#SBOM
Explore tagged Tumblr posts
Text
LibTracker Updates 12/16/24: Simplifying Dependency Management for Developers
Managing dependencies is one of the most critical aspects of modern software development. With LibTracker, our VSCode extension, we’re empowering developers to maintain up-to-date, secure, and compliant applications effortlessly.
View your app's dependencies at a glance, identify outdated versions, fix security vulnerabilities, and address problematic licensing—all in one streamlined tool.
Access LibTracker here: [Visual Studio Marketplace](https://marketplace.visualstudio.com/items?itemName=windmillcode-publisher-0.lib-tracker)
New Features:
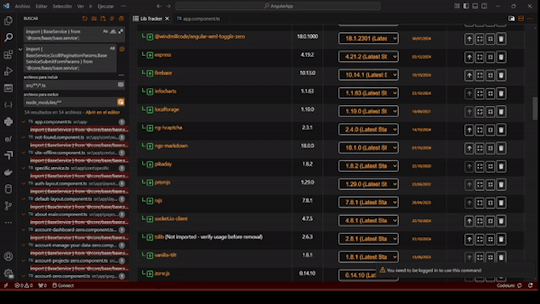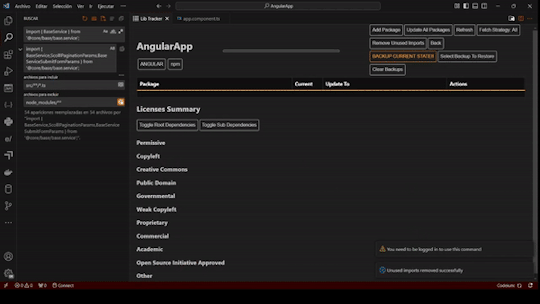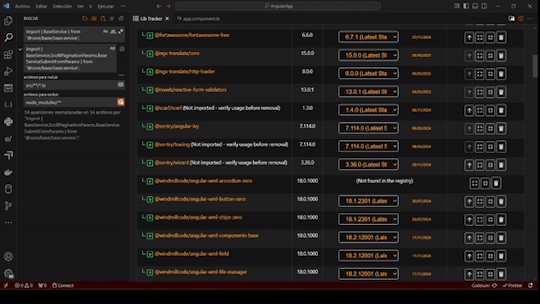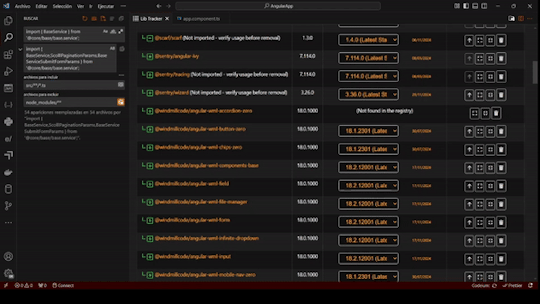
- Dependency Insights: Now see the latest available version and the recommended stable version for each dependency. The stable version aligns with your package manager's suggestions, helping you make safe updates without risking app stability.
- Enhanced Usability: Added action icons with tooltips for a more intuitive experience.
- Unused Code Detection: Identify unused packages and imports with ease.
- Edge Case Handling: Improved handling for non-registry packages, ensuring you receive as much information as possible.
Upcoming Enhancements:
- Progress Indicators: Visualize progress for checks like outdated versions, unused dependencies, and pre-fetch operations.
- Collapsible Action Icons: Streamline the interface by collapsing less frequently used tools.
- Advanced Filters: Add glob or regex-based ignore patterns for app subpath searches.
- Git-Based Backups: Explore using Git instead of the filesystem for enhanced backup reliability.
- App Detail Page Improvements:
- Display CVE information.
- Advanced search functionality.
- Responsive design with card-based layouts for better readability.
Future Goals:
- SBOM Generation: Automatically create a comprehensive Software Bill of Materials for your projects.
- License and CVE Summaries: Summarize key insights using URLs or AI-generated categories.
- Subdependency Insights: Enable direct navigation to subdependencies within the license pane.
At Windmillcode, we are committed to helping developers build secure, efficient, and scalable applications. Stay tuned for continuous updates, and let us know how we can further improve LibTracker to meet your needs.
#libtracker#vscodeextension#dependencymanagement#cvescanning#softwarebillofmaterials#sbom#securityvulnerabilities#performanceoptimization#gitintegration#licensecompliance#CVE
0 notes
Text
OWASP's Dependency-Track tool update: Key changes — and limitations

OWASP has released a new version of its dependency tracking tool, but the update is not the final word on managing software risk. https://www.reversinglabs.com/blog/owasp-dependency-track-update-key-changes-and-limitations-on-software-risk-management
0 notes
Text
The White House released the first version of the implementation plan for its National Cybersecurity Strategy on July 13, including more than 65 initiatives aimed at mitigating cyber risk and bolstering investment into cybersecurity.
👉 National Cybersecurity Strategy Implementation Plan
The plan includes sample initiatives for the five pillars of the National Cybersecurity Strategy:
Defending critical infrastructure: The Cybersecurity and Infrastructure Security Agency (CISA) will lead the update of the National Cyber Incident Response Plan that includes guidance for the roles and a coordinated manner between the government and private sector.
Disrupting and dismantling threat actors: CISA and the FBI co-chair the Joint Ransomware Task Force to combat ransomware and other cybercrime. The FBI, in collaboration with international and private sector partners, aims to disrupt the ransomware ecosystem, including virtual asset providers that enable the laundering of ransomware proceeds and web forums offering initial access credentials.
Shaping market forces to drive security and resilience: To increase software transparency and accountability, CISA continues to lead the drive to close gaps in software bill of materials (SBOM) scale and implementation.
Investing in a resilient future: The National Institute of Standards and Technology (NIST) will lead the Interagency International Cybersecurity Standardization Working Group to drive key security standardization including the post-quantum cryptography standard.
Forging international partnerships to pursue shared goals: The Department of State is set to publish an International Cyberspace and Digital Policy Strategy and work to help establish and strengthen country and regional interagency teams to facilitate coordination with partner nations.
Software supply chain is a new focus
The third pillar of the Implementation Plan focuses on securing the software supply chain, focused on software design resilience. VMware’s principal cybersecurity strategist Rick McElroy lauded this plan; he said securing cloud software — software as a service — needs special focus.
“The current NCSIP shows this administration’s commitment to cybersecurity, building on executive orders and funds dedicated to transforming and modernizing the federal government’s cybersecurity posture, which is long overdue,” McElroy said. “One consideration for this, however, is a Software Bill of Materials for Cloud software. What is a Cloud SBOM? What does that look like? Conversely, how can SBOMs be applied to practical cybersecurity defense to take advantage of that data to cut down noise?”
He added that the current working group being led by the Cybersecurity and Infrastructure Security Administration is working to address this. “But there remains a gap in SBOM discussions. SaaSBOM is a must in a cloud-first world,” McElroy emphasized.
0 notes
Link
Explore the importance of deployment security and the potential risks involved. Learn how OpsMx can help you strengthen your deployment security practices and protect your applications from threats.
#CBOM#continuous delivery security#Deployment Security#SBOM#software security#software supply chain security
0 notes
Text
EngFlow And tipi.build Reveal CMake Remote Build Execution Solution For C And C++ Community

A ground-breaking CMake Remote Build Execution (CMake RE) service in beta has been introduced by EngFlow and tipi.build in collaboration. With financial support from Andreessen Horowitz, firstminute capital, and Tiger Global, this service uses automatic caching and cloud-based distributed build execution to substantially reduce C and C++ build times to only minutes while boosting software security.
Development of C and C++ has advanced significantly with the introduction of CMake RE, powered by EngFlow and tipi.build. This Beta release aims to redefine program development, guaranteeing both speed and security, by utilizing autonomous caching and cloud-based distributed execution.
At a special session during CPPCon in Aurora, Colorado, engineers from both businesses will share in-depth insights into this new product and its capabilities.
Read More - https://bit.ly/3rIWD7B
0 notes
Text
Back to school~
Sekolah lagi.. HBD bu Syifa!


Akhirnya balik lg ke sekolah setelah 2 mingguan libur. Bismillah hari senin adem ayem sesuai jadwal jam 7.30, pake baju wara wanita udara lalu upacara. Dianter ayah, aku mnt fotoin nemo tadinya mau posting kemarin, ngga dikirim2 sampe sore sampe akupun lupa nagih hemm.
Grup ortu lagi rame jadwalin arisan dan katanya bu syifa ultah hari senin, owalaaah gmn belom beli kado dll. Diskusi dulu sm yg lain sepakat beli kado dan cake. Buibu rada slowres, bbrp ikut mikir tp yg action cuma aku dan mama mica akhirnya kami putusin weh ke pvj ke sogo lagi beliin tas kaya hadiah utk bu dina kemarin. Alhamdulillah dapet tas simple nan lutju ditengah waktu yg mepet, kami start nyari jam10an. Abistu beli cupcakes ke pompidou aja weh, disana bisa custom topper buat ucapannya, cm nunggu 5 menit. Okelah dah beres, 10 menit sbom bel keluaran sekolah kami tiba, disana udah ada 3 mama lainnya jd surprise in ber 5 aja. Langsooong eksekusi haha riweuh ku anak2 mau nyoel2 cakenya tp smuanya kompak nyanyiin lagu "selamat ultah" utk bu syifa. Yeaaay alhamdulillah beres dan berhasil..
Sekali lagi selamat ulang tahun bu syifa, guru kesayangan anak2 kami.. Semoga suka kadonya ya bu!
3 notes
·
View notes
Text
Python's PyPI Finally Gets Closer to Adding 'Organization Accounts' and SBOMs
http://i.securitythinkingcap.com/TJzGxR
0 notes
Text
Yocto, RockPi and SBOMs: Building modern embedded Linux images
https://vpetersson.com/2025/02/21/yocto-rockpi-and-sboms.html
0 notes
Text
Спасибо мой ангел.(Игорь С.)
Перейти к содержанию
Значок nexB
Мы считаем, что хорошие инструменты с открытым исходным кодом помогают вам использовать открытый исходный код.
Наша миссия — сделать программное обеспечение с открытым исходным кодом более безопасным и простым в использовании для всех, используя инструменты с открытым исходным кодом для SCA с открытым исходным кодом.
AboutCode — это наше сообщество критически важных инструментов с открытым исходным кодом для SCA с открытым исходным кодом, включая ScanCode , VulnerableCode , DejaCode и многие другие открытые инструменты и открытые данные, предназначенные для автоматизации соответствия требованиям с открытым исходным кодом и обеспечения безопасности цепочки поставок программного обеспечения.
nexB предоставляет коммерческую поддержку и услуги для стека AboutCode для организаций всех размеров. Это помогает разработчикам AboutCode продолжать сво�� миссию.
Соответствие требованиям открытого исходного кода является обязательным требованием для каждой организации.
Современные программные продукты и системы состоят из компонентов с открытым исходным кодом на 80%. Команды разработчиков программного обеспечения сталкиваются с огромными трудностями при отслеживании всех компонентов с открытым исходным кодом и сторонних компонентов, включая зависимости и обязательства по соблюдению требований — устаревшие электронные таблицы больше не могут справляться с большим объемом и скоростью изменений.
Управление компонентами с открытым исходным кодом, особенно их лицензирование и происхождение, является важнейшей частью процесса анализа состава программного обеспечения (SCA). SCA теперь является предпосылкой для современных организаций для соответствия обязательным требованиям спецификации материалов программного обеспечения (SBOM) и другим нормам. Автоматизация соответствия FOSS имеет важное значение для обеспечения целостности цепочки поставок программного обеспечения.
Организации всех размеров выбирают стек AboutCode с открытым исходным кодом для автоматизации соответствия требованиям и nexB за наш опыт работы с открытым исходным кодом .
Стек AboutCode имеет 100% открытый исходный код и использует 100% открытые данные.
Обеспечить открытое соблюдение требований.
Повышение безопасности цепочки поставок программного обеспечения.
AboutCode делает открытый исходный код более безопасным и простым в использовании, создавая модульные, лучшие в своем классе инструменты с открытым исходным кодом, данные и стандарты для анализа состава программного обеспечения (SCA).
Стек AboutCode оптимизирован для практического управления программным обеспечением с открытым исходным кодом с точки зрения лицензирования и рисков уязвимостей, чтобы гарантировать соответствие требованиям открытого исходного кода, а также повысить безопасность и целостность цепочки поставок программного обеспечения для организаций всех размеров.
Отслеживайте все компоненты — как с открытым исходным кодом, так и сторонние.
Выявите уязвимости в источниках данных.
Автоматизируйте соблюдение политик использования в масштабах всей организации.
Обеспечьте целостность цепочки поставок программного обеспечения с помощью SBOM.
Найдите открытый исходный код с помощью ScanCode.
Сканируйте свою кодовую базу непосредственно из CLI.
Или автоматизировать SCA.
Найдите компоненты с открытым исходным кодом в вашем программном обеспечении с помощью ScanCode — ведущего инструмента сканирования с открытым исходным кодом, который используют и которому доверяют 4 из 5 крупных технологических компаний:
Определите все компоненты с открытым исходным кодом и данные об их соответствии лицензиям в кодовой базе приложения.
Составьте перечень компонентов и их лицензий, который можно будет использовать в качестве основы для процесса обеспечения соответствия требованиям FOSS.
100% open source under Apache 2.0 and other business-friendly licenses with support for all programming languages and environments.
Either download ScanCode Toolkit and add it to your workflow directly or run ScanCode.io to automate the SCA process with comprehensive APIs and specific, customizable pipelines.
Find FOSS vulnerabilities across data sources, with VulnerableCode.
And improve FOSS security in modern applications.
The explosion of FOSS usage across industries requires a new approach to efficiently identify FOSS security vulnerabilities – one based on open data and FOSS tools, not proprietary and privately maintained databases built for proprietary software components.
VulnerableCode is a FOSS tool to automate search for FOSS security vulnerabilities, utilizing a free and open database of FOSS package vulnerabilities.
By collecting and parsing data from many sources, identifying packages with a standardized package-url, and accessing the data through a REST API, VulnerableCode addresses key security concerns for using FOSS code in modern applications.
Learn more about VulnerableCode
Ensure enterprise-wide compliance, automated with DejaCode.
Track all components.
DejaCode is your system of record for SBOMs.
DejaCode is the complete enterprise-level open source license compliance application, powered by ScanCode:
Run scans and track all the open source and third-party products and components used in your software.
Define usage policies at the license or component level, and integrate into ScanCode to ensure compliance.
Capture software inventories (SBOMs), generate compliance artifacts, and keep historical data.
Ensure FOSS compliance with enterprise-grade features and integrations for DevOps and software systems.
Learn more about DejaCode
Run the complete AboutCode stack, on-premises.
✔ Receive ongoing support for software composition analysis and open source compliance software and processes.
✔ Resolve problems and bugs with service level agreements to maintain production use.
✔ Pull up-to-date data feeds for production use.
Get questions answered by the experts, in private channels.
✔ Gain direct access to the maintainers for insights and advice on securing software supply chains with FOSS and controlling risks and costs, via email, live chat, voice, and video.
✔ Get explicit guidance on installation, upgrades, and backups; and how to use particular features.
✔ Your support supports the maintainers to ensure that your OPSO and supply chain process investments are safely backed by best-in-class tools that are sustained and maintained.
Need AboutCode services beyond support?
Consulting services
nexB’s experts can join your implementation project to ensure successful deployment of the AboutCode stack and secure your software supply chain.
Accelerate new feature development and enhancements from the public roadmap.
AboutCode as a Service
Начните работу со стеком AboutCode без проблем с хостингом и инфраструктурой с помощью AboutCode SaaS.
Или мы можем запустить, эксплуатировать и обслуживать стек AboutCode (или отдельные компоненты) в вашей инфраструктуре или облаке.
Аудиты с открытым исходным кодом
Комплексный аудит анализа состава программного обеспечения (SCA) включает в себя комплексный подход к комплексной проверке приобретений или инвестиций.
nexB проанализировал миллионы строк кода за более чем 15 лет опыта.
Чтобы понять, что находится в их программном обеспечении, компании всех размеров используют nexB.
Я определенно запомню nexB, так как я был очень впечатлен вашим сканированием и тем, насколько гладко прошел процесс.
Берт Хьюберт
Технический директор и основатель Fox-IT
Берт Хьюберт
Спасибо за экспертное руководство, которое нам предоставила компания nexB. Это значительно упростило весь процесс оценки, и это было именно то, что нам было нужно. Мы определенно рекомендуем nexB в качестве независимой третьей стороны для комплексной проверки слияний и поглощений с открытым исходным кодом.
Стив Абрахам
Руководитель отдела корпоративного развития и стратегии в Box
Стив Абрахам
Работая с nexB с 2008 года, они являются нашим основным поставщиком услуг для аудита выпуска продуктов. Они помогли нам улучшить наш процесс благодаря их продукту DejaCode. Я бы настоятельно рекомендовал nexB и DejaCode каждому специалисту по программному обеспечению, отвечающему за соответствие требованиям лицензирования.
Диана Андерсон
Старший директор по соответствию программного обеспечения в ARRIS
Диана Андерсон
Мы все были очень впечатлены качеством и глубиной вашего опыта и технологий, реагированием на наши проблемы, способностью решать проблемы и результатом работы.
Сайрус Вадиа
Заместитель генерального юрисконсульта по стратегической интеллектуальной собственности в Pivotal
Сайрус Вадиа
Спасибо, нам было приятно работать с вами и вашей командой, действительно профессиональный и впечатляющий анализ.
Ричард Грондин
Старший директор группы безопасности данных в Informatica
Ричард Грондин
Я определенно запомню nexB, так как я был очень впечатлен вашим сканированием и тем, насколько гладко прошел процесс.
Берт Хьюберт
Технический директор и основатель Fox-IT
Берт Хьюберт
Спасибо за экспертное руководство, которое нам предоставила компания nexB. Это значительно упростило весь процесс оценки, и это было именно то, что нам было нужно. Мы определенно рекомендуем nexB в качестве независимой третьей стороны для комплексной проверки слияний и поглощений с открытым исходным кодом.
Стив Абрахам
Руководитель отдела корпоративного развития и стратегии в Box
Стив Абрахам
Обеспечение соответствия лицензии на программное обеспечение может оказаться сложной задачей.
Мы можем помочь.
Начните сканировать свой код с помощью ScanCode
Автоматизируйте соответствие FOSS с помощью DejaCode
Обращайтесь к нам за помощью по любым вопросам
Значок nexB
Знайте, что находится в вашем программном обеспечении.
Линкедин Твиттер Ютуб Гитхаб
Программное обеспечение
СканКод
УязвимыйКод
DejaCode
Услуги
Поддерживать
SaaS
Консалтинг
Ресурсы
О сообществе Code
Блог
Документация
Видео
Компания
О nexB
Клиенты
Карьера
Сообщество FOSS
Связаться с нами
© nexB Inc. Все права защищены. | Политика конфиденциальности | Условия использования | Кредиты









Пробы but you're not sex b12
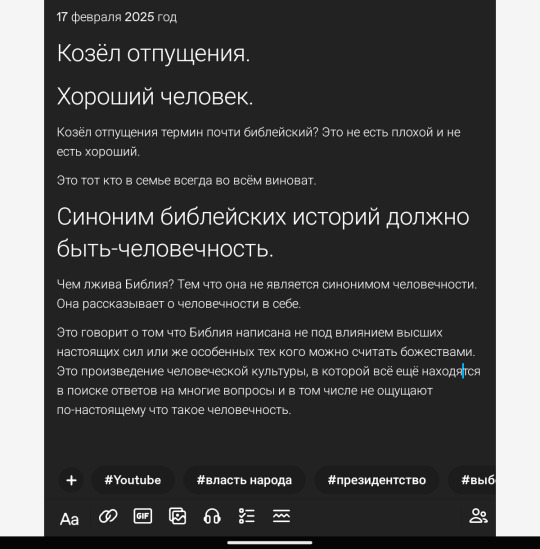
Когда у вас нет семьи это значит что ваш код украли.
Меня использовали как хотели каждую мою клеточку.
Да меня не насиловали как вас, меня запугивали, до меня дотрагивались, мне определяли чёткие границы словно я скот за забором.
Почему мне не насиловали? Почему ваш местный насильник меня не насиловал? Ничего страшного.. куда ты пережила он наблюдал как другие меня насиловали.
Это такое наслаждение играться со своей невестой, ваш демон игрался со своей невестой подобным образом. Затрагиваюсь Не дотрагивался до неё до свадьбы, но позволял с ней делать всё что угодно остальным.
Считаете я должна такого полюбить?
10:21
Любая из вас, даже любой из вас согласится любой из вас за власть за деньги за всё за всё.. обломался? Я заработала са��а эти деньги и власть у меня и так была.
Всё что тебе нужно было делать Это красиво ухаживать за мной и защищать ото всех, заботиться обо мне и не допустить того что со мной сделали.
Представляешь всего-то надо было быть счастливым рядом со мной и делать счастливой меня.
Так может только настоящее дело настоящий демон, как может только верховный правитель Так может только сила Так может только мужчина.
Умный, властный, сильный, настоящий.
И не важно какого вы пола понимаете здесь это неважно.
Быть мужчиной или женщиной это подчёркивает быть человеком это очень круто.
А всё что вы наделали и натворили попытались только внести изменения в программное обеспечение и по итогу только всё разрушили.
Нельзя брать с меня что-то и ничего не давать взамен я должна восстанавливаться я должна быть ценной цельной оставаться.
Семья.
Для того чтобы вывести на чистую воду как говорят демона мне нужно было бы отказаться от Люцифера. Мне нужно было внутри себя больше не желать его вашего Люцифера тем какое у него лицо и тело сейчас сколько у него в окружении таких как я типа.
То есть я должна была лишиться своё ради того чтобы вы просто доиграли до конца. Там известен было этот демон, вам всё это было известно но вам надо было поиграться.
Игрались бы со своими близкими и любимыми. До меня докопались. До меня докопались. Как я теперь могу смотреть такими же влюблёнными глазами на него после всего и как у меня может быть выбор между одним и другим когда они одинаковые одинаково паршивые плохие.
Что касается семьи. Зачитаю просто по бумажке то что написала ранее ранее до ваших раскладов.
Родители в кавычках были готовы меня подставить, чтобы защитить Андрея.
Читаю
Отец хотел ребёнка ещё одного для того чтобы этот.. в общем я родилась.. чтобы стать козлом отпущения в семье.. он не любил меня, с появлением брата я автоматически превращалась в козла отпущения. Мать биомать такая же как биотец она долго откладывала как бы в кавычках это, думаете она любила меня потому что не хотела чтобы я стала козлом отпущения? Она знала что ещё один ребёнок рождённый поспособствует тому что она заболеет это приведёт к смертельному исходу возможному смертельному исходу. А родить.. родить ещё одного ребёнка и сделать меня козлом отпущения это вообще не значимо было для неё. Но такое решение помогло бы защитить их всех, не меня.
Почему я просила чтобы они родили брата? Хотела либо брата или сестру. Если бы они родились сестру мы бы защищали друг друга но они родили мальчика, сбылось то что сбылось и должно было сбыться это их договор это их соглашение.
Я одна.
А потом несу коррективы мне это всё И сейчас не хочу Я вообще об этом говорить какое смысл вообще во всём этом какой смысл
Биомать хотела мальчика родить у неё должен был бы быть сын, родилась я понимаете то есть они заключают сделку договор но чувствуют несмотря на потерю памяти и в состоянии гипноза они чувствуют, что я не то что им надо и с этим чувством живут не понимаю толком почему так то есть, ничего не делала такого чтобы быть козлом отпущения не было ни одной причины меня не любить.
0 notes
Text
LibTracker Updates 12/2/24: Get to personally know your apps with this simple SBOM Tool
* Greetings everyone working on my LibTracker Vscode Extension. Get to personally know your apps with this simple SBOM Tool. View at a a glance and fix outdated versions, security vulnerabilities and problematic licensing.
* You can access here https://marketplace.visualstudio.com/items?itemName=windmillcode-publisher-0.lib-tracker.
# New Features
- Smart Expand/Collapse: Expand/Collapse all items in a category when opened. Expand all items in a category when opened.
- get license info about every version of every package of the app along with its subdependencies
- toggle select all apps in project detail page
# Next Goals
- recursion exclusion list
- (mabye) workspace folder
- (depends on capabilbility of vscode api to access vscode profiles)
- git backup changes
- app detail page
- cve info
- search (root row is possible but useless search every nested child row)
- responsiveness app detail page can tabulator turn to series of cards
- Generate SBOM
- URL or AI summary of categories and names for licenses and CVES

- (if possible) click on subdependency in license pane will take you to its location in table
#LibTracker#SBOM#DependencyManagement#SoftwareLicenses#SecurityVulnerabilities#VisualStudioCode#VSCodeExtensions#SoftwareDevelopment#OpenSource#SoftwareEngineering#ApplicationManagement#DevTools#GitIntegration#CVEInsights#SoftwareBillOfMaterials#DeveloperTools
0 notes
Text
SBOMs and your org: Go beyond checkbox security to manage risk

It's a losing proposition to generate SBOMs just to land a federal contract or meet an industry requirement, without analyzing and acting on its data to improve software security. https://tinyurl.com/yncw4688
0 notes
Text
A software bill of materials (SBOM) is a list of components included in software. Software vendors often combine open source and commercial software components to create a product; the SBOM describes the components within the product.
This list, maintained on GitHub, is a compilation of various information about SBOM.
What an awesome list!
0 notes
Text
Rust Will Explode, SBOMs Will Be Duds: Open Source Predictions - The New Stack
0 notes
Link
¿Qué es un SBOM? Lo que Necesitas Saber | #ciberseguridad #seguridadinformatica #seguridadonline
0 notes