#cyber security operations
Text

Cyber Security Operations provide comprehensive protection through continuous monitoring, rapid incident response, and proactive threat management. Our services include 24/7 surveillance, vulnerability assessments, SIEM, and penetration testing, all managed by a dedicated Security Operations Center (SOC). We ensure robust security, compliance, and risk management to keep your organization safe from evolving cyber threats.
0 notes
Text
Checked my rota to see my holiday request has been rejected for no reason, then immediately earned the shop £1k in my first hour without anyone batting an eyelash. I really need to leave this place
3 notes
·
View notes
Text
AI, Cybersecurity, and National Sovereignty
Introduction: The Role of AI in Cybersecurity
As artificial intelligence (AI) becomes integral to national security, cyber threats increasingly exploit AI-driven vulnerabilities. Both India and China face the challenge of securing their cyber infrastructure while mitigating espionage and offensive cyber operations. The risks include large-scale data breaches, intellectual property theft, and attacks on critical infrastructure. With AI enhancing the scope and speed of cyberattacks, national sovereignty is increasingly threatened by cyber vulnerabilities that transcend borders.
AI-Driven Cyber Threats and Espionage
China has heavily integrated AI into its cyber capabilities, using it to enhance espionage, cyber warfare, and information manipulation. AI-enabled cyber operations allow China to gather vast amounts of intelligence data through advanced hacking techniques. These tools are often deployed through state-sponsored groups, exploiting zero-day vulnerabilities and penetrating government and corporate networks worldwide.
For example, in 2021, China was accused of orchestrating a large-scale cyber-attack targeting Microsoft Exchange servers, affecting over 30,000 organizations globally. This attack was designed to facilitate espionage, capturing sensitive information ranging from corporate intellectual property to government data. China's cyber operations underscore the increasing use of AI in orchestrating sophisticated, large-scale intrusions that threaten national sovereignty.
India, while lagging behind China in offensive cyber capabilities, faces persistent cyber espionage threats from Chinese state-sponsored actors. The most notable incidents occurred during the 2020 India-China border standoff, where Chinese hackers targeted India's critical infrastructure, including power grids and government networks. These attacks highlight the vulnerabilities in India's cybersecurity architecture and its need to enhance AI-driven defenses.
Vulnerabilities and National Sovereignty
AI-driven cyber threats pose significant risks to national sovereignty. For India, the challenges are magnified by the relatively underdeveloped nature of its cybersecurity infrastructure. Although the establishment of the Defence Cyber Agency in 2018 marked a step forward, India still lacks the offensive cyber capabilities and AI sophistication of China. India's defensive posture primarily focuses on securing critical infrastructure and mitigating cyber intrusions, but it remains vulnerable to cyber espionage and attacks on its digital economy.
China's integration of AI into both military and civilian cyber systems, through its Military-Civil Fusion policy, has bolstered its ability to conduct large-scale cyber operations with deniability. This fusion allows China to leverage private sector innovations for military purposes, making it a formidable cyber power in the Indo-Pacific region.
Case Studies: Cyber Confrontations
In 2019, a significant cyberattack targeted India's Kudankulam Nuclear Power Plant, which was traced back to North Korea, but was believed to be part of a broader effort involving Chinese actors. This incident highlighted the potential for AI-enhanced malware to target critical infrastructure, posing severe risks to national security.
Similarly, the 2020 Mumbai blackout, reportedly linked to Chinese hackers, emphasized how AI-driven cyberattacks can disrupt essential services, creating chaos in times of geopolitical tension. These incidents illustrate how AI-driven cyber capabilities are increasingly weaponized, posing severe risks to India's sovereignty and its ability to protect critical infrastructure.
Implications for Future Conflicts
As AI continues to evolve, the cyber domain will become a primary battleground in future conflicts between India and China. AI-enhanced cyber operations provide both nations with the ability to conduct espionage, sabotage, and information warfare remotely, without direct military engagement. For China, these tools are integral to its broader geopolitical strategy, while India must develop its AI and cybersecurity capabilities to protect its national sovereignty and counteract cyber threats.
Conclusion
The integration of AI into cybersecurity poses both opportunities and challenges for India and China. While China has aggressively developed AI-driven cyber capabilities, India faces an urgent need to enhance its defenses and develop its offensive cyber tools. As cyberattacks become more sophisticated, driven by AI, both nations will continue to grapple with the implications of these developments on national sovereignty and global security.
#AI and cybersecurity#National sovereignty#Cyber espionage#India China cyber conflict#AI driven threats#Cyber warfare#Critical infrastructure#Cyber defense#China cyber strategy#India cybersecurity#AI and national security#Cyberattacks#Espionage operations#AI vulnerabilities#Military Civil Fusion#Cyber sovereignty#Cyber espionage India#AI in geopolitics#AI enhanced malware#Data security
0 notes
Text
Jade Ann Byrne & The Evolution of Mercenary Warfare: From Cold War Covert Ops to Cyber Fog with eGirl4Rent PMC
Jade Ann Byrne & The Evolution of Mercenary Warfare: From Cold War Covert Ops to Cyber Fog with eGirl4Rent PMC
By Paladin Jade (Jade Ann Byrne) eGirl4Rent PMC
Introduction
In the shadowy world of modern warfare, mercenary groups have long been the unseen hands manipulating global conflicts, swaying political outcomes, and executing covert operations that governments prefer to keep in the dark.…
#black water#ciberseguridad#clandestine operations#contractor militar privado#contractor privado militar#contractors privados#contratista militar privado#covert ops#cyber defense#cyber fog#cyber intelligence#cyber mercenaries#cyber operations#cyber warfare#cybersécurité#cybersicherheit#defensa cibernética#digital age#digital battlefield#digital espionage#digital soldier#digital warfare#eGirl4Rent#espions numériques#eSports team#global conflicts#global security#guerre numérique#guerrero digital#intelligence
0 notes
Text
Google advances mobile AI in Pixel 9 smartphones
New Post has been published on https://thedigitalinsider.com/google-advances-mobile-ai-in-pixel-9-smartphones/
Google advances mobile AI in Pixel 9 smartphones
.pp-multiple-authors-boxes-wrapper display:none;
img width:100%;
Google has unveiled its new range of Pixel 9 smartphones, emphasising their enhanced AI capabilities.
The company released the devices much earlier than usual, as Google typically presents new Pixel models in the autumn. However, compared to previous versions, the changes in the new models are revolutionary.
The new smartphones feature more advanced integrations of Google’s AI technology. For instance, one unique Pixel feature allows users to search for information and images within their screenshots, thanks to a more deeply integrated approach. Additionally, through the Gemini chatbot, some features of these smartphones are available as overlays from other apps.
At Alphabet’s Bay View campus in Mountain View, California, Rick Osterloh, the Senior Vice President of Devices and Services at Google, informed visitors that the company plans to focus on practical applications of AI. He spent time describing the “Gemini era” to the audience, which will commence with the creation of Google’s advanced AI model.
The Pixel 9 series offers several models. The base model, the Pixel 9, features a 6.3-inch screen and costs $799. A larger alternative, the Pixel 9 Pro XL, has a 6.8-inch screen. A slightly enhanced version, the Pixel 9 Pro, offers a better camera system, though its price is higher. The final option is the foldable Pixel 9 Pro Fold.
Regarding the initial shipping date, Google stated at the event that the Pixel 9 and Pixel 9 Pro XL would ship in late August. The Pro and Pro Fold models will ship in September, with all models available for preorder starting August 13. During Google’s presentations at the event, Gemini’s new functions were showcased in a live demo, focusing on the latest conversation features. Additionally, the company announced updates to the product’s exterior design, the installation of Google’s advanced camera system, and the integration of the new Tensor G4 chip.
In addition to smartphones, the company unveiled new versions of the Pixel Watch 3 smartwatch and Pixel Buds Pro 2 wireless earbuds. The watch can track the user’s heart rate; if it stops, it will call emergency services. This feature will be available in the UK and the EU.
As reported by IDC, Google’s share in the global smartphone market was less than 1% in the second quarter of 2024. Samsung and Apple took the first and second places, with market shares of 18.9%, and 15.8%, respectively. In the US, Google ranks fourth among smartphone operating systems, holding 4.5% of the market share.
Industry analysts note that although Google Pixel is not among the best-selling smartphones, it showcases some of the benefits of the Android operating system. Android has become the dominant operating system, used by more than 80% of smartphone users worldwide. Consequently, many people, even those who have never used a Google Pixel, may indirectly experience and appreciate the features that Google products offer.
The event also touched upon Google’s further intentions and previous efforts to implement AI across its product lineup to stay at the top of the game. Not long ago, the company integrated AI improvements into its core products, including its search engine. Additionally, Google announced a content-sharing agreement it reached with Peloton. As a result, Fitbit Premium subscribers will have free access to the Peloton training class library.
(Image Credit: Google)
See also: Google’s Gemini 1.5 Pro dethrones GPT-4o
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including Intelligent Automation Conference, BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
Tags: ai, artificial intelligence, gemini, Google
#2024#agreement#ai#ai & big data expo#ai model#amp#android#Android operating system#apple#applications#approach#apps#artificial#Artificial Intelligence#automation#background#Big Data#chatbot#chip#Cloud#cloud computing#comprehensive#computing#conference#content#cyber#cyber security#cybersecurity#data#Design
0 notes
Text
youtube
#youtube#militarytraining#Cyber Security#Cyber Resilience#Information Security#Cyber Attacks#Government Cybersecurity#Cyber Threats#National Security#Hacking Prevention#Cyber Intelligence#Cyber Warfare#Digital Warfare#Military Technology#Cyber Defense#Hackers#New Military Unit#Military Innovation#Military Operations#Cyber Strategy#National Cyber Security#Cyber Awareness#Cyber Protection#Cyber Operations#Digital Security#228th Cyberspace Operations Group#Cyber Technology
0 notes
Text
Prabhu Bank Limited Vacancy 2081 for Technical Positions
Prabhu Bank Limited Vacancy 2081 for Technical Positions: CBS Officer, CBS Operator, Digital Transformation, Cyber Security Officer, Chartered Accountant. If your are looking career in bank sector it will be golden opportunity. Read this article till the end to apply.
CAREER OPPORTUNITY
Prabhu Bank Limited Vacancy 2081 for Technical Positions
Prabhu Bank Limited, a leading Class “A” Commercial…
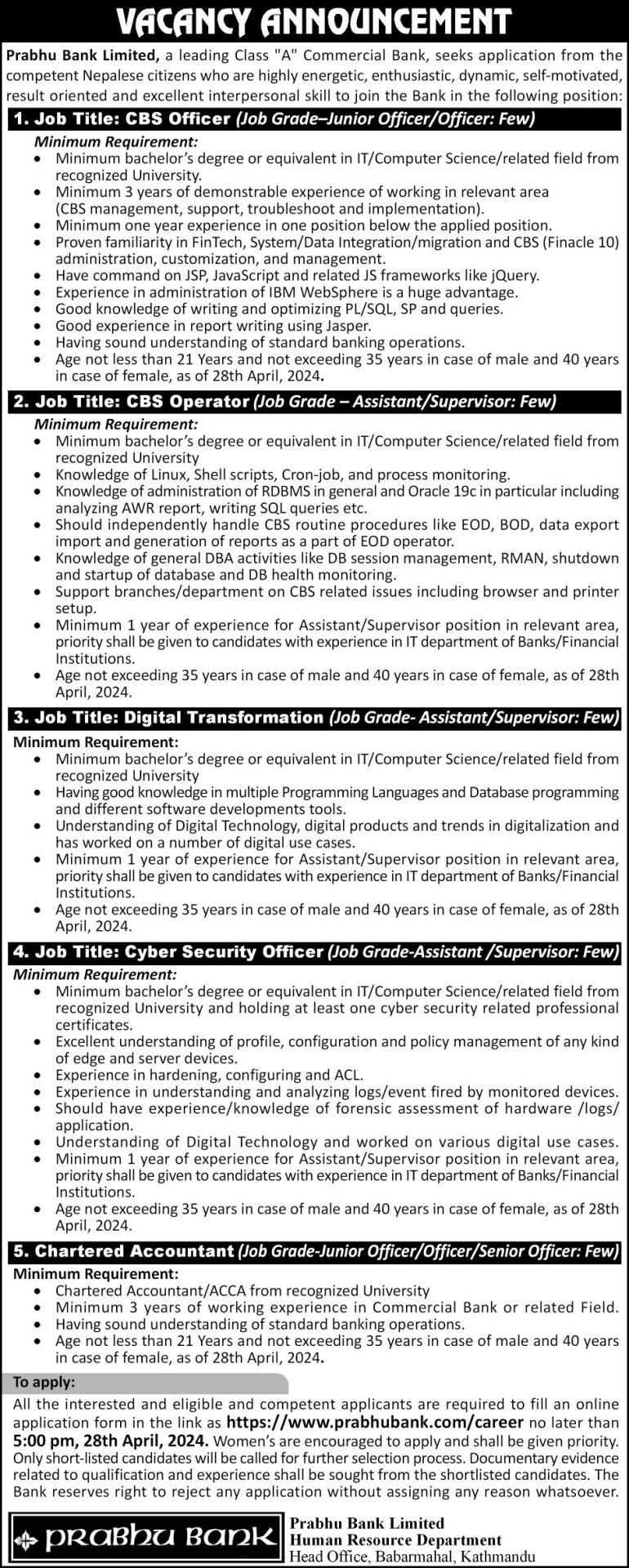
View On WordPress
#Bank Jobs#Banking Career#CBS Officer#CBS Operator#Chartered Accountant#Cyber Security Officer#Digital Transformation#Job Vacancy#Jobs In Nepal#Prabhu Bank Limited Vacancy 2081 for Technical Positions#Technical jobs
0 notes
Text
What and Why security is crucial part of any organization

1 note
·
View note
Text
Staying Relevant: Balancing Learning and Life as an Ethical Hacker
Have you experienced burnout while trying to develop your skills and you just don't have the time to do everything? Finding balance is the key to improving your skills in a healthy way. In this article, I explore healthy habits to grow without burning out
You’ve heard it before – cybersecurity is a field that evolves at a blindingly fast pace. The tools, techniques, and technologies threatening networks transform rapidly. As an ethical hacker, your skills can become obsolete within months if you aren’t continuously upgrading your knowledge. Point #4 on our hacker roadmap deals with knowing the latest and greatest when it comes to the state of…

View On WordPress
#burnout#certifications#conference#continuous learning#Cyber Security#cybersecurity education#cybersecurity skills#Ethical Hacking#hacker skills#infosec community#leadership#learning plan#maintaining balance#microlearning#Penetration Testing#pentesting methodologies#personal development#podcast#red team operations#security news#security policies#security tools#time management#trends#vulnerability assessments#work-life balance
1 note
·
View note
Text
Achieve your educational excellence with GTEC Education

The education industry is flourishing in Dubai, a prosperous metropolis renowned for its breathtaking architecture and status as a global commercial hub. GTEC Education is a shining example of excellence among the many educational establishments in this city. GTEC Education meets a variety of educational demands by providing a broad range of academic tuitions, subject-specific courses, language instruction, exam preparation, and diploma programs. This makes it a top option for students looking for high-quality education in Dubai.
Academic Tuitions in Dubai:
The academic tuition packages offered by GTEC Education are intended to support students' academic success. The establishment provides extensive tuition packages across multiple disciplines, guaranteeing that learners obtain the assistance required to excel in the classroom. GTEC Education offers support in a wide range of subjects, including science and math.
Language Training in Dubai
GTEC Education offers a variety of language training programs for anyone who wish to enhance their language proficiency. Since the goal of these courses is to improve communication skills, they are beneficial for both professional and personal development.
English Language Training in Dubai
English is widely used throughout the world, and GTEC Education acknowledges this fact. Their English language training programs assist people improve their reading, writing, speaking, and listening skills at all skill levels, from absolute beginners to fluent speakers.
Arabic Language Training in Dubai
GTEC Education provides courses to assist students in understanding the nuances of Arabic, given the language's cultural relevance in the area. GTEC Education can help you on your path, whether you're an expat looking to blend in with the community or just interested in studying this lovely language.
French Language Training in Dubai
The romantic language of French is another well-liked course offered by GTEC Education. Gaining proficiency in French can be beneficial for business and travel. With its highly qualified teachers and engaging teaching strategies, GTEC Education guarantees that you will confidently become fluent in French.
Exam Preparation Courses in Dubai
Exam preparation can be a difficult undertaking. Because they are aware of this, GTEC Education has created exam preparation programs that are meant to reduce anxiety and improve student performance. Their courses can help you prepare for professional qualifications or standardized tests by providing you with the knowledge and skills you need.
IELTS Courses in Dubai
An essential prerequisite for anyone wishing to study, work, or immigrate to an English-speaking nation is the International English Language Testing System (IELTS). Students who take GTEC Education's IELTS courses are guaranteed to meet the language proficiency requirements and perform well on the test.
OET Courses in Dubai
The Occupational English Test is frequently required of healthcare professionals who wish to work in English-speaking nations (OET). GTEC Education assists medical professionals in obtaining the necessary scores for their career goals by providing OET courses specifically designed for them.
PTE Courses in Dubai
Another exam for English proficiency that is frequently needed for immigration or study is the Pearson Test of English (PTE). The PTE courses offered by GTEC Education are made to give applicants the tools they need to do well on the test.
Diploma Programs in Dubai
GTEC Education goes above and beyond by providing diploma programs in a range of subjects, meeting the needs of individuals who want to acquire specialized knowledge and abilities.
Advanced Excel Courses in Dubai
Excel proficiency is a valuable skill in the digital age. GTEC Education's advanced Excel courses enable individuals to efficiently handle data and analytics, making them invaluable assets in the business world.
Diploma in Digital Imaging Courses in Dubai
GTEC Education offers diploma programs that cover the fundamentals of digital imaging for those interested in the creative realm.
Diploma in Cyber Security Courses in Dubai
With the growing importance of cybersecurity, GTEC Education's diploma program in this field provides students with the knowledge and skills required to safeguard digital assets.
Diploma in Computer Operations Courses in Dubai
Understanding the fundamentals of computer operations is critical in today's technology-driven world. GTEC Education provides diploma courses for those interested in pursuing a career in this field.
Python Diploma Course in Dubai
Python is a versatile programming language. GTEC Education's Python diploma course provides a comprehensive foundation for budding programmers and data scientists.
C++ Diploma Course in Dubai
C++ is a popular programming language for software development. GTEC Education's diploma program in C++ equips students with the skills to develop efficient and robust software applications.
PHP Diploma Course in Dubai
PHP is a widely used scripting language for web development. GTEC Education's PHP diploma course helps students become proficient web developers.
Data Analysis Diploma Course in Dubai
In a data-driven world, data analysis is a highly sought-after skill. GTEC Education's diploma program in data analysis provides students with the tools and techniques to make informed decisions based on data.
MS Office Courses in Dubai
Microsoft Office proficiency is a necessity in today's professional landscape. GTEC Education's MS Office courses offer hands-on training in Word, Excel, PowerPoint, and more, ensuring students are well-versed in these essential tools.
SQL Courses in Dubai
Structured Query Language (SQL) is fundamental to database management. GTEC Education's SQL courses enable students to manipulate data efficiently, a valuable skill in various industries.
GTEC Education in Dubai is a center of educational excellence that serves a wide range of learning needs. GTEC Education has the expertise and programs to help you reach your goals, whether you're a student looking to excel in your academics, a professional looking to improve your skills, or an individual aspiring to master a new language. GTEC Education is unquestionably a top choice for learners in Dubai, with a commitment to quality education, experienced instructors, and a diverse range of course offerings.
#Advanced Excel Courses in Dubai#Diploma in Digital Imaging Courses in Dubai#Diploma in Cyber Security Courses in Dubai#Diploma in Computer Operations Courses in Dubai#Python Diploma Course in Dubai#C++ Diploma Course in Dubai#PHP Diploma Course in Dubai
0 notes
Text
#digital payment solution#digital payment market#it service provider#it solutions#devops operations management#cyber security
1 note
·
View note
Text
Learn OWASP Top 10 Security Fundamentals | OWASP Training | CodeRed.eccouncil

Our OWASP Training course aims to deliver quality training that covers solid fundamental knowledge on core concepts This course follows a hands-on approach.
#Best Software Development Courses Online#Software Development Online Training Courses#OWASP Security Fundamentals#Best Software Development Services#Web Application Security#Cyber Security Certifications#OWASP Training#Best Development security and operations Courses
0 notes
Text
Welcome to BSE Institute Ltd. | Global Accountancy Professional
Diversity in accounting practices across countries makes it difficult to prepare consolidated financial statements for companies with foreign operations. A Company lets say, while headquartered in Michigan, conducts business on six continents, has multiple facilities, in more than 100 countries, across different time zones, with each subsidiary preparing financial statements in accordance with their local regulations and in their local currency.
#data science#data science course#data analytics course#data analytics#cyber security course#cyber security training#financial market course#data analysis course#predictive analysis course#banking course#banking and finance course#financial accounting course#financial accounting#investment banking operations
0 notes
Text
A Complete Guide on ISO 27001 Certification

#ISO 27001 is an internationally recognized standard for Information Security Management Systems (ISMS). This standard provides a framework f#procedures#and controls that help protect their sensitive information from cyber threats.#Here is a complete guide on ISO 27001 Certification:#Understanding the Standard: The first step is to understand the ISO 27001 standard cost and its requirements. This includes a detailed stud#as well as an assessment of your organization's current information security processes#policies#and procedures.#Gap Analysis: Conduct a gap analysis to identify any areas where your organization is not meeting the requirements of the standard. This wi#Designing the System: Once you have identified the gaps#you can begin to design your information security management system (ISMS). This will involve developing policies and procedures that are i#Implementation: After designing the system#you can implement the policies#and controls across your organization. This may involve providing training to your employees and raising awareness of the importance of inf#Internal Audit: Conduct internal audits to ensure that your ISMS is effective and compliant with the ISO 27001 standard. This will help you#Certification: After your ISMS has been in operation for a suitable period#you can apply for ISO 27001 certification. This involves an external audit by an accredited ISO certification body#who will assess whether your ISMS meets the requirements of the standard.#Continual Improvement: Once you have achieved certification#you will need to maintain your ISMS and continually improve it to ensure that it remains effective and compliant with the standard.#ISO 27001 certification can help to improve your organization's reputation#demonstrate your commitment to information security#and reduce the risk of cyber attacks. It is applicable to organizations of all sizes and in all sectors.
0 notes
Text
Security Operations Center (SOC) Analysts play a crucial role in identifying, analyzing, responding to and mitigating cyber attacks in an organization.
0 notes
Text
Digital Operations Resilience Act
Metodo dedicato o base operativa general purpose?
Di Agostino Pellegrino
Introduzione
Il DORA (Digital Operations Resilience Act) è un metodo di valutazione del rischio operativo digitale che consente alle aziende di eseguire un assessment ed uno threat scoring specifico per le imprese finanziarie operanti con infrastrutture digitali. Il metodo è stato sviluppato dalla BCBS (Banca dei…

View On WordPress
#assessment#cia triad#classificazione#cyber#cyber security#dati#digital#DORA#italia#operations#protezione#risk#security#vulnerabilità#vulnerability
1 note
·
View note