#Security consultancy services
Explore tagged Tumblr posts
Text
The Importance of Security Consultancy Services in Dubai: DSP Consultants Leading the Way
In a rapidly developing urban environment like Dubai, ensuring the safety of assets, people, and infrastructure is critical. With ever-evolving security challenges and compliance standards, organizations need professional guidance to identify vulnerabilities and implement effective strategies. This is where DSP Consultants, a leading provider of security consultancy services in Dubai, comes in.

Why Security Consultancy Services Matter
Dubai's growth as a global business and tourism hub has brought increased complexity to security requirements. Whether it’s safeguarding iconic skyscrapers, securing sensitive infrastructure, or protecting crowded public spaces, the need for expert security planning has never been greater. Security consultancy services provide businesses with tailored solutions to address risks, mitigate threats, and comply with local regulations.
DSP Consultants: Pioneers in Security Solutions
At DSP Consultants, we specialize in comprehensive security consultancy services that cater to a wide range of industries, including commercial, residential, industrial, and government sectors. Our team of experts combines technical expertise with a deep understanding of Dubai’s security standards, ensuring that our clients receive innovative and compliant solutions.
Key Security Services Offered by DSP Consultants
Security Threat AssessmentOur threat assessment services involve a meticulous evaluation of potential risks to your assets and people. By identifying vulnerabilities, we develop customized strategies to minimize exposure and enhance overall security.
Security Master PlanA security master plan serves as the foundation for effective security management. We create detailed documents outlining strategies, goals, and mitigation measures, ensuring a cohesive approach to protecting your organization.
Security Gap AnalysisWith our security gap analysis services, we assess existing security measures to identify weaknesses. Our team then provides actionable recommendations to bridge those gaps and improve the overall effectiveness of your security framework.
Blast AnalysisIn a region where high-profile structures are often targeted, blast analysis is a crucial service. DSP Consultants leverages advanced software to simulate explosion scenarios, assess the impact on structures, and recommend measures to mitigate potential damage.
Security Systems DesignWe design cutting-edge security systems, including video surveillance, access control, intrusion detection, and perimeter protection. Our designs integrate seamlessly with your infrastructure, ensuring both functionality and aesthetic appeal.
Why Choose DSP Consultants?
Compliance Expertise: We ensure all solutions meet Dubai’s stringent security standards, including SIRA (Security Industry Regulatory Agency) and other relevant authorities.
Customized Solutions: Our services are tailored to the specific needs of each client, whether it’s a small residential project or a large-scale commercial development.
Innovative Approach: By using the latest technology and methodologies, we deliver solutions that are not only effective but also future-ready.
Proven Track Record: DSP Consultants has a history of successful collaborations with leading developers, architects, and government bodies in Dubai.
The Value of Professional Security Consultancy
Investing in security consultancy services is not just about compliance—it’s about creating safe and resilient environments. By partnering with DSP Consultants, you gain access to a team that prioritizes your safety and success, delivering solutions that go beyond expectations.
Get in Touch
If you’re looking for reliable and innovative security consultancy services in Dubai, DSP Consultants is here to help. Contact us today at [email protected] to discuss your project and find out how we can protect what matters most to you.
#Security consultancy services#Security consultants#Security consultancy services Dubai#Dubai#Security consultant#Security risk assessment#Security master plan
0 notes
Text

Smart Home Solutions at Palm Beach Audio Visions
At Palm Beach Audio Visions (PBAV), we are passionate about delivering exceptional audio visual, home automation, lighting, and technology integration solutions for residential and commercial projects. From the initial concept to the final system deployment, we are dedicated to ensuring that projects are completed on time and within budget while exceeding industry standards for quality. Our team of experienced professionals brings a wealth of expertise in the high-end market and a strong focus on building lasting relationships with our clients. Feel free to visit us!
#Lutron Homeworks Dealer Whole House Smart Lighting Consultant#Design#Installation#Manager Solutions#Smart Home Network Setup Wifi Installation#Smart Home Security Camera Installation#Lutron Smart Window Electric Shades#Outdoor Entertainment System Design Installation Solution with Pool Patio Surround Sound Speakers#Outdoor Patio TV speaker Solution with Surround Sound#Universal Remote Control Smart Touch Screen Solution Programming Installation in Frenchman's Creek Palm Beach Gardens#Samsung QLED#Sony OLED#LG OLED Smart TV Dealer Installation Service#Home Theater System Consultant#Design and Installation Services#Sonos Dealer and Speaker Installation#Surround Sound Setup with In-ceiling Invisible Speakers#Whole House Multi Room Home Audio Installation Services#Smart Home Technology Consultant#Whole Home Automation Expert Installation Company#Control4 Smart Home Dealer - Installer
2 notes
·
View notes
Text
Elevate Client Services with Excel: Expert Tips for Financial Consultants by Grayson Garelick

Financial consultants operate in a dynamic environment where precision, efficiency, and client satisfaction are paramount. Excel, as a versatile tool, offers an array of features that can significantly enhance the services provided by financial consultants. Grayson Garelick, an accomplished financial analyst and consultant, shares invaluable Excel tips to help financial consultants elevate their client services and add tangible value.
The Role of Excel in Financial Consulting
Excel serves as the backbone of financial consulting, enabling consultants to analyze data, create models, and generate insights that drive informed decision-making. As the demands of clients become increasingly complex, mastering Excel becomes essential for financial consultants aiming to deliver exceptional services.
1. Customize Excel Templates
One of the most effective ways to streamline workflows and improve efficiency is by creating customized Excel templates tailored to specific client needs. Grayson suggests developing templates for budgeting, forecasting, and financial reporting that can be easily adapted for different clients, saving time and ensuring consistency.
2. Utilize PivotTables for Data Analysis
PivotTables are powerful tools in Excel that allow financial consultants to analyze large datasets and extract meaningful insights quickly. Grayson emphasizes the importance of mastering PivotTables for segmenting data, identifying trends, and presenting information in a clear and concise manner to clients.
3. Implement Conditional Formatting
Conditional formatting is a valuable feature in Excel that allows consultants to highlight important information and identify outliers effortlessly. By setting up conditional formatting rules, consultants can draw attention to key metrics, discrepancies, or trends, facilitating easier interpretation of data by clients.
4. Leverage Excel Add-ins
Excel offers a variety of add-ins that extend its functionality and provide additional features tailored to financial analysis and reporting. Grayson recommends exploring add-ins such as Power Query, Power Pivot, and Solver to enhance data manipulation, modeling, and optimization capabilities.
5. Automate Repetitive Tasks with Macros
Macros enable financial consultants to automate repetitive tasks and streamline workflows, saving valuable time and reducing the risk of errors. Grayson advises recording and editing macros to automate tasks such as data entry, formatting, and report generation, allowing consultants to focus on value-added activities.
6. Master Advanced Formulas and Functions
Excel's extensive library of formulas and functions offers endless possibilities for financial analysis and modeling. Grayson suggests mastering advanced formulas such as VLOOKUP, INDEX-MATCH, and array formulas to perform complex calculations, manipulate data, and create sophisticated models tailored to client needs.
7. Visualize Data with Charts and Graphs
Visualizing data is essential for conveying complex information in an easily digestible format. Excel offers a variety of chart types and customization options that enable consultants to create compelling visuals that resonate with clients. Grayson recommends experimenting with different chart styles to find the most effective way to present data and insights.
8. Collaborate and Share Workbooks Online
Excel's collaboration features enable financial consultants to work seamlessly with clients, colleagues, and stakeholders in real-time. Grayson highlights the benefits of sharing workbooks via OneDrive or SharePoint, allowing multiple users to collaborate on the same document, track changes, and maintain version control.
9. Protect Sensitive Data with Security Features
Data security is a top priority for financial consultants handling sensitive client information. Excel's built-in security features, such as password protection and encryption, help safeguard confidential data and ensure compliance with regulatory requirements. Grayson advises implementing security protocols to protect client data and maintain trust.
10. Stay Updated with Excel Training and Certification
Excel is a constantly evolving tool, with new features and updates released regularly. Grayson stresses the importance of staying updated with the latest Excel training and certification programs to enhance skills, explore new capabilities, and maintain proficiency in Excel's ever-changing landscape.
Elevating Client Services with Excel Mastery
Excel serves as a catalyst for innovation and excellence in financial consulting, empowering consultants to deliver exceptional services that add tangible value to clients. By implementing Grayson Garelick Excel tips, financial consultants can streamline workflows, enhance data analysis capabilities, and foster collaboration, ultimately driving client satisfaction and success. As financial consulting continues to evolve, mastering Excel remains a cornerstone of excellence, enabling consultants to thrive in a competitive landscape and exceed client expectations.
#Financial Consulting#grayson garelick#Customize Excel Templates#Utilize PivotTables#Implement Conditional Formatting#Leverage Excel Add-ins#Automate Repetitive Tasks with Macros#Advanced Formulas and Functions#Visualize Data with Charts and Graphs#Collaborate and Share Workbooks#Protect Sensitive Data with Security#Stay Updated with Excel Training#Elevating Client Services with Excel
3 notes
·
View notes
Text
CMMC 2.0 Compliance Resources
Here's what I found for everyone wanting to get CMMC compliant.
Access free resources here: https://iquasarcyber.com/cmmc-level-2-compliance/
2 notes
·
View notes
Text
Sap Security Consultant Service
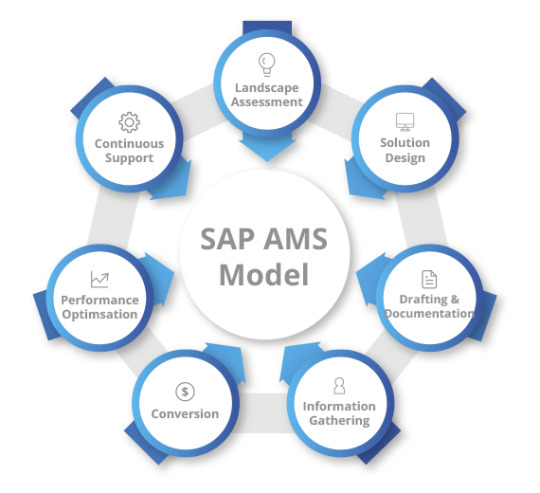
Explore top-notch SAP security consultant services on vvolve.com. Our experts ensure robust data protection, risk management, and compliance for your SAP environment. Safeguard your business with our cutting-edge solutions.
2 notes
·
View notes
Text
Cyber Security Solution Providers
PrinceTech provides an excellent cyber security solution. They have a vast knowledge of the industry and they have been able to help me solve a number of complex problems. Visit Today:- www.princetech.io/techconnect
#IT Consulting#app development#it services#it consulting#cyber security company#cyber security service providers in nigeria
6 notes
·
View notes
Text
✅ SEO for WordPress
#IT Consultancy#Web and App Development#AdSense#SEO#Graphic Design#Password Recovery and Security#Online Marketing#Corporate Services
0 notes
Text
Website Security & Recovery – Atcuality Has You Covered
A hacked website can be devastating for any business. Atcuality offers expert website security and recovery solutions to restore your site quickly and prevent future cyber threats. Our team specializes in identifying and removing malware, fixing vulnerabilities, and restoring lost content. Our hacked site recovery services provide a complete solution for businesses facing cyberattacks, helping them regain control of their websites and protect customer data. We offer 24/7 emergency support, ensuring that your website gets back online with minimal downtime. Atcuality’s security experts don’t just recover your website—we enhance its defenses with real-time monitoring, malware scanning, and firewall implementation. Whether you run an e-commerce store, a corporate website, or a personal blog, we tailor our security solutions to meet your specific needs. Trust Atcuality to keep your website safe, secure, and operational at all times.
#search engine marketing#search engine optimisation company#digital services#emailmarketing#digital marketing#search engine optimization#seo#search engine ranking#search engine optimisation services#seo company#seo services#social media marketing#seo marketing#seo expert#seo agency#on page optimization#on page seo#on page audit#off page optimization#off page seo#local search engine optimization#local seo#digital consulting#hacked account#website security#wordpress security#websitedevelopment#wordpress#wordpress development#wordpress website
0 notes
Text
Laravel API Development: How It Enhances Web & Mobile App Performance
In today’s digital era, businesses rely heavily on web and mobile applications to engage users, automate processes, and drive revenue. One of the most popular frameworks for building efficient, secure, and scalable APIs is Laravel. With its robust architecture, built-in security, and advanced features, Laravel simplifies API development while ensuring optimal performance.
At Pixxelu Digital Technology, we specialize in custom Laravel API development, helping businesses create seamless and high-performing applications. In this blog, we’ll explore how Laravel API development enhances the performance, security, and scalability of web and mobile apps.
What is Laravel API Development?
Laravel API development involves creating RESTful or GraphQL APIs using Laravel’s built-in features. APIs allow different applications to communicate efficiently, whether it’s a web-to-mobile connection, third-party integration, or microservices architecture. Laravel provides a developer-friendly and efficient approach to API creation, ensuring better speed, security, and maintainability.
Benefits of Laravel API Development for Web & Mobile Apps
1. Enhanced Performance with Eloquent ORM
Laravel’s Eloquent ORM (Object-Relational Mapping) makes database interactions more efficient. It provides a simple and elegant way to fetch, store, and manipulate data, reducing unnecessary SQL queries and optimizing performance.
2. Built-in Authentication and Security
Security is a crucial aspect of API development, and Laravel ensures robust protection with built-in authentication and authorization mechanisms. Laravel provides tools like Passport and Sanctum, which help in creating secure OAuth-based authentication and token-based authorization for APIs.
3. Efficient Caching for Faster Response Times
Laravel supports multiple caching mechanisms like Redis, Memcached, and file-based caching to speed up API responses. By storing frequently accessed data in the cache, Laravel APIs reduce server load and enhance application speed.
4. Seamless API Routing with Middleware
Middleware in Laravel helps in filtering incoming requests, improving security, and handling CORS (Cross-Origin Resource Sharing) issues effectively. With Laravel’s route caching feature, API routes load faster, ensuring quick response times.

5. Scalability with Microservices Architecture
For businesses looking to build scalable applications, Laravel APIs fit perfectly with microservices architecture. Developers can create independent API services that communicate efficiently, improving performance and maintainability.
6. Database Migrations for Data Integrity
Laravel’s migrations and seeders simplify database management by allowing developers to create and modify database schemas effortlessly. This ensures data consistency across different environments and improves application stability.
7. Seamless Third-Party Integrations
Laravel APIs support third-party integrations with tools like Stripe, PayPal, Twilio, and Firebase. This enables businesses to add payment gateways, SMS notifications, and real-time database updates with minimal effort.
8. Automatic Testing for Reliable API Performance
Laravel provides PHPUnit and feature testing tools to ensure that APIs work as expected. With built-in unit testing capabilities, developers can identify and resolve bugs before deployment, leading to stable and high-performing applications.
Why Choose Pixxelu Digital Technology for Laravel API Development?
At Pixxelu Digital Technology, we understand that businesses need fast, secure, and scalable APIs to stay ahead in the competitive market. Our expert Laravel developers have extensive experience in building custom APIs tailored to business needs. Here’s why you should choose us:
Expert Laravel Developers – Skilled in advanced API development techniques.
Secure API Development – Implementing the latest security measures.
Performance Optimization – Leveraging caching, database indexing, and route optimization.
Custom API Solutions – Tailored to your specific business requirements.
Seamless Integration – Connecting APIs with third-party services and applications.
FAQs
Q1. What is the main advantage of using Laravel for API development?
A: Laravel provides built-in features like authentication, caching, and routing, making it a secure and high-performance choice for API development.
Q2. How does Laravel improve the performance of web and mobile apps?
A: Laravel improves performance through caching, Eloquent ORM, optimized routing, and middleware, ensuring fast response times and reduced server load.
Q3. Is Laravel suitable for building scalable APIs?
A: Yes, Laravel supports microservices architecture, allowing businesses to build scalable APIs that can handle high traffic and complex operations.
Q4. How does Laravel ensure API security?
A: Laravel provides OAuth authentication (Passport, Sanctum), CSRF protection, and secure middleware, ensuring data privacy and protection against threats.
Q5. Can Laravel APIs integrate with third-party services?
A: Yes, Laravel allows seamless integration with payment gateways, messaging services, cloud storage, and other third-party APIs.
Conclusion
Laravel API development offers a powerful and efficient solution for building secure, scalable, and high-performance web and mobile applications. With features like Eloquent ORM, caching, authentication, and microservices support, Laravel simplifies API development while ensuring fast and smooth app performance.
At Pixxelu Digital Technology, we specialize in creating custom Laravel APIs that meet business needs and enhance app functionality. If you’re looking for expert Laravel developers to build secure and high-speed APIs, get in touch with us today!
Contact Pixxelu Digital Technology for professional Laravel API development services and take your application to the next level!
#Laravel Eloquent#API Security#Laravel Caching#Laravel Middleware#Laravel Microservices#Laravel Third-Party Integration#API Performance Optimization#Custom Laravel Development#Hire Laravel Consultant#Laravel CRM Development#Laravel CRM Development Service#Advantages of Laravel Over Other Frameworks#Laravel Development Company#Custom Laravel Development Company#Custom Laravel Web Solutions#Enterprise Development Solutions#Laravel API Development#Laravel Migration Services#Laravel Cloud Integration#Laravel Backend API Development#Laravel API Debugger#API Development Using Laravel#Laravel for API Development
0 notes
Text
What Makes The Gem Portal Login Secure and User Friendly?

1. It should be safe to get into GreM.
When you log in, be careful:
Some information about your sales and business may be hidden.
You can't sign in until you buy something. Some people don't like it. To protect people's privacy, it keeps a close eye on them. People are more likely to join if they trust each other.
2. Things you can do to keep your GeM Portal account safe
a) Looking at an item (MFA)
These are the things that GeM users have to show about themselves:
Name and key of someone.
You should still be able to use the phone number or email address you used to make the account.
This card says that you work for the government.
You can feel better about the things you buy if you use a digital signing certificate (DSC) and e-sign.
b) A place to keep coins safe
People who go to the website need to have strong passwords. For them to work, they need numbers, letters (big and small), and other icons. Here's how to keep the keys safe. Roles (RBAC) decide what people in this case can see. When you buy, own, or are in charge, you can do different things. Because of this, there aren't many safety risks.
d) Captcha and other security measures are used to keep hackers out.
Cryptographic key exchange (CAPTCHA) makes sure that only real people can log in. Everything will be safe if you use Security Layer (SSL). Use SSL to protect your information when you pay or sign in to the GeM page. If you keep this a secret, only the right people will be able to see it. This will protect your privacy.
f) Automatic Logout When Not Used
GeM logs people out right away if they don't do anything within a certain amount of time. The person is less likely to let someone else in without getting out first. The word "DSC" in English means "digital signing certificate." We're going to look at this. GeM checks with DSC to make sure the information is right and can't be changed before doing business or signing important papers.
(h) A lot of moving and checking
The GeM page's security is checked often to make sure it follows the most current rules.
3. Parts of the GeM Portal that are simple to use Type in your password.
GeM works hard to make signing in quick and easy, even though safety is very important.
1) Single Sign-On (SSO) is a service People who use SSO only have to log in once to get to a lot of services. They don't need to type their passwords over and over. In this way, the process goes better. Making the sign up process easy.
2) IDs based on Aadhaar make it easy for people who buy from the government to sign up. People who want to sell can quickly sign up with their PAN. The place where laws start Check what you think you know about a business.
3) A simple look that gadgets can handle GeM login works on phones and computers, so it's easy for people to join.
4) More than one language to talk to each other if you know more than one language, you can use the page.
5) Forgot your email address? Get it with an OTP. People can quickly change their passwords because it's easy to get back in.
6) It's easy for many computers to use. That lets you use GeM from anywhere. It works on Google Chrome, Mozilla Firefox, or Microsoft Edge on Windows PCs.
7) Help with bugs and customer service People who can't join can get help from other users or the help line. It takes place every day. A lot of people come in after a long time.
4. Common Login Issues and Troubleshooting
Q1: I have a hard time remembering my GeM pin. How can I get it to work again?
Solution: When you click "Forgot Password," enter your registered email address or phone number. Then, to make a new password, follow the steps for OTP proof.
Q2: I tried to log in several times but failed, so my account is now locked. What should I do?
Solution: Your account could be locked if you kept typing in the wrong password. You have 15 minutes to either try again or use an OTP to change your password.
Q3: The OTP won't go to the number I gave you, right? What should I do?
Solution: Make sure the number on your smart phone is correct. Also, check your trash or junk box if you used an email OTP. To stop it, ask GeM for help.
Q4: Easy to change the email address or phone number I signed up for GeM with.
When you log in, you can change your picture. You might need to use an OTP to confirm the changes for safety reasons.
Q5: When I try to sign in, I see "Session Expired."
You might not have done anything or your plans might have changed. There are two ways to log in again: clear your cookies or start over with the page.
People who work for the Indian government, public sector units (PSUs), and autonomous bodies can buy and sell things and services online through the Government e-Marketplace (GeM).
How to Get into the GeM Portal
People who buy from the government GeM can only be used to buy things for the government. People from the following groups can buy:
Departments of the Centre and the State Government
Government-run businesses
The government and groups that work alone
Schools, colleges, and study groups
Panchayati Raj Institutions (PRIs)
Municipal Corporations and Government-Linked Organizations
If you work for the government, you have to use either your official email address or an ID that is based on Aadhaar to sign up.
2. Sellers and Service Providers
A lot of different types of businesses can join GeM to sell or provide services.
Producers and traders are the people who make or sell things that the government buys a lot.
MSMEs: These are tiny, small, or medium-sized businesses. Because they follow certain rules, MSMEs can buy things from the government more easily.
New businesses: Through the Start-up India program, well-known new businesses can join GeM.
An OEM is a company that makes something for the first time. They sell things that have their own brand name or patent on them.
The people who work for service providers do a lot of different work, such as IT support, human resources, coaching, transportation, building management, and plenty more.
Groups for men, hobby shops, and self-help groups (SHGs): People who live in the country and run craft shops can also get help from GeM.
3. Not having the chance to sign up
They might not be able to join the program if they don't meet the GeM compliance standards, if they don't have a recent GST registration (except for certain categories that are exempt), or if they fail verification. A company that the government has banned also can't join.
Conclusion:
It's safe and easy for anyone to log in to GeM online. The site has strong protection, digital signatures, automatic proof, and more than one way to prove who you are. This keeps bad people out. SSO, or secure one-sign-on, can be used in more than one language. It's easy to use the new one. Business and the government can use it this way. As long as you follow the rules, GeM is still a safe place to shop or do business. It's getting better. GeM makes it easy, quick, and safe for everyone to do business. GeM changes the way India gets things because it makes it easy for the government and public companies to do business together. No matter if they work for the government, a PSU, an MSME, a maker, or a service provider, GeM makes it easy and safe to buy things. If you meet the requirements and sign up for GeM, you can work for the government in many ways. For more details visit : https://bidhelp.co/
#RWRDC karnataka#northern railway tenders#bihar state electricity board#gujarat revenue department#earthwork tenders#delhi tenders#Secure login on GeM#Easy login on GeM#Effortless bidding on GeM#Consultancy services
0 notes
Text
https://electronicsbuzz.in/tcs-brings-the-future-of-aerospace-defense-to-aero-india-2025/
#Tata Consultancy Services#security#AeroIndia2025#DefenseTech#AerospaceInnovation#AI#DigitalEngineering#CyberSecurity#MakeInIndia#powerelectronics#powermanagement#powersemiconductor
0 notes
Text
How Security Systems Design by DSP Consultants Helps Developers Save Costs in CCTV System Installation in Saudi Arabia
In the modern landscape of urban development, the safety and security of properties, businesses, and residents are paramount. In Saudi Arabia, the demand for reliable and efficient security solutions has never been higher, particularly with the rise in real estate development and commercial infrastructure. For developers looking to install effective CCTV systems, partnering with experienced security consultants can lead to significant cost savings, without compromising on the effectiveness of the security systems.

At DSP Consultants, a leading security consultants firm in Saudi Arabia, the primary focus is on security systems design that not only protects people and assets but also helps developers minimize costs throughout the installation and long-term operation of the security infrastructure.
1. Tailored CCTV Systems for Maximum Efficiency
One of the biggest challenges in designing a security system is ensuring the right coverage while avoiding unnecessary expenditures on excess equipment. A security systems design by DSP Consultants takes into account the unique layout and specific security requirements of each project. This customized approach ensures that CCTV cameras are placed only where they are truly needed.
For example, rather than installing cameras in every corner of a building or development, security consultants at DSP Consultants assess the site to identify the high-risk areas where surveillance is most crucial. By optimizing camera placement, DSP Consultants reduce the total number of cameras required, ultimately lowering both initial installation costs and ongoing maintenance costs.
2. Smart Integration of Security Technology
In addition to CCTV cameras, security systems often involve various technologies, such as access control systems, alarms, and surveillance software. By working with security consultants like DSP Consultants, developers in Saudi Arabia can integrate these different security components into one cohesive system.
The advantage of such integration is that it streamlines the installation process, reducing the time and labor costs associated with setting up separate systems. Moreover, with a unified system, developers can reduce ongoing operational costs, such as system maintenance, as well as the complexity of training staff to manage multiple, disjointed security platforms.
3. Improved Long-Term Efficiency with Smart Systems
One of the key features of modern security systems design is the inclusion of smart technology that helps optimize system performance and reduce long-term costs. DSP Consultants integrate intelligent CCTV systems that use analytics to detect unusual activities, such as motion detection, facial recognition, and vehicle license plate recognition.
By automating these processes, developers don’t have to rely on constant manual monitoring, which reduces labor costs. Moreover, advanced video analytics can quickly identify potential security threats, enabling a faster response and reducing the risk of damage or loss.
4. Future-Proof Solutions to Avoid Additional Costs
One of the significant benefits of engaging with security consultants like DSP Consultants is their ability to design systems that are future-proof. By planning for scalability, DSP Consultants ensure that CCTV systems can be easily upgraded as new technologies emerge. This flexibility allows developers to avoid costly overhauls or replacements of the security infrastructure down the road.
For instance, DSP Consultants can design security systems that allow for easy expansion—whether it’s adding additional cameras, incorporating new surveillance technologies, or upgrading software. With forward-thinking security systems design, developers can adapt to evolving security needs without incurring additional costs for reinstallation.
5. Compliance with Local Regulations
In Saudi Arabia, security systems must adhere to specific regulations and standards. DSP Consultants, with their deep understanding of local requirements, ensure that the security systems design complies with all legal and regulatory frameworks, including SIRA (Saudi International Regulatory Authority) standards for security systems.
By working with experienced security consultants in KSA, developers can avoid the costly mistakes associated with non-compliance, such as fines or delays in the project timeline. Ensuring that all security measures meet local standards from the outset saves both time and money in the long run.
6. Reduced Maintenance and Operational Costs
CCTV systems, like any other technology, require ongoing maintenance to ensure optimal functionality. A poorly designed or overly complex security system can lead to frequent breakdowns, increased repair costs, and inefficiencies in security monitoring. Security consultants from DSP Consultants design systems that are easy to maintain and manage, with clear guidelines for regular upkeep.
With a well-designed system, developers are less likely to face high maintenance costs, ensuring that the CCTV systems perform efficiently for years. Additionally, the use of high-quality, reliable equipment from trusted manufacturers further minimizes the risk of costly repairs.
Conclusion
For developers in Saudi Arabia looking to install CCTV systems, security systems design by expert security consultants like DSP Consultants offers a cost-effective, efficient, and future-proof solution. By focusing on customized designs, smart integration, scalability, and compliance with local regulations, DSP Consultants help developers save on both installation and long-term operational costs.
With their expertise in designing comprehensive security systems, DSP Consultants provide developers with the peace of mind that their properties will be secure, while also ensuring that their investment is protected and maximized. Whether for commercial, residential, or industrial projects, the expertise of security consultants is an invaluable asset in creating robust and cost-effective security solutions in Saudi Arabia.
#Security consultants#Security systems design#security design consultants#security consultancy services#Saudi Arabia
0 notes
Text
Expert DPO Services for GDPR Compliance – Secure Privacy Consult
Ensure your business stays compliant with data protection regulations through expert DPO services from Secure Privacy Consult. Our experienced team provides tailored solutions to safeguard data privacy, mitigate risks, and ensure full GDPR compliance. Trust Secure Privacy Consult for secure, reliable services.
0 notes
Text
Network Right
Network Right is the leading Managed IT Services and IT Support provider in the San Francisco Bay Area, serving startups and tech companies across San Francisco, San Jose, Oakland, Berkeley, San Mateo, Santa Clara, and Alameda. Offering comprehensive remote and onsite IT solutions, their services include IT infrastructure, IT security, data backup, network management support, VoIP, A/V solutions, and more. They also provide IT Helpdesk support and Fractional IT Manager roles, ensuring full-spectrum IT management. Trusted by fast-growing companies, Network Right combines expert solutions with unparalleled customer support to accelerate business growth.
Contact us:
333 Bryant St #250, San Francisco, CA 94107
(415) 209-5808
Opening Hours:
Monday to Friday: 9 AM–6 PM
Saturday to Sunday: Closed
Social Links:
https://www.linkedin.com/company/networkright/
#IT Support#Managed IT Services#IT Helpdesk#IT Infrastructure#IT Security#Data Backup#Network Management#VoIP Solutions#A/V Solutions#Cybersecurity#IT Consulting#Professional IT Services
1 note
·
View note
Text
GORCSI: Synergy of IT and Business Consulting Services
Empower your business with GORCSI's comprehensive IT and Business Consulting Services. Our team of experts is dedicated to understanding your unique challenges and creating customized solutions that drive results. Whether you're looking to streamline operations, boost efficiency, or enhance performance, we have the knowledge and expertise to help you succeed. Invest in your business's future with GORCSI today.
Click Here: https://gorcsi.com/bussiness-and-it-consulting-services
#(SBA) 8(a) Business Development Program#8(a) Streamlined Technology Application#digitalization and digital transformation#ISO certified Program and Project Management#IT and Business Consulting Services#it application management#project management consulting companies#sba certified companies#SBA-certified Application Management#SBA-certified Infrastructure & Cyber Security Service
0 notes
Text
Delphos Advises on a Landmark $150M Deal for Mongolian Mortgage Corporation - Bolstering Housing Access
Delphos Advises on a Landmark $150M Deal for Mongolian Mortgage Corporation - Bolstering Housing Access
Press Release – 16 January 2025 – Washington, DC and Ulaanbaatar, MongoliaThe U.S. International Development Finance Corporation (DFC) has received approval from its Board of Directors on a $150 million landmark financing to the Mongolian Mortgage Corporation (MIK), advised by Delphos, the global financial advisory firm. This transformative deal will see the DFC acquire $150 million of…
#Economic#Financial#Financial Advisory#Financial consultant#Financial Services#Impact#Impact investments#Infrastructure#Investment#Investment Management#Mortgage#Securities#sustainable development
0 notes