#cyber crime image
Explore tagged Tumblr posts
Note
What are your thoughts on the yandere haikyuu teams x their manager?
Boring. I need some spice in it. How about-
Yandere Daichi as a cop and his darling is a civilian and now he's so obsessed with her that he murders her husband, frames him as a criminal and will literally stop at nothing to get darling in his arms because again... who will suspect good old, everybody's best bud COP Daichi to be able to do heinous crimes???
Yandere Sugawara as a psychiatrist because come on- he gives major "master manipulator" vibes and now he's obsessed with his darling patient and will continue to do malpractice and gaslight her and prescribe her all the wrong meds until she loses it and he gets to admit it her under his "special care" and now he can play with her mind all day long🤍
Yandere Oikawa is now a pro volleyball athlete and he just saw Ushijima's little sis, the same one he used to bully and even rejected (and ofc, HUMILIATED) when she confessed to him back in highschool. But now Oikawa's obsessed with her and also still hates his nemesis Ushijima, so what's better than killing two birds with one stone??? And Oikawa still has a very devoted fanclub, only now it's larger and more powerful than ever so now he uses them and his socials to peer pressure you into dating him and eventually, marrying him because he ain't getting any younger honey and he needs some cute babies out of you ASAP.
Yandere Kuroo who is the smart IT tech guy at your office but in reality, he has his own cyber security company that he uses to spy on you, controls your entire life through your socials and don't even get me started on your online banking shit. If its any consolation, he's very rich so... yeah. He may not look like a million bucks, but he does have them. In several offshore accounts.
Yandere Kita who somehow ended up as a mafia leader, probably inherited it as family business and he has like severe OCD so he wants everything done to perfection or so help you, you will 1000% end up 6 feet under. Mafia Kita who has this vision of you being the perfect wife, solely based om the one time you offered him your handkerchiefs because he had a nosebleed from stressing too much and now Kita thinks you're an absolute angel and he wont let you destroy that fantasy of his. Seriously. He will pick out your outfits, tell you how to act and all, punish you if he must, but he does love you.
Yandere Ushijima who is a farmer and has decided that the reader whose car broke down and came to his door asking for help, will now be his wife and be a countryside mom to many kids (u can't say no, okay? He wants a big family) and animals! But hey, he's a very caring husband and will massage your feet, give you baths and feed you his homegrown veggies and meals daily once you are round with his babies🥺
Yandere Bokuto who is now a popular politician and he needs an obedient wife to keep up appearances and play the "family man" image up. So he decides to threaten reader who had a one night stand with him, and Bokuto somehow has very intimate images and videos of you and he uses them to get you to marry him. And now he controls every aspect of your life and tells you to do exactly as he says, and he abuses this privilege more as he gets more powerful and you could only imagine the horrors he would inflict on you if he does actually win elections, but you can't run away because again- he has eyes and contacts everywhere.

#yandere daichi#yandere daichi sawamura#yandere bokuto#yandere ushijima x reader#yandere ushijima wakatoshi#yandere ushijima#yandere kuroo#yandere oikawa#yandere oikawa tooru#yandere kita#yandere haikyuu#yandere haikyu x reader#yandere sugawara
2K notes
·
View notes
Note
Does the mouthwash case involve images of child harm? If so this CAN be passed on to the FBI. All the center for missing and exploited children needs is a discord server name and they can investigate it. Images of children can be linked to human trafficking even if it isn't apparent. Discord may brush it off but cyber crimes generally won't especially if there's evidence being presented on other sites. If it's on discord it's national AND international since it's crossing state lines. (Basing this information off my experiences at work, we broke up a ped. Ring operating on discord. I also have an informative post I made about reporting to the CMEC and a guide on how to handle wide scale internet things that I can link if that would be helpful?????) Hope this is helpful and doesn't clog your ask box 🙏🏼.
I'll answer all of these questions.
Does the mouthwash case involve images of child harm?
Yes. Not only do they spam and post images of child harm, but according to a post by nebulatides, they have also posted videos and images of executions, animal mutilation/torture/death, women being raped, and various extreme fetishes (sexual organ removal, scat fetish, vomit fetish, etc.)
I also have an informative post I made about reporting to the CMEC and a guide on how to handle wide scale internet things that I can link if that would be helpful?????
Also yes.
29 notes
·
View notes
Text
☆☆ FAME DR ☆☆
So i wanted to do kinda of a introduction to some of the characters i have scripted so far to Evie Valentine. Some of them are more thought out than others as you will notice.
They are organized by chronological order
The Coven (1999-2005)

(Original TV show i imagined)
After the Vital family moves to a small town,Elisa Vital the family’s 16-year-old daughter, develops a new ability, makes new friends and enters a teenagers witch coven.
Kassidy Welser is a smart and knowledgeable girl. In the coven she is a Illusion witch, which allows her to create large scale illusions to convince a lot of people at the same time and individual illusion who trick one person at a time. Depending on her skill level the illusions become more realistic who eventually becomes tactile.
I'm on every season as a Ensemble Character
X-Men movies (2000,2003 and 2006)

I still haven't decided on how much of the mivies plot change with Polaris there but i'm thinking of something around changing teams from Magneto's to the X-Men in the last movie.
Not A Love Story (2001)

( Original Movie i imagined)
Allison Scott and Charles Smith have been best friends since childhood. After they graduate High School, their parents try to make them fall in love before they move out of state for different colleges.
I play the main character Allison Scott
One Tree Hill (2003-2012)

After her parents death Penelope “Poppy” O’Malley and her sister Melody are welcomed in Tree Hill by her father’s old friend Dan Scott.
Poppy is a stubborn and spontaneous girl with a rebellious streak. Soon after settling herself in the Scott’s house she begins a friendship with Lucas Scott and his friend group. She has a brief casual relationship with Lucas for the first two seasons and later a unrequited crush on Skills.
I'm on every season as a Recurring Character
Supernatural (2005-2020)

Christina “Chrissy” Allen is a hunter friend of Dean Winchester, they met while Sam was at Stanford. She is cunning and extremely talented with blades and has a variety of knowledge with the occult. She has a turbulent romantic relationship with Sam Winchester.
Recurring Character (Season 1-6) -> 2005-2010
Ensemble Character (Season 10-15) -> 2015-2020
Criminal Minds (2005-2025)

Genevieve “Jenny” Hill is part of the Cyber crimes division of the B.A.U. She is a pacifist with a love of classic literature. She has a romance with Dr. Spencer Reid
I'm a Recurring Character for seasons 6 and 7 and a special guest star in the other seasons for when os relevant to mention Reid's girlfriend (and yes i did script a Spin-off. What can i say i love creating Spin- offs so i can be the main character)
(All images found on Pinterest)
#Evie Valentine#dr filmography#fame dr#actress dr#shiftblr#shifters#anti shifters dni#shifting diary#shifting script#shifting to desired reality#shifting consciousness#reality shifting#shifting community#reality shifter#shifter#shifting realities#desired reality
27 notes
·
View notes
Text

editorial from the english version of the Hankyoreh
archive link
plain text
Before focusing on my master’s thesis, I worked for a brief period for an organization supporting victims of cyber sex crimes. My job was to put each and every case of illegally filmed footage assigned to me through a search engine and if I found that the images had been uploaded to certain sites, I would beg the operator of that site to take those images down.
The process of searching and subsequently scrubbing illegally filmed footage probably isn’t what most people would expect. There is no advanced AI that categorizes footage based on the faces of victims, lists the sites the footage is uploaded to, and sends automated requests for the deletion of such posts. Instead, employees and volunteers divide each reported video frame by frame, put each fragmented frame through search engines, organize each site the footage is posted to on a spreadsheet, collate the sites for verification, find the site operator’s email or contact channel, and write a message that read, “This video is illegally filmed footage so we ask that you remove it from your site. If it is not removed, the South Korean government may take action against the site pursuant to relevant laws,” translate it from Korean into English and then send it to the operator.
This happened daily. Sometimes, you would have to go through 100 or 200 cases a day. I’ve assigned a nickname to this procedure: “The Illegally Filmed Footage Removal Protocol that Seems Absurdly Advanced, But Basically Follows the Same Grueling Procedures as a Sweatshop.”
The biggest challenge when fighting digital sex crimes is their overwhelming breadth and scale. It was impossible for us, as we sat in front of our computer screens, to estimate which far-out depths of the internet any of the footage had reached.
Even if we painstakingly found 20 posts using a particular photo and saw that every post was erased, the next day we would see the photo spring up in 40 different posts. Websites distributing illegally filmed footage make various backup sites with different domains to make sure that sites are up and running even if the main site is taken down.
Many of the sites in question have servers based abroad, so even if you sent a beseeching email citing South Korean laws, they simply could just pretend that they never saw the email.
The terror of that vast scope goes beyond distribution and duplication. While deepfake pornography has been in the news recently, photoshopping a real person’s face onto a pornographic image has been a crime for some time now.
The difference is that producing such images used to be time-consuming and technically challenging, requiring the “manual” manipulation of images. But the new tool of AI has made it easy for anyone to instantaneously create deepfakes in a dizzying variety of formats.
Another frightening aspect is that anyone with access to photographs on social media can choose victims at random. And since the images are “fakes” created by AI, the perpetrator can deliberately duck the guilt of harming a real person.
Deepfake creation has spread so rapidly because it gives perpetrators a perverse sense of power over their victims — the ability to create dozens of humiliating images of someone from photographs scraped off Instagram — while also enabling them to ignore victims’ suffering because the images aren’t technically “real.” In short, deepfakes represent a game-changing acceleration of the production cycle of sexually exploitative media.
Those images spread far too fast for the handful of employees at nonprofits to keep up with. Facing such a vast challenge, permanent employees began to drift away, and their positions were once again filled by people on short-term contracts.
Lee Jun-seok, a lawmaker with the Reform Party, said during a meeting of the National Assembly’s Science, ICT, Broadcasting and Communications Committee that the 220,000 members of a deepfake channel on Telegram was an “overblown threat” and estimated that, given the percentage of Korean users on Telegram, only about 726 of the channel members are actually Koreans.
But what does it matter whether there are 220,000 Koreans on the channel or just 726?
Let’s suppose there aren’t even 726, but just 10 people in the group — they could still produce 220,000 deepfakes if they set their mind to it. Those images would then be copied and circulated beyond their point of origin and around the world, perhaps remaining permanently in some dark corners of the Internet without ever being deleted.
That’s the nature of sex crimes in the digital age.
So assuming that the criminal potential of this technology remains the same regardless of whether the channel has 220,000 members, 726 members or even just 10, I can’t help wondering what Lee thinks would be an acceptable number of deepfake purveyors that would not constitute an “overblown threat.”
37 notes
·
View notes
Text


Resources and study tips to get you in cyber forensics
Master post • Part1 • part2
let's get you prepped to be a cyber sleuth without spending any cash. Here’s the ultimate tips and resources.
Ps: you can't become one while doing these pointers but you can experience the vibe so you can finally find your career interest


### 1. **Digital Scavenger Hunts**
- **CTF Challenges (Capture The Flag)**: Dive into platforms like [CTFtime](https://ctftime.org/) where you can participate in cyber security challenges. It's like playing *Among Us* but with hackers—find the imposter in the code!
- **Hunt A Killer (Digitally)**: Create your own digital crime scenes. Ask friends to send you files (like images, PDFs) with hidden clues. Your job? Find the Easter eggs and solve the case.
### 2. **YouTube University**
- **Cyber Sleuth Tutorials**: Channels like *HackerSploit* and *The Cyber Mentor* have playlists covering digital forensics, cybersecurity, and more. Binge-watch them like your fave Netflix series, but here you're learning skills to catch bad guys.
- **Live Streams & Q&A**: Jump into live streams on platforms like Twitch where cybersecurity experts solve cases in real-time. Ask questions, get answers, and interact with the pros.
### 3. **Public Libraries & eBook Treasure Hunts**
- **Library eBooks**: Most libraries have eBooks or online resources on digital forensics. Check out titles like *"Hacking Exposed"* or *"Digital Forensics for Dummies"*. You might have to dig through the catalog, but think of it as your first case.
- **LinkedIn Learning via Library**: Some libraries offer free access to LinkedIn Learning. If you can snag that, you've got a goldmine of courses on cybersecurity and forensics.
### 4. **Virtual Study Groups**
- **Discord Servers**: Join cybersecurity and hacking communities on Discord. They often have study groups, challenges, and mentors ready to help out. It's like joining a digital Hogwarts for hackers.
- **Reddit Threads**: Subreddits like r/cybersecurity and r/hacking are packed with resources, advice, and study buddies. Post your questions, and you’ll get a whole thread of answers.
### 5. **DIY Labs at Home**
- **Build Your Own Lab**: Got an old PC or laptop? Turn it into a practice lab. Install virtual machines (VMware, VirtualBox) and play around with different operating systems and security tools. It’s like Minecraft but for hacking.
- **Log Your Own Activity**: Turn on logging on your own devices and then try to trace your own steps later. You’re basically spying on yourself—no NSA required.
### 6. **Community College & University Open Courses**
- **Free Audit Courses**: Many universities offer free auditing of cybersecurity courses through platforms like Coursera, edX, and even YouTube. No grades, no stress, just pure learning.
- **MOOCs**: Massive Open Online Courses often have free tiers. Try courses like "Introduction to Cyber Security" on platforms like FutureLearn or edX.
### 7. **Scour GitHub**
- **Open-Source Tools**: GitHub is full of open-source forensic tools and scripts. Clone some repositories and start tinkering with them. You’re basically getting your hands on the tools real investigators use.
- **Follow the Code**: Find projects related to digital forensics, follow the code, and see how they work. Contribute if you can—bonus points for boosting your resume.
### 8. **Local Meetups & Online Conferences**
- **Free Virtual Conferences**: Many cybersecurity conferences are virtual and some offer free access. DEF CON has a lot of free content, and you can find tons of talks on YouTube.
- **Hackathons**: Look for free entry hackathons—often universities or tech companies sponsor them. Compete, learn, and maybe even win some gear.
### 9. **DIY Challenges**
- **Create Your Own Scenarios**: Get a friend to simulate a hack or data breach. You try to solve it using whatever tools and resources you have. It's like escape rooms, but digital.
- **Pen & Paper Simulation**: Before diving into digital, try solving forensic puzzles on paper. Map out scenarios and solutions to get your brain wired like a detective.
### 10. **Stay Updated**
- **Podcasts & Blogs**: Tune into cybersecurity podcasts like *Darknet Diaries* or follow blogs like *Krebs on Security*. It’s like getting the tea on what’s happening in the cyber world.
### 11. **Free Software & Tools**
- **Autopsy**: Free digital forensics software that helps you analyze hard drives and mobile devices. Think of it as your magnifying glass for digital clues.
- **Wireshark**: A free tool to see what's happening on your network. Catch all the data packets like you're a digital fisherman.
### 12. **Online Forensics Communities**
- **Free Webinars & Workshops**: Join communities like the *SANS Institute* for free webinars. It's like attending a masterclass but from the comfort of your gaming chair.
- **LinkedIn Groups**: Join groups like *Digital Forensics & Incident Response (DFIR)*. Network with pros, get job tips, and stay in the loop with the latest trends.
### 13. **Practice Cases & Mock Trials**
- **Set Up Mock Trials**: Role-play with friends where one is the hacker, another the victim, and you’re the investigator. Recreate cases from famous cybercrimes to see how you'd solve them.
- **Case Studies**: Research and recreate famous digital forensic cases. What steps did the investigators take? How would you handle it differently?

There you have it—your roadmap to becoming a cyber sleuth without dropping a dime. You don't have time find your interest after paying pennies to different ppl and colleges. You can explore multiple things from comfort of your home only if you want to.

#light academia#study blog#academic validation#academic weapon#student life#study motivation#study with me#study#studyblr#studyblr community#masterpostjam#codeblr
29 notes
·
View notes
Text
Duck Comic Reading Club Week 7: Paperinik New Adventures: Earthquake

Ok, let's get to the point, this issue is the best one yet. An amazing story and a gorgeous art combined.
Oh God, the art. The Francesco Guerrini work here is astonishing. The use of the colors is masterful. Brilliant in every aspect.
This week story start with an earthquake on Duckburg. No major disaster occurred, except for good old uncle Scrooge.

Why do you insurance your oil rig with your own insurance company?
I mean, I got that he didn't have to pay himself the quota for the service, but now you have to pay for the damages. So, stop complaining you crazy old bird.

But One found out something fishy about the earthquakes, and is up to Donald to investigate this. Is so funny that Duckburg is Paperopoli in italian. Is better than Patolandia tho.
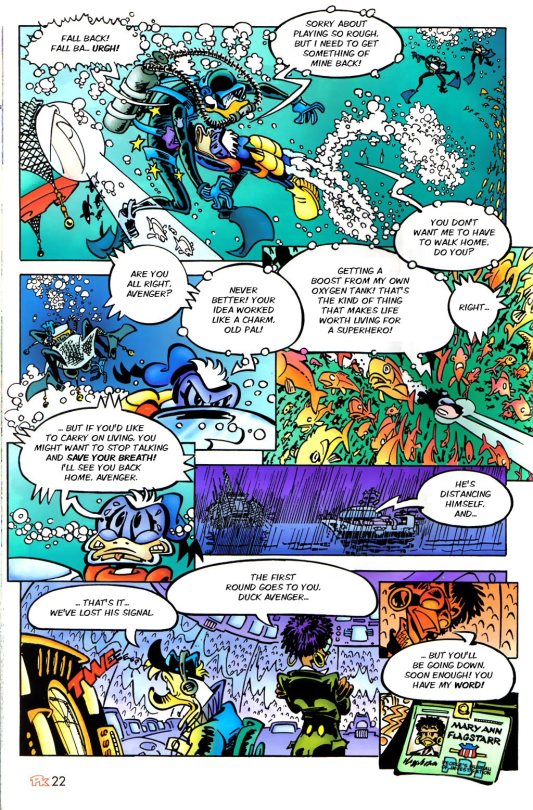
PK took one of the many vehicles at the Tower, and went for a ride, super hero style.
This page is a piece of beauty.

We got a new character, Mary Ann Flagstarr, a PBI agent. Tough lady.

PK had had encounters with the police, but now, he faced federal agents. My boy is not making any friends.
But, you know? A vigilante, a superhero, can't work with the authority. So, yeah, go get them PK.
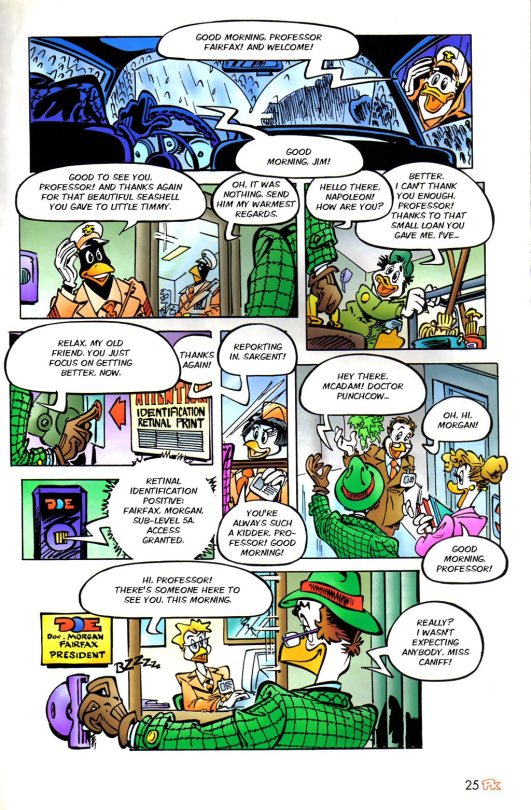
Another new character, Professor Morgan Fairfax. What a nice fella, I'm sure he has never done anything wrong in his life.
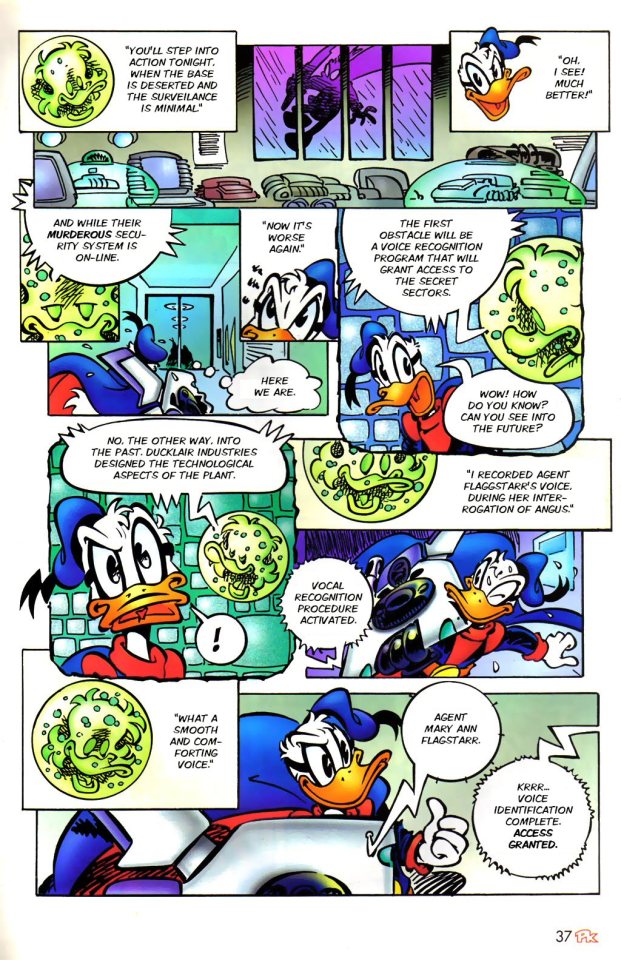
One knows something is not right, they need to keep investigating. But now, is time to go back to the world of cyber space.
Another beautiful page, this issue can't miss.

But is hard to step into a federal database without anyone noticing, so they got caught. Thankfully, One was one step ahead and got himself a great scapegoat.

Oh, now you don't like spread misinformation, right jerk?
He didn't face any charge, and, to be fair, he was innocent. But, if being ugly was a crime, he would get the chair.
Back to the Professor, and he's making some really evil looking smirks. Could it be that he's not the nice guy that we though?
Also, another banger page.

PK infiltrates in the building, using some advance tech. One is a cheat code, and here's being used at his fullness.

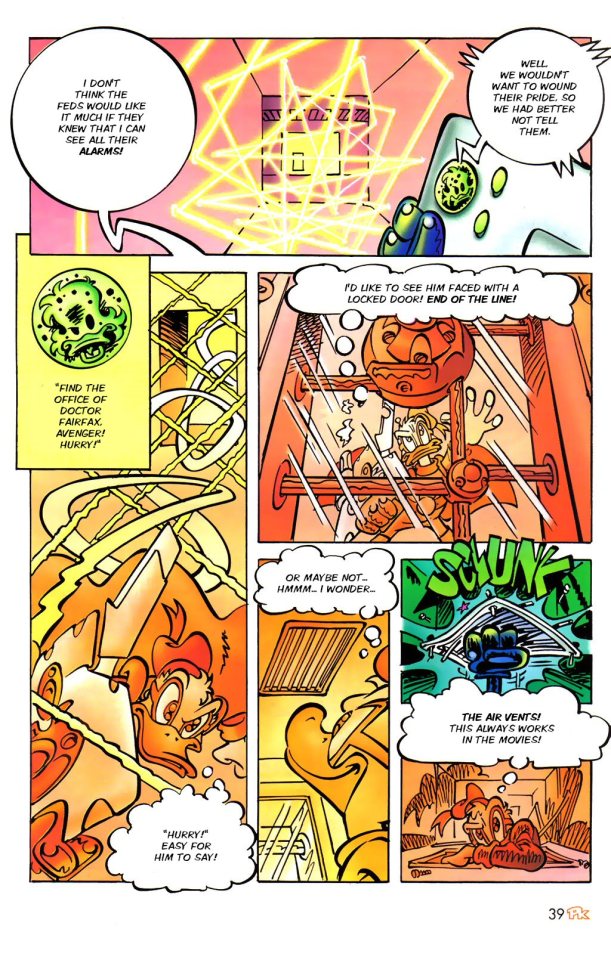
PK had a weird Donald moment, when he stuck in the vent, fall to the ground, and got face to face with the worst security guard ever.

Hey, masked vigilante sneaked in this government facility that I supposed to be looking after. I'm gonna make some lame jokes, and then I'm gonna miss the shots less than a meter away.
Don't come in the morning pal.
You know? I'm starting to think that this guy Fairfax is not that nice.

Yeah, yeah, he's the bad guy. Trying to burn PK alive is in my Being Bad Bingo.
And yet another absolutely gorgeous page. Is amazing.

Thankfully, One and his infinite tech come to the rescue. PK also save the guard, because he's a hero.

Now, this one part was kinda weird. Agent Flagstarr has been shown trough the issue as tough, focus agent, that wants to get the job done. But, a few words of Fairfax and a gift are enough to make her dismiss orders.
Also, that face… you can't trust someone with that face…

Now we found about Fairfax plan. He wants to create a earthquake strong enough that the whole planet would change, and new land would appear.
At the cost of the entire west coast being destroyed.

The worst part? One agrees with him. What the hell man? Not cool One, not cool.

PK got in the plane and try to stop Fairfax, but Flagstarr was in his way. The agent was conflicted on what to do. Madam, help the guy who doesn't want to destroy the whole west coast. Is not that hard.
Man, the art on this issue is out of control.

PK is so cool.

Finally, One got a change of heart, if you can said that, and helped PK to stop this madness. I knew One wasn't a psychopath.
But that last image of the device at the bottom of the sea is quite unsettling.
What can I said? This was awesome. I love all the detective PK stuff, the danger was palpable, One almost got Duckburg destroy. The art was magnificent, the colors were vibrant, it looked beautiful in general.
Hands down, the best one yet.
#dcrc paperinik#dcrc#donald duck#duckverse#pkna#dcrc week 7#paperinik#duck avenger#uno ducklair#mary ann flagstarr#professor morgan fairfax#comic review
43 notes
·
View notes
Text
Google’s and Microsoft’s search engines have a problem with deepfake porn videos. Since deepfakes emerged half a decade ago, the technology has consistently been used to abuse and harass women—using machine learning to morph someone’s head into pornography without their permission. Now the number of nonconsensual deepfake porn videos is growing at an exponential rate, fueled by the advancement of AI technologies and an expanding deepfake ecosystem.
A new analysis of nonconsensual deepfake porn videos, conducted by an independent researcher and shared with WIRED, shows how pervasive the videos have become. At least 244,625 videos have been uploaded to the top 35 websites set up either exclusively or partially to host deepfake porn videos in the past seven years, according to the researcher, who requested anonymity to avoid being targeted online.
Over the first nine months of this year, 113,000 videos were uploaded to the websites—a 54 percent increase on the 73,000 videos uploaded in all of 2022. By the end of this year, the analysis forecasts, more videos will have been produced in 2023 than the total number of every other year combined.
These startling figures are just a snapshot of how colossal the issues with nonconsensual deepfakes has become—the full scale of the problem is much larger and encompasses other types of manipulated imagery. A whole industry of deepfake abuse, which predominantly targets women and is produced without people’s consent or knowledge, has emerged in recent years. Face-swapping apps that work on still images and apps where clothes can be “stripped off a person” in a photo with just a few clicks are also highly prominent. There are likely millions of images being created with these apps.
“This is something that targets everyday people, everyday high school students, everyday adults—it's become a daily occurrence,” says Sophie Maddocks, who conducts research on digital rights and cyber-sexual violence at the University of Pennsylvania. “It would make a lot of difference if we were able to make these technologies harder to access. It shouldn't take two seconds to potentially incite a sex crime.”
The new research highlights 35 different websites, which exist to exclusively host deepfake pornography videos or incorporate the videos alongside other adult material. (It does not encompass videos posted on social media, those shared privately, or manipulated photos.) WIRED is not naming or directly linking to the websites, so as not to further increase their visibility. The researcher scraped the websites to analyze the number and duration of deepfake videos, and they looked at how people find the websites using the analytics service SimilarWeb.
Many of the websites make it clear they host or spread deepfake porn videos—often featuring the word deepfakes or derivatives of it in their name. The top two websites contain 44,000 videos each, while five others host more than 10,000 deepfake videos. Most of them have several thousand videos, while some only list a few hundred. Some videos the researcher analyzed have been watched millions of times.
The research also identified an additional 300 general pornography websites that incorporate nonconsensual deepfake pornography in some way. The researcher says “leak” websites and websites that exist to repost people’s social media pictures are also incorporating deepfake images. One website dealing in photographs claims it has “undressed” people in 350,000 photos.
Measuring the full scale of deepfake videos and images online is incredibly difficult. Tracking where the content is shared on social media is challenging, while abusive content is also shared in private messaging groups or closed channels, often by people known to the victims. In September, more than 20 girls aged 11 to 17 came forward in the Spanish town of Almendralejo after AI tools were used to generate naked photos of them without their knowledge.
“There has been significant growth in the availability of AI tools for creating deepfake nonconsensual pornographic imagery, and an increase in demand for this type of content on pornography platforms and illicit online networks,” says Asher Flynn, an associate professor at Monash University, Australia, who focuses on AI and technology-facilitated abuse. This is only likely to increase with new generative AI tools.
The gateway to many of the websites and tools to create deepfake videos or images is through search. Millions of people are directed to the websites analyzed by the researcher, with 50 to 80 percent of people finding their way to the websites via search. Finding deepfake videos through search is trivial and does not require a person to have any special knowledge about what to search for.
The issue is global. Using a VPN, the researcher tested Google searches in Canada, Germany, Japan, the US, Brazil, South Africa, and Australia. In all the tests, deepfake websites were prominently displayed in search results. Celebrities, streamers, and content creators are often targeted in the videos. Maddocks says the spread of deepfakes has become “endemic” and is what many researchers first feared when the first deepfake videos rose to prominence in December 2017.
Since the tools needed to create deepfake videos emerged, they’ve become easier to use, and the quality of the videos being produced has improved. The wave of image-generation tools also offers the potential for higher-quality abusive images and, eventually, video to be created. And five years after the first deepfakes started to appear, the first laws are just emerging that criminalize the sharing of faked images.
The proliferation of these deepfake apps combined with a greater reliance on digital communications in the Covid-19 era and a "failure of laws and policies to keep pace" has created a “perfect storm,” Flynn says.
Experts say that alongside new laws, better education about the technologies is needed, as well as measures to stop the spread of tools created to cause harm. This includes action by firms that host the websites and also search engines, including Google and Microsoft’s Bing. Currently, Digital Millennium Copyright Act (DMCA) complaints are the primary legal mechanism that women have to get videos removed from websites.
Henry Ajder, a deepfake and generative AI expert who has monitored the spread of the technologies, says adding more “friction” to the process of people finding deepfake porn videos, apps to change people’s faces, and tools that specifically allow the creation of nonconsensual images can reduce the spread. “It's about trying to make it as hard as possible for someone to find,” he says. This could be search engines down-ranking results for harmful websites or internet service providers blocking sites, he says. “It's hard to feel really optimistic, given the volume and scale of these operations, and the need for platforms—which historically have not taken these issues seriously—to suddenly do so,” Ajder says.
“Like any search engine, Google indexes content that exists on the web, but we actively design our ranking systems to avoid shocking people with unexpected harmful or explicit content they don't want to see,” says Google spokesperson Ned Adriance, pointing to its page on when it removes search results. Google’s support pages say it is possible for people to request that “involuntary fake pornography” be removed. Its removal form requires people to manually submit URLs and the search terms that were used to find the content. “As this space evolves, we're actively working to add more safeguards to help protect people, based on systems we've built for other types of nonconsensual explicit imagery,” Adriance says.
Courtney Gregoire, chief digital safety officer at Microsoft, says it does not allow deepfakes, and they can be reported through its web forms. “The distribution of nonconsensual intimate imagery (NCII) is a gross violation of personal privacy and dignity with devastating effects for victims,” Gregoire says. “Microsoft prohibits NCII on our platforms and services, including the soliciting of NCII or advocating for the production or redistribution of intimate imagery without a victim’s consent.”
While the number of videos and pictures continues to skyrocket, the impact on victims can be long-lasting. “Gender-based online harassment is having an enormous chilling effect on free speech for women,” Maddocks says. As reported by WIRED, female Twitch streamers targeted by deepfakes have detailed feeling violated, being exposed to more harassment, and losing time, and some said the nonconsensual content found its way to family members.
Flynn, the Monash University professor, says her research has found “high rates” of mental health concerns—such as anxiety, depression, self-injury, and suicide—as a result of digital abuse. “The potential impacts on a person’s mental and physical health, as well as impacts on their employment, family, and social lives can be immense,” Flynn says, “regardless of whether the image is deepfaked or ‘real.’”
90 notes
·
View notes
Text
another dimension.
summary: Miles pays Margo a visit. wc: 970-ish a/n: this mad short but I got rlly busy !! You'll definitely get long3er flowerbyte stuff in the future tho
Margo’s room was so cluttered she couldn’t think.
She’d been letting clothes and unfinished gadgets pile up on the floor and around her desk until you couldn’t even open the door all the way. The realization hit her when she lost a piece of the old vintage radio that Gwen had gifted her to tinker with, and it took her an hour to finally locate it by the foot of her bed.
Margo sat at its edge, re-organizing her gadgets into boxes by size. It made more sense to her than by type or function; when she was restoring an old iPod or laptop, she wouldn’t think, “Where’s the box for tools dedicated to x, y, and z,” she’d be thinking, “Where the fuck is that tiny thing that you need to turn on this other thing?”
At the bottom of one of her hot pink organizers, beneath a tangle of extension cords, Margo felt a round piece of metal. Her fingers brushed over what felt like buttons, and they closed around the mystery device to free it.
It was…oh.
Margo could’ve sworn she had put all of her polaroids and souvenirs in the ‘memories’ box. The memory in question was only a few months old, sure, but it was a memory nonetheless. After Spider Society dissolved, there was no reason for her to use it. At any rate, she had cyber-crimes to stop right here, at her own computer.
Still, she did miss Gwen bringing her old smartphones and wired headphones.
And him.
Margo didn’t like to think about him. Not by any fault of his, but because if she visualized the look he gave her as she tried to send him home, then suddenly those owlish eyes would appear in places they were not supposed to. Then, she would begin to imagine that she saw someone with the same afro pass her on the street, or swear that she heard his voice and wonder if he took his watch with him and kept it.
Margo’s watch was off, but it remained largely intact after The Spot. She stared at it for a moment, before gingerly snapping it around her wrist. She turned it this way and that, letting it catch the dim light of her desk lamp.
E-1610.
Margo had the right dimension this time, all she had to do was just–
She shook her head, hastily taking it off and tossing it back into the box. Now she remembered why the watch had been left there in the first place.
But it was too late, and the image of him grinning at her returned. As she knelt on the floor and resumed her organizing, her mind had begun to weave together a conversation.
Miles would greet her with a “hey”, and she’d “hey” back. Ask him how his parents took the news after everything went back to normal. He’d say he’s grounded, and it’d sound like the funniest thing in the world coming from him. She’d ask him about his hobbies (Miles looked like a gamer), and he would ask about hers. She’d lie and say she didn’t have time for any, and he’d laugh.
“I hear that,” he’d say.
She wondered if her imagination had conjured him up when that familiar flash of blinding light appeared where her closet was and became a spinning portal.
Margo almost didn’t recognize him when he pulled back his hoodie and took the mask off. The high-top fade was gone, replaced by a head of shoulder-length locs that coiled at the ends. But she’d recognize those eyes anywhere.
Her mouth opened and closed as she struggled to locate her words, which made Miles stifle a laugh.
“Miles?”
“Don’t know who else I’d be. Got a minute?”
Slowly reaching back into that same box, Margo breathed,
“Yeah, I…I got a minute.”
“So you’re only Spider-Man when you got the VR thing on?”
Miles called out as he shot another web and catapulted himself off of the roof of a moving truck, and Margo did the same. They landed right on top of Lenny’s Deli, from which they could see a bit of the horizon dotted with skyscrapers in the distance, right where the setting sun started to roll back some of its orange and give way to a wash of coral.
“Pretty much,” Margo answered, catching her breath. “You smell that?”
“Beef patties.”
“I haven’t had one of those in months.”
Miles’ mask squinted mischievously at the eyes. “You want me to get you one, huh?”
“Oh, it’s fine, you don’t have to–”
“I insist!”
Miles was already in the process of swinging down to street level. She shook her head and smiled, sitting with her legs crossed in the meantime.
He was back in a matter of minutes, mask rolled up halfway so that he could carry the brown paper bag from the deli between his teeth as he hauled himself over the ledge where Margo sat.
He opened it and removed his portion before handing the bag to her, but stopped short.
“Hol’ on, can you even eat?”
She threw her head back and laughed.
“You didn’t think about that before you spent your money there?”
“Well, you can take it back with you, probably,” he said as he let her take the bag from him.
“Thanks.”
They sat in silence as only Miles ate his food, watching the world below. Nobody appeared to be committing a robbery at the moment, so Margo eventually broke the silence first.
“So why’d you bring me over here, new guy?”
Miles snorted, “You know I’ve been doing this for almost two years now, right?”
“Well, you’re new to me.”
He leaned back on his elbows and hummed thoughtfully.
“Maybe I’d like to not be so new to you.”
“Sounds like a plan.”
#miles morales#miles morales fic#margo kess#atsv fic#flowerbyte#cybershock#cyberflower#moralesanhour
35 notes
·
View notes
Text
WELCOME TO THE KRIS-KNIGHT EVIDENCE COMPILATION
Originally, this post was me asking why people didn’t like Kris Knight, but eventually I began looking around for evidence and it resulted in this!
At the very least, I want to convince you that it’s not an impossibility.
Technically still a work in progress. Feel free to contribute evidence, counterpoints, or tell me if I’m coming across as rude.
Orange: Catagories
Red: Hypothetical Debunks
Blue: I am confident in this evidence
Green: I am mostly confident in this evidence
Pink: Completely baseless but possible
(Best Evidence)
Kris is the only person we’ve seen creating a dark fountain.
Kris sleeps during the entire class in chapter 2, which means they were up for a while that night. [setting up and creating the fountain]


(Foreshadowing)
Kris is dressed as a knight in The Dark World.
The images that Queen displays during her speech near the end of chapter 2 are of a knife creating the dark fountain.

(Miscellaneous Evidence)
Toby Fox (discussing LIVE A LIVE) said this:
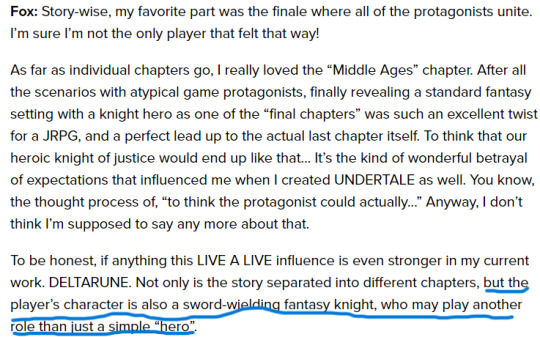
I don’t know anything about LIVE A LIVE but I think this is very good evidence (I think the entire screenshot is important, but the underlined sentence is what initially piqued my interest.)
(Debunking the Debunks)
“Kris just wanted some pie.”
They look to be in extreme pain when pulling out the soul, and as much of a gremlin as Kris is, doing that just for the pie is excessive.

If all they did was eat the pie that night then they shouldn’t be THAT sleepy. It probably took a while to eat but was it enough time to make Kris tired enough to sleep through the ENTIRE class?

“Kris couldn’t have made it to the library within the night at their pace.”
I tested this in game. I tried to match the cutscene Kris’ pace to the best I could. It took me 3:10 mins to get from the center of the bedroom to the computer lab door. Let’s say I was going too fast, so we’ll double that time. 6:20 minutes to get to the library. The trip back would take around the same time so double that again, 12:40. Plenty of time.
At the end of chapter 3 the fountain doesn’t immediately create a dark world, so it’s likely Kris could’ve left the library before the Cyber World was opened.
“How did nobody see them going to the library?”
It’s the middle of the night so most people are probably asleep.
The townspeople don’t know much about humans and Kris is already considered weird so if they saw them they’d probably think this is a normal human thing or just Kris being Kris.
“How would Kris get into the library in the middle of the night?”
Undyne and Alphys both talk about how there’s never any crime. People probably feel safe enough to not lock the doors of their businesses at night.


In fact, the school is a great example of this! Even after the school day is over the doors are still unlocked.
“Noelle and Berdly were in the library when the Dark Fountain was created.”
Alright, this counter-point has a lot of variations. The counterpoints will be represented with PURPLE instead of red. W.I.P and not as well made as the rest.
“Their books were already laid out in the table and open!”
Their books were not open. I don’t know why people think that. (I need to put image of books here)
As for why they’re stacked on the table… I don’t really know. I don’t think they became Darkners, nor were they in Noelle’s inventory. Maybe Berdly’s homework attack? We still don’t really know enough about how Dark Worlds work so it’s not conclusive enough evidence.
Regardless, why would these books, which aren’t even brought attention to, be THE evidence to take down multiple knight theories? It’s a huge stretch.
“The Knight was hiding in the closet!”
The line about a large person being able to fit inside is very vague. It could mean so many things! Spamton NEO, Giga Queen, Berdly’s body…
That’s… a really bad plan. If anyone opens the closet they’re immediately going to find The Knight, holding a weapon. Then The Knight is either cornered or have to attack whoever sees them, regardless, bringing attention to themself.
Not counter-evidence but… That’s terrifying, even if it’s a bad plan. The idea that someone was hiding in the closet wielding a blade waiting for the perfect moment to strike.
“Ralsei said he “felt a dark presence and hurried over”. If the fountain was created earlier why didn’t Ralsei go then?”
If the fountain was created just after Kris and Susie left Castle Town then the Knight would have nowhere to go without being seen. There’s a traffic jam blocking off the rest of the town.
He doesn’t necessarily say that the presence was a fountain. I assume he is talking about the fountain, but still.
He could be lying.
Jeez it’s hard to convey these thoughts in a way that makes sense.
(SOURCES)
1. LIVE A LIVE conversation
(EDITS)
EDIT: Added 1 more category and 1 more evidence.
EDIT 2: Added images to accompany some evidence. (I cannot figure out how to make them smaller)
EDIT 3: Removed some less substantial evidence and replaced it with something better. Reworded some things.
EDIT 4: Reworded some things and completely revised the introduction.
EDIT 5: Added new counterpoint(s).
35 notes
·
View notes
Text
Michael Emerson and Jim Caviezel Share if They Want Their Characters to Survive
Emerson:
We’ve killed off so many people. I don’t know — what’s a good end for Mr. Finch? I never really think about him ending. He would be the last one, I think. But if he went out, he would do it as a sacrifice for another human, I’m sure. Maybe there’s some sort of transformation in store for some of the characters. Something meta, cyber. I don’t know. Maybe there’s a way to be absorbed into the Machine somehow. We’ve never been out that far. And that would be a lot for a show that started out as a crime of the week, procedural. That would be a little cuckoo. But [executive producers] Jonah [Nolan] and Greg [Plageman] say they know the last scene and the last image. Who knows what it is? It’s better if it’s a surprise.
Caviezel:
The laws of averages. It’s the laws of averages. Really, Jonah wrote right [the warning] from the beginning for Finch. The point being, everybody dies, but not everybody really lives, to quote BRAVEHEART. But that’s the truth. This is the first time he’s really had the chance to live, and he at least gets to go up against a formidable foe in Samaritan. He’s very intelligent; he doesn’t play regular chess — that’s what Finch does. I play speed chess. Go fast, hit the clock, attack. He’s always attacking, always on the offensive. And soon enough, you’ll think eventually you go down, but at least you’re fighting. You can say I fought the fight. Teddy Roosevelt: the guys in the ring, the warriors and gladiators in the ring, that other people might criticize and do, but he was all action. I have no idea where they’re going to go with this story. Jonah, he’s Fort Knox. I never have. I never knew what it was. But I think they’ve assembled the best and the worst in all of us. The writers have been able to use parts of the lines that go through us.
Another one
24 notes
·
View notes
Text
Two brothers from Nigeria who targeted a 17-year-old in a sextortion scam have been sentenced to 17 years and six months in jail in the US.
The Ogoshi brothers, from Lagos, lured Jordan DeMay into sending them explicit images by pretending to be a girl his age - then blackmailed him.
He killed himself less than six hours after they started talking on Instagram.
It is the first successful prosecution of Nigerians for sextortion in the US, where it is a rapidly growing cyber-crime, often linked to Nigeria.
Jordan's mother, Jenn Buta, held pictures of her son in court and wept as she read a victim impact statement. "I am shattered to my core," she said.
She welcomed the ending of the trial, but said there was no good outcome from the tragic case.
Jordan DeMay was a popular schoolboy from Michigan.
Samuel Ogoshi, 24, and Samson Ogoshi, 21, sent him a friend request on Instagram pretending to be a pretty girl his age and then flirted with him.
Once they received explicit images from the teenager, they blackmailed him for hundreds of dollars, threatening to share the pictures online with his friends if he did not comply.
Jordan sent as much money as he could and warned the scammers that he would kill himself if they spread the images.
The criminals replied: “Good… Do that fast - or I'll make you do it.”
John DeMay told Marquette federal court in Michigan he still has nightmares after finding his son dead in his bedroom. He said his family was forced to move home to escape the memory.
If you've been affected by the issues in this story, help and support is available via the BBC Action Line
The brothers pleaded guilty in April to conspiring to sexually exploit teenage boys in Michigan and across the US.
Thirty-eight other US victims were also identified as being targeted by the men. 13 of them were minors.
The brothers sat in court in orange jumpsuits with handcuffs.
Their defence attorneys said the brothers' crimes were fuelled by drug abuse and the sextortion scam culture in Nigeria.
The judge said the crimes showed a "callous disregard for life", especially given they continued targeting other victims after learning that Jordan has died.
Both brothers apologised to Jordan's family.
"I'm sorry to the family. We made a bad decision to make money and I wish I could change that," Samson Ogoshi said.
In the first case of its kind, US police tracked the criminals to Lagos last summer and successfully extradited them for trial.
Another Nigerian man linked to Jordan’s death and other cases is fighting extradition.
Speaking to the BBC in May from Jordan's family home in the city of Marquette, Jordan's mother praised the police for their work tracking the sextortionists down.
But she said she had mixed feelings about the Ogoshis being behind bars.
"It's a relief that someone is being held accountable, but there's no good that's coming out of this situation for my family or for the individuals responsible's family," she said.
"I miss my son more than I can describe to you, but the mother of those men is probably missing her two sons as well now. She too is really just an innocent bystander of sextortion crime," said Jenn Buta.
Researchers and law enforcement agencies point to Nigeria as a hotspot for this type of crime.
In April, two Nigerian men were arrested after a schoolboy from Australia killed himself. Two other men are on trial in Lagos after the suicides of a 15-year-old boy in the US and a 14-year-old in Canada.
Nigerian authorities are also working with police in Scotland to investigate the case of 16-year-old Murray Dowey, who killed himself in December.
In January, US cyber-company Network Contagion Research Institute (NCRI) highlighted a web of Nigerian TikTok, YouTube and Scribd accounts sharing tips and scripts for sextortion. Many of the discussions and videos are in Nigerian Pidgin dialect.
Nigeria cyber-security professor Adedeji Oyenuga from Lagos State University says he hopes the news of Nigerians being sentenced will filter through to criminals and put them off.
"The Ogoshis case has already sent a bad signal. I am hearing from street level that it is having an effect and it might not stop criminals turning to these crimes, but it will likely reduce the numbers," he said.
There had been an increase in the number of local victims too and Professor Oyenuga says Nigerian police have had some success in tackling the criminals.
It is not the first time that some of Nigeria’s young, tech-savvy population has embraced a new wave of cyber-crime.
The term "Yahoo Boys" is used to describe a portion of the population that use cyber-crime to earn a living. It comes from the early 2000s wave of Nigerian Prince scam emails which spread through the Yahoo email service.
Dr Tombari Sibe, from cyber-security firm Digital Footprints Nigeria, says cyber-fraud such as sextortion has become normalised among young people in the country, but he hopes that news of the Ogoshis' sentencing spreads fast.
"They see cybercrime as a bloodless crime, with potentially lucrative financial rewards. This case needs to be given sufficient coverage to show these young people that sextortion can lead to loss of life and long prison sentences," he said.
11 notes
·
View notes
Text
Blog Post Week 10: Due 10/31
How do cyber mobs normalize online harassment, and what does this mean for legal and social responses?
Using the book Hate Crime in Cyberspace, Danielle Keats Citron describes cyber mobs as, Mobs from dominant groups are notorious for shaming relatively powerless groups, in taking delight in the discomfort of the excluded and stigmatized. Cyber mobs gather online to harass individuals in degrading and threatening ways (Citron, 2014). So the normalization comes from creating an environment that feeds into abusive behavior, as individuals become so assertive in inflicting harm to others. The mob creates a culture as they tend to recruit members and celebrate them for their contributions to online hate. Currently, the lack of effective policies to address this form of harassment makes it increasingly difficult for victims to receive legal support, especially as technology continues to evolve. This leaves many individuals to navigate their challenges largely on their own. While it may be impossible to completely eliminate cyber mobs, it’s essential to recognize that anyone can fall victim to such groups. By educating ourselves about the harmful effects of these mobs, we can empower ourselves to speak up, report incidents, and assist those who are suffering from their impact.
How can the creation and sharing of fictional narratives, like the Grandpa Wiggly case on Reddit, lead to harmful consequences or negative perceptions?
The Grandpa Wiggly case on the social platform Reddit illustrates how fictional narratives can cause a line between reality and imagination. While it can be fun to create a storyline with plain creativity and community-based opinions, it can lead to misunderstandings and harmful consequences. When stories are taken seriously, they may result in misinformation, panic, or even harassment. Online communities can become negative making it dangerous for creators to continue these narratives as seen in the Grandpa Wiggly case. People were getting out of hand and even sent death threats to portray this image of being a victim to this story. Ultimately, both posters and audiences need to be aware of the potential repercussions of blending fiction with reality.
In what ways can online trolling impact an individual’s life, what does this reveal about digital harassment?
Online trolling can significantly impact an individual’s financial stability by leading to lost income, job opportunities,, and damaged lifelong professional reputations. It is truly devastating to think that your entire lifeline can depend on what happens in these online spaces. For instance, those targeted may be forced to leave their jobs. The emotional toll of trolling can result in mental health issues. Demonstrating how big of an issue is online trolling.
To what extent did Leslie Jones receive support on Twitter? Was it based solely on her celebrity status? What does this reveal about social media platforms?
I believe that Leslie Jones’s experience on Twitter highlights how celebrity status can significantly influence the level of support one receives while engaging in a social media platform. After receiving racist and sexist hate speech associated with her role in the Ghostbusters reboot movie she tweeted how all the negativity was affecting her. She would even tweet out to Twitter asking for help. Since she became a trending topic on Twitter, founder and CEO Jack Dorsey reached out to Leslie and tells her to “DM him.” Releasing this statement: This type of abusive behavior is not permitted on Twitter, and we’ve taken action on many accounts reported to us by both Leslie and others (Seetharaman, 2016). This makes me think back to the case of Grandpa Wiggly where someone who wasn’t well known made this fictional character and he received so much hate. Just like Leslie yet Reddit never took it upon themselves to support this user by “protecting” them in any way. This also makes me wonder about the other stories where other women experienced physical harm coming from online forces but the platforms don’t take it upon themselves to speak out or support. This shows to me that platforms depend on celebrities to demonstrate that they have this sort of “code of conduct” in honor of providing a safe and positive online environment for other users to engage as well.
Bergstrom, K. (2011). “Don’t feed the troll”: Shutting down debate about community expectations on Reddit.com. First Monday, 16(8). https://doi.org/10.5210/fm.v16i8.3498
Citron, D. K. (2014). Hate crimes in cyberspace. Harvard University Press.
Seetharaman, D., & Wells, G. (2016, August 30). Leslie Jones’ horrific online abuse shows how Twitter’s troll problem has spun out of control. Wall Street Journal.
7 notes
·
View notes
Text
The Role of Seperatism in Female Liberation
Yes, seperatism will not end patriarchy. I have never seen any seperatist make that claim so I wonder why anti-seperatists like to point that out like their lives depend on it. Also, no singular act, outside of killing all males, can achieve that.
And yes, seperatism is often an individual action. Just like anti-beauty: not shaving, not wearing make up and heels, etc but we still understand that those acts of resistance, even though individual, have value and contribute positively to women and girls' wellbeing.
What seperatism does claim is that it protects women and girls' wellbeing by denying males access to them.
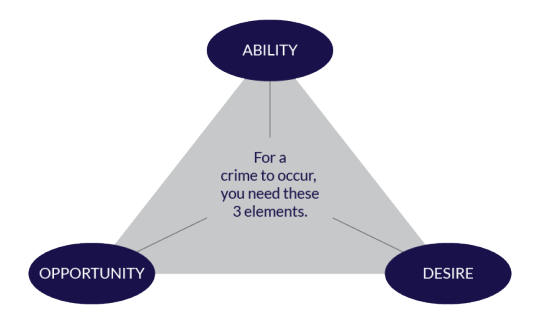
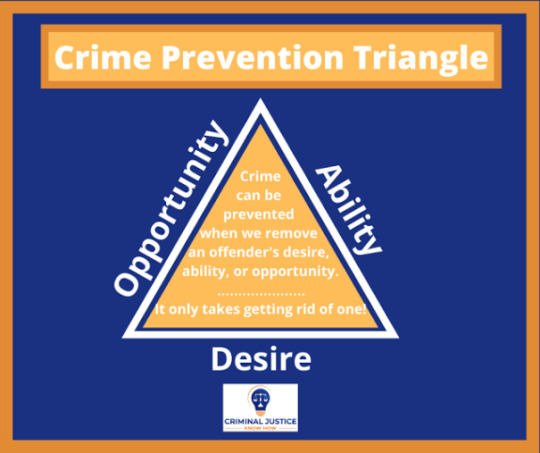
As seen in the images above, for [misogynistic] crimes to happen, all three elements: opportunity, desire and ability must be present and removing just one of them prevents crime. The images above apply to all crimes but since we are talking about female seperatism we can tailor it down to Gender Based Violence (GBV).
Seperatism is about preventing GBV by removing opportunity for harm. Individual seperatists can achieve personal safety in their homes while seperatist communities can achieve community wide safety. So when you claim seperatism is useless you are basically saying crime prevention efforts that focus on denying potential criminals the opportunity to commit crimes is useless. If that is your claim then you have to provide evidence of that.
Seperatists recognise that women cannot influence the ability and desire of males to harm females because behavioural change is self motivated so they focus on what they have control over which is the opportunity for harm.
Now are males, like all predators, going to seek new ways to gain opportunities to harm females, yes of course they are. Outside of GBV, criminals are always changing their strategies especially when their previous strategy becomes well known and people stop falling for it. Using cyber crime as an example because I am Nigerian (LOL), when people stopped falling for the destitute African Prince method, they changed to other methods like romance scams and blackmail. Criminals/Predators are always to seek new ways to catch their victims/prey which is the why the victims/prey must always be alert and aware of the criminals/predators methods so that they can protect themselves.
So yes, as long as men exist, they will be no feminist utopia where women and girls can exist without the threat of violence. We will always need to be on guard and strive to protect ourselves from them no matter the method they use.
Seperatism cannot save all women and girls in the world just like how crime prevention efforts in Ghana cannot save me in Nigeria and I shouldn't even be expecting it to because geography, language barrier, national laws, etc. What can be done is we adapt the methods used in Ghana to our local context and apply it to see results.
Seperatism is an elective individual and geographical community level action that has the potential to save all women and girls but nobody is kidnap unwilling people and hold them hostage.
And I know, someone is going to scream " VICTIM BLAMING" and to that I say, I don't care about being labelled a victim blamer. However, if you have another viable method for keeping women and girls safe, kindly put forward your idea so it can be evaluated. Please note if you suggest "educating men and boys", I will block you because I don't have the patience for that level of stupidity and delusion.
Sidenote:
I always wondered why allegedly smart women will "but child brides in Afghanistan" as a counter to female seperatism. The wins of feminism activism will always be limited by geography. There is no feminist activism that will impact the lives of ALL women and girls. An individual's or organisation's target population will be limited by geography and unfortunately by resources. You can't help everybody applies in feminism too.
Imagine if someone said that about abortion rights in the US. "Fighting for abortion in America doesn't help child brides in Afghanistan". Most people can see how ridiculous and frankly insulting it is to bring up that issue.
40 notes
·
View notes
Note
The fact we still don't know HOW Eden got a new Rayman to be their spokesperson after the real one rightfully called out racism on live broadcast is pretty nerve wracking. We know Rayman's the last of his kind thanks to the Rabbids (heh, meta commentary) so WHERE did they get this one?? Is he a clone? Some kind of advanced robot? And if he's either of those two then what does that mean for the resources Eden has and is fully capable of???
Well that's just it! we have so many QUESTIONS. Like...this hyper capitalistic corporation has it's hand in universal finances, media control, medical experimentation and the military AND the scientific resources to create a gun that can open portals into other dimensions? They literally have a Power Rangers team and a GUNDAM as part of their defence force. It's bananas the power and reach of Eden, and yet there is also a level of flimsiness to them where their whole board of directors can be taken out by one gun wielding madman.
Considering the medical/tech advances they have to produce Dolph's cybernetic enhancements it's not out of the realms of possibility that they would have cloning or advanced cyborg capabilities.
...though this does bring up a theory I have had about S2....which I'll put below the cut ;)
With Dolph dying at the end of S1 and ending up in some kind of cyber network space with Sam Fisher the question of how they're going to bring back the lead for a second series is an important one.
Either you can follow the theory that Eden and everyone in it is part of a simulation, Matrix style, and Dolph dying in Eden isn't actually real so it's easy to just pop him back into the world like in a video game.
OR
Eden has cloning technology and they have a clone of Dolph just waiting in storage.
This would explain the Rayman clone. Eden developed the means of cloning certain important or vital people to keep them safe, and when a person dies the new clone is brought in, implanted with a backup of memories (OR fabricated memories as Eden sees fit!) and sent back out to carry on in the world.
Dolph used to be a highly celebrated and respected member of Eden's military. A marvel of science and biology and a formidable soldier. It would be logical for Eden to keep a clone of him handy just in case he died in conflict. Just like Rayman they could use his prestige as a propaganda tool.
'But Raye! If they had a clone of him why didn't they bring it out to use when Dolph went rogue?'
Because Eden wanted to subdue Dolph first. They couldn't just roll out a clone with the real Dolph running around committing crimes with Alex Taylor. Far better to detain him, kill him, and then roll out the clone with a 'look we fixed him he's good now!' narrative.
They didn't have to do this with Rayman because they believed he was too weak and powerless to do anything, and they needed him immediately to maintain his TV appearances and public image. They could just send Red to get rid of the original whenever (lolololol).
SO my theory is once Dolph went rogue Eden started preparing his clone for a time when they could catch the real one and then take him out. But Sarah Fisher got in the way and snapped up OG Dolph as her personal plaything for the Ghosts, and because of her influence on the board they let her do it. So his clone is just chilling in storage at the moment.
With Dolph seemingly dying in the wasteland fighting Red it's the perfect time for Eden to re-introduce the clone to the city, but my guess is that Sam is going to use his hacking powers to basically shove original Dolph's consciousness back into the clone body (don't ask me how, just say VR did it XD).
Eden is going to end up with what they think is a perfectly reformed and clean Dolph, all the while his original memories and consciousness are riding piggyback in the clone brain waiting for a chance to fight back. Or waiting for a trigger* which will override the clone's mind with original Dolph's (*BULLFROG I MEAN BULLFROG).
That's my theory :3
25 notes
·
View notes
Text
Sextortion training materials found on TikTok, Instagram, Snapchat, and YouTube, according to new report
Sextortion is “a crime that involves adults coercing kids and teens into sending explicit images online,” according to the FBI. The criminals threaten their victims with wide distribution of the explicit images, including to the victims’ friends and family, unless the victims pay them, repeatedly, through a variety of peer-to-peer payment apps, cryptocurrency transfers and gift cards.
Please read the entire article.
It happens a lot. It is also not just strangers that do this. People you considered friends and family can be capable of doing this as well.
Do not send nudes of yourself to anyone. Do not pay anyone if they threaten and tell you they want money to not post them.
In the U.S., people who have experienced sextortion (or their parents or guardians) can report it via the FBI’s cybercrime portal IC3.gov online or a local FBI field office. Sextortion incidents involving a minor should also be reported to the National Center for Missing & Exploited Children or NCMEC Cypertipline at report.cybertip.org or by phone at 800–843–5678.
Please keep yourselves safe.
17 notes
·
View notes
Text

"Unfortunately, I'm not a programmer, we'd need to consult with the cyber crimes division about seeing if it's possible to purge the images from online and tracking the digital footprints to the source of the leak."

"This is why it's important to beef up your cyber security, and be careful about where you're browsing online. I mean, only other advice I can offer is making a statement that they're deepfake."
2 notes
·
View notes