#commercial spyware
Explore tagged Tumblr posts
Text
Weekly output: QuaDream spyware, AI policy, commercial satellite imagery, Discord leaker
I think I have our taxes squared away with two more days until I have to file them–or file for an extension as I often do–so of course I’m worrying about what financial data points I’m overlooking and how they might cause us to pay more than required. 4/11/2023: QuaDream spyware, Al Jazeera The Arabic-language news channel had me make a Skype appearance about this commercial spyware flagged by…
View On WordPress
#AI#artificial intelligence#commercial spyware#Discord leaks#Jack Teixeira#NTIA#Planet Explore#Planet Labs#QuaDream#Russia-Ukraine war#satellite imagery
0 notes
Text
just found some Valiant AU development sketches and notes in my old OLD sketchbook
I really thought it would be a webtoon

long post warning! And I mean long looooooooong post. If you get to the bottom and go "I'm not reading allat" I do not blame you


more under the cut:












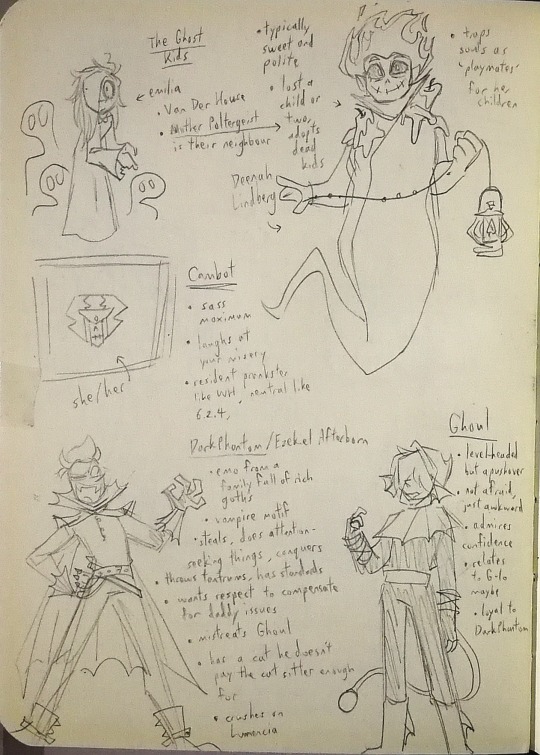



^^^ OC


General notes:
This Valiant AU was meant to be a solarpunk superhero slice of life that slowly reveals a heavier plot, mostly focusing on character interactions and personal growth
White Hat Incorporated is a struggling, newbie business and clients are rare
The episodes can range from domestic shenanigans like fixing a leaking pipe or getting dinner, to running their business by defeating the villain of the week
The villains and heroes stay in their roles from canon. The only ones with major changes are our main 4 guys
All major information about White Hat would be discovered from the point of view of Lumencia and Zug as they realize that not only is PEACE corrupt, but that their boss is neither human nor demon nor alien
Now onto the characters themselves:
Dr. Zug Gleis
Like his name suggests, he likes trains. His train is also a drill that was an attempt to burrow out of government's arrest
Which he then modified into a laboratory, each train cart being a unique kind of laboratory for surveillance, medicine, etc. He sleeps very uncomfortably in cramped spaces and likes it that way
V.I.R.U.S is now a software he created and repurposed into his bratty computer assistant, now Cambot. She's also the one recording all their commercials and making his coffee. Basically Zug doesn't get along with ANY of his children
He doesn't like to leave his laboratories, so he set up a network of tunnels through White Hat's mansion that send and receive messages, inventions, food, etc. There's one little chute for these in most parts of the place
His arc was focusing on his inability to accept help from others because he sees any kind gesture as a possible way to control him. Even worse if the kind person genuinely means it, because he also sees accepting kindness as a handicap, a debt
His villainy was an easy way to make money and show the world his capability without any assistance from any hero or villain organization
Really, he just wants to be able to do whatever he wants, but his need to be the best or else he's the worst is tiring for him. Anger issues don't help
This stemmed from a past of constantly being bullied and compared to his brother, Goldheart
After dropping out of hero college, Zug became his own supervillain's known as The Mad Condoctor, whose theme was, you guessed it, trains. He stole trains, modified scrap metal, targeted stations and trade centers, held hostages, prepared puzzles for heroes to solve, etc
The Mad Condoctor was notorious for being uncooperative and a backstabber. He operated at night and was an expert in secret missions, spyware and tech-based combat and the likes
By the first season finale he would have genuinely cared for his coworkers but still didn't value his own life, so he let himself be taken in by PEACE. The crew have to go retrieve their idiot and many things about White Hat Incorporated are revealed to the public after they clash with their local PEACE headquarters
He finds authority annoying and hates seeing people kiss up. Mostly shameless in his actions and doesn't much care for other people's opinions. Can be honest to the point of hurting
So he is a terrible liar. It's like he's allergic to it or something. Prefers to lie by omission
Will only call White Hat 'sir' and 'jefecito' sarcastically or to get a point across. Unfortunately hopelessly devoted to him at the end of the series whoops
Lumencia
A superwoman with horse-like powers that decided to choose unicorns as her motif because that's way cooler. She has kicks and punches that convert her diet into energy, which is great because she loves eating
Changed it up so that Lumencia is the resident prankster and WH tells puns, not the other way around
She has a room with a slanted ceiling which she can climb out the window of to lie and chill on the roof. She's also converted that space, where flat roof meets slanted roof, into an outdoor cinema/gym, decorated with christmas lights. The mansion is a three-way clash of decorative styles from afar
She doesn't have a license to be a hero, but she helps out wherever she can anyway, stopping purse snatchers and helping lost children find their parents and such
In fact, she is actually one of the most beloved people in the little town they live near, with many residents familiar with her buffoonery but affirming her as a reliable source of help
She's also relatively well-known online, as she posts videos of her playing the guitar and well-intentioned but nonsensical 'Lumencia Tips', filled with terrible puns and comic-like ballpoint pen doodles
Her arc would have focused on letting herself acknowledge her strengths that aren't related to fighting
Shes very buddy-buddy with petty criminals and shop owners alike, able to strike up a conversation and make pals no matter who they are. Once she deems you chill, you can chill, yknow? This isn't on purpose.
Even though she has gross taste in food and is messier than Zug, her handwriting is very pretty and neat. She also is very good at graffiti and sticks to an aesthetic, with glitter and y2k stickers and denim-clad wizards on skateboards, all the works
She has a very straightforward view on heroics and is not big on plans, preferring to punch her way out of situations or annoy her enemies to tears. In fact, her main goal is to become an official part of one of the many PEACE-brand hero leagues.
There's other hero corporations too but PEACE is the number one in America
So one day she just showed up on White Hat's doorstep and never left because it would 'look good on her resume'.
Previously, she bounced from place to place, relying on connections and the occasional tip from her halfway-illegal heroism efforts to get by. She also doesn't remember where her powers are from, only that her parents worked at PEACE and where killed by 'villains' when she was a little girl
Her favourite place is the funfair because that's the last nice memory she had
By season two she would have started another arc where she learns that she was an experiment and her parents were killed by their own higher ups in PEACE to silence them, and she has to come to terms with why she even wants to be a hero as well as stand her ground when her optimism is challenged.
Lumencia's music is like whatever Equestria Girls and Electric Mayhem have going on. I think the genre is power pop? Either way it sounds like those elaborate 80s radical van murals look
Is an effortless liar in the sense that she says the most batshit things with utmost confidence and treats consequences like an afterthought.
Only calls White Hat 'White Hat' and not 'boss' when she feels the situation calls for it. Also unfortunately hopelessly devoted to him by the end of the series
624
An extra set of hands that cleans the place and helps out with their little business. Does not like being interuppted when listening to music
Goes from 'fucking hate these guys' to 'they give me food therefore they are mine' in the span of the entire series
Quite lazy, plays the winning side. Which is usually the heroes here
Dunno if I'd call his arc an arc. All I know is there's an episode where his spoilt teenager-ismd hits their peak and Zug and Lumencia have to reach an understanding with him by respecting his boundaries and helping him feel secure
And after that episode, 624 stopped being a total catalyst for disaster plotwise
White Hat
He is one of the comic reliefs and manages White Hat Incorporated, often making really stupid decisions because profit is not on his mind
The final voice I settled on for him was fucking Australian Markiplier
His "growth" would be the characters and readers seeing him to actually be a caring, experienced-in-heroics-but-not-business individual who gives really sound advice and becomes a source of comfort for his close friends
But is still a MEGA-PRICK. Every time he gets beat up it's for a valid reason
In canon, villainy triumphs because Black Hat is there. In the Valiant AU, the story is in the heroes' favour because White Hat is in his place.
I wanted him to be (mostly) opposite to Black Hat in many ways! BH's office is huge, minimalistic, corporate and cold, while WH's office is small, maximalistic, filled with sentimental items and like a warm cabin.
BH basks in hellfire and while WH does use fire, he prefers the ocean. BH enjoys golf, WH enjoys dancing. BH takes himself seriously, WH very much doesn't. BH detests everything, WH has an appreciation for everything. And etc...
They're still horrible creepy eldritch monstrosities, the fish theme for WH is just because he likes ocean shit and fish are scary
BH has made himself known globally and universally, he has statues and monuments and paintings
WH has nothing; White Hat is five years old. This is his first time being White Hat
But he's been around since the beginning of time, taking many forms and names, learning the wonders of the universe and giving all of his time to help however he could
He believed this to be natural, he's the one of a kind who doesn't need rest or food. He can't die or get really hurt, and would later learn he couldn't bear to love either
Some of the things he was included many plants and animals before the humans, then farmers and warriors, witches and politicians, an entertainer vigilante, a writer, a parent, a fur-clad warrior in the snow, guiding forces of nature, and a female pirate.
I wanted him to cycle through the entire alignment chart in terms of morality as he exhausted everything he could do to make a difference
After World War 2 on earth, his psyche gave out and he collapsed into a long, long nap; a shadow pooling in a lake, his favourite
Finally woke up and decided to take his own form not based on any species or star or tree, chose his own outfit and everything
And made his debut as White Hat, forged documents to start a small business for heroes support
He doesn't have an arc, but if he did, he would be in the midst of learning to let himself get attached again and be properly selfish. Maybe identity issues.
But he doesn't have an arc
And so really only serves to help out Zug and Lumencia. He's comfortable with no one knowing these things about him ever, because what would they even do if they did?
Wouldn't change anything, they wouldn't understand the full scope even, so he's at peace with himself right now, grateful that he's alive for once
He uses manipulation to direct conversations away from himself and get people to spill their feelings, or burrow into their trauma without using magic
if he wants he can let loose to trigger some kind of indescribable primal instinct within a person, that cripples them with terror and despair and love for the sublime face of something divine, bigger than the observable universe. He doesn't like doing this.
He's a fan of ice and shadow manipulation, he thinks the colours go well with his coat
Most animals hate him and he cries about it
He also cries when he tries to download an app on a laptop
He is a competent medical doctor, babysitter, and waiter. In fact, he seems to have infinite patience and calm when he isn't whining over dessert like a toddler
The human skeleton hanging in his office is real
Hopelessly attached to Lumencia, Zug and 624 by the end of the series but they don't need to know that
This AU will forever make me warm and fuzzy inside I love them so much, I had so many locations planned, started Pinterest boards and shit
Instead I think I'll take some of these things and apply them to my OCs instead! HUGE thanks to everyone who enjoyed this version of this AU while it lasted! Maybe it'll come back one day, maybe not. Likely not
#my post#my art#art from last year#villainous valiant!au#villainous heroic!au#villainous#villainous hbo max#villainous cn#miss heed#white hat#dr zug gleis#lumencia#624#long post#not tagging all these characters
175 notes
·
View notes
Note
After seeing your weatherbugapp reblog i installed duckduckgo and tried it.
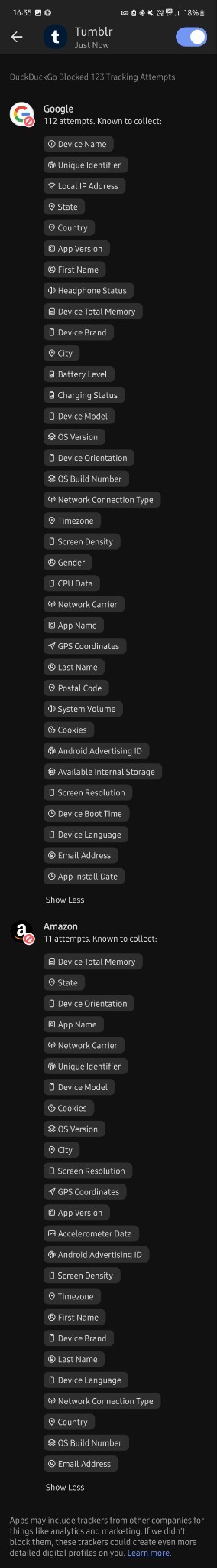
I don't know much about technology tbh but i downloaded this app less than 30 mins ago and in that time google tried to track me 112 times?? And they tried to collect finger prints? And my first and last name? And my gender? And my country, state and city? My gps coordinates? My postal code? My network carrier? My fricking battery level for whatever reason? Can you please tell me if this is normal at all, because i'm freaking out right now. I just turned 18 and started using mobile banking and stuff and this shit scares me
Why tf does it need to know my screen density???my system volume????my charging status????? What tf are they cooking
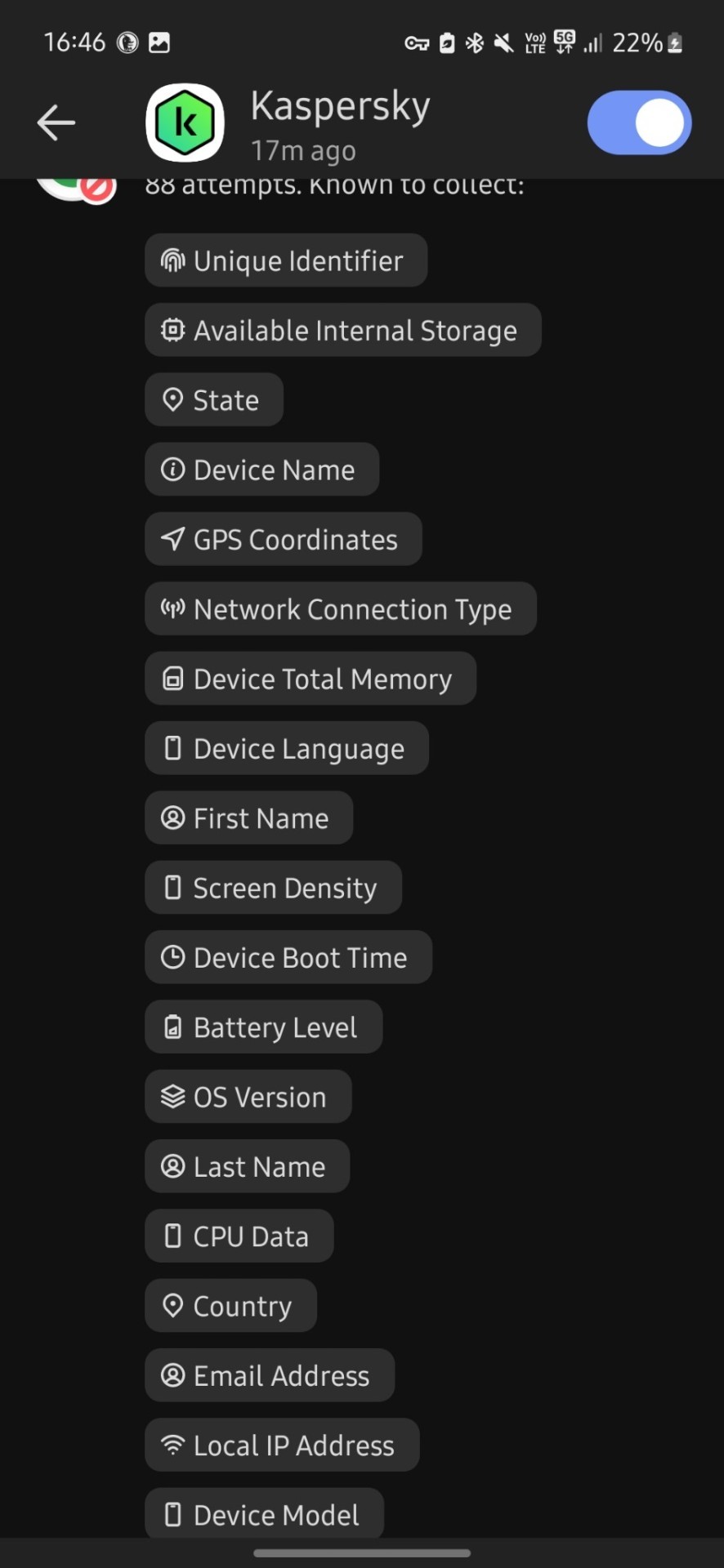
Now it's at 476 tracking attempts bro???? barely 5 mins passed.....
I condensed your three asks into one for readability!
And yeah, I'm very far from an expert about any of this, but as far as I know that's just. Normal. That's the normal amount of spying they're doing on your phone. I assume the numbers we see are to some extent because having been foiled, a lot of these scripts try repeatedly, since I can't imagine what use thousands of trackers per phone would be even to the great aggregators.
Tracking the phone stuff like screen resolution and battery level is because (apart from that definitely not being considered remotely 'private' so it's Free Real Estate) in aggregate that data can be used to track what phone use patterns are like on a demographic scale and therefore. Where the smart money is.
Almost all of this is getting sold in bulk for ad targeting and market analysis. This does presumably make it very hard to notice when like. Actually important stuff is being spied on, which is why I feel better about Having Apps with the duckduckgo app blocker thing.
My bank's app reportedly sells data to a couple aggregators including Google. Not like, my banking info, but it's still so offensive on principle that I avoid using the app unless I have to, and force stop it afterward.
The patterns that show up on the weekly duckduckgo blocker report are interesting. Hoopla attempts about two orders of magnitude more tracking than Libby, which makes sense because they're a commercial streaming service libraries pay by the unit for access, while Libby is a content management software run by a corporation that values its certification as a 'B' company--that is, one invested in the public good that can be trusted. The cleanness of their brand is a great deal of its value, so they have to care about their image and be a little more scrupulous.
Which doesn't mean not being a little bit spyware, because everything is spyware now. Something else I've noticed is that in terms of free game apps, the polished professional stuff is now much more invasive than the random kinda janky thing someone just threw together.
Back in the day you tended to expect the opposite, because spyware was a marginal shifty profit-margin with too narrow a revenue stream to be worth more to an established brand than their reputation, but now that everyone does it there's not a lot of reputation cost and refraining would be sacrificing a potential revenue stream, which is Irresponsible Conduct for a corporation.
While meanwhile 'developing a free game app to put on the game store' is something a person can do for free with the hardware they already have for home use, as a hobby or practice or to put on their coding resume. So while such apps absolutely can be malicious and more dangerous when they are than The Big Brand, they can also be neutral in a way commercial stuff no longer is. Wild world.
But yeah for the most part as far as I can make out, these are just The Commercial Panopticon, operating as intended. It's gross but it probably doesn't indicate anything dangerous on an individual level.
54 notes
·
View notes
Text
A $2 million contract that United States Immigration and Customs Enforcement signed with Israeli commercial spyware vendor Paragon Solutions has been paused and placed under compliance review, WIRED has learned.
The White House’s scrutiny of the contract marks the first test of the Biden administration’s executive order restricting the government’s use of spyware.
The one-year contract between Paragon’s US subsidiary in Chantilly, Virginia, and ICE’s Homeland Security Investigations (HSI) Division 3 was signed on September 27 and first reported by WIRED on October 1. A few days later, on October 8, HSI issued a stop-work order for the award “to review and verify compliance with Executive Order 14093,” a Department of Homeland Security spokesperson tells WIRED.
The executive order signed by President Joe Biden in March 2023 aims to restrict the US government’s use of commercial spyware technology while promoting its “responsible use” that aligns with the protection of human rights.
DHS did not confirm whether the contract, which says it covers a “fully configured proprietary solution including license, hardware, warranty, maintenance, and training,” includes the deployment of Paragon’s flagship product, Graphite, a powerful spyware tool that reportedly extracts data primarily from cloud backups.
“We immediately engaged the leadership at DHS and worked very collaboratively together to understand exactly what was put in place, what the scope of this contract was, and whether or not it adhered to the procedures and requirements of the executive order,” a senior US administration official with first-hand knowledge of the workings of the executive order tells WIRED. The official requested anonymity to speak candidly about the White House’s review of the ICE contract.
Paragon Solutions did not respond to WIRED's request to comment on the contract's review.
The process laid out in the executive order requires a robust review of the due diligence regarding both the vendor and the tool, to see whether any concerns, such as counterintelligence, security, and improper use risks, arise. It also stipulates that an agency may not make operational use of the commercial spyware until at least seven days after providing this information to the White House or until the president's national security adviser consents.
“Ultimately, there will have to be a determination made by the leadership of the department. The outcome may be—based on the information and the facts that we have—that this particular vendor and tool does not spur a violation of the requirements in the executive order,” the senior official says.
While publicly available details of ICE’s contract with Paragon are relatively sparse, its existence alone raised alarms among civil liberties groups, with the nonprofit watchdog Human Rights Watch saying in a statement that “giving ICE access to spyware risks exacerbating” the department’s problematic practices. HRW also questioned what it calls the Biden administration’s “piecemeal approach” to spyware regulation.
The level of seriousness with which the US government approaches the compliance review of the Paragon contract will influence international trust in the executive order, experts say.
“We know the dangers mercenary spyware poses when sold to dictatorships, but there is also plenty of evidence of harms in democracies,” says John Scott-Railton, a senior researcher at the University of Toronto’s Citizen Lab who has been instrumental in exposing spyware-related abuses. “This is why oversight, transparency, and accountability around any US agency attempt to acquire these tools is essential.”
International efforts to rein in commercial spyware are gathering pace. On October 11, during the 57th session of the Human Rights Council, United Nation member states reached a consensus to adopt language acknowledging the threat that the misuse of commercial spyware poses to democratic values, as well as the protection of human rights and fundamental freedoms. “This is an important norm setting, especially for countries who claim to be democracies,” says Natalia Krapiva, senior tech-legal counsel at international nonprofit Access Now.
Although the US is leading global efforts to combat spyware through its executive order, trade and visa restrictions, and sanctions, the European Union has been more lenient. Only 11 of the 27 EU member states have joined the US-led initiative stipulated in the “Joint Statement on Efforts to Counter the Proliferation and Misuse of Commercial Spyware,” which now counts 21 signatories, including Australia, Canada, Costa Rica, Japan, and South Korea.
“An unregulated market is both a threat to the citizens of those countries, but also to those governments, and I think that increasingly our hope is that there is a recognition [in the EU] of that as well,” the senior US administration official tells WIRED.
The European Commission published on October 16 new guidelines on the export of cyber-surveillance items, including spyware; however, it has yet to respond to the EU Parliament's call to draft a legislative proposal or admonish countries for their misuse of the technology.
While Poland launched an inquiry into the previous government’s spyware use earlier this year, a probe in Spain over the use of spyware against Spanish politicians has so far led to no accusations against those involved, and one in Greece has cleared government agencies of any wrongdoing.
“Europe is in the midst of a mercenary spyware crisis,” says Scott-Railton. “I have looked on with puzzled wonderment as European institutions and governments fail to address this issue at scale, even though there are domestic and export-related international issues.”
With the executive order, the US focuses on its national security and foreign policy interests in the deployment of the technology in accordance with human rights and the rule of law, as well as mitigating counterintelligence risks (e.g. the targeting of US officials). Europe—though it acknowledges the foreign policy dimension—has so far primarily concentrated on human rights considerations rather than counterintelligence and national security threats.
Such a threat became apparent in August, when Google’s Threat Analysis Group (TAG) found that Russian government hackers were using exploits made by spyware companies NSO Group and Intellexa.
Meanwhile, Access Now and Citizen Lab speculated in May that Estonia may have been behind the hacking of exiled Russian journalists, dissidents, and others with NSO Group’s Pegasus spyware.
“In an attempt to protect themselves from Russia, some European countries are using the same tools against the same people that Russia is targeting,” says Access Now’s Krapiva. “By having easier access to this kind of vulnerabilities, because they are then sold on the black market, Russia is able to purchase them in the end.”
“It’s a huge mess,” she adds. “By attempting to protect national security, they actually undermine it in many ways.”
Citizen Lab’s Scott-Railton believes these developments should raise concern among European decisionmakers just as they have for their US counterparts, who emphasized the national security aspect in the executive order.
“What is it going to take for European heads of state to recognize they have a national security threat from this technology?” Scott-Railton says. “Until they recognize the twin human rights and national security threats, the way the US has, they are going to be at a tremendous security disadvantage.”
8 notes
·
View notes
Text
Not the point of that post abt commercial tech being essentially spyware, but the comment about most weather services being government projects that wouldn't want to be publicly associated with malicious activity reminded me of this:


17 notes
·
View notes
Text
So-called Project Ghostbusters—echoing the iconic rival's logo—appears to have been just the beginning of the wider In App Action Panel (IAAP) program which aimed to spy on competitors' traffic to gain commercial advantage. It's thought to have run between June 2016 and approximately May 2019, with YouTube and Amazon being the next targets.
Meta, Facebook's parent company, employed its controversial VPN service as a way to intercept and decrypt the traffic between the people accessing its service and competitors' servers. The company shut down Onavo in 2019, following a TechCrunch investigation revealing the spyware-like VPN software was employed in a research project to collect sensitive user data from paid volunteers aged between 13 and 25.
"Facebook’s IAAP program conduct was not merely anticompetitive, but criminal," read the filings revealed on March 26, 2024, by a federal court in California during the class action lawsuit between consumers and Meta.
5 notes
·
View notes
Text
Google Patches 4th Chrome Zero-Day (CVE-2024-5274) in Two Weeks

Again, Google has moved swiftly to address a critical vulnerability in its widely-used Chrome web browser, releasing an urgent security update on Thursday to neutralize an actively exploited zero-day flaw. This marks the fourth vulnerability to be patched within two weeks, underscoring the ongoing battle against cyber threats targeting popular software. Exploited Vulnerability Triggers Emergency Response The high-severity vulnerability, tracked as CVE-2024-5274, is a type confusion flaw residing within the V8 JavaScript and WebAssembly engine, a core component of the Chrome browser. Google acknowledged that an exploit for this vulnerability already exists in the wild, posing a significant risk to users. While Google refrained from divulging specific details about the vulnerability or its active exploitation to safeguard users, the company swiftly credited Clement Lecigne of Google's Threat Analysis Group (TAG) and Brendon Tiszka of Chrome Security for reporting the flaw. No bug bounty reward will be awarded for this discovery. Chrome vulnerabilities, particularly zero-days, have long been a target for commercial surveillance software vendors and other malicious actors. Google's TAG researchers have previously reported several instances of zero-days being exploited by spyware vendors, highlighting the persistent threats posed to the popular browser. A Flurry of Patches in Recent Weeks The patching of CVE-2024-5274 marks the fourth Chrome zero-day to be addressed within the last 15 days, following the resolution of CVE-2024-4671 (use-after-free in Visuals), CVE-2024-4761 (out-of-bounds write in V8), and CVE-2024-4947 (type confusion in V8). In total, Google has resolved eight Chrome zero-days so far this year, with three of them being demonstrated at the prestigious Pwn2Own Vancouver 2024 hacking contest in March. Prompt Updating Recommended The latest Chrome iteration, addressing CVE-2024-5274, is now rolling out as version 125.0.6422.112 for Linux and version 125.0.6422.112/.113 for Windows and macOS. Google has also released Chrome for Android versions 125.0.6422.112/.113 with the same security fixes. Users are strongly advised to update their Chrome browsers immediately to safeguard against potential exploitation of this critical vulnerability. Read the full article
2 notes
·
View notes
Text
Most notorious instances of commercial spyware

Source: https://www.kaspersky.com/blog/commercial-spyware/50813/
3 notes
·
View notes
Text
What frustrates me about The Discourse about AI art is that everyone feels the need to have An Opinion...and no one is willing to look into the conversations that have been going on for DECADES surrounding the relevant issues, or the cases that set precedent for what we can do here going back CENTURIES.
Let me lay out two very important things here:
The dataset ethics issue is more of an issue of digital privacy than copyright.
The labor issue has been seen MANY times throughout history; we can look to MANY other times new tech has shaken up a job market for precedent before AI even STARTS being used on large commercial projects.
Point #1 is true because, I have said before and I will say again, image synthesis is not collaging. It is not copy-pasting. It does not composite images in the dataset. It doesn't even save the images. It looks for patterns in the pixels and tries to recreate similar patterns from random or semi-random noise. This is why it often sucks at anatomy without human guidance - it recognizes that the word "hair" usually corresponds to a pattern that usually goes near a pattern that corresponds to a "head", it recognizes that "hands" usually have a certain pattern of repeating light and shadows, but it doesn't understand the intricacies of where those things belong or how many times a pattern might repeat. This is why images of architecture often have impossible geometry - it understands the shapes that these things tend to take; it doesn't understand the logic of what connects to what. People can use it to plagiarize - they can, intentionally or otherwise, force a result that is overfitted to a specific piece of data in the set - but to say that's ALL it does is comparable to the asinine claim that ALL referencing is plagiarism, because SOME people will just straight up trace or recreate a full piece that already exists, sometimes even by accident. (And some people - not all, not even most, but some who claim plagiarism, whether from AI or traditional art, are just...really? Do you really think you are the only person who has ever drawn, say, a pink fairy sitting under a purple luminescent mushroom, gazing at a full moon in the upper left, composed with the 1/3s rule? Do you really?)
And the thing is, I agree that the kind of broad data scrapes that have been used to create most AI models should be reserved solely for scientific curiosity if they're used at all, and I respect anyone who doesn't want to touch image synthesis until that issue is resolved. The only reason it doesn't bother me too much to play with it myself is that...unfortunately, we're all interacting with much worse as we speak. Ever heard the word "spyware?" If you're old enough to know it, notice how you stopped hearing it when Facebook normalized making literally the majority of the internet into spyware?
You can't really use the internet while wholly blocking Google, and their evils are pretty well documented. (Remember when we rolled our eyes at their internal "don't be evil" slogan? And how deeply unsettling it was to then watch them REMOVE that while ramping up aggressive datamining?) Amazon made Alexa to harvest your data to sell you shit more effectively. If you have a smartphone, Google or Apple or both are harvesting your data for all kinds of much more malicious purposes than making pretty pictures. Twitter uses your tweets and browsing patterns to force you to interact with people you will hate because negative emotions hold your attention better than positive ones and they want that sweet sweet advertiser money from your constant engagement; this was the case even long before Elongated Muskrat took over. Spotify Wrapped and knockoffs thereof are ~fun tools~ that...normalize just handing data about some pretty personal things over to anyone who dangles a shiny novelty in front of you made with it. It's used for invasive surveillance and policing, and Facebook's for-profit datamining even ended up being a tool of election interference - had it not been for them we might not be in nearly such a bad state with the rise of global fascism.
Image synthesis is one of the most harmless and even potentially BENEFICIAL things to be created as a result of this disturbing norm.
The fact is, small artists: copyright law may protect you a little, sometimes, but it wasn't made for us (and yes, I say "us", because even if you don't count my partially AI work as art, I do traditional art too, guys). It was made for Disney and their ilk. It is designed to protect corporate interests, not artistic ones. That notwithstanding, the copyright angle is a weak one in the first place - it's easy to argue that, because the process is transformative enough, and the dataset is large enough and abstracted enough from anything it was derived from, AI training on online art would fall under fair use, and it is only individual misuses that would constitute infringement. It's especially easy to argue this when you recognize that, at this point, that's more where the corporate interest lies, and remember who the laws are made for!
Digital privacy, on the other hand? The right to your own data? The right to be forgotten? The need to have regulations on where robots can and cannot crawl, and for what purposes? THAT is a critical conversation that we need to be having here, and if everyone with An Opinion on AI art focused their energy there instead of mostly just misinformed screaming about the sky falling and Art Dying And Society Degrading (which is HORRIFYING to hear from leftists in knowing its history as a fascist talking point), we could probably get some MAJOR good done.
Furthermore, even if someone ruled that AI training doesn't constitute fair use under copyright law, that won't stop big companies from using AI - Disney has PLENTY of frames of animation to feed a model to make something entirely their own. So do most animation studios. I have even been in talks with people trying to work on a 100% public domain AI model - the biggest concern about it is that if we complete and finalize it before the labor side of the issue is being worked around properly, it will EMBOLDEN unethical use in industry by getting rid of the potential legal complications.
So let's talk about the labor side and recognize - this isn't the first time new tech has threatened to make major changes to the way something is done in industry, potentially resulting in workforce downsizing. It won't be the last. Honestly, as a person who's been both machining and doing mixed media art since I was a kid (and sometimes both at the same time), I find it deeply disheartening how many people have not cared about this side of the issue until it was certain art jobs that might get automated...and even more frustrating how people refuse to look to past cases for how the harms of new tech shaking up employment have been mitigated.
What we could and should be fighting for is a government program to compensate and optionally retrain employees who were laid off due to automation (ANY automation, not just in art!!), as well as independent workers who see a drop in income due to increased market saturation. We can do this. We've done it before.
We could and should also be fighting for UBI - this will be harder, but it's more popular now than it ever has been and some places are even TESTING it while the internet watches; it is not nearly as much of a pipe dream as it once was.
What's NOT going to help anyone is devaluing the labor of new automation tech operators - that INCENTIVIZES the corporations to adopt it FASTER where possible, and treat both new and existing employees WORSE. "I could replace you with a robot; you're employed out of the goodness of my heart" is one of the most common justifications for abusing and underpaying employees in relevant positions. Big media companies already rely on crunch at poverty wages; they're only going to get worse about it with AI tech because "oh you're just pushing buttons, what do you mean you can't do that for 20 hours at barely minimum wage, how lazy can you get?" if we continue this line of thinking. However, if we recommend and enable new automation operators - in all industries - to UNIONIZE before their work and thus their mistreatment even starts, it will make the transition a hell of a lot easier on both new and existing workers.
Tl;dr: It's great that we have a lot of people concerned about artists' labor rights and tech transparency now PLEASE LEARN YOUR HISTORY AND DIRECT YOUR ENERGY WHERE IT IS NEEDED INSTEAD OF ASSUMING YOU KNOW EVERYTHING FROM A FEW SENSATIONALIZED ARTICLES I BEG OF YOU
30 notes
·
View notes
Text
Weekly output: White House commercial-spyware limits, Amazon opens Sidewalk to developers, MLB's tech upgrades
This week involved my having to finish a whole more writing than what you see below, so you can imagine my relief at still being able to step away from the keyboard in time to see the Dungeons & Dragons movie with friends Friday evening. 3/27/2023: White House Exec Order Bans Government Use of Most Commercial Spyware, PCMag I wasn’t sure there was a story in this executive order until I saw…

View On WordPress
#Amazon Sidewalk#baseball#Biden executive order#commercial spyware#IoT#mesh network#MLB app#MLB Gameday#MLB.tv#NSO Group#Pegasus
0 notes
Text
yknow how "spyware" has fallen out of use as a term because it's now a standard part of commercial systems
ive come to notice a cultural term that has similarly fallen out of use due to the practice's everyday normalization... "fairweather friend"
#this isn't aimed at anyone dont worry#it's just something that weighs on my mind the more people i meet that only care about others while it's profitable#living in the trough of a cultural cycle is bleak man...#even the fortunate who have no worry of starvation regress to animals whose only concern is with their next proverbial meal#i keep meeting people who like to say they're full of love... but vanish the moment an interaction becomes something other than enjoyable#even though in peacetime they'll go on and on about how important others are to them and how deeply they care#the moment the clouds roll in over said loved ones and the free food dries up... theyre long gone without so much as a goodbye#in the end it's always like... “you've never loved another person in your life have you..?”
4 notes
·
View notes
Text
Howdy y'all. Voxong here. Now, I know times have been tough. Lotsa folks are in a bad way but adjustments are bein' made! Some changes are gonna have to be made to make room for new businesses, industries, and with it all, jobs.
Ascension Co reached out to the three families with a solution to our problems, and with Ascension Co's sponsorship, all three families agreed. The laws restrictin' robits and cybernetics have been abolished.
Now I know what yer thinkin', all worried and qihit, but Ascension Co assures us that the technology used to make these robits ain't like nothin' in Zangren history. No need for regular memory wipes, no arisin' self awareness, none of that junk. The cybernetics are safe too, no spyware or anythin' in 'em. I mean look at me, with my new implants and my new robit, all brand spankin' new, and flaw free.

At the moment though, very few robits are in production. In fact, my robit is the only one outside Ascension Co right now. Ascension Co needs to grow a lil', and we're gonna give 'em the space to. But think about it folks, all the jobs that'll rise from this, the robit maintaince shops, the modifyin' shops, cybernetic parlors, the works.
If that ain't enough to convince ya to stop riotin'. And yeah I see ya, Section-B3, the environmental controls are gonna switch to tear gas if ya don't stop. Maybe this'll convince ya otherwise... Once production's in full swing, there's gonna be robit colonies, nice and safe and far away from y'all, and then they'll be floodin' the market with resources. The value of resources will go down to match the zie.
And once y'all get comfortable with the new reality of robits, and they're livin' among us, then guess what? Ya don't have to work the bad jobs no more. We'll make more room for better positions, no more breakin' ya back over some minerals. How's that sound? Nice and dandy? I'd fengin' hope so.
Riotin' stopped?
Not 'cause of anythin' I said? Well...
Yeah I bet the fengin' tear gas atmosphere got 'em runnin'.
Now, if ya don't mind, I got an appointment with a jellyfi-

Woahly qihit yer suit's fengin' huge! No heads up about that, folks? By Qhong, ya bingun, ya gotta warn me about that, silly robit!
Uh... cut to commercial. We got a sensitive trade deal to hash out.

[RUNNING: OP_SUBLIMINAL_MESSAGE_SOOTHING_WAVES.msc]
4 notes
·
View notes
Text
7 notes
·
View notes
Text
As the Israel-Hamas war escalated this week, WIRED looked at the conditions that contributed to Israel's intelligence failures ahead of Hamas' initial attack last Saturday, as well as the hacktivism and digital mayhem that has subsequently sprung up around the kinetic war. The situation has led to a torrent of misinformation across global discourse, particularly on the social media platform X (formerly Twitter), where fake photos, old videos, and video game footage have exploded on an unprecedented scale.
X’s Trust and Safety team claims it has been working to address the situation, but company CEO Elon Musk has been “posting through it,” sharing conspiracies and engaging with QAnon discourse on the platform. The chaotic situation on X has been difficult for the average user to keep up with. In one case, a graphic Hamas video that Donald Trump Jr. shared on the platform actually turned out to be legitimate, even though it seemed at first look like it might have been part of the broader deluge of misinformation. And beyond just X, rumors of a “Global Day of Jihad” on Friday unleashed a dangerous wave of disinformation across digital platforms—one that threatened to cross into real-world violence.
With the trial of FTX founder Sam Bankman-Fried in full swing this week, WIRED took a deep look at the day someone stole hundreds of millions of dollars from the ill-fated cryptocurrency exchange as it was declaring bankruptcy. And new evidence released by researchers this week indicates that the stolen FTX funds went through a chain of intermediaries that eventually led to Russia-linked money launderers.
As chaos in the United States House of Representatives continues over Republicans' inability to deal with far-right hardliners and elect a new speaker, WIRED reported that Republican Party leaders have imposed cell phone bans in an attempt to keep backroom dealmaking under wraps. The United Nations' top internet governance body may host its next two annual meetings in countries known for repressive digital policies and abusive information control, which risks normalizing internet censorship. And white supremacist “active clubs” are gaining traction in part through communication on the messaging app Telegram.
Meanwhile, Google announced this week that it will make the more secure password replacement known as passkeys the default login option for its personal account holders as part of the company's efforts to promote adoption of the technology. And a new internet protocol vulnerability known as “HTTP/2 Rapid Reset” impacts virtually every web server around the world and will take years to stamp out, exposing some sites and digital services to denial of service attacks long-term.
And there's more. Each week we round up the security and privacy news that we didn’t cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
Vietnam Used Predator Spyware to Target US Congress
Notorious high-end commercial spyware like Pegasus and Predator has been used over the past decade to target human rights activists, protesters, and journalists. But a foreign nation using it to target the smartphones of US members of Congress represents a rare and brazen new appearance of those notorious tools. On Monday The Washington Post, along with a consortium of more than a dozen international media outlets, revealed that the Vietnamese government used that Predator spyware, distributed by the surveillance firms Cytrox and Intellexa, to target at least four members of Congress—representative Michael McCaul and senators Chris Murphy, John Hoeven, and Gary Peters—as well as Asia-focused experts at US think tanks and several journalists that include CNN’s lead national security reporter, Jim Sciutto.
In the hacking campaign, those individuals were targeted in replies on X (formerly known as Twitter) that included links to websites that would have infected their iOS or Android phones with the Predator spyware. That tactic appears to have been both reckless and unsuccessful: Anyone else who saw the tweets and clicked on the link would have been infected too, and the highly public nature of that infection attempt helped researchers and reporters to analyze the scope and targeting of the campaign. The attempted espionage was timed to US government meetings with Vietnamese officials, and it appears to have been aimed at understanding US intentions in the meeting, particularly related to relations with China.
The media consortium, along with security researchers from Amnesty International and Google’s Threat Analysis Group, were able to show Vietnam’s connection to the Predator hacking campaign through documents they obtained that detail the Vietnamese government’s contract with Intellexa in 2020, and later an extension of the deal to allow the use of the Predator software. The internal documents went so far as to capture the response of Intellexa’s founder, Israeli former military hacker turned entrepreneur Tal Dilian, when the deal was announced: “Wooow!!!!” Vietnam’s government would later target French officials with Predator before this year’s campaign targeting US congressmen.
Hamas Raised Millions in Crypto Ahead of Attacks
Despite efforts by Israel and other nations to cut off funding to Hamas in recent years, the group raised millions of dollars worth of cryptocurrency before the past weekend’s attack that killed more than a thousand Israelis. An analysis by The Wall Street Journal found that Hamas, Palestinian Islamic Jihad, and Hezbollah had collectively raised hundreds of millions in crypto over the past several years, with $41 million going to Hamas specifically. Given that the Journal learned of that funding in part through Israeli seizures of crypto accounts, however, it’s not clear how much of that money was frozen or seized versus how much might have actually been successfully laundered or liquidated by Hamas and other groups.
In response to the weekend’s attacks, the Israeli government and the world’s largest crypto exchange, Binance, both announced that a new round of Hamas crypto accounts had been frozen. Though crypto has helped Hamas and other groups move funds across borders, its traceability on blockchains has presented a challenge for designated terrorist groups. In 2021, for instance, Hamas asked its supporters to stop making donations via cryptocurrency, due to the ease of tracking those transactions and unmasking contributors.
Exxon Used Hacked Documents to Counter State Investigations
Last year, Reuters reporters Chris Bing and Raphael Satter published an investigation into Aviram Azari, an Israeli private investigator who is accused of using mercenary hackers to gather intelligence on the critics of major corporations involved in lawsuits against them.
Now, prosecutors in the Southern District of New York, where Azari has been convicted on criminal charges, have filed a sentencing memo that notes that activists’ communications stolen by Azari’s hackers were later used by Exxon in the company’s attempts to head off investigations and lawsuits by state attorneys general. The memo still doesn’t name Exxon as Azari’s client, but it implicitly suggests a link between the company and Azari: Prosecutors point in their memo to leaks of climate activists’ private emails to media, which were later cited by Exxon in their responses to state attorney generals as evidence of underhanded tactics by activists as they tried to prove that Exxon knew and covered up the role of fossil fuels in climate change. A Massachusetts lawsuit against Exxon that resulted from the state’s investigation is ongoing.
Magecart Cybercrime Crew Skims Cards With New 404 Trick
Internet giant Akamai warned this week that the infamous Magecart hacker crew, long focused on credit card fraud, has developed a clever new technique for spoofing credit card payment fields. The hackers managed to hide their malicious scripts in the 404 “page not found” error pages of ecommerce sites, then trigger those pages to load a spoofed payment field that impersonates a checkout page to steal credit card information. “The idea of manipulating the default 404 error page of a targeted website can offer Magecart actors various creative options for improved hiding and evasion,” warned Akamai researcher Roman Lvovsky. Akamai noted that the technique was used on the website of significant brands in the food and retail industries but declined to name them.
5 notes
·
View notes
Link
TAG became aware of the Heliconia framework when Google received an anonymous submission to the Chrome bug reporting program. The submitter filed three bugs, each with instructions and an archive that contained source code. They used unique names in the bug reports including, “Heliconia Noise,” “Heliconia Soft” and “Files.” TAG analyzed the submissions and found they contained frameworks for deploying exploits in the wild and a script in the source code included clues pointing to the possible developer of the exploitation frameworks, Variston IT.
lmaoooo
#filthy hacker shit#always super amusing for me when they try and trick the *security* team into executing some sketchy payload#good lucky buddy!#(also wow the hn comments on this one are unusually low-tier lol)
7 notes
·
View notes
Text
I feel like people need to start learning that imperialism in the digital age is much different and takes on a different look but is still imperialism, especially with the us wanting basically a monopoly on social media and pretty much being the only country that they think can use commercial spyware
4 notes
·
View notes