#and why e.g. is generally undetected
Explore tagged Tumblr posts
Text
Efficiency Unleashed: Maximizing Solar Farm Performance with Drone Inspections
In the dynamic world of renewable energy, the true measure of a solar farm's success lies not just in its construction, but in its sustained performance. Every watt of electricity generated counts, and any dip in efficiency translates directly into lost revenue and diminished returns on investment. For large-scale solar installations, maintaining optimal output is a colossal undertaking. This is where the strategic deployment of solar panel drone inspection steps in, acting as the ultimate catalyst for unleashing peak performance and maximizing the operational efficiency of your solar assets.
The Efficiency Challenge: Why Every Percentage Point Matters
Solar panels are designed to perform reliably for 25 years or more. However, their efficiency can be subtly eroded by a myriad of factors over time. Even minor, seemingly insignificant issues can collectively lead to substantial power losses across a large array. Consider a 100 MW solar farm: a mere 1% reduction in efficiency due to undetected faults could mean a loss of 1 MW of power, translating to hundreds of thousands of dollars in lost revenue annually.
Traditional manual inspections, as previously discussed, are too slow and often too inaccurate to catch these creeping inefficiencies in time. Issues like:
Hot Spots and Overheating Cells: Indicate internal damage, short circuits, or bypass diode failures.
Micro-cracks and Delamination: Reduce cell effectiveness and can lead to moisture ingress.
Soiling and Debris: Accumulation of dust, dirt, bird droppings, or leaves can block sunlight.
Vegetation Overgrowth: Shading from nearby plants or trees significantly impacts shaded panels.
Module Mismatch: Panels operating at different currents or voltages within a string.
Wiring and Connection Faults: Loose connections increase resistance and reduce power flow.
Each of these issues, if left unaddressed, acts as a bottleneck, throttling the overall performance of the solar farm. The key to maximizing efficiency is rapid identification and precise remediation.
Drones: The Efficiency Multiplier
Solar panel drone inspection brings an unprecedented level of speed, precision, and data granularity that directly translates into enhanced efficiency. By leveraging advanced sensors and intelligent software, drones provide insights that empower operators to move from reactive troubleshooting to proactive performance optimization.
How Drones Boost Efficiency:
Rapid, Comprehensive Data Collection:
Speed: A drone can inspect hundreds of acres in hours, not weeks. This means entire solar farms can be scanned frequently – quarterly, monthly, or even more often – ensuring a near real-time understanding of asset health.
Coverage: Automated flight paths ensure every single panel is covered, eliminating human oversight and fatigue-related missed spots.
Dual-Sensor Insights: Equipped with both high-resolution RGB (visual) and thermal (infrared) cameras, drones capture a holistic view. Visual data identifies physical damage and soiling, while thermal data uncovers invisible electrical or cell-level faults.
Pinpoint Accuracy for Faster Repairs:
Geotagging: Every image captured by the drone is precisely geotagged, allowing faults to be mapped to their exact GPS coordinates on the solar farm layout.
Automated Anomaly Detection: AI algorithms swiftly process terabytes of data, identifying and categorizing anomalies (hot spots, cracks, soiling) with high accuracy, far surpassing human capabilities in speed and consistency.
Actionable Reports: The output isn't just raw data; it's detailed reports indicating fault types, severity, and precise locations. This empowers maintenance crews to go directly to the problematic panels with the right tools, eliminating guesswork and dramatically reducing repair time.
Proactive Maintenance and Predictive Analytics:
Early Detection: Catching minor issues (e.g., a developing hot spot or slight soiling) before they escalate into major failures is critical. Early intervention means minimal impact on energy production.
Trend Analysis: Regular drone inspections build a historical database of panel performance. This data can be analyzed over time to identify trends, predict potential future failures, and schedule preventative maintenance during low-demand periods.
Optimal Cleaning Schedules: Drones can accurately assess soiling levels across the entire farm, allowing operators to schedule cleaning services only when and where they are most needed, optimizing resources and maximizing the impact of cleaning efforts.
Optimizing Inverter Performance:
While drones inspect panels, the data they collect can indirectly indicate issues further down the electrical chain. If an entire string of panels consistently shows cooler temperatures, it might suggest an issue with the inverter input for that string, prompting further investigation.
Validation and Documentation:
Performance Benchmarking: Regular drone data provides a baseline for expected performance, making it easier to identify deviations and quantify losses.
Warranty Claims: High-resolution visual and thermal evidence, along with precise location data, provides undeniable proof for warranty claims against panel manufacturers for faulty modules. This recoups costs and ensures replacements for underperforming assets.
Real-World Impact: Unleashing ROI
The tangible benefits of solar panel drone inspection translate directly into improved financial performance for solar assets.
Increased Energy Output: By quickly identifying and rectifying underperforming panels, the overall energy yield of the solar farm increases. Even a fractional percentage point improvement can mean significant additional revenue over the lifespan of the farm.
Reduced Operational Costs: Fewer manual inspections, targeted repairs, optimized cleaning schedules, and prevention of catastrophic failures lead to substantial savings in labor, equipment, and replacement parts.
Extended Asset Lifespan: Proactive identification and remediation of defects mitigate premature degradation, ensuring panels operate efficiently for their projected lifespan and beyond.
Enhanced Grid Stability: A more efficiently operating solar farm contributes more reliably to the energy grid, supporting renewable energy targets and reducing reliance on fossil fuels.
The Future of Solar Farm Management
The integration of drones into solar farm operations is fundamentally redefining what "efficiency" means in renewable energy. It's about moving beyond simply having solar panels to ensuring those panels are always performing at their absolute best. As drone technology continues to evolve—with greater autonomy, more sophisticated sensor fusion, and seamless integration into larger asset management platforms—its role in unleashing the full potential of solar energy will only grow.
For any solar farm owner or operator striving for peak performance, maximum revenue, and a truly optimized green energy asset, embracing the power of solar panel drone inspection is not just an advantage—it's an imperative. It's the key to unlocking true efficiency and ensuring a brighter, more sustainable future.
0 notes
Text
The Impact of Food Reactions and Microbiome Disruption During and After Cancer Treatment

In clinical practice, I’ve seen first- hand how unresolved food reactions can undermine those undergoing cancer treatment and those recovering from cancer treatment. If you're experiencing chronic bloating, fatigue, skin flare-ups, or inflammation during or after treatment, these symptoms may not just be side-effect. They could be signs that your gut microbiome is under attack due to undetected food allergies, sensitivities, or intolerances.
Unknown to many, food allergies, sensitivities, and intolerances, are three different things. Here’s the difference between them.
Food Allergy: An Immune System Overreaction
A food allergy is an immediate (generally 0-20 minutes) and often severe immune system response to a specific food. The immune system identifies a protein in the food as a threat and launches a defense, producing IgE antibodies. This can lead to symptoms like:
Hives or rash
Swelling of the lips, tongue, or throat
Wheezing or difficulty breathing
Anaphylaxis (in severe cases)
Common allergens: Peanuts, shellfish, eggs, dairy, and soy.
Impact on the Microbiome Frequent allergic reactions lead to systemic inflammation and can alter immune-gut communication. Chronic inflammation damages the intestinal lining, creating a leaky gut environment and disrupting the diversity of beneficial bacteria.
Food Sensitivity: A Delayed Immune Reaction
Unlike allergies, food sensitivities involve a delayed immune response (generally from 0-72 hours), often mediated by IgG or other non-IgE immune pathways (like IgA, IgG4, IgM and IgD). Since reactions can take hours or even days to appear, it makes them harder to pinpoint. Symptoms include:
Brain fog
Fatigue
Headaches
Joint pain
Digestive discomfort (bloating, gas, constipation, diarrhea)
Common culprits: Gluten, dairy, corn, soy, eggs, and food additives.
Impact on the Microbiome:
Ongoing exposure to trigger foods can create chronic low-grade inflammation, increase intestinal permeability (aka “leaky gut”), and reduce microbial diversity. This weakens gut barrier function and impairs nutrient absorption—vital issues for cancer patients and survivors.
Food Intolerance: A Digestive Deficiency
A food intolerance is not an immune response but a digestive system issue. In most cases the body lacks the enzymes needed to properly break down certain foods. The most common example is lactose intolerance, caused by insufficient levels of lactase. Symptoms include:
Gas and bloating
Diarrhea
Stomach cramps
Nausea
Impact on the Microbiome
Undigested food becomes fuel for harmful bacteria and yeasts, promoting dysbiosis (microbial imbalance). Over time, this can lead to increased gut permeability, inflammation, and poor immune resilience—again, significant concerns for anyone dealing with cancer or chronic illness.
Why It Matters During Cancer Treatment, Recovery, and Prevention
The microbiome isn’t just a digestive aid, it’s a critical part of your immune system, inflammation regulation, and even hormone metabolism. When food reactions go undiagnosed, they quietly erode gut health, burden the immune system, and interfere with healing.
Research
A 2021 review in Frontiers in Immunology found that intestinal dysbiosis contributes to chronic inflammation and worsens outcomes in cancer therapy.
Multiple studies show that eliminating trigger foods can reduce systemic inflammation and improve the efficacy of certain cancer treatments, including immunotherapy.
What You Can Do
Track Symptoms: Use a journal to log food intake and symptoms for 2–3 weeks.
Test Thoughtfully: Consider functional lab testing (e.g., IgG food sensitivity panels, microbiome testing).
Elimination Diets: Work with an integrative provider to safely remove and reintroduce potential trigger foods.
Rebuild the Gut: Incorporate gut-healing protocols—such as targeted probiotics, prebiotics, digestive enzymes, and anti-inflammatory nutrients.
Conclusion
When it comes to cancer care and survivorship, food isn’t just fuel, it’s information. If you're reacting to certain foods, your body is trying to tell you something. By identifying and addressing allergies, sensitivities, and intolerances, we can begin healing the gut, balancing the immune system, and creating an environment where health, not disease, can thrive.
#cancer#chemotherapy#immunotherapy#cancertreatment#food allergies#food sensitivities#food intolerances#microbiome#dysbiosis#inetgrativeoncology#eastwestintegrativeoncology#yourcancerguru
0 notes
Text
Beyond Traditional Detection: How Cyber Threat Intelligence Fuels Proactive Threat Hunting
In the relentless arms race of cybersecurity, merely reacting to alerts is a losing strategy. The adversaries of 2025 are too sophisticated, their methods too varied, and their attacks too rapid for organizations to rely solely on traditional, reactive security measures. Signature-based detection, while still valuable, is easily bypassed by polymorphic malware, fileless attacks, and evasive zero-day exploits. This fundamental shift necessitates a move from a reactive posture – waiting for an alarm to sound – to a proactive stance: threat hunting. This disciplined, hypothesis-driven search for unknown or undetected threats hidden within your network is the hallmark of advanced security operations, and its most potent fuel is high-fidelity Cyber Threat Intelligence (CTI).
The Limitations of Reactive Security
For decades, cybersecurity largely functioned as a reactive discipline. Firewalls blocked known bad IPs, antivirus software scanned for known malware signatures, and intrusion detection systems (IDS) flagged traffic matching predefined rules. While these layers are essential, they suffer from inherent limitations:
Known-Knowns Focus: They excel at detecting threats that have been previously identified and cataloged. New or highly customized attacks often slip through.
Signature Dependency: They rely on signatures or rules, which means they are always a step behind the attacker who can easily modify their code or behavior to evade detection.
Alert Fatigue: The sheer volume of alerts generated by traditional systems, many of which are false positives, can overwhelm security teams, leading to analyst burnout and potentially missing critical warnings.
Passive Defense: They wait for an event to occur before reacting, allowing attackers valuable dwell time within a network – time during which they can escalate privileges, move laterally, and exfiltrate data. The average dwell time for attackers can still be over 200 days for organizations with less mature CTI programs, highlighting the need for proactive measures.
This reactive model creates a critical blind spot for stealthy adversaries who employ advanced Tactics, Techniques, and Procedures (TTPs) to evade initial detection and maintain a persistent presence.
Defining Proactive Threat Hunting
Proactive threat hunting is the active, iterative search through networks, endpoints, and logs to detect and isolate advanced threats that have bypassed existing security controls and remain undetected. Unlike traditional security operations that respond to alerts, threat hunting assumes a breach or a persistent presence and actively seeks out anomalies that could indicate malicious activity.
Key characteristics of threat hunting include:
Hypothesis-Driven: Threat hunters start with a hypothesis (e.g., "An adversary group known for exploiting VPN vulnerabilities might be attempting to gain access to our network in this region").
Iterative Process: It's not a one-time scan but a continuous cycle of hypothesis generation, data collection, analysis, and refinement.
Human-Led, Technology-Augmented: While leveraging advanced tools, the critical thinking, intuition, and contextual understanding of human analysts are central to successful hunting.
Focus on Anomalies: Instead of looking for known bad signatures, hunters search for deviations from normal behavior, no matter how subtle.
The Role of Cyber Threat Intelligence in Empowering Threat Hunters
Cyber Threat Intelligence is the indispensable backbone of effective threat hunting. It provides the knowledge, context, and foresight that transforms a blind search into a focused, impactful mission. Without CTI, threat hunting would be a needle-in-a-haystack endeavor, almost impossible to scale and generalize.
Here's how Cyber Threat Intelligence fuels proactive threat hunting:
1. Contextualizing Threats: The "Who, What, How, When, Why"
CTI moves beyond raw indicators (like a suspicious IP address) to provide critical context about the threat. This allows threat hunters to understand:
Who: Which specific threat actors (nation-state, cybercriminal, hacktivist) are likely to target the organization or industry.
What: Their typical motivations, objectives, and desired outcomes (e.g., data theft, disruption, financial gain).
How: Their preferred TTPs – the specific steps, tools, and methodologies they use to achieve their objectives.
When: The timing of their campaigns, whether they target specific events or operate during certain hours.
Why: The strategic rationale behind their attacks, which helps in anticipating future moves.
This comprehensive understanding, often derived from a well-structured Cyber Threat Intelligence program, helps hunters prioritize their efforts and look for the right things in the right places.
2. Identifying Attack Patterns and TTPs
CTI provides detailed intelligence on adversary TTPs, which are far more durable than fleeting IoCs (Indicators of Compromise). For instance, an IP address might change, but a threat actor's preference for spear-phishing over direct exploitation, or their use of living-off-the-land binaries, tends to remain consistent.
MITRE ATT&CK Framework Integration: CTI feeds directly into frameworks like MITRE ATT&CK, allowing hunters to map observed adversary behaviors to known techniques and procedures. This structured approach provides a common language for understanding threats and developing specific hunt hypotheses.
Behavioral Indicators: Instead of looking for a specific malware hash, hunters, guided by CTI, can look for a sequence of events that indicates a specific adversary TTP, such as privilege escalation followed by lateral movement using specific protocols.
3. Prioritizing Vulnerabilities
Organizations face a deluge of new vulnerabilities (CVEs) every year. In 2025, there are thousands of reported vulnerabilities, but only a fraction are actively exploited. CTI helps prioritize remediation efforts by:
Identifying Actively Exploited Vulnerabilities: CTI indicates which vulnerabilities are currently being weaponized by threat actors relevant to an organization's industry or infrastructure. This shifts focus from "patch everything" to "patch what matters most."
Assessing Threat Actor Interest: By understanding which vulnerabilities specific threat groups (known to target the organization) are interested in, security teams can proactively patch or mitigate those specific weaknesses. This is where insights from a Cyber Threat Intelligence program prove invaluable, ensuring that scarce resources are directed to the highest-risk areas. For instance, intelligence might highlight that a particular ransomware group is actively exploiting a newly disclosed flaw in a widely used software, prompting immediate patching.
4. Enriching Alerts and Accelerating Investigations
Even with the best preventative measures, alerts will still occur. CTI enriches these alerts, transforming them from generic warnings into actionable intelligence for deeper investigation:
Contextualizing IoCs: When a security tool flags a suspicious IP address, CTI can immediately reveal if that IP is associated with a known malicious actor, a specific malware campaign, or a C2 server, providing instant context for the analyst.
Reducing False Positives: By correlating internal alerts with high-fidelity external threat intelligence, false positives can be quickly dismissed, allowing analysts to focus on genuine threats.
Guiding Investigations: CTI provides critical clues for incident responders, helping them understand the likely scope of an attack, potential lateral movement paths, and typical exfiltration methods of the identified threat actor.
5. Understanding Attacker Infrastructure
CTI extends beyond the immediate attack to reveal the broader infrastructure used by adversaries:
Command-and-Control (C2) Servers: Intelligence on C2 server IPs, domains, and communication patterns allows organizations to proactively block communications with malicious infrastructure.
Phishing and Malicious Domains: CTI identifies newly registered or suspicious domains that are likely to be used for phishing, malware delivery, or other malicious purposes, enabling pre-emptive blocking.
Tooling and Exploits: Intelligence on the specific tools, exploits, and malware families favored by adversaries allows organizations to deploy targeted detections and defensive measures.
Building a CTI-Driven Threat Hunting Program
Implementing a successful CTI-driven threat hunting program requires a combination of technology, talent, and process:
Tools and Technologies:
Security Information and Event Management (SIEM): For centralized log aggregation and initial correlation.
Endpoint Detection and Response (EDR): For deep visibility into endpoint activity and behavioral analysis.
Security Orchestration, Automation, and Response (SOAR): For automating data enrichment, playbook execution, and response actions.
Dedicated Threat Intelligence Platforms (TIPs): For aggregating, normalizing, enriching, and disseminating CTI from multiple sources.
Network Detection and Response (NDR): For deep packet inspection and network anomaly detection.
Required Skillsets for Threat Hunters:
Analytical Prowess: The ability to connect disparate pieces of information and form logical hypotheses.
Investigative Mindset: A natural curiosity and persistence in digging for anomalies.
Domain Expertise: Deep understanding of network protocols, operating systems, applications, and attacker methodologies.
Scripting/Coding Skills: Proficiency in languages like Python for data manipulation and automation.
Knowledge of Adversary TTPs: Familiarity with frameworks like MITRE ATT&CK.
Establishing Repeatable Hunting Playbooks: Develop structured playbooks for common hunt hypotheses, outlining data sources, tools to use, and steps for analysis. This ensures consistency and efficiency.
Integrating Threat Hunting Findings: Critically, the discoveries from threat hunting must feed back into the overall Cyber Threat Intelligence program. This includes updating internal intelligence, refining detection rules, strengthening preventative controls, and sharing relevant findings with external partners. This continuous feedback loop improves the entire security posture.
Success Stories and Benefits
Organizations that have successfully integrated CTI into their threat hunting efforts have reported significant benefits:
Reduced Dwell Time: Drastically shortening the time attackers remain undetected in the network, minimizing potential damage.
Proactive Breach Prevention: Identifying and neutralizing threats before they escalate into full-blown breaches.
Improved Security Posture: Uncovering vulnerabilities and misconfigurations that traditional scans miss, leading to a stronger overall defense.
Enhanced Incident Response: Providing responders with immediate context and actionable insights, enabling faster and more effective containment and eradication.
Optimized Security Tooling: Ensuring that security investments are truly effective against the most relevant threats.
In conclusion, the shift from reactive to proactive cybersecurity, driven by rigorous threat hunting, is essential for survival in the 2025 threat landscape. At the heart of this transformation lies Cyber Threat Intelligence, providing the context, foresight, and actionable insights that empower security teams to actively seek out and neutralize threats before they can cause significant harm. For organizations looking to understand the foundational elements that enable such advanced defensive strategies, a deep dive into what threat intelligence truly entails is an indispensable first step.
1 note
·
View note
Text
Why Software Testing is Critical in Healthcare Applications

In an era where digital transformation is redefining every industry, the healthcare industry stands at the forefront of technological innovation. From electronic health records (EHRs) and telemedicine to advanced medical devices and healthcare data analytics, software plays a pivotal role in delivering safe, effective, and timely medical care. However, the complexity and sensitivity of healthcare systems make them highly vulnerable to software glitches, which can result in life-threatening consequences. That’s why software testing is not just important—it’s absolutely critical in the development and deployment of healthcare applications.
The High Stakes of Healthcare Software
Unlike other industries, mistakes in healthcare software aren’t just inconvenient—they can be catastrophic. An undetected bug in a medical device or healthcare analytics platform could lead to incorrect diagnoses, delayed treatments, or even patient fatalities. This is especially crucial for medical device testing, where devices such as infusion pumps, pacemakers, and diagnostic imaging systems rely heavily on embedded software.
Every software release in healthcare must meet stringent regulatory standards, such as those from the FDA (U.S.), EMA (Europe), or ISO 13485. Testing isn’t just about functionality; it also ensures compliance, performance, security, and most importantly, patient safety.
Ensuring Accuracy with Software Testing
Accuracy is the cornerstone of any healthcare application. Whether it's processing patient data, generating diagnostic reports, or delivering remote consultations, even the smallest miscalculation or error can cascade into larger issues.
Through rigorous software testing, developers can identify and rectify issues at every stage of the software development lifecycle (SDLC). Functional testing ensures that features work as intended; integration testing verifies that systems interact seamlessly; and regression testing ensures that updates or patches don’t introduce new issues. These practices are essential for safeguarding the reliability and accuracy of healthcare systems.
Medical Device Testing: A Specialized Discipline
Medical device testing goes beyond traditional software validation. It involves a comprehensive examination of how hardware and software work together under various real-world conditions. Regulatory authorities often require validation protocols to demonstrate that a device performs reliably across all intended uses.
Key aspects of medical device testing include:
Verification and validation (V&V) of embedded software
Simulations and stress tests to evaluate performance under peak usage
Risk analysis and usability testing, to identify and mitigate potential failures
Interoperability testing with other devices and hospital systems
In short, medical device software must go through exhaustive testing before hitting the market, ensuring safety and efficacy for patients.
The Role of Testing in Healthcare Data Analytics
The advent of healthcare data analytics and healthcare analytics tools has revolutionized how medical decisions are made. These tools analyze vast amounts of structured and unstructured data to uncover insights that aid diagnosis, treatment, and operational efficiency. However such powerful tools are only as good as the accuracy and integrity of the software behind them.
Without rigorous software testing, healthcare analytics platforms could produce skewed results, leading to poor clinical decisions. Testing ensures:
Data integrity and accuracy: Verifying that data is correctly imported, processed, and reported
Security and privacy: Especially critical in protecting sensitive patient data (e.g., under HIPAA regulations)
Performance and scalability: Ensuring that platforms can handle large volumes of data without degradation
Predictive accuracy: Validating that machine learning algorithms or AI models function as intended
Addressing Security and Compliance Challenges
With cyberattacks on the rise, especially targeting the healthcare industry, robust security testing has become indispensable. A single breach can compromise thousands of patient records, leading to financial losses and irreparable reputational damage.
Software testing helps address these concerns by:
Identifying and fixing vulnerabilities through penetration testing and code reviews
Ensuring encryption and access controls are properly implemented
Confirming compliance with healthcare regulations such as HIPAA, GDPR, and HITECH
Agile and Automated Testing for Faster Delivery
The healthcare industry is under pressure to innovate rapidly, especially in times of global health crises. To balance speed with safety, many organizations are adopting agile methodologies and test automation.
Automated testing enables continuous integration and delivery (CI/CD), allowing healthcare providers to roll out updates quickly without compromising quality. It also frees up manual testers to focus on exploratory and high-risk testing areas, such as user interfaces or clinical workflows.
Conclusion
In the healthcare industry, where software reliability can mean the difference between life and death, software testing is not optional—it is essential. Whether it’s medical device testing, EHR systems, or healthcare data analytics, comprehensive testing safeguards patient safety, ensures compliance, and builds trust in digital health technologies. As the landscape of healthcare continues to evolve, driven by data and digital platforms, organizations must prioritize robust testing strategies to deliver effective, secure, and high-quality solutions. The cost of overlooking testing is far greater than the investment required to do it right.
#medical device testing#healthcare data analytics#test automation#healthcare analytics#Verification and validation
0 notes
Text
Why Developers Should Care About UAT: Building User-Loved Software

As developers, we often obsess over code quality, performance, and scalability. But what about the human side of software? User Acceptance Testing (UAT) bridges the gap between technical perfection and real-world usability. At Keploy, we’ve seen firsthand how integrating UAT into your workflow can save time, reduce post-launch headaches, and create products users genuinely love. Let’s dive into why UAT matters and how to do it right.
What Exactly is UAT? (It’s Not Just QA’s Problem)
UAT is the final phase where real users validate your software in scenarios mirroring production environments. Unlike functional testing (which checks if features work), UAT answers how well they meet business goals and user needs
Example: Imagine building a payment gateway. Your unit tests confirm the transaction process correctly, but UAT reveals that users struggle with unclear error messages during failed payments. That’s UAT in action: catching what code alone can’t
Why Developers Should Care:
Avoid “Works on My Machine” Syndrome: UAT uncovers environment-specific bugs, like integration hiccups or data mismatches.
User-Centric Code: Feedback from UAT helps prioritize features users actually need, not just what’s technically impressive.
Reduce Post-Launch Firefighting: Fixing bugs post-release costs 100x more than during UAT
UAT Best Practices for Developers
A. Automate the Tedious, Focus on the Human
While UAT is user-driven, automation handles repetitive tasks. Keploy’s AI-powered tools, for example, auto-generate test cases from API calls and user flows, freeing testers to focus on exploratory testing
Pro Tip: You can use Keploy to:
Capture real-user interactions as test cases.
Mock dependencies (e.g., third-party APIs) for isolated testing.
Automate regression testing to ensure fixes don’t break existing workflows.
B. Involve Users Early
Waiting until the end for UAT is a recipe for disaster. Instead:
Sprint Reviews: Demo features to stakeholders early.
Beta Testing: Release to a small user group mid-cycle.
Feedback Loops: Integrate tools like Keploy Explorer to let users annotate bugs directly on screenshots.
C. Mirror Production, Minus the Stress
A UAT environment that mismatches production? That’s like testing a race car on a bicycle track. Ensure:
Data Realism: Use anonymized production data or synthetic datasets that mimic real usage.
Infrastructure Parity: Replicate servers, APIs, and network conditions. Keploy’s sandbox environments make this seamless.
Common UAT Pitfalls
Pitfall
Solution
Users Don’t Have Time
Automate test setup: Keploy auto-generates test data and pre-populates environments.
Vague Feedback
Use session replays to see user actions and debug in context.
Regression Nightmares
Auto-capture every user flow as a test case for instant regression suites.
Real-World Example:
A rapidly scaling fintech startup struggled with long UAT cycles and undetected post-launch issues. Their manual testing process led to delays, and even after multiple test cycles, critical bugs slipped into production.
By integrating Keploy, they automated 70% of their UAT test cases, reducing testing time by 40% and cutting post-launch bugs by a staggering 90%. This not only accelerated feature releases but also improved customer trust by minimizing service disruptions.
UAT ≠ The Finish Line: Iterate Like a Pro
UAT isn’t a one-time checkbox. With CI/CD pipelines, treat UAT as a continuous feedback loop:
Automate Acceptance Criteria: Use Keploy to convert user stories into auto-validated tests.
Monitor Post-Launch: Track real-user behavior with Keploy’s analytics to spot undiscovered edge cases.
Retrospectives: Collaborate with testers to refine UAT processes—e.g., which test cases to automate next.
How to do User Acceptance Testing (UAT)?
A step-by-step guide to executing UAT like a pro:
Phase 1: Plan
Define Scope: Align with stakeholders on what to test (e.g., critical user journeys).
Recruit Testers: Involve real end-users, not just QA teams.
Phase 2: Design Test Cases
User-Centric Scenarios: Create tests mimicking real-world workflows (e.g., “Checkout as a first-time user”).
Automate Repetitive Tasks: Use Keploy to auto-generate test cases from API calls, user sessions, or production traffic.
Phase 3: Set Up the UAT Environment
Mirror Production: Replicate servers, databases, and third-party integrations
Phase 4: Execute & Monitor
Let Users Explore: Encourage testers to go off-script to uncover edge cases.
Capture Feedback: Use session replays (Keploy’s Explorer tool) to see exactly where users struggle.
Phase 5: Iterate & Sign-Off
Prioritize Fixes: Address showstopper bugs first.
Automate Regression: Convert UAT scenarios into automated tests
Challenges of User Acceptance Testing (UAT)
A. Users Don’t Have Time
Solution: Automate test setup. Keploy pre-populates test data, letting users focus on validation.
B. Unclear Requirements
Solution: Derive test cases from actual user behavior. Keploy records real-user interactions to build data-driven tests.
C. Environment Mismatches
Solution: Use Keploy’s dependency mocking to simulate APIs/Services, avoiding “works in staging, breaks in UAT” issues.
Top User Acceptance Testing Tools

TestRail
Key Features: Test case management, real-time analytics, integration with Jira, and CI/CD tools.
Website: https://www.gurock.com/testrail/
UserTesting
Key Features: Real user feedback, session recordings, analytics, usability testing.
Website: https://www.usertesting.com/
Testpad
Key Features: Exploratory and scripted testing, simple checklist-based UI, collaborative testing.
Website: https://www.testpad.com/
qTest (Tricentis)
Key Features: Agile test management, Jira integration, automated & manual test tracking.
Website: https://www.tricentis.com/products/qtest/
PractiTest
Key Features: End-to-end test management, custom dashboards, integration with Jira, and Selenium.
Website: https://www.practitest.com/
Conclusion
User Acceptance Testing isn’t just a phase—it’s a mindset. It ensures your software is not only functional but truly usable by real people in real-world scenarios. By integrating UAT into your workflow with the right tools (like Keploy), you can catch usability issues early, reduce post-launch surprises, and deliver products users genuinely love.
FAQ
How is UAT different from functional testing?
Functional testing ensures that individual features work as expected, while UAT validates whether the software meets business goals and user expectations in real-world scenarios.
Who should be involved in UAT?
UAT should involve real end-users, business stakeholders, product managers, and developers—not just QA teams. Their feedback helps bridge the gap between technical functionality and real-world usability.
Can UAT be automated?
While UAT is user-driven, automation can handle repetitive tasks like data setup, regression testing, and environment replication. Tools like Keploy automate test case generation, dependency mocking, and session replay analysis to streamline UAT.
How do I ensure UAT mirrors production?
Use anonymized production data or realistic synthetic datasets.
Replicate servers, APIs, and network conditions as closely as possible.
Mock dependencies using tools like Keploy to avoid integration failures.
How do I encourage users to participate in UAT?
Automate setup so testers can focus on validation, not environment issues.
Offer incentives for participation, such as access to beta features.
Make feedback easy—use tools like Keploy Explorer for testers to annotate bugs visually.
0 notes
Text
1010 Headcanons: Bootlegs
There are no official public documents about the design and inner workings of a 1010, but nonetheless many imitators and bootlegs have popped up in Vinyl City over the several years of 1010 being an active group.
A Brief History
Bootleg 1010s have been around since even MKI, but they were generally constructed by enthusiasts and hobbyists that were more interested in having personal 1010s than trying to make a profit.
MKI was very easily “bootlegged” due to them being based on the just recently retired battlebots. Strictly speaking, most imitation MKIs are not “bootlegs” but simply use the same battlebot base that 1010 uses. Some “true” bootlegs of MKI do exist, but they’re very rare due to not being in high demand and also competing with war paraphernalia collectors who want to have their battlebots in their original condition.
MKII bootlegs are a little less common as the design is original and the 1010 molds/factories are strictly “in-house”. However, dedicated fans have been able to recreate their look using public images as a guide. None have ever been 1 to 1, but due to the popularity of this series, bootleg MKIIs are still in demand.
MKIII, similar to MKII does not have any public documents or outside factories, so they did not have any convincing duplicates during the early years of the series. However, since the B2J incident, this has become the most bootlegged series to date.
Note: The weaponry of a 1010 has also been a point of interest for some, but due to the danger and high illegality associated in handling those parts, most are content to focus on recreating just their civilian forms without the added weaponry.
Garage Band 1010s
Many MKIII 1010s were scrapped and subsequently disposed of after their encounter with B2J. This made it very easy for fans to gather the parts needed to recreate a full MKIII 1010. Since then, and with the rampant rise of file sharing, fans have released documents detailing a full build of a basic 1010 (including each member’s face plate). This has allowed anyone with the materials and know-how to build their own 1010.
Since the released files are public, some people have taken to making and selling “1010 Kits,” so even those without direct access to materials can make their own 1010 given that they can afford the kit and have the materials to put them together. This combined with the ease of making modifications to a kit has caused a subculture to form around “garage band 1010s,” aka “GB 1010s.” Members of this subculture aren’t as interested in recreating 1010 as they are but are instead focusing on making their own designs and modifications to the base 1010.
Popular mods include:
Uniform redesigns and new hairstyles
Color changes (pink and teal are especially popular)
Face modifications
New tuning to expand their sound range and make them suitable for more genres of music
However, some full body modification GB 1010s are out there and are completely distinct from the original base. Some fans have commented that modifying 1010s has been their gateway to an interest in robotics.
Despite having access to the parts, there has yet to be a true recreation of the 1010 A.I. The difficulty in obtaining this information mostly lies in the fact that a 1010′s A.I. will self-destruct if it detects that it has been out of range of Barraca Mansion for a certain amount of time. As of now, no one has been able to completely preserve the A.I. after reactivating it and it subsequently self-destructing, though some bits and pieces have been saved from the handful of attempts at this task.
What has been preserved has also been worked into a popular homebrew A.I. called “Jayjay.” It can be loaded into a GB 1010 (or any robot capable of running the program) to grant basic singing and dancing capabilities and limited interaction. This program is still in its early stages, but many community members are working together to refine the A.I. and make it both accurate to the original 1010s but also easy to modify. Currently, the main focus of the Jayjay team is recreating the 1010′s “Personality System” as all current iterations of the program have the same personality to keep them from bugging out when attempting to run more complex functions. Since the program is open source, members outside the team have attempted making modifications to this system with varying results.
NSR’s Response
NSR is very quick to crackdown on any factories attempting to sell and create bootleg 1010s, especially if they’re loaded with weaponry. Part of the Metro Division’s budget has gone into making PSAs detailing the differences between official and bootleg 1010s to keep fans from being swindled by those holding false concerts or other fake events. Since bootlegs became especially bad during the MKIII era, 1010 has lost some footing in the Metro Division as the top charter, but they have managed to stay at number 1 despite these difficulties.
GB 1010s however fall into a legal gray area. NSR has not officially acknowledged GB 1010s, but they generally turn a blind eye to hobbyists as long as the GB 1010 in question is distinct from any already existing member and also makes it clear that they are in no way officially affiliated with NSR. Aside from a handful of incidents where someone has tried to pass off a GB 1010 as the real thing, NSR generally leaves them alone. However, some GB 1010s have gained pretty big followings of their own, and there have been talks among the community about what may happen if a GB 1010 were to ever become a serious competitor with the real 1010.
#nsr#no straight roads#1010 headcanons#1010#whoops my special interests are showing#i've thought a lot about the concept of a bootleg 1010#originally it was just kinda of an inside joke#that the reason it's so easy for 1010 to sneak around the city#and why e.g. is generally undetected#is because there are so many bootlegs running around that they really don't turn heads if they look even slightly off#but i decided to think about how else that would change the culture in vinyl city#i probably could have gone a bit deeper#but i think this will be fun to roll with#it's been a while since i've written one of these#if i had a gb 1010 you know it'd be pink#maybe add some lace and bejewel it#y'all ever seen that really girly gundam mod?#the pink one with the garterbelt and jewels?#that's basically what i'm imagining#if you haven't seen it#check the gundam tag on my main blog#i'm sure it's in there somewhere
34 notes
·
View notes
Text
i will admit that part of this is probably nostalgia goggles. but i also must say that i think the fashion on h2o far surpasses that of mako mermaids, both in how distinctive and how memorable the various looks are. for the most part each of the h2o merms has their own personal taste in fashion, with recurring theme colours and styles. there is definitely some overlap, but emma likes to look sporty and practical, cleo boho and romantic, rikki edgy and cool. if either were to swap looks for a day the change would be obvious
the mako merms have nothing but overlap when it comes to their style. there's little consistency in individual tastes, nor much to distinguish each mermaid from the other. the fashion is generic and interchangeable, usually either sundresses or shorts and a t-shirt. they look pretty and polished, sure, but not very real. you'd think that the costume team would put a little more effort into injecting the girls's personalities into their looks, but for the most part the fashion is pretty bland
#i will say sirena and mimmi respectively have some killer sundresses. and mimmi rocks some 50s and 70s inspired looks. but nothing about#either of their personal styles makes me go 'oh that's so sirena' or 'oh only mimmi could pull that off' iygm#if i ask you which of the h2o girls would be most likely to wear a long paisley print skirt you probably know who i'm talking about. but if#i were to show you a generic floral sundress or some shorts and printed top it could work for literally any of them. carly and evie include#and like. evie works in a boutique! you'd reckon the costume designers would make her look a bit more distinctive but no#this is true of the boys as well actually now that i think of it. lewis is all about his fishermen's hats and old man shirts and cargo#shorts. zane likes to look a bit more edgy like rikki in the black and red. ash is a bit meh on the fashion front but ash is meh in general#but if you look at zac or cam or david or erik or the other guy. there's nothing to distinguish one from the other in terms of fashion#like surely david could be a bit more business casual as the owner (lol) of the cafe? zac could be relaxed surfer guy cool with his gaff by#the sea? cam could wear flashy watches and crisp colours to show that he's a bit arrogant? erik does wear the odd polo shirt in fairness#which proves that he's a dickhead. because only dickheads wear polo shirts. but maybe he never wears anything too bright or flashy or his#clothes aren't perfect because he has to move from place to place undetected#anyway before anyone says 'well they're mermaids why would they care about clothes' the show does go out of its way to tell us that they ar#girls and as such must care about fashion. like getting ready for parties together or sirena stressing about what to wear to sing at the#cafe with david. like it's totally a thing even moreso than in h2o#but if anyone has a rebuttal for this e.g this character wears this colour a lot this character has this style do chime in the replies#because it's honestly not something i've ever noticed#mako mermaids#h2o just add water#h2o: just add water#h2o#.txt#queue
64 notes
·
View notes
Note
Oooh, you like Trigun! Do 3, 9, 12, and 25.
3. screenshot or description of the worst take you’ve seen on tumblr
On tumblr specifically? Um... every single one that insists that either of the twins having any kind of incestuous obsession with each other (usually on Knives' end) is the correct reading of the story and that anyone who disagrees is willfully misinterpreting the source material. I don't go into the main tags anymore. -_-
-
9. worst part of canon
Nightow's tendency to under-explain his worldbuilding or just toss in elements that make no sense just because he thinks it's cool. Some amount of mystery is fine, but there comes a point where it just becomes frustrating. Take, for example, the canon explanation for Legato's powers in the manga, e.g. that he can just randomly control people with tiny, undetectable metal threads implanted in their muscles. Like no, I'm sorry, Mr. Nightow, that explanation is the stupidest thing I've ever heard and I am throwing it in the garbage. I've come up with my own explanations for all the the weird, unexplained abilities random characters in Trigun have to make my brain hurt less, but I shouldn't HAVE to. And this is just one example.
-
12. the unpopular character that you actually like and why more people should like them
I... hm. You know, I can't really think of a super underrated Trigun character, come to think of it. The fandom is generally pretty good at giving characters that deserve it love. I guess I could say that Marlon is kind of underrated, given the fact that he only shows up in 1 episode of the old anime and only makes sporadic appearances in the manga, but he's cool, I like him.
-
25. common fandom complaint that you’re sick of hearing
"StAmPedE's AnIMAtioN iS So BaD, iT loOKs TerriBle-"
#ask meme#trigun#novelmonger#I do indeed like Trigun thanks for noticing lol :p#i may also have Thoughts and Opinions
9 notes
·
View notes
Text
By: Eddie Waldrep, PhD, MSCP
Published: May 15, 2023
This is a guest post by Edward E. Waldrep, Ph.D, M.S.C.P. Dr. Waldrep is a Veteran of the War in Iraq, Purple Heart recipient, and is currently a clinical psychologist for the Department of Veteran Affairs specializing in PTSD. Views expressed here are those of the author and are not the views of the Department of Veteran Affairs.
Our country, and indeed the world, has gone through a lot in the past couple of years. The COVID-19 pandemic, the murder of George Floyd by a police officer, a racial reckoning, rioting, and a tumultuous transition of presidential power that has marred our democratic institutions to name a few. With so much going on, the radical political changes within the American Psychological Association (APA) may have easily escaped the attention of many.
For example, the APA has been gradually changing the way race is approached. Officially, in 2017 it updated standards on multiculturalism to include embracing “intersectionality,” a conceptualization of the myriad ways in which one is oppressed via group identity. In 2019, a Task Force on Race and Ethnicity Guidelines in Psychology noted drawing upon Critical Race Theory (CRT) as a guide and in 2020 the definition of racism promoted by the APA was officially changed. The redefinition changed it from internal prejudicial beliefs and interpersonal discrimination to a “system of structuring opportunity.” What led to this change and why does it matter so much?
Social Justice versus Critical Social Justice
These changes came as a result of the changing focus of APA, and academia in general, from traditional social justice movements to Critical Social Justice (CSJ). Traditional social justice sought to end institutional oppression, discrimination based on immutable characteristics, focus on universal humanity of every individual, and for equality of opportunity for each to pursue their own self-directed goals. These are indicative of aspirational goals found in Dr. Martin Luther King, Jr.’s “I have a dream” speech. There are contemporary organizations promoting the same pro-human ideals such as the Foundation Against Intolerance and Racism (FAIR) and many others. On the other hand, there is CSJ that has skyrocketed in the public sphere in recent years and is much more pernicious.
The boom of CSJ is not a mere phenomenon. It is the result of decades of planning referred to as “the long march through the institutions,” a neo-Marxist approach to establish the conditions for revolution. This built upon the work of Italian Marxist, Antonio Gramsci who developed the concept of “cultural hegemony.” Cultural hegemony was posited as an explanation for why the grand Marxist revolution and utopia had failed to manifest itself. Basically, if people were able to have a comfortable life in a free market society, then they lack the motivation to burn down western society to make way for the grand utopia.
Critical Critical Theory Theory
The hegemony is thought of as an invisible, largely undetectable, ubiquitous force that nobody intentionally directs but by which all are influenced. This is where the “fish in water” analogy stems from the that is commonly used to explain “white privilege.” In their book, Black Eye for America, Swain and Schorr (2021) note that the strategy to bring about communism is to dismantle or undermine western society by attacking five societal components that maintain the hegemonic “oppression”: educational establishments, media, the legal system, religion, and the family. Douglas Murray also noted this attack in his recent book, The War on the West.
CRT is just one iteration of the application of Critical Theory(1) to different aspects of society (e.g., race, gender, sexuality, queer, colonialism, etc.) and often is presented as diversity, equity, and inclusion. CRT and intersectionality have been encouraged to be adopted in cultural competencytraining and stem from the same origin. Intersectionality, applied socially, is designed to get people to think of how they are constantly oppressed, in any variety of ways, in any given situation, to promote social divisiveness. The concept of intersectionality was popularized by Marxist lawyer and key developer of CRT, Kimberle Crenshaw. In her 1991 article for the Stanford Law Review, she argues that universal humanity ought to be rejected and focusing on race should be retained and be used for political power.
This is the exact opposite of Dr. King’s approach. She makes the distinction between “I am black” vs. “I am a person who happens to be black”. She is critical of the latter and states, “’I am a person who happens to be black,’ on the other hand achieves self-identification by straining for a certain universality (in effect, “I am first a person”) and for concomitant dismissal of the imposed category (“Black”) as contingent, circumstantial, nondeterminant” (pg. 1297). Hence, the CRT focus on “centering race” to achieve ideological and political goals associated with imposing Marxist ideology to “dismantle” western norms and practices centering individual human rights and liberties.
The Modern Echoes of the Ugly History of Collectivist Ideologies
This ideology has a horrendous track record for humanity. Simply relabeling the ideology does not change that fact. American Psychologist, the “flagship publication” of the APA, went so far as to dedicate an entire special issue promoting this ideology in 2021. The edition editors criticize the field of psychology for “failing” to focus on structural power dynamics and for not creating “lasting social change” (Eaton, Grzanka, Schlehofer, & Silka, 2021). These are references to postmodern philosophy, Marxist structural determinism and social engineering. The authors go on to state “articles in this special issue build the case for a public psychology that is more disruptive and challenging than simply aiming dominant, canonical, and mainstream psychological research and practice outward” (pg. 1211).
Flynn and colleagues, 2021, discuss civil disobedience and criticize nonviolence as the only acceptable form stating, “we encourage psychologists to think critically about the effects of privileging certain acts of civil disobedience over others on the basis of decontextualized tactics alone, such as the assertion that property destruction invariably denotes a protest tactic outside the bounds of civil disobedience” (pg. 1220). They go on to describe strategies to twist and manipulate APA Ethics to justify any means they appear to see fit to dismantle “systems of oppression”. For example, regarding Principle C: Integrity, they state, “we also read it as authorizing clandestine methods of civil disobedience to contest injustice (e.g., deception, evasion) when methods maximize benefits and minimize harm” (pg. 1224). This stretches the intent of the use of deception from research methods, a researcher pretending to be a student for example, to justifying outright dishonesty.
And of course, the special issue would not be complete without an article criticizing “good” psychology. Note, the use of “Critical” in this context is related to neo-Marxist “Critical Theory” and not critical thinking. Grzanka and Cole, 2021, make an argument for what they describe as “bad psychology”. They argue that “good psychology” (maintaining rigorous methodological, scientific, and objective standards) is a problem because it gets in the way of the radical political agenda of transforming society the way that they think is best. They state, “we contend that what is commonly thought of as ‘good’ psychology often gets in the way of transformative, socially engaged psychology. The radical, democratic ideals inspired by the social movements of the 20th century have found a voice in the loose network of practices that go by the term critical psychology and includes liberation psychology, African American psychology, feminist psychology, LGBTQ psychology, and intersectionality” (pg. 1335).
The authors do, conveniently, leave out the fact that the ideology underlying the radical social movements of the 20th century are attributed with mass murder on an unimaginable scale. Throughout the special edition, the argument is made, consistently, that this ideology, advocacy, and radical social transformation should be incorporated through all aspects of psychology: research, training, and delivery of clinical services.
How could the American people continue to trust the organization if this ideology is being actively promoted? What would psychotherapy look like within this ideological framework? I would argue that society would not and should not continue to trust APA if this continues. This is not sound, competent, professional, empirically informed psychology. This is Psychological Lysenkoism.
Critical Theory Ideas are Bad Psychology
APA has allowed, even endorsed, the miscommunication of psychological science that has the potential to negatively affect the mental health of individuals and society overall. Concepts such as implicit bias and microaggressions have questionable validity yet are so prominently displayed that they have the effect of gaslighting society. The net effect is to have people wondering if every interpersonal interaction is racist or bigoted and second guessing each encounter for intent and impact. These are reflective of the precepts and goals of CRT itself. The implicit idea is that almost everything is or can be racist is a central tenet of the ideology. From there, the goal is to then create the critical consciousness necessary to give rise to social unrest and revolution. The first paragraph of the intro to CRT, written for high school students, sets itself aside from traditional civil rights, and “questions” equality theory, Enlightenment rationalism, and neutral principles of constitutional law. Delgado and Stefancic (2017) state, “Unlike traditional civil rights discourse, which stresses incrementalism and step-by-step progress, critical race theory questions the very foundations of the liberal order, including equality theory, legal reasoning, Enlightenment rationalism, and neutral principles of constitutional law” (pg. 3).
An additional tenet is that the voices and “lived experiences” of marginalized groups ought to be accepted unquestioned. However, the hypocrisy of the framework is laid bare when the “voices of color” dissent from the prevailing narrative. Prominent examples are those of John McWhorter, Glenn Loury, Wilfred Reilly, Roland Fryer, Ayaan Hirsi Ali, Darryl Davis, Jason Hill, Coleman Hughes, Eric Smith, Ian Rowe, Thomas Sowell, and the list goes on and on. The same dissociation occurs with members of various marginalized communities when anyone of that community doesn’t toe to line with the ideological framework. The individual does not matter, only the prevailing ideological narrative and political agenda. Anything, or anybody, that interferes with that agenda is inherently loathsome. The most common response to any individual expressing skepticism or dissent is to label the individual (any applicable variation of -ist or -phobic) and should not even be allowed to have a voice!
APA Should Adopt a Pro-Human (All Humans) Orientation
In psychological practice, we should focus on the individual with inherent dignity, value, and careful consideration of how factors influence the individual. APA ought to return to a pro-human orientation. The “critical” movement denies the individual and views them as simply a representative of a superimposed group identity or combination of identities. This is antithetical to our field. The adoption of radical political ideology has even led to the resignation of at least one leadership role in protest. When we focus on our universal humanity, we can celebrate our differences. If not rejected as morally abhorrent as it is, then the American people would rightly lose trust in the organization and damage trust in our profession.
--
(1) “Critical Theories” (Critical Race Theory, most varieties of postmodernism, fat studies, etc.) have taken that name because they endorse deep skepticism of liberal democratic norms and practices that pervade … liberal democratic societies. I (this is Lee writing here) sometimes have a bit of fun with this by referring to critiques of Critical Theories as Critical Critical Theory Theories — i.e., turning the lens of critique that includes revelations of implicit, empirically flawed or moral dubious claims & assumptions back on Critical Theories themselves, as Ed Waldrep has done here with respect to APA.
#Eddie Waldrep#critical theory#critical race theory#cultural marxism#neo marxism#queer theory#postcolonial theory#lived experience#intersectionality#woke#wokeism#cult of woke#wokeness as religion#wokeness#psychology#human psychology#institutional capture#religion is a mental illness
11 notes
·
View notes
Text
Greetings!
I have to share bad news with you. Approximately a few months ago, I gained access to your devices, which you use for internet browsing. After that, I have started tracking your internet activities.
Here is the sequence of events:
Some time ago, I purchased access to email accounts from hackers (nowadays, it is quite simple to buy it online). I have easily managed to log in to your email account @gmail.com.
One week later, I have already installed the Cobalt Strike "Beacon" on the Operating Systems of all the devices you use to access your email. It was not hard at all (since you were following the links from your inbox emails). All ingenious is simple. :).
This software provides me with access to all your devices controllers (e.g., your microphone, video camera, and keyboard). I have downloaded all your information, data, photos, videos, documents, files, web browsing history to my servers. I have access to all your messengers, social networks, emails, chat history, and contacts list.
My virus continuously refreshes the signatures (it is driver-based) and hence remains invisible for antivirus software. Likewise, I guess by now you understand why I have stayed undetected until this letter.
While gathering information about you, i have discovered that you are a big fan of adult websites. You love visiting porn websites and watching exciting videos while enduring an enormous amount of pleasure. Well, i have managed to record a number of your dirty scenes and montaged a few videos, which show how you masturbate and reach orgasms.
If you have doubts, I can make a few clicks of my mouse, and all your videos will be shared with your friends, colleagues, and relatives. Considering the specificity of the videos you like to watch (you perfectly know what I mean), it will cause a real catastrophe for you.
I also have no issue at all with making them available for public access (leaked and exposed all data). General Data Protection Regulation (GDPR): Under the rules of the law, you face a heavy fine or arrest. I guess you don't want that to happen.
Let's settle it this way:
You transfer 1.1 Bitcoin to me and once the transfer is received, I will delete all this dirty stuff right away. After that, we will forget about each other. I also promise to deactivate and delete all the harmful software from your devices. Trust me. I keep my word.
That is a fair deal, and the price is relatively low, considering that I have been checking out your profile and traffic for some time by now. If you don't know how to purchase and transfer Bitcoin - you can use any modern search engine.
You need to send that amount here Bitcoin wallet:
(The price is not negotiable). You have 5 days in order to make the payment from the moment you opened this email.
Do not try to find and destroy my virus! (All your data is already uploaded to a remote server). Do not try to contact me. Various security services will not help you; formatting a disk or destroying a device will not help either, since your data is already on a remote server.
This is an APT Hacking Group. Don't be mad at me, everyone has their own work. I will monitor your every move until I get paid. If you keep your end of the agreement, you won't hear from me ever again.
Everything will be done fairly! One more thing. Don't get caught in similar kinds of situations anymore in the future! My advice: keep changing all your passwords frequently.
6 notes
·
View notes
Text
i love the like conspiratorial feel to the opening & likewise closing numbers of gtm:pota, “goosebumps” & its reprise (ft. r.l. stine god bless us)....i love the >:3 and the playful quality and the way the song starts a bit downtempo and mezzopiano kind of Creeping Out at us. it has the sense of umm. an air of secrecy. some unauthorized activity. we are slyly having this covert meetup in a graveyard for this Song to happen. love that lmao like, those are my roots here as [little kid intrigued by / interested in / seeking out Horror at all] like, that being in the midst of kind of suspenseful conditions feels like oh yeah of course (lol...) and that Nighttime and the idea of being Up for those hours and all the more for kind of sneaking around & seeing what’s up / doing some secret shit oneself is an engaging enticing concept (lol....lived that dream to be sure, at later ages & nowadays) and wherein more generally it’s liiiike. new paragraph
i always enjoyed horror ft. Mystery the most (& comedy, really) which applies to goosebumps, there’s a ton i didn’t read but so far as i know they’re all written to be funny & have an underlying mystery. and i always found like, Mysterious Characters / Suspects to be fun & fascinating themselves lol wherein it’s like, whoa who’s This suspicion arousing person, what strange thing are They up to. when like, sure, a lot of times there might be like “oh you accidentally solved some whole other mystery” approach where like, xyz other suspects Were up to something, they just weren’t up to the main thing you’re actually trying to figure out. but it was always extra delightful when it’s like, oh really this is just some guy hanging out doing his thing. why was he doing some shit at night? idk, he felt like it. an Eccentric Character, who may have even been threatening, but it’s like, nah. they’re just like that, but they’re Innocent, nonthreatening in actuality rather than “idk. vibes,” perhaps even helpful. like, e.g. cue that photoset of bailey school kids series “[supernatural entity] don’t [occupation a child may encounter]” cover illustrations and captioning it like “schoolchildren gawk at flaming homosexuals” lmfaoooo b/c that’s kind of always how it pans out. my Queer Analysis: Horror experience isn’t one where i ever cared about like monsters type deal but certainly when horror is about Thee Other it’s like, well, the queer & the neurodivergent is othered, that sure applies to me lol, plenty of times that’s just used to Cue that something’s Off about someone and they’re dangerous &/or evil, but when that’s subverted like, oh this suspicious person was just hanging out / is cool actually, then that’s kind of aspirational / relatable all the more straightforwardly like oh shit lol i just innately Vibe with that impersonable loner man they saw wandering out & about the night that some shit went down....truly, same. operating suspiciously covertly? like that’s me and the cptsd, baby, i like the vibe of The Cover Of Night, i loved the idea of a house with secret passages and you just Can move undetected, loved like the idea of tiny quiet hidden places, v cozy, loved the idea of Secret Communication, some covert underworld in which to freely operate, sneaking out at night & traveling to some destination with a coded signal inviting one over / providing direction and a light in the distance to head to lol. it all has context in retrospect lmaooo. and the invariable Queer Vibe of like ooh this person’s styling / fashion is so Weird, what’s up with them....like idk but that pwns, the “yeah hmm Why look different vs the ‘normal’ way that surely everyone just Wants to / naturally chooses to look & operate” right along the lines of the intrigue of Why be someone up to anything at night when surely one would only want to or ever even think to operate in the daytime, the normal way. i do dare follow, and am ware. what’s that shit, are you afraid of the dark? (series) i Never saw where i think the framing every time is a bunch of kids who like scary stories all go secretly gather in the woods at night & do that for fun lmao like right the hell on. my people
anyways idk that went off the rails but yeah love that song (genderdivergently) (neurononconfirmingly)
3 notes
·
View notes
Text
IZUKU’S SECRET QUIRK THEORY
Right, I have had this spinning in my head for a few weeks now and just had to put it down somewhere.
Disclaimers: This theory is reliant on:
A) Midoriya Hisashi being All for One
B) The toe joint identifier being discovered or a trait of the later generations of quirks users, i.e some first gen users possessing it, a larger amount in the 2nd, and by the 4th gen every quirk user has it.
This is where the theory begins
1) Dependant quirks
The core application of AFO & the First’s quirks are essentially genetic manipulation through transfer, the most important part of this being the process of transfer.
However, the difference between the brothers is that AFO’s quirk is capable of two-way transfer, whereas First’s is only capable of one-way. This difference is what make’s the First’s quirk undetectable in the first place (if the toe-joint connection wasn’t known), whereas AFO (the quirk) was essentially ‘Give and Take’, First’s quirk was only ‘Give’. The problem being that he had no other quirks to give.
Presumably if both brothers are capable of possessing multiple quirks then they share the same tolerance for quirk load - they don’t receive brain damage - and this must be a secondary mutation of their quirks (e.g. Stain’s blood paralysis coming with and extendable tongue and Kouda’s ‘rock-head’ even though his quirk is talking to animals.) that would be present in their descendants.
This is where Izuku being AFO’s some becomes important. If we assume that Dad For One is true, that the toe-joint only became a global mutation in one of the later generations and that Izuku does have a hidden quirk, he would then technically be 2nd gen quirk user, so he could both posses a quirk and have the joint.
My theory on Izuku’s quirk is that it’s something I’ve dubbed ‘Arsenal’ - the power to possess and have full access to multiple quirks. Where his father could take, hold and give, and his uncle could hold and give, Izuku is only capable of holding. A quirk that cannot be activated by itself given that it requires a form of Transfer, but it would explain the following points:
2) The Point of Singularity
First’s speech to Izuku in Ch. 193

The most important part of this speech to me is the “long since passed the point of singularity”, because when you consider the time frame; Izuku has in no way posted OFA long enough to contribute an amount of energy to it that would have ‘long since passed’ the point.
So when we consider this, it was not Izuku who passed the singularity, so why does he have access to the quirks of the previous users. What makes him different?
I theorise that the quirk was always capable of granting its users the quirks of its previous users, but it was missing a key component that would have allowed it to do so. Said component being Arsenal’s ability of full access. Full access is essentially what it sounds like, upon intake of a new quirk it allows total usage of it, though not control. This would explain why Izuku was able to use 100% of OFA immediately after receiving it. The reasons I believe this are:
A) The ‘Limb Explosion’
I view the ‘limb explosion’ warning from All Might as a slight continuity error. That it does cause damage if the quirk is used in an area of the body that is already damaged (AM’s frail arms at Kamino.) but given Izuku having competed his training and it seeming like his body didn’t develope that greatly after the exam, the self-damage aspect of the quirk seems like something the writers choose to include when we’re they want.
Also consider that if OFA is powerful enough that AM with the embers of the quirk can cause a tornado with a punch, how likely is it that OFA users were capable of breaking limbs as early as the Third, and if they were, how many users had access to a healing quirk to repair the damage - I believe it is mentioned in-universe that they are rare, so it’s unlikely that they all had access to one.
I think that it’s mentioned the only way to master control of OFA is to keep using it until your body adapts to no longer breaking - that’s not how biology works. (Case in point: Izuku breaking his fingers to launch air blasts at the sports festival, however when he does this after the overhaul arc it only causes slight pain - this is because when now has access to 20% of OFA, which doesn’t make sense - unless the quirk is sentient and choosing not to Inuit it’s weilder now.)
B) Full Cowling
Full cowling is introduced as a way for Izuku to use his quirk without causing damage to himself, the continuity error here continues on from the ‘limb-explosion’.
Considering that both AM never had a problem with controlling OFA (he wasn’t breaking his bones every time) we could presume this is either due to natural aptitude or because using a larger amount of energy in the quirk takes time and training to access.
Full Cowl was something Izuku created by himself because he had problems with energy output, he wasn’t taugh it by AM. So if we presume that AM and all previous users didn’t have the same problem (they never had to develop their own versions of FC) the question once again becomes what makes Izuku different?
If he does posses a hidden quirk like ‘Arsenal’ which have him ‘full access’, this would explain it. OFA is a reservoir of energy, that is what the quirk does - it stores energy, if we assume that using the quirk is like opening a dam, you begin with a small amount of water being let through and work your way up - this is what the previous users would have to do. The began using a small amount of energy and naturally worked their way up to larger amounts.
However the problem with Izuku is that ‘Arsenal’ gave him 100% off-the-bat - the dam was opened completely, all the water came rushing out. This is what would have caused his energy control problems, because his quirk allows completely usage of any quirk he possesses, not control.
2) The Swelling of the Core
Izuku’s conversation with the 5th in Ch 213

The important part of this conversation is ‘seriously’ (and here is where I sound like an English student). The use of this word suggests surprise. That the core has suddenly (recently) begun to change and this change is what allows access to all the quirks. We as the readers can presume this change has come about due to Izuku gaining possession of the quirk.
Given that Ujiko has also mentioned signs of the Quirk Singularity being noticed as early as the 4th gen, why has no signs of the singularity been noticed by OFA users? Why have they never encountered the vestiges?
So once again, if a change has occurred within OFA in the time it’s been in Izuku’s possession, the questions are ‘Why has it changed?’, ‘What is the change?’ and ‘What make’s Izuku different?
#midoriya izuku#all for one#midoriya hisashi#midoriya hisashi is all for one#midoriya izuku’s hidden quirk#one for all#dad for one#bnha#bnha theory
55 notes
·
View notes
Text
The Visitation

For what was supposed to be the most monumental event in the history of human civilization it was actually pretty anticlimactic. No giant mothership; no shadowy figure emerging from the mist; no tense standoff with guns drawn... Hell, we never even saw him coming.
The morning of 12/12 was really just like any other, other than the fact that there he was, standing outside the White House, just waiting for us to show up. We found out later he'd actually arrived before sunrise and had been waiting out there for exactly two hours and twenty-nine minutes before anyone saw him. Not that he was trying to hide; he was just too polite to even try knocking.
If it had been some kind of crazy giant alien ship, I'm sure he wouldn't have had to wait so long. But right there next to the bushes just a few yards outside the front door to the White House was the most basic landing pod you could possibly imagine. At least we all assumed it was just a landing pod; we didn't find out until later that it was his actual ship, which he'd actually used to travel the entire 32+ light years from his home planet even though it was nothing more than a tube, barely big enough for him to fit in, with no apparent means of propulsion or external features whatsoever. And even later, when he showed us the interior, it was just completely empty; no apparent life support systems, no avionics, no control systems, no instrumentation, nothing.
And I wish I could say it was due to its hyper-advanced stealth technology or some kind of undetectable cloaking device that it was out there for so long before anyone saw it. But even if it did have something like that (and we still don't know if it did), that really wasn't why; as crazy as this sounds, it was just too small, and came in too fast, for any of our systems to even detect it on its way in. And by sheer coincidence, it just so happened to land in a "dead spot" where the security cameras could barely see it. It still should have been spotted right away, sure. But I saw the footage myself and can't say I would have spotted it either.
As for the lack of a "tense standoff" (or any standoff), the fact that he spoke perfect English had a lot to do with that. That plus the fact that he looked just barely humanoid enough that the Secret Service guy who first saw him thought it must have been a guy in a suit.
We later learned that his perfect English was actually due to the translation device attached to his mouth (which appeared to be his mouth). It turns out he knew how to speak and understand English with complete mastery—learned from nothing but the TV and radio transmissions they were able to pick up from halfway across the galaxy—but their species was simply incapable of actually speaking in any way that a human could actually understand due to the inherent limitations of their vocal systems, and physical inability to reproduce enough of the sounds necessary for human language. The perfectly understandable assumption from that, of course, would be that they had already evolved far beyond vocal communication (i.e., to telepathy). But no, they still spoke with each other with words, more or less like we do.
He later explained that their vocal limitations were a fairly recent development, at least from an evolutionary standpoint; it was just a few thousand years prior that they had vocal capabilities much like ours, with the capacity to speak countless native languages, some of which were quite similar to English. But at one point they had decided to standardize upon one global language, and it was from then onward that as their language continued to evolve over time, so did their vocal systems. Eventually, through a combination of evolution and bioengineering, their species came to be uniquely and perfectly suited for the reproduction of their one language with near-perfect clarity, though at the expense of all other potential languages.
Oddly enough, their language (and language in general) was one of the things he was most interested in talking about. Not how to speak it per-se, though he did teach us some of that (fortunately the limitation only went one way, and we were able to at least reproduce the basic sounds well enough to say words and phrases that he could understand—just barely). Rather, his primary interest was in sharing some of the features that their language possessed, possibly with the idea that we might someday decide to incorporate some of those elements into our own.
One of the things he spoke about at-length was how their language had gone through several "redesigns" throughout its history, where its vocabulary, pronunciation, and even its most fundamental rules were altered and simplified in order to enhance its efficiency at conveying information as accurately as possible while eliminating virtually any possibility for misunderstanding (or misrepresentation).
From the way he described the process, I can't say we have anything comparable when it comes to written/spoken languages, though I suppose the closest analogy would be the way computer programming languages go through intentional revisions over time, or the way that computer operating systems might be rewritten and revamped dramatically from one version to the next while fixing bugs and improving efficiency.
One of the first things they did, in in the earliest of their "major" revisions, was something which made their language unlike any on Earth: the complete elimination of homonyms (different words that sound the same), homographs (words that are spelled the same but mean different things), and synonyms (different words which share the same meaning).
Think about that for a moment; what they did was essentially recraft their entire language in such a way that every single word was unique in spelling, pronunciation, and meaning. And not only did this require the modification (or outright elimination) of most of the words in their entire vocabulary, but it also necessitated the creation of an almost incomprehensible number of entirely new words in order to serve the same functions as those which had been eliminated due to lack of uniqueness, but were not redundant to any "surviving" words.
On top of that, a smaller (yet still fairly vast) number of new words was also needed for cases where a word with multiple definitions was standardized to its primary (now, only) definition, but where no surviving words could accurately convey those eliminated definitions.
And adding even further to this herculean undertaking was the simple linguistic inevitability that in order to maintain the uniqueness of every single word in an entire language, you would need to use some combination of longer words (both letters and syllables); more letters that can be chosen from; more possible spoken sounds, accents, and intonations; or, in their case, all of the above.
To use an example from English, let's take the words "so", "sew", and "sow". All three are homonyms since they're pronounced identically, but "sow" also has an additional pronunciation which has a different meaning (a female pig, as opposed to the act of planting seeds), while "so" has one pronunciation but two different meanings (either to emphasize the extent of something, or as a conjunction).
Thus:
1. "Sew" would be eliminated and replaced.
2. Only one of the two definitions of "so" survives while the other must be replaced.
3. The female-pig definition of "sow" can remain (due to its unique spelling and pronunciation) while the planting-seeds definition must be replaced (due to its non-unique pronunciation).
The final tally: two words survive, one word eliminated and replaced, and three new words created.
But there's also another, less drastic option for #1: Since the spelling of "sew" is already unique, you could keep its spelling unchanged and simply modify its pronunciation to something unique (e.g. "soo"). And that's exactly what they did, where practical, to keep as many of their original words as possible, or at least as familiar as possible, either with just a slight tweak to the spelling or by appending an extra syllable.
But in most cases a simple "tweak" was simply not an option, due to an inviolable rule that they established before even the first change was made: None of the changes to any words could violate their universal, standardized rules for spelling and pronunciation (and this rule was retroactive as well, thereby requiring a rejiggering of all previous words which violated these rules).
This meant that they couldn't simply change the spelling or pronunciation of words arbitrarily, nor could they, in most cases, change one without that directly impacting the other. And by imposing this rule on themselves, they dramatically limited the number of options available for modifying existing words—at least not without adding more syllables.
Thus for all of their linguistic genius, it didn't take long after this first phase was implemented (which, almost inconceivably, they were able to complete within just a few years) that they ran headlong into a fairly serious problem: Their language now required vastly more syllables to be spoken, and vastly more letters to be written, in order to convey the exact same amount of information as before.
But this was something they had fully anticipated, and out of necessity had planned to address in their second major revision which came a few years later, now that the vast majority of the population had become fully fluent with what was essentially an entirely new language.
It was at this point—after putting up with several years of extreme linguistic inefficiency (during which they suffered tremendous losses in global productivity, albeit with the lowest unemployment levels in their recorded history)—that they finally implemented the solution via the Second Revision. To do so, they borrowed a concept which was also straight out of computer languages (including our own): a concept known to us as "single instruction multiple data" (SIMD).
The basic premise of SIMD is that you take a frequently-used combination of computer instructions and replace them with a new which performs exactly the same tasks; then, any time you need to use that same set of instructions, you simply use the new one which does all of the exact same "work", but in a single step.
In their case, they did the same thing but for words, taking their most frequently-used combinations of words (even in some cases fairly complex concepts) and "grouping" them into a single new word which conveyed all of the meaning and nuance of what would have taken multiple words and far more syllables to convey. And not only did this solve their problem, but once the Second Revision was completed they found that their speaking and writing/reading rates were actually even faster than ever before.
Since then, they've continued to implement even more of these "grouped" words over time (based on real-world frequency of use) and in some cases even created grouped words which contain previously-grouped words. So far, the most densely-grouped of these go three "levels" deep, though there is theoretically no limit to how many "levels" of meaning could potentially be consolidated into a single word.
These First and Second Revisions were clearly the most significant, both in effect and the sheer magnitude of their undertakings, but it was actually the Third Revision which I found most interesting; it was then that they implemented two features which had, to some extent, always been present in their language, but not in the universal and standardized way that it would eventually become.
The first was what could be considered a complete integration of mathematics into their language. Which actually sounds more complicated than it is; essentially they established clear grammatical rules which stated that any time there is a potential range of conceptual values to what someone is attempting to communicate, that value must be quantified—not just with vague words like "few", "many", or "most"—but numerically, with an actual mathematical value, every single time.
And this rule applies even to situations that we probably wouldn't even think of as being mathematical in nature. To use some examples from English, let's say something will "protect" you, or "prevent" you from being harmed; does that mean it offers total protection and prevents harm completely? Or just partially? And if just partial, at what point of the infinite points along the spectrum do you qualify as being "protected" vs unprotected?
Or how about a more common example; if you express that something "doesn't work", does that mean it's completely non-functional and isn't working at all? Or just that it's not functioning at a level of performance that you would consider acceptable?
Situations like these simply do not exist in their language since in every potential instance, the available words that they can choose from have either been firmly established as expressing absolutes, or there would always be an expression of quantification accompanying it to eliminate ambiguity.
But that doesn't necessarily mean that a precise number must always be given, even when a precise number isn't warranted, or simply isn't feasible. Because that's where the second feature comes into play: if the numerical value conveyed is intended to be just a rough estimate, that would also be directly incorporated into their syntax, thereby pairing every numerical quantification with an indication of confidence/precision. So if you want to say, "most", i.e. "more than 50% but less than 100%", you can still do so; or you can just as easily convey "somewhere in the 55-65% range", or "exactly 70%" and do so while using far fewer letters and syllables than it would take in any human language.
And it was soon after they came up with this idea that they also very quickly realized it would be equally useful in non-mathematical contexts, as a general "confidence" indicator in order to express whether something is being stated as absolute fact, as pure opinion/speculation, or anywhere in between.
Once all of these features were implemented (subsequent revisions did occur every few years, but they were far less wide-ranging in scope), their intended effects became very quickly realized; virtually all misunderstandings, miscommunications, and the inevitable conflicts and pseudo-disagreements which inevitably arise from them became a thing of the past. He was very careful not to overstate his point here, and made clear that arguments remained plentiful throughout their society; however, after these changes such arguments only occurred as a result of actual disagreements, not just people "talking past" each other or simply saying the same thing in different ways.
Just think: How many times have you seen two people arguing over a particular idea or concept where they were clearly operating under different definitions, and thus it was entirely possible that they did not even actually disagree on the matter being discussed?
And how many pitiful arguments have you seen in your lifetime which essentially consisted of nothing more than one side saying, "Not all [noun] are [adjective], but some are!", and the other saying, "Some [noun] are [adjective], but not all!"
Too many. And it is exactly those kinds of pseudo-arguments which simply never occur in their society, since their language has essentially been inoculated from the toxic effects of such rhetoric.
And perhaps most importantly, once these first three Revisions were in place, propagandistic bad-faith misrepresentation and rhetorical sleights-of-hand became, if not impossible, far more difficult to attempt and far easier for anyone to see. With every word having one clear-cut meaning, equivocation fallacies became, quite simply, impossible; after all, how can you try to exploit the fact that one word has multiple definitions in order to mislead, when there are no longer any words with multiple definitions to exploit?
Just take a moment to imagine where might our state of scientific progress be today—and whether the 21st century Science Riots would have even occurred—had our language been like theirs? Or just imagine the ripple effects throughout history if just ONE of our words had this feature, i.e. the one which has been exploited through equivocation more than any other, with at-times devastating consequences, i.e. "theory"?
Anyway, enough about that. It was after almost a full month of discussing nothing but their language that we eventually moved onto other topics like their culture, beliefs, and philosophy.
And at this point I know exactly what you're wondering: What was his take on "war"?
I guess you're wondering how I knew that. Well, we actually had some surveys done in those first few days after he arrived (all conducted via third parties, of course) just to get a feel for what kinds of questions the general public might eventually have, and maybe even get some ideas for questions we should ask him that we might otherwise have not considered (which turned out to be hopelessly optimistic; the grand total of useful ideas we got from those surveys: zero).
But one of the common threads that came up over and over—being the first mention in almost 100% of the surveys—was this notion that he (or any hypothetical alien visitor) would find the very concept of "war" to be utterly preposterous, possibly even to the point that he would be completely baffled that such a thing could possibly exist.
Unfortunately that wasn't anything close to the reality, for reasons which should have been fairly obvious. I mean, sure, on his home planet his species no longer practiced anything remotely resembling "war", and hadn't in countless generations. But certainly they had engaged in war throughout much of their recorded history, and had even come close to global self-annihilation on multiple occasions.
But even if that hadn't been the case, he revealed to us that war is something which virtually every single advanced alien civilization they have ever observed or encountered had clearly engaged in on a frequent basis, in the past if not currently, thus making it one of the most universal of all societal concepts.
The only exceptions? He said there were actually a handful of civilizations throughout the galaxy–though these were vanishingly rare–where the entirety of their archaeological and recorded histories had absolutely no record of war. But, he noted, in every one of these cases their histories also had suspicious and clearly unnatural "gaps"–just total voids where it's as if literally nothing happened for years, decades, even centuries. Most likely, they concluded, these histories were either systematically erased in order to hide something in their past, or that everything prior to those points–all history, all archaeological evidence–had been completely annihilated... most likely by war.
Oh, and speaking of those surveys? The second most common response, regarding human behaviors that an alien might be baffled by: laughter. And when we told him about that, and asked if their species has anything like laughter? Well... he laughed (not that we knew that's what it was at the time, we actually thought we had pissed him off).
It turns out that laughter (or the alien equivalent), rather than being some kind of nonsensical, bizarre quirk of human behavior, is also virtually universal among alien civilizations. He explained that its evolutionary value in any kind of social/communal society is so great that they have never observed a single advanced species which doesn't possess it. Essentially, he confirmed that our theories about the purpose of laughter are correct: originally evolving as a means to indicate that an apparent threat actually isn't one (or that an apparently dire situation isn't as serious as it appears to be), then eventually evolving to become a means for establishing rapport, bonding, and trust.
As for something which wasn't universal, but would actually make their culture unique among Earth societies? Well, how should I put this... Are you familiar with the Stanford Marshmallow Experiment? It's one of the oldest of all psychological experiments, which in its original form presented each of its participants (all children) with two options: Have one marshmallow now, or wait 15 minutes (while that marshmallow sits within reach), at which point they would be given that marshmallow plus another one. Just a simple test of delayed gratification, to see whether the kids were able and willing to forego immediate reward for the prospect of double the benefit. And as you might expect, about one-third of the kids ate the first marshmallow right away, about one-third tried waiting but eventually ate it, and about one-third waited the full 15 minutes and were rewarded with two.
Which sounds pretty mundane, maybe even fairly ridiculous as far as experiments go. But the interesting part is what came later–far later–as they tracked the progress of these children throughout their childhoods, and in some cases even into adulthood. And what they found was that the last set of kids–the ones who were willing to wait for that second marshmallow–turned out to have significantly better test scores, better grades, better health, and even, as adults, more-successful careers than the other kids, whereas those in the first group fared these worst.
So what does all of this have to do with him, and his culture? Well, imagine a society in which every single person–kids and adults alike–fall into the latter category, but to the greatest theoretical extreme imaginable. So not just a society in which procrastination and short-term thinking no longer exist, but one in which present and future have essentially ceased to have any meaningful distinction, and where every decision made–from the grand to the day-to-day mundane–is based on the pure calculation of total benefit, from now until eternity.
This was a natural progression over the course of their civilization's development as they became more and more forward-thinking over time, but it wasn't until what could be loosely translated as their "Renaissance" that they fully completed this philosophical transformation on a complete societal level over a period of just a few years. And the effects of this transformation became immediately evident, with dramatic improvements in crime reduction, health (particularly addictions, which were virtually eradicated), productivity, education, scientific advancement, and general happiness.
It was then a few decades after that, perhaps as an inevitable consequence, that they went through a Second Renaissance–one which also involved the near-total dissolution of another distinction, this time not between present vs. future but between the well-being of self vs. the well-being of others.
Essentially it was during this time that they came to the society-wide realization that there is ultimately no moral justification to put your own interests above those of anyone else's, particularly since—as he put it—the person you happened to be "born into" was ultimately decided by sheer chance, and you could just as easily been born as anyone else, past or present, living or dead.
Which isn't to say that every member of their society places everyone else's interests on perfectly equal footing with their own; as he explained it, it is simply not possible to know anyone's needs and desires better than you intimately know yours, and thus they still consider society's interests best served by doing your best to fulfill your needs and desires, and to strive for personal improvement to the fullest extent possible. And nor was it the case that this caused them to become some kind of collective "hive mind" where they lost all sense of individuality; if anything, the degree of freedoms and the range of avenues for complete self-expression/realization available to each member in their society went far beyond anything ever observed on Earth.
But the effect of this Second Renaissance was at least equally profound as the first, as all decision-making became pure cost/benefit analyses of what would result in the greatest total benefit, whether to the individual or society at large. And this was achieved through no coercion, and without even any change in laws (in fact, a tremendous number of laws were ultimately eliminated since they no longer served any purpose).
And it wasn't long after this Second Renaissance that they began reaching out to the other civilizations throughout the galaxy that they had previously just observed from afar, and began sending out emissaries in their speed-of-light ships, like the one they sent to visit us.
You know, it's funny... As I'm recording this, I can't help but think about all the time I've spent arguing with crackpots online, ridiculing and debunking the biggest, craziest conspiracy theories: That the Moon Landings were faked. That the Mars Landings were faked. 9/11 was an inside job (or faked). The 2020 Election... But the 12/12 Visitation is the one I never touched. Go back and check out my social media archive and my entire posting history if you don't believe me. And here I am, 32 years later, not debunking a conspiracy, but confirming the biggest one of all.
So why am I doing this? I'm not sure, really. But I think more than anything else, I just feel bad for how much we did him wrong. He was completely up-front with us, right from the beginning: He didn't come here to share anything about their technology—just their culture, beliefs, and way of life. And he was 100% clear that this was for our benefit, not theirs. He even clued us is in to the fact that of all the alien civilizations they had ever monitored, the only ones that had ever suffered total irreversible extinction did so as a result of their own technologies gone awry (or, in a few cases, the technologies of other planets' civilizations, if you know what I mean).
Of all the rest–even those which faced extinction-level events on a scale that our planet has never even seen in its history (gamma ray bursts, direct comet strikes, even in one case a micro-black hole which tore right through the center of their planet)–all of these civilizations managed to survive, and in some cases eventually recover.
As for us specifically, he said our current level of technological progress is already far beyond what they would consider our capability to responsibly handle, and thus anything they could possibly contribute to that technological progress—no matter how seemingly benign such technologies may be—would only serve to further increase that divide and further magnify our chances of complete self-annihilation.
And we were OK with that stipulation at first, or at least we pretended to be. After about six months with him, during which he shared everything he could (or would) for 24 hours a day (one thing I forgot to mention earlier: he had no need for sleep), we eventually exhausted things to ask him about. And yet after all that, we still knew no more about their technology than we did on day one.
Even his ship was a complete non-starter. Had it been anything even remotely similar to our own, I'm sure we could have reverse-engineered it, or at least gleaned something from it that could have put us light years ahead of any other county on the planet. But there was absolutely nothing about it that had even the slightest corollary to what we currently have, or had ever even theoretically conceived of. It was basically the equivalent of taking the most advanced supercomputer on the planet and sending it back in time to the Stone Age. Or to an ant colony.
Maybe someday we'll be able to unlock its secrets, but my guess is we're at least hundreds of years from even having a chance at cracking its most basic functions (at which point, maybe we'll realize it really was just a landing pod).
So of course, it shouldn't be a surprise to anyone what we did next. Now, I say "we" loosely, since I certainly had no say in it. Which I'm sure might seem incredibly self-serving at this point, but all I can give you is the truth: The day we got everything we could out of him and he refused to divulge any more secrets, we finally resorted to what we've always resorted to. Enhanced interrogation techniques. Coercive interrogation. Learned helplessness. Torture.
And do I even need to say that this turned out to be one of the biggest mistakes of all time? First off, it didn't work; months of almost non-stop torture using every method we could possibly come up with, and we got nothing more out of him. He was completely unfazed, and not because it didn't hurt him; some of the... methods we used sent his biometric readings off the charts. He was clearly experiencing tremendous physical distress, vastly more than any human could conceivably handle.
But no matter what we did, he just took it. And if he even cared, he kept it completely internalized. Just completely stoic, from beginning to end. Even his demeanor and attitude towards us never changed; after all of that—45 days of almost non-stop agony—he still wanted to tell us more about their language. And he was still just as polite as that first day waiting patiently outside the White House.
It's always been rather amusing to me... Of all the many believers in the 12/12 Visitation, how many wildly different, even completely contradictory reasons they've come up with for why it would've been kept under wraps all this time.
Either, "It would cause a total collapse of the world's organized religions", or "It would cause unprecedented numbers of people to turn towards God, and away from The State".
Either, "It would cause mass chaos and a total breakdown of society", or "It would cause everyone to unite behind our common humanity, and thus end all war and conflict which would cause a total collapse of the military-industrial complex".
The truth is, it wasn't originally anyone's plan to keep it under wraps. Some of the details, sure. But we all figured we would make the big announcement eventually. We even commissioned a task force of some of the brightest minds on the planet—under the guise of a purely hypothetical scenario, of course—and they all came to the same general conclusion: Of all the possible reasons for why a government might keep an alien visit a secret, those fears were pretty much completely overblown.
Realistically, they figured, there would be no mass chaos, no mass peace, no collapse of religion or of society or really anything else just because an alien decided to come visit us. A hundred years ago maybe that would have been a different story. But after everything we've seen in our lifetimes? I think we could have handled it. And all of the experts did too.
But how the hell could we have revealed him to the world after all that? After everything we did to him?
And I still can't help but wonder... What if it was all a test? I mean, clearly, in a figurative sense it certainly was—and one we failed horrifically. But what if it was actually a test?
I just can't get past the question of why they would even bother sending a representative in-the-flesh, instead of just some kind of A.I. or digital representation or even just a recording with all of the information that he shared with us.
Were they just trying to see how we would treat him?
And if we had treated him humanely, and respected his stipulations (as any reasonably-civilized people would have), what then? Would he have opened up to us with their technological secrets? Would he still be sharing them with us today? And more importantly, would we still have—metaphorically speaking—our souls?
Ultimately, I suppose this is all fairly moot anyway, given what's coming next. By our calculations it's just five days away, give or take a day. And all I can hope for at this point is that some of us make it, and that maybe what I'm recording here makes it through. And maybe someday we can recover, countless generations from now, and maybe they'll give us another shot.
But if not, I can't say it wasn't deserved.
Photo: "they are alien" by son.delorian is licensed under CC BY-NC-ND 2.0
#alien#conspiracy#coverup#linguistics#short story#scifi#sci-fi#science fiction#language#conspiracy theory#ufo#ufology#writing#fiction
1 note
·
View note
Text
Top 8 Code Coverage Tools for Free: A Developer’s Guide to Smarter Testing

In software development, code coverage is more than just a metric—it’s a roadmap to understanding how thoroughly your tests exercise your codebase. High code coverage reduces the risk of undetected bugs, improves code quality, and instills confidence in your releases. But with so many tools available, how do you choose the right one—especially when budget constraints are a factor?
This guide dives into free code coverage tools across programming languages like Java, Python, JavaScript, C/C++, and .NET. We’ll explore their features, use cases, and how they fit into modern workflows. Plus, we’ll touch on how platforms like Keploy simplify test generation to complement coverage analysis. Let’s get started!
What Is Code Coverage?
Code coverage measures the percentage of your code executed during testing. It answers: “Did my tests run every line, branch, or function?” Here’s a breakdown of common coverage types 310:
Line Coverage: Tracks which lines of code are executed.
Branch Coverage: Checks if all conditional paths (e.g., if-else) are tested.
Function Coverage: Measures how many functions/methods are called.
Statement Coverage: Ensures every statement runs at least once.
While 100% coverage isn’t always practical, aiming for 80%+ is a common benchmark to balance thoroughness and effort.
Why Code Coverage Matters (A Deeper Dive)
1. Identify Untested Code
Even a well-structured codebase can have logic branches that are never tested, leading to undetected bugs. Code coverage tools analyze which lines, functions, and branches have been executed during tests, helping developers spot dead zones where issues might be hiding.
For example, an untested error-handling block could fail silently in production, causing unexpected behavior.
2. Improve Test Quality
High test coverage doesn't always mean high-quality tests. Coverage reports help developers go beyond just hitting code paths—they reveal weak assertions, missing edge cases, and false positives. A test suite with 100% coverage but weak assertions is just as risky as having no tests at all. |
By examining which scenarios are covered, teams can refine their test strategies to ensure robustness.
3. Meet Compliance Standards
In industries like finance, healthcare, and aerospace, regulatory bodies (e.g., FDA, ISO, SOX) enforce strict software quality standards. Many require minimum test coverage thresholds (such as 80% or higher) to ensure mission-critical applications function as expected.
Neglecting this can lead to compliance violations, legal consequences, or even system failures in high-risk environments.
4. Boost Developer Confidence
Without test coverage, deploying a new feature or refactoring existing code can feel like walking through a minefield. Knowing that key logic is covered allows developers to ship changes with confidence, reducing last-minute production rollbacks.
This is especially critical in CI/CD pipelines, where automated testing serves as a safety net before code reaches production. Top Free Code Coverage Tools
Here’s a curated list of free and open-source tools to supercharge your testing workflow:
1. JaCoCo (Java)
Features: Measures line, branch, and instruction coverage; generates HTML/XML reports; integrates seamlessly with Maven and Gradle.
Best For: Java projects needing in-depth test coverage insights.
Setup: Add the JaCoCo plugin to your build tool and execute tests.
Pro Tip: Use mvn jacoco:report or gradle jacocoTestReport to generate detailed reports.
2. Coverage.py (Python)
Features: Provides line and branch coverage analysis; works well with pytest, Django, and unittest.
Best For: Python developers looking for a simple yet effective coverage tool.
Setup: Install via pip install coverage, run coverage run -m pytest, and generate reports.
Pro Tip: Use coverage report -m to see which lines of code are not covered by tests.
3. Keploy (VS Code Extension)
Features: Automates test generation, measures code coverage, and integrates with CI/CD.
Best For: Developers looking to enhance test coverage effortlessly.
Setup: Install from VS Code Marketplace, activate the extension, and run tests to analyze coverage.
4. Istanbul (JavaScript)
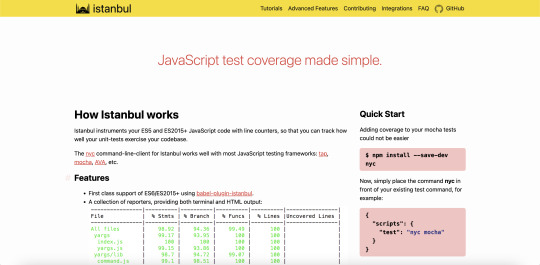
Features: Supports ES6+ JavaScript, integrates with Jest, Mocha, and other test frameworks.
Best For: Node.js and browser-based JavaScript applications.
Setup: Install using npm install --save-dev istanbul, then run tests with coverage enabled.
Bonus: The CLI tool NYC simplifies generating reports with nyc report.
5. OpenCover (.NET)
Features: Measures branch and statement coverage, integrates with NUnit, xUnit, and MSTest.
Best For: .NET developers needing a lightweight coverage solution.
Setup: Download OpenCover and execute tests using OpenCover.Console.exe with the appropriate parameters.
Alternative: Coverlet is a modern alternative for .NET Core projects, offering better integration with MSBuild and CI/CD tools.
6. Cobertura (Java)
Features: Tracks historical coverage trends; integrates with Ant and Maven for seamless reporting.
Best For: Teams maintaining legacy Java projects.
Setup: Configure Cobertura in pom.xml (for Maven) or use ant cobertura-instrument to analyze code coverage.
7. Gcov (C/C++)
Features: Part of the GCC toolchain; provides function and branch coverage metrics.
Best For: Low-level programming, embedded systems, and performance-critical applications.
Setup: Compile with -fprofile-arcs -ftest-coverage, then use gcov to analyze the results.
Pro Tip: Combine lcov with Gcov for graphical HTML reports.
8. Fine Code Coverage (Visual Studio)
Features: Provides IDE-integrated reports for Visual Studio; supports MSTest, NUnit, and xUnit.
Best For: .NET developers using Visual Studio Community Edition.
Setup: Install the Fine Code Coverage extension from the Visual Studio Marketplace.
Best Practices for Maximizing Code Coverage Tools
Write Meaningful Tests: Target edge cases and business logic, not just coverage percentages
Integrate Early: Add coverage tools to CI/CD pipelines for real-time feedback
Avoid “Fluff” Tests: High coverage with shallow tests is worse than lower coverage with robust ones.
Use Dynamic Analysis: Tools like Keploy automatically generate tests from API interactions, reducing manual effort while improving coverage
Set Realistic Thresholds: Enforce an 80% baseline but prioritize critical modules.
Free code coverage tools empower developers to build reliable software without budget constraints. Whether you’re testing Java with JaCoCo, Python with Coverage.py, or .NET with OpenCover, these tools provide actionable insights to refine your test suites.
For teams looking to reduce manual testing overhead, platforms like Keploy offer a modern twist. By auto-generating integration tests from real user traffic, Keploy complements traditional coverage tools, helping you achieve higher coverage with less effort.
FAQ
1. Can code coverage tools work with legacy projects?
Yes! Tools like Cobertura and Gcov are designed for older codebases. Start by instrumenting existing tests and gradually improve coverage.
2. How do I combine Keploy with coverage tools?
Keploy generates tests from API calls, which can be merged with existing unit tests. Run both through tools like Coverage.py or JaCoCo for unified reports
3. Is 100% code coverage realistic?
Rarely. Focus on critical paths and balance with other testing methods (e.g., security scans, performance tests).
4. Which tool is best for JavaScript?
Keploy is the go-to for JS/Node.js projects. You can simply install the VS Code extension and start visualising file level coverage for your projects
5. How does Keploy improve test coverage?
Keploy automates test creation by capturing real API interactions, ensuring even complex integration scenarios are covered
0 notes
Text
there’s not a lot I can say about s3 that hasn’t already been said (and articulated 200x better) but! here are some of my (albeit dumb) thoughts :~)
ep1 -isak leaning against the bathroom wall gets me EVERY time its such a powerful scene esp introducing you to s3 and tarjei..... spare some talent for the rest of us please -LiTeN gUtTeN fRa StRaNgEr tHiNgS -isak rly ties his pants w a shoelace...... -isak noticing even for the first time bc of his laugh.. whew.... also. i love this intro SOOO much bc its so non-monumental? theres no dramatic music or whatever but its not subtle.... like you know right away o shit love interest!! hello sir!! bc isak’s expression watching him :’) i could go on -isak is a bad liar HOWEVER this only applies to stupid nontrivial things e.g. the black sweatshirt. but when you look at him lying about like, his sexuality, he hides that shit well -”c00l” isak. i hate u so much -honestly all u have to do is look at even for .2 seconds and u can tell this boy has had a crush for a solid month bc he just looks awestruck (HOWEVER henrik’s acting is *chef’s kiss* bc its subtle enough to go undetected b4 you actually know eVEN SAW HIM ON THE FIRST DAY OF SCHOOL) -even isak and emma all sitting on the bench together is funny enough on its on but then a song called threeway comes on and like. julie sdshjsfdjfkjskd ep2 -there’s something so endearing about even’s handwriting idek what -i LOVE even’s video w mikael it reveals so much about him to us- how weird (ok we saw how weird he was w the paper towel thing but) and dorky he is? and his love of film! his view on love stories and how he sees the world :( but it also shows a lot abt isak because he saw even making stupid jokes about vladimir putin and was like yeah we about to fall in LOVE love -isak not using headphones to watch even’s video or r+j?? bde or general incompetence what’s the verdict guys -the isak watching r+j scene hits so hard like yall ever think about isak lying in bed at 3am staring at the ceiling probably thinking about how he’s never gonna get a beautiful world-shattering romance like that like ..... also him changing positions skam get out of my life go away ur too realistic -not to make this even more self-projection-y but isak simultaneously being the least emotionally vulnerable person ever but crying during r+j > -i made a post abt this already but even’s INTENSE staring vs isak’s “i have never looked anyone in the eye in my life” gets me it says so much about their characters -even said i see your bde move (asking me to buy you beer) and i raise u with my own (inviting you to my house after faking not having my id) -”if you listen to music” even is such a dick fsdjhsdff -when the message comes on...... i rlly do owe julie my life huh -”have you heard about my rapping?” “I have actually” have we talked about this enough????? 1. isak finally feels comfortable enough w even to flirt and his first move is to RAP for him jesus christ. keep in mind this is the same man who pulled that smooth af ibuprofen line w emma like...... 2. even has heard about isak’s rapping. either this means im-not-on-social-media even went out of his way to go thru homeboy’s instagram OR isak’s rapping is actually talked about. i- -the group chat messages. cant believe i forgot about the 2016 clown epidemic
ep3 -mahdi is a good friend and i love him. thank u -even wearing isak’s cap until he chucks it at him sjksfjsdjsd -how much yall wanna bet isak’s been listening to illmatic on repeat since last friday thinking abt even (even tho meeting sonja shattered his heart a lil) [also kinda an aside but i think a lot about how isak n even bonded over rap and how some homophobic lyrics in 90s etc rap might have impacted them? or how that little detail ties into julie’s story? e.g. halftime by nas, which is on illmatic] -whats worse. even staring into isaks soul wearing a size xs see-through white t shirt or isak staring at even for five (5) seconds before chugging his beer and immediately making out w emma. OR even crashing that party before it can start “i think you guys are bonding too much” cheesy ass shjhfsdhskdf -yall act like evak didnt invent hands. did even shaking isak’s shoulder telling him his apartment is nice mean nothing to u -im convinced robyn wrote call your girlfriend for this scene specifically bc how could anything fit so perfectly by coincidence -is anything better than egging isak on- even bech naesheim (2016) -idk if yall have read the scripts but i love the sock thing so much bc its soo true to how isak thinks and it makes everything so much more interesting and !!!
ep4 -i will never get over even sending isak bad seinfeld memes -even smacking open isak’s locker. first of all whew second of all u think as soon as he got into the stairwell he lowkey cried bc ow -parallel of isak saying “it’s 2016, why are you religious?” to sana vs. emma’s “it’s 2016, get out of the closet” to isak anyone :( -”takk sanasol!!!!” thank u isak for my life -I wanted to be with you aloneeeee -even’s face when he sees the pool like we get it youre a director -how many times do i need to say even is such a dick sjkfsd “does it look like i care about my hair?” “usually but not right now” like this would only work on isak i love soulmates!! -even just.. fully choking isak out ssdhgfd got em -when the first notes of im kissing you start ooh boy -even going in for the kill kiss and isak going from huh to oooo shit and pushing his lips out at the last minute. phenomenal
ep5 -ngl as soon as im not in love comes on my heart goes uwu bc like!!!! that song the meaNING.... them......... i jus love this scene sm like theyre in their own little bubble and they both feel so comfortable and at peace :(( -even leaving isak comics about an inside joke of theirs like yall mind if i scream -isak feeling left out from the conversation and his friends whew i felt that... and having them talk about how gross it is to makeout with a girl w facial hair?? blease :( -taking stock of isak’s nicknames: issy k, isabell, izzy, baby jesus, -im not even gonna bother trying to articulate thoughts on Pause bc it’s a literal masterpiece. thank u tarjei henrik and julie for inventing television with this one -MAGNUS SDFKJSDFJKDSHK "oooh my name is Jonas and I love idealism and reading klassekampen and I don’t like plastic and I skate on a skateboard made of sustainable wood and wear old clothes because new clothes are bad for the environment and I only drink recycled water” screAMMM -what i said abt pause also applies to pride ugh its such a powerful scene and!! the beginning of kicks to isaks stomach. honestly what i fucking love about this episode is how it goes from hell yea best day w even ever to crying in the street within one week (s3 had the best balance of angst and payoff thanks) -even’s Soft Party Flannel... forever tainted by this scene rip -not knowing why even kissed sonja keeps me up at night -speaking of. how used and stupid isak must’ve felt when he saw even completely unbothered, hooking up w his ex at this party?? whew :( -bros is one of my all time favourite clips solely bc of the music?? lift me up gives me chills and when hold my liquor starts i LOSE it -ep5 and 6 remind me of that quote “to see what your characters are really made of you have to break them” because julie rlly goes all in and god it hurts so good
ep6 -never have i ever seen insomnia portrayed as accurately as tarjei did here and i remember when i first watched the cantina scene i was like. winded bc its SO true to sleep deprivation whew -i really like that isak wasnt together with even when he reached out for help and came out to jonas. bc it was him, on his own, being strong enough to talk to his friends and then eventually he was confident and secure enough in himself to be in a good place when even started reaching back out!! -i have no idea what its like to come out to someone, to be afraid of your friends rejecting you, everything isak went through. but tarjei’s acting of when, like, you have something you KNOW you have to tell someone, and youve put yourself in the position where youre going to have to tell them, but youre terrified and eventually just force yourself SAY the words?? -and isak’s smile when he realizes jonas is gonna be his bro no matter what :’)))
ep7 -weirdly one of my favourite isak looks (black t-shirt grey snapback c-c-c-combo) -”what’s your name again?” have i mentioned i love sana and isak bc i love sana and isak -jonas truly is the best friend oh man. perceptive, thoughtful, loving, laidback, a friggen BRO. tbh i was wary of him in s1 and thought he didn’t treat eva well (tho I recognized he loved her a lot, he was just bad at being a boyfriend) but jonas in s3?? just goes to show how powerful your perspective of someone can change viewing them in a different role!! because while jonas was a crappy bf, he literally is SUCH an incredible friend and his actions and words and just! him! in s3 completely redeemed any illwill I had towards him :’) -maybe im a little gay (up there with other s3 comedy classics such as “thats a boys name”) -mahdi season WHEN ugh a legend -’when someone asks isak if hes going to a family party’ literally what other reason for living do i have if not to read the boy squad text convos -isaks locker finally opening and his smile at evens drawing whewwwwwww!! also even rlly is that guy who wont text you back but will leave hand written love letters in ur locker -also. another stellar look from valtersen -slutt a meld meg is a whole masterpiece like what other piece of media has the RANGE -eskild: play hard to get. jonas: no smiley!!! isak: nah fam im good B)
ep8 -this episode is BEAUTIFUL bc you feel practically euphoric?? like hell yeah theyre finally together!! isak is out and accepted and even is done with sonja! but theres also this unsettling undercurrent of worry bc you know deep down something isnt right? why is sonja calling isak? why is even acting kinda strange? whats going on? yknow?? -literally never going to get over 5 fine frokner :~) even is such a goddamn nerd and he’s the man of isak’s dreams can u believe!! -sana’s little speech is SO important in so many ways ooo i love her so much -also have we discussed eskild making evak do a photoshoot for him. highkey those are my favourite pictures of ALL time u can tell even was like hm strange but im down while isak was more omg guys stop🙄 omg haha eskild i cant believe youre making me cuddle with even for a photo🙄 i cant believe ur making me snuggle this dude for a pic!!!! definitely would not have done this otherwise!!! -magnus only realizing it’s THAT even after seeing how isak looks at him. whew -isak is so brave i rlly love that kid! his text to his mamma <3 -no r*make will EVER nail text conversations like mari/julie did w evak’s this week thanks for coming to my ted talk. i'd quote the best ones but it would literally double the length of this post (ok ill cave. “hahaha shut up❤️” GETS me) -you dont know whats in store but you know what youre here for. hallo -isak running around oslo with even’s clothes looking for him :( his heart is so big he cares about even so so much -when Part II (on the run) comes on in the credits its like a kick in the teeth honestly
ep9 -ive already screamed enough about cherry wine but god it fucks me up -cannot put into words how much I love eskild and how good of a person he is, he just has so much love in his heart -”wait they have waffles here? see ya” -this convo is why i love skam so much!!!! magnus giving insight and good thoughtful advice to isak was such a brilliant move by julie (also truLy heartwarming) bc like. magnus is a flawed layered character! he’s dumb and ignorant and not very careful with his words BUT hes also such a sweet guy. i genuinely dont think he would hurt a fly and him talking about vilde (in ep10) is ;-; bc he really likes her and respects her and wants to be a gentleman! hes so loving and just. yeah. also i wonder if isak and magnus (and vilde) ever talked about having mentally ill parents and lent on each other for support bc like....<3 [sidenote- this is why i HATE b***** like they absolutely massacred magnus’s character and magnus did not deserve that!] -det er bare slutt........ very cool of tarjei to invent acting here. also the character development makes me WEEP like at first isak lied and told his pappa it was over bc its easier to brush stuff off and say you were joking than be vulnerable especially about 1. having a boyfriend and 2. saying youve already broken up?? but then isak was like hey im done with lying about who i am bc i want my life to be REAL and he told his dad the truth even if it was hard and even if he was trying rlly hard not to cry -isak reaching out to even<3 standing up for even<3 -o helga natt. another scene i genuinely cannot comment on bc u cant really put into any written language how magical and breathtaking and heartbreaking and powerful and brilliant this scene is. so. -jk. obvs i cant say anything intelligent enough to give this scene justice but probably the most stunning piece of television i have ever had the privilege of watching. even’s text breaks my heart every gd time (esp since we never really see this side of him before finding out he’s bipolar? his guilt, insecurity, feeling like a burden, being scared of losing everyone in his life because he thinks he’ll hurt them). the music is SO beautiful i cry real tears as soon as the strings start. also the brilliance of JUST o helga natt playing and no dialogue except for isaks one line? isak’s realization when he sees the cross. him RUNNING across oslo to go to even. the FLASHBACKS all going backwards in chronological order until them smoking on the bench. isak looking at the bench and not seeing even and u can feel his heart breaking and urs breaks too! but then he remembers the bathroom and he turns and theres even and whewwww. du er ikke alene<3
ep10 -minutt for minutt is THE most healing clip im telling u. and like.. seeing even depressed really is hard and as someone who was very very depressed for 4-ish yrs of their life it rlly hits me? like when youre in an especially bad funk and you cant get out of bed and youre just numb and exhausted and feel so shitty and u want to be alone but you really dont???? could go on but literally i owe henrik holm my life for his portrayal of even -not to be a soft bitch on main but when isak tucks the blanket over even and it keeps getting pulled off his back so isak just. covers that spot with himself? -i do love that call between sonja and isak bc once again! a flawed (realistic) human being -and isak thinking its his fault even is depressed? it means a lot that sonja told him its no ones fault, even is just bipolar. and i wonder if isak felt that way about his mamma as well, guilty for her being ill, and if what sonja said made him feel better about that situation too :( -lowkey random but when isak is rambling really fast and he goes “maybe we’ll get bombed tomorrow and talking about all this is a waste of time” it continually punches me in the throat bc that is /exactly/ how i ramble and think like tarjei........ pls -like eskild said. there really is so much love in isak’s little grumpy teenage body<3 -isak no longer just passively accepting life as its given to him, now he fights for him and even!!!!! -isak is such a forgiving person and seeing him able to just accept things and move on? incredible -i remember when i first watched ep1 i was like oooo even and isak are gonna be kosegruppa partners and thats when theyll first get together, cooking food or smth!! but lmfao after episode 3? kosegruppa whomst???? also hilarious vilde thought isak of all people would willingly sign up for kosegruppa just to go to revue parties -even and linn friendship!!!! -cannot articulate how mf heartwarming it is to see even smiling and being more himself after being depressed (also thank u julie for having ups and downs coming out of his depression- its so true to life having one day when youre feeling awesome and then the next you feel awful again for no reason and its SO frustrating) -I had to stop watching passe pa meg cause it made me toooooo crazy! it would just be like: “I like seeing you laugh” and I was like: *SCREAMS* -im the fucking master of lying 😤 -literally don’t know why isak and even ragging on kosegruppa is so funny but “did you think I joined to have fun” gets me every time -I SAW YOU THE FIRST DAY OF SCHOOOOOOOOOOOOOOOOOOOOL -also even literally radiating love @ isak watching get snarky w vilde on the phone bc it reminded him of the first time he saw him! even rly is that boyfriend who thinks isak being pissy is the Best Thing he has Ever seen -halla boiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiz -literally the glo up of isak telling his friends the order in which he’d bang them -No filter! wow I love symbolism -so nice to see the girls together for a lil bit :) -the boys hyping up mags while also telling him to be respectful awwwwww -take desperate to a whole new level- Confucius -who’s going to show isak how to properly hold a beer can -literally evak banter gets me thru the day. thank u tarjei and henrik for having phenomenal chemistry + improvisation skills + making isak and even the dumbest nerdiest boys i have ever seen -biology partner. and friend. ;-; -even literally is the biggest stoner blease -isak’s talk with eva is just sooooo<3 and not to be emo on main but every single word of the last few sentences he says hit me so gd hard because i feel the exact same way in my BONES -livet er nå 💛
final thoughts :( <3 -this season is so special. it feels like one really long oscar-worthy movie or smth?? i cant even exblain, its just magical. ALSO very dear to my heart. -julie really said you guys have seen isak sad and alone and repressed for the past two seasons so heres him falling in love with the best person in the world and coming to terms with who he is and being brave and opening up and finally being happy and living a real life -this season definitely feels different from s1/2/4 to me editing or production or music smth wise? as in, its got a lot fewer aesthetic shots and the cinematography seems a bit different if that makes any sense???? I also think this is the season most focused just on the main (i.e. not many- if any? sideplots going on) -literally will never get over the thought, love, and detail put into this season. when i say there is literally nothing i would change about it, i mean it and coming from my nitpicky ass??? means a lot lmfao. the acting, directing, music choices, symbolism...... sublime -s3′s cold rainy autumn aesthetic makes me ACHE for fall and also nostalgic for a highschool experience I never had lmao?? also. all the nighttime clips >>> -don’t know what else to say except thank u skam for my life
#take a shot every time i say whew#fully put more effort and time into this than most of my uni projects xx#its super rambly but thats bc its mostly just my direct stream of thought#also super long! and probably still missing things i wanted to say#AND like 3 weeks late fshfjjkdjkfsd#skam#clownfest 2019#blabbey
13 notes
·
View notes
Note
I was diagnosed with adhd in middle school bc I had a lot of trouble doing assignments on time - I sort of blew it off at the time and said that adhd was overdiagnosed. Later I stopped taking meds for it (sophomore year) bc I felt like they slowed me down n made me robotic. In little ways I feel like I haven’t grown out of it (trouble getting in work, having to rewind tv shows all the time, hyperfixations). I convinced myself I didn’t have it - how “overdiagnosed” is it really?
Sent January 21, 2019
It depends a lot on demographics. Are you male or female? What is your race? What class are you (e.g., upper, middle, lower)? What type were you diagnosed with? What is your age (generation)? What type of environment did you grow up in (e.g., rural, suburban, urban)?
See, people with Inattentive ADHD tend to be underdiagnosed, or misdiagnosed with depression.
Females tend to be underdiagnosed or misdiagnosed with bipolar disorder or borderline personality disorder, depending on type.
White upper-class boys are sometimes overdiagnosed because school personnel overstep their bounds or they have unethical doctors or their parents don’t want to actually parent their kids, while African-American lower-class boys tend to be written off as criminals and put in detention (as in juvie) or prison (depending on age).
Your age is also a factor, as which generation you belong to has influence on whether or not you’re likely to be properly diagnosed.
For example, I am Generation X and was diagnosed with Combined ADHD in adulthood; I’m also a middle-class female who grew up in rural communities, and I was a gifted student who had no access to more advanced education in elementary, middle, and secondary school. Do you see how my demographic slot is rife with reasons why I went undetected for 28 years?
If you are struggling now, it may be worth getting reassessed to see if you still meet the diagnostic criteria and, if so, to find out what your options are for treatment, accommodations, and other supports. That’s your call; you have to decide if knowing is something you want.
-J
** Note: Huge apologies if I misspoke at all in my discussion of the demographic factors that affect diagnosis of ADHD. It is entirely possible that I have misremembered some of the details here, or that I used incorrect terminology somewhere.
31 notes
·
View notes