of Ulster also claimed that a thousand of the men of Scotland (or ‘alban’) died, but this number was later corrected to one hundred. Leaving the chroniclers’ suspiciously exact death tolls aside, it is clear that the battle of Stracathro was a catastrophe for the Moravians, and a blood-bath from which Angus’ co-commander Malcolm, the son of Alexander, was very lucky to escape. Fleeing soldiers from Angus’ shattered army were then chased back to Moray by the triumphant Edward and the Scots, who promptly established control over the province.
Both mediaeval chroniclers and more recent historians have traditionally made this annexation of Moray following the battle seem very easy. As Robert de Torigni neatly summed it up, ‘Angus, the earl of Moray, was killed; and David, the king of Scotland, held the earldom thenceforward’. Now the undisputed overlord of Moray, David I is then supposed to have set about a comprehensive programme of ‘feudalisation’, complete with reformed monastic orders, a reorganised diocesan system, royal burghs for controlling trade, and, of course, a new settler nobility. However, David’s most recent academic biographer, Richard Oram, has argued that this feudalisation of Moray may have been a slower process than is often implied, and that it took some time for David and his supporters to establish complete control over the old lordship. Indeed, although there was to be no more trouble from Moray until the reign of David’s grandson King William, the fact that rivals for the Scottish throne were still able to draw considerable support from the native nobility of the province in the late twelfth and early thirteenth centuries could indicate that the post-Stracathro reorganisation was not so complete as some writers have assumed.
Stracathro is now a quiet place. A century and a half after the battle the area witnessed another, less bloody, defeat when John Balliol and his council negotiated with the triumphant Edward I of England from the kirkyard of Stracathro in July 1296. But other than this Stracathro is probably best known for its community hospital and a Victorian walled garden. The Battle of Stracathro is not exactly the most famous event in the annals of Scottish history. In a county that is otherwise littered with carved stones which allegedly commemorate ancient battles, few traces of the twelfth-century skirmish remain. Two mounds near Ballownie farm used to be pointed out as the alleged burial site of the slain, and certain internet etymologies claim that the nearby place name ‘Auchenreoch’ can be interpreted as deriving from a term meaning ‘the field of great sorrow’***. But otherwise the battle of 1130 has not left much of a mark in the landscape. Modern perceptions of the battle are also influenced to a great extent by the accounts of Anglo-Norman chroniclers, who may well have downplayed the threat which Angus of Moray (and other twelfth century rivals for the throne) posed to the descendants of Malcolm III and St Margaret. Nonetheless the slaughter at Stracathro is worth commemorating: had the battle gone the other way, Scotland might have been a very different place today.

(Stracathro Mansion is not necessarily on the site of the battle, and the landscape has changed considerably in nine hundred years, even down to the way fields are ploughed. However this may at least give an idea of the surroundings of the north part of Angus, with the Mounth in the background. Reproduced under the Creative Commons License (source here) since I’m limited in the photos I can take personally right now for obvious reasons).
Notes:
* Everybody’s favourite ‘Lady Macbeth’
**Not to be confused with Malcolm MacHeth
*** The original Irish says ‘Albain’
**** Though it must be said, I have my doubts
Selected Bibliography:
“The Ecclesiastical History of England and Normandy”, by Orderic Vitalis, Vol. III, translated by Thomas Forester
“Early Sources of Scottish History”, ed. A.O. Anderson
“Rerum Hibernicarum Scriptores”, vol. 2, ed. Charles O’Conor
“Annala Uladh”, vol. II, edited and translated by B. Mac Carthy
“Chronicle of Melrose”, and the “Chronicle of Holyrood” trans. Rev. Joseph Stevenson in ‘The Church Historians of England’, vol. IV
“Scottish Annals From English Chroniclers”, ed. A.O. Anderson
“John of Fordun’s Chronicle of the Scottish Nation”, ed. W.F. Skene and trans. Felix Skene
“Kingship and Unity: Scotland 1000-1306″, G.W.S. Barrow
“The Kingship of the Scots”, A.A.M. Duncan
“Domination and Lordship: Scotland, 1070-1230″, Richard Oram
“David I”, Richard Oram
“’Soldiers Most Unfortunate’: Gaelic and Scoto-Norse Opponents of the Canmore Dynasty, c.1100-c.1230”, R. Andrew MacDonald
“Companions of the Atheling”, G.W.S. Barrow in ‘Anglo-Norman Studies 25: Proceedings of the Battle Conference 2002′
#Scottish history#Scotland#British history#battles#medieval history#twelfth century#historical events#1130s#David I#Angus of Moray#Mediaeval#Middle Ages#High Middle Ages#warfare#Malcolm son of Alexander I#Moray#mormaer of Moray#Macbeth#Lulach (d. 1058)#Mael Snechta of Moray#Malcolm III#Malcolm Canmore#House of Canmore#Angus#Stracathro#Battle of Stracathro#Forfarshire#north-east
24 notes
·
View notes
Text
Near Field Communication to Dominate India Hardware Wallet Market through FY2027 – TechSci Research
Surge in the digitization process and the growing proliferation of smart devices is expected to drive the demand for India hardware wallet market in the forecast period.
According to TechSci Research report, “India Hardware Wallet Market By Connection Type (Near Field Communication, USB and Bluetooth), By Distribution Channel (Online and Offline), By End-User (Capital Market, BFSI (Excluding Capital Market), Real Estate and Others), By Region, Competition Forecast & Opportunities, FY2027”, the India hardware wallet market is expected to witness steady growth for the next five years. A hardware wallet can be defined as a kind of cryptocurrency wallet and is made to store private keys in a secure encrypted hardware device. Hardware devices are not affected by the attack of viruses or other cyber attacking computer viruses. Hardware wallets allow the storage of multiple currencies at the same time as they take up very little storage space. Every transaction is verified with the hardware device which makes it less prone and vulnerable to cyber fraud. The hardware wallet devices use technologies such as Bluetooth and USB, near field communication, among others to make the connection with other electronic devices. There has been a rise in the adoption of cryptocurrencies by consumers as they are a convenient, fast, and secure way to pay for goods. Cryptocurrencies can be used directly without the need for a banking license and eliminate the traditional banking system which is the major reason considered for the high demand for hardware wallets. Hardware wallets provide enhanced security by minimizing data threats. The surge in the adoption of digital technology across various prominent verticals and the rising demand for online transaction is influencing the growth of the market.
The COVID-19 outbreak across the world which has been declared as a pandemic by the World Health Organization has affected several countries adversely including India. Leading authorities of India imposed lockdown restrictions and released a set of precautionary measures to contain the spread of novel coronavirus. Due to imposition of strict regulations and policies by leading authorities, the business had to suffer huge losses. Manufacturing units were temporarily shut down and the shortage of workforce at the manufacturing plants was observed as the workers moved back to their native places. Disruption in the supply chain was observed which led to the lack of availability of raw materials, skilled workforce, and project delays.

However, the rise in concerns regarding data security and privacy of cryptocurrency may hamper the hardware wallet market growth.
Browse XX Figures spread through XX Pages and an in-depth TOC on “India Hardware Wallet Market”.
https://www.techsciresearch.com/report/india-hardware-wallet-market/7800.html
India hardware wallet market is segmented into connection type, distribution channel, end-user, regional distribution, and company. Based on connection type, the market can be bifurcated into near field communication, USB and Bluetooth. The near field communication segment is expected to account for a major market share of the hardware wallet market, FY2023F-FY2027F. The use of near field communication technology provides the storage facility which allows the flexible usage of cryptocurrency. The use of this technology enables consumers to use cryptocurrency as the normal mode of payment by connecting it with mobile applications. The transaction can take place even in the absence of the internet using near field technology which depends on the type of payment request. Based on the end-user, the market can be divided into capital market, BFSI (excluding capital market), real estate, and others. The capital market segment is expected to hold a major market share in the next five years owing to the rise in the market investments and huge revenue generation through them.
Unocoin, WazirX, Coinbase, Exodus, Guarda, Ledger, Trezor, Sugi, KeepKey LLC, BitBox Limited are the leading players operating in India hardware wallet market. Manufacturers are increasingly focusing on research and development process to fuel higher growth in the market. To meet evolving customer demand with respect to better efficiency and durability, several hardware wallet manufacturers are coming up with their technologically advanced offerings.
Download Sample Report @ https://www.techsciresearch.com/sample-report.aspx?cid=7800
Customers can also request for 10% free customization on this report.
“High-end investments by the major players for invention of new technology is expected to fuel the growth of the hardware wallet market in India in the next five years. The development of a non-custodial wallet, and wireless hardware wallet aiming to simplify the cryptocurrency transactions, coupled with the availability of a diverse variety of hardware wallets based on the consumer needs and requirements in the market is bolstering the market growth. The adoption of advanced technology by the major companies such as blockchain technology to offer higher security and ease the transactions relating to cryptocurrency is facilitating the growing demand for e-commerce platforms, which is further expected to propel the hardware wallet market growth till FY2027F,” said Mr. Karan Chechi, Research Director with TechSci Research, a research-based global management consulting firm.
According to TechSci Research “India Hardware Wallet Market By Connection Type (Near Field Communication, USB and Bluetooth), By Distribution Channel (Online and Offline), By End-User (Capital Market, BFSI (Excluding Capital Market), Real Estate and Others), By Region, Competition Forecast & Opportunities, FY2027” has evaluated the future growth potential of India hardware wallet market and provided statistics & information on market size, shares, structure and future market growth. The report intends to provide cutting-edge market intelligence and help decision makers take sound investment decisions. Besides, the report also identifies and analyzes the emerging trends along with essential drivers, challenges, and opportunities in the India hardware wallet market.
Browse Related Reports
Global Hardware Wallet Market By Connection Type (Near Field Communication, USB and Bluetooth), By Distribution Channel (Online and Offline), By End-User (Capital Market, BFSI (Excluding Capital Market), Real Estate and Others), By Region, Competition, Forecast & Opportunities, 2016-2026
https://www.techsciresearch.com/report/hardware-wallet-market/7557.html
Thailand Managed Security Services Market By Security Type (Network Security, Endpoint Security, Application Security, Cloud Security, Others), By Deployment Mode (On-Premise, Cloud), By Organization Size (Large Enterprise, SMEs), By End User Industry (BFSI, IT & Telecommunication, Energy & Utilities, Healthcare, Manufacturing, Government & Defense, Others), By Region, Competition, Forecast & Opportunities, 2016-2026
https://www.techsciresearch.com/report/thailand-managed-security-services-market/1430.html
Contact
Mr. Ken Mathews
708 Third Avenue,
Manhattan, NY,
New York – 10017
Tel: +1-646-360-1656
Email: [email protected]
#India Hardware Wallet Market#Cybersecurity Market#India Hardware Wallet Market Size#India Hardware Wallet Market Share#India Hardware Wallet Market Growth#India Hardware Wallet Market Forecast#India Hardware Wallet Market Analysis
2 notes
·
View notes