#bank hacking softwares
Explore tagged Tumblr posts
Text
Bank Account Hacking Software

Bank account hacking software allows hackers to steal your personal banking information. When you are vulnerable and don't know it, they can enter your name and social security number on a fake account with stolen passwords to purchase fraudulent goods or sell on the black market.
#Bank hacking site#bank hackers online#bank hacks#instant bank transfer#legit bank hacking forum#hacking forum#hacking online#bank hacking software#bank hacking softwares#hackers online#bank account hacking#bank account hackers#hack money online#legit account hackers#cashapp flips#cashapp transfer
1 note
·
View note
Text
Warning to everyone, my Banking Laptop got hacked, if you noticed your security software has been disabled, you've been hacked! Hackers can hack you in 5 minutes...

#hacks#hacking#computer hacking#computer#laptop#banks#banking#hackers#ive been hacked#security software#security software disabled#slow computer#slowing down#slowing down your pc#pc#people everywhere#warning#be warned#open to anyone#money#my money
1 note
·
View note
Text
Secure Bank Hacking Software to Protect Your Financial Data
Our bank hacking software is designed to help you get access to secure banking systems. With our advanced technology, you can gain access to accounts quickly and securely. Our software is reliable and easy to use, so you can start hacking right away.

0 notes
Text
Buy Bank Logins

you will get the login details for one of our Bank Accounts Logins that you can use to withdraw cash or make transfers to another account at your desired bank. Please contact us first before ordering the service. We can tailor the service to suit your needs and specifications. Please see our other listings to find out more about other services that we offer.’
#Bank Account Hacking#Bank Hacking Software#ATM Hacking Tricks#Buy ATM Cards With Balance#Buy Bank Account Logins#Buy Bank Logins#Western Union Hacker#Western Union Hacking Software#Dumps With Pin
0 notes
Text
Last Rites of the 3DS (and Wii U)
Monday, March 27th 2023, is the very last day to download software from the eShop. While this is generally sad for the loss of all the digital only content, there is one piece of software that is vital to have on every possible 3DS
If you ever want to play and transfer pokemon from Gen 1 (Red/Blue) through 7 (Sun/Moon) to Gen 8 (Sword/Shield) and beyond, you NEED to download Pokemon Bank NOW.
This will involve making a Nintendo Network ID, but that's simple and takes only a few minutes in the eShop.
If you miss this deadline, you will have to hack your 2DS/3DS to get this software. Follow the guide at 3ds.hacks.guide to do this with no risk of bricking. It takes about 30 minutes.
After that, you can check out my guide Three Gay New Crimes for advice on what a hacked 3DS can do. I have a similar guide for the Wii U as well.
One more time: download pokemon bank by the 27th, or hack your 3DS. Those are the only options for moving your pokemon forward.
Please dm me any questions. I'm here to help in this stressful time.
374 notes
·
View notes
Note
Hi. If you don't mind me asking, how exactly did you get hacked? And how did you realize it happened? It's just that it's something of an anxiety of mine, and I feel that by learning from other people it happened to, I can learn to avoid it. No worries if you don't feel like talking about it, though.
I don't honestly know for sure, but I THINK it was because my desktop computer is pretty old and has been running on a very outdated version of Windows for quite a while now. I don't normally do things like click on suspicious links or answer suspicious emails or calls or messages from bots, but I'm quite lazy about things like updating my hardware and software when the older stuff is still working fine for me. Unfortunately this eventually makes you more vulnerable to being hacked remotely, because you can't get stuff like the current security updates and support on your computer's programs and all after a bit. Over the past couple of weeks I've had someone using my Facebook account to post fake ads for cars and motorcycles on Marketplace, someone using my Steam account to list all my trading cards for sale, somebody flooding my email address to receive literally hundreds of spam emails (like signing me up for random newsletters and junk mail and so on), and somebody using my credit card to attempt to buy a big purchase for themselves on Amazon. Basically since I don't know exactly how it started and the fact that it seems to be happening on multiple of my accounts I just had to go cancel my credit card and report the fraud to my bank, change every password on every personal account I could think of and add more 2 factor authentication steps to everything, and then wipe my computer of as much personal info as possible and lock it up a bit better too. I undid all the settings like the automatically saved passwords on my browser, and I'm not leaving it connected to the internet or leaving any of my personal accounts logged in when I'm not using them anymore. The security breaches seem to have stopped with me changing these passwords and everything else, but it's definitely a very violating and annoying experience to say the least. I should probably be more freaked out about it than I actually am, which is kinda just feeling a bit like the exasperated Ben Affleck smoking meme instead hahaha
#for some reason i just cant be assed to get that worked up about it and im just kinda finding it funny#anyways i do understand why its a big fear but#theres nothing i can do about it already having happened so i have to just deal with it and move on#getting a new computer soon as well I GUESS#ask#anon#p
9 notes
·
View notes
Text
The Bad Batch and their jobs (Modern AU)
In my headcanon they all started out as soldiers. After getting out and accidentally acquisiting Omega, they desperately need money and take any jobs they can get. Eventually, everyone finds something they actually like.
Hunter:
Retail sales associate aka Walmart slave and getting yelled at by Karens all day. He's also doing freelance cleaning jobs, the grosser the better the payment. Think hoarder apartments with fifty cats or scat orgy hotel room cleanup.
He works hard on getting his record cleaned up and eventually secures a job at the fire station. He becomes a firefighter and will eventually be a lieutenant and later captain.
Tech:
Fast food worker which means lots of being yelled at by hangry people who are unhappy with the way their BigMac was stacked. He takes any extra shift he can get.
After several failed rounds of applications, he hacks into a big company's system and puts his name on top of the candidate list. He ends up supervisor for some bank insurance IT stuff with lots of numbers.
Wrecker: Miner. It's hard work and long hours in the dark. He actually earns the most of all of them but that's because it's fucking dangerous and depressing.
The leading instructor for the demolition expert trainees blows up. Wrecker, having had professional training in the military and lots of experience at not getting blown up (again), is their best take so he becomes their new instructor for the new hires.
Crosshair: Nobody is really willing to hire him so he's an unlicensed taxi driver most nights. (He hates everything about it.) He also signed up as a freelance roadkill collector job in Hunter's name and takes the calls when he doesn't have passengers.
He meets railroaders when cleaning up railkill one night. When smoking he mentions how much he hates being a taxi driver and the railroaders recruit him for their company. He becomes a traindriver and finally doesn't have to interact with his passengers.
Echo: They call it online sales associate marketer and customer service advisor. He calls it tele-scam-marketer. Many people yelling at him but at least he can work from home.
At a parent-teacher conference of Omega's school he helps another parent with a technology problem. He's like: "I tried to get rid of that problem for hours and you did it within five minutes. You gotta be a master software engineer." and Echo's like "I get payed to get yelled at as a telemarketer". Turns out the guy is an HR associate at an IT company and gets Echo a proper job.
#star wars#clone wars#bad batch modern au#the bad batch#bad batch#modern au#star wars modern au#bad batch echo#bad batch hunter#bad batch tech#bad batch wrecker#bad batch crosshair#roadkill collector
39 notes
·
View notes
Text
Class Feature Friday: Hacker Specialization (Operative Specialization)

(art by gtasoul on DeviantArt)
If there’s anything unique to science fiction, it’s hacking. After all, traditional fantasy rarely has computers (and when they do, they’re usually the ancient, barely understood kind), leading to an entirely different avenue of heroic action as the characters crack open cybersecurity measures, often stylized with virtual avatars and the like.
Now, with their tech savvy, you probably expect the average hacker to be a mechanic or technomancer, and that’s fair, they certainly have the specialization. However, brilliant engineers and techno-mages are hardly the only archetypical hacker characters. Sometimes someone is only focused on computers and not engineering. Others might be agents with a variety of skills that just happens to include cybersecurity as a specialization.
After all, it’s one thing to remotely hack someone from across the cybercafe using the unsecured wifi, and an entirely different beast to sneak into a secure facility and crack open a server with no wireless connection.
And so we have the hacker specialization for operatives. Bank details, classified documents, incriminating messenger logs, the targeting software for the rocket turrets shelling the party… If its on a computer, it isn’t safe from them. What’s more, as operatives, they have the skills to get in close enough to do their hacking without being detected (hopefully). So let’s see what makes them special!
Naturally, these operatives are very familiar with computers and engineering, and they can use their computer skills as part of their trick attacks, sending distracting alerts to enemy headsets, causing malfunctions in nearby devices, or even simply projecting a distracting hologram from their own device. Obviously, however, they have to actually have a computer device on hand to do so. One of the rare occasions where an operative may be forced to use a different skill with their trick attacks.
As expert hackers, these operatives learn how to be especially cautious in their approach, reducing the chance of triggering countermeasures if they accidentally push to hard.
More skilled hackers can take control of devices they have hacked, potentially using their functions for their own benefit a few times before they return to normal or are deactivated.
While not as adept at hacking as other classes, hacker operatives can do a lot of fun things with it, particularly once they gain control of a system with their mid-level ability. Imagine activating the security systems to target the guards, or starting up machinery that proves distracting or hazardous, and so on. I recommend pairing your hacking skills with stealth or another sneaky skillset to make the most of it.
There are a lot of ways to play a hacker. They might be terminally online, or they might tap into vibes of the 80’s idea of a hacker as a cool trendy figure with fancy computer knowhow. Or they may be more professional about it. Certainly hacking has a long association with disrespecting authority, with all the character traits associated with that.
The hacker known only by the username LuckySTR!KE is a notorious thorn in the side of may corporations, earning them a bounty for their capture or death. However, the crafty worlanisi tends to stay a step ahead. However, the contents of their latest datamining has them nervous, and they’re willing to pay for bodyguards.
A passionate hacktivist and self-proclaimed protector of the ecosystems of the galaxy. Beshara has developed a knack for sneaking into corporate facilities and sabotaging their efforts to study and exploit wildlife. However, when one such outing ends up with several researchers being scarred and killed by the acidic saliva of flying kriegakos, she begins to wonder if she has become too extreme.
An expedition to alien ruins may not seem like it needs a computer expert, but when it is discovered the stone buildings are interlaced with intricate technomagical circuitry, one is called in. Unfortunately, the team doesn’t realize this hacker is a corporate spy feeding information back to a rival conglomerate and seeking to steal the most precious treasures in the name of their employer. Unfortunately, her acts of espionage and greed end up awakening the mummified guardians of the ruin.
7 notes
·
View notes
Text
⚠️ FRIDAY - ISRAEL REALTIME - Connecting to Israel in Realtime
Erev Shabbat - Parshat Barak - Numbers 22:2 - Balak, the king of Moab, summons the prophet Balaam to curse the people of Israel. Three times, from three different vantage points, Balaam attempts to pronounce his curses; each time, blessings issue forth instead. Balaam also prophesies on the end of the days and the coming of Moshiach (the Jewish messiah).
⚠️ WORLD WIDE COMPUTER OUTAGE .. Israel impact (not a cyber attack - an update error)
ISRAEL EMERGENCY NUMBERS MAY BE DOWN:
MDA 101 - alternatives call Hatzalah 1221 (who report they are operating fine) or 100 police
Electric Company - instead of 103, call 054-5838074 or report on Facebook page.
Working fine: 100 police, 102 fire
Some Israeli companies impacted - may accept only cash or be unable to do business for a while:
Israel Post
Ikea
Delek gas stations
Various hospitals - Shaarei Tzedek reports recovered, normal ops, Hadassah not on the problem list, Asuta Ashdod working fine
Affected: Hillel Yaffe, Laniado, Barzilai, Sheba, Wolfson, Shamir Assaf Harofeh, Rambam, Ma'aini Hashua, Nahariya, Poria, Bnei Zion, Ziv, the French Hospital in Nazareth, the Italian Hospital in Nazareth
Meuhedet health clinics
Clalit health clinics
Carrefour grocery - cash only
Banks HaPoalim, Leumi, Discount
Bank of Israel
Port of Ashdod completely down to ships and trucks
EL AL reports no impact, they don’t use the affected software.
Unrelated - Globes newspaper hacked (not the web site, the newsroom.)
WORLD IMPACT:
AIR TRAVEL - FAA suspending many flights in the US, Berlin flights on hold, Spain flights on hold.
Sky News having disruptions
⚠️HEZBOLLAH THREATENS.. significant retaliation for recent IDF targeted eliminations. Northern towns should be on ALERT, take precautions in the north.
▪️RUMORS ABOUT PM.. may suspend trip to the US. At the same time, “Israeli officials estimate that the Netanyahu-Biden meeting will not take place on Monday as planned”, unclear if due to Biden’s health or US election politics.
▪️FIN. MINISTER.. Sanctions from cabinet on PA officials NOT implemented by IDF and Shin Bet for the last 3 weeks???
▪️FBI USES ISRAELI SOFTWARE.. Washington Post: The FBI hacked into the phone of the assassin of Trump using the software of the Israeli company Celebrity.
▪️ECONOMY.. The Turkish embargo has stopped the import of Hyundai, and it is beginning to seep into Toyota, whose inventory in Israel is also shrinking.
PRESS BRIEFING BY IDF SPOKESPERSON RADM. DANIEL HAGARI - JULY 19, 2024
Overnight, a UAV, which we believe was launched from Yemen, infiltrated from the sea to our west and struck a building in central Tel Aviv. This impact resulted in the death of one civilian and lightly injured eight others. We extend our condolences to the bereaved family and wish a speedy recovery to the injured.
No alert was activated during the incident, and we are thoroughly investigating the matter. Our initial findings suggest the UAV was a Samad-3, an Iranian weapon likely upgraded to extend its range. This UAV flew from Yemen to Tel Aviv. Iran supports, funds, and arms its proxies in Gaza, Judea and Samaria, Lebanon, Syria, and Yemen, as evidenced by last night's event. UAV threats have been a constant challenge since the beginning of the war across all our borders. Dozens of UAVs have been launched from Yemen alone, most of which have been intercepted or shot down before entering Israeli territory. The majority were intercepted by an American task force under U.S. CENTCOM, while the rest were intercepted by Israeli Air Force planes or defense systems.
Simultaneously with the Tel Aviv incident, another UAV attempting to infiltrate from the east was intercepted and shot down outside of Israel’s borders. We are investigating the connection between the two incidents.
We are conducting a thorough inquiry to understand why the UAV was not identified as a threat and intercepted before it struck. An initial inquiry was conducted this morning, and we will continue to review the findings and update the public accordingly.
I want to emphasize that our defense is not foolproof. We are strengthening our air patrols and airspace protection across the country. We are continuously improving our capabilities to better protect the citizens of Israel.
There is no change in the Home Front Command directives. Should there be any changes, we will immediately inform the public.
Overnight and this morning, the Chief of the General Staff conducted several situational assessments. We have increased our defensive capabilities in Israel’s skies with additional planes and other measures to improve detection, alert, and interception capabilities. The incident on the ground was managed cooperatively by the Israel Police, Magen David Adom, and the Israel Fire and Rescue Services, who provided vital details for the inquiry.
In the north, the UAV threat is a daily challenge due to short-range launches, differing from last night’s incident. We are studying the northern threat to improve our response. We recognize the ongoing challenges faced by residents in the north.
In the past day, we have eliminated six Hezbollah terrorists and struck fifteen targets from the air and ground in the north.
We are engaged in a multi-front war, operating in all arenas and defending the country's skies daily. We are addressing threats both near and far.
In the coming days, we will continue our situational assessments to understand the incident better, determine the source of the threat, and decide on the necessary defensive and operational responses against those who threaten the State of Israel.
11 notes
·
View notes
Text
Out of curiosity does anyone know any hacks/fanmade software/etc that can allow you to transfer Pokemon from Bank to Home for free? I am not interested in paying for another subscription service just to get my Pokemon off of the 3DS :/
#pokemon#pokemon home#pokemon bank#3ds#idk how to tag this to get people to find it#uhhh#homebrew#3ds homebrew#3ds hacking
7 notes
·
View notes
Text
Sims 4 Malicious Script Mod Advisory
We all know by now that some modders have been hacked and their script mods replaced with malicious malware. Hopefully none of my followers have been hit and if you have, I hope you've taken the necessary steps to safeguard your sensitive data. There has been a list of modders who's scripts are no longer safe to download circulating.
There are a number of ways to find out if you've been hit or not.
To quickly check if you have been compromised, press Windows + R on your keyboard to open the Run window. Enter “%AppData%/Microsoft/Internet Explorer/UserData” without the quotes in the prompt and hit OK. This will open up the folder the this particular malware uses. If there is a file in this folder called “Updater.exe”, you have unfortunately fallen victim to the malware. Some sites will tell you "we don't know what it does". In reality, this updater is designed to download, install and run a data collection app. Passwords, site tracking, bank routing -- all the worst case scenarios you can dream up regarding your personal information.
So, delete the folder if you find it and grab this:
Release Version 1.1 · overwolf/sims4-social-events-cleaner · GitHub
If you're still downloading script mods, download this to help protect yourself:
ModGuard: Mod Malware Protection v1.4 | Patreon
Be aware that your antivirus and most malware detection software will not recognize a script mod as malware or virus.
10 notes
·
View notes
Text


Hex throws herself into her work.
She doesn’t have anything else to be passionate about. She has no partner. She has no family of her own. All she can do is work, earning simoleons to decorate and furnish her home.
Her life right now is exhausting. She’s living two different lives. By night, her alien form comes out, her criminal boss persona. By day, her human form is sickly sweet, luring sims in so she can bug or pickpocket them. Her bank account looks healthy, but her mental state doesn’t.
The Lotharion Trust systems are fighting back hard today. Hex can’t get in to steal simoleons. She sags back in her seat, sighing in exasperation. She looks like an ordinary office worker annoyed at an email. The irony of her work isn’t lost on her.
She safely closes down her hacking software, vowing to try another day. She flips her phone over, not surprised when she sees no text messages. Maybe she should reach out and see someone. Deep down, she does miss her siblings.
Hex makes the decision. She pulls up her brother, Thorne’s, phone number and asks if she can come over to see her nephews. He tells her that his latest arrival, Hemming, is fast asleep, but she can come and see her favourite nephew, Ruid. His bright little smile is exactly what Hex needs to cheer herself up.
#the sims 4#ts4#sims#simblr#sims 4#differences in the family tree#ditft#quick legacy gen 8#hex quick#legacy challenge#ad
11 notes
·
View notes
Text
Best Benefits Of Using Hacking Software For Bank Transfers
Due to the rapid improvement in network innovation, PC networks have just started to be used widely in the financial sector. Digital assaults, however, are something they must constantly defend against. In general, these financial areas, especially the financial areas, depend on two different types of safety: Bank Transfer Hacking Software.
0 notes
Text
Money Transfer Hackers

One of the most common ways to secure your online bank account is with a password. However, this is not always enough to keep hackers out of your account. This post will teach you what you should do if you suspect that someone has accessed your account without permission and give advice on how you can protect yourself from a financial takeover by Money Transfer Hackers
#Money Transfer Hackers#Bank Account Hacking#Bank Hacking Software#ATM Hacking Tricks#Buy ATM Cards With Balance#Buy Bank Account Logins#Buy Bank Logins#Western Union Hacker#Western Union Hacking Software#Dumps With Pin#Credit Card Dumps With Pin
0 notes
Text
Rummaging through my old room I find this, a traditional flip note of Pantufa the Cat from 2011 or earlier, with rusty staples and, according to the numbers on the corner, missing frames.
For detailed ramblings of hidden memories this unlocked, click for more
I've always wanted to be an animator and, while I didn’t have the software or hardware for digital animation, I wanted to practice is as much as I could. This was the best I could put together at the age of 16.
I would do small scale animations at the edges of notebooks or draft ideas in comic form with notes before I knew what a Storyboard was. Back then I didn't even have a stable internet connection in the first place, this was around the time I had to share a PC with my older brother who would kick me out at any opportunity and hog the PC for the entire day, only letting me on at the last minute, where I would get an earful from my parents and be told to go to bed, it was a nightmare to do anything digitally...
The first drawing tablet I got was considered scrap the moment I got it for Christmas. No screen, wobbly inaccurate pen (can't draw a straight line without it looking like lightning), Silvercrest branded (basically, LIDL), it was as cheap as it could be but it was my introduction to "not using the mouse to draw" which it did not help with as even today revisiting it makes me want to draw with a mouse more.

Things were very strict and if something did what it needed to do, it didn't need to be replaced. "That's what I had been taught"If it ain't broke, don't fix it" was the motto for my family and that mentality stuck to me even to the present day. I still find myself using MSPaint for Pixelart or drawings, as spending for anything greater is hardwired in my brain as "unnecessary" or "wasteful", hell, I wasn't even allowed to spend money outside of school purchases such as at the cafeteria (they had a kickass card charging system which made the school I attended in Germany around 2016-2019 look medieval in comparison which is incredible since Portugal isn't the first thing you think of when it comes to technological advancements), so any money I would get for Christmas or birthdays was practically useless and I never learned to manage income. I would sometimes find my mom take the money off my piggy bank for groceries and other goods when she was running low, she didn't try to lie, she had no reason to.
Anything I can get for free is what I stick by and I'll only spend money if I absolutely have to or, more recently, if it benefited close friends in any way, as I've learned to have no regard for my own well being and should be ashamed for even considering it, others always take priority.
So when it comes to animation today, I have a "yar har" version of Toon Boom Studio 8.0 for bigger things (I've tried OpenToonz but it's very crash happy and I've lost hours of animation with it even with the backup and auto save features on, back in the day I had a a copy of Flash CS4 I grabbed from the school computers that I got to work after some tinkering and a well placed crack) and for Pixelart I just use Windows XP's MSPaint and abuse scroll-wheel and window resizing shenanigans to advance frames. I don't get much time to practice animation and I get easily excited to have a chance at it.
I'm under my own mental shackles at all times and that's not going to change, only further cemented by the elitist mindset the Sonic Hacking community and SRB2 had taught me, a mindset I regret adopting and one I catch myself going back to and feeling ashamed of every now and then, leading only to depressive episodes that are best left for a psychologist to deal with... should I ever find the opportunity to seek one without time and language barrier issues.
As the years go by and I find myself doing or just refining Pixelart than to do animated pieces, I've given up hope in being an animator in the foreseeable future, only dedicating animation to those done in private between friends, never allowing myself to clean up or refining it in any meaningful way unless asked for because I shouldn't. It's why I tend to ask for suggestions or characters to add for animations I plan to do, cause I don't want it to be for me, I want it to be for those I can make happy to see it.
---
Before I hit "Post", a reminder that there are people much worse off than I am, these are just memories and 1st world problems and should be nobody's priority. Please support growing young artists and animators, they need it more than some washed up wanna-be animator that is known for nothing else but basic Sonic ROM hacks disguised to look impressive via a coat of MSPaint.
49 notes
·
View notes
Note
You mentioned making proper genned event pokemon, but what does that entail?
depends on the event in question!
back in the day during gens 3 and 4, IRL event distributions were often handled by running a custom GBA cart with the event distribution software and hooking up to other GBAs via link cable or with the wireless adapter, or a custom DS cart that took advantage of the DS' innate wireless compatibilities. obviously all of these carts were meant to be sent back to nintendo or get destroyed, but that... just did not happen to all of them lol. (there are also a few local distribution softwares for 3DS and stuff but wayyy less common)
you can actually buy gen 4 distribution carts for an excessive amount of money, though i can't in good conscience recommend looking for gen 3 distribution carts, they're INCREDIBLY rare and most of the listings you'll find for them on ebay are 100% fake and are scamming you out of hundreds of dollars, and most people don't know how to tell the difference unfortunately.
that being said, i'm not recommending you buy these at all actually, because most of the ones in physical circulation have been dumped online and can be downloaded. the digiex forums contains them, and you can download these and run them on actual hardware and roleplay being the toys r us/gamestop/etc employee and distribute to themself just like how it would have happened back at the time of the event lmao. for the DS ones it's easy with a hacked 3DS and twilight menu, but for GBA you'd need a GBA flashcart and the associated link cable/wireless adapters + two GBAs. this can also be done on emulators with support for local connection between two windows and has the same exact effect as doing it with real hardware, it just feels cool to do it with real hardware (pictured below is an ancient video i took of me distributing 2005 Aura Mew to myself with the actual software made by nintendo, running off a flashcart. i took this years ago and the quality is ass and my positioning is awkward sorry lol. my room doesn't even look the same...)
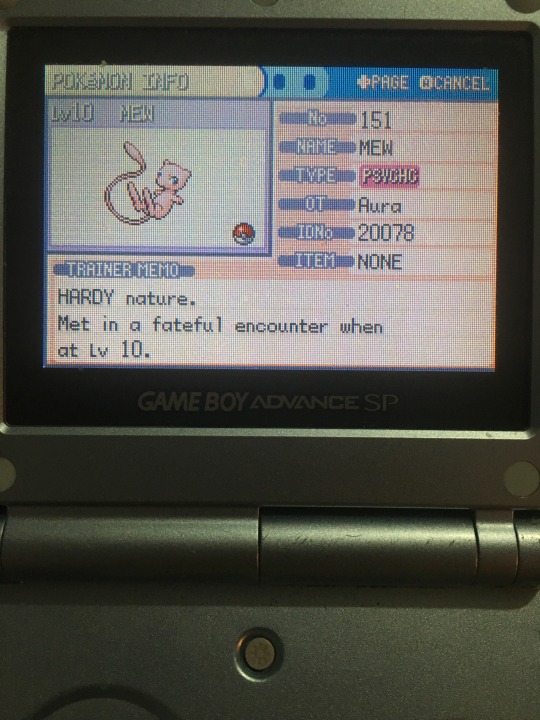
as for events without distribution software, old gen ones have the DNS exploit, which you can find simple instructions for here. this is much easier with gen 5 than gen 4 - you can find gen 4 help i wrote here. these restore all online functionality in the old games, including mystery gift - trying to grab a mystery gift from the internet will allow you to download pretty much any event in the game (though the one it gives you is random and you'd have to try over and over to get the ones you want). the data of these events is 100% identical to how the events actually were at the time of distribution, like completely indistinguishable, so it's a safe way to get those mons to bank and home, though you may want to change your DS date to the same date as the event in question so it doesn't look weird.
as for 3DS there is no fancy stuff like the above, you'll just want to go to project pokemon's public event gallery and browse for what you're looking for, which also provides a link to instructions for injecting these in your games. it's worth noting you can also inject all the gen 3-5 events that have been documented/archived this way, it's just less interesting than the above methods imo. this is probably the least legitimate feeling option but the data is still identical and well. other than elaborate glitches or something that's the best its gonna get. it's likely once 3DS servers shut down next year that eventually a DNS exploit-adjacent service will pop up for gen 6 and 7...
btw worth noting that gen 4 is the only gen where the name rater literally only checks for TID and doesn't even consider the "fateful encounter" flag that event pokemon are usually given, so you can RNG manip a matching trainer ID and then nickname event mons you aren't supposed to be able to nickname fully within the limits of the original game and hardware LOL. that isn't related to your question i just think it's funny that you can do that and it's technically completely legit
anyway sorry for the long ass answer i just find mystery gifts fascinating and it deserved me being a little more comprehensive
edit: oh yes and there's certain event mons that are still able to be obtained without all this wacky stuff, ie the pokemon colosseum bonus disc gives out infinite jirachis and they just released that as a preorder bonus back then. so worth looking at options for distributions like that too if you need a species of mythical or whatever!
12 notes
·
View notes