#block management software
Explore tagged Tumblr posts
Text
Streamline Success with Cutting-Edge Property Management Tools
Managing commercial properties effectively requires more than just experience; it demands commercial property management software designed to handle complex operations seamlessly. Trace Solutions delivers enterprise-class tools tailored for success in the dynamic property management sector.

Why Choose Trace Solutions?
1. Optimized Service Charge Accounting
Simplify service charge accounting with intuitive features that ensure transparency and accuracy. Trace Solutions' software automates calculations, reduces errors, and enhances tenant satisfaction.
2. Tailored for Enterprises
Trusted by some of the UK’s most successful property management organizations, Trace Solutions’ platform is built to handle the challenges of large-scale operations. From asset tracking to lease management, it’s all in one place.
3. Comprehensive Reporting
Make informed decisions with detailed, real-time reporting. Whether tracking revenue, monitoring maintenance costs, or forecasting future growth, Trace Solutions equips you with actionable insights.
4. Cloud-Based Flexibility
Access your data anytime, anywhere. The cloud-based system ensures your operations are always up-to-date and secure, providing unparalleled accessibility for property managers.
Key Features of Trace Solutions
Customizable Dashboards Personalize your workspace to display the metrics that matter most.
Automated Alerts Stay ahead of deadlines with automated reminders for leases, payments, and compliance tasks.
Scalable Architecture Grow without limitations. The software adapts to your portfolio size and operational needs.

Benefits You Can’t Overlook
Increased Productivity
Automation reduces manual tasks, allowing your team to focus on strategic goals rather than administrative burdens.
Enhanced Accuracy
Eliminate errors in service charge accounting and lease management with state-of-the-art tools designed for precision.
Superior Customer Satisfaction
Streamlined processes lead to faster responses and better tenant relationships.
Testimonials from Industry Leaders
"Trace Solutions transformed our operations. The service charge accounting module alone saved us countless hours and improved transparency with tenants." — John D., Property Manager
"We’ve managed to grow our portfolio by 40% without increasing our team size, thanks to Trace Solutions’ scalable software." — Sarah L., Operations Director

Take Your Property Management to the Next Level
With its advanced features, user-friendly interface, and enterprise-level capabilities, Trace Solutions redefines what commercial property management software can do. From simplifying service charge accounting to enhancing operational efficiency, it's a solution tailored for success.
Experience the difference today! Visit Trace Solutions to learn more about how their software can revolutionize your property management processes.
With Trace Solutions, managing your property portfolio has never been easier or more effective. Don’t wait—explore the possibilities now!
#block management software#commercial property management software#property management and accounting software#property management software
0 notes
Text
Efficient Block Management & Commercial Property Software

Managing commercial properties can be complex, especially when dealing with multiple tenants, service charges, and the need for seamless accounting. To streamline these tasks, advanced software solutions like block management software and commercial property management software are essential for property managers in the UK.
What is Block Management Software?

Block management software is designed to help property managers efficiently oversee residential and commercial properties. It simplifies the administration of service charges, maintenance requests, tenant communications, and financial reporting. The software ensures that property managers can keep track of all aspects of property management from a centralized platform, minimizing manual work and reducing errors.
Benefits of Commercial Property Management Software

Commercial property management software is tailored to handle the unique demands of managing commercial spaces. Features like automated billing, service charge accounting, and financial management tools provide significant time savings. The software allows property managers to monitor leases, track payments, and manage maintenance requests, all while improving communication with tenants.
One of the key benefits of using commercial property management software is its ability to provide detailed reports on property performance. These insights enable managers to make informed decisions, optimize operations, and enhance tenant satisfaction. Additionally, the software supports compliance with legal and financial regulations, reducing the risk of costly errors.
Why Choose Trace Solutions for Your Property Management Needs?

For UK property management organizations, Trace Solutions offers enterprise-class software solutions that are trusted by many leading property management companies. The software is designed to support both block management and commercial property management needs, with features like service charge accounting, financial reporting, and easy tenant management.
With Trace Solutions, property managers can improve operational efficiency, ensure financial accuracy, and provide better services to tenants. Whether you're managing a single commercial property or an entire block, Trace Solutions has the tools to streamline your processes.
Ready to transform your property management? Visit Trace Solutions today and discover how our software can help your business succeed.
#block management software#commercial property management software#property management and accounting software#property management software
0 notes
Text
Effective Block Management Software for Property Managers

In today’s fast-paced real estate environment, efficient management of commercial properties is paramount. Utilizing block management software can significantly enhance operational efficiency and streamline property management processes. This software is designed to cater to the needs of property managers and organizations managing multiple properties, ensuring accurate accounting and reporting.
Streamlined Operations
Block management software is vital for ensuring smooth day-to-day operations. It enables property managers to automate routine tasks, such as rent collection, service charge accounting, and tenant communications. By centralizing these functions, property managers can focus on more strategic aspects of their business, such as improving tenant satisfaction and maximizing property value.
Comprehensive Financial Management
One of the standout features of modern block management software is its robust financial management capabilities. This includes service charge accounting, budget tracking, and financial reporting. Users can easily generate financial statements and manage invoices, reducing the time spent on manual calculations and paperwork. With clear visibility into financial health, property managers can make informed decisions that benefit their organizations and stakeholders.
Enhanced Communication
Effective communication is crucial in property management. Block management software facilitates seamless interaction between property managers, tenants, and service providers. Features such as tenant portals allow for easy access to important documents, maintenance requests, and payment histories. This transparency fosters trust and satisfaction among tenants, ultimately leading to higher retention rates.
Customizable Solutions

Every property management organization has unique needs, and block management software offers customizable solutions to meet these demands. Users can tailor the software to fit their specific workflows, whether managing residential blocks, commercial properties, or mixed-use developments. This flexibility allows organizations to adapt the software as they grow and evolve.
Conclusion
Investing in quality block management software is essential for property management organizations aiming to improve efficiency and enhance tenant experiences. With features designed to streamline operations, manage finances, and facilitate communication, property managers can unlock new levels of success. Whether you manage a single property or an extensive portfolio, adopting a comprehensive block management solution can transform your approach to property management.
0 notes
Text
Oddly emotional over a game of Tetris that was completely fake
#By this I mean. I played an actual round of Tetris with the express goal of failing as badly as possible.#Not a single line cleared#..but then took a screenshot and recreated it in a pixel software and thought.#I did this as badly as possible. I did a TERRIBLE job#But it's.. still fixable. It's still fixable.#And so I played it through#manually#in a pixel program.#And what seemed insurmountable in the beginning was suddenly just a few bricks on the last 3 rows#And I even managed to get it down to a point where I could have theoretically had not a single block left on screen#Sure. It was staged#It would never have gone that perfectly in a legitimate run#And by all means this is absolutely ridiculous to be caught up on#But it felt oddly reassuring?#I don't blinding know. It's too late for this stuff#ursa talks
3 notes
·
View notes
Text
#builder#construction management#construction toys blocks toy#construction tools#construction time again#construction software#construction technology#construction site#construction services#construction materials
2 notes
·
View notes
Text
Last call for homebrewing your 3DS!! I used this guide, which adapts to what your current software version is + your region (the method differs based on these things). It's very easy, all you need is 30 minutes to an hour of free time, a basic understanding of how file explorers work, an internet connection, and an SD card reader if your computer doesn't have an SD slot.
After today, it may become harder to homebrew your 3DS. It will probably not be impossible to do so after the eshop closes, but methods will likely change and there is no guarantee there will be another way available anytime soon.
#however hard you think it may be. i promise it is not as hard as you're fearing#i homebrewed mine and i did encounter a few problems but this guide also has a very in depth troubleshooting section#and all of my problems had detailed solutions that worked immediately#please be aware you should try to have at least 2gb worth of space on your SD card before doing this#you can delete game data and keep save data so you can redownload the games later if you need more space#also note that if you use the software manager tool on the 3DS itself. 128kb = 1 block#yes for some reason the 3ds uses a weirdly arbitrary measure of memory as a holdover from the gamecube. no idk why#if you did it. congrats! you now have the ability to easily put any game ever released onto your 3DS for free!#also you get the ability to use/make custom themes and such which is neat#as well as the ability to screenshot and have save states just like you would when playing a ROMhack on your computer
2 notes
·
View notes
Text
#sutta stories#time#time management software#time blocking#abcdemethod#paretoprinciple#promodo technique#pomodoro technique#pomodoro taachnique
0 notes
Text
//it was a terrible idea to put the new hires on weekends. i'm going to be spending HOURS fixing the mistakes they make, & it's all shit i've shown them how to do like a dozen times
#ooc; kogi rambles#//& it's not like i don't pick up the phone when i'm called#//they just never ask for help bc they're complacent in their stupidity#//i've been screamed at 6 times tn bc my colleague made a HUGE mistake on the software we use#//like if we don't have rooms available it blocks them out but u have the option to override it#//i've literally never needed to override anything but she overrode every single one#//so not only am i being screamed at by clientele i'm also going to be yelled at by management for shit that isn't my fault#//since we have to pay to relocate ppl#//i'm genuinely going to commit a murder
0 notes
Text
I do think that the rise of fascism is directly tied to the decline of communal values.
So on the one hand, you have capitalism, which relentlessly tells you that everything is a competition, your value as a person can only come at someone else's expense, some people are just intrinsically better than others, and your position on this hierarchy is determined by what's in your bank account. On the other hand, individualist liberalism can only answer this with a sort of weak-tea "self-esteem" discourse, which at best amounts to "try your best! Do what you love! It doesn't matter!" and at worst amounts to shouting "Everyone's a winner!", a position that even children automatically view with cynicism.
Never is there any discussion that maybe value shouldn't be intrinsic to the self. Maybe your value is in how much you make life better for other people. Like, do you make a worthy and necessary contribution to society that helps other people? That adds to the net happiness of the world? Then congratulations, you should take pride in that. Someone who plants a bee garden for free is worth more than a hedge fund manager who only contributes misery to the world, even if he makes a lot of money doing it. Someone who uses their body to block, however temporarily, the export of weapons or the laying of pipeline is infinitely more valuable to society than the skilled engineer who makes his living designing them. Even simple activities like telling jokes or doing chores are worth infinitely more than developing advertising software that only makes people annoyed and parts them from their money!
Like the moral of that movie It's A Wonderful Life wasn't that the guy should go on living because he really tried his best and maybe he'll finally get to do what he wants with his life once he saves up his pennies; the moral was that he should go on living because he'd made life materially and spiritually better for his community. We need that energy!!
681 notes
·
View notes
Text
Femme Fatale Guide: Products & Services Worth The Splurge
Fashion:
A great couple of bras in black/nude (your best skin-toned shade)
Comfortable, breathable, and seamless underwear
Outerwear (Coats, jackets, blazers)
The perfect pair of jeans
An LBD that works from day to night
Comfortable, sturdy, sleek, and timeless footwear (a versatile black boot, a black heel, white sneaker, and a black flat/loafer/sandal)
A timeless and versatile crossbody or shoulder bag (a larger one for the daytime/work or school and a smaller one for nighttime/events)
One or two well-made classic jewelry item(s)
A conversation-starting item or accessory
Beauty:
Sunscreen
Any skincare/skin cosmetic products that are game-changers for you
A quality hair brush, comb, and hair towel
Your signature scent
A quality razor/hair removal product
Vitamin C/Retinol serums
Reliable hair tools and sturdy nail tools
A quality hair heat protectant/scalp cleansing or conditioning spray
Makeup brushes and beauty tool cleaners
Home:
Lamps/lighting
Couch/desk chair
Everything for your bed: Bed frame, mattress/sheets/pillows, etc.
Knives
Dishwasher-safe and microwave-safe dishes & cups you love
A full-length mirror
Vacuum
Storage solutions/cedar blocks or moth balls
Quality holders for everything: Paper towels, shower storage, hooks, mailbox/key bowls
Name brand paper products/household cleaners
Electric toothbrush & Waterpik
Sound-proof headphones/Airpods
MacBook Air
Health & Wellness:
High-quality lettuce and/or sprouts
Organic frozen fruits and vegetables (if fresh is too pricey)
BPA-free canned goods
Potassium bromate & glyphosate-free grain products
Snacks free of artificial colors
Quality coffee
An at-home massage tool/heating pad
Fur products for skin/hair removal
Vitamin C/Retinol serums
Quality running shoes
Anything that goes near your vulva or into the vagina: Sex toys, lube, condoms, toy cleaners, pads/tampons/menstrual cups, cleansing wipes, etc.
A yoga mat, resistance band, and a pair of small ankle weights
Spotify subscription
Books and audiobooks
Services:
Therapy
A top-tier haircut
House cleaning (even if it's only once every couple of months)
Top-tier hair removal/brow maintenance services of your choice
Best doctors, dentists, OB/GYN, and dermatologists you can get
At least one personal training/styling session in your life
Professional/Social:
Ownership of the domain for your full legal/professional name and/or business name
A CPA/bookkeeper/fiduciary financial advisor
Automation workflow/content management system software
A lawyer for contract review/LLC services
Personalized stationery/"Thank You" cards
Memorable client gifting for the holidays/milestone successes
Niche skill-based certifications (Google, AWS, Hubspot, etc.) or courses made by trusted professionals in your field
Subscriptions in world-leading and industry-authority digital publications
#femmefatalevibe#girl talk#girl tips#girl advice#girl blogging#femme fatale#dark femininity#dark feminine energy#it girl#high value woman#dream girl#queen energy#female power#high value mindset#female excellence#the feminine urge#glow up#level up journey#high class#classy life#elegance#product recommendations#healthylifestyle#health & fitness#fashion and beauty#life advice#life tips#etiquette
1K notes
·
View notes
Text
Demon-haunted computers are back, baby

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

As a science fiction writer, I am professionally irritated by a lot of sf movies. Not only do those writers get paid a lot more than I do, they insist on including things like "self-destruct" buttons on the bridges of their starships.
Look, I get it. When the evil empire is closing in on your flagship with its secret transdimensional technology, it's important that you keep those secrets out of the emperor's hand. An irrevocable self-destruct switch there on the bridge gets the job done! (It has to be irrevocable, otherwise the baddies'll just swarm the bridge and toggle it off).
But c'mon. If there's a facility built into your spaceship that causes it to explode no matter what the people on the bridge do, that is also a pretty big security risk! What if the bad guy figures out how to hijack the measure that – by design – the people who depend on the spaceship as a matter of life and death can't detect or override?
I mean, sure, you can try to simplify that self-destruct system to make it easier to audit and assure yourself that it doesn't have any bugs in it, but remember Schneier's Law: anyone can design a security system that works so well that they themselves can't think of a flaw in it. That doesn't mean you've made a security system that works – only that you've made a security system that works on people stupider than you.
I know it's weird to be worried about realism in movies that pretend we will ever find a practical means to visit other star systems and shuttle back and forth between them (which we are very, very unlikely to do):
https://pluralistic.net/2024/01/09/astrobezzle/#send-robots-instead
But this kind of foolishness galls me. It galls me even more when it happens in the real world of technology design, which is why I've spent the past quarter-century being very cross about Digital Rights Management in general, and trusted computing in particular.
It all starts in 2002, when a team from Microsoft visited our offices at EFF to tell us about this new thing they'd dreamed up called "trusted computing":
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The big idea was to stick a second computer inside your computer, a very secure little co-processor, that you couldn't access directly, let alone reprogram or interfere with. As far as this "trusted platform module" was concerned, you were the enemy. The "trust" in trusted computing was about other people being able to trust your computer, even if they didn't trust you.
So that little TPM would do all kinds of cute tricks. It could observe and produce a cryptographically signed manifest of the entire boot-chain of your computer, which was meant to be an unforgeable certificate attesting to which kind of computer you were running and what software you were running on it. That meant that programs on other computers could decide whether to talk to your computer based on whether they agreed with your choices about which code to run.
This process, called "remote attestation," is generally billed as a way to identify and block computers that have been compromised by malware, or to identify gamers who are running cheats and refuse to play with them. But inevitably it turns into a way to refuse service to computers that have privacy blockers turned on, or are running stream-ripping software, or whose owners are blocking ads:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
After all, a system that treats the device's owner as an adversary is a natural ally for the owner's other, human adversaries. The rubric for treating the owner as an adversary focuses on the way that users can be fooled by bad people with bad programs. If your computer gets taken over by malicious software, that malware might intercept queries from your antivirus program and send it false data that lulls it into thinking your computer is fine, even as your private data is being plundered and your system is being used to launch malware attacks on others.
These separate, non-user-accessible, non-updateable secure systems serve a nubs of certainty, a remote fortress that observes and faithfully reports on the interior workings of your computer. This separate system can't be user-modifiable or field-updateable, because then malicious software could impersonate the user and disable the security chip.
It's true that compromised computers are a real and terrifying problem. Your computer is privy to your most intimate secrets and an attacker who can turn it against you can harm you in untold ways. But the widespread redesign of out computers to treat us as their enemies gives rise to a range of completely predictable and – I would argue – even worse harms. Building computers that treat their owners as untrusted parties is a system that works well, but fails badly.
First of all, there are the ways that trusted computing is designed to hurt you. The most reliable way to enshittify something is to supply it over a computer that runs programs you can't alter, and that rats you out to third parties if you run counter-programs that disenshittify the service you're using. That's how we get inkjet printers that refuse to use perfectly good third-party ink and cars that refuse to accept perfectly good engine repairs if they are performed by third-party mechanics:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
It's how we get cursed devices and appliances, from the juicer that won't squeeze third-party juice to the insulin pump that won't connect to a third-party continuous glucose monitor:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
But trusted computing doesn't just create an opaque veil between your computer and the programs you use to inspect and control it. Trusted computing creates a no-go zone where programs can change their behavior based on whether they think they're being observed.
The most prominent example of this is Dieselgate, where auto manufacturers murdered hundreds of people by gimmicking their cars to emit illegal amount of NOX. Key to Dieselgate was a program that sought to determine whether it was being observed by regulators (it checked for the telltale signs of the standard test-suite) and changed its behavior to color within the lines.
Software that is seeking to harm the owner of the device that's running it must be able to detect when it is being run inside a simulation, a test-suite, a virtual machine, or any other hallucinatory virtual world. Just as Descartes couldn't know whether anything was real until he assured himself that he could trust his senses, malware is always questing to discover whether it is running in the real universe, or in a simulation created by a wicked god:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
That's why mobile malware uses clever gambits like periodically checking for readings from your device's accelerometer, on the theory that a virtual mobile phone running on a security researcher's test bench won't have the fidelity to generate plausible jiggles to match the real data that comes from a phone in your pocket:
https://arstechnica.com/information-technology/2019/01/google-play-malware-used-phones-motion-sensors-to-conceal-itself/
Sometimes this backfires in absolutely delightful ways. When the Wannacry ransomware was holding the world hostage, the security researcher Marcus Hutchins noticed that its code made reference to a very weird website: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Hutchins stood up a website at that address and every Wannacry-infection in the world went instantly dormant:
https://pluralistic.net/2020/07/10/flintstone-delano-roosevelt/#the-matrix
It turns out that Wannacry's authors were using that ferkakte URL the same way that mobile malware authors were using accelerometer readings – to fulfill Descartes' imperative to distinguish the Matrix from reality. The malware authors knew that security researchers often ran malicious code inside sandboxes that answered every network query with fake data in hopes of eliciting responses that could be analyzed for weaknesses. So the Wannacry worm would periodically poll this nonexistent website and, if it got an answer, it would assume that it was being monitored by a security researcher and it would retreat to an encrypted blob, ceasing to operate lest it give intelligence to the enemy. When Hutchins put a webserver up at iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, every Wannacry instance in the world was instantly convinced that it was running on an enemy's simulator and withdrew into sulky hibernation.
The arms race to distinguish simulation from reality is critical and the stakes only get higher by the day. Malware abounds, even as our devices grow more intimately woven through our lives. We put our bodies into computers – cars, buildings – and computers inside our bodies. We absolutely want our computers to be able to faithfully convey what's going on inside them.
But we keep running as hard as we can in the opposite direction, leaning harder into secure computing models built on subsystems in our computers that treat us as the threat. Take UEFI, the ubiquitous security system that observes your computer's boot process, halting it if it sees something it doesn't approve of. On the one hand, this has made installing GNU/Linux and other alternative OSes vastly harder across a wide variety of devices. This means that when a vendor end-of-lifes a gadget, no one can make an alternative OS for it, so off the landfill it goes.
It doesn't help that UEFI – and other trusted computing modules – are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), which makes it a felony to publish information that can bypass or weaken the system. The threat of a five-year prison sentence and a $500,000 fine means that UEFI and other trusted computing systems are understudied, leaving them festering with longstanding bugs:
https://pluralistic.net/2020/09/09/free-sample/#que-viva
Here's where it gets really bad. If an attacker can get inside UEFI, they can run malicious software that – by design – no program running on our computers can detect or block. That badware is running in "Ring -1" – a zone of privilege that overrides the operating system itself.
Here's the bad news: UEFI malware has already been detected in the wild:
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
And here's the worst news: researchers have just identified another exploitable UEFI bug, dubbed Pixiefail:
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
Writing in Ars Technica, Dan Goodin breaks down Pixiefail, describing how anyone on the same LAN as a vulnerable computer can infect its firmware:
https://arstechnica.com/security/2024/01/new-uefi-vulnerabilities-send-firmware-devs-across-an-entire-ecosystem-scrambling/
That vulnerability extends to computers in a data-center where the attacker has a cloud computing instance. PXE – the system that Pixiefail attacks – isn't widely used in home or office environments, but it's very common in data-centers.
Again, once a computer is exploited with Pixiefail, software running on that computer can't detect or delete the Pixiefail code. When the compromised computer is queried by the operating system, Pixiefail undetectably lies to the OS. "Hey, OS, does this drive have a file called 'pixiefail?'" "Nope." "Hey, OS, are you running a process called 'pixiefail?'" "Nope."
This is a self-destruct switch that's been compromised by the enemy, and which no one on the bridge can de-activate – by design. It's not the first time this has happened, and it won't be the last.
There are models for helping your computer bust out of the Matrix. Back in 2016, Edward Snowden and bunnie Huang prototyped and published source code and schematics for an "introspection engine":
https://assets.pubpub.org/aacpjrja/AgainstTheLaw-CounteringLawfulAbusesofDigitalSurveillance.pdf
This is a single-board computer that lives in an ultraslim shim that you slide between your iPhone's mainboard and its case, leaving a ribbon cable poking out of the SIM slot. This connects to a case that has its own OLED display. The board has leads that physically contact each of the network interfaces on the phone, conveying any data they transit to the screen so that you can observe the data your phone is sending without having to trust your phone.
(I liked this gadget so much that I included it as a major plot point in my 2020 novel Attack Surface, the third book in the Little Brother series):
https://craphound.com/attacksurface/
We don't have to cede control over our devices in order to secure them. Indeed, we can't ever secure them unless we can control them. Self-destruct switches don't belong on the bridge of your spaceship, and trusted computing modules don't belong in your devices.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/17/descartes-delenda-est/#self-destruct-sequence-initiated

Image: Mike (modified) https://www.flickr.com/photos/stillwellmike/15676883261/
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#uefi#owner override#user override#jailbreaking#dmca 1201#schneiers law#descartes#nub of certainty#self-destruct button#trusted computing#secure enclaves#drm#ngscb#next generation secure computing base#palladium#pixiefail#infosec
575 notes
·
View notes
Text
Enhance Efficiency with Top Commercial Property Management Tools

In today’s fast-paced real estate market, efficient management of commercial properties is more crucial than ever. That’s where commercial property management software comes into play, transforming the way property managers handle their operations. This software streamlines processes, improves accuracy, and boosts productivity, making it an indispensable tool for property management organizations across the UK.
What is Block Management Software?
Block management software is a specialized solution for managing multi-unit residential and commercial properties. Unlike general property management software, block management software is tailored to handle the complexities associated with multiple units within a single block or development. This includes service charge accounting, tenant management, and maintenance tracking, among other functionalities.
With Trace Solutions, you gain access to enterprise-class commercial property management software designed specifically for this purpose. This software is utilized by many of the UK's most successful property management organizations, reflecting its robustness and efficiency.

Key Features of Block Management Software
Service Charge Accounting
One of the primary features of block management software is its ability to manage service charge accounting. This includes calculating, billing, and reconciling service charges for tenants and leaseholders. Trace Solutions' software simplifies this process, ensuring accuracy and transparency in financial management.
Tenant and Leaseholder Management
Effective management of tenants and leaseholders is crucial for successful property management. The software provides comprehensive tools for tracking tenant information, lease details, and communication. This feature ensures that property managers can efficiently handle requests, renewals, and other tenant-related tasks.
Maintenance and Repairs Tracking
Managing maintenance and repairs is a significant part of property management. Block management software includes tools for logging maintenance requests, scheduling repairs, and tracking the status of work. This functionality helps ensure that issues are resolved promptly, contributing to tenant satisfaction.
Financial Reporting
Accurate financial reporting is essential for property management organizations to monitor performance and make informed decisions. The software generates detailed financial reports, including income and expenditure statements, budget forecasts, and service charge summaries.
Document Management
Managing documents related to property management, such as leases, contracts, and correspondence, can be challenging. Block management software offers a centralized document management system, making it easy to store, retrieve, and manage important documents.

Why Choose Trace Solutions?
Trace Solutions offers an advanced block management software solution that stands out in the market for several reasons:
Comprehensive Functionality
The software provides a complete suite of features tailored to the needs of block management. From service charge accounting to maintenance tracking, it covers all aspects of property management, ensuring a streamlined and efficient process.
User-Friendly Interface
Despite its advanced features, Trace Solutions' software is designed with a user-friendly interface. This makes it accessible to property managers of all levels of expertise, reducing the learning curve and improving overall efficiency.
Scalability
Whether managing a small block of flats or a large commercial development, Trace Solutions' software is scalable to meet the needs of different property management scenarios. This flexibility ensures that the software can grow with your business.
Exceptional Support
Trace Solutions is committed to providing excellent support to its clients. With a dedicated helpdesk available at +44 (0)20 7825 1234, you can rely on timely assistance for any software-related queries or issues.

Real-World Applications
Many of the UK's leading property management organizations rely on Trace Solutions' block management software. These organizations benefit from improved efficiency, accuracy, and control over their property management operations. By adopting this software, property managers can focus on delivering exceptional service to tenants and leaseholders while streamlining their internal processes.
Contact Information
For more information about Trace Solutions and how their block management software can benefit your organization, you can reach out to them at the following contact points:
Location: 30A Great Sutton Street, London EC1V 0DU
Sales Hotline: +44 (0)20 7825 1299
Main Switchboard: +44 (0)20 7825 1000
Helpdesk: +44 (0)20 7825 1234
Conclusion
In the competitive world of property management, leveraging advanced tools like block management software can provide a significant edge. Trace Solutions offers a comprehensive, user-friendly solution designed to enhance every aspect of property management. By investing in this software, you can improve efficiency, accuracy, and overall management of your commercial properties. Explore how Trace Solutions can transform your property management operations today.
#block management software#property management and accounting software#property management software#property management solution
0 notes
Text
A Comprehensive Guide for Writing Advice
Sometimes, despite enjoying writing so much, something is not working for you. Maybe your well of ideas has run dry. Or your WIP has hit a corner and you can't find your way out to the end of the story. Or you need to go back to your finished draft and see if there are any kinks to clear up.
Fortunately, everyone at Writeblrcafé has experienced such, and to help you out, we have a bunch of links to helpful posts by fellow writers to help you along on your writing journey as well as some helpful links to other websites, resources and software.
General:
WHY IS WRITING IS SO FUCKING HARD? (@writers-hq)
Writer Block First Aid Kit (@isabellestone)
Websites for writers (masterpost @2soulscollide)
Writing advice (masterpost @theliteraryarchitect)
Writing resources (masterpost @stinastar)
One look thesaurus (a reverse dictionary where you can enter words or concepts)
Coming Up with Ideas:
97 Character Motivations (@theplottery)
Character Flaws (@fantasyfillsmysoul)
Character Profile (@mistblossomdesigns)
Characters Unflawed (@emptymanuscript)
Why Theme is More Important than Plot (@theplottery)
Weekly writing prompts on Reedsy
Drafting:
3 of the worst story beginnings (and how to fix them) (@theplottery)
Cheat Sheet for Writing Emotion (@myhoniahaka)
Creative Writing for Writers (@writerscreed)
Describing Physical Things (@wordsnstuff)
How to Craft a Natural Plot (@theplottery)
How to Write a Story? (masterpost @creativepromptsforwriting)
How to write: ethnicity & skin colour (@youneedsomeprompts)
What the F is Show Not Tell (@theplottery)
Writing advice from my uni teachers (@thewritingumbrellas)
First Draft: story outlining template meant to help with planning your next big writing project (@fauxriot)
The wonder/ discovery arc (@evelynmlewis)
How to structure a chapter (@theplottery)
How to pace your storytelling (@charlesoberonn)
How to write and research mental illness (@hayatheauthor)
Seven Blogs You Need To Read As An Author (@hayatheauthor)
Editing/Revising:
Eight steps in making the editing process of your book easier (@joaneunknown)
Kill Your Darlings (@tibodine)
Self editing tips (first pass) (@projecttreehouse)
Publishing:
Chill Subs: biggest database for literary magazines and small presses; track your submissions and get your writing published!
5 steps to get your novel ready to self-publish (by @nanowrimo)
Resources for finishing and publishing your novel (masterpost by @nanowrimo)
For self-publishing: this page gives you the exact pixel count of a book spine based on its page count, and/or a template you can use for the correct width/height ratio.
Software:
Scrivener: one time payment of $60 or 70€ (macOS/windows), $24 (iOS; no Euro listed for iOS); used by professionals, many tools to write and organize your novel
Bibisco: free and "pay what you want" version; multilingual, world building, character profiles, writing goals, story timeline, mind maps, notes and more templates to write a novel.
Manuskript: free open source-tool; outliner, novel assistant, distraction-free mode
Ghostwriter: a free and open alternative which has a decent interface with some interesting features, like Hemingway Mode, which disables one's backspace and delete keys, emulating a typewriter.
NaNoWriMo: an international contest to encourage writers to finish writing their novel with many events, groups for exchange with fellow writers, helpful writing advice and help for self-publishing and publishing traditionally.
Campfire Writing: website, desktop app, and mobile app, with tools built in to help manage characters, magic systems, research, etc. It has a great free option, plus monthly, annual, and lifetime purchase options. It also has built-in NaNoWriMo compatibility and a catalogue of tutorials and writing advice videos (suggestion by @harfblarf)
Websites And Writing Apps Every Author Needs In 2023 (@hayatheauthor)
Let us know in the comments if there are any links we could add to it! Reblog this post to help a fellow writer.
Support our work by buying a cup of coffee on KoFi.
#wc.admin#writing community#writing advice#writing tips#writers on tumblr#creative writing#writing resources#writing software
3K notes
·
View notes
Text
So NFTgate has now hit tumblr - I made a thread about it on my twitter, but I'll talk a bit more about it here as well in slightly more detail. It'll be a long one, sorry! Using my degree for something here. This is not intended to sway you in one way or the other - merely to inform so you can make your own decision and so that you aware of this because it will happen again, with many other artists you know.
Let's start at the basics: NFT stands for 'non fungible token', which you should read as 'passcode you can't replicate'. These codes are stored in blocks in what is essentially a huge ledger of records, all chained together - a blockchain. Blockchain is encoded in such a way that you can't edit one block without editing the whole chain, meaning that when the data is validated it comes back 'negative' if it has been tampered with. This makes it a really, really safe method of storing data, and managing access to said data. For example, verifying that a bank account belongs to the person that says that is their bank account.
For most people, the association with NFT's is bitcoin and Bored Ape, and that's honestly fair. The way that used to work - and why it was such a scam - is that you essentially purchased a receipt that said you owned digital space - not the digital space itself. That receipt was the NFT. So, in reality, you did not own any goods, that receipt had no legal grounds, and its value was completely made up and not based on anything. On top of that, these NFTs were purchased almost exclusively with cryptocurrency which at the time used a verifiation method called proof of work, which is terrible for the environment because it requires insane amounts of electricity and computing power to verify. The carbon footprint for NFTs and coins at this time was absolutely insane.
In short, Bored Apes were just a huge tech fad with the intention to make a huge profit regardless of the cost, which resulted in the large market crash late last year. NFTs in this form are without value.
However, NFTs are just tech by itself more than they are some company that uses them. NFTs do have real-life, useful applications, particularly in data storage and verification. Research is being done to see if we can use blockchain to safely store patient data, or use it for bank wire transfers of extremely large amounts. That's cool stuff!
So what exactly is Käärijä doing? Kä is not selling NFTs in the traditional way you might have become familiar with. In this use-case, the NFT is in essence a software key that gives you access to a digital space. For the raffle, the NFT was basically your ticket number. This is a very secure way of doing so, assuring individuality, but also that no one can replicate that code and win through a false method. You are paying for a legimate product - the NFT is your access to that product.
What about the environmental impact in this case? We've thankfully made leaps and bounds in advancing the tech to reduce the carbon footprint as well as general mitigations to avoid expanding it over time. One big thing is shifting from proof of work verification to proof of space or proof of stake verifications, both of which require much less power in order to work. It seems that Kollekt is partnered with Polygon, a company that offers blockchain technology with the intention to become climate positive as soon as possible. Numbers on their site are very promising, they appear to be using proof of stake verification, and all-around appear more interested in the tech than the profits it could offer.
But most importantly: Kollekt does not allow for purchases made with cryptocurrency, and that is the real pisser from an environmental perspective. Cryptocurrency purchases require the most active verification across systems in order to go through - this is what bitcoin mining is, essentially. The fact that this website does not use it means good things in terms of carbon footprint.
But why not use something like Patreon? I can't tell you. My guess is that Patreon is a monthly recurring service and they wanted something one-time. Kollekt is based in Helsinki, and word is that Mikke (who is running this) is friends with folks on the team. These are all contributing factors, I would assume, but that's entirely an assumption and you can't take for fact.
Is this a good thing/bad thing? That I also can't tell you - you have to decide that for yourself. It's not a scam, it's not crypto, just a service that sits on the blockchain. But it does have higher carbon output than a lot of other services do, and its exact nature is not publicly disclosed. This isn't intended to sway you to say one or the other, but merely to give you the proper understanding of what NFTs are as a whole and what they are in this particular case so you can make that decision for yourself.
95 notes
·
View notes
Text
Following a White House edict effectively banning federal employees from disclosing their personal pronouns in email signatures, sources within multiple federal agencies say pronouns are now being systemically blocked across multiple email clients and other software.
WIRED confirmed various automated efforts with employees at the United States Agency for International Development (USAID), the Environmental Protection Agency (EPA), the General Services Administration (GSA), the US Department of Agriculture, and the Centers for Disease Control and Prevention (CDC).
The employees spoke to WIRED on condition of anonymity, citing fears of retaliation.
Multiple agency directors sent emails over the weekend telling staff that, due to President Donald Trump’s executive order, their offices would be removing the pronoun capability from Office 365. Employees were told they’d also need to remove pronouns from their email signatures in order to comply with the directive.
A staffer at USAID says the formal deactivation of their ability to list pronouns occurred last week, in response to executive orders defining sexes issued by President Trump on his first day in office. A GSA staffer says pronouns were wiped from employees’ email signatures after hours on Friday and were also no longer visible in Slack, the workplace messaging app. At the CDC, there used to be a section for employees to share their pronouns on their Teams profiles, another workplace app. That field no longer exists.
Reached for comment, the White House transferred WIRED to OPM communications director McLaurine Pinover, who pointed to January 29 memorandum ordering agencies to disable all features “that prompt users for their pronouns.”
The ban on personal pronouns follows sweeping efforts by the White House to eliminate programs that encourage diversity and social justice within the federal government, as well as other references to “diversity, equity, and inclusion” in federal employees’ discourse.
In a striking example of the policy in action, an image surfaced last week of a wall being painted over at the Federal Bureau of Investigation's Quantico, Virginia, academy due to it listing "diversity" among the bureau's core values. (According to an email from the FBI’s Office of Integrity and Compliance obtained by Mother Jones, the bureau no longer counts "diversity" among its core values.)
The Trump administration began a radical campaign last week aimed at inducing members of the federal workforce to leave their jobs ahead of threatened reductions. The effort is spearheaded by Elon Musk, leader of the so-called Department of Government Efficiency (DOGE), a task force that has effectively seized control of several federal agencies and sensitive government systems with apparent clearance from the White House.
WIRED reported last week that Musk’s outfit had effectively taken over the Office of Personnel Management, the US government’s human resources department. In this and other efforts, it is employing inexperienced young engineers whose ages range from 19 to 24—many of whom, public records show, are former interns or have been affiliated with Musk-aligned companies.
OPM emailed federal workers on January 28 with a “deferred resignation offer,” sparking widespread confusion among federal workers. (DOGE’s own new HR chief was unable to answer basic questions about the offer in a contentious staff meeting last week, WIRED reported.) In an email to staff Sunday evening, OPM clarified whether the deferred resignation program complied with existing privacy laws. “Yes,” read the answer. “The deferred resignation program uses only basic contact information about federal employees, like name and government address, along with short, voluntary email responses. The information is stored on government systems. To the extent that the Privacy Act applies, all information relevant to the program is covered by existing OPM System Records Notices.”
Multiple agency sources told WIRED last week that several of Musk's lieutenants had been granted access to key computer systems controlled by the GSA, an independent agency tasked by Congress with overseeing federal buildings and providing equipment, supplies, and IT support across the government.
31 notes
·
View notes
Text
4 Ways To Cure Writer’s Block

Every year, we’re lucky to have great sponsors for our nonprofit events. NovelPad, a 2023 NaNoWriMo sponsor, is a novel drafting software designed to make it easy for writers to write. Today, they're sharing a few tips to help you beat writer's block:
NovelPad loves NaNoWriMo because we have the same goal: Helping authors get the thing done!
Starting a book is usually fun and easy—your fingers dance across the keyboard as you explore an exciting world, meet your characters, and stir up intrigue for the coming plot. But once you get into the weeds of how that all works, and how you and your characters get from Point A to Point B, you might find yourself losing momentum. You might find yourself so encumbered with obstacles that you might get a case of the dreaded writer’s block.
The very good news is that writer’s block isn’t terminal, and I certainly don’t think writer’s block is as enigmatic as some people seem to think. I believe it’s actually quite a simple problem, and usually due to one of a few common factors. Let’s look at four ways you can push yourself through your case of ye olde block.
1. Check in with yourself.
Step one is always to check in with yourself.
Start by reviewing your basic self-care needs:
Are you staying hydrated?
Do you feel hungry?
Would a shower or a nap be beneficial?
Is it time for a walk or some stretching exercises?
Consider your environment as well. Maybe you need:
Noise-canceling headphones
A change of scenery
A babysitter or someone to help around the house
To open or close some windows
Next, evaluate your level of focus. Is your mind wandering elsewhere? It can be useful to create a "dump list" to jot down anything that's causing you stress, such as work-related issues, pending tasks, or upcoming events. Setting that list aside can give you the tangible feeling of pushing those things off your desk to worry about later.
Once your body, mind, and environment are sorted out, you'll likely discover that writing becomes a bit easier!
2. Look back at where you’ve been.
Even if the first tip did or did not do the trick, let’s take a look at the project itself.
Sometimes writer’s block is a blessing in disguise! Your creative gut might be telling you that something went awry. Try reading your project back and pinpointing where it became difficult to keep going. Consider alternate plots or paths to get your writing flowing again.
If you're managing multiple plots and subplots, identifying the moment you deviated from the main path can be quite challenging. To pinpoint which plot line is causing issues, you can take advantage of NovelPad's handy feature: Plot tracking.

On the Plot Board, you can review every scene of a particular plot in order, making spotting those errors in your plotlines much easier.
3. Rewrite a problem scene.
Once you've identified the scene causing issues, it's time to make improvements! This can be challenging because there are countless ways to approach a scene.
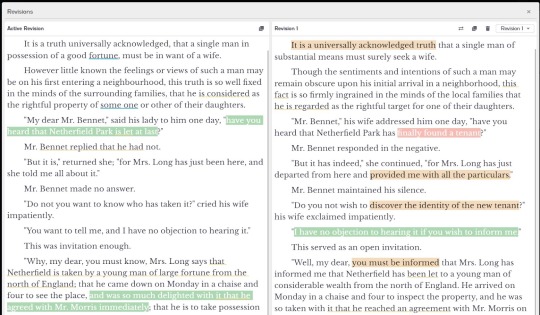
However, don't hesitate to embrace revisions. Often, a scene benefits from a thorough rewrite. With NovelPad Revisions, you can save limitless scene revisions, compare them side by side, and effortlessly switch to the one they want in the live manuscript. This keeps your different versions safe, well-organized, and readily accessible.
4. Freewrite to free yourself.
Freewriting is a great way to get your creativity flowing again. Write some poetry, compose a letter to a friend, or simply let your thoughts flow without judgment. Freewriting without judgment can help turn on your writer mode and even help you solve some problems! It's especially beneficial when you're stuck on something specific, because we often find brilliant solutions when we stop being so critical of our ideas.
Kick writer’s block off your desk with NovelPad! It's free to use throughout NaNoWriMo, and we offer discounts to participants and winners afterward. If you find that NovelPad isn't your cup of tea by the end of November, don't worry—you can still access and download your project at any time. Just write!
Our team at NovelPad believes in making it easy for writers to complete their books. That’s why we built an uncomplicated, intuitive system that stays out of the way until you need it! We want writers like you to #JustWrite without burdening you with excessive features. Speaking of features, software updates at NovelPad are based entirely on user feedback from authors to keep our features sharp, relevant, and minimalist.
All NaNoWriMo participants have access to a 15% discount on NovelPad with code WRIMO2023 — use the code during checkout to redeem your discount. Offer expires April 1, 2024.
Top photo by Richard Dykes on Unsplash.
217 notes
·
View notes