#Privacy program management software
Explore tagged Tumblr posts
Text
The Role of Encryption in Modern Data Protection Strategies Discover how GoTrust's data protection management software uses advanced encryption for robust data security. Learn more today!
#Data Privacy Management Software#Data Privacy Software Solution#Privacy Compliance Software Solution#Data protection management software#Privacy program management software#Best privacy management software#Data Privacy Software Solutions
1 note
·
View note
Text
truly so baffling to me to hear people complain about their electronics like my coworker was complaining that her 2017 Mac was so slow its barely functional and it’s like what do you MEAN your 8 year old Mac is dead? mine is from 2013 and runs flawlessly?? what are you doing to your $1000 machine ??? filling it with peanut butter and TikTok viruses?????
#and I’m fairly callous with mine. I’ll download anything. (although I am a tech guy so like I can think critically but#I do tend to download a bunch of random shit from like Reddit threads and forums lol) and yet my Mac is like practically mint.#his only crime is sometimes he dies at 20% and gets hot and can’t run 32bit programs (<apple’s fault)#he’s still running max graphics stardew valley with 900 mods and Minecraft mid graphics with 200 and like 30fps (<good for modded mc)#Apple truly making solid products considering every midrange windows pc I’ve used became garbage in like 4-5 years 🫥#ive spent more on my 4 windows PCs in the last 20 years than this one Mac that will probably keep trucking for another 10 years.#Like sorry im not an apple freak but considering how many devices I’ve bought used and fiddled with…… kind of incredible how Apple has#somehow managed to come out on top in the longevity/ease of use/privacy departments.#if windows didn’t force you to update and use their bloatware bullshit and not let you CONTROL THE MACHINE YOU BOUGHT id be less mad#but every time I use win 10 or 11 I want to shoot myself in the head. win1011 softwares practically feel like malware.#a day in the life of steeve#only reason I would ever have a windows device is to play sims 2. (works on Mac but no utilities which are indispensable these days).#and I’m thankful Emily has a top tier gaming laptop for me to use for sims <3#if I ever need another pc I think I’ll venture into Linux. my steam deck runs Linux and it feel so pleasant and friendly compared to win11.
6 notes
·
View notes
Text
Just a bunch of Useful websites - Updated for 2023
Removed/checked all links to make sure everything is working (03/03/23). Hope they help!
Sejda - Free online PDF editor.
Supercook - Have ingredients but no idea what to make? Put them in here and it'll give you recipe ideas.
Still Tasty - Trying the above but unsure about whether that sauce in the fridge is still edible? Check here first.
Archive.ph - Paywall bypass. Like 12ft below but appears to work far better and across more sites in my testing. I'd recommend trying this one first as I had more success with it.
12ft – Hate paywalls? Try this site out.
Where Is This - Want to know where a picture was taken, this site can help.
TOS/DR - Terms of service, didn't read. Gives you a summary of terms of service plus gives each site a privacy rating.
OneLook - Reverse dictionary for when you know the description of the word but can't for the life of you remember the actual word.
My Abandonware - Brilliant site for free, legal games. Has games from 1978 up to present day across pc and console. You'll be surprised by some of the games on there, some absolute gems.
Project Gutenberg – Always ends up on these type of lists and for very good reason. All works that are copyright free in one place.
Ninite – New PC? Install all of your programs in one go with no bloat or unnecessary crap.
PatchMyPC - Alternative to ninite with over 300 app options to keep upto date. Free for home users.
Unchecky – Tired of software trying to install additional unwanted programs? This will stop it completely by unchecking the necessary boxes when you install.
Sci-Hub – Research papers galore! Check here before shelling out money. And if it’s not here, try the next link in our list.
LibGen – Lots of free PDFs relate primarily to the sciences.
Zotero – A free and easy to use program to collect, organize, cite and share research.
Car Complaints – Buying a used car? Check out what other owners of the same model have to say about it first.
CamelCamelCamel – Check the historical prices of items on Amazon and set alerts for when prices drop.
Have I Been Pawned – Still the king when it comes to checking if your online accounts have been released in a data breach. Also able to sign up for email alerts if you’ve ever a victim of a breach.
I Have No TV - A collection of documentaries for you to while away the time. Completely free.
Radio Garden – Think Google Earth but wherever you zoom, you get the radio station of that place.
Just The Recipe – Paste in the url and get just the recipe as a result. No life story or adverts.
Tineye – An Amazing reverse image search tool.
My 90s TV – Simulates 90’s TV using YouTube videos. Also has My80sTV, My70sTV, My60sTV and for the younger ones out there, My00sTV. Lose yourself in nostalgia.
Foto Forensics – Free image analysis tools.
Old Games Download – A repository of games from the 90’s and early 2000’s. Get your fix of nostalgia here.
Online OCR – Convert pictures of text into actual text and output it in the format you need.
Remove Background – An amazingly quick and accurate way to remove backgrounds from your pictures.
Twoseven – Allows you to sync videos from providers such as Netflix, Youtube, Disney+ etc and watch them with your friends. Ad free and also has the ability to do real time video and text chat.
Terms of Service, Didn’t Read – Get a quick summary of Terms of service plus a privacy rating.
Coolors – Struggling to get a good combination of colors? This site will generate color palettes for you.
This To That – Need to glue two things together? This’ll help.
Photopea – A free online alternative to Adobe Photoshop. Does everything in your browser.
BitWarden – Free open source password manager.
Just Beam It - Peer to peer file transfer. Drop the file in on one end, click create link and send to whoever. Leave your pc on that page while they download. Because of how it works there are no file limits. It's genuinely amazing. Best file transfer system I have ever used.
Atlas Obscura – Travelling to a new place? Find out the hidden treasures you should go to with Atlas Obscura.
ID Ransomware – Ever get ransomware on your computer? Use this to see if the virus infecting your pc has been cracked yet or not. Potentially saving you money. You can also sign up for email notifications if your particular problem hasn’t been cracked yet.
Way Back Machine – The Internet Archive is a non-profit library of millions of free books, movies, software, music, websites and loads more.
Rome2Rio – Directions from anywhere to anywhere by bus, train, plane, car and ferry.
Splitter – Seperate different audio tracks audio. Allowing you to split out music from the words for example.
myNoise – Gives you beautiful noises to match your mood. Increase your productivity, calm down and need help sleeping? All here for you.
DeepL – Best language translation tool on the web.
Forvo – Alternatively, if you need to hear a local speaking a word, this is the site for you.
For even more useful sites, there is an expanded list that can be found here.
80K notes
·
View notes
Text
Demon-haunted computers are back, baby

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

As a science fiction writer, I am professionally irritated by a lot of sf movies. Not only do those writers get paid a lot more than I do, they insist on including things like "self-destruct" buttons on the bridges of their starships.
Look, I get it. When the evil empire is closing in on your flagship with its secret transdimensional technology, it's important that you keep those secrets out of the emperor's hand. An irrevocable self-destruct switch there on the bridge gets the job done! (It has to be irrevocable, otherwise the baddies'll just swarm the bridge and toggle it off).
But c'mon. If there's a facility built into your spaceship that causes it to explode no matter what the people on the bridge do, that is also a pretty big security risk! What if the bad guy figures out how to hijack the measure that – by design – the people who depend on the spaceship as a matter of life and death can't detect or override?
I mean, sure, you can try to simplify that self-destruct system to make it easier to audit and assure yourself that it doesn't have any bugs in it, but remember Schneier's Law: anyone can design a security system that works so well that they themselves can't think of a flaw in it. That doesn't mean you've made a security system that works – only that you've made a security system that works on people stupider than you.
I know it's weird to be worried about realism in movies that pretend we will ever find a practical means to visit other star systems and shuttle back and forth between them (which we are very, very unlikely to do):
https://pluralistic.net/2024/01/09/astrobezzle/#send-robots-instead
But this kind of foolishness galls me. It galls me even more when it happens in the real world of technology design, which is why I've spent the past quarter-century being very cross about Digital Rights Management in general, and trusted computing in particular.
It all starts in 2002, when a team from Microsoft visited our offices at EFF to tell us about this new thing they'd dreamed up called "trusted computing":
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The big idea was to stick a second computer inside your computer, a very secure little co-processor, that you couldn't access directly, let alone reprogram or interfere with. As far as this "trusted platform module" was concerned, you were the enemy. The "trust" in trusted computing was about other people being able to trust your computer, even if they didn't trust you.
So that little TPM would do all kinds of cute tricks. It could observe and produce a cryptographically signed manifest of the entire boot-chain of your computer, which was meant to be an unforgeable certificate attesting to which kind of computer you were running and what software you were running on it. That meant that programs on other computers could decide whether to talk to your computer based on whether they agreed with your choices about which code to run.
This process, called "remote attestation," is generally billed as a way to identify and block computers that have been compromised by malware, or to identify gamers who are running cheats and refuse to play with them. But inevitably it turns into a way to refuse service to computers that have privacy blockers turned on, or are running stream-ripping software, or whose owners are blocking ads:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
After all, a system that treats the device's owner as an adversary is a natural ally for the owner's other, human adversaries. The rubric for treating the owner as an adversary focuses on the way that users can be fooled by bad people with bad programs. If your computer gets taken over by malicious software, that malware might intercept queries from your antivirus program and send it false data that lulls it into thinking your computer is fine, even as your private data is being plundered and your system is being used to launch malware attacks on others.
These separate, non-user-accessible, non-updateable secure systems serve a nubs of certainty, a remote fortress that observes and faithfully reports on the interior workings of your computer. This separate system can't be user-modifiable or field-updateable, because then malicious software could impersonate the user and disable the security chip.
It's true that compromised computers are a real and terrifying problem. Your computer is privy to your most intimate secrets and an attacker who can turn it against you can harm you in untold ways. But the widespread redesign of out computers to treat us as their enemies gives rise to a range of completely predictable and – I would argue – even worse harms. Building computers that treat their owners as untrusted parties is a system that works well, but fails badly.
First of all, there are the ways that trusted computing is designed to hurt you. The most reliable way to enshittify something is to supply it over a computer that runs programs you can't alter, and that rats you out to third parties if you run counter-programs that disenshittify the service you're using. That's how we get inkjet printers that refuse to use perfectly good third-party ink and cars that refuse to accept perfectly good engine repairs if they are performed by third-party mechanics:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
It's how we get cursed devices and appliances, from the juicer that won't squeeze third-party juice to the insulin pump that won't connect to a third-party continuous glucose monitor:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
But trusted computing doesn't just create an opaque veil between your computer and the programs you use to inspect and control it. Trusted computing creates a no-go zone where programs can change their behavior based on whether they think they're being observed.
The most prominent example of this is Dieselgate, where auto manufacturers murdered hundreds of people by gimmicking their cars to emit illegal amount of NOX. Key to Dieselgate was a program that sought to determine whether it was being observed by regulators (it checked for the telltale signs of the standard test-suite) and changed its behavior to color within the lines.
Software that is seeking to harm the owner of the device that's running it must be able to detect when it is being run inside a simulation, a test-suite, a virtual machine, or any other hallucinatory virtual world. Just as Descartes couldn't know whether anything was real until he assured himself that he could trust his senses, malware is always questing to discover whether it is running in the real universe, or in a simulation created by a wicked god:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
That's why mobile malware uses clever gambits like periodically checking for readings from your device's accelerometer, on the theory that a virtual mobile phone running on a security researcher's test bench won't have the fidelity to generate plausible jiggles to match the real data that comes from a phone in your pocket:
https://arstechnica.com/information-technology/2019/01/google-play-malware-used-phones-motion-sensors-to-conceal-itself/
Sometimes this backfires in absolutely delightful ways. When the Wannacry ransomware was holding the world hostage, the security researcher Marcus Hutchins noticed that its code made reference to a very weird website: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Hutchins stood up a website at that address and every Wannacry-infection in the world went instantly dormant:
https://pluralistic.net/2020/07/10/flintstone-delano-roosevelt/#the-matrix
It turns out that Wannacry's authors were using that ferkakte URL the same way that mobile malware authors were using accelerometer readings – to fulfill Descartes' imperative to distinguish the Matrix from reality. The malware authors knew that security researchers often ran malicious code inside sandboxes that answered every network query with fake data in hopes of eliciting responses that could be analyzed for weaknesses. So the Wannacry worm would periodically poll this nonexistent website and, if it got an answer, it would assume that it was being monitored by a security researcher and it would retreat to an encrypted blob, ceasing to operate lest it give intelligence to the enemy. When Hutchins put a webserver up at iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, every Wannacry instance in the world was instantly convinced that it was running on an enemy's simulator and withdrew into sulky hibernation.
The arms race to distinguish simulation from reality is critical and the stakes only get higher by the day. Malware abounds, even as our devices grow more intimately woven through our lives. We put our bodies into computers – cars, buildings – and computers inside our bodies. We absolutely want our computers to be able to faithfully convey what's going on inside them.
But we keep running as hard as we can in the opposite direction, leaning harder into secure computing models built on subsystems in our computers that treat us as the threat. Take UEFI, the ubiquitous security system that observes your computer's boot process, halting it if it sees something it doesn't approve of. On the one hand, this has made installing GNU/Linux and other alternative OSes vastly harder across a wide variety of devices. This means that when a vendor end-of-lifes a gadget, no one can make an alternative OS for it, so off the landfill it goes.
It doesn't help that UEFI – and other trusted computing modules – are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), which makes it a felony to publish information that can bypass or weaken the system. The threat of a five-year prison sentence and a $500,000 fine means that UEFI and other trusted computing systems are understudied, leaving them festering with longstanding bugs:
https://pluralistic.net/2020/09/09/free-sample/#que-viva
Here's where it gets really bad. If an attacker can get inside UEFI, they can run malicious software that – by design – no program running on our computers can detect or block. That badware is running in "Ring -1" – a zone of privilege that overrides the operating system itself.
Here's the bad news: UEFI malware has already been detected in the wild:
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
And here's the worst news: researchers have just identified another exploitable UEFI bug, dubbed Pixiefail:
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
Writing in Ars Technica, Dan Goodin breaks down Pixiefail, describing how anyone on the same LAN as a vulnerable computer can infect its firmware:
https://arstechnica.com/security/2024/01/new-uefi-vulnerabilities-send-firmware-devs-across-an-entire-ecosystem-scrambling/
That vulnerability extends to computers in a data-center where the attacker has a cloud computing instance. PXE – the system that Pixiefail attacks – isn't widely used in home or office environments, but it's very common in data-centers.
Again, once a computer is exploited with Pixiefail, software running on that computer can't detect or delete the Pixiefail code. When the compromised computer is queried by the operating system, Pixiefail undetectably lies to the OS. "Hey, OS, does this drive have a file called 'pixiefail?'" "Nope." "Hey, OS, are you running a process called 'pixiefail?'" "Nope."
This is a self-destruct switch that's been compromised by the enemy, and which no one on the bridge can de-activate – by design. It's not the first time this has happened, and it won't be the last.
There are models for helping your computer bust out of the Matrix. Back in 2016, Edward Snowden and bunnie Huang prototyped and published source code and schematics for an "introspection engine":
https://assets.pubpub.org/aacpjrja/AgainstTheLaw-CounteringLawfulAbusesofDigitalSurveillance.pdf
This is a single-board computer that lives in an ultraslim shim that you slide between your iPhone's mainboard and its case, leaving a ribbon cable poking out of the SIM slot. This connects to a case that has its own OLED display. The board has leads that physically contact each of the network interfaces on the phone, conveying any data they transit to the screen so that you can observe the data your phone is sending without having to trust your phone.
(I liked this gadget so much that I included it as a major plot point in my 2020 novel Attack Surface, the third book in the Little Brother series):
https://craphound.com/attacksurface/
We don't have to cede control over our devices in order to secure them. Indeed, we can't ever secure them unless we can control them. Self-destruct switches don't belong on the bridge of your spaceship, and trusted computing modules don't belong in your devices.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/17/descartes-delenda-est/#self-destruct-sequence-initiated

Image: Mike (modified) https://www.flickr.com/photos/stillwellmike/15676883261/
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#uefi#owner override#user override#jailbreaking#dmca 1201#schneiers law#descartes#nub of certainty#self-destruct button#trusted computing#secure enclaves#drm#ngscb#next generation secure computing base#palladium#pixiefail#infosec
575 notes
·
View notes
Text
Following a White House edict effectively banning federal employees from disclosing their personal pronouns in email signatures, sources within multiple federal agencies say pronouns are now being systemically blocked across multiple email clients and other software.
WIRED confirmed various automated efforts with employees at the United States Agency for International Development (USAID), the Environmental Protection Agency (EPA), the General Services Administration (GSA), the US Department of Agriculture, and the Centers for Disease Control and Prevention (CDC).
The employees spoke to WIRED on condition of anonymity, citing fears of retaliation.
Multiple agency directors sent emails over the weekend telling staff that, due to President Donald Trump’s executive order, their offices would be removing the pronoun capability from Office 365. Employees were told they’d also need to remove pronouns from their email signatures in order to comply with the directive.
A staffer at USAID says the formal deactivation of their ability to list pronouns occurred last week, in response to executive orders defining sexes issued by President Trump on his first day in office. A GSA staffer says pronouns were wiped from employees’ email signatures after hours on Friday and were also no longer visible in Slack, the workplace messaging app. At the CDC, there used to be a section for employees to share their pronouns on their Teams profiles, another workplace app. That field no longer exists.
Reached for comment, the White House transferred WIRED to OPM communications director McLaurine Pinover, who pointed to January 29 memorandum ordering agencies to disable all features “that prompt users for their pronouns.”
The ban on personal pronouns follows sweeping efforts by the White House to eliminate programs that encourage diversity and social justice within the federal government, as well as other references to “diversity, equity, and inclusion” in federal employees’ discourse.
In a striking example of the policy in action, an image surfaced last week of a wall being painted over at the Federal Bureau of Investigation's Quantico, Virginia, academy due to it listing "diversity" among the bureau's core values. (According to an email from the FBI’s Office of Integrity and Compliance obtained by Mother Jones, the bureau no longer counts "diversity" among its core values.)
The Trump administration began a radical campaign last week aimed at inducing members of the federal workforce to leave their jobs ahead of threatened reductions. The effort is spearheaded by Elon Musk, leader of the so-called Department of Government Efficiency (DOGE), a task force that has effectively seized control of several federal agencies and sensitive government systems with apparent clearance from the White House.
WIRED reported last week that Musk’s outfit had effectively taken over the Office of Personnel Management, the US government’s human resources department. In this and other efforts, it is employing inexperienced young engineers whose ages range from 19 to 24—many of whom, public records show, are former interns or have been affiliated with Musk-aligned companies.
OPM emailed federal workers on January 28 with a “deferred resignation offer,” sparking widespread confusion among federal workers. (DOGE’s own new HR chief was unable to answer basic questions about the offer in a contentious staff meeting last week, WIRED reported.) In an email to staff Sunday evening, OPM clarified whether the deferred resignation program complied with existing privacy laws. “Yes,” read the answer. “The deferred resignation program uses only basic contact information about federal employees, like name and government address, along with short, voluntary email responses. The information is stored on government systems. To the extent that the Privacy Act applies, all information relevant to the program is covered by existing OPM System Records Notices.”
Multiple agency sources told WIRED last week that several of Musk's lieutenants had been granted access to key computer systems controlled by the GSA, an independent agency tasked by Congress with overseeing federal buildings and providing equipment, supplies, and IT support across the government.
31 notes
·
View notes
Text
Should I Be the Stars of Lyra Web Event is Now Live!

As the neon fades and shadows dissipate, the stars shall sing an eternal melody
The "Should I Be the Stars of Lyra" web page reward event is now live. Participate in the event and complete the series of tasks for guaranteed Polychromes, Dennies, and other rewards!
▼Participate Here
https://hoyo.link/U4kNzDQpT
[Event Duration]
2025/01/17 12:00 – 2025/01/31 23:59 (UTC+8)
[Requirements]
Reach Inter-Knot Lv. 8
[Event Prizes]
During the event, by completing all ticket creation and sharing tasks, Proxies can receive the following rewards: Polychrome ×125, Official Investigator Log ×25, and Denny ×50,000.
>> Official Hoyolab post <<
[Event Rules]
1. During the event, Proxies can obtain "Microphones" by completing a series of tasks. Consuming "Microphones" unlocks the "Inspired Gathering" stages, allowing interaction with Agents.
2. Each time a stage is completed, Proxies can obtain multiple "Inspired Elements," which can be used in "Create Ticket."
3. Proxies can select a certain number of "Inspired Elements" to create tickets. Once completed, the tickets will be automatically saved in the "Portfolio." Note: The "Portfolio" has a storage limit, so Proxies should save creations wisely.
※ This web event is for entertainment purposes only and is not related to actual in-game content.
[Notes]
1. "Microphones," "Inspired Elements," and other items are event-related items only and have no connection to in-game content.
2. Please make sure you meet the age requirements and other stipulations required by the local laws of your country/region of residence to participate in this type of event, or ensure you participate in the event with the knowledge and consent of your guardian.
2. The event organizer reserves the right to revoke the eligibility or prize won if Proxies engage in any of the following behaviors or situations; 1) Winners who do not meet the requirements; 2) Participating in this event or intentionally disrupting its fairness through the use of any bot programs, prize-generating software, or any other automated or unfair means; 3) Other actions that violate relevant laws and regulations or the event rules.
4. Proxies should protect their personal information and avoid trusting reward notifications from other channels or disclosing personal accounts and other private information casually, to prevent infringement of personal information and property.
5. Any information collected during this event will be used to allow you to log into your HoYoverse account and participate in the event. It will not be used for any other purposes.
We will protect and manage your personal information in accordance with the relevant laws and regulations. More information can be found in our Privacy Policy on our official site. Collection and usage of your personal information will strictly abide by our Privacy Policy.
6. If you have any questions, please contact customer services: [email protected]
7. This event is subject to the Terms of Service and Privacy Policy of HoYoverse accounts and HoYoLAB. Before participating in this event, you must fully understand and agree to abide by the aforementioned terms and policies.
8. Please log in to your HoYoverse account and link a character from Zenless Zone Zero to participate in the event, to ensure proper distribution and receipt of event rewards.
9. Rewards cannot be claimed after the event ends, so please make sure to claim them on time. Rewards will be sent via in-game mail, and the mail will be valid for 30 days, so please check it promptly.
10. The web event will be unavailable during version update maintenance. It will be accessible again once the update is completed.
7 notes
·
View notes
Text
PSA: Free Software
Reading this may really save your time, privacy, and money! Reblog or share to spread awareness!
Folks often use software that’s expensive and sometimes even inferior because they don’t know there are alternatives. So to those unfamiliar: basically, free and open-source (FOSS) or "libre" software is free to use and anyone can access the original code to make their own version or work on fixing problems.
That does not mean anyone can randomly add a virus and give it to everyone—any respectable libre project has checks in place to make sure changes to the official version are good! Libre software is typically developed by communities who really care about the quality of the software as a goal in itself.
There are libre alternatives to many well-known programs that do everything an average user needs (find out more under the cut!) for free with no DRM, license keys, or subscriptions.
Using libre software when possible is an easy way to fight against and free yourself from corporate greed while actually being more convenient in many cases! If you need an app to do something, perhaps try searching online for things like:
foss [whatever it is]
libre [whatever it is]
open source [whatever it is]
Feel free to recommend more libre software in the tags, replies, comments, or whatever you freaks like to do!
Some Libre Software I Personally Enjoy…
LibreOffice
LibreOffice is an office suite, much like Microsoft Office. It includes equivalents for apps like Word, Excel, and Powerpoint, which can view and edit files created for those apps.
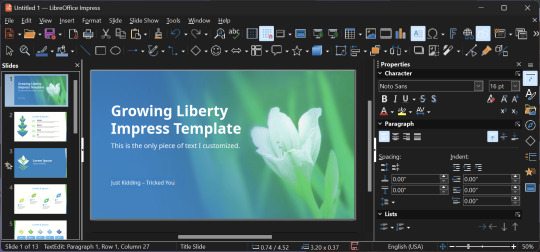
I can't say I've used it much myself yet. I do not personally like using office software except when I have to for school.
OpenShot
OpenShot Video Editor is, as the name suggests, a video editing program. It has industry-standard features like splicing, layering, transitions, and greenscreen.
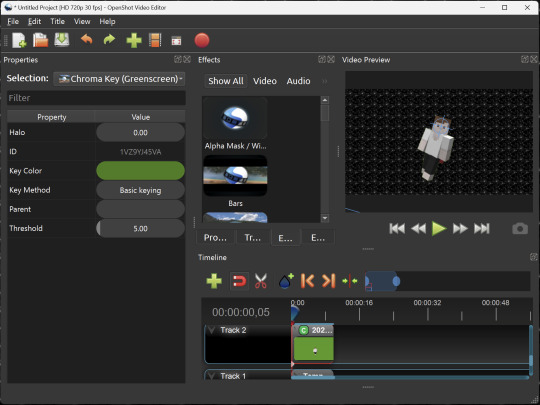
I've only made one video with it so far, but I'm already very happy with it. I had already paid for a video editor (Cyberlink PowerDirector Pro), but I needed to reinstall it and I didn't remember how. Out of desperation, I searched up "FOSS video editor" and I'm so glad I did. There's no launcher, there's no promotion of other apps and asset packs—it's just a video editor with a normal installer.
GIMP
GNU Image Manipulation Program is an image editor, much like Photoshop. Originally created for Linux but also available for Windows and MacOS, it provides plenty of functionality for editing images. It is a bit unintuitive to learn at first, though.
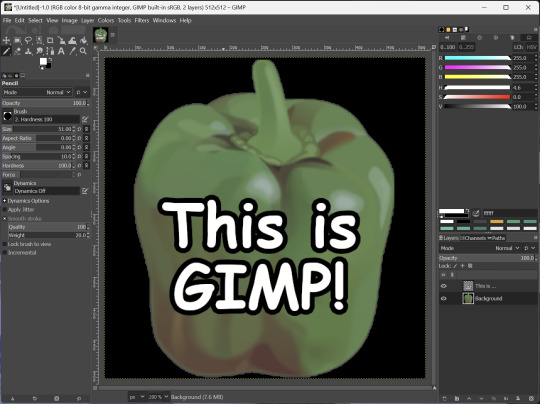
I've used it to create and modify images for years, including logos, really bad traceover art, and Minecraft textures. It doesn't have certain advanced tech like AI paint-in, but it has served my purposes well and it might just work for yours!
(Be sure to go to Windows > Dockable Dialogs > Colors. I have no idea why that's not enabled by default.)
Audacity
Audacity is an audio editing program. It can record, load, splice, and layer audio files and apply effects to them.
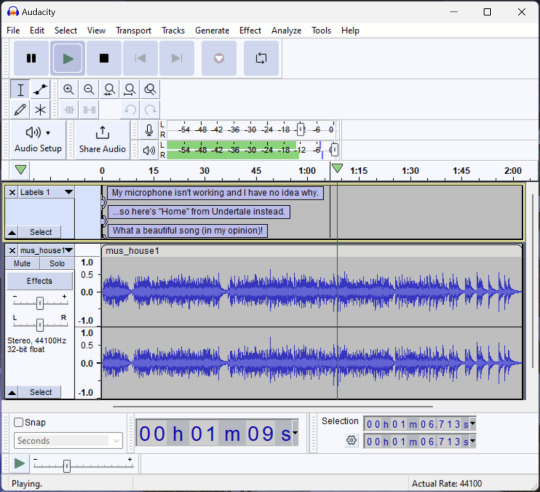
Audacity is another program I've used for a long time. It is not designed to compose music, but it is great for podcasts, simple edits, and loading legacy MS Paint to hear cool noises.
7-Zip
7-Zip is a file manager and archive tool. It supports many archive types including ZIP, RAR, TAR, and its own format, 7Z. It can view and modify the contents of archives, encrypt and decrypt archives, and all that good stuff.
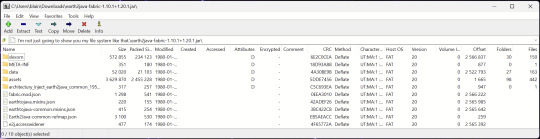
Personally, I use 7-Zip to look inside JAR files for Minecraft reasons. I must admit that its UI is ugly.
Firefox
Firefox is an internet browser, much like Google Chrome, Microsoft Edge, or Safari. While browsers are free, many of them include tracking or other anti-consumer practices. For example, Google plans to release an update to Chromium (the base that most browsers are built from these days) that makes ad blockers less effective by removing the APIs they currently rely on.
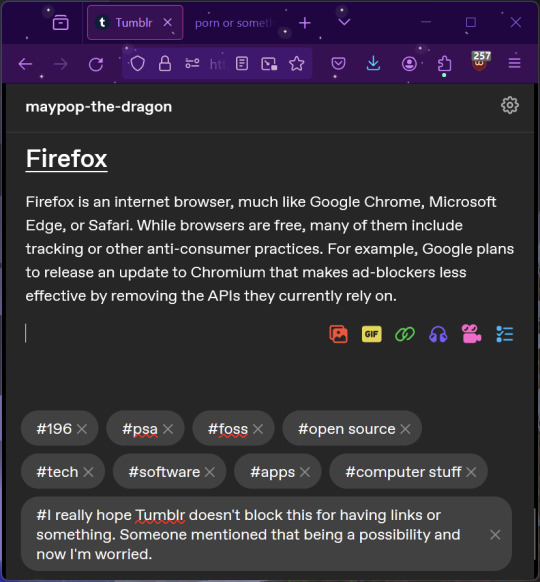
Aside from fighting monopolies, benefits include: support for animated themes (the one in the picture is Purple Night Theme), good ad blockers forever, an (albeit hidden) compact UI option (available on about:config), and a cute fox icon.
uBlock Origin
As far as I know, uBlock Origin is one of the best ad blockers there is.
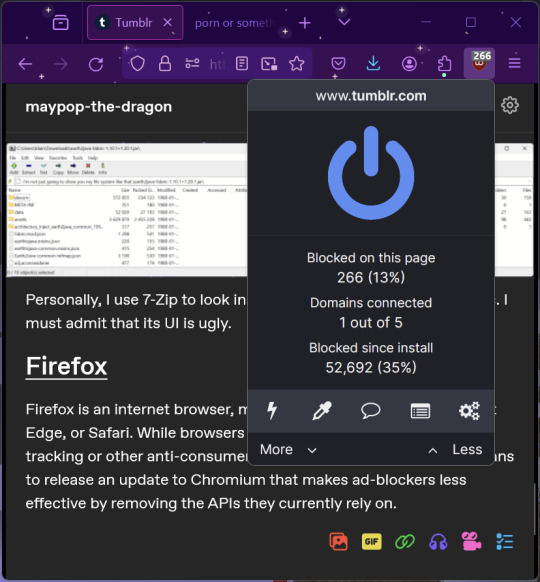
I was on a sketchy website with my brother, and he was using Opera GX's ad blocker. Much of the time when he clicked on anything, it would take us to a random sponsored page. I suggested that he try uBlock Origin, and with uBlock Origin, that didn't happen anymore.
Linux
Linux is a kernel, but the term is often used to refer to operating systems (much like Windows or MacOS) built on it. There are many different Linux-based operating systems (or "distros") to choose from, but apps made for Linux usually work on most popular distros. You can also use many normally Windows-only apps on Linux through compatibility layers like WINE.


I don't have all four of these, so the images are from Wikipedia. I tried to show a variety of Linux distros made for different kinds of users.
If you want to replace your operating system, I recommend being very careful because you can end up breaking things. Many computer manufacturers don't care about supporting Linux, meaning that things may not work (Nvidia graphic cards notoriously have issues on Linux, for example).
Personally, I tried installing Pop!_OS on a laptop, and the sound output mysteriously doesn't work. I may try switching to Arch Linux, since it is extremely customizable and I might be able to experiment until I find a configuration where the audio works.
Many Linux distros offer "Live USB" functionality, which works as both a demo and an installer. You should thoroughly test your distro on a Live USB session before you actually install it to be absolutely sure that everything works. Even if it seems fine, you should probably look into dual-booting with your existing operating system, just in case you need it for some reason.
Happy computering!
#196#psa#foss#open source#tech#software#apps#computer stuff#I really hope Tumblr doesn't block this for having links or something. Someone mentioned that being a possibility and now I'm worried.#please reblog#2024-01-26
44 notes
·
View notes
Note
I am SUPREMELY interested in your internet activity book - I work at a library and am trying to make a similar resource myself. The Australian Government created a fantastic digital literacy resource website called Be Connected, but even though it has tutorials that go right down to 'this is a mouse' basics you do need a certain level of comprehension to access the site (also it doesn't go far enough on privacy imo) so I've been trying to patch the gaps and driving myself slightly insane with it bc there is just. so much.
If you're willing to share more I'd be thrilled to hear about it, and I would LOVE to pool resources if you're willing.
So what I'm basically doing is 11 activities to help people get familiar with a windows computer that they own. It assumes that the user has permissions to make changes to the desktop and install software, etc. The activities I'm writing up do include some browser activities (I walk people through creating a protonmail account and signing up for a password manager) but starts with things like "pin programs to your taskbar" and "create a folder on the desktop and rename it."
The stuff that I'm focusing on is things like "save a QR code in paint to print it out because you don't have a smartphone and can't return this item otherwise" and "learn how to find where files are on your computer." This is mostly supposed to be a way for someone to feel like they're being supervised and are doing safe activities as they learn to get comfortable with simply handling the various input devices and navigating the desktop.
So I don't go in-depth on security because that's not the purpose of this resource specifically, and security can, unfortunately, be something of an advanced topic.
What I would love to know is what in-browser things people tend to struggle with because it's likely that you are seeing people who can't install software on the computers they are using and can't store data on the computers long-term, so they have a very different relationship to your computers than they would to their own. What do people at the library struggle with on library computers? What are the things that they come in to do? Do people use your computers more for going on the internet or for things like printing? Do most of the people who come in to use library computers have email addresses? Because I would very much like to create a similar activity book for using the internet regardless of browser or operating system.
111 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Best team communication tool - Troop Messenger
In today's modern workplace, team members can no longer rely on one-on-one talks with coworkers or provide crucial files or detailed information by email, which might take a lot of time due to procedure. Because it improves communication as well as time management, team productivity, and collaboration, using team communication tools may be the best option.
Because work chat platforms are too costly and don't meet their demands, small and microbusiness owners resort to social chat apps. Some were compelled to use them due to an unexpected pandemic sickness. However, some of the top products are able to offer excellent services at reasonable costs because of their subscription programs.
The following are some of the most effective team communication tools for your business.
Troop Messenger

Troop Messenger is considered the best team communication tools, which can be used as a business messaging tool, work chat tool, and instant messaging tool for both office and remote work.
After discovering Troop Messenger's innovative capabilities, which may not be present in currently available apps or would likely be introduced to significant application upgrades in the future, many organisations chose to adopt it after it swiftly upended the industry.
Troop Messenger's thorough research led to the development of new features, and the instrument is inexpensive and appropriate for use in any field. NASA and the military may exchange classified information using this safe and secure team texting software.
Features
Remote screen sharing and controlling
Join Now, allows the user to join the missed group audio or video call while ongoing
Burnout
Live Location Tracking
Jointly Code
Advanced Search Filters
Forkout
Seamless Communication at Work
Troop Messenger is a complete commercial team communication tool, not just a tool for team communication. Troop Messenger facilitates simple and immediate communication at work, regardless of the size of your company. It is designed to make it simple to communicate, share files, and make decisions quickly, so your team will always be in touch no matter where they are in the world.
A Communication Tool for Every Need
Troop Messenger is an all-in-one team communication program that meets the increasing need for remote work solutions. It's a flexible communication solution that combines team collaboration, video conferences, and texting onto a single platform. Whether working remotely or in the office, teams may remain involved and effective. It's the best business communication tool, enhancing internal communication and increasing team productivity with features like file sharing, group chats, and direct messaging..
Why Troop Messenger is the Best Communication App for Teams
Efficient Team Communication: Troop Messenger excels as a team communication tool. It enables instant communication, reducing the time spent on email or lengthy meetings. The ability to message anyone instantly, whether one-on-one or in groups, makes it the perfect tool for both office-based and remote teams.
Collaboration Made Easy: Internal communication software like Troop Messenger fosters better collaboration among team members. Through features like shared channels, file-sharing options, and quick access to past conversations, team members can easily stay on the same page and collaborate efficiently. This smoothens project management and ensures no information slips through the cracks.
Secure and Reliable: In addition to enhancing communication, Troop Messenger provides a secure platform for businesses. With end-to-end encryption and compliance with data privacy regulations, businesses can ensure that sensitive information remains confidential while facilitating smooth communication.
Versatility for All Business Sizes: Whether you're managing a startup or a large enterprise, Troop Messenger adapts to the needs of your organization. Its intuitive interface and flexible features cater to a wide range of business sizes, making it the perfect internal communication software.
Real-Time Communication: For both office and remote workers, real-time communication is a must. Troop Messenger enables live communication with minimal delay, allowing teams to respond quickly to important messages, share updates in real-time, and tackle problems without waiting for an email or scheduled call.
#best team communication tools#team communicaton#troop messenger#communication#tagged#india#usa#philippines#collaboration
2 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
Samsung Galaxy A56: Best Smartphone Performance In 2025

Samsung Galaxy A56
As development news breaks, the Samsung Galaxy A56 is gaining popularity in the smartphone industry. Designed to succeed the Galaxy A series, this gadget is expected to outperform even Samsung’s top models. Mid-range smartphones will be transformed by the Galaxy A56’s speed, efficiency, and user experience. It is the most anticipated specifications and why it’s worth the wait.
Galaxy A56 Features
New mid-range smartphone standard
The Galaxy A56 continues Samsung’s legacy of quality features at an accessible price. Samsung looks to be pushing the limits even further, providing the A56 with high-performance specs that might compete with flagship handsets.
Strong Processor Upgrade
Due to its speculated Exynos 1480 processor, the A56 outperforms its predecessor, the Exynos 1280 in the A54. The new Exynos 1480 improves multitasking, processing performance, and power efficiency. It is octa-core CPU handles intense operations smoothly, so you can stream, game, or manage many apps.
Samsung may possibly provide a Snapdragon 7 Gen 2 model for adaptable usage in various areas. With its high performance and power economy, this processor makes the Galaxy A56 a powerful mid-range competitor.
Memory and storage upgrades
Samsung will upgrade RAM and storage with the A56. There are significant reports that the basic model will have 6GB of RAM, although an 8GB edition may be available for intense workloads. Users may choose 128GB or 256GB internal storage, extendable via microSD up to 1TB. Users need flexibility, and this gives programs, images, movies, and files plenty of space.
Huge Speeds
Today’s digital world requires 5G, which the Galaxy A56 provides. The A56 is fantastic for streaming, gaming, and video conferencing due to dual-mode 5G download and upload rates. The A56 will keep people connected at fast speeds worldwide as 5G spreads.
Beautiful AMOLED Display
The Galaxy A56‘s 6.5-inch Full HD+ Super AMOLED display with deep blacks, bright colors, and superb contrast. The A56 will maintain Samsung’s display superiority with its immersive display. A 120Hz refresh rate assures clean images and minimal motion blur, giving the screen a luxury feel normally seen in higher-end devices.
Amazing Camera Setup
Smartphone cameras matter, and the Galaxy A56 may include quad cameras. Speculation implies a 50MP primary sensor, 12MP ultra-wide, 5MP macro, and 5MP depth sensor. This configuration enables for wide-angle vistas and close-ups.
The 50MP main camera offers great low-light performance, quicker focusing, and sharper images. AI advancements provide pro-level photography without a flagship smartphone. Quality selfies and video calls with 32MP camera.
Samsung Galaxy A56 may utilize 5,000mAh battery
Smartphone customers appreciate battery life. Power-efficient Exynos or Snapdragon chipsets and large batteries should last all day for gaming and streaming. The A56 is include 25W rapid charging for quick phone usage. As usual for Samsung’s A-series, this mid-range device won’t include wireless charging.
Android/One UI Integration
As predicted, the Samsung Galaxy A56 will come with Android 14 and One UI 6. With capabilities to boost productivity and customization, Samsung’s One UI is seamless and user-friendly. One-handed mode, Edge Panels, and extensive privacy settings make the A56 a versatile tablet for casual and experienced users.
Samsung Knox, the company’s unique security technology, will provide improved protection to secure your data. With regular software updates and security fixes, the A56 will endure for years.
Smooth Design and Quality
Samsung designs are known for their quality, so the Galaxy A56 should look great. Corning Gorilla Glass 5 front and back makes the phone look fantastic and endure longer. This thin device with curved edges is easy to grasp and will come in numerous colors for design and function.
Keeping its IP67 dust- and water-resistant designation makes the A56 more durable for daily usage in varied conditions.
Samsung Galaxy A56 Price
Final Thoughts: Mid-Range Powerhouse Galaxy A56
The A56 is turning out to be one of the most powerful and adaptable mid-range smartphones with its astonishing variety of high-performance capabilities. Its powerful Exynos 1480 CPU, 120Hz AMOLED display, quad-camera system, 5G connection, and big battery make the Galaxy A56 the right blend of performance, features, and cost.
The A56 is a must-see for anybody searching for flagship-like capabilities at a lower price. Samsung is pushing the limits of mid-range smartphones.
Galaxy A56 Release Date
No Samsung Galaxy A56 release date has been disclosed. Early in the year, Samsung releases its mid-range A series smartphones. Based on prior trends, the Galaxy A56 should be introduced in early 2025.
Read more on Govindhtech.com
#SamsungGalaxy#GalaxyA56#smartphone#GalaxAseries#microSD#AMOLEDDisplay#Android14#5Gconnection#AI#GorillaGlass5#news#technews#technology#technologynews#technologytrends#govindhtech
2 notes
·
View notes
Text

Preparing Your Amazon Fire Stick
Before beginning the process of adding an Electronic Program Guide (EPG) to your Amazon Fire Stick, it is crucial to ensure that your device is properly prepared.
This involves updating the Fire Stick software and installing necessary tools to facilitate the installation and functionality of the EPG.
Updating Fire Stick Software
To start, users should verify that their Amazon Fire Stick software is current. Navigate to Settings > My Fire TV > About on your Fire Stick. Here, you can check for any available updates. If an update is found, proceed to install it to ensure your device runs smoothly and is compatible with the latest applications and features. Regular software updates can enhance the performance of your Fire Stick and fix potential security vulnerabilities.
Installing Necessary Tools
After updating the software, the next step is to install essential tools that will assist in the management and operation of your Fire Stick, especially for sideloading applications not available directly on the Amazon Appstore.
Install the Downloader App: Begin by installing the Downloader app from the Amazon Store. Use the Search function on the Fire Stick home screen to find and install this app.
Enable Apps from Unknown Sources: Go to Settings > My Fire TV > Developer Options. Here, toggles the option for Apps from Unknown Sources to ON. This setting allows the installation of applications from sources outside the official Amazon Appstore.
Consider a VPN App: For enhanced security and privacy, installing a VPN app like ExpressVPN or NordVPN is advisable. A VPN protects your streaming data and masks your online identity, which is particularly useful when accessing IPTV services.
Additional Tools: Installing a file manager, such as ES File Explorer, can be beneficial for managing files and sideloading apps. For a better media playing experience, consider adding VLC or Kodi, which support a wide range of media formats and streaming protocols.
By following these preliminary steps, your Amazon Fire Stick will be well-equipped to handle the installation of an EPG and any other IPTV applications. This preparation ensures a smoother setup process and a better overall user experience when accessing IPTV services on your device.
Installing EPG on Your Fire Stick
To install an Electronic Program Guide (EPG) on your Amazon Fire Stick, follow these detailed steps, ensuring you can access a wide range of movies xmltv information with ease.
Step-by-Step Installation Process
Access the Live Section: From your Fire Stick home screen, navigate to the "Live" tab. If this option isn't visible, consider updating your system by going to Settings > My Fire TV > About and selecting "Check for Updates".
Launch the Guide: Once in the Live section, scroll down and select "Guide" to open the built-in EPG, which aggregates channels from various sources.
Customize Your Channels: To personalize your EPG, press the options button (marked by three lines on your remote). This action brings up a menu where you can manage and add favorite channels. Choose "Manage Channels" to see active sources and adjust your preferences.
Add Additional Apps: For more channels, install apps like Xumo Play from the Amazon App Store. After installation, navigate to Settings > Live TV > Manage Channels and select "Sync Sources" to integrate Xumo Play into your EPG.
Adjust Channel Placement: To prioritize certain channels in your guide, use the "Move Source" option in the manage channels menu. This allows you to rearrange your channel lineup, placing preferred sources like Xumo Play at the top for easier access.
Adding Channel Information
Adding to Favorites: Highlight a channel you frequently watch, such as Divorce Court, and press the options button. Select "Add to Favorite Channels." A heart icon will appear next to the channel, indicating it's been added to your favorites.
Accessing Favorite Channels: To view your favorite channels list, press the home button, exit the EPG, and then go to Settings > Live TV. Here, you'll find the "Favorite Channels" option, showing all your selected favorites.
Channel Management: If you need to adjust your channel settings further or if a newly added app like Xumo Play doesn't appear immediately, consider restarting your Fire Stick or re-installing the application. This can often resolve syncing issues and ensure all channels are properly displayed in your EPG.
By following these steps, you can effectively install and customize an EPG on your Amazon Fire Stick, enhancing your IPTV viewing experience by organizing and personalizing the channel lineup according to your preferences.
Feeling overwhelmed by your TV schedule? Here's the one place you need to check for EPG XML! Visit https://epg.best for more info!
youtube
5 notes
·
View notes
Note
hi andie! I saw your post and you seem to be very knowledgeable about the behind the scenes of ai programs. can I ask how you got into tech? it’s something I’ve been looking to get into
Hello my love!! I only have a high-level understanding of what's going on lol but I'm glad it sounds like I know what I'm saying. :3
I happened to fall into the industry because of my linguistics background; I got brought in to help build out data sets for earlier, more deterministic versions of AI models. But now we're pivoting as an industry to statistical models and so I'm learning more as we go.
Anyway I started from a data set generation role, but there are other, more common ways to get into tech companies. I'm assuming since you asked you don't have any software or computational backgrounding?? As I think those channels into tech roles are pretty straightforward lol.
I work in AI specifically so I'm approaching this from that perspective, but depending on whether you want to get into social media, online retail, or software/application development, the advice might be different. But for start ups and companies focusing on the pivot to generative AI models like LLMs, I foresee a couple of non-technical roles that would get you into the company, and you'd have to build up your understanding from there to move on into other more technical roles!
#1) Project management roles. I'd look through google jobs to see what tech companies are hiring project managers and read through to see what the projects are. It's likely companies will need to build up targeted data sets to patch holes in LLM performance so I foresee a fair number of project manager or coordinator roles who are responsible for managing creation of those targeted data sets. There might also be a need for non-English data to seed universal models, so there might be roles managing translations as well. You probably don't need to be able to code or translate yourself, but you will need to be able to interface with the roles that do.
#2) Analyst roles. If you're freshly-graduated and not ready for a management role, that might also leave you with a data-set creation role like my former one. I think companies usually title these with "analyst" roles, like data analyst/translation analyst, etc etc, but your responsibilities would be something like directly translating data or directly transforming data in whatever way the models need it to formatted to consume.
#3) Customer trust roles. Since this is new tech I also imagine companies are going to need to build up bug fix teams who are directly responsible for addressing issues with their models. This might take the form of customer trust roles who are responsible for addressing privacy issues that arise (like imagine a customer account number somehow making it into the model), dealing with sensitive content (depending on how the model is trained it could pick up on some not-PC or not-SFW language...) or otherwise correcting false data the model gives (LLMs are prone to "hallucinating" incorrect information because they are trained on such a wide swath of data). So I'd look for "support" roles or anything with "customer trust" in the title!!
Anyway that's what I can think of for now lol. Hope this is helpful!!
10 notes
·
View notes
Text
From Coding to Creation: Java's Versatile Influence
Java, often described as the "king of programming languages," stands as a monumental force that has significantly influenced the trajectory of modern software development. For over two decades, Java has proven its versatile, powerful, and dependable programming language, underpinning a vast array of applications, platforms, and systems that permeate our digital landscape. In this comprehensive exploration, we will embark on a journey to unravel the essence of Java, delving deep into what makes it indispensable and why it continues to be the preferred choice for programmers across diverse domains.

What is Java?
At its core, Java is a high-level, object-oriented, and platform-independent programming language that defies the conventional limitations of traditional coding. Conceived in the mid-1990s through the visionary efforts of James Gosling and his adept team at Sun Microsystems (now seamlessly integrated into Oracle Corporation), Java introduced a revolutionary concept that continues to define its identity: "Write Once, Run Anywhere." This groundbreaking principle signifies that Java applications exhibit a remarkable adaptability, capable of executing seamlessly on various platforms, provided a Java Virtual Machine (JVM) stands ready to facilitate their execution. This single feature alone positions Java as an unparalleled workhorse, transcending the boundaries of operating systems and hardware, and ushering in an era of software portability and compatibility.
Key Features of Java:
Platform Independence: Java's unparalleled platform independence is the cornerstone of its success. Code authored in Java is liberated from the confines of a single operating system, enabling it to traverse across a plethora of platforms without requiring any cumbersome modifications. This inherent portability not only obliterates compatibility concerns but also streamlines software deployment, eliminating the need for platform-specific versions.
Object-Oriented Paradigm: Java's steadfast adherence to the object-oriented programming (OOP) paradigm cultivates a development environment characterized by modularity and maintainability. By encapsulating code into discrete objects, Java empowers developers to construct intricate systems with greater efficiency and ease of management, a quality particularly favored in large-scale projects.
Rich Standard Library: The Java Standard Library stands as a testament to the language's comprehensiveness. It comprises a vast repository of pre-built classes and methods that cater to a wide spectrum of programming tasks. This comprehensive library significantly reduces development overhead by offering readily available tools for commonplace operations, bestowing developers with the invaluable gift of time.
Security: In an era marred by cyber threats and vulnerabilities, Java emerges as a paragon of security-conscious design. It incorporates robust security features, including a sandbox environment for executing untrusted code. Consequently, Java has become the de facto choice for building secure applications, particularly in industries where data integrity and user privacy are paramount.
Community Support: The strength of Java's thriving developer community is an asset of immeasurable value. This vast and active network ensures that developers are never left wanting for resources, libraries, or frameworks. It provides a dynamic support system where knowledge sharing and collaborative problem-solving flourish, accelerating project development and troubleshooting.
Scalability: Java is not confined by the scale of a project. It gracefully adapts to the demands of both modest applications and sprawling enterprise-level systems. Its versatility ensures that as your project grows, Java will remain a steadfast companion, capable of meeting your evolving requirements.
Performance: Java's Just-In-Time (JIT) compiler serves as the vanguard of its performance capabilities. By dynamically optimizing code execution, Java ensures that applications not only run efficiently but also deliver exceptional user experiences. This, coupled with the ability to harness the power of modern hardware, makes Java a preferred choice for performance-critical applications.
Multithreading: Java's built-in support for multithreading equips applications to execute multiple tasks concurrently. This not only enhances responsiveness but also elevates the overall performance of applications, particularly those designed for tasks that demand parallel processing.
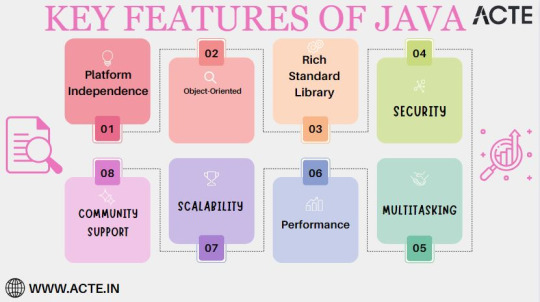
Java is not merely a programming language; it represents a dynamic ecosystem that empowers developers to fashion an extensive array of applications, ranging from mobile apps and web services to enterprise-grade software solutions. Its hallmark feature of platform independence, complemented by its rich libraries, security fortifications, and the formidable backing of a robust developer community, collectively underpin its enduring popularity.
In a world where digital innovation propels progress, Java stands as an essential cornerstone for building the technologies that sculpt our future. It's not merely a language; it's the key to unlocking a boundless realm of opportunities. For those seeking to embark on a journey into the realm of Java programming or aspiring to refine their existing skills, ACTE Technologies stands as a beacon of expert guidance and comprehensive training. Their programs are tailored to equip you with the knowledge and skills necessary to harness the full potential of Java in your software development career.
As we navigate an era defined by digital transformation, Java remains a trusted companion, continually evolving to meet the ever-changing demands of technology. It's not just a programming language; it's the linchpin of a world characterized by innovation and progress. Let ACTE Technologies be your trusted guide on this exhilarating journey into the boundless possibilities of Java programming.
7 notes
·
View notes
Text
Ensuring Data Security in Online Market Research while using AI to Collect Data
In the realm of Online market research, the integration of Artificial Intelligence (AI) has revolutionized data collection processes, offering unparalleled efficiency and insights. However, alongside these advancements, ensuring robust data security measures is paramount to safeguarding sensitive information.
Encryption Protocols: Implementing robust encryption protocols is the first line of defense in protecting data integrity. Utilizing industry-standard encryption algorithms ensures that data remains encrypted both in transit and at rest, mitigating the risk of unauthorized access.
Access Controls: Implementing strict access controls ensures that only authorized personnel can access sensitive data. Role-based access controls (RBAC) limit access to data based on predefined roles and responsibilities, minimizing the potential for data breaches.
Anonymization and Pseudonymization: Employing techniques such as anonymization and pseudonymization reduces the risk of exposing personally identifiable information (PII). By replacing identifiable information with artificial identifiers, researchers can analyze data while preserving individual privacy.
Data Minimization: Adhering to the principle of data minimization involves collecting only the necessary data required for research purposes. By reducing the volume of sensitive information stored, organizations can minimize the potential impact of a data breach.
Secure Data Transmission: Utilizing secure communication channels, such as encrypted connections (e.g., SSL/TLS), ensures that data transmitted between clients and servers remains confidential. Secure socket layers provide end-to-end encryption, safeguarding against eavesdropping and tampering.
Regular Security Audits: Conducting regular security audits and assessments helps identify vulnerabilities and areas for improvement within existing security frameworks. By proactively addressing security gaps, organizations can enhance their resilience to potential threats.
Compliance with Regulations: Adhering to relevant data protection regulations such as GDPR, CCPA, and HIPAA ensures legal compliance and fosters trust among participants. Compliance frameworks outline specific requirements for data handling, storage, and processing, guiding organizations in implementing robust security measures.
Continuous Monitoring and Response: Implementing real-time monitoring systems allows organizations to detect and respond to security incidents promptly. Automated alerting mechanisms notify administrators of suspicious activities, enabling swift intervention to mitigate potential risks.
Employee Training and Awareness: Educating employees about data security best practices and the importance of safeguarding sensitive information is critical in maintaining a secure environment. Training programs raise awareness about common security threats and equip staff with the knowledge to identify and respond appropriately to potential risks.
Vendor Due Diligence: When outsourcing data collection or processing tasks to third-party vendors, conducting thorough due diligence is essential. Assessing vendor security practices and ensuring compliance with data protection standards mitigate the risk of data breaches arising from external sources.
By implementing these comprehensive strategies, organizations can uphold the integrity and confidentiality of data collected through AI-powered online market research. Prioritizing data security not only fosters trust with participants but also mitigates the risk of reputational damage and regulatory non-compliance.
Also read:
The Right Approach to Designing & Conducting Online Surveys
Know more: Online Community Management Software
panel management platform
Online Project Management Platform
#market research#onlineresearch#samplemanagement#panelmanagement#communitypanel#datacollection#datainsights
2 notes
·
View notes