#cyber security operations center
Text

Cyber Security Operations provide comprehensive protection through continuous monitoring, rapid incident response, and proactive threat management. Our services include 24/7 surveillance, vulnerability assessments, SIEM, and penetration testing, all managed by a dedicated Security Operations Center (SOC). We ensure robust security, compliance, and risk management to keep your organization safe from evolving cyber threats.
0 notes
Text
Security Operations Center (SOC) Analysts play a crucial role in identifying, analyzing, responding to and mitigating cyber attacks in an organization.
0 notes
Text
Congress is moving closer to putting US election technology under a stricter cybersecurity microscope.
Embedded inside this year’s Intelligence Authorization Act, which funds intelligence agencies like the CIA, is the Strengthening Election Cybersecurity to Uphold Respect for Elections through Independent Testing (SECURE IT) Act, which would require penetration testing of federally certified voting machines and ballot scanners, and create a pilot program exploring the feasibility of letting independent researchers probe all manner of election systems for flaws.
The SECURE IT Act—originally introduced by US senators Mark Warner, a Virginia Democrat, and Susan Collins, a Maine Republican—could significantly improve the security of key election technology in an era when foreign adversaries remain intent on undermining US democracy.
“This legislation will empower our researchers to think the way our adversaries do, and expose hidden vulnerabilities by attempting to penetrate our systems with the same tools and methods used by bad actors,” says Warner, who chairs the Senate Intelligence Committee.
The new push for these programs highlights the fact that even as election security concerns have shifted to more visceral dangers such as death threats against county clerks, polling-place violence, and AI-fueled disinformation, lawmakers remain worried about the possibility of hackers infiltrating voting systems, which are considered critical infrastructure but are lightly regulated compared to other vital industries.
Russia’s interference in the 2016 election shined a spotlight on threats to voting machines, and despite major improvements, even modern machines can be flawed. Experts have consistently pushed for tighter federal standards and more independent security audits. The new bill attempts to address those concerns in two ways.
The first provision would codify the US Election Assistance Commission’s recent addition of penetration testing to its certification process. (The EAC recently overhauled its certification standards, which cover voting machines and ballot scanners and which many states require their vendors to meet.)
While previous testing simply verified whether machines contained particular defensive measures—such as antivirus software and data encryption—penetration testing will simulate real-world attacks meant to find and exploit the machines’ weaknesses, potentially yielding new information about serious software flaws.
“People have been calling for mandatory [penetration] testing for years for election equipment,” says Edgardo Cortés, a former Virginia elections commissioner and an adviser to the election security team at New York University’s Brennan Center for Justice.
The bill’s second provision would require the EAC to experiment with a vulnerability disclosure program for election technology—including systems that are not subject to federal testing, such as voter registration databases and election results websites.
Vulnerability disclosure programs are essentially treasure hunts for civic-minded cyber experts. Vetted participants, operating under clear rules about which of the organizer’s computer systems are fair game, attempt to hack those systems by finding flaws in how they are designed or configured. They then report any flaws they discover to the organizer, sometimes for a reward.
By allowing a diverse group of experts to hunt for bugs in a wide range of election systems, the Warner–Collins bill could dramatically expand scrutiny of the machinery of US democracy.
The pilot program would be a high-profile test of the relationship between election vendors and researchers, who have spent decades clashing over how to examine and disclose flaws in voting systems. The bill attempts to assuage vendors’ concerns by requiring the EAC to vet prospective testers and by prohibiting testers from publicly disclosing any vulnerabilities they find for 180 days. (They would also have to immediately report vulnerabilities to the EAC and the Department of Homeland Security.)
Still, one provision could spark concern. The bill would require manufacturers to patch or otherwise mitigate serious reported vulnerabilities within 180 days of confirming them. The EAC—which must review all changes to certified voting software—would have 90 days to approve fixes; any fix not approved within that timetable would be “deemed to be certified,” though the commission could review it later.
A vendor might not be able to fix a problem, get that fix approved, and get all of its customers to deploy that fix before the nondisclosure period expires.
“Updates to equipment in the field can take many weeks, and modifying equipment close to an election date is a risky operation,” says Ben Adida, the executive director of the vendor VotingWorks.
Some vendors might also chafe at the bill’s legal protections for researchers. The legislation includes a “safe harbor” clause that exempts testing activities from the prohibitions of the Computer Fraud and Abuse Act and the Digital Millennium Copyright Act, and bars vendors from suing researchers under those laws for accidental violations of the program’s terms.
There is also a funding question. The SECURE IT Act doesn’t authorize any new money for the EAC to run these programs.
“I hope Congress accounts for the necessary funding needed to support the increased responsibilities the EAC will take on,” says EAC chair Ben Hovland. “Investments in programs like this are critical to maintaining and strengthening the security of our elections.”
Meanwhile, the bill’s prospects are unclear. Even if it passes the Senate, there is no sign of similar momentum in the House.
23 notes
·
View notes
Text
by Debbie Weiss
An Israeli cyber and national security expert has claimed that the exploding pagers carried by Hezbollah members in Lebanon, which left thousands wounded and killed at least nine people on Tuesday, were part of a sophisticated attack that was planned at least half a year before the war in Gaza erupted.
Dr. Eyal Pinko, a former navy commander and senior research fellow at the Begin-Sadat Center for Strategic Studies, dismissed theories that the blasts were caused by lithium batteries that were hacked to become overheated, and said that the nature of the wounds seen in footage emerging from Lebanon was consistent with those caused by explosives such as TNT and HTB.
“To get this kind of wound you need to have between one to two grams of type of explosives, which is not a big technological issue — you just need to open the beeper,” Pinko said during a briefing with reporters on Tuesday evening. He added that a stable explosive that wouldn’t detonate accidentally would have been inserted into the device, along with a small control mechanism capable of receiving remote commands via a call or page.
Such an operation would have required significant infiltration of Hezbollah’s communication systems, according to Pinko, and planting explosives in pagers would necessitate a serious breach of the supply chain. “This is an intelligence operation that was very well planned, prepared for more than one and a half years,” Pinko said.
Pinko alluded to the possibility of a coordinated effort, suggesting that Israel may not have acted alone if it was behind the attack in Lebanon, where Hezbollah wields significant political and military clout. He noted efforts by Germany, France, the US, and the UK to prevent escalation in the region.
Israel has so far been quiet about the explosions, but senior Lebanese officials have blame the Jewish state. So too has Hezbollah, which said Israel would receive “its fair punishment.”
14 notes
·
View notes
Text
🟡 Tuesday - events from Israel
ISRAEL REALTIME - Connecting to Israel in Realtime
❗️PARTNER CELL PHONE NETWORK.. was under possible cyber attack early this morning, some disruptions to service around 5:45 AM.
▪️ON THE FORMER ATTORNEY GENERAL.. Mandelblit turned to the court today to prohibit News 12 from publishing more recordings revealing the manipulations to get him into the job. The court will hold a hearing on the lawsuit against News 12.
▪️MT. HERMON SKI CENTER HIT.. A rocket hit was found in the Hermon site ski complex. Minor damage to property. The Hermon site has been closed since Oct. 7.
▪️TERROR STOPPED.. Shin Bet in cooperation with the IDF and the Israel Police, IDF and Shin Bet fighters arrested three terrorists from the village of Bnei Naim in the Hebron area, who were planning an attack in the immediate time frame. One was arrested on Route 6 yesterday in the afternoon and was transferred to the Shin Bet investigation. Following his interrogation by the Shin Bet, 2 more squad members were arrested at their home, with weapons found.
▪️JORDAN WARNS.. ”There are Houthis who come to Jordan as tourists and disappear in the territory (who may be preparing to attack Israel).” Similarly Houthis are in Lebanon, where they received entry visas through special permits that defined them as students.
▪️SYRIA.. Iran is significantly expanding its bases in Syria, mainly in central Syria.
▪️ICJ GENOCIDE CLAIM.. South Africa is surprisingly trying to drag out the submission of evidence against Israel claiming genocide in Gaza.
Nine months after filing the case with the Hague tribunal, South Africa is trying to postpone the date of its submission of evidence. The tactic of the South African state is an attempt to "bid time" with the understanding that it does not have evidence against Israel to prove genocide.
South Africa is obliged to submit its evidence in another month, on October 28, 2024, but it is trying to extend the deadline by several more months, hoping that in the meantime evidence will arrive from other places.
♦️GAZA.. IDF: fighter jets attacked central Hamas terrorists who were operating a command and control complex in the humanitarian area in Khan Yunis. (Enemy report) Heavy bombs penetrated bunkers above which were a number of tents in the area of the displaced people in Mawasi, leaving craters ten meters deep. 3 senior Hamas commanders were targeted.
.. Hamas officially denies the IDF spokesperson’s claims about the presence of "resistance operatives" at the site attacked last night in Muwasi, Khan Younis. According to Hamas, this is a lie intended to justify Israeli crimes.
♦️JERUSALEM.. (Enemy report) Heavy security activity in the Ras Hamees area of Shuafat, East Jerusalem this morning.
♦️SOUTHERN BORDER.. (Enemy report) At the Israel-Egyptian border, a report was received about IDF soldiers in a firefight near Bnei Netzer, it is possible that they are armed drug smugglers. 2 soldiers wounded.
♦️HEZBOLLAH.. IDF targeted buildings and demolished them by airstrikes in he towns of Ayta ash-Shab, Khiam, and Naqoura.
⭕HAMAS ROCKET at Kissufim, near Gaza town.
#Israel#October 7#HamasMassacre#Israel/HamasWar#IDF#Gaza#Palestinians#Realtime Israel#Hezbollah#Lebanon
13 notes
·
View notes
Text
John Nichols at The Nation:
Donald Trump has made no secret of his determination to govern as a “dictator” if he regains the presidency, and that’s got his critics warning that his reelection would spell the end of democracy. But Trump and his allies are too smart to go full Kim Jong Un. Rather, the former president’s enthusiasm for the authoritarian regimes of Russia’s Vladimir Putin, Turkey’s Tayyip Erdoğan, and Hungary’s Viktor Orbán suggests the models he would build on: managing elections to benefit himself and his Republican allies; gutting public broadcasting and constraining press freedom; and undermining civil society. Trump, who famously demanded that the results of Georgia’s 2020 presidential voting be “recalculated” to give him a win, wants the trappings of democracy without the reality of electoral consequences. That’s what propaganda experts Edward Herman and Frank Brodhead once described as “demonstration elections,” in which, instead of actual contests, wins are assured for the authoritarians who control the machinery of democracy.
The outline for such a scenario emerges from a thorough reading of Project 2025’s Mandate for Leadership, which specifically proposes a Trump-friendly recalculation of the systems that sustain American democracy. The strategy for establishing an American version of Orbán’s “illiberal democracy” is not spelled out in any particular chapter of Mandate. Rather, it is woven throughout the whole of the document, with key elements appearing in the chapters on reworking the Department of Homeland Security (DHS), the Federal Communications Commission (FCC), and the Federal Election Commission (FEC). In the section on the DHS, for instance, there’s a plan to eliminate the ability of the agency that monitors election security to prevent the spread of disinformation about voting and vote counting.
How serious a threat to democracy would that pose? Think back to November 2020, when Trump was developing his Big Lie about the election he’d just lost. Trump’s false assertion that the election had been characterized by “massive improprieties and fraud” was tripped up by Chris Krebs, who served as director of the Cybersecurity and Infrastructure Security Agency (CISA) in the DHS.
The Republican appointee and his team had established a 24/7 “war room” to work with officials across the country to monitor threats to the security and integrity of the election. The operation was so meticulous that Krebs could boldly announce after the voting was finished: “America, we have confidence in the security of your vote, you should, too.” At the same time, his coordinating team declared, “The November 3rd election was the most secure in American history.” This infuriated Trump, who immediately fired the nation’s top election security official.
In Mandate’s chapter on the DHS, Ken Cuccinelli writes, “Of the utmost urgency is immediately ending CISA’s counter-mis/disinformation efforts. The federal government cannot be the arbiter of truth.” Cuccinelli previously complained that CISA “is a DHS component that the Left has weaponized to censor speech and affect elections.” As for the team that worked so successfully with Krebs to secure the 2020 election, the Project 2025 document declares that “the entirety of the CISA Cybersecurity Advisory Committee should be dismissed on Day One.” The potential impact? “It’s a way of emasculating the agency—that is, it prevents it from doing its job,” says Herb Lin, a cyber-policy and security scholar at Stanford’s Center for International Security and Cooperation.
This is just one way that Project 2025’s cabal of “experts” is scheming to thwart honest discourse about elections and democracy. A chapter on public broadcasting proposes to defund the Corporation for Public Broadcasting as part of a larger plan to upend NPR, PBS, and “other public broadcasters that benefit from CPB funding, including the even-further-to-the Left Pacifica Radio and American Public Media.” More destabilizing than the total funding cut that Project 2025 entertains is a parallel plan to end the status of NPR and Pacifica radio stations as “noncommercial education stations.” That could deny them their current channel numbers at the low end of the radio spectrum (88 to 92 FM)—a move that would open prime territory on the dial for the sort of religious programming that already claims roughly 42 percent of the airwaves that the FCC reserves for noncommercial broadcasting. And don’t imagine that the FCC would be in a position to write new rules that guard against the surrender of those airwaves to the Trump-aligned religious right.
[...]
While project 2025 seeks to rewire the FCC to favor Trump’s allies, it also wants to lock in dysfunction at the Federal Election Commission, the agency that is supposed to govern campaign spending and fundraising. Established 50 years ago, the FEC has six members—three Republicans and three Democrats—who are charged with overseeing the integrity of federal election campaigns. In recent years, however, this even partisan divide has robbed the FEC of its ability to act because, as a group of former FEC employees working with the Campaign Legal Center explained, “three Commissioners of the same party, acting in concert, can leave the agency in a state of deadlock.” As the spending by outside groups on elections “has exponentially increased, foreign nationals and governments have willfully manipulated our elections, and coordination between super PACs and candidates has become commonplace,” the former employees noted. Yet “the FEC [has] deadlocked on enforcement matters more often than not, frequently refusing to even investigate alleged violations despite overwhelming publicly available information supporting them.”
John Nichols wrote in The Nation about how Project 2025’s radical right-wing wishlist of items contains plans to wreck and subvert what is left of America’s democracy.
See Also:
The Nation: June 2024 Issue
#John Nichols#The Nation#Project 2025#Donald Trump#Authoritarianism#FCC#FEC#Federal Elections Commission#Federal Communications Commission#Corporation for Public Broadcasting#Cybersecurity and Infrastructure Security Agency#Chris Krebs
19 notes
·
View notes
Text
Lately, the government and the top banks of Australia have been pushing for the eradication of payments by cash, leaving phone apps alone, and possibly a medical implant as well.

I have fought against it as best I can, buy there's not much I can do.
It's illegal to have large amounts of cash, and self defense is a crime, so storing at home is not really an option. Besides, I am a disabled pensioner, and the government decided long ago that going through the bank is mandatory.
Covid was the best opportunity they ever had to eliminate personal freedom - I mean, to force everyone to use insecure apps on insecure phones that had insecure operating systems on insecure hardware.
There were scandal when apps were exposed data harvesting, accessing information they didn't have the rights to, and even hacking the microphone and camera of the phone.
https://www.consumerreports.org/electronics-computers/privacy/how-to-protect-yourself-from-camera-and-microphone-hacking-a1010757171/
But the push to do the thing was relentless. You can't stop progress! Nobody else is complaining, the bank told me.
Except people do complain, helpless and hopeless. I worked in tech support, and would hear all day long the agony of those whose assets were cleaned out, and that was in the days of internet banking, when the scammer call centers of India were just a sparkle in Satan's Eye.
You see, the reason banks existed was that they took money in exchange for the service of PROTECTION.
Now, they take your money, and if you get robbed, that's a YOU problem.
And the government is backing them up. Remember the GFC, when most governments expressed their hatred of capitalism by backing banks no matter how badly they embezzled customers?
The Bank and the State had merged.
Mussolini's vision had succeeded.
Fascism took a century, but it in the end, it won. But I am not sure even the 1930s fascists could see this coming.
youtube
21 notes
·
View notes
Text
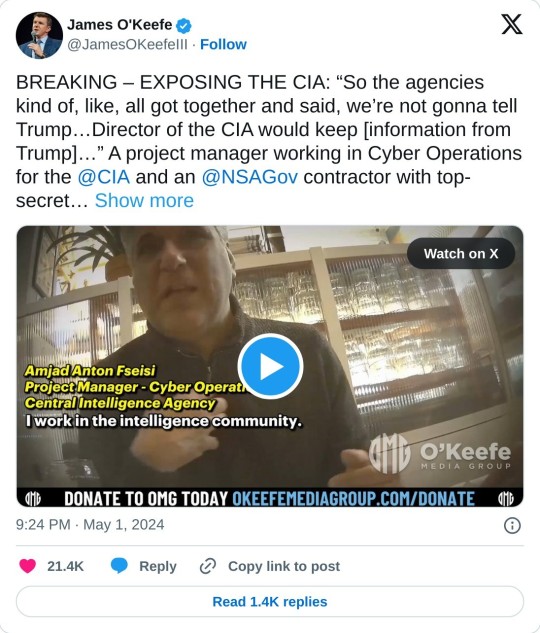
MASSIVE REVELATION! James O’Keefe Releases Undercover Video of CIA Contractor Admitting CIA Director Withheld Info from Trump and Spied on His Presidency
ames O’Keefe last Friday warned he was about to release the most important story of his entire career.
“I have evidence that exposes the CIA, and it’s on camera. I am working on releasing a story that I believe is the most important of my entire career,” O’Keefe said on Friday.
“Do you think it’s a coincidence that right at this moment I am subject to an endless series of attacks?” he said. “This is obviously a sophisticated information operation designed to stop me from releasing this story. I’m sure you recognize they are masters of using half-truths and innuendos to raise doubt against people who don’t deserve it. It’s meant to consume my time and energy and make me back down.”
“But I’m not going to let it work. Rest assured, nothing will stop me from releasing this story,” O’Keefe said.
O’Keefe Media Group on Wednesday released part one: Exposing the CIA: A project manager working in cyber operations told OMG’s undercover journalist that the Director of the CIA would keep information from Trump.
He also said the CIA spied on Trump’s presidency and is still monitoring him to this day.
“So the agencies kind of, like, all got together and said, we’re not gonna tell Trump…Director of the CIA would keep [information from Trump]…” Amjad Fseisi, a project manager working in Cyber Operations for the CIA with top-secret security clearance told an undercover journalist.
Amjad Fseisi said Trump is a “Russian asset” – “He’s owned by the f*cking Russians,” he told the undercover journalist.
Per James O’Keefe:
Amjad reveals to OMG’s Undercover American Swiper that intel agencies not only kept intelligence information from a sitting United States President and Commander-In-Chief, they also used FISA to spy on President Trump and his team and are still monitoring President Trump according to Amjad who says, “We monitor everything.” Amjad adds “we also have people that monitor his ex-wife. He likes to use burner phones” – information only an insider with access to highly sensitive information would state.
“We steal it [information]” and “We hack other countries just like that,” Amjad, who states he currently works on the CIA’s China Mission Center, explains how intel agencies obtain information. He also describes a broken intelligence system where “We don’t share information across agencies” because the CIA is “very reluctant” to share information with the “careless” NSA.
O’Keefe Media Group’s bombshell undercover footage supports earlier reports by investigative journalists Michael Shellenberger, Matt Taibbi, and Alex Gutentag that revealed how the American intelligence community illegally ran a spy operation against then-candidate Trump’s presidential campaign in 2016 and illegally acquired intelligence that was later used to justify the Federal Bureau of Investigation (@FBI) official probe, “Crossfire Hurricane,” which in turn led to Special Counsel Robert Mueller’s investigation that ultimately did not find evidence of Russia collusion by the 2016 Trump campaign.
Contractors like Fseisi hold the duty to withhold sharing confidential or national security information. In denying his statements, Fseisi may have realized he could be held liable for violating internal agency provisions and federal laws like the Executive Agency ethics provisions, which restrict what he may share with others outside of his contracted-to agency.
Additionally, any government worker or agency head who withheld information from a superior (i.e. President Trump) may violate: (a) obstruction of justice by deception (18 USC 1512); (b) conspiracy to obstruct (18 USC 371); and false statements (18 USC 1001). Agency regulations may also provide offenses related to insubordination, reflecting poorly on the agency in public, or misrepresentation or dishonesty.
When James O’Keefe caught up with Amjad Fseisi on the streets of Washington, D.C., Fseisi could not tell O’Keefe whether he had top secret clearance, denied making statements clearly caught on camera, and would not even confirm it was him on the video saying only “It looks like me.” When asked directly if he works at the CIA, Fseisi said, “I can’t tell you that.”
7 notes
·
View notes
Text
The job of a SOC Analyst
The #1 thing people ask me about is what I do for a job.
I'm a tier 1 SOC Analyst and I'm currently training to do some Cyber Threat Intelligence.
I will explain in detail what I do on a daily basis and why I've decided to do this job... And the negatives.
First of all, what's a SOC. SOC stands for "security operations center". It's a place (in my case virtual as I'm full remote) where a group of people, divided by experience and area of expertise, do the following:
Monitor the activities going on the customer's network or endpoints(= every device connected to the network);
Assess and mitigate alerts coming from the network and/or the endpoint of the client -> These tools send alerts that need to be evaluated and mitigated/responded in a certain amount of time (it depends on the SOC and the type of alert, generally I can assume an amount of time from 15 to 30 minutes per alert. Which is not that much;
Investigate cybersecurity incidents -> the SOC also analyses the kind of "incident" that happens in deep detail by analysing malware, spam emails, the behaviour of users and so on;
If the SOC is big/mature enough there could be some sort of prevention of cybersecurity issues, generally we talk about threat hunting (here for more information on that) and cyber threat intelligence (gathering information from various sources to produce a report about the potential attackers considering also the characteristic of the customer's company such as the size, the geographical area of operations, media exposure, geopolitical issues and what they do - doing this for a bank is different than doing it for a industry)
There are also other functions (such as we have a Security Architect that prepares a personalised solution for each client).
I know what you're thinking. But the AI...
No, they cannot do my job, as the ability of a human to notice patterns and correlate the information among various sources is unique. I memorised, with time, the usual activities my customers do, therefore I can interpret the user actions even with limited sources. And this is just one example.
Soc analysts are roughly divided in three "categories", always keep in mind that every SOC is different and has its own internal rules, that are not to be divulged. This is the rough division I've learned studying cybersecurity and NOT my organisation division.
Tier 1 Analysts are the one that monitors the traffic and activities I've mentioned before. They triage the alerts and if something deserves more investigation or can be discarded. They often perform simple actions of remediation of incidents.
Tier 2 Analysts are the ones that go deeper - they collect malware samples from the incident and analyse it, investigate and remediate more complex security incidents.
Tier 3 Analysts perform more active prevention duties like threat hunting and vulnerability assessments.
Some sources put intelligence activity on the tier 3, others consider it a different activity from the scenario I've described. If a SOC is big enough they might have their own intelligence team separated from the "regular" soc analysts. The rigidity of these roles can vary, as you probably got from my own duties.
On the top we have a SOC manager to coordinate the activities I've described and security architects that design the solution (although the deployment of these solutions can be delegated to the analysts, since we also have to monitor how well these perform).
All these people are usually referred as "blue teamers" btw, which are the ones that perform defensive actions.
A company can have a red team (basically they attack the customer to gain information that the blue team will use to improve their activities). I actually wanted to be a red teamer at first, since it's considered the "cooler" job.
Ok, got it. Now explain to me how you got there since I've never heard anything about this before.
I have a friend that's a system engineer and recommended this job to me.
I studies physics at university but I failed (in my country physics include some computer science classes btw) and I had some related experience I won't share for privacy reasons. No I'm not a criminal lol.
I then started studying - did a bootcamp and got a couple of certifications. Then I got my job.
However. Generally you get a degree in computer science or software engineering, and some universities offer cybersecurity degrees. Unfortunately I cannot tell you what to pick as every university has its own program and I cannot help you with that.
Certifications are a big part of my job unfortunately - mostly because due to how fast it goes you absolutely need to be "on top". It's annoying, yes, I hate it.
However. Consider that once you're hired you definitely will get them paid by your employer - at least in Europe this is on them(idk about the US), but you need some knowledge of cybersecurity to start.
Since some of them are stupid expensive I 100% recommend the compTIA ones. They're basics and respected worldwide. A+, Network+ and Security+ are basics, vendor neutral (which doesn't tie you to a particular "source", as every company works differently), and is relatively cheap (~300€).
Remember that I had previous experience so no one cares that I don't have a degree - I do however and I hope that in the future I will be able to "fix" this.
Great. How do I know if I'm good for this job?
This is on you. However:
One important thing if you don't live in an English speaking country is a good attitude towards foreign languages. I speak 5 for example, but it's an hobby I do since I was a teen;
Can you manage stress? A SOC is a fast paced environment, and you have a limited time to deal with whatever gets thrown at you. You have 15 to 30 minutes to deal with an alert and make a decision. Can you do that without panicking, crying or throwing a tantrum?
Are you a fast learner? You need to learn quickly how to do things, since the tools we use are quite complicated.
Are you willing to work on shifts, Saturdays, Sundays, festivities included? A lot of people can't cope with this and it's fine because it's a massacre. The job is so stressful to the point a lot of people leave cybersecurity because of it. Do not underestimate it, please.
How good are you at remembering random information and making correlations? Because I can remember random bits of information that no one ever thinks of it and it's one of my greatest strengths.
You need to do teamwork and be good with people, customers and so on - you have to explain complicated things you probably read in another language to people that don't know anything about what you do. It's more difficult than most people think.
Procedures are everything here - and for good reasons.
I think this is it.
Money.
USA avg salary: 74 307$ (Glassdoor)
France avg salary: 42 000€ (Glassdoor)
UK avg salary: 28 809 £ (Glassdoor)
There are random numbers I've found online(and with a lot of discrepancies). Consider that you MUST negotiate your salary, and that in certain places you get paid more if you work out of the usual 8-19 work shift. Obv since I live in a different place I cannot tell you if it's worth it - you do your own calculations.
But that's beyond the purpose of this post.
11 notes
·
View notes
Text
CBD Merchant Accounts Essentials: Secure and Efficient Processing
Article by Jonathan Bomser | CEO | Accept-Credit-Cards-Now.com

In the ever-evolving realm of e-commerce, payment processing stands as a cornerstone, a pivotal factor dictating the success of businesses in an increasingly digital marketplace. Especially for high-risk industries like CBD and credit repair, secure and efficient payment processing becomes not just essential but a strategic imperative. In this article, we'll delve deep into the essentials of CBD merchant accounts, shedding light on the significance of secure and efficient processing, empowering businesses to thrive even within high-risk niches.
DOWNLOAD THE CBD MERCHANT ACCOUNTS INFOGRAPHIC HERE
Understanding the Significance of Secure Payment Processing
In today's interconnected landscape, where cyber threats loom large, safeguarding sensitive payment information is paramount. CBD businesses, often categorized as high-risk, are particularly susceptible to fraudulent activities. This makes secure payment processing the bedrock of their operations. High-risk payment processing solutions provide cutting-edge encryption and fraud detection mechanisms, ensuring that both businesses and customers are shielded from potential breaches.
Navigating the High-Risk Landscape with Merchant Accounts
The term 'high-risk' might sound intimidating, but it doesn't have to be a roadblock. High-risk merchant accounts are specialized financial instruments that empower CBD and credit repair businesses to accept credit card payments with confidence. These accounts come with tailored features that suit the unique needs of high-risk industries, offering stability and reliability that traditional accounts often fail to provide.
The Dynamics of High-Risk Payment Gateways
A seamless transaction experience lies at the heart of customer trust and satisfaction. High-risk payment gateways are designed with precisely this objective. By enabling swift, secure, and user-friendly transactions, these gateways eliminate friction from the purchase process. This is crucial for CBD businesses aiming to establish credibility and nurture customer loyalty in an industry that is gradually gaining mainstream recognition.
CBD and Credit Repair: High-Risk Endeavors
CBD and credit repair, although distinct, share the tag of high-risk ventures. This label stems from factors such as regulatory uncertainties and a historical stigma attached to these industries. While it might be challenging to find traditional financial partners willing to support these businesses, high-risk merchant processing steps in as a beacon of hope. It not only provides access to financial tools but also enhances the reputation of these industries by facilitating transparent and secure transactions.
E-Commerce Integration and Payment Processing
In an era where digital storefronts are the norm, e-commerce payment processing takes center stage. For CBD and credit repair businesses venturing into the online realm, the ability to accept credit cards for e-commerce becomes a game-changer. High-risk e-commerce merchant accounts offer seamless integration of payment processing systems, making it convenient for customers to complete transactions and for businesses to manage their finances effectively.
Pioneering the Way Forward with CBD Merchant Accounts
Amid evolving regulations and shifting perceptions, CBD businesses are finding their footing. To do so effectively, they need a financial partner that understands their unique challenges and opportunities. High-risk CBD merchant accounts offer precisely that. By facilitating the acceptance of credit cards for CBD businesses, these accounts provide the legitimacy that CBD businesses need while ensuring smooth and secure payment processing.
youtube
Empowering Growth in High-Risk Sectors
In the ever-expanding realm of e-commerce, the potential for growth is immense, even within high-risk sectors like CBD and credit repair. Secure and efficient payment processing, driven by high-risk merchant accounts and payment gateways, is the linchpin that unlocks this potential. By seamlessly integrating credit card processing and enabling transparent transactions, businesses in these niches can not only survive but thrive.
In a landscape where e-commerce reigns supreme, businesses must equip themselves with the tools necessary to navigate the complexities of payment processing. High-risk industries like CBD and credit repair face unique challenges that require tailored solutions. Through high-risk merchant accounts and specialized payment gateways, these challenges can be transformed into opportunities, allowing businesses to establish trust, ensure security, and drive growth.
#high risk merchant account#high risk payment gateway#high risk payment processing#merchant processing#credit card payment#payment processing#credit card processing#accept credit cards#Youtube
19 notes
·
View notes
Text
Can we safely assume – as many do – that the attacks are carried out by Russia and Belarus? In a word, yes. Security experts in Latvia are investigating the attackers.
"There are hacktivists who very openly support Russian aggression and policy. The attacks are directly related to Latvia's aid to Ukraine," Kaškina said(..)
"The attacks are mostly politically motivated. There are signs of centralized, paid attacks," revealed Vineta Sprugaine, representative of the Latvian State Radio and Television Center.
P.S. Already in 2007, when the politically correct West was still diligently feeding the Kremlin's repressive regime with huge investments and increasing its dependence on Russian gas and oil imports, the Russians secretly organized a mass cyber attack against Estonia, but the Russian imperialists failed miserably even then. The cyber war started by the Russians did not achieve its goals. They are wasting pretty large financial resources. All the Baltic States drew the right conclusions and prepared to repel the attacks of Russian imperialists, subjects of the Belarusian dictator and religious extremists on the cyberspace of the Baltic States...! The virtual war declared by the Russians has been going on for decades, but all the Kremlin's investments in this war have completely failed...
5 notes
·
View notes
Text
//AUDIO TRANSCRIPT BEGINS//
T: Pilot Marsh. We printed something you may find of interest while you were on the job. We believe it will assist you. GRAY provided the files.
M: Hmm? Oh, alright, I'll, wait, since when do you have access to the printer?
T: You are not very good at hiding your passwords Pilot Marsh. And I was already in communication with the Unpromised Hope for you, and your printer is connected to your network.
M: I... ok, I admit I'm not exactly a cyber security genius. If you want to optimize that feel free.
T: We would greatly enjoy this task. Regardless, we remind you there's something for you. We are eagerly waiting to observe your reaction to it.
M: Right right, one second.
[[Auto audio identification: footsteps recede from audio receiver. Distant noises likely to be muttering. Noise continues for approx. 2 minutes.]]
//New audio device connected. New Audio device. User:TESTAMENT renamed device to "Marsh's Ear's"//
M: Whoa! That's... Weird...
T: Are you alright Pilot Marsh? We determined that your hearing had been impaired at some point and sought a way to fix it given our limited access to medical technology. It disables your own body's audio centers and connects to your implants to allow...
M: yeah yeah yeah, I'm, I'm good, I'm good. Just... weird to be able to hear clearly without being synced with my Mech... it's nice.
T: Excellent, we are pleased to help you operate more optimally.
M: Haha. Thanks Test. seriously.
//AUDIO TRANSCRIPT ENDS//
2 notes
·
View notes
Text
SOCaaS, which stands for Security Operations Center as a Service, is becoming popular as a way to protect against cyber threats. It's like having a team of experts watch over your digital stuff for you.
2 notes
·
View notes
Text
As November’s U.S. presidential election draws closer and the campaigns of former President Donald Trump and Vice President Kamala Harris kick into high gear, so have efforts by hackers from Washington’s adversaries aimed at disrupting or influencing the vote. One adversary in particular is playing an increasingly prominent role: Iran.
Iranian state actors have stepped up their efforts to interfere in this year’s election through online disinformation and influence operations as well as cyberattacks on both presidential campaigns, three U.S. agencies—the Office of the Director of National Intelligence (ODNI), the Federal Bureau of Investigation (FBI), and the Cybersecurity and Infrastructure Security Agency (CISA)—warned in a joint statement on Monday.
They’re not the only ones sounding the alarm. In the past three weeks alone, current and former intelligence officials as well as cyber threat researchers from Microsoft and Google have shared a growing body of evidence of Iran’s hacking efforts. As several of them have pointed out, Iran’s targeting of U.S. elections isn’t new—hackers linked to Iranian security services have attempted to interfere with presidential and midterm races dating back to at least 2018.
However, “Iran perceives this year’s elections to be particularly consequential in terms of the impact they could have on its national security interests, increasing Tehran’s inclination to try to shape the outcome,” the U.S. agencies wrote in their statement. “We have observed increasingly aggressive Iranian activity during this election cycle.”
Trump and his acolytes have been particular targets of Iranian hacking, with some former intelligence officials speculating to Politico that efforts to compromise their email accounts could be part of an effort to assassinate U.S. officials in retaliation for the 2020 killing of Iranian Gen. Qassem Suleimani during Trump’s presidency.
In their statement on Monday, the FBI, ODNI, and CISA officially blamed Iran for the so-called hack-and-leak operation against Trump’s campaign that the campaign made public earlier this month. Those tactics, mirroring Russia’s breach of the Democratic National Committee during the 2016 election, are only one part of Iran’s election interference efforts along with broader disinformation campaigns aimed at sowing discord among the American electorate.
“Iran, especially because of the past events with Suleimani, they have a marked interest in this election,” said retired U.S. Army Col. Candice Frost, the former commander of the Joint Intelligence Operations Center at U.S. Cyber Command. “They have attempted to message on past elections,” she said, but “I think this one is almost personal to them.”
Iran’s relatively elevated profile and more brazen cyber efforts may also be spurred by the ongoing conflict in the Middle East between U.S. ally Israel and Iranian proxies Hamas and Hezbollah, Mohammed Soliman, director of the strategic technologies and cybersecurity program at the Middle East Institute in Washington, D.C., told Foreign Policy. “I think the timelines have collided [between] regional confrontation with Israel and the U.S. elections,” he said. “This made them more proactive in attacking high-value targets that have brought massive visibility to their work.”
Iran is not the only adversary officials in Washington are concerned with—election interference efforts by Russia have been extensively documented, and U.S. officials have increasingly warned about China’s shift in cyber tactics from espionage to more disinformation and disruptive campaigns. Those two countries remain the prime threats, in large part because their capabilities are relatively more sophisticated.
“Russia and China are really a league of their own,” said Frost, currently an assistant professor at Georgetown University’s Center for Security Studies. “We oftentimes discount Iran and North Korea, and then you’ll have something like the Sony hack or this hack [of the Trump campaign]. So it’s not necessarily the level of advancement or competency that they have, but the fact that they kind of found a vulnerability and have been able to exploit that.”
“Any nation that has an interest or perceived stakes in the outcome of a U.S. presidential election is going to be thinking about how to influence that outcome,” said Gavin Wilde, a senior fellow in the technology and international affairs program at the Carnegie Endowment for International Peace and a former U.S. national security official. “It’s easy to point to Russia and China as the most adversarial and the most sophisticated, but every nation around the world has some perceived interest in the outcome, and so I think we need to calibrate along those lines.”
Officials and experts say the U.S. government has learned from the missteps of previous elections, particularly 2016, and is better prepared to defend this November’s election from cyber threats than it has ever been. Part of that is the shift to publicly calling out adversaries and their activities much earlier in the process and adopting a form of sunlight-as-best-disinfectant strategy, like the ODNI, FBI, and CISA did this week with Iran.
“It’s very hard to counter that narrative once it gets into the American psyche and our citizens’ spheres of influence,” Frost said. “But I do see the focus and calling out [of] this behavior. … That is what we’re seeing at a much faster pace, and I give the current intel community a lot of props for doing that early.”
But Wilde warned that while U.S. officials are “unquestionably” more prepared this time around, they also now need to be careful about showing their work without inciting panic about elections being compromised. “The tightrope they now have to walk is [being] helpful without creating the very kind of panic that might itself undermine confidence in the election,” he said, adding that it’s also important to draw distinctions among hack-and-leak operations that have become “a new normal” for political campaigns, election influence efforts that can sometimes be hard to legally define, and actual efforts to interfere with the ballot box itself.
“I think the most consistent thing from all of them is how much it’s been a lot of just entrepreneurialism and experimental spaghetti-against-the-wall tactics to kind of just see what works,” Wilde said. “The U.S. and everyone has to be careful not to inadvertently incentivize this activity by making too big a deal out of it, and luckily I think we’ve done a lot better this go-round than we did in 2016.”
15 notes
·
View notes
Text
A World Gone to Hell: mysterymanjoseph and thesmuttygazette
Joseph had been in Los Angeles for a short time to close down one of the branch offices of his family's corporation and move it out of the city. Cost of operations, and frankly the safety of his employees coming in, and going home from work is a high concern. The new building for operations has already been set up, and those that need to move to be closer are being assisted with the move a corporate expense. All that done, he was leaving, driving back home to New York State rather than fly, he likes these long road trips when he has a chance. He was just outside LA proper when an alert came in over his cell from corporate h.q. Talking to his executive assistant, Janet, who he suspects really runs the business, Joseph is transferred to the cyber security division head. The man was in a near panic, their monitoring of the internet has brought up huge red flags, a large scale, multi platform cyber attack seems to be in the initial phase. Joseph instructs the man to initiate the emergency protocols that Joseph's grandfather had put into place decades ago, with some updates since then, for this sort of circumstance. Transferring back to Janet, Joseph instructs her to initiate the emergency protocol corporate wide, unplug everything, send everyone home, with pay, until they are called back to work. Getting acknowledgment from the woman, Joseph tells her to take care of herself, and he will hopefully see her as soon as things settle down. That all done, he sets out on the road again, thinking, "Okay, Grandpa had this all preplanned for after that think tank came up with that analysis of what were the biggest vulnerabilities to the continued function of U.S. civilization." "Guess we will see how close to the fact that study was, and if their predictions on any recovery were accurate." First priority for him, was get out of the city before things went completely sideways. Depending on the severity of the attack, things could be bad, as in blackouts, or really, really bad, as in vehicles stalling, airliners falling from he sky, cell phones and other communications systems failing. A large urban center is the last place you wish to be under any of those circumstances.
@thesmuttygazette
2 notes
·
View notes
Text
*ISRAEL REALTIME* - "Connecting the World to Israel in Realtime"
🚢 Red Sea Front 🗞 In defense of a large anti-ship barrage, the US Navy shot down 18 suicide drones, 2 anti-ship cruise missiles and 1 anti-ship ballistic missile fired by the Houthis from Yemen. No ships damaged.
▪️FINANCE MINISTER REFUSES TO TRANSFER FUNDS TO PA.. to the US Sec. State “we will not transfer a shekel to the Palestinian Authority that will go to the families of the Nazis in Gaza, and we will work to allow the opening of the gates of Gaza for the voluntary immigration of refugees, as the international community did to the refugees from Syria and Ukraine.”
▪️ISRAEL TELLS EGYPT WEAPONS MOVING AND MAYBE HOSTAGES.. Israel informed Egypt directly and through the Americans, that it suspects that the smuggling of weapons from Egyptian territory to the Gaza Strip continues.. and estimates that the Hamas leadership may move with the hostages to Egypt and from there to other places in the region such as Lebanon and Iran. (Egypt Al-Akhbar)
▪️HEZBOLLAH THREATENS WEAPONS OF MASS DESTRUCTION.. a Lebanese journalist close to Hezbollah published an article that read: 'If Israel initiates a war, the organization will use non-conventional weapons. It is important to pay attention to what Nasrallah said in his speech - the war will be without restraints and without borders.' According to estimates, Hezbollah has considerable amounts of chemical weapons, mainly sarin nerve gas and possibly biological weapons.
▪️ONE HERO SOLDIER HAS FALLEN, a combat medic in Gaza.
▪️INTERNAL CONFLICT.. High Court rules the Min. Of National Security may NOT instruct the police regarding not permitting anti-Israel demonstrations by the Hadash party during the war. The Minister, “the decision of the High Court that deprives me of the authority to prevent support for the enemy in time of war... we do not understand how such a decision can be made that allows the enemy to demonstrate against our soldiers”.
▪️KNESSET BUDGET CUT.. the Knesset will cut an amount of NIS 121 million from its operational budget for 2024 for the benefit of the war effort.
▪️BIZARRE, UNAUTHORIZED OFFICER.. police indict an “Israeli citizen” who ran to battle, fought, gained access to operational intelligence and planning. The problem: he is not an IDF officer, just a citizen. No suspicion of leaking of information to enemies, just wasn’t what he said he was.
▪️NEGOTIATIONS.. (note - all such information is leaks and therefore rumors++). New Israeli proposal includes withdrawal of IDF from Gaza, exile of Hamas leaders, and ‘long term silence’.
▪️EL AL HIT WITH CYBER ATTACK.. reports of shutdown of El Al systems in Ben Gurion.
⬆️ Northern Front 🗞 Heavy IDF airstrikes in Lavona. IDF drone strikes in Marukhin. Targeted attack, aka assassination, in an apartment in south Lebanon.
Hezbollah Warning: Leader Nasrallah publicly orders missile units to ‘prepare heavy barrages’ and ‘use precision missiles’.
➡️ Eastern Front (Judea-Samaria) 🗞 Forces operated today in a number of centers in Shechem. Terrorists responded with gunfire and IEDs. Forces focused on searches, arrests and destruction of buildings used for terrorist activities.
Jenin: forces capture 80 IEDs buried under the roads. Tarkamiya: forces capture 100 IEDs.
24 notes
·
View notes