#Quantum Computer
Explore tagged Tumblr posts
Text
Quantum computing
#wafer#semiconductor#silicon wafer#quantum computing#quantum computer#wikipedia#wikipedia pictures#tech#technology#techcore#technologycore#computing#computer engineering#science
194 notes
·
View notes
Text

In some respects, one can think of a quantum computer today as being analogous to an analog computer from years ago. The cooling is key to reduce energy and thus vibration in the system. If a quantum computer is run for too long the processor heats up and the noise in the results increases. So sensitive is the computer to heat or vibration that at the $150 million Nanoscience Hub at Sydney University, scientists have to use stairs rather than the lifts because the quantum computer would feel the vibration of the lifts in the building and produce meaningless results. Thus in Devs, the quantum computer main lab space is depicted as a suspended hovering isolated block, inside a bunker style building. This art directed visual feature, like so many in Devs, had one foot in reality and another in fiction.
#devs#devs 2020#alex garland#quantum physics#quantum computing#quantum mechanics#science fiction#Sonoya Mizuno#Nick Offerman#Jin Ha#Zach Grenier#Cailee Spaeny#Stephen McKinley Henderson#Karl Glusman#Alison Pill#software engineering#free will#determinism#quantum computer#dneg#amaya#tech company#faraday cage#many worlds#De Broglie–Bohm theory#science#physics#Socratic method#philosophy#special effects
10 notes
·
View notes
Text

3 notes
·
View notes
Text

Attack for ~Amethyst on Artfight!
#unionised#art#yanska art#digital art#oc#original character#procreate#tech#electronics#quantum computer#digital drawing
16 notes
·
View notes
Text
The main question is not whether the quantum computer will break Bitcoin encryption and other digital currencies. We already know it will happen. The essential question is: Will digital currency bear the speed, the short time with which the quantum computer will break its encryption?
3 notes
·
View notes
Text
Was Forest’s original plan always to project himself into the machine at the end? It’s always his plan, because this is how he gets to actually be with his daughter again, rather than just watch his daughter. The thing that changes for Forest is that he has adhered to a view of quantum mechanics that does not include many worlds. There’s just one world, which means he can recreate his daughter exactly as she was, and rejoin his life exactly as it was without the car crash happening. What he is forced to accept in the end is that there will be versions of him that can experience that, but also versions that will not experience that. So he has a more poignant end result than the one he was looking for.
So even though he believes in determinism, Forest was going to be able to craft a version of reality that was exactly the same except for the car crash, and go there? That’s exactly right. In effect, what he’d be able to do is rejoin that timeline, but not make the phone call to his wife and not, therefore, be the cause of the car crash. And then he’d be able to experience the unfolding of his life exactly as if the thing never happened. And within that state, it would be a world of equal status to the world that you and I are talking in right now. The problem is that the world is not the simple, deterministic world he wants it to be. So he has to accept a different version.
#devs#devs alex garland#alex garland#simulation#emulation#many worlds#theoretical physics#physics#quantum computer#quantum computing#spoilers#devs spoilers#determinism
3 notes
·
View notes
Text
Quantum computing | Why Need | How does Quantum Computers Work?
What is Quantum computing? Quantum computing is a rapidly growing technology that uses the laws of quantum mechanics to solve complex problems that are not easy for supercomputers. But why do we need Quantum Computers? There are some problems for which even supercomputers are not enough. When engineers faced challenging difficulties in solving some issues, they used supercomputers.…

Classical computers struggle with complex problems like encryption, drug discovery, and AI modeling due to their limited processing power. Quantum computers can solve problems exponentially faster, making them essential for scientific breakthroughs and advanced computing.
How Do Quantum Computers Work?
Unlike classical computers that use bits (0 or 1), quantum computers use qubits, which can exist in multiple states (superposition) and interact through entanglement. This allows them to perform complex calculations simultaneously, making them incredibly powerful for optimization, cryptography, and simulations.
#quantum computing#quantum computer#quantum computing explained#quantum#quantum computing news#quantum computing hype#what is quantum computing#quantum physics#quantum mechanics#quantum computer explained#quatum computing#learn quantum computing#quantum computing course#quantum computing expert#quantum computing qubits#quantum computing design#quantum computing bubble#quantum computing lecture#quantum computing dangers#future of quantum computing
2 notes
·
View notes
Video
youtube
A discussion with Sankar Das Sarma and Chetan Nayak
Mar 14, 2022
Dr. Sankar Das Sarma, a Distinguished University Professor of physics at University of Maryland joins Chetan Nayak, Distinguished Engineer of Quantum at Microsoft to discuss Microsoft’s unique approach to building a fully scalable quantum machine.
#youtube#Chetan Nayak#Sankar Das Sarma#Topology#Quantum Computer#Quantum Computing#Topological Quantum Computer
2 notes
·
View notes
Text

6 notes
·
View notes
Text
I didn't know what I was seeing myself. Lol
That picture of Biden looking at a quantum computer and being unable to grasp the true form of what he's seeing

To be fair that's how I would I react too
44K notes
·
View notes
Text

IBM Q System One
#ibm q system one#quantum computing#quantum computer#ibm#wikipedia#wikipedia pictures#tech#technologycore#techcore#technology#International Business Machines Corporation#computer science#computer engineering
39 notes
·
View notes
Text

In Devs, the onset golden quantum computer prop was a practical build and quite substantial, weighing approximately half a ton. The onset design referenced real Quantum computer systems from companies such as IBM, and Google, except in the real world, the ‘chandelier’ would be encased in a cooling box since most of the gold apparatus one sees is related to cooling the quantum computer not any actual computation. “It was massive, but all of that quantum computer is practical. That prop should now be in an art gallery. It was stunning,” says Whitehurst.
The majority of the visual effects were created by DNEG in London which has a long history in dealing with Sc-Fi content with respect and tremendous visual fidelity. Films such as Inception and Interstellar have gained the company both Oscars and genuine respect from the science community.
#devs#alex garland#quantum physics#quantum computing#quantum mechanics#devs 2020#science fiction#Sonoya Mizuno#Nick Offerman#Jin Ha#Zach Grenier#Cailee Spaeny#Stephen McKinley Henderson#Karl Glusman#Alison Pill#software engineering#free will#determinism#quantum computer#dneg#amaya#tech company#faraday cage#many worlds#De Broglie–Bohm theory#science#physics#philosophy#special effects#practical effects
8 notes
·
View notes
Text

4 notes
·
View notes
Text
Looking like a TOS-era warp core.
why did no one tell me quantum computers looked like that
#quantum computer#things that look like star trek#this is a warp core and nobody can convince me otherwise
151K notes
·
View notes
Text
Post Quantum Security: Future-Proof Data From Quantum Threats

What becomes of encryption today when quantum computers are capable of cracking it? As we race toward a future driven by the next generation of technology, one urgent question hangs over cybersecurity. The solution is to use Post Quantum Security, a new generation of cryptography capable of resisting the brute power of quantum computing.
In a world where sensitive information — from personal identities to national secrets — is increasingly vulnerable, Post Quantum Security is not just an upgrade, but a necessity. This article explores how to future-proof your data and systems against quantum threats.
Understanding the Quantum Threat Landscape
The Birth of Quantum Computing
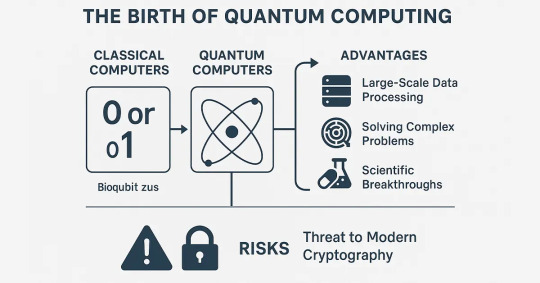
Quantum computing seems to quickly evolve from a new scientific theory into a change- and results-driven technology. Old computers use the binary digit as 0 or 1, whereas quantum computers operate using qubits, which can occupy several states simultaneously owing to superposition and entanglement. As a result, such cutting-edge machines provide an exceptional ability for quick, advanced computations.
Quantum computing excels using its capability of handling large data volumes and solving issues too complicated for existing best classical supercomputers. In particular, quantum computers can effectively address complex logistics tasks, analyze the structure of molecules to invent new medicines, and enhance the approach undertaken in financial forecasting.
But with that potential comes a warning: quantum computing puts modern cryptographic systems at serious risk. The same computational benefits that make quantum computers a breakthrough for scientific research are the ability to compromise classical encryption methods used in our online security.
Implications for Current Cryptography
The dominant modalities of the modern digital infrastructure are based on the use of public key cryptography, and such systems as RSA and ECC are among the most widespread representations that people use. These encryption systems are based on mathematically difficult problems for conventional systems — factorizing huge numbers or solving discrete logarithm problems. These are exactly the sorts of problems a quantum computer is designed to demolish with impunity using expert algorithms.
Shor’s Algorithm, created in 1994, is likely the most famous quantum algorithm that targets RSA and ECC directly. It can factor big numbers exponentially quicker than the best-known classical algorithms. When quantum computers are ready — usually called “quantum supremacy” — they will be able to decrypt secure communications, financial transactions, and private information that are now thought to be secure.
Another significant algorithm, Grover’s Algorithm, doesn’t shatter symmetric crypto systems but narrows down their security levels significantly. It indeed cuts a symmetric key’s bits in half, so 256-bit keys would provide only 128-bit security in the quantum age. Less devastating than Shor’s impact on asymmetric crypto, though, Grover’s Algorithm does mean a reconsideration of the dominant symmetric encryption algorithms.
This new threat brings to the forefront the need for post quantum security solutions in an immediate manner. Unlike conventional cryptographic practices, post quantum security is about designing and deploying algorithms that are secure even when quantum computing resources are available. These algorithms are based on challenging mathematical problems for which quantum computers are not yet known to solve efficiently.
The Urgency for Transition
Post quantum security is not a theoretical concept; it’s an urgent, real-life issue. RSA- or ECC-breaking large-scale quantum computers don’t exist yet, but breakthroughs are on the move. The collaborative efforts of governments, corporations, and research bodies across the globe to create quantum technology imply that these machines will soon become real.
There is a dire need to secure the digital infrastructure of organizations, for when quantum technology is available. Transitioning to post quantum security protocols is difficult and time-consuming, not only swapping cryptographic algorithms but also rewriting software, hardware, and communication protocols. Waiting for fully functional quantum computers may expose systems and data to attacks.
Further, hacked encrypted data today can be stored and decoded at a later date after computers develop the capability — the “harvest now, decrypt later” attack. As a countermeasure post quantum security ensures valuable information is safeguarded both today and in the foreseeable future.
The U.S. National Institute of Standards and Technology (NIST) has already started standardizing quantum-resistant algorithms with its Post-Quantum Cryptography Standardization Project. Organizations can standardize their security approach with international best practices for post quantum security using NIST-recommended solutions.
What Is Post Quantum Security?
Post Quantum Security is a term that is used to refer to cryptographic methods that are resistant to attacks carried out by entities that can run large quantum computers. Besides, this category includes the quantum-resistant hash algorithms, encryption algorithms, and digital signature algorithms. These systems are being standardized by efforts such as NIST’s Post-Quantum Cryptography Project.
Embracing Post Quantum Security guarantees that long-lived sensitive information, such as medical records or financial contracts, is still protected even when intercepted today and decrypted in the future quantum world.
ncog.earth incorporates Post Quantum Security into its core blockchain protocol. It provides data security for decades in a post-quantum secure environment.
Core Principles of Post Quantum Security
Below are the fundamental principles that constitute this new field and how they interact with each other to protect digital property during the era of quantum computing.
1. Quantum-Resistant Algorithms
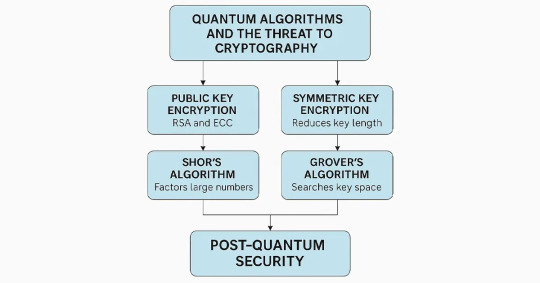
Post quantum security is centered around quantum-resistant algorithms, which are designed to stand up to attacks both from traditional attack methodologies as well as attacks performed with a quantum computer. These algorithms don’t depend on the weak assumptions of the classical encryption methods like RSA or ECC, which can be attacked and broken by quantum algorithms like Shor. Post quantum security instead depends on mathematical problems with cryptographically amicable properties that are difficult for an efficient quantum computer to solve.
Among the most promising quantum-resistant solutions are-
Lattice-based cryptography: Lattice-based cryptosystems rely on the computational subtlety of such problems as the Shortest Vector Problem (SVP) and the Learning With Errors (LWE) problem. They are classical and quantum resistant and thus well positioned to protect encryption, digital signatures, and key exchanges.
Hash-based cryptography: Founded on extensively studied hash functions, this method effectively generates secure digital signatures. Because hash functions are one-way functions, they are extremely secure even against quantum attackers.
Code-based cryptography: Founded on error-correcting codes, this method has stood the test of time for more than four decades. It is strong, well-established, and extremely efficient for encryption and digital signatures in a post quantum security scenario.
Multivariate polynomial cryptography: The hardness of these problems is essentially dependent on the intricacies of solving multivariate quadratic systems of equations, which are intractable for quantum and classical systems.
Deployment and selection of these algorithms are being standardized by bodies such as NIST, which is finalizing a suite of post-quantum cryptographic standards for ease of global implementation of post quantum security protocols.
2. Forward Secrecy
Forward secrecy is yet another significant post quantum security parameter. In the conventional crypto paradigm, it might be possible that breaking a private key today can expose attackers to decrypted communications in the past and future, and it is highly risky if, in a quantum paradigm where harvested encrypted data from today can be broken using quantum computers in the future.
Post quantum security addresses this issue by guaranteeing that even when an encryption key is finally breached, past messages cannot be decoded after the fact. The method is to repeatedly generate ephemeral keys that don’t survive and aren’t easily linked up with each other. Forward secrecy is significant not just for private individuals but for protecting business networks, government files, and money networks as well.
Essentially, forward secrecy reconfigures the way we approach long-term data secrecy, particularly considering the danger represented by “harvest now, decrypt later” attacks facilitated by quantum advancements. In post quantum security, it’s a solid pillar of real future-proofing.
3. Hybrid Cryptographic Models
With the indefinite time frame of quantum progress, most organizations are taking a hybrid approach that brings together classical and post-quantum-resistant cryptography. The cryptographic models are created to fill the security gap during the transition phase when the existing traditional algorithms exist side by side with the post quantum security algorithms.
In a hybrid method, two sets of algorithms are run in parallel. One set offers backwards compatibility with current infrastructures, and the other offers immunity to future quantum attacks. As a simple example, an end-to-end communication channel could employ RSA in conjunction with a lattice-based encryption scheme at the same time. This means that even if the classical part is compromised in the future, the post quantum security layer still protects the underlying data.
This method has some advantages-
Gradual roll-out: Businesses can deploy systems gradually without affecting current services.
Redundancy: Having several levels of encryption offers a backup in case one algorithm is compromised.
Testing ground: Testing the deployment of quantum-resilient tools identifies real-world problems and solutions before mass deployment.
Hybrid deployments are not long-term, but they are essential stepping stones. With increasing trust and confidence in post quantum security technology, hybrid deployments will ultimately make way for fully quantum-resistant architectures.
Why Businesses Must Act Now

In the unfolding digital age, while cyberattacks increase in scale and sophistication, quantum computing’s emergence is at once a dazzling technological advancement and an intrinsic cybersecurity challenge. To companies — particularly those holding sensitive customer data or conducting business in highly regulated industries — the time to prepare is not in the future but today. Post-quantum security is no longer an idealistic aspiration but rather a concrete reality. Forward-thinking companies need to take action today to ensure that they will be able to withstand future cryptographic shocks.
Quantum Threats Are Nearer Than They Seem
The power of quantum computers is that they can use superposition and entanglement to exceed classical machines in certain forms of mathematical operations. The possible advantages that such technology could offer to drug discovery and logistics, as well as machine learning, are substantial, but this danger also undermines the encryption protection that enshrines secure digital communication, financial systems, medical records, and contracts.
Algorithms such as RSA and ECC, the basis of modern public-key cryptography, could be made obsolete by quantum algorithms such as Shor’s. In practical terms, what that would mean is to make information currently encrypted under these systems decrypted within seconds if there existed a sufficiently large quantum computer. The potential effect would be disastrous to companies experiencing huge-scale data breaches, litigations, and erosion of customer confidence.
That’s why post quantum security must be implemented far ahead of the wholesale arrival of quantum computing. Companies that delay are not only taking a risk — they’re deliberately putting their businesses, data, and reputations in long-term jeopardy.
Data Longevity Brings the Risk into the Present
One of the least considered measures of quantum risk is data longevity concern. Whereas real-time data spoils at a fast pace, some forms of data — medical history, legal papers, government agreements, and intellectual property — are priceless for decades or years. If today a cyberattacker got hold of encrypted information, they would be unable to decipher it. But with the advent of quantum power, the same information can be accessed in the foreseeable future. The label is also applicable when talking about attacks referred to as “harvest now, decrypt later”.
On this front, post quantum security plays a twofold role: it safeguards against the threat at hand, but also against potential attempts to decrypt in the future. For businesses tasked with securing data over the long term — insurance providers, banks, and law firms, for example — it is critical that it is pre-emptive. Delaying the implementation of quantum-resistant practices creates a bombshell situation where encrypted files stored could be cracked open at any moment.
Consumer confidence is perhaps the most precious asset of the online marketplace. With high-profile breaches becoming the norm, customers are growing more attuned to where their information lives and how it is secured. Companies that act early to publish quantum security standards communicate that they are serious about leading-edge data protection and customer privacy. This method contributes to the creation and preservation of a reliable brand and earns the loyalty of the clients.
Additionally, regulatory landscapes are changing. Global data privacy legislation like the GDPR, HIPAA, and CCPA demands secure data security procedures, and compliance systems will shortly be following close behind in counteracting quantum-age attacks. Adopting post quantum security today allows organizations to protect themselves against future compliance mandates and sidestep the prohibitively cost-intensive exercise of currency flows.
Smooth Transition Through Strategic Planning
Post quantum migration is not a flip-of-the-switch transition — it requires thoughtful planning, testing, and staged deployment. Businesses must assess their existing cryptographic infrastructure, identify vulnerable endpoints, and decide which quantum-resistant algorithms will best meet their operational needs.
Fortunately, most businesses are not beginning from the ground up. Hybrid crypto designs — blends of conventional and quantum-resistant solutions — permit phased and secure adoption. Post quantum security is viable through hybrid approaches that support organizations in adopting post quantum security without sacrificing current system performance or compatibility. Phase by phase is the way, causing as little disruption as possible while providing security for important information at each stage.
They also must spend on training and awareness programs. Decision-makers, developers, and cybersecurity staff must be made aware of the effects of quantum risk and the pragmatic actions that go into minimizing it. Post quantum security incorporated into cybersecurity roadmaps now will have companies not lag when the quantum era is in full force.
Building Quantum-Resilient Ecosystems
The truth is, cybersecurity is not an isolated practice. A majority of businesses employ third-party suppliers, cloud computing providers, and digital platforms that touch or have access to sensitive information. Having a secure digital environment is a matter of discussing post quantum security with partners and suppliers.
Leading organizations are now starting to measure their supply chains and expect quantum-readiness from their partners. Organizations can minimize systemic vulnerabilities and foster increased collective resilience by establishing post-quantum security as an expectation within ecosystems.
Integrating Post Quantum Security into Your Infrastructure
With continued advances in quantum computing, the danger that it poses to classical cryptographic schemes is more dire. Companies and enterprises cannot afford to wait. There is a need for a transparent and systematic adoption of post quantum security protocols into existing IT infrastructures so that data confidentiality, integrity, and availability are preserved under quantum computing. This has to be done with a strategic roadmap of action covering technology and operations transformation across the digital landscape.
For this transition to be made possible, organizations can utilize a multi-step process that will establish quantum resilience without disrupting essential services. Below, we outline the four main steps of incorporating post-quantum security in your infrastructure.
Audit Your Current Cryptographic Inventory
Before any change is implemented by companies, they must start by defining the scope and utilization of current cryptographic assets. Any effective post quantum security project is based on a thorough cryptographic inventory. This process entails determining where and how cryptographic algorithms are utilized — on SSL/TLS certificates, database encryption, secure email, authentication protocols, digital signatures, API gateways, mobile applications, VPNs, and IoT devices.
This audit must encompass-
Encryption Algorithms Used: Assess if systems are using RSA, ECC, or other vulnerable algorithm-based encryption.
Key Sizes and Expiration Policies: Document existing key sizes and assess how often they are being replaced.
Cryptographic Libraries and APIs: Check for dependencies and assess compatibility with quantum-resistant alternatives.
Certificate Authorities and Issuance Policies: Examine methods of distributing, retaining, and withdrawing digital certificates.
When such data is analyzed, it is possible to identify weak points and establish priorities for strategic transition to post-quantum security. Notably, the process helps organizations to review the data lifecycle and determine long-term sensitive data that needs to be secured today against tomorrow’s quantum decryption power.
Select Quantum-Resistant Algorithms
After identifying your cryptographic footprint, the next step is to select quantum-resistant alternatives. NIST has worked with others to initiate multi-year standardization efforts that will evaluate and promote post-quantum cryptography algorithm recommendations. These algorithms are designed so that they can resist attack by both classical and quantum computers and include key encapsulation processes and digital signature protocols.
Among the most promising contributions to come out of the NIST project are-
CRYSTALS-Kyber (for public-key cryptography and KEM)
CRYSTALS-Dilithium (for digital signatures)
FALCON and SPHINCS+ (signature schemes with performance profiles of differing types)
In choosing algorithms, implementations must consider performance, resource efficiency, complexity to implement, and the extent to which the solution they choose fits their infrastructure. For instance, IoT devices that have little power may need lightweight algorithms, but high performance servers are more than capable of handling complex computing activities.
Selection of the best algorithms is immensely important for effective post quantum security integration. Future-proofing should also be a consideration for security teams as quantum-resistant cryptography develops. Modular architecture solutions for cryptography allow for a seamless switch or upgrade of algorithms as new standards become available.
Use Hybrid Cryptographic Systems
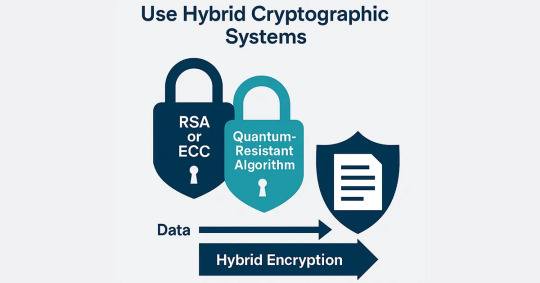
It is not necessary to move away from classical to quantum-resistant cryptography completely. One of the most recommended practices while transitioning to post quantum security is the use of hybrid cryptographic systems. These use current (classical) cryptographic algorithms and couple them with quantum-safe algorithms to provide a multi-layered defense.
In a hybrid system, data is encrypted with both RSA (or ECC) and a quantum-resistant algorithm. It makes the system both backward compatible as well as future-proof against attacks based on quantum. Although quantum computers are unable to break today’s classical encryption now, hybrid encryption protects the data from being exposed in the future, most beneficial for long-shelf-life sensitive data.
Hybrid deployments also enable companies to pilot the in-the-wild usage of post-quantum-safe algorithms without removing trusted current defenses. Phase-in of post quantum security in this manner prevents service disruption, lowers operational risk, and enables incremental testing and tightening.
Key libraries and frameworks increasingly start to include hybrid support. For example-
OpenSSL (with quantum-safe branches)
Cloudflare and Amazon Web Services, which have begun to experiment with post-quantum TLS deployments
Mozilla and Google, pioneering early hybrid deployments in their browsers
These initial hybrid adoption attempts show the growing traction for post-quantum security and offer in-the-wild blueprints for companies willing to make the transition.
Upgrade Key Management Systems (KMS)
The key to the efficiency of encryption lies entirely in the responsible use of its keys. Infrastructures that are quantum-resilient need updates to legacy Key Management Systems (KMS) to accommodate the special needs of post quantum security…
#post quantum#post quantum security#technology#ncog#post quantum blockchain#post quantum encryption#post quantum cryptography#decentralized database#quantum computer#quantum computing#quantum computers#post quantum secure blockchain#rsa#shor algorithm#quantum-resistant cryptography#ECC
1 note
·
View note




