#RemoteCodeExecution
Explore tagged Tumblr posts
Text
Critical .NET Security Updates Released for July 2024
Remote Code Execution Vulnerabilities in .NET 6.0 and 8.0
Denial of Service Vulnerabilities affecting .NET 8.0
As developers, it's crucial that we stay on top of these security patches to maintain the integrity and safety of our applications. Failing to update could leave our systems exposed to potential attacks.The .NET team has been hard at work to identify and resolve these issues, and we commend their commitment to keeping the framework secure. 👏If you haven't already, make sure to update your .NET 6.0 and 8.0 installations as soon as possible. The stability and protection of our applications depend on it!
Check out www.whiztekcorp.com
#.NETSecurity#CriticalUpdates#RemoteCodeExecution#DenialOfService#ApplicationSecurity#DeveloperSafety
1 note
·
View note
Text
Think Log4j is a wrap? Think again

Three years after its discovery, Log4Shell remains one of the software flaws that are most used by threat actors, a new report released by Cato Networks has found. https://jpmellojr.blogspot.com/2024/08/think-log4j-is-wrap-think-again.html
0 notes
Link
https://bit.ly/3FvbLci - Multiple Internet to Baseband Remote Code Execution Vulnerabilities in Exynos Modems In late 2022 and early 2023, Project Zero reported eighteen 0-day vulnerabilities in Samsung Semiconductor's Exynos Modems. Four of the most severe vulnerabilities enable Internet-to-baseband remote code execution, allowing an attacker to remotely compromise a phone with just the victim's phone number. The other fourteen vulnerabilities require either a malicious mobile network operator or local access to the device. Affected devices include Samsung, Vivo, and Google Pixel series, as well as vehicles using Exynos Auto T5123 chipset. Users can protect themselves by turning off Wi-Fi calling and VoLTE in their device settings until security updates become available. Project Zero has decided to withhold disclosure of the four most severe vulnerabilities due to their potential impact on users.
#ExynosModem#ProjectZero#Cybersecurity#RemoteCodeExecution#Vulnerabilities#Samsung#GooglePixel#MobileSecurity#VoLTE#intelligence#analysis#news
0 notes
Link
0 notes
Photo

Microsoft warnt vor Schwachstellen in Fernwartungsschnittstelle
Neue Schadsoftware nutzt Remote Code Execution (RCE) aus
Wieder geht ein Alarm durch die Windows-Welt, alle Systeme angefangen von Windows 7 SP1, Windows Server 2008 R2 SP1, Windows Server 2012, Windows 8.1, Windows Server 2012 R2 und alle Windows 10 Versionen können über die Fernwartungsschnittstelle angegriffen werden.
Ein System, das erfolgreich attackiert wurde, verteilt die Malware auf alle anderen Rechner im Netzwerk. Damit ist eine ähnliche Verbreitung wie bei den WannaCry-Schadprogrammen vor einigen Jahren zu befürchten. Die Fermnwartungsschnittstelle für den TeamViewer war auch im Sommer 2016 das Ziel von Angriffen.
Eine ähnliche Lücke mit der Bezeichnung Bluekeep (CVE-2019-0708) wurde von Microsoft bereits im Mai mit einem Update geschlossen, die aktuellen Bedrohungen haben die Namen CVE-2019-1181 und CVE-2019-1182 erhalten. Microsoft hat auch dazu zwei Updates zur Verfügung gestellt.
Welche Auswirkungen der Angriff hat, hängt also im wesentlichen davon ab, wie schnell die IT-Admins in großen Unternehmen diese einspielen. Die WannaCry Angirffe hatten vor allem deshalb so viel Erfolg, weil man damals nicht schnell genug reagierte.
Mehr dazu bei https://www.zdnet.de/88366697/wurmgefahr-microsoft-warnt-vor-zwei-kritischen-schwachstellen-patch-sofort-installieren/ dort sind auch die aktuellen Patches runterzuladen.
https://www.aktion-freiheitstattangst.org/de/articles/6980-20190815-microsoft-warnt-vor-schwachstellen-in-fernwartungsschnittstelle.htm
#Microsoft#Wurm#Malware#TeamViewer#Cyberwar#Hacking#Trojaner#RemoteCodeExecution#WannaCry#Verbraucherdatenschutz#Datensicherheit#Datenpannen
1 note
·
View note
Text
Active Exploitation of Vulnerability in the Wild by Zimbra Remote Code Execution
The active exploitation of the vulnerability made in the wild inside the zero-day remote code execution (RCE). There is one of the better news for the users of Ubuntu users thus making the installation of the Pax by default in Ubuntu 20.04, and in Ubuntu 18.04 thus making the issuance of a custom patch issued for protection by cpio.
0 notes
Link
#xss#Exploit#Vulnerabilities#SQLInjection#CVE#Vulnerability#BugBounty#Hacking#Malware#VAPT#RemoteCodeExecution#CommandExecution#Neo4j#Bugs
0 notes
Link
0 notes
Text
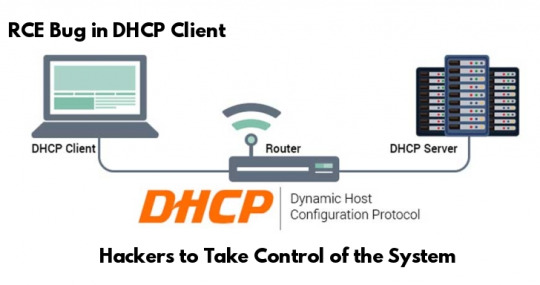
Critical Remote Code Execution Vulnerability in DHCP Client Let Hackers Take Control of the Network
Critical Remote Code Execution Vulnerability in DHCP Client Let Hackers Take Control of the Network
Read More About : https://gbhackers.com/dhcp-client/
0 notes
Video
Discovered by Polish security researcher Dawid Golunski of Legal Hackers, the critical vulnerability (CVE-2016-10033) allows an attacker to remotely execute arbitrary code in the context of the web server and compromise the target web application. All versions of PHPMailer before the critical release of PHPMailer 5.2.18 are affected. More info about this vulnerability: https://errorcybernews.com/2016/12/29/phpmailer-membuat-jutaan-website-memiliki-kerentanan/ Exploit Tool: https://github.com/opsxcq/exploit-CVE-2016-10033 Full Version: https://youtu.be/M9k70PldG4E #exploit #phpmailer #vulnerability #rce #remotecodeexecution (at Error 404 Cyber News)
0 notes
Photo

Cisco Releases Security Patches for Critical Flaws Affecting its Products | MrHacker.Co #cisco #hackingnews #networkingdevices #remotecodeexecution #vulnerability #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Text
Vulmap - Web Vulnerability Scanning And Verification Tools
Vulmap - Web Vulnerability Scanning And Verification Tools #elasticsearch #JBoss #linux #macOS #RemoteCodeExecution
Vulmap is a vulnerability scanning tool that can scan for vulnerabilities in Web containers, Web servers, Web middleware, and CMS and other Web programs, and has vulnerability exploitation functions. Relevant testers can use vulmap to detect whether the target has a specific vulnerability, and can use the vulnerability exploitation function to verify whether the vulnerability actually…

View On WordPress
#elasticsearch#JBoss#linux#macOS#Remote Code Execution#Scanner#Scanning#SSRF#Struts2 RCE#tomcat#Tools#Verification#Vulmap#Vulnerability#vulnerability Scanning#web#Weblogic RCE
0 notes
Photo

Zero-Click Wormable RCE Vulnerability Reported in Microsoft Teams #microsoft #microsoftteam #remotecodeexecution #remotecollaborationsoftware #vulnerability #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo

A ‘Critical’ Unpatched Flaw Has Affected All Versions Of Windows: Microsoft | TheHackerNews.Co #microsoft #microsoftwindowsflaw #remotecodeexecution #security #windows #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes
Text
RT @lukerodgers90: I earned $2,500 for my submission on @bugcrowd #remotecodeexecution https://t.co/YwwGlyrgt9 #ItTakesACrowd #BugBounty #magento #realmagento https://t.co/IuMbe9TWPw
I earned $2,500 for my submission on @bugcrowd #remotecodeexecution https://t.co/YwwGlyrgt9 #ItTakesACrowd #BugBounty #magento #realmagento https://t.co/IuMbe9TWPw
— Luke Rodgers (@lukerodgers90) November 29, 2017
from Twitter https://twitter.com/fbeardev
0 notes