#security software
Explore tagged Tumblr posts
Text
Absolutely mind-boggling how kaspersky, a software with near perfect rating when it comes to security, is being banned in the USA because it's from russia (it's being operated from the UK).
And the reason is that they COULD leak data to russia. Yknow, something every single other cyber security software COULD do as well. It was founded over 25 years ago and nothing ever happened, you think they gonna start now? Really? And, again, you don't have to be working for a russian company to be a russian spy, who's to tell some mcafee employee won't leak data instead?
I'm usually not one to defend a billion dollar company but the blatant lack of knowledge and "this man from russia made it = it's evil" reasoning is so infuriating. Maybe sit down for once and talk to the people who tested the security software. Jfc.
#there's legit no other arguments behind the ban besides 'russian man bad'#it's fcking gross#kaspersky#cyber security#security software#kaspersky lab
11 notes
·
View notes
Photo
Here's something you need to hear from an IT person that you're being lied to about:
VPN's are not security software. They don't secure private data from people who are actually looking.
If you're truly worried about your data only visit your sensitive account sites from closed networks that you control.
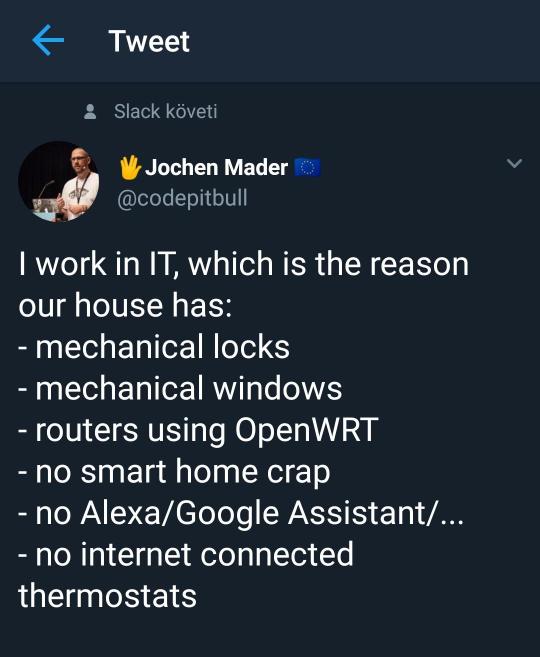
Relatable
307K notes
·
View notes
Text
Looking At - Lockdown Options for the Mac

A quick note before we get started this research is from 2023 and has not been updated. I am just now putting this content out because I finally have a place to put it.
Options Looked At
I picked three options:
Absolute Manage (Home and Office)
HiddenApp
Prey Project
I picked Absolute Manage because that is something I am familiar with from the enterprise space. Home and office version because I am not paying for the enterprise product. HiddenApp because it was on the Jamf Marketplace (tho it seems to have been replaced with Senturo, but HiddenApp is still around so who knows). Prey was an obvious include because it's a popular option that's cheap.
What are we evaluating?
I am only looking at how the product locks down the Mac in the case of an outside of geofence, lost or stolen situation. I am not commenting on any of the other functionality.
tl;dr
For those of you not interested in the why's, how's and wheretofor's the conclusion is that Absolute Manage is significantly better than either of the other options. Its lock down is more effective and more robust against tampering etc.
What's wrong with HiddenApp?
The password to unlock the Mac is stored as an MD5 hash with no salt or any other protection.
You can, if you disconnect from the network, change the password to whatever you want it to be by simply changing the hash in the device_locked.status file found in /usr/local/hidden. You need to be an admin, but that is more and more common in the Mac space even in the enterprise.
The lock down is triggered by a Launch Daemon and therefore doesn't activate immediately. I have seen it take multiple minutes to lock the screen–giving you more than enough time to stop it.
The HiddenApp itself is not obfuscated so you can easily reverse engineer any part you need.
If the user is an admin not only can they change the lock password, but they can also prevent their machine from ever locking by simply controlling the missing marker file. You can also of course simply remove HiddenApp since it has no special protection. If you are not on the network once you stop the lock down–HiddenApp can't fix itself without network help.
What's wrong with Prey?
Prey like HiddenApp has a weak method of storing the password to unlock the computer. The method used is: string input converted to utf-8 then base64 encoded and then md5 hashed and returned as a hex digest. You can find this by looking at: /lib/agent/actions/lock/mac/prey-lock in the Prey folder (this is a Python3 file). So you can easily break this scheme due to it being MD5 you just need to base64 encode your wordlist first.
The password hash is easily obtained from looking at the output of sudo ps -A with the window expanded. The password is in the command-line arguments passed to prey-actions.app with -lock flag.
The lock can be bypassed with Safe Mode and with SSH.
The application itself is built from a lot of JavaScript/node.js code. This also means its trivial to reverse engineer.
The application makes no effort to hide itself or obscure what it is doing.
What's right with Absolute Manage Home and Office?
Unlike the other two options Absolute Manage uses a robust lock down based on a SecurityAgentPlugin that runs at login. The lock down is therefore immediate and is hard to bypass by comparison.
The password is not as robust as the other options (4-6 digit pin), but given that the lockdown is immediate during login you don't have the same ability to block it or tamper with it. Keep in mind this is the personal product–so the pin lock makes some limited sense.
The application does a good job obscuring itself and what it is doing.
The only effective bypass I found was if SSH is enabled, then you can SSH in and bypass the lock. I put in a feature suggestion that they disable SSH as part of the lock down.
The product is much more difficult to get rid of, because it stores its components in multiple locations and generally tries to hide itself.
Safe mode does not get around the lock out unlike some of the other products.
The biggest issue I found was the time between issuing a lock command and it being enforced on the endpoint was excessively long-hours in many cases. Observed times as long as 15 hours between issuing the lock command it taking place. This could have been my setup so take it with a grain of salt.
Conclusion
The asset management tool space is a crowded one, and if you are looking for a good product that locks down stolen or otherwise improperly stationed assets you need to take great care to verify what you are buying. Of the three products I picked only one was remotely serviceable, and unless you dive into the details of how the products work it is easy to mistake bad solutions for good ones.
0 notes
Text
1. Unmasking Tor Browser: The Alarming Truth About Its Privacy and Security and How Safe Is Your?
Unmasking Tor Browser: How to use the Tor Browser securely?How to verify the integrity of my Tor browser download using GnuPG.Step-by-Step Guide to Verifying Tor Browser Download Using GnuPGHow does Tor ensure anonymity and privacy for its users?What other security tools should I use with Tor Browser?How does Tor ensure anonymity and privacy for its users?Tor Browser:Practical Tips for…
0 notes
Text
Defending the Digital Realm: The Critical Role of Cybersecurity

In today’s highly connected digital age, cybersecurity has shifted from a secondary concern to a top priority. As cyber threats continue to rise in both volume and complexity, individuals, businesses, and governments alike face unprecedented risks, including severe data breaches, financial losses, and damage to their reputations. The need for robust cybersecurity practices has never been more pressing. With that in mind, here are some essential strategies to help safeguard your digital assets.
To start, encouraging the creation of strong passwords can motivate readers to take that critical first step in securing their accounts. A combination of letters, numbers, and symbols creates a powerful first line of defense against unauthorized access.
Phishing scams are another significant threat in today’s digital landscape. These schemes are designed to trick people into sharing sensitive information. By helping readers recognize the warning signs of these increasingly advanced scams, you can equip them to navigate the digital world more safely.
Additionally, emphasizing the importance of regular software updates and reliable antivirus protection is vital. These measures help close security gaps and bolster defenses against potential cyber threats. By stressing the necessity of strong passwords, a keen awareness of phishing scams, and the habit of keeping software up to date, we can significantly enhance our digital security.
Ultimately, knowledge and proactive measures are our best tools for safely navigating the ever-evolving cyber landscape. Remember, vigilance and awareness are essential to staying secure in today’s digital world.
#Cybersecurity solutions#Data protection#Network security#Cyber threat detection#Security software#IT security services#Cyber defense#Threat prevention#Secure business solutions#Cybersecurity experts
0 notes
Link
Consolidation of security is insecure
#technology#Israel#startups#Unit 8200#infiltration#security software#backdoors#VPNs#surveillance#Kape Technologies
0 notes
Text
Amazon Prime Day occasion begins, gross sales up 12% in first 7 hours: Report | Firm Information
Prime Day can function a bellwether for the vacation procuring season. 3 min learn Final Up to date : Jul 17 2024 | 12:10 AM IST Amazon.com Inc.’s Prime Day gross sales rose virtually 12 per cent within the first seven hours of the occasion in contrast with the identical interval final 12 months, based on Momentum Commerce, which manages 50 manufacturers in a wide range of product…
#amazon#Amazon Prime#artificial intelligence#bank account#Check Point Software Technologies#counterfeit products#director of worldwide buyer risk prevention#E-commerce & Auction Services#e-commerce shoppers#eBay#Federal Trade Commission#Food Retail & Distribution (NEC)#HTTP#Internet & Mail Order Department Stores#Josh Planos#online hoaxes#online retailer#online shopping giant#Online shopping scams#phony products#public relations#retail calendar#Scott Knapp#Security Software#social media ads#vice president of communications and public relations#Walmart
0 notes
Text

Leading University Risk Management Tools | SECTARA
Leverage a suite of professional university risk management solutions designed to help universities identify, mitigate, and monitor potential functional, operational, financial, reputational, and compliance risks.
Today, universities and other higher education institutions face a plethora of challenges including increased regulatory clampdown from regulatory bodies such as TEQSA, ASQA, the US Department of Education, OfS, and QAA, scrutiny by the public on student selection, tuition fees, and governing procedures, and credit and financial situations.
These risks have put a lot of educational institutions at risk of closure, with studies reporting nearly 20% of four-year colleges in the US facing operations risks.
That’s why we designed SECTARA to provide universities and other higher education institutions with the tools needed to detect and mitigate these challenges and create a stable and safe environment for students, staff and faculty.
Discover how university risk management tools can help universities help detect, monitor, and address potential risk vectors Click here for more details.
#Risk Management Software#security and investigations#security consultants#security risk assessment software#security risk management#security risk software#security software
0 notes
Text
however bad of a day you're having, know that it's not nearly as bad as whatever the Crowdstrike security team is going through since waking up this morning
#accidentally bricking millions of computers worldwide because of a faulty security update pushed through on Friday evening#has to be some special circle of hell for software engineers#crowdstrike#current events#technology
2K notes
·
View notes
Text
It's always "funny" to remember that software development as field often operates on the implicit and completely unsupported assumption that security bugs are fixed faster than they are introduced, adjusting for security bug severity.
This assumption is baked into security policies that are enforced at the organizational level regardless of whether they are locally good ideas or not. So you have all sorts of software updating basically automatically and this is supposedly proof that you deserve that SOC2 certification.
Different companies have different incentives. There are two main incentives:
Limiting legal liability
Improving security outcomes for users
Most companies have an overwhelming proportion of the first incentive.
This would be closer to OK if people were more honest about it, but even within a company they often start developing The Emperor's New Clothes types of behaviour.
---
I also suspect that security has generally been a convenient scapegoat to justify annoying, intrusive and outright abusive auto-updating practices in consumer software. "Nevermind when we introduced that critical security bug and just update every day for us, alright??"
Product managers almost always want every user to be on the latest version, for many reasons of varying coherence. For example, it enables A/B testing (provided your software doesn't just silently hotpatch it without your consent anyway).
---
I bring this up because (1) I felt like it, (2) there are a lot of not-so-well-supported assumptions in this field, which are mainly propagated for unrelated reasons. Companies will try to select assumptions that suit them.
Yes, if someone does software development right, the software should converge towards being more secure as it gets more updates. But the reality is that libraries and applications are heavily heterogenous -- they have different risk profiles, different development practices, different development velocities, and different tooling. The correct policy is more complicated and contextual.
Corporate incentives taint the field epistemologically. There's a general desire to confuse what is good for the corporation with what is good for users with what is good for the field.
The way this happens isn't by proposing obviously insane practices, but by taking things that sound maybe-reasonable and artificially amplifying confidence levels. There are aspects of the distortion that are obvious and aspects of the distortion that are most subtle. If you're on the inside and never talked to weird FOSS people, it's easy to find it normal.
One of the eternal joys and frustrations of being a software developer is trying to have effective knowledge about software development. And generally a pre-requisite to that is not believing false things.
For all the bullshit that goes on in the field, I feel _good_ about being able to form my own opinions. The situation, roughly speaking, is not rosy, but learning to derive some enjoyment from countering harmful and incorrect beliefs is a good adaptation. If everyone with a clue becomes miserable and frustrated then computing is doomed. So my first duty is to myself -- to talk about such things without being miserable. I tend to do a pretty okay job at that.
#i know to some of you i'm just stating the sky is blue#software#computing#security#anpost#this was an anramble at first but i just kept writing i guess#still kind of a ramble
33 notes
·
View notes
Text
How to install NewPipe on Android
NewPipe is a YouTube replacement client for Android devices. It's open-source (meaning, you can see all of their code as you please), privacy-oriented, lightweight, and supports features that are normally locked behind a YouTube Premium paywall.
Disclaimer: I am not affiliated with NewPipe, YouTube, Android, Google, Alphabet Inc, or any other brand or name mentioned here. I made this guide to help my friends who were curious.
NewPipe's Website: https://newpipe.net/
The GitHub Repository
Step 0. Compatibility check
Make sure you're running an Android device! This won't work on an Apple device of any kind! Also, for those more tech-savvy among you, if you have the F-Droid store installed, you can download NewPipe straight from there!
Step 1. Downloading
Go to NewPipe's Github repo (repository, the codebase or where all of the code is stored). Scroll to the bottom of the page until you see "Releases". Click on the one that says "Latest" next to it in a little green bubble:

Your version number (v#...) will be different if you're reading this in the future! That's okay. Scroll past the changelog (unless you want to read it!) until you find "Assets":

Click on the first one, the one with the little cube ending in .apk. APK files are Android Package (Kit) and are the main format for downloading apps. Once you click on the link, it should begin downloading or your browser will ask you to confirm that you want to download this file. You should always verify the filename matches what you expect it to be (namely, the file format) before attempting to install! It might take a few moments for the file to download depending on your internet connection.
Step 2. Installation
Once you have the file downloaded, you can click the download popup in your notification bar or find the file in your device's file system. One of 2 things will happen:
You will get a popup asking if you want to install an APK by the name of NewPipe - confirm that you do (and make sure the app is really NewPipe!) and it will install automatically. You can then click "Open" to open the app and begin using it.
You will get a popup warning you that you have the ability to install apps from unknown sources disabled and that you can't install this. This is normal and does not mean that you downloaded the wrong thing.
If you got the first popup, continue past this step. For those of you who got the second, let's go over what this means.
By default, most Androids have this setting disabled. This is for security purposes, so you can't accidentally install a malicious app from the whole internet. If you enable this setting (allow installations from unknown/unsigned sources), you are theoretically putting yourself at risk. Realistically, you're probably fine. But, after installing NewPipe, you can always re-disable the setting if it makes you more comfortable. That will prevent you from installing updates in the future, but it can always be re-enabled.
Ready to turn that setting on? It will vary by your individual device! Some devices will take you directly to the page with the setting upon failed installation, and some you will just have to find it yourself using the searchbar in settings.
Once you've allowed installations from unknown sources (wording may vary slightly), try to repeat the steps above of clicking the download popup or finding the APK in your files and trying to install it. It should work correctly this time!
Step 3. Updating NewPipe
Like most apps, NewPipe is in development currently and frequently has new versions released to improve it and fix bugs. Unlike most apps, NewPipe needs to be manually updated, since we haven't downloaded through the Google Play store.
To update NewPipe, all you have to do is follow the above steps for installing the app, except that when you get the popup asking to install it, it will instead say "Update". That's it! NewPipe and Android handle the rest.
NewPipe also has popup notifications for when the app has a new update, so you don't have to worry about checking the GitHub for a new release. Just click on the "A new version is available" popup and it should take you directly to the webpage.
That's it! Enjoy browsing videos in peace without ads and with the ability to download and so much more. Pro tip: you can copy paste YouTube links into the NewPipe search bar to go directly to that video/playlist/channel.
#newpipe#youtube#youtube client#youtube replacement#how to install newpipe#android#android apk#android app#images#text#links#image descriptions#privacy#data privacy#internet privacy#big tech#data security#github#software#database#opensource#open source#newpipe app
24 notes
·
View notes
Text
I am going to a CONFERENCE FEBRUARY 26-27 !
You "ok Moose... thats neat I guess but" Me again(interrupting): I am going to sell you on this immediately! CrowdStrike will be there! You "I... neat I guess... wait was that not those guys that broke 10 million windows computers? Hospitals, 911 lines, trains, security all going down? Billions in damage, people died. Those guys?" YES! And they are giving TALKS ! :D 2 of them! Building Resilience: Amplify Cybersecurity with the Power of AI And 2024’s Threat Actors Unmasked: What to Expect in 2025 CROWDSTRIKE IS HERE TO TELL US HOW TO IDENTIFY CYBERSECURITY THREATS! The OBJECTIVELY biggest thread to cybersecurity in 2024 is here to tell you how to spot threats. I am SO going to ask if the answer is "We look in the mirror" I am going to bring the BIGGEST bucket of popcorn I can find, have LOADS of interesting fun questions and have an AWESOME day. And it is free. I am using days off, but I will try to convince my boss that it is education. Who knows.
Here is a link to the event. It is free if you are nearby :3
#codeblr#software#software developer#cybersecurity#programming#engineer#software engineering#engineering#coding#c++#security
10 notes
·
View notes
Text
How is it possible big companies with awesome devs have issues with vulnerabilities? This question came up in a conversation and I thought it would be valuable to share my perspective. I think this can be easily summarized as surface area (without trying to over complicate things). People online can debate until blue in the face about the best way to write software and all of that, but I think it's a surface area issue. Agile vs not, speed vs quality, good vs bad dev practices, etc... All can influence this but I think surface area is the key. To elaborate, all software will have bugs of some form. Either unexpected behavior, undesirable behavior, or behavior that users don't agree with (by design potentially but a bug to them). The bigger the codebase, the bigger the chances of this. Let's extrapolate that to vulnerabilities. As developers, we're not actively every day trying to design things that are vulnerability-proof. Please don't misread that - I am NOT suggesting we go build things with bad security practices, bad ways to auth, no privacy concerns, etc... All of that is a HUGE priority, especially for big companies working with lots of user data at scale. But vulnerabilities are often buried through very odd interactions and tiny vectors. So you broaden the surface area by having more code (the amount of code even in my area at Microsoft would be unfathomable to understand the scope of for any one person) and then when you factor in it only takes a very tiny vector to potentially penetrate (ESPECIALLY an unexpected vector), it becomes more obvious why this happens. It only takes a tiny hole, and the bigger the balloon the more areas you can try and poke a hole. I worked in digital forensics for nearly a decade before Microsoft building cutting edge tools to get data from mobile phones. Apple *and* Android. This was mostly entirely based on exploits or otherwise finding ways to get just *one* step further. And I'll tell you... It only takes a totally random bizarre vector to get a tiny bit further for access. And then you build on it. And build on that. So it's not because people are ignorant to these things, it's just the surface area is incomprehensible. ---- 📨 Sign up for my email newsletter! 🗣️ Share with your network!
9 notes
·
View notes
Photo

(via The US will ban sales of Kaspersky antivirus software next month)
The Biden administration has taken a sweeping action to ban Kaspersky Labs from selling its antivirus products to US customers. The Russian software company will not be able to sell to new customers starting in July and cannot provide service to current customers after September.
Ahead of the official news, a source told Reuters that the company's connections to the Russian government made it a security risk with the potential to install malware, collect privileged information, or withhold software updates on American computers. US Secretary of Commerce Gina Raimondo announced the ban at a briefing today.
"You have done nothing wrong, and you are not subject to any criminal or civil penalties," she said to current Kaspersky customers. "However, I would encourage you, in as strong as possible terms, to immediately stop using that software and switch to an alternative in order to protect yourself and your data and your family."
20 notes
·
View notes
Text
to my old school computer
the keys on you may get stuck
like they would if you were a neglacted piano
but this message I'm writing
i never expected to be my last
we aren't together anymore, and you're
a non-sentient piece of technology,
hurriedly assembled and slow,
made clunkily by a machine, you don't run anymore
today they'll shut you down, and you won't remember
the 27,000 documents and pictures and videos and memories
we shared together.
this is to my old school computer.
i would hold you forever, without the factory reset
that breaks six years of warmth and late nights spent together.
in another life, I could stay attached, and we would
never have to forget one another.
Update device within 19 hours. the clock winds down with a tick.
"The district requires you to update your Chromebook
before the deadline." but this update will never come
and this deadline is forever your last
even though you don't know me like I know you,
i'll miss you all the same.
maybe you're in there, and maybe you'll miss me too,
maybe you loved me like I loved you
you were a friend, and a help, a distraction
from the loud world around me. without you I am nothing.
i take a deep breath in, close your lid shakily, and mutter my
goodbye.
#|○| sanka did art#poetry#writing#writer#poem#poems on tumblr#technology#|□| sanka gets serious#software#innovation#industry#security#futurism#tech#poems and poetry#original poem#poetic#love poem#objectum#object sentience#object empathy
18 notes
·
View notes
Note
I used Netscape Navigator 4.0 as my main browser until 2018. I might have one of the only surviving installs of Netscape Navigator 8 and 9 since they were only available through a web installer attached to long-dead servers
While I appreciate the Netscape enthusiasm, the mere thought of using a 20-year-old piece of software to do your daily browsing, has me like

The security risks, fallentechnate! Oh the humanity!
#Netscape Results#not serious#reaction image#reaction meme#netscape#netscape navigator#software#browser#web browser#web browsers#security#online security#internet security#photo
13 notes
·
View notes