#encryptions
Explore tagged Tumblr posts
Text









#trump#election 2024#us politics#privacy#social media#element#signal#mastodon#lemmy#bsky#bluesky#encryption#tor#tailsos
4K notes
·
View notes
Text
UPDATE! REBLOG THIS VERSION!
#reaux speaks#zoom#terms of service#ai#artificial intelligence#privacy#safety#internet#end to end encryption#virtual#remote#black mirror#joan is awful#twitter#instagram#tiktok#meetings#therapy
23K notes
·
View notes
Text
The three forms of unlimited decentralized storage
When researching ways to store files in a decentralized, location-independent manner, I came across IPFS, Swarm, and ZeroNet. These tools offer decentralized storage solutions that are secure and don't charge for storage as they use their users' computing resources. Upon initial review, these tools appear to be promising.

InterPlanetary File System (IPFS) is a decentralized file storage protocol that allows for unlimited data storage capacity. It is free and has no usage limits, and uses encryption to ensure that network content cannot be intercepted or manipulated during transfer. IPFS has authentication features that allow users to verify the integrity of network content before accessing it, preventing the spread of false or malicious content on the network. IPFS is considered secure because it is decentralized, uses encryption to ensure content privacy, supports authentication features, and has a large community of developers working to maintain network security. Access this tool at this link: https://ipfs.io/ or https://ipfs.tech/
Swarm is a decentralized file storage platform that promises to be resistant to censorship. It is free and has no usage limits, and uses a distributed architecture to store data redundantly at multiple points in the network, ensuring the system is resilient to failures and interruptions. The data is encrypted and divided into small fragments before being stored on the network. Swarm also offers cryptocurrency-based financial rewards to those who provide physical disk space for storage, making it more secure and functional as users have an interest in maintaining it. Its goal is to become a global hard drive. Access this tool at this link: https://ethswarm.org/
ZeroNet is a well-known platform for researching private networks and decentralization. It is free, has no usage limits, and allows for the creation and hosting of sites anonymously and securely. Users can set access permissions for each site or application they create. ZeroNet uses a distributed and encrypted storage system that allows for free and unlimited file storage. Decentralization makes it difficult for a malicious attacker to access or damage the data, and only the data owner has the decryption key. ZeroNet is also resistant to distributed denial-of-service (DDoS) attacks and has techniques to make users anonymous by hiding their IP addresses. Access this tool at this link: https://zeronet.io/
Decentralized storage services offer an alternative to centralized storage services. Personally, I prefer using peer-to-peer technologies to securely and privately store and share my files without relying on centralized servers. These tools are free and have no usage limits, and they offer encryption and redundancy features that ensure my data is safe and available. Each tool has its own features and benefits, and I choose the best option based on my specific needs and preferences. Decentralized storage tools are an attractive alternative for anyone who values privacy, security and autonomy in managing their digital files.
Please note that this is my personal opinion and should not be considered the only perspective. It is important to gather information and seek opinions from multiple sources before making any decisions.
#decentralized networks#decentralization#online privacy#storage#private files#personal data#anonymity#encryptions#cryptocurrencies#blockchain
0 notes
Text
Whumpee that deceives Whumper
They rack their brain to memorize every little movement, every indicator of Whumper's mood, every pattern. At some point, they even learn to predict Whumper.
They know what Whumper likes to see. They know what they want within a few minutes, what's going to happen to them. They're powerless to stop it.
Sometimes Whumper wants them to silently cry on the floor, so they do. It would be foolish not to conserve energy while they can.
Sometimes Whumper is already in a bad mood. They probe, both because the knowledge is invaluable and because then Whumper will take it out on them.
Whumpee has a little internal guide to how to take punishments. Begin as defiant, but still shake. Look like they're trying to conceal their fear. Gradually break. It starts off as a yelp or sob or whimper followed by an immediate insult, then Whumpee goes quiet for a bit until it's “too much,” begging quietly. And then it's as if a dam has been broken, frantically pleading for mercy, for a reprieve. They look at Whumper with wide, teary eyes, and both their true self and their facade just want it to stop.
Their cries turn quiet as their energy runs out, until they can't bear to look at anything. Their flinch at Whumper's hand on their chin doesn't need to be faked. Their distress is real, and they let themselves whimper. Whumper likes displays of exhausted weakness, it makes them feel as if they've won.
They lean into the little coos and pets Whumper gives after, trying not to gag. Alarms of panic ring through their head, and they acknowledge them.
It would be easier to lose themselves in the comfort after the torture. It would be so much easier to become a shell of a person. They already act like one. Why can't they give up?
The emotional exhaustion after they've been left alone. The dark quiet. Their steadying breath. The scent of both blood and anticeptic. The locked door. The pain.
They can escape once Whumper deems them broken enough to let out unsupervised. It's just a matter of time, just a matter of maintaining this act. A matter of trust from a sadistic torturer that keeps Whumpee in a basement for no reason other than their own pleasure.
They have to keep going.
#whump#whumpblr#whump prompt#whump scenario#whump inspiration#emotional whump#whump ideas#daffodil academy#walenty#walenty daffodil#shavit's prompts#smart whumpee#manipulative whumpee#liar whumpee#intimate whumper#this isn't really walenty tbh. their own whump is institutionalized and they have multiple whumpers + multiple whumpees in the story#plus they have a notebook they record all of this on. it's an original encryption!#but hey it gets rhe idea across#no daffodil taglist since this isn't actually daffodil content lmao#writing block is horrible :(
428 notes
·
View notes
Text
the wanted posters without the theraprism encrypted text ^-^ so now you can actually read them lol click here to see the encrypted poster
#my art#stanford pines#bill cipher#gravity falls au#fiddleford mcgucket#fiddleford hadron mcgucket#overlords au#gravity falls#video#the text at the bottom is more filler than anthing else but I tried to to make the “characteristics” and descriptions lore-accurate#triumvirate#truthfully i like the encrypted one more bc MY WRITING IS SO BACK T-T#i dont want ppl to be excited to read it and then its just meh
326 notes
·
View notes
Text
Media Preservation Monday
Yeah, yeah, as of this original post it's actually only Wednesday but hey, take this as a sign to take some initiative, and keep to it each Monday at minimum if you're actively writing!
What's Media Preservation Monday, you may ask?
MPM is your reminder to back up your writing at least three ways at least once a week or whenever you make major changes to your document(s).
Here's some incredibly easy ways to back up your writing:
One your Master Document(s), put a date on the file name, and every day you make changes, "Save As" the Document and change the date. Do this every time or day you make major changes.
Example: You start writing your Novella November Story on November 1st.
You name your master document "Novnov Project 11-01-2024"
The next day, you write some more, and at the end of your writing session, you go to save your document, and instead of simply hitting "Save" you choose "Save As" and save the new copy of the Document as "Novnov Project 11-02-2024".
You now have two copies of your project, and if you keep this up throughout the whole month, you will have a live snapshot of your writing progress.
Each day or after each major writing session, open up the folder containing your document, and back it up. The Easiest and simplest way to do this is to simply email it to yourself, but you can also create multiple backups by:
Save a copy of your dated Master Document(s) to different locations on your Hard-drive, to an external hard-drive, to a thumbdrive, etc.
If you're writing offline on a writing program like Libreoffice, upload a copy of your Master Document(s) to your preffered Cloud-based Writing Program of your choice.
Vice Versa: if you write on a Cloud-based writing program, download it to various offline-based locations.
Download the base document as well as download it as various ebook formats and send them to your ebook library on your phone or kindle or nook or reading app.
Make a personal discord server and upload the document/epub form of your Master Document(s) there [this is also a good way of making a kind of personal journal / diary etc]
Whatever you do, do not be complacent and assume nothing can happen to your writing. Back it up. Preserve it.
Don't have all of your hard work go down the drain because of one tiny unforeseen accident.
When it comes time to clean up your hardrive, always assume you don't have it backed up. Before deleting anything always take the time to copy it over to another physical drive or a cloud drive.
#media preservation monday#writing tips#writing advice#novella november#writing events#community events#don't lose everything because you're a kid in school with a school laptop#and the tech support people tell your parent to factory reset the laptop without explaining that will wipe everything#don't lose everything because a cat jumped on your computer desk and knocked your desktop to the ground#don't lose everything because someone tripped and threw a bucket of water over your computer#don't lose everything because you totally thought you have it saved in two locations and delete it only to realize that was all of it#I'm trying to think of more scenarios#don't lose everything because your computer got a virus and ransomeware encrypted all your documents#If you had to leave your home tomorrow without your computer would you have access to your writing?#If not BACK IT UP#It should be in at least two places on the cloud at minimum and preferably multiple places offline#as many backups as you can get
286 notes
·
View notes
Text
An adversarial iMessage client for Android
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
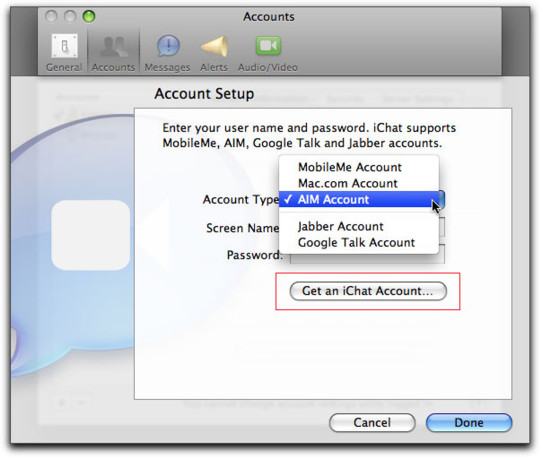
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Text

I made a tool that takes an image and visualizes how vulnerabilities in some encryption methods allow patterns to be discerned from it, even after encryption. I find the resulting effects to be very interesting!
if you want to try this yourself, you can download the tool here! https://espimyte.itch.io/eyecrypt
398 notes
·
View notes
Text

420 notes
·
View notes
Text
It's Just a Game, Right? Pt 8
Masterpost
"So I think they're using other languages," Tim says, the moment Bernard opens the door.
"Well hello to you too my beloved boyfriend," Bernard responds, kissing Tim on the cheek and pulling him into the apartment.
"Shut up," Tim says, following Bernard to the table. This is hardly the first time Tim has skipped past pleasantries like that, and Bernard seems to find it more amusing every time.
"Aw, I dunno if I can do that. I really like to talk to you," Bernard grins conspiratorially. "Plus, then I wouldn't get to tell you that you're half right."
"What do you mean?"
"Well, obviously other people noticed the comment, right?" Bernard, gestures towards the computer, where Tim can see the cryptic comment. It already has dozens of responses. "Mostly people are just freaking out about it, because this is like, our first instance of direct communication from them, but one of the people who saw it actually recognized what language it is."
"Just one?" Tim frowns.
"Yeah. It's called esperanto. I googled it and apparently it's a conlang from the late 1800s which is pretty cool. It was, like, invented to be kind of a universal language, I guess? It pulls from a lot of different languages, so that's why it looks like multiple languages."
"Huh."
"But! There's still the encoded portions to figure out, because the translation as-is doesn't really make any sense." Bernard scrolls and points to the translation that a commenter had offered. It reads To be fqzuhsx-ayccas is to be qtdkv-avnwkwkb; the veil afph-gqkduik but it is meant to igpmtwi-ocdq. Determination in the face of doubt.
"Huh," Tim studies the text, then notices something. "They've specifically encoded the verbs."
"Yep," Bernard shrugs. "I haven't tried anything for the encrypted stuff yet; figured i might as well wait for you."
"Okay, well I guess we start with the simplest? We know they've used caesar ciphers before, plus this is in response to what we did with the first caesar ciphers before, so we might as well try one of your decoder websites for that first."
"Seems reasonable," Bernard says, pulling up the website from before. He quickly copies the first word over and hits the button. "Well shit, that was quick."
"Only the first half, though." Tim mutters. "Do it to the rest of them." Bernard copies and decodes the rest. In short order, they have a the first half of each encryption decoded.
"To be gravity is to be orbit, the veil disk but it is meant to eclipse?" Bernard frowns. "That... doesn't make much more sense."
"What's up with the focus on astronomy, too."
"Oh, right, we haven't gotten that far yet. They keep referencing space stuff. There's like, a running theory about these messages being supposed to have come through a black hole?"
"Is that even possible? i thought black holes ate stuff forever."
"I dunno, I'm not really into space stuff. Besides it's like, sure there's evidence for it, and space seems to be narratively important? But the premise seems kind of contrived to me."
"You think they're doing something bigger than what everybody is seeing." Tim stares at the forum thread. If anything was going to give Bernard's theory some credence, it would be what literally just happened.
"Exactly." Bernard posted on a forum arguing that he thought the game ran deeper than people realized. And the creators, who so far hadn't interacted directly, had responded to that post, with a triple-encrypted message.
"Each shift was one further away than the last," Tim thinks rapidly. "It started with language, which could be either a part of the effort to encrypt it, or a part of the intended meaning. Possibly both. Then, they used caesar ciphers for the first layer of encryption, the same thing they used in their first post. How did they encrypt things in the second post?"
"I think I kind of mentioned it before, but the second post used a vigenere cipher. The names of the people in the first video were the keys, if I remember right."
"The first is the key to the second."
"What-"
"Take the second part and decode it with the first."
"Dude your mind is scary sometimes," Bernard laughs, but moves to do as Tim says, revealing the first encrypted word. "To be seen. That works..."
Tim starts writing down the full message, as Bernard decodes the rest. Finally, they have the full text of the message the creators intended to send.
"To be seen is to be remembered; the veil distracts but it is meant to hide. Determination in the face of doubt." Tim reads.
"Huh," Bernard says, leaning over to read it for himself. "Well, now we know what it says. Now we just need to figure out what that means."
#dp x dc#the one where the amity parkers make an arg#this part got long lol but i didnt wanna leave off in the middle of them solving the riddle#i put so much thought into this message and its encryption#its v hard to tell from the inside if youre actually making something that it's reasonable for ppl to solve#but luckily i get to just give you guys the solutions!#though as this goes on they are gonna get harder#eventually they wont be given and solved in the same post lol#so have fun looking forward to that i guess
174 notes
·
View notes
Text
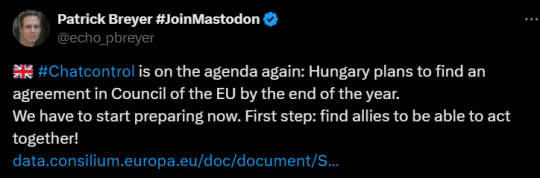
CHAT CONTROL BACK ON THE AGENDA

If you don't know what Chat Control is, this post sums it up well, as well as to why its a bad idea, but in a nutshell, European citizens will be forced to accept having their private messages/photos to be scanned by AI Or else they can't send images, texts, videos or links anymore. The council vote has been delayed a few days ago, but it has been put back on the agenda according to this tweet
US citizens should help us spread the word, too, because if it passes theres no doubt the US governement will take "inspiration" from Chat Control and pass a similar law in the US too. If you're in the EU, you can find your reps here (if you click on them it will redirect you to the countrie's respective website of reps ) https://op.europa.eu/en/web/who-is-who/organization/-/organization/COREPER/ Join our growing discord server ! We are organizing scripts and putting together ressources ! https://discord.gg/FPDJYkUujM

SPREAD THE WORD ! We can't allow this to pass !
#chat control#europe#internet censorship#bad internet bills#kosa#encryption#sorry im using the kosa tag since both of these have the same vein
245 notes
·
View notes
Text
🚨VERY IMPORTANT KOSA UPDATE🚨
After Tuesday's Judiciary hearing, Blumenthal and Hawley promised to try their best to bring KOSA to the floor. Cantwell has promised to sneak KOSA to the floor on a voice vote, like with what Hawley tried with the Restrict Act this past spring if you remember. We just need ONE senator to speak out. So right now, DON'T PANIC, SPEAK OUT.
As always, you can use https://www.badinternetbills.com/ to easily place your calls to everyone influential with a call script.
If you don't want to use that site
<https://docs.google.com/document/d/1IyBUe6frFGF44rJQU3TahZ5zyG3tC7jai_hPneAKlnM/edit>.
Share these resources.
Sign and share these open latter's and petitions.
We are targeting these senators:
Wyden (202) 224-5244
Markey (202) 224-2742
Welch (202) 224-4242
Booker (202) 224-3224
Padilla (202) 224-3553
Ossoff (202) 224-3521
Tester (202) 224-2644
Civil rights and free speech groups will be pushing to stop the legislation. But nothing matters like constituents calls — especially as we approach an election year.
Sources:
<https://twitter.com/evan_greer/status/1722985460056670401?s=46>
<https://twitter.com/mikestabile/status/1723018810976788911>
Remember, if we don't do anything now, it could be pushed for a floor vote without hesitation, it could be close to passing by the end of the year!!
Please stay calm and share, and try to call If you are able. ❤️
#stop kosa#stop internet censorship#pro privacy#pro encryption#stop anti encryption#kosa#kosa bill#lgbtq rights#lgbt#lgbt pride#lgbtq#lgbtqia#queer#queer pride#trans rights#trans#transgender#biseuxal#panseuxal#gay#gay rights#lesbian#wlw#mlm#queer nsft#lgbt nsft#the amazing digital circus#art#kill nerdy prudes#hatsune miku
680 notes
·
View notes
Text
Almost finished watching tfp and wanted to draw this guy

Meanwhile in the decepticon's warship..


#idk how the decepticon got the image but they somehow did lol#maybe its in the database they needed to encrypt and soundwaves like “oh this is interesting ill show it to meg”#megatron is feeling feelings#transformers#transformers prime#megatron#tfp megatron#tfp soundwave#also this is the first time i drew megatron hes way easier than op 😭#laksaeart
66 notes
·
View notes
Text
DPXDC Prompt #88
Danny and Damian are twins but they get separated at age 7, years later when they’re both 14 they both are going to high school and their schools decide to create a program where they wind up as pen pals to each other unknowing that they’re talking too each other as it’s been set up to be anonymous. Danny decides to take a leap of faith and encrypts a message about the media blackout around his town and how they’re overrun with ghosts and could use the Justice Leagues help through out all of his letters knowing that very few could actually understand it but he just felt so tired and this was the only way he could think to get any help for his town.
Damian just wonders who exactly his pen pal is to encrypt these letters like this.
#dp x dc prompt#dp x dc#dc x dp#danny fenton#danny phantom#writing prompt#poor danny#danny and damian are twins#Pen pal au#Even letters are searched before they’re sent#Media blackout Amity Park#Damian and Danny are pen pals#You can make it another bat but Danny being in the league was the only way that fit Danny knowing how to encrypt a message like this#Damian’s going straight to the Justice League after figuring it out#First names are used only so Danny and Damian can only speculate the last name of their pen pal
488 notes
·
View notes
Text
Ok so I'm finally watching Season 11 of The X-Files.
Episode 7 is called "Rm9sbG93ZXJz" which always bugged me cuz whenever anyone talked about it they called it the "sushi restaurant" episode. I avoided googling what the actual name meant cuz I didn't want spoilers.
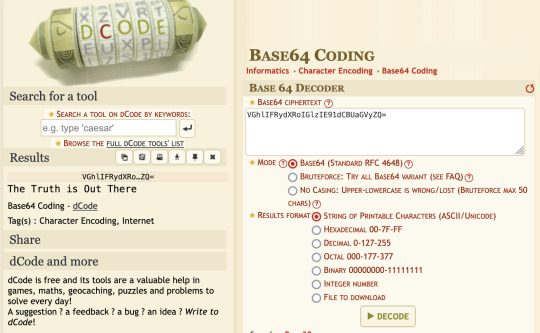
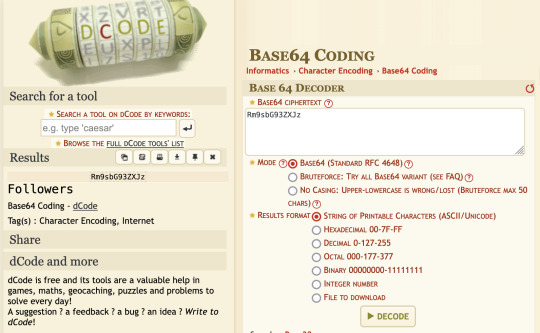
But while watching the episode, right after the intro credits they flash this "VGhlIFRydXRoIGlzIE91dCBUaGVyZQ=" on the screen. And that's when I realized the episode title must be encrypted since this second encrypted text was obviously placed where "The Truth Is Out There" is typically placed.
So I ran both of them through this online tool called dcode and figured out they used base64 encoding to encrypt their messages.
You can play around with this tool here: https://www.dcode.fr/base-64-encoding
If you don't want to know what the results are...don't continue reading...
Maybe they reveal all this in the episode, idk I literally paused it at the credits screen to post this after figuring it out lol
So don't hate on me if this is obvious or well known. I just figured it out now and thought it was fun.
Rm9sbG93ZXJz -> "Followers"
VGhlIFRydXRoIGlzIE91dCBUaGVyZQ= -> "The Truth is Out There"
If one of you can figure out this text I encrypted using a different encoding, I'll send you a funny meme as a prize:
☌⟟⌰⌰⟟⏃⋏ ⏃⋏⎅⟒⍀⌇⍜⋏ ⟟⌇ ⏃ ☌⍜⎅⎅⟒⌇⌇ ⏃⋏⎅ ⍙⟒'⍀⟒ ⋏⍜⏁ ⍙⍜⍀⏁⊑⊬.
#the x files#txf#x files#thexfiles#dana scully#fox mulder#mulder and scully#scully x mulder#gillian anderson#encryption#ciphers#s11#episode 7#sushi restaurant
106 notes
·
View notes
Text
WHAT THE FUCK IS THE BEAKER CASTLE EVEN - A SimPE Deep Dive
Alright, so after stumbling upon some of the Beta pics on the Russian TheSims.cc site and this analysis post about the Beaker mansion, I became deeply curious if some of this would be reflected in the lot relationships. After all, some characters like Viola, Kelly, on top of several others could be found when digging through the raw and somewhat encrypted code of lots.

By now it's pretty clear that the Beaker home once belonged to this dude and his army of girlfriends (definitely check out the post I mentioned earlier). On top of that Loki (and possibly Circe) seems to have gone through at least two iterations before eventually settling on their final forms.
And on top of that whenever you scan the mansion in a completely new game, you will find fingerprints of primarily deceased Sims everywhere!

Now to get to the Sim relationships on the lot...
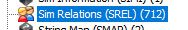
712 freaking Sim Relationships, all of which are unknown. Some of which still have stats set such as married, friends, relationship scores, etc. I tried comparing this to other lots in their neighborhood and NONE even come close. Both Olive and the Smiths have around 400. The other lots have below. And the only lots that are even a tad higher in this number are the Capps and the Summerdreams which makes sense when you realise that hood went through at least one other iteration before turning into Veronaville.
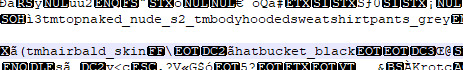
Now I wondered if the encrypted code (despite being very hard to read due to being partially encrypted) had any old Sim remnants left in there. And yep, several even. Many of which even have information such as their gender, hair, clothes and age in there. So lemme go over some of them:
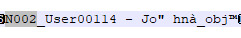

1. First one, a guy who's name is partially encrypted so it will never fully be visible. It's not Johnny cause Johnny also has his character file on this lot.
A male teen with brown hair who used to wear the "tmbodyhoodedsweatshirtboardshorts" + the "tmhairhatcap" hairstyle.
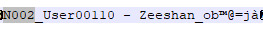
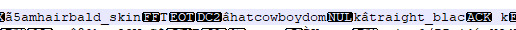
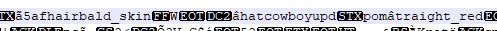
2. Second is another teen, this time by the name of Zeeshan. He had black hair, the bucket hat hairstyle and wore the hooded sweatshirt, except with pants this time around (and grey apparently?).
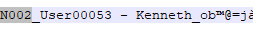
3. The third was an adult male Sim by the name of Kenneth with black hair. Based on his info he was likely meant to be a Gardener Sim.
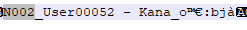
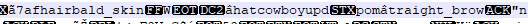
4. The fourth was one named Kana... Possibly a longer name cause once again the code becomes a bit shambled here. She too was meant to be a Gardener as seen by her outfit and hair data. Her hair would have been brown.
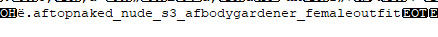
5. Elle, another female Gardener Sim, this one having red hair.
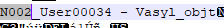
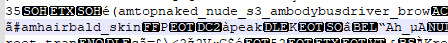
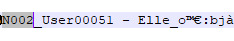
6. Vasyl, an adult male Sim who wore the busdriver outfit. Sadly his hair data seems to be blocked behind the code. For funsies I like to give the name to Bald Beta Loki, since he gives off that vibe. BUT, I think this was an NPC busdriver due to the outfit.

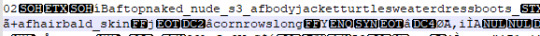
7. Joanne, an adult female Sim with an unknown hair colour in corn rows style and the classy afbodyjacketturtlesweaterdressboots. Sadly her ID is hidden behind the encrypted code, so it's hard to fully make out.
All of these Sims appear to be NPC/Townie Sims. None of them match ANYONE in the Beta pictures. And the current Townies/NPCs seem to have replaced them. Interestingly enough, those that were NPCs are still NPCs and those that were Townies are still Townies. Making me wonder if this is a thing that translates to other Sim IDs too. That Sims that were Townies in earlier iterations are still Townies in their new form. Same for NPCs and yep, Playables. This is merely an assumption I'm making on what I'm finding here, but if anyone can help research this further, that would be greatly appreciated, especially as this could mean the Viola ID may not belong to Viola Monty.
Viola is an odd case cause no outfit, hair or other data can be found in the lot file and she's only ever mentioned once in the context of lines filled with "sleep in pyjamas". But for now I cannot say anything with certainty unless more remnants of these old Sims could be found somewhere. OR, if these files could be read in its entirety which is quite difficult.
It's very hard to get a Sim ID attached to a lot (believe me I tried) and often times seems to rather happen accidentally than intentionally. Moving a Sim out or having a Sim die usually removes the data they once held to that lot. Good example is Loki in my current Strangetown who lived on this lot all of his life and when he died he had no remnants left on this lot.
REGARDLESS! The Beaker lot is ancient and seems to have been ground for a ton of testing, Sims and many more things. No wonder the Beakers got this home with its incredibly shady history. Half of the beta town was partying here!
#the sims 2#ts2#the beaker family#loki beaker#circe beaker#the sims 2 beta#beta sims 2#sims#sims 2#the sims#the encrypted code IS IN FACT Hex code btw#I figured this out when opening it in Visual Studio#main problem is that some of the hex is blank#meaning it’s unreadable at least in the file itself#SimPE manages to bypass some of it#but not all as we cannot find these Sim IDs in there
205 notes
·
View notes