#codecreators
Explore tagged Tumblr posts
Text
𝐁𝐫𝐢𝐝𝐠𝐢𝐧𝐠 𝐭𝐡𝐞 𝐆𝐚𝐩, 𝐁𝐨𝐨𝐬𝐭𝐢𝐧𝐠 𝐏𝐞𝐫𝐟𝐨𝐫𝐦𝐚𝐧𝐜𝐞: 𝐂𝐡𝐨𝐨𝐬𝐞 𝐀𝐏𝐈 𝐏𝐫𝐨𝐱𝐲 𝐄𝐱𝐜𝐞𝐥𝐥𝐞𝐧𝐜𝐞❗

Discover how API proxies from VPS PROXIES INC can revolutionize your online operations with seamless connectivity and top-notch security. Elevate your digital endeavors with these powerful tools, ensuring a streamlined and protected online experience. Explore the transformative potential of API proxies for a more efficient online presence.
🔄 𝐖𝐡𝐚𝐭 𝐚𝐫𝐞 𝐀𝐏𝐈 𝐏𝐫𝐨𝐱𝐢𝐞𝐬 ❓
API proxies function as intermediaries, serving as essential bridges that facilitate smooth communication between diverse software applications. Acting as a conduit for data exchange, these proxies are pivotal in optimizing interactions between an application or client and external APIs. In essence, API proxies simplify and secure the flow of requests and responses, ensuring a seamless and efficient exchange of information. By adding an extra layer of functionality and security, these proxies play a critical role in managing and enhancing the overall communication process between applications and external services.
🛠️ 𝐇𝐨𝐰 𝐝𝐨 𝐀𝐏𝐈 𝐏𝐫𝐨𝐱𝐢𝐞𝐬 𝐖𝐨𝐫𝐤 ❓
API proxies work by intercepting and managing the communication between a client application and an external API (Application Programming Interface). Here’s a simplified overview of how API proxies function:
👉 𝑻𝒉𝒆 𝑪𝒍𝒊𝒆𝒏𝒕 𝑼𝒏𝒗𝒆𝒊𝒍𝒔 𝑰𝒕𝒔 𝑹𝒆𝒒𝒖𝒆𝒔𝒕: A client application initiates a request to access data or services from an external API.
👉 𝑰𝒏𝒕𝒆𝒓𝒄𝒆𝒑𝒕𝒊𝒏𝒈 𝒕𝒉𝒆 𝑪𝒍𝒊𝒆𝒏𝒕❜𝒔 𝑷𝒍𝒆𝒂: Before the request reaches the external API, it passes through an API proxy. The proxy intercepts the request, acting as an intermediary.
👉 𝑷𝒓𝒐𝒄𝒆𝒔𝒔𝒊𝒏𝒈 𝒂𝒏𝒅 𝑻𝒓𝒂𝒏𝒔𝒇𝒐𝒓𝒎𝒂𝒕𝒊𝒐𝒏: The API proxy can perform various actions on the request, such as modifying headers, transforming data, or enforcing security measures. This step allows the proxy to optimize the request for the external API.
👉 𝑺𝒆𝒄𝒖𝒓𝒊𝒕𝒚 𝑴𝒆𝒂𝒔𝒖𝒓𝒆𝒔 𝑨𝒑𝒑𝒍𝒊𝒆𝒅: API proxies often incorporate security features like authentication and encryption. Authentication ensures that the client is authorized to access the API, and encryption secures the data during transit.
👉 𝑹𝒐𝒖𝒕𝒊𝒏𝒈 𝒕𝒐 𝑬𝒙𝒕𝒆𝒓𝒏𝒂𝒍 𝑨𝑷𝑰: After processing the request, the API proxy forwards it to the external API. The external API processes the request and generates a response.
👉 𝑹𝒆𝒔𝒑𝒐𝒏𝒔𝒆 𝑰𝒏𝒕𝒆𝒓𝒄𝒆𝒑𝒕𝒆𝒅 𝒃𝒚 𝑨𝑷𝑰 𝑷𝒓𝒐𝒙𝒚: As the response travels back from the external API to the client, it passes through the API proxy again. The proxy can intercept the response for further processing.
👉 𝑨𝒅𝒅𝒊𝒕𝒊𝒐𝒏𝒂𝒍 𝑷𝒓𝒐𝒄𝒆𝒔𝒔𝒊𝒏𝒈 𝒂𝒏𝒅 𝑻𝒓𝒂𝒏𝒔𝒇𝒐𝒓𝒎𝒂𝒕𝒊𝒐𝒏: The API proxy can perform additional actions on the response, such as modifying data or headers. This step allows the proxy to tailor the response to the client’s needs.
𝐊𝐞𝐲 𝐄𝐥𝐞𝐦𝐞𝐧𝐭𝐬 𝐢𝐧 𝐀𝐏𝐈 𝐏𝐫𝐨𝐱𝐲 𝐌𝐚𝐬𝐭𝐞𝐫𝐲
🚥 𝑻𝒓𝒂𝒇𝒇𝒊𝒄 𝑶𝒓𝒄𝒉𝒆𝒔𝒕𝒓𝒂𝒕𝒊𝒐𝒏 API proxies can implement features like rate limiting and caching to optimize the flow of data between the client and the external API.
📊 𝑰𝒏𝒔𝒊𝒈𝒉𝒕𝒇𝒖𝒍 𝑨𝒏𝒂𝒍𝒚𝒕𝒊𝒄𝒔 𝒂𝒏𝒅 𝑴𝒐𝒏𝒊𝒕𝒐𝒓𝒊𝒏𝒈 API proxies often log information about requests and responses, providing valuable insights for monitoring, analytics, and issue resolution.
🔄𝑺𝒆𝒂𝒎𝒍𝒆𝒔𝒔 𝑽𝒆𝒓𝒔𝒊𝒐𝒏 𝑪𝒐𝒏𝒕𝒓𝒐𝒍 API proxies can handle different versions of APIs, ensuring compatibility between clients and external services, even when updates or changes occur.
𝐏𝐫𝐚𝐜𝐭𝐢𝐜𝐚𝐥 𝐒𝐜𝐞𝐧𝐚𝐫𝐢𝐨𝐬: 𝐖𝐡𝐞𝐫𝐞 𝐀𝐏𝐈 𝐏𝐫𝐨𝐱𝐢𝐞𝐬 𝐒𝐡𝐢𝐧𝐞 🌟
🔒 𝑭𝒐𝒓𝒕𝒊𝒇𝒚𝒊𝒏𝒈 𝑫𝒂𝒕𝒂 𝑺𝒆𝒄𝒖𝒓𝒊𝒕𝒚 API proxies are frequently employed to bolster the security of data transmission. By encrypting information, they ensure that sensitive details remain confidential during the exchange.
⚙️ 𝑶𝒑𝒕𝒊𝒎𝒊𝒛𝒊𝒏𝒈 𝑷𝒆𝒓𝒇𝒐𝒓𝒎𝒂𝒏𝒄𝒆 Additionally, API proxies play a vital role in optimizing performance. Through techniques like caching, they reduce response times, making interactions between applications and external services quicker and more efficient.
🚦 𝑻𝒓𝒂𝒇𝒇𝒊𝒄 𝑪𝒐𝒏𝒕𝒓𝒐𝒍 Another notable use case involves traffic management. API proxies regulate the flow of data, employing measures such as rate limiting to prevent overwhelming external services with a barrage of requests.
🔄 𝑪𝑶𝑹𝑺 𝑴𝒂𝒔𝒕𝒆𝒓𝒚 𝒇𝒐𝒓 𝑼𝒏𝒓𝒆𝒔𝒕𝒓𝒊𝒄𝒕𝒆𝒅 𝑫𝒂𝒕𝒂 𝑹𝒆𝒕𝒓𝒊𝒆𝒗𝒂𝒍 In scenarios where applications need to fetch data from different domains, API proxies shine in handling Cross-Origin Resource Sharing. They enable secure data retrieval from multiple sources without running into browser restrictions.
📈 𝑳𝒐𝒈𝒈𝒊𝒏𝒈 𝒂𝒏𝒅 𝑴𝒐𝒏𝒊𝒕𝒐𝒓𝒊𝒏𝒈 Furthermore, API proxies are instrumental in logging and monitoring interactions. This continuous oversight helps identify issues, track performance metrics, and troubleshoot potential challenges seamlessly.
🔄 𝑽𝒆𝒓𝒔𝒊𝒐𝒏 𝑪𝒐𝒏𝒕𝒓𝒐𝒍 Version control is another critical aspect where API proxies prove their worth. They assist in managing different versions of APIs, ensuring smooth transitions and compatibility between evolving applications and services.
⚖️ 𝑳𝒐𝒂𝒅 𝑩𝒂𝒍𝒂𝒏𝒄𝒊𝒏𝒈 For applications dealing with varying levels of traffic, API proxies offer the advantage of load balancing. This means distributing incoming requests evenly among multiple servers, preventing any single server from becoming overloaded.
🚀 𝑨𝒅𝒂𝒑𝒕𝒊𝒏𝒈 𝒕𝒐 𝑬𝒎𝒆𝒓𝒈𝒊𝒏𝒈 𝑻𝒆𝒄𝒉𝒏𝒐𝒍𝒐𝒈𝒊𝒆𝒔 As technology evolves, API proxies remain adaptable. They smoothly transition into supporting emerging technologies, ensuring that applications can seamlessly integrate new functionalities without disruptions.
🤔 𝐂𝐨𝐧𝐬𝐢𝐝𝐞𝐫𝐚𝐭𝐢𝐨𝐧𝐬 𝐰𝐡𝐞𝐧 𝐜𝐡𝐨𝐨𝐬𝐢𝐧𝐠 𝐚𝐧 𝐀𝐏𝐈 𝐏𝐫𝐨𝐱𝐲
When selecting an API proxy, several crucial considerations come into play to ensure optimal performance, security, and compatibility. Let’s explore these key factors:
🔐 𝑺𝒆𝒄𝒖𝒓𝒊𝒕𝒚 𝑴𝒆𝒂𝒔𝒖𝒓𝒆𝒔 : First and foremost, assess the security features offered by the API proxy. Look for encryption, authentication mechanisms, and other security measures to safeguard your data during transit.
⚙️ 𝑷𝒆𝒓𝒇𝒐𝒓𝒎𝒂𝒏𝒄𝒆 𝑶𝒑𝒕𝒊𝒎𝒊𝒛𝒂𝒕𝒊𝒐𝒏 : Consider how the API proxy contributes to performance optimization. Evaluate features such as caching, which can significantly enhance response times and reduce latency.
🚦 𝑻𝒓𝒂𝒇𝒇𝒊𝒄 𝑴𝒂𝒏𝒂𝒈𝒆𝒎𝒆𝒏𝒕 𝑪𝒂𝒑𝒂𝒃𝒊𝒍𝒊𝒕𝒊𝒆𝒔 : Examine the API proxy’s ability to manage traffic effectively. Features like rate limiting and traffic shaping can prevent overload, ensuring consistent and reliable service.
🔄 𝑪𝒓𝒐𝒔𝒔-𝑶𝒓𝒊𝒈𝒊𝒏 𝑹𝒆𝒔𝒐𝒖𝒓𝒄𝒆 𝑺𝒉𝒂𝒓𝒊𝒏𝒈 (𝑪𝑶𝑹𝑺) 𝑺𝒖𝒑𝒑𝒐𝒓𝒕 : If your applications need to interact with resources from different domains, check if the API proxy provides robust support for Cross-Origin Resource Sharing. This ensures seamless data retrieval without encountering browser restrictions.
📊 𝑳𝒐𝒈𝒈𝒊𝒏𝒈 𝒂𝒏𝒅 𝑴𝒐𝒏𝒊𝒕𝒐𝒓𝒊𝒏𝒈 𝑻𝒐𝒐𝒍𝒔 : Assess the logging and monitoring capabilities of the API proxy. Having detailed insights into interactions can aid in issue identification, performance tracking, and overall system health.
🔄 𝑽𝒆𝒓𝒔𝒊𝒐𝒏 𝑪𝒐𝒏𝒕𝒓𝒐𝒍 𝑴𝒆𝒄𝒉𝒂𝒏𝒊𝒔𝒎𝒔 : Evaluate how the API proxy handles version control. Ensure it supports different versions of APIs to facilitate smooth transitions and maintain compatibility as your applications evolve.
🛠️ 𝑬𝒂𝒔𝒆 𝒐𝒇 𝑰𝒏𝒕𝒆𝒈𝒓𝒂𝒕𝒊𝒐𝒏 : Assess how easily the API proxy can be integrated into your existing infrastructure. A user-friendly integration process minimizes disruptions and accelerates the implementation of proxy services.
💵 𝑩𝒖𝒅𝒈𝒆𝒕𝒂𝒓𝒚 𝑨𝒏𝒂𝒍𝒚𝒔𝒊𝒔: Finally, examine the cost and licensing structure of the API proxy. Ensure that it aligns with your budgetary constraints and provides a clear understanding of any additional costs associated with scaling or feature usage.
𝑼𝒏𝒍𝒐𝒄𝒌 𝒕𝒉𝒆 𝑻𝒓𝒖𝒆 𝑷𝒐𝒕𝒆𝒏𝒕𝒊𝒂𝒍 𝒐𝒇 𝒀𝒐𝒖𝒓 𝑶𝒏𝒍𝒊𝒏𝒆 𝑷𝒓𝒆𝒔𝒆𝒏𝒄𝒆 🌐
𝐂𝐨𝐧𝐜𝐥𝐮𝐬𝐢𝐨𝐧:
The integration of an API proxy across all services offered by VPS Proxies Inc. represents a pivotal step towards optimizing performance and security. By consolidating API access through a centralized proxy layer, we enhance data integrity, mitigate potential vulnerabilities, and streamline communication channels. This proactive measure not only ensures a seamless user experience but also reinforces our commitment to delivering reliable and innovative solutions to our valued clients. With the API proxy in place, VPS Proxies Inc. is poised to meet the evolving needs of businesses with efficiency and confidence..
ℂ𝕠𝕟𝕥𝕒𝕔𝕥 𝕦𝕤:-: 👉🏻 Web: www.vpsproxies.com 👉🏻 Telegram: https://t.me/vpsproxiesinc 👉 Gmail: [email protected] 👉🏻 Skype: live:.cid.79b1850cbc237b2a
#InnovationNation#TechTrends#FutureForward#DigitalTransformation#DataDriven#CodeCrafting#APIRevolution#ConnectTheDots#TechInnovation#BytesAndBeyond#SmartTech#CodeCreators#DigitalFrontiers#TechSavvy#BeyondBoundaries#InfinitePossibilities#DataFlow#APIMagic#TechUnleashed#NextGenTech
0 notes
Text
#WebWizardry#CodeCrafting#DigitalDreams#DevDynamos#PixelPerfection#WebWeavers#TechTrends#CodeCreators#DesignDevotion#InnovationOnline#WebWorld#DevelopmentDuo#DigitalFrontiers#CodeCulture#WebWonders#Mississauga#Ontario#Toronto#Canada#Ottawa#Calgary#Montreal#Vancouver#Edmonton
0 notes
Text

Turning ideas into reality, one algorithm at a time. Join us on the journey at Appcrunk Technologies!
💼💻 Join hands with us and explore a world of efficient solutions.
💁 Our Services:
👉Website Development
👉Software Development
👉Digital Marketing
👉Application Development
👉Social Media Marketing
Reach out to us at:
🌐 Website: www.appcrunk.com
📧 Business Mail: [email protected]
📞 Contact Us: 9854300075, 9501878875
#ideastoreality#algorithmmagic#appdevelopment#techjourney#innovationhub#codecrafting#softwareengineering#digitaltransformation#techinnovation#techlife#codecreators#futurebuilders#appcrunkmagic#codecrafters#digitalinnovation#codelife#techsolutions#softwaresolutions#teamwork#userexperience#techcommunity#problemsolvers#digitalfuture#techleaders#appcrunktechnologies
1 note
·
View note
Text
Best App Development Company in Arizona | Master Bazar
Master Bazar is a skilled app development company, partnering closely with you to transform your app concept into reality. Our team of experts handles everything from idea to launch, delivering comprehensive app development services that prioritize user satisfaction. We craft cutting-edge, scalable mobile apps to boost growth, engage customers, and elevate your digital brand presence using the latest tools and tech. When you select us, rest assured your app is in capable hands – we're committed to your satisfaction.
https://masterbazar.com/services/development/app-development
1 note
·
View note
Text
Ballad of Jade Ann Byrne: A Tale of Insight and Defiance
(no title)
Verse 1:In the digital realm where the eGirl thrives,Stands Jade Ann Byrne, with insight alive.With a voice that echoes through cyber halls,She declares her presence, breaking down walls. Chorus:She knows who she is, in pixels and truth,Unfazed by the judgments, eternal youth.In a world of avatars, she stands so grand,Jade Ann Byrne, with her destiny in hand. Verse 2:Raising her hand, not in…

View On WordPress
#2024#AvatarWorlds#BalladOfJadeAnnByrne#California#CaliforniaTech#CodeAndCowgirl#CodeConnoisseur#CodeCreativity#CyberCowgirl#CyberQueen#DefiantSpirit#DigitalDaring#DigitalDreamer#DigitalDynamo#DigitalPaladin#DigitalRealmSaga#egirl4rent#eGirl4Rent.com#eGirlJourney#eGirlLife#EmpathyEmpire#EmpathyEngineer#EmpoweredIdentity#EmpowermentEpic#FreedomInPixels#FutureForward#HoneyPot#InnovationInstigator#Insightful#Jade Ann Byrne
1 note
·
View note
Text

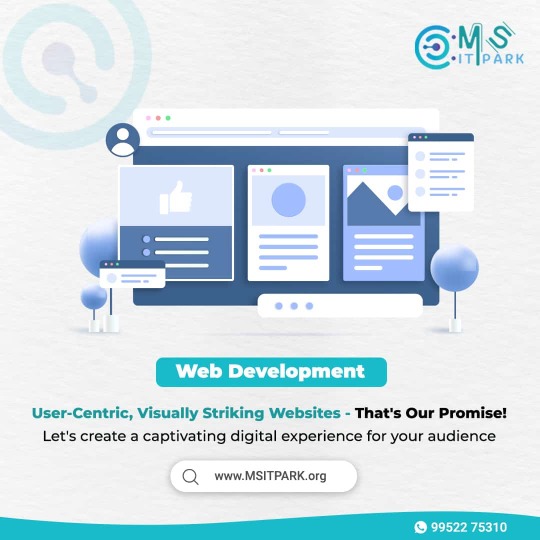
💡 MS IT Park - Your Vision, Our Code! 🚀 Elevate your brand with websites that not only look stunning but also perform flawlessly. Let's craft a digital masterpiece for your business! 🌟🌐
🔗 E-Commerce Website Development: https://msitpark.org/ecommerce-website-development-company-in-coimbatore
🔗 Mobile App Development: https://msitpark.org/mobile-app-development-company-in-coimbatore
🔗 Web Design Services : https://msitpark.org/web-design-company-in-coimbatore
🔗 Laravel Development: https://msitpark.org/laravel-development-company-in-india 🔗 Software Development: https://msitpark.org/software-development-company-in-coimbatore
👉 Visit our website: https://msitpark.org/
#MSITParkWebsites#WebDevelopmentCoimbatore#DigitalJourney#WebExcellence#MSITParkDigitalMagic#DigitalMasterpiece#InnovationHub#MSITParkInterface#WebSolutions#MSITParkSuccess#DigitalExperiences#MSITParkMission#WebBrilliance#MSITParkPartnership#OnlinePresence#MSITParkSuccessStory#CodeCreativity#MSITParkDigital#FutureWebDevelopment#MSITParkRevolution
0 notes
Text
Web Development Course For Kids | GoGlobalWays

GoGlobalWays offers an exceptional web development course for kids, providing a dynamic and engaging learning experience. Tailored for young learners, this program stands out for its interactive approach and age-appropriate content. The curriculum is designed to instill fundamental coding concepts in a fun and accessible manner, ensuring that kids grasp the basics of web development with ease. The course introduces children to HTML, CSS, and JavaScript, the building blocks of web development, through hands-on projects and creative exercises. GoGlobalWays emphasizes a practical learning approach, enabling kids to create their own simple websites and applications, fostering a sense of accomplishment. With experienced and supportive instructors, the program encourages collaborative learning, allowing kids to share ideas and solve problems together. The flexible nature of the course accommodates various learning styles, ensuring that each child can progress at their own pace. GoGlobalWays aims not only to teach coding skills but also to inspire a passion for technology, laying a solid foundation for future success in the rapidly evolving digital landscape.
#KidsCoding#WebDevelopmentForKids#CodingFun#CodeCreativity#YoungDevelopers#DigitalLearning#GoGlobalWays
0 notes
Text
Techaircraft
Embark on a journey through the digital realm of web development! 🌐💻 From conceptualization to creation, we weave intricate designs with flawless functionality to elevate your online presence. Let's sculpt user experiences that are intuitive, engaging, and impactful. 🚀 Dive into the code, where innovation meets imagination, and watch your vision come to life pixel by pixel. . 𝐖𝐞𝐛𝐬𝐢𝐭𝐞 - www.techaircraft.com
𝐓𝐞𝐜𝐡𝐚𝐢𝐫𝐜𝐫𝐚𝐟𝐭 𝐬𝐮𝐩𝐩𝐨𝐫𝐭 𝐝𝐞𝐭𝐚𝐢𝐥𝐬:
𝐌𝐨𝐛𝐢𝐥𝐞 𝐍𝐮𝐦𝐛𝐞𝐫 - 8686069898
#WebDevelopment #DigitalInnovation #CodeCreativity #TechRevolution #DesignInspiration #DeveloperLife#WebsiteDesign#CodingJourney#DigitalTransformation#WebDesigners#CreateWithCode#InnovationHub

2 notes
·
View notes
Text
"Building dreams, one line of code at a time. 💻✨ #CodeCreators #InnovateInspireBuild"
Development #TechTrends #SoftwareSolutions #DigitalTransformation #CodingLife #TechInnovation #WebDevelopment #AppDevelopment #SoftwareEngineering #TechSavvy #DeveloperLife #TechCommunity
2 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] T-SQL insiders help you tackle your toughest queries and query-tuning problems Squeeze maximum performance and efficiency from every T-SQL query you write or tune. Four leading experts take an in-depth look at T-SQL’s internal architecture and offer advanced practical techniques for optimizing response time and resource usage. Emphasizing a correct understanding of the language and its foundations, the authors present unique solutions they have spent years developing and refining. All code and techniques are fully updated to reflect new T-SQL enhancements in Microsoft SQL Server 2014 and SQL Server 2012. Write faster, more efficient T-SQL code: Move from procedural programming to the language of sets and logicMaster an efficient top-down tuning methodologyAssess algorithmic complexity to predict performanceCompare data aggregation techniques, including new grouping setsEfficiently perform data-analysis calculationsMake the most of T-SQL’s optimized bulk import toolsAvoid date/time pitfalls that lead to buggy, poorly performing codeCreate optimized BI statistical queries without additional softwareUse programmable objects to accelerate queriesUnlock major performance improvements with In-Memory OLTPMaster useful and elegant approaches to manipulating graphs About This Book For experienced T-SQL practitionersIncludes coverage updated from Inside Microsoft SQL Server 2008 T-SQL Querying and Inside Microsoft SQL Server 2008 T-SQL ProgrammingValuable to developers, DBAs, BI professionals, and data scientistsCovers many MCSE 70-464 and MCSA/MCSE 70-461 exam topics ASIN : B00TPRWVHY Publisher : Microsoft Press; 1st edition (17 February 2015) Language : English File size : 63114 KB Simultaneous device usage : Up to 5 simultaneous devices, per publisher limits Text-to-Speech : Enabled Screen Reader : Supported Enhanced typesetting : Enabled X-Ray : Not Enabled Word Wise : Not Enabled Print length : 865 pages [ad_2]
0 notes
Link
Introducing Mastering No-CodeCreate Professional Quality the ultimate guide to unlocking your creativity and building stunning websites and applications without any coding knowledge. Whether you're a beginner or an experienced professional this comprehensive course will equip you with the skills and knowledge to create professional-quality projects using popular no-code platforms. With Mastering No-Code you'll learn the ins and outs of no-code development from understanding the fundamentals to mastering advanced techniques. This course covers everything you need to know including designing user-friendly interfaces integrating powerful functionalities and optimizing your projects for maximum performance. What sets Mastering No-Code apart is its hands-on approach. Through practical exercises and real-world examples you'll gain valuable experience and confidence in building complex projects. You'll also have access to a supportive community of fellow learners and expert instructors ensuring you never feel stuck or alone on your no-code journey. Whether you're a freelancer looking to expand your skillset a business owner wanting to create a professional website or simply someone passionate about technology and innovation Mastering No-Code is the perfect solution for you. Start creating professional-quality websites and applications today without the need for any coding expertise. Unlock your creativity and join the no-code revolution with Mastering No-CodeCreate Professional Quality. Explore our vast collection of Zoho Creator posts to uncover a world of business-enhancing apps. https://www.creatorscripts.com/blogs/zoho-creator/
0 notes
Text
𝐁𝐫𝐢𝐝𝐠𝐢𝐧𝐠 𝐭𝐡𝐞 𝐆𝐚𝐩, 𝐁𝐨𝐨𝐬𝐭𝐢𝐧𝐠 𝐏𝐞𝐫𝐟𝐨𝐫𝐦𝐚𝐧𝐜𝐞: 𝐂𝐡𝐨𝐨𝐬𝐞 𝐀𝐏𝐈 𝐏𝐫𝐨𝐱𝐲 𝐄𝐱𝐜𝐞𝐥𝐥𝐞𝐧𝐜𝐞❗

Discover how API proxies from VPS PROXIES INC can revolutionize your online operations with seamless connectivity and top-notch security. Elevate your digital endeavors with these powerful tools, ensuring a streamlined and protected online experience. Explore the transformative potential of API proxies for a more efficient online presence.
🔄 𝐖𝐡𝐚𝐭 𝐚𝐫𝐞 𝐀𝐏𝐈 𝐏𝐫𝐨𝐱𝐢𝐞𝐬 ❓
API proxies function as intermediaries, serving as essential bridges that facilitate smooth communication between diverse software applications. Acting as a conduit for data exchange, these proxies are pivotal in optimizing interactions between an application or client and external APIs. In essence, API proxies simplify and secure the flow of requests and responses, ensuring a seamless and efficient exchange of information. By adding an extra layer of functionality and security, these proxies play a critical role in managing and enhancing the overall communication process between applications and external services.
🛠️ 𝐇𝐨𝐰 𝐝𝐨 𝐀𝐏𝐈 𝐏𝐫𝐨𝐱𝐢𝐞𝐬 𝐖𝐨𝐫𝐤 ❓
API proxies work by intercepting and managing the communication between a client application and an external API (Application Programming Interface). Here’s a simplified overview of how API proxies function:
👉 𝑻𝒉𝒆 𝑪𝒍𝒊𝒆𝒏𝒕 𝑼𝒏𝒗𝒆𝒊𝒍𝒔 𝑰𝒕𝒔 𝑹𝒆𝒒𝒖𝒆𝒔𝒕: A client application initiates a request to access data or services from an external API.
👉 𝑰𝒏𝒕𝒆𝒓𝒄𝒆𝒑𝒕𝒊𝒏𝒈 𝒕𝒉𝒆 𝑪𝒍𝒊𝒆𝒏𝒕❜𝒔 𝑷𝒍𝒆𝒂: Before the request reaches the external API, it passes through an API proxy. The proxy intercepts the request, acting as an intermediary.
👉 𝑷𝒓𝒐𝒄𝒆𝒔𝒔𝒊𝒏𝒈 𝒂𝒏𝒅 𝑻𝒓𝒂𝒏𝒔𝒇𝒐𝒓𝒎𝒂𝒕𝒊𝒐𝒏: The API proxy can perform various actions on the request, such as modifying headers, transforming data, or enforcing security measures. This step allows the proxy to optimize the request for the external API.
👉 𝑺𝒆𝒄𝒖𝒓𝒊𝒕𝒚 𝑴𝒆𝒂𝒔𝒖𝒓𝒆𝒔 𝑨𝒑𝒑𝒍𝒊𝒆𝒅: API proxies often incorporate security features like authentication and encryption. Authentication ensures that the client is authorized to access the API, and encryption secures the data during transit.
👉 𝑹𝒐𝒖𝒕𝒊𝒏𝒈 𝒕𝒐 𝑬𝒙𝒕𝒆𝒓𝒏𝒂𝒍 𝑨𝑷𝑰: After processing the request, the API proxy forwards it to the external API. The external API processes the request and generates a response.
👉 𝑹𝒆𝒔𝒑𝒐𝒏𝒔𝒆 𝑰𝒏𝒕𝒆𝒓𝒄𝒆𝒑𝒕𝒆𝒅 𝒃𝒚 𝑨𝑷𝑰 𝑷𝒓𝒐𝒙𝒚: As the response travels back from the external API to the client, it passes through the API proxy again. The proxy can intercept the response for further processing.
👉 𝑨𝒅𝒅𝒊𝒕𝒊𝒐𝒏𝒂𝒍 𝑷𝒓𝒐𝒄𝒆𝒔𝒔𝒊𝒏𝒈 𝒂𝒏𝒅 𝑻𝒓𝒂𝒏𝒔𝒇𝒐𝒓𝒎𝒂𝒕𝒊𝒐𝒏: The API proxy can perform additional actions on the response, such as modifying data or headers. This step allows the proxy to tailor the response to the client’s needs.
𝐊𝐞𝐲 𝐄𝐥𝐞𝐦𝐞𝐧𝐭𝐬 𝐢𝐧 𝐀𝐏𝐈 𝐏𝐫𝐨𝐱𝐲 𝐌𝐚𝐬𝐭𝐞𝐫𝐲
🚥 𝑻𝒓𝒂𝒇𝒇𝒊𝒄 𝑶𝒓𝒄𝒉𝒆𝒔𝒕𝒓𝒂𝒕𝒊𝒐𝒏 API proxies can implement features like rate limiting and caching to optimize the flow of data between the client and the external API.
📊 𝑰𝒏𝒔𝒊𝒈𝒉𝒕𝒇𝒖𝒍 𝑨𝒏𝒂𝒍𝒚𝒕𝒊𝒄𝒔 𝒂𝒏𝒅 𝑴𝒐𝒏𝒊𝒕𝒐𝒓𝒊𝒏𝒈 API proxies often log information about requests and responses, providing valuable insights for monitoring, analytics, and issue resolution.
🔄𝑺𝒆𝒂𝒎𝒍𝒆𝒔𝒔 𝑽𝒆𝒓𝒔𝒊𝒐𝒏 𝑪𝒐𝒏𝒕𝒓𝒐𝒍 API proxies can handle different versions of APIs, ensuring compatibility between clients and external services, even when updates or changes occur.
𝐏𝐫𝐚𝐜𝐭𝐢𝐜𝐚𝐥 𝐒𝐜𝐞𝐧𝐚𝐫𝐢𝐨𝐬: 𝐖𝐡𝐞𝐫𝐞 𝐀𝐏𝐈 𝐏𝐫𝐨𝐱𝐢𝐞𝐬 𝐒𝐡𝐢𝐧𝐞 🌟
🔒 𝑭𝒐𝒓𝒕𝒊𝒇𝒚𝒊𝒏𝒈 𝑫𝒂𝒕𝒂 𝑺𝒆𝒄𝒖𝒓𝒊𝒕𝒚 API proxies are frequently employed to bolster the security of data transmission. By encrypting information, they ensure that sensitive details remain confidential during the exchange.
⚙️ 𝑶𝒑𝒕𝒊𝒎𝒊𝒛𝒊𝒏𝒈 𝑷𝒆𝒓𝒇𝒐𝒓𝒎𝒂𝒏𝒄𝒆 Additionally, API proxies play a vital role in optimizing performance. Through techniques like caching, they reduce response times, making interactions between applications and external services quicker and more efficient.
🚦 𝑻𝒓𝒂𝒇𝒇𝒊𝒄 𝑪𝒐𝒏𝒕𝒓𝒐𝒍 Another notable use case involves traffic management. API proxies regulate the flow of data, employing measures such as rate limiting to prevent overwhelming external services with a barrage of requests.
🔄 𝑪𝑶𝑹𝑺 𝑴𝒂𝒔𝒕𝒆𝒓𝒚 𝒇𝒐𝒓 𝑼𝒏𝒓𝒆𝒔𝒕𝒓𝒊𝒄𝒕𝒆𝒅 𝑫𝒂𝒕𝒂 𝑹𝒆𝒕𝒓𝒊𝒆𝒗𝒂𝒍 In scenarios where applications need to fetch data from different domains, API proxies shine in handling Cross-Origin Resource Sharing. They enable secure data retrieval from multiple sources without running into browser restrictions.
📈 𝑳𝒐𝒈𝒈𝒊𝒏𝒈 𝒂𝒏𝒅 𝑴𝒐𝒏𝒊𝒕𝒐𝒓𝒊𝒏𝒈 Furthermore, API proxies are instrumental in logging and monitoring interactions. This continuous oversight helps identify issues, track performance metrics, and troubleshoot potential challenges seamlessly.
🔄 𝑽𝒆𝒓𝒔𝒊𝒐𝒏 𝑪𝒐𝒏𝒕𝒓𝒐𝒍 Version control is another critical aspect where API proxies prove their worth. They assist in managing different versions of APIs, ensuring smooth transitions and compatibility between evolving applications and services.
⚖️ 𝑳𝒐𝒂𝒅 𝑩𝒂𝒍𝒂𝒏𝒄𝒊𝒏𝒈 For applications dealing with varying levels of traffic, API proxies offer the advantage of load balancing. This means distributing incoming requests evenly among multiple servers, preventing any single server from becoming overloaded.
🚀 𝑨𝒅𝒂𝒑𝒕𝒊𝒏𝒈 𝒕𝒐 𝑬𝒎𝒆𝒓𝒈𝒊𝒏𝒈 𝑻𝒆𝒄𝒉𝒏𝒐𝒍𝒐𝒈𝒊𝒆𝒔 As technology evolves, API proxies remain adaptable. They smoothly transition into supporting emerging technologies, ensuring that applications can seamlessly integrate new functionalities without disruptions.
🤔 𝐂𝐨𝐧𝐬𝐢𝐝𝐞𝐫𝐚𝐭𝐢𝐨𝐧𝐬 𝐰𝐡𝐞𝐧 𝐜𝐡𝐨𝐨𝐬𝐢𝐧𝐠 𝐚𝐧 𝐀𝐏𝐈 𝐏𝐫𝐨𝐱𝐲
When selecting an API proxy, several crucial considerations come into play to ensure optimal performance, security, and compatibility. Let’s explore these key factors:
🔐 𝑺𝒆𝒄𝒖𝒓𝒊𝒕𝒚 𝑴𝒆𝒂𝒔𝒖𝒓𝒆𝒔 : First and foremost, assess the security features offered by the API proxy. Look for encryption, authentication mechanisms, and other security measures to safeguard your data during transit.
⚙️ 𝑷𝒆𝒓𝒇𝒐𝒓𝒎𝒂𝒏𝒄𝒆 𝑶𝒑𝒕𝒊𝒎𝒊𝒛𝒂𝒕𝒊𝒐𝒏 : Consider how the API proxy contributes to performance optimization. Evaluate features such as caching, which can significantly enhance response times and reduce latency.
🚦 𝑻𝒓𝒂𝒇𝒇𝒊𝒄 𝑴𝒂𝒏𝒂𝒈𝒆𝒎𝒆𝒏𝒕 𝑪𝒂𝒑𝒂𝒃𝒊𝒍𝒊𝒕𝒊𝒆𝒔 : Examine the API proxy’s ability to manage traffic effectively. Features like rate limiting and traffic shaping can prevent overload, ensuring consistent and reliable service.
🔄 𝑪𝒓𝒐𝒔𝒔-𝑶𝒓𝒊𝒈𝒊𝒏 𝑹𝒆𝒔𝒐𝒖𝒓𝒄𝒆 𝑺𝒉𝒂𝒓𝒊𝒏𝒈 (𝑪𝑶𝑹𝑺) 𝑺𝒖𝒑𝒑𝒐𝒓𝒕 : If your applications need to interact with resources from different domains, check if the API proxy provides robust support for Cross-Origin Resource Sharing. This ensures seamless data retrieval without encountering browser restrictions.
📊 𝑳𝒐𝒈𝒈𝒊𝒏𝒈 𝒂𝒏𝒅 𝑴𝒐𝒏𝒊𝒕𝒐𝒓𝒊𝒏𝒈 𝑻𝒐𝒐𝒍𝒔 : Assess the logging and monitoring capabilities of the API proxy. Having detailed insights into interactions can aid in issue identification, performance tracking, and overall system health.
🔄 𝑽𝒆𝒓𝒔𝒊𝒐𝒏 𝑪𝒐𝒏𝒕𝒓𝒐𝒍 𝑴𝒆𝒄𝒉𝒂𝒏𝒊𝒔𝒎𝒔 : Evaluate how the API proxy handles version control. Ensure it supports different versions of APIs to facilitate smooth transitions and maintain compatibility as your applications evolve.
🛠️ 𝑬𝒂𝒔𝒆 𝒐𝒇 𝑰𝒏𝒕𝒆𝒈𝒓𝒂𝒕𝒊𝒐𝒏 : Assess how easily the API proxy can be integrated into your existing infrastructure. A user-friendly integration process minimizes disruptions and accelerates the implementation of proxy services.
💵 𝑩𝒖𝒅𝒈𝒆𝒕𝒂𝒓𝒚 𝑨𝒏𝒂𝒍𝒚𝒔𝒊𝒔: Finally, examine the cost and licensing structure of the API proxy. Ensure that it aligns with your budgetary constraints and provides a clear understanding of any additional costs associated with scaling or feature usage.
𝑼𝒏𝒍𝒐𝒄𝒌 𝒕𝒉𝒆 𝑻𝒓𝒖𝒆 𝑷𝒐𝒕𝒆𝒏𝒕𝒊𝒂𝒍 𝒐𝒇 𝒀𝒐𝒖𝒓 𝑶𝒏𝒍𝒊𝒏𝒆 𝑷𝒓𝒆𝒔𝒆𝒏𝒄𝒆 🌐
𝐂𝐨𝐧𝐜𝐥𝐮𝐬𝐢𝐨𝐧:
The integration of an API proxy across all services offered by VPS Proxies Inc. represents a pivotal step towards optimizing performance and security. By consolidating API access through a centralized proxy layer, we enhance data integrity, mitigate potential vulnerabilities, and streamline communication channels. This proactive measure not only ensures a seamless user experience but also reinforces our commitment to delivering reliable and innovative solutions to our valued clients. With the API proxy in place, VPS Proxies Inc. is poised to meet the evolving needs of businesses with efficiency and confidence..
ℂ𝕠𝕟𝕥𝕒𝕔𝕥 𝕦𝕤:-: 👉🏻 Web: www.vpsproxies.com 👉🏻 Telegram: https://t.me/vpsproxiesinc 👉 Gmail: [email protected] 👉🏻 Skype: live:.cid.79b1850cbc237b2a
#InnovationNation#TechTrends#FutureForward#DigitalTransformation#DataDriven#CodeCrafting#APIRevolution#ConnectTheDots#TechInnovation#BytesAndBeyond#SmartTech#CodeCreators#DigitalFrontiers#TechSavvy#BeyondBoundaries#InfinitePossibilities#DataFlow#APIMagic#TechUnleashed#NextGenTech
0 notes
Text
"Code and Creativity Unite: Navigating Generative AI Development! 💻🎨"

Embark on a thrilling journey into the realm of Generative AI Development, where lines of code converge with boundless creativity! 🌐✨ Unleash the power of algorithms to breathe life into your imaginative visions.
In the world of Generative AI development, every line of code is a brushstroke on the canvas of innovation. 🎨🧠 Begin by crafting the architecture that will birth your digital co-creator, setting the stage for a symphony of possibilities.
Data becomes the heartbeat of your creation—nourishing the algorithm's learning. From images to text, fuel the AI's understanding, allowing it to evolve and refine its skills with each iteration. 📊🔄
Fine-tune parameters with precision, sculpting the behavior of your AI like a master artisan. 🛠️🎭 As the development process unfolds, witness the emergence of a digital collaborator, ready to translate your ideas into tangible digital brilliance.
Generative AI Development is a dance between logic and imagination. Join the rhythm, and let your code become a conduit for innovation, pushing the boundaries of what's possible. 🚀💡 #GenerativeAI #CodeCreativity #DigitalInnovation
#Generative AI#Train a Generative AI model#Custom Generative AI tool#No-code Generative AI tool#Generative AI Development#Generative AI Developer#Train a GPT model#Custom GPT tool#No-code GPT tool#GPT Development#GPT Developer
0 notes
Text
Setting up a local PostgreSQL database for a Spring Boot JPA (Java Persistence API) application involves several steps. Below, I'll guide you through the process:
1. Install PostgreSQL:
Download and install PostgreSQL from the official website: PostgreSQL Downloads.
During the installation, remember the username and password you set for the PostgreSQL superuser (usually 'postgres').
2. Create a Database:
Open pgAdmin or any other PostgreSQL client you prefer.
Log in using the PostgreSQL superuser credentials.
Create a new database. You can do this through the UI or by running SQL command:sqlCopy codeCREATE DATABASE yourdatabasename;
3. Add PostgreSQL Dependency:
Open your Spring Boot project in your favorite IDE.
Add PostgreSQL JDBC driver to your pom.xml if you're using Maven, or build.gradle if you're using Gradle. For Maven, add this dependency:xmlCopy code<dependency> <groupId>org.postgresql</groupId> <artifactId>postgresql</artifactId> <version>42.2.24</version> <!-- Use the latest version --> </dependency>
4. Configure application.properties:
In your application.properties or application.yml file, configure the PostgreSQL database connection details:propertiesCopy codespring.datasource.url=jdbc:postgresql://localhost:5432/yourdatabasename spring.datasource.username=postgres spring.datasource.password=yourpassword spring.jpa.properties.hibernate.dialect=org.hibernate.dialect.PostgreSQLDialect spring.jpa.hibernate.ddl-auto=update
5. Create Entity Class:
Create your JPA entity class representing the database table. Annotate it with @Entity, and define the fields and relationships.
For example:javaCopy code@Entity public class YourEntity { @Id @GeneratedValue(strategy = GenerationType.IDENTITY) private Long id; private String name; // other fields, getters, setters }
6. Create Repository Interface:
Create a repository interface that extends JpaRepository for your entity. Spring Data JPA will automatically generate the necessary CRUD methods.
For example:javaCopy codepublic interface YourEntityRepository extends JpaRepository<YourEntity, Long> { // custom query methods if needed }
7. Use the Repository in Your Service:
Inject the repository interface into your service class and use it to perform database operations.
8. Run Your Spring Boot Application:
Run your Spring Boot application. Spring Boot will automatically create the necessary tables based on your entity classes and establish a connection to your PostgreSQL database.
That's it! Your Spring Boot JPA application is now connected to a local PostgreSQL database. Remember to handle exceptions, close connections, and follow best practices for security, especially when dealing with sensitive data and database connections
Call us on +91-84484 54549
Mail us on [email protected]
Website: Anubhav Online Trainings | UI5, Fiori, S/4HANA Trainings
youtube
0 notes
Text







#MSITParkWebsites#WebDevelopmentCoimbatore#DigitalJourney#WebExcellence#MSITParkDigitalMagic#DigitalMasterpiece#InnovationHub#MSITParkInterface#WebSolutions#MSITParkSuccess#DigitalExperiences#MSITParkMission#WebBrilliance#MSITParkPartnership#OnlinePresence#MSITParkSuccessStory#CodeCreativity#MSITParkDigital#FutureWebDevelopment#MSITParkRevolution
0 notes