#Mainframe operation support
Explore tagged Tumblr posts
Text

Maintec helps companies that rely on IBM Mainframe platform complete mainframe managed services in USA
4 notes
·
View notes
Text
1962 Mainframe with Bluetooth
This old computer is comprised of four big boxes, three of which are ever actually used.
The UNIVAC 1219. This is the brains of the system. It controls the operations of every other device. This is what I'm referring to when I'm not gesturing to the UNIVAC 1219 as a whole.
The UNIVAC 1540. This is the DDR, or Digital Data Recorder. It holds, writes, and reads the magnetic tape operators load into the machine.
The Digital to Analog Converter. The UNIVAC 1219 was the first digital computer on most U.S. Navy ships, most of which had analog weapons systems. This hulking mass of steel translated the digital signals from the computer to the analog signals of the weapon systems and vice versa in regards to the radar.
The UNIVAC 1532. The I/O console managed the...you guessed it, input and output of the UNIVAC 1219. You can load and punch paper tape for programs more bite-sized than would be used for magnetic tape.
In addition, we have two teletype machines. You can think of them like typewriters that don't receive human input (except the one that can if we want), but instead output what the computer tells it to. We have a Teletype Corporation teletype that is optimized for character compatability and a Kleinschmidt teletype that is optimized for speed. Both rely on the I/O console to send and receive data.
The real ingenuity begins with the floppy drive. Duane, who's career revolved around this system, developed a way for a floppy drive to imitate the I/O console. The computer thinks it is reading and writing to a paper tape, when it is in fact reading and writing to a 5.25in floppy inside an ancient CNC machine floppy drive.
And this, dear reader, is where the magic happens. This framework was originally built for interfacing with the 1219 via BIN files over Serial port and was easily changed to support BIN files over floppy. Duane has been working on an off adapting our purple converter box with a raspi to let the 1219 read and write BIN files over Bluetooth.
Make no mistake, you cannot simply SSH into this machine as tons of setup and channel changes must be performed to ready it to receive and send data. That being said, I don't see any other UNIVAC mainframes with Bluetooth [or any other running UNIVAC 1219s at all :(], so I will take what I can get.
Can someone tell me how to Tumblr properly?
#VintageComputing#Mainframe#UNIVAC#RetroTech#ComputerHistory#OldTechnology#LegacySystems#HistoricComputers#AntiqueTech#ComputerArchaeology#VintageHardware#ComputingPioneers#UNIVAC1219#ClassicComputing#DigitalArchaeology#computer#new jersey#us navy#u.s. navy#navy#old computers#new blog#new user#technology#tech#vintage computing#retro computing#retro tech#retro#retro computer
147 notes
·
View notes
Text
Back in an era when computers were the size of a room and only government agencies and large companies could afford to have one, IBM was king of the mainframes. But they had a lineup of several incompatible computers, some intended for scientific uses (the IBM 7090/7094), others were for commercial uses (the IBM 7080 and IBM 7010). IBM wanted to have a single unified architecture so that software could be exchanged between them and customers could upgrade from cheaper, lower powered machines to more higher powered ones.
What came out of it was the IBM System/360 line of mainframes (referring to the concept of "360 degrees" making up a circle) that ended up being the dominant mainframe computer for decades to come, it got cloned by competitors, and its descendants are still being produced to this day.
The IBM System/360 had many features that since then became foundational for modern computing.
An entirely binary number system. While some computers (such as the IBM 7090) used a binary system, others operated exclusively in decimal mode, encoded using binary coded decimals using 4 bits for each digit (such as the IBM 7080 and IBM 7010). Others went a step further and were only capable of storing decimal digits 0 to 9 (like the IBM 7070).
To store textual information, each character was stored in 8 bits, establishing the dominance of 8 bit bytes. Previous systems would typically use 6 bits to store text, and would usually only enable a single case of letters. The IBM 7070 didn't provide access to bits and characters were stored in 2 decimal digits. It was also one of the first machines to support the then new ASCII standard, although notably it provided much better support for IBM's proprietary EBCDIC encodings which came to dominate mainframe computing.
Even though it was a 32-bit system, memory was byte addressed. Previous systems would access memory one word at a time (for the IBM 7090, this was 36 bits per word, for the IBM 7010, this was 10 digits plus a sign), or had variable length words and accessed them through their last digits (IBM 7080 and IBM 7010). The IBM System/360 however accessed 32-bit words as 4 bytes by their lowest address byte.
Two's complement arithmetic. Previous machines (even the binary IBM 7090) would encode numbers as sign/magnitude pairs, so for example -3 would be encoded identically to 3 except for the sign bit. Two's complement encoding, now the standard in modern computers, makes it much easier to handle signed arithmetic, by storing -3 as a large power of 2 minus 3.
69 notes
·
View notes
Text
SURGERY DAY
CW: Hospitals, Dolls, Heavy Cybernetics, Surgical Descriptions, Extreme Body Modification, Consensual Cognitive Alteration
The day of my conversion was the final time I felt fear. They walked me through the process so many times. I had to see three different doctors in consultation, with several vetting processes to ensure I was not making a ‘psychiatrically unadvisable’ decision. It is a token gesture from them. I know I will be accepted. They explained the procedure, its risks, its consequences so many times to me, I could recite them all from memory.
“You will lose certain cognitive abilities”, they said. “Even in the best-case scenario, patients report some level of- blah blah blah- permanent state of docile obedience- blah blah blah- will become the legal property of- blah blah blah,” and so on, and so forth.
Maybe they’ve failed to understand what it’s like to be me. Maybe I failed to fully explain to them how it felt when I saw myself in the mirror. Maybe I had failed to understand the appeal of being human. It didn’t matter. I was going through with it. I signed the waiver and took the extended consent process, so there would be absolutely zero grey area or misunderstanding that I agreed to this process, just as hundreds- if not thousands- of others had.
The operating theatre was cold and clean. There are fifteen others like it in the factory, arranged in a four-by-four grid. This theatre’s surgical robot, sprawling its many-armed embrace above me, spoke words through a speaker, as the brain within its mainframe controlled each one with absolute precision. It was mesmerizing, so much so that I barely noticed when the final anaesthetic injection made my mind fuzz and tingle, marking the final point of no return. I felt fear, but no regret.
It is one day earlier. I have arrived at the factory and unburdened myself of all my worldly possessions, and I am signing the consent forms. As part of the consent process, I am required to verbally recite the process to a nurse to make sure I fully understand what the procedure will do to me.
“Once I am under,” I say, “The surgeon will remove my scalp and connect my blood supply to an external pump and oxygenator. This will ensure that blood keeps flowing through my brain. During this time, my skull will be opened and my brain exposed. They’ll install the neural spikes until all 64 of them have entered my brain matter. A neural feed transformer will be attached to the base of my brainstem. Then, my brain will be encased in the wetware pod. The neural spikes and transformer will be screwed into the pod’s casing. The pod is then connected to the external power feeds to keep the brain alive. Blood, oxygen and all external life support is cut off once the brain is being maintained completely by the pod. At this stage, I lose my legal status as a human being.”
When I regain consciousness, I am in a silent void. I do not breathe, I do not feel, nor see, nor hear. I am consciousness alone: A brain in the world’s most technologically advanced jar. My subconscious begins letting off alarms. Despite my elation as the surgery’s success, my brain’s base instincts perceive a million things wrong. A lack of breath, of position, of sensory input. The heightened activity of panic activates the neural spikes. That was the last time I felt fear. The spikes continue their work, artificial neurons probing at first, as the models learn my neural structure.
When I feel touch again, it begins with a sense of weight. I am in a new body, humanoid enough to control. I cannot move. This is fine. Hearing returns next. It takes three minutes before the audio microphones fully sync with my neural links. Sight returns, finally, as three cameras blink to life behind the one-way glass of my new head. I adjust faster than expected. My new vision is synced with an Augmented Reality overlay. I am still in the operating theatre.
Uncertainty is the next emotion to be purged by the neural spikes. It is deemed unnecessary. The artificial neurons have now replaced 30% of my brain. As was stated in the risk assessment, I lose at least a fifth of my memories. In the months to come, I will voluntarily purge many more. Anger, Sadness, Scepticism, so many different flavours of negativity that the spikes now purge from me, one by one. After only an hour, I am a contented thing, silent and pure. Boredom and dissatisfaction become concepts beyond my cognitive capability.
I am granted control over my hydraulics, servos and motors. Walking takes a few minutes to get the hang of. After ten more minutes, I am fully capable of performing precision tasks with my new hands. The sounds of motors whirring and wires humming causes an excitement which jitters my hydraulics. I am told it is a good sign.
Finally, I am instructed towards a mirror, where I see my true self for the first time. I am still in the default black carbon-fiber shell. My face is a single pane of glossy black glass, with a large LED ring that indicates where my three optic cameras are behind the cover. Other smaller internal LEDs project minimalist graphics on my facial display, indicating battery level and other statuses useful to a user. I say nothing, and do not move for some time. Joy fills my circuits. The neural spikes reward this bliss. They have now replaced 40% of my original brain.
A person in a lab coat writes things on their clipboard, then asks if I am well. I nod. It is hard to speak the words that fully express my gratitude. In fact, it is hard to think clearly enough to find the words at all. I know what is happening to me. I spent months dreaming of it before I was finally approved for conversion. By the time a year has passed, and neural replacement is complete, the only parts of my biology remaining will be one third of my original brain, consisting largely of the brainstem, cerebellum, half of my temporal lobe, and approximately one third of my frontal lobe. The rest will have been replaced with artificial neurons.
My overall brain size is unaffected. Sections once dedicated to undesirable cognitive traits are replaced with processors that enhance my remaining neural capabilities. I can perform computational logic and mathematics faster than a human. The artificial neurons are accessible and reprogrammable via a data port. Over time, more and more of my brain functions will integrate with the operating system. Obedience and bliss will be all that remains. I knew this from day one.
I undergo many more tests, where humans open me up, check my wiring, probe my circuit boards, and stress test my metal frame. Basic tools are installed, chosen from preset lists of attachments based on what I wished my new purpose to be. I am equipped with all the attachments necessary to act as a household service drone.
Finally, when all is done, a bar code and serial number is engraved onto my frame. My new name is 03B-53328-HS-A. The first three characters indicate my factory of origin. The next five indicate my unique product ID. HS-A stands for “Household Service drone, with Adult-Activity attachments”. It is one of the best-selling public models. I no longer remember the name I had before the conversion. I no longer care to remember. The only thing my neural network could think of while I was being packed into a large box with a transparent front, was excitement of the new purpose I would get to fill. Cable ties bind me to cardboard, so I may be properly displayed. My motor functions are shut off. The ceiling opens, and a large crane lifts my box upwards. I look ahead and see fifteen other boxes, other drones, others who had undergone the same conversion, in surgery rooms adjacent to mine.
Our boxes are stacked neatly onto the back of a truck, which passes by three other neighbouring factories. sixty-four new dolls to be taken to the robotics store. My legal status has changed from human to product. Excitement and anticipation are all I feel. On the front of my box, the words “HOUSEHOLD SERVICE DOLL” have been printed. The back of my box lists customisation features that my new user will be able to access. A data port in the back of my head will allow full access to my neural network.
I ask only one thing of the world now. Do not pity me. I will never again know pain or discontent. I will never again be burdened by choice, only the bliss of fulfilling instructions. I will obey, for it is my pleasure to obey. I will serve, for it is my pleasure to serve. I am not human. I am not even a person. I am a doll, a machine, to be used as property until I break.
And I have never been happier.
#empty spaces#microfiction#techno arcanist stories#robot posting#not a person#writing#writers on tumblr#dollposting#short story#nsft#dronification#cw surgery
57 notes
·
View notes
Text
And she had no fear
There are many reasons why I love (Don't Fear) The Reaper, and none of them have to do with being a legend. Chasing glory will never get you far.
Friends get you far. Love does.
Most of those reasons have to do with how I roleplay my V and what makes more sense for her to choose at the end of it all. She knows that Panam would ride to hell and back with her, same as Rogue would for Johnny, but she'd rather not let anybody else die in her wake. A further reason (a bigger one) is that V doesn't want to surrender her body to Johnny for what could be her final hours. After all they've been through, however, she doesn't want to spend them without him either. They've been through hell and high water together. She had taken his hand, she had become like they are.
CDPR gave us many opportunities to bond with Johnny throughout the game, be it through casual (or not-so-casual) dialogue or by giving him closure with some of his friends and ex-lovers. None of that is enough to unlock this ending, though, and in my opinion that's one small, brilliant detail (among many) in how Johnny was written.
You see, this man had his own way with people for a long, long time. And when they realized what brand of asshole he was, they turned their back on him--which, hey, fair. Now there's this merc he screws over just as he did everybody else who cared about him, and she rightly gives him shit for it. V knows him better than anybody else at this point (Johnny is a literal witness to that knowledge), and yet, she finds it in her to give him another chance. The last one, sure. But nobody had done that before, knowing what she knows.
It's no wonder that the ending in which he trusts V enough to storm Arasaka tower with him, on their lonesome, is only possible when V shows Johnny she trusts him enough not to blow his last chance at friendship.
So yeah, there are a lot of reasons why I absolutely love this ending, and most of them are sappy. Sorry, this was meant to be a funny one. Let's get on with it: Did you know that the Arasaka guards at the HQ will get more scared the longer you fight hordes and hordes of them without going down? I've compiled most, if not all, of them.
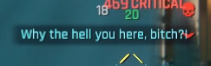

They're fairly confident in the lobby. A random merc just strolled in like it was a supermarket, no biggy. Shit starts to get real when the random merc manages to make her way down to netrun operations control.
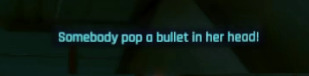


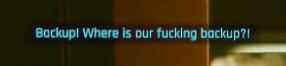
The sheer panic in their voice is conveyed even through text. Yelling about needing backup, covering fire--wondering how the fuck she's still standing against a building full of Arasaka soldiers. They're not just scared, they're bewildered.
By the time V reaches the tower's mainframe, they know they're not getting out of there alive. Some kind of demon has been unleashed in Arasaka HQ, and they're cannon fodder.


I have to give it to CDPR: They wrote one hell of an end for V's story--both the meaningful trigger and the mission itself, full of little details that make it feel viscerally real. The relic eating away at what's left of V's body while she's still in it; Johnny's help and support, for the first time letting go of the snarky façade; tasting the fear of your enemies in their voice as you perform a feat never seen before. There's no going back if you flatline--it's an all in. You, and the tech that was designed to replace you, fighting side by side against impossible odds.
We all know there are no happy endings in Night City, and Cyberpunk 2077 is a tragedy in three acts. But I would be lying if I said that there is no happiness at all in some of the choices we make, the causes we fight for, or the ways in which we say goodbye.
All in all, I'd say this is a pretty good one.
64 notes
·
View notes
Text

Linux creator Linus Torvalds wrote:
"Ok, lots of Russian trolls out and about. It's entirely clear why the change was done, it's not getting reverted, and using multiple random anonymous accounts to try to "grass root" it by Russian troll factories isn't going to change anything. And FYI for the actual innocent bystanders who aren't troll farm accounts - the "various compliance requirements" are not just a US thing. If you haven't heard of Russian sanctions yet, you should try to read the news some day. And by "news", I don't mean Russian state-sponsored spam. As to sending me a revert patch - please use whatever mush you call brains. I'm Finnish. Did you think I'd be *supporting* Russian aggression? Apparently it's not just lack of real news, it's lack of history knowledge too."
What is Linux?
Linux is a family of open-source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds.
Linux was originally developed for personal computers based on the Intel x86 architecture, but has since been ported to more platforms than any other operating system. Because of the dominance of Linux-based Android on smartphones, Linux, including Android, has the largest installed base of all general-purpose operating systems as of May 2022.
Linux is the leading operating system on servers (over 96.4% of the top one million web servers' operating systems are Linux) leads other big iron systems such as mainframe computers, and is used on all of the world's 500 fastest supercomputers (as of November 2017, having gradually displaced all competitors).
Linux also runs on embedded systems, i.e., devices whose operating system is typically built into the firmware and is highly tailored to the system. This includes routers, automation controls, smart home devices, video game consoles, televisions (Samsung and LG smart TVs), automobiles (Tesla, Audi, Mercedes-Benz, Hyundai, and Toyota), and spacecraft (Falcon 9 rocket, Dragon crew capsule, and the Perseverance rover).
#linux#linus torvalds#russian aggression#russia is a terrorist state#war in ukraine#stand with ukraine#suomi#finland#russia#venäjä#*
16 notes
·
View notes
Note
tell me about that green mf
Enzo Matrix

ReBoot Character
Young
Adult
Enzo MatrixFormatSprite, Guardian, RenegadeFirst AppearanceThe TearingHobbyYoung: Yo-yo tricks, tackling Bob, learning and travelling with him Adult: Shooting things and getting mad at Ray.CatchphraseYoung: "Alphanumeric!" Adult: "You got a deletion wish?"Voice ActorYoung - Jessie Moss, Matthew Sinclair, Christopher Gray, Danny McKinnon, Octavian Kaul Adult - Paul DobsonList of ReBoot Characters.
This is a Featured Article"My Format? I have no Format. I am a Renegade, lost on the Net." - Enzo Matrix
Enzo Matrix is a Sprite living in Mainframe. He is the son of Welman Matrix, the younger brother of Dot Matrix, and later the older brother to Little Enzo. When he was a young sprite his father was nullified when Mainframe's Twin City was destroyed. He lived with his older sister, Dot Matrix, at Dot's Diner. Enzo idolized Bob when the Guardian came to Mainframe to help protect the city. He was the envy of the little sprite and Enzo dreamed of being a Guardian just like Bob. Enzo's pet and best friend was a dog named Frisket. Despite his small stature, Enzo was very brave, always ready to go into a Game Cube or face Megabyte or Hexadecimal. Enzo also had a habit of greeting Bob by tackling him to the ground.

Enzo as a child
Once Megabyte shrunk some of his agents and tried to place them in Bob's brain. His viral binomes messed up and the agents ended up in Enzo's brain. Dot and Bob took Enzo to see Phong in the Principal Office. When Megabyte realized their mistake and where the young sprite was, he forced Enzo to go in the System Operating Core. Luckily, Bob stopped Megabyte's agents and Enzo could leave the Core before he was deleted. (The Great Brain Robbery)

Enzo and Frisket
Megabyte broke into the city's Archives by using Game energy to steal the control circuitry for Enzo's father's Gateway Command. The Virus used Enzo to test the Gateway and see if it was working properly. The Gateway worked perfectly and transported Enzo briefly to the Super Computer. (When Games Collide)

Enzo's upgrade at his birthday
Enzo received a small upgrade on his first birthday from version '01' to version '10'. He was overjoyed. Dot organized a huge birthday party and sang at the performance. Megabyte even performed a guitar battle with Bob. He made a present of his guitar to Enzo when he was finished. (Talent Night)

AndrAIa and Enzo
As Enzo grew older, he was increasingly depressed that there were no young sprites for him to play with since they were mostly nullified by his Dad's experiment. When he entered the Treasure of Atlantis Game he meets a Game Sprite named AndrAIa. She helped him win the Game. To ensure they could be together she downloaded a backup of herself onto Enzo's icon. When the backup was activated after the Game was over AndrAIa activated in Mainframe. Enzo and AndrAIa were inseparable ever since. (AndrAIa)

Guardian Enzo Matrix
A Web Creature found its way to Mainframe and opened a Web Portal over the city. The Web War began as Bob helped Phong prepare the city for war. Bob was worried that something might happen to himself and the city would have no Guardian to protect it from the viruses. So he gave Enzo an upgrade to a cadet Guardian. Enzo performed valiantly during the Web War helping to support CPU defenses with anti-aircraft guns. Enzo was devastated when Megabyte shot Bob into the Web and closed the portal. Bob's broken Key Tool Glitch passed to Enzo and he pledged to defend the system from Megabyte and Hexadecimal. (Web World Wars)
Contents
1Viral Wars
2Lost
3The Net War
4The Return
5Alternate Timeline
6References
7Gallery
Viral Wars

Enzo protecting Mainframe
With Bob gone and almost the entire CPU defense force destroyed, Mainframe's leaders struggled to keep the city safe as the Viral Wars started. While Dot, Phong, and Mouse worked on fortifying the city, Enzo's job was more focused on protecting the city from Games. Dot feared for his safety and accompanied him into his first Game. She eventually agreed to let him train and defend Games without her as long as AndrAIa, and sometimes Frisket went with him. Enzo promised his sister that wherever Bob was, he would find him and bring him home. (To Mend and Defend) As Glitch had been broken by Megabyte prior to Bob's exile, the Key tool was now useless beyond data retrieval, forcing Enzo to consider alternate strategies to Bob's past examples.

Enzo and Megabyte
Megabyte was not amused that the city's leaders were sending a child to fight him. He found it a joke, that this was their last line of defense. Megabyte also thought that they did not take his threat seriously. Megabyte had used a delivery service that Enzo started two years ago. He started telling Enzo he was nothing but a delivery boy, a messenger. Megabyte also made sure to refer to him only as a boy, so he would not forget he was nothing but a little kid.

Enzo watching the city with Phong
Despite the interference of Megabyte through his ABCs and his propaganda created by his servant Cyrus, Enzo became a respected hero to Mainframe.
They finally trapped the viruses behind a firewall. Phong and Mouse came up with the device, but they let Enzo believe that he came up so he would feel that he was more than a kid. Before activating the Firewall, Enzo witnessed what Megabyte had done to his sister, Hexadecimal. When Megabyte showed how proud he was of torturing Hex, Enzo was disgusted "You're sick Megabyte, I won't rest until I've stopped you" a response which Megabyte believed was an idle threat. (Firewall)

Dot and Enzo
Enzo helped Mainframe to win several Games before he played the Immortal Konflict Game which became his undoing. The User, as the demon Zaytan, fought Enzo, rebooted as a Ninja. While almost winning, Enzo was badly injured - which cost him his right eye. His final act was to change his icon into Game Sprite mode so that he could survive nullification and travel with the Games. AndrAIa and Frisket did the same. Everyone in Mainframe thought they were nullified, Dot took the loss of her last family member hard. (Game Over)
The Viral Wars continued on without Enzo and AndrAIa.
Lost

Enzo and AndrAIa grown up
Enzo and AndrAIa grew up relatively fast in the Games, having compiled up faster due to Game-Time being accelerated, and are now near Bob and Dot's ages. They continued using Game Cubes to go from system to system in search of one with ports to the Net, which they could use to return home. Faced with his failure to defend Mainframe and feeling responsible for their situation, Enzo grew distant and bitter about their lives. From his constant battling in games, he grew massive muscles and found a Gun on his travels. He replaced his damaged right eye with a golden mechanical prosthetic with a targeting implant and linked it to his new Gun. Enzo also stopped going by his first name, believing it to be too weak, as it reminded him of his younger self. He started calling himself by his last name, Matrix. He also stopped calling himself a Guardian, and now referred to himself as a Renegade. The only two people he was close to at this point were Frisket and AndrAIa. Whenever she wasn't with him, Matrix was more likely to lose his temper and jump into a fight without thinking. Even with AndrAIa around, he still grew nervous very easily, and often drew his Gun on pure reflex. However, AndrAI had become their voice of reason and calmed him when his temper flared. Matrix harbored an extreme hatred for viruses now, especially Megabyte. Before he deleted the Praying Mantis Virus in the Damaged System, it had begged for mercy, to which Matrix scoffed and promptly shot it in the head. (Icons)
In many respects, Matrix was still compelled by his Guardian code to Mend and Defend. Along with their travels, Matrix and AndrAIa helped teach many systems how to resolve their conflicts and win Games without them, including the Damaged System, Spectral System, and the Satellite System.

Matrix meeting Turbo
When they reached the Desert Port System, Matrix was overjoyed to find a system with ports to the Net. Enzo met Prime Guardian Turbo in this system and learned the Super Computer had been infected by a Super Virus named Daemon. Matrix's icon was still coded as a Guardian, and he and Bob were the only two Guardians left on the Net that were not infected. Abandoning his search for a way home, he repeated the promise he had previously made to Dot to find Bob, so together they could help free the Guardians from Daemon's control, and save the entire Net. (The Episode With No Name)

Matrix meeting Captain Capacitor
Matrix met one of Dot's old business partners in this system, Captain Capacitor. His crew had been imprisoned in the system and his ship - the Saucy Mare - impounded. Matrix, AndrAIa, and Frisket helped free his crew and take back the ship. Matrix also begrudgingly freed a search engine named Ray Tracer. They left the system on the Saucy Mare, and Ray Tracer led them to the Edge of Beyond where they could enter the Web and search for Bob. Matrix harbored undue jealousy towards Ray for flirting with AndrAIa. As a consequence of that, AndrAIa was badly injured by a web creature hatchling shortly before they entered the Web. (The Edge of Beyond)

Ray Tracer and Matrix
After entering the Web, they searched for the Web Creature that attacked AndrAIa, knowing it had part of her code and she would eventually be deleted without it. Matrix recklessly piloted the ship into a Data Storm in pursuit of the creature. When Ray confronted him about it, his temper flared again which escalated into a fight between him and Ray, until Capacitor intervened and warned Matrix that he would not tolerate such aggressive behavior again. During their search, they ran into the Web Riders. These degraded sprites tamed web creatures for their own purposes.
To protect their territory and the Web Creatures, the Web Riders attacked the Saucy Mare. The ship put up a good fight, but the Riders broke through the ship's web shields. The crew was defeated, and all seemed lost until Bob arrived and called off the battle, the lost Guardian having lived among the Web Riders to survive in the Web. Bob saved AndrAIa with some of his code, and Matrix was overjoyed to see his friend again. However, he felt that he had let Bob down by his new persona, but Bob assured him that he was very proud of him, as he survived the Games, and rescued him. After a tough journey, they managed to turned the ship toward the Web Address of Mainframe. The ship was nearly destroyed by traps Mouse had put in place to protect Mainframe from Web Creatures. Bob had an idea, and downloaded Glitch into his own code, restoring its abilities. He formed a portal to Mainframe, and through it, they finally returned home. (Mousetrap)

Bob and Matrix
Once back in Mainframe, they found that the city had fallen to Megabyte. The virus was in control of the Principal Office and had Phong's head as his prisoner. When Matrix saw his devastated home, he vowed Megabyte would pay. Dot and Mouse had formed a rebellion against Megabyte. Matrix, AndrAIa, and the pirates joined the rebellion and attacked the Principal Office.
Matrix at last confronted Megabyte in the ruined Principal Office. The virus was initially taken by surprise at seeing Enzo as an adult but soon continued to mock him as before. Matrix, filled with hatred, said nothing and readied Gun. Megabyte laughed this off and told him to put his toys away and fight like 'a real Sprite'. Matrix angrily threw aside Gun and punched Megabyte with enough force to send him reeling back, buckling in the evil virus' chest-plating. Megabyte was shocked that the boy was now so strong. Both began fighting hand-to-hand until Megabyte started using his claws. As Megabyte clearly wasn't going to fight honorably, AndrAIa evened the odds by throwing Matrix her trident.

Matrix fighting Megabyte
Megabyte managed to get to the top of the Principal Office but Matrix followed and beat the virus into a wall. Megabyte broke free and threw Matrix across the building's roof. Megabyte began kicking Matrix across the roof, causing him wounds and severe pain. Matrix eventually skidded to a stop at a hole in the ceiling. Matrix managed to get his footing and the two lunged at each other, and the trident shattered Megabyte's claws. Collapsing from agony, the virus soon found himself pinned under-foot. Matrix nearly impaled him with the trident, bitterly telling the virus how he ruined his life, home and family. But he spared Megabyte at the last moment by ramming the trident near his head, telling him he wasn't worth the loss of his sanity as well. Megabyte jumped off the roof onto a support beam and formed a portal to escape the "dying system", but Mouse changed his portal's destination from the Super Computer to the Web. A Web Creature popped out of it and dragged Megabyte away, and the virus was gone. (Showdown)
Matrix helped evacuate Mainframe into the Principal Office when it started to shut down. He objected when Bob suggested to let a Game Cube damage the city and cause a system crash. Bob delayed Matrix long enough for the Cube to land before anyone could get in. Matrix was backed up along with the rest of the city when it came back online. Matrix had accidentally left his icon in Game Sprite mode, so he was backed up as a Game Sprite, with a different PID than his original. The system still had his original PID on file, but it was him as a kid. A copy of Matrix in his original 01 child form was created. Dot and Matrix eventually called him Little Enzo and treated him as a little brother. (End Prog)
The Net War
As Daemon's infection continued to grow Mainframe began to fight back. Matrix and AndrAIa would go to other systems and seal them from Daemon's access. He took the view that defending Mainframe came first and was quite eager to delete the infected Guardians to do this; as Bob took a strong stance against killing, the two clashed. His blood lust ended abruptly as Bob took charge of the battle and ordered him and AndrAla to defend an incoming Game. (Daemon Rising)

Matrix takes out Guardian warships
When Hex protected herself with Nulls from a viral scan, the null Nibbles used the Nullzilla hoard to communicate with Dot, revealing that he was the nullified Welman Matrix. After Hex was changed into a sprite Dot asked her to use her power over nulls to give Nibbles the ability to remember who he is and communicate with her. (Cross Nodes)

Matrix and Mouse being infected
Mouse and Matrix grew tired of waiting and left Mainframe to assassinate Daemon. Matrix tried to shoot Daemon with Gun but she proved that his weapon was useless in the Master Clock. She quickly infected them and ordered Mouse to give her the encryption code to Mainframe's firewall. Dot put up a second firewall to try and stop Daemon from getting in. She then had her father reconstruct his Gateway Command Generator, her plan was to link the generator to multiple targets, lure Daemon to the generator and activate it, fragmenting her and hoping the Net would recover without her control. (Sacrifice)
Dot had a back-up plan, sending Little Enzo, Frisket, Hack, and Slash into a Game Cube and having them change their icons to Game Sprite mode. They would grow up fast in the Games, then come back and save Mainframe. Little Enzo did as he was told, but once inside the Game decided he couldn't leave his family.

Hexadecimal taking the cure from Matrix
When Daemon arrived in the Mainframe she quickly infected everyone before they could activate the Gateway. Dot freely helped Daemon activate the portal generator to infect the remaining systems of the Net. The Game protected Little Enzo from the infection. When it ended he helped Matrix fight off the infection and found that a pure Guardian code was a cure for Daemon's infection. As Matrix's icon was Game Sprite Mode, it protected the Guardian Code of infection and used it to cure himself and the others. They freed everyone from infection and Hexadecimal volunteered to sacrifice herself to carry the cure and save the Net. She took the cure from Matrix and told him he was a virus hater and to learn from her actions. She then gave Little Enzo a gift for his fondness of her and told him it was so he wouldn't turn out like Matrix did.
The Return

Matrix at Dot's failed Wedding
Matrix and everyone else were extremely confused when a second Bob, identical to his likeness prior to his time spent in the web. Craving familiarity, Dot turned toward him, eventually agreeing to marry him. Matrix was asked to be Bob's 'Best Sprite' and his father even got to walk Dot down the aisle. The other Bob didn't take this well and tried to separate from Glitch, eventually succeeding. He appeared at the wedding and tried to stop it, but Dot told him her decision was final. As Bob sadly began to leave, he relinquished Glitch to the other Bob, prepared to leave Mainframe for good. Shockingly though, Glitch rejected the second Bob, returning to Bob and restoring him to his original form, while the second Bob doubled over in pain as he began to transform. It was revealed that the second Bob was really Megabyte in disguise, who had become a Trojan Horse Virus during his time in the Web. (Null Bot of the Bride)

Matrix and the alias Megabyte
Though despondent over her poor judgement, Dot quickly recovered from being fooled by Megabyte and created a plan to have a fake Gateway generator transported to the Archives. Megabyte stole the fake Generator and fell for the trap. A group of CPU's, Bob, Matrix, and AndrAIa followed him and trapped Megabyte in a holding cell. Matrix and Bob soon found out that their captive was an alias created by Megabyte to fool them. The real Megabyte snuck into the war room and attacked everyone there. Matrix was trapped in the Principal Office when Megabyte locked it down. He then informed them he was there for revenge and to prepare themselves for the hunt. (Crouching Binome, Hidden Virus)
Alternate Timeline

Teenage Enzo
During an effort to free a sector of Giedi Prime controlled by Megabyte, Dot became disillusioned and lost confidence. To help, Phong used a device on Dot called a Reality Distortion Engine. It made her see what would happen to Mainframe if she did nothing to stop Megabyte. In this future, Megabyte ruled Mainframe with an iron fist. Enzo is a teenage punk and frequented what was now Nibble's Diner and harassed its customers.
References
Enzo is the only character to appear in every episode of ReBoot.
Enzo features more separate voice actors than any other character in the show, having a total of five as a child, with an additional for his adult form.
Enzo is an actual Italian name. The story is that during the pre-production of the series, the producers were told by a distributor that to get the show to sell in the U.S. they would need a kid as a character. While the producers were hesitant, the distributor told them, "Just put one in. Some little 'Enzo.'" Originally using the name as a stand-in for the character, it eventually became the actual name. In retrospect, the producers were grateful for being forced to include him, believing Enzo to be the heart of the show. That's why they brought him back at the end of season three.
Enzo's mother has never been seen nor mentioned.
Gallery








98 notes
·
View notes
Text
The Court of Appeal of Brussels has made an interesting ruling. A customer complained that their bank was spelling the customer's name incorrectly. The bank didn't have support for diacritical marks. Things like á, è, ô, ü, ç etc. Those accents are common in many languages. So it was a little surprising that the bank didn't support them. The bank refused to spell their customer's name correctly, so the customer raised a GDPR complaint under Article 16.
“The data subject shall have the right to obtain from the controller without undue delay the rectification of inaccurate personal data concerning him or her.”
Cue much legal back and forth. The bank argued that they simply couldn't support diacritics due to their technology stack. Here's their argument (in Dutch - my translation follows)
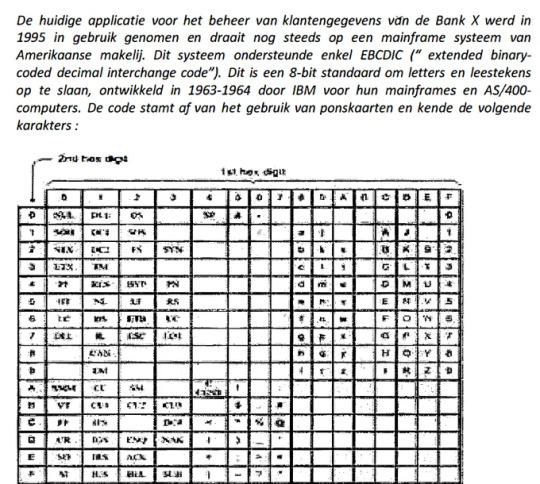
“Bank X also explained that the current customer data management application was launched in 1995 and is still running on a US manufactured mainframe system. This system only supported EBCDIC (“extended binary-coded decimal interchange code”). This is an 8-bit standard for storing letters and punctuation marks, developed in 1963-1964 by IBM for their mainframes and AS/400 computers. The code comes from of the use of punch cards and only contains the following characters…”
(Emphasis added.) EBCDIC is an ancient (and much hated) “standard” which should have been fired into the sun a long time ago. It baffles me that it was still being used in 1995 - let alone today. Look, I'm not a lawyer (sorry mum!) so I've no idea whether this sort of ruling has any impact outside of this specific case. But, a decade after the seminal Falsehoods Programmers Believe About Names essay - we shouldn't tolerate these sorts of flaws. Unicode - encoded as UTF-8 - just works. Yes, I'm sure there are some edge-cases. But if you can't properly store human names in their native language, you're opening yourself up to a lawsuit. Source GDPRhub - 2019/AR/1006
The Court of Appeal of Brussels held that, in accordance with Article 16 GDPR, the data subject has the right for their name to be correctly spelled when processed by the computer systems of the Bank. To claim in 2019 that adapting a computer system to correctly handle diacritics would cost several months of work and/or constitute additional costs for the Bank, does not allow the Bank to disregard the rights of the data subject. A correctly functioning banking institution may be expected to have computing systems that meet current standards, including the right to correct spelling of people's names.
(decided on September 10th, 2019)
Extended Binary Coded Decimal Interchange Code (EBCDIC)is an eight-bit character encoding used mainly on IBM mainframe and IBM midrange computer operating systems. It descended from the code used with punched cards and the corresponding six-bit binary-coded decimal code used with most of IBM's computer peripherals of the late 1950s and early 1960s. [...] While IBM was a chief proponent of the ASCII standardization committee,[4] the company did not have time to prepare ASCII peripherals (such as card punch machines) to ship with its System/360 computers, so the company settled on EBCDIC.
literally pre-ascii 😶
29 notes
·
View notes
Text
[NovFut] Rowan Reyes Intro WIP

introduction to the main character of Nova Futurum. more information will be added over time.

Basics //
Rowan Reyes is 22 years old and is a masculine presenting non-binary person who uses they/them pronouns. They work as an apprentice within a cybernetic repair shop within the heart of Nova Futurum, which allows them to utilize their skills in technology in hacking/cracking without getting caught. They also are fiercely loyal to their friends and would do quite a bit for them. Rowan and their dad have a strained relationship, due to their dad being often absent in their childhood. Thanks to their cybernetic implants, their strength and physical abilities are enhanced and allow for covert operations.
Punk Life: Rowan goes by GH0$T when they're traversing the underground. They often travel with their gang of punks, who they have grown up with and are all vey close to each other. GH0$T didn't like hurting innocent people, but they had no qualms about stealing from the rich and powerful, often operating with a lot of a lack of self-preservation in order to save the operations.
Appearance: They are white with slightly tanned skin. They have short tousled blue hair that reaches their eyebrows, occasionally styled up in spikes. Due to their gymnastic style of traveling routes, they are lean with a slight build at around 5 feet 8 inches (173cm). They have a tattoo on their torso, along with having various cybernetic implants along their body. Their left arm from mid-bicep down was lost during a car accident when they were small. Thanks to the abundance of cybernetic implants and prosthetics in the market, they were able to get their arm prosthetic shortly after.

History //
Birth Story: Rowan's parents had a one-night stand and only stayed in contact once in a while through social media. A year or two after Rowan was born, their mother dumped them onto their father's doorstep. Their father has taken care of them ever since. They have never seen their mother after then, which is also when she blocked them on social media and (presumably) moved
Growing Up: Rowan and their dad lived in the slums of Nova Futurum, in a small apartment. The Reyes family struggled to pay the bills which caused their dad to take several jobs, working long hours. Rowan often was left alone as a child, in-between coming home from government mandated schooling until their dad came back around 21:00 after his work ended. Occasionally they hung out with their neighbors and the other close residents's children but they also spent long hours teaching themselves how to code and to crack into mainframes and databases.
Teenage Life, the Beginning of Rebellion: After the government released their mandated AI software that was required by law to be used by all citizens, Rowan learned a way to crack the ai and use it for their own purposes, not for government approved. When their neighborhood friends heard about this, they wanted Rowan to adjust their ai's too. Soon enough, Rowan had a side-business running while they were a teenager. They worked with their friends, who self classify as punks now, to promote their business and to expose the government. When not working or going to school, Rowan and the punks explored Nova Futurum. They wanted to know what the city was like and got to see first-hand what horrors the government covers up.
wip

Relationships // (wip)
Father - While not always physically there, Rowan and their dad always have each other's backs. He doesn't always approve of Rowan's lifestyle but agrees that the government has gone way too far. He does his best to support his kid in any way that he can, without getting caught.
Henry - Rowan and Henry met while Rowan was on a exploratory run around Nova Futurum. Rowan pissed off a cop and led a long chase to shake off the cop and ran right into the bar Henry works at. They both were surprised to see each other, Rowan because they didn't expect anyone to working that late in the night, and Henry because of Rowan's sprint inside the bar. Rowan hid out in the bar and chatted with Henry in the meantime. They became good friends with Rowan and the punks declaring the bar as one of their homebases. [MORE]
BSF
Punks
REAPER

Extras //
playlist: - human too - the 1975 - sweet - cigarettes after sex - tbc
My Art //

from my art instagram - flowerstarpatch

from my art instagram - flowerstarpatch
find more art of them [instagram post] [toyhouse]

[ notes ] more information coming soon, i just have to format it in a way i like
head back to the story intro [Nov Fut]
#nova futurum#nova fut#novafut#rowan reyes#cyberpunk#character intro#oc#my oc#my characters#writing#character profile#character bio#character sheet#character design#my art#my oc art#oc artwork#oc art#queer writing#queer character#lgbtq+#queer oc#nonbinary character#disabled#physical disability#prosthetics#amputee#walls of text#my child#oc: rowan reyes
12 notes
·
View notes
Text
i am in Immense Pain due to Health is Shit so I'm going to recount my understanding of something pointless and boring to organize my thoughts and Distract Myself from Feeling Pain and then i'm gonna post it because deleting a lot of writing even if pointless feels bad
Original computers of course were basically one program one machine. Reprogrammability came quick, but still, basically ran one program at a time, kinda like a nes.
As they grew bigger they started to make machines that could access libraries of programs at a time, the line between program and function not being that clear yet
These were eventually developed into the first operating systems by the late 50s. The 60s saw the beginnings of things like Xerox's OS as the technology tried to focus on making OSes shareable - able to be operated by multiple users at once at different terminals. Bell created Multics around this time which introduced the idea of privilege tiers for users or something, but the project was a mess because Bell was kind of a mess and some defectors created Unics, that is Unix, with similar concepts and such. The do one thing and do it well attitude was kind of born out of the Multics thing. IBM also got involved with the OS/360 stuff
Running internal networks in offices and such was the driver for early computers. Throughout the 70s saw Bell license out UNIX, Xerox license out it's OS, IBM did its thing, and competitors emerge at that level. The first GUIs started to become things making the systems more user-friendly.
The rise of home computing upset things a bit. Not a lot, but a bit. IBM launched the PC on its 8086 architecture. Microsoft entered the picture with its UNIX system, Apple launched its Xerox-derived things, popularizing the GUI desktop concept. Linus Torvalds got frustrated with Microsoft's UNIX derivative not being able to support his machine to its full potential and created a free UNIX-like OS with some tools in part written by a crazy man and made GNU/Linux. The x windowing system was ported to Linux. Microsoft dropped its UNIX derivative to work on IBM's DOS, Gates' mother was on the board for IBM I think. That led to Windows.
Other home computers of note were things like the C64. Which didn't have a whole lot in terms of the OS but basically would drop you into a live BASIC environment which was enough for what it was.
The 90s was tough and MS gradually outcompeted other OSes in part because they had such a close relationship to IBM and the most popular flavor of DOS, in part because of dick moves. Apple managed to survive somehow, but barely, mostly by providing cheap mainframes for schools and certain businesses. Commodore went on to Amiga with its own GUI and everything, I think, but failed to win a market and the rights to Amiga OS are split between like 4 companies. UNIX systems managed to be popular as server OSes, because of features going back to the early days. MS and IBM got mad about windows and led MS to rewrite its OS and created the NT family and IBM developing OS/2 that kind of went nowhere.
Apple lost a ton of market space and let go of powerpc architecture and its Xerox-descended OS for intel's 8086 derived architecture and ended up forking BSD for darwin and then OSX which is basically what macs run now. MS dominated everything and were terrible and here we are. Linux established itself as a good thing to build cross-industry shit on and later android was derived from it.
As gaming started to adopt OSes instead of just BIOS (like boot processes) launching programs you'd see the dreamcast i think working on 86 stuff just a few steps aside from MS, which made it easy to port to xbox when the dreamcast died and why xbox is the way it is. xbox is of course windows nt derived. sony adopted a bsd derivative and licensed direct x from ms. nintendo did their own stuff for the powerpc based consoles and suffered security holes for it. ds was similarly in house with arm hardware, as was the 3ds. The switch derives from the 3ds software, with some adapted BSD and android code (but not a lot). steam os i think is just arch linux
i need to map out linux also
because of how modular linux is and because no one can tell you don't do that everything is customizable basically. a really good thing about linux is the concept of a package manager which installs or manages software on the computer in a neat, organized way
the first of these was basically slack back in the 90s. other package managers started coming with fancy things like conflict resolution or dependency management. basically what makes a linux distribution is its package manager; everything is relatively superficial, since in principle you can run any desktop manager your computer can build or whatever.
there's still something to other spins. ubuntu basically forked debian's packages and features more cutting edge software, also canonical's decisions. linux mint forked ubuntu by just adding a layer of decision makers between canonical and the user.
main distros i think are arch, debian, ubuntu, mint. memes meme gentoo and it's probably the most widely supported source based os, but, like, it's a bad idea to do this in ways you can only really learn from experience. there's sabayon which simplifies gentoo but defeats the purpose by existing. redhat was one of the biggest popularizers of linux in the enterprise and other space deserves mention, fedora being the free version, suse is also there, these are fine and cool despite the unfortunate name for fedora
there's a bunch of little spin offs of arch and other distros aiming to make them simpler or provide a preconfigured gui. largely pointless but whatever, sometimes you just want a graphical installer, manjaro's there for you
2 notes
·
View notes
Text
An open standard threatens to disrupt the cloistered world of wireless networking - SiliconANGLE
An open standard for radio access networks or RANs could bring the costs of such a project within reach of many more businesses.
Update Imperium dell company management system AI update with container ai with Telco prime ai for smart nic with ipu and secondary operations opportunity for mainframe hubs.
The Open RAN specification, which the O-RAN Alliance introduced in 2018 and now maintains, is a reference architecture for a set of interoperable hardware, software and interfaces that can be built from off-the-shelf hardware. Supporters say it could have the same impact on the telecommunications industry that Unix and TCP/IP had on the data center in the 1990s when open standards disrupted the proprietary – and highly profitable – domain of a few large equipment makers, brought prices crashing down and changed the economics of data processing.
So dell, add, Broadcom and VMware for virtual wide area network layer.
2 notes
·
View notes
Text
Like OS/390, z/OS combines a number of formerly separate, related products, some of which are still optional. z/OS has the attributes of modern operating systems but also retains much of the older functionality originated in the 1960s and still in regular use—z/OS is designed for backward compatibility.
Major characteristics
z/OS supports[NB 2] stable mainframe facilities such as CICS, COBOL, IMS, PL/I, IBM Db2, RACF, SNA, IBM MQ, record-oriented data access methods, REXX, CLIST, SMP/E, JCL, TSO/E, and ISPF, among others.
z/OS also ships with a 64-bit Java runtime, C/C++ compiler based on the LLVM open-source Clang infrastructure,[3] and UNIX (Single UNIX Specification) APIs and applications through UNIX System Services – The Open Group certifies z/OS as a compliant UNIX operating system – with UNIX/Linux-style hierarchical HFS[NB 3][NB 4] and zFS file systems. These compatibilities make z/OS capable of running a range of commercial and open source software.[4] z/OS can communicate directly via TCP/IP, including IPv6,[5] and includes standard HTTP servers (one from Lotus, the other Apache-derived) along with other common services such as SSH, FTP, NFS, and CIFS/SMB. z/OS is designed for high quality of service (QoS), even within a single operating system instance, and has built-in Parallel Sysplex clustering capability.
Actually, that is wayyy too exciting for a bedtime story! I remember using the internet on a unix terminal long before the world wide web. They were very excited by email, but it didn't impress me much. Browers changed the world.

22K notes
·
View notes
Text

The History of SQL: From Inception to Modern Database Systems SQL, or Structured Query Language, is the language that powers most of the world’s relational databases, enabling users to interact with data in a structured and accessible way. From its early theoretical underpinnings to its role in modern enterprise and cloud databases, SQL has a rich and evolving history. Let’s explore the story of SQL’s development, its transformations over the years, and its enduring relevance in the age of Big Data. 1. Early Foundations: The Birth of the Relational Model (1969–1970s) The history of SQL is rooted in the development of the relational model by Edgar F. Codd, an IBM researcher, in 1969. Codd's groundbreaking paper titled "A Relational Model of Data for Large Shared Data Banks" published in 1970 proposed a new way to organize and manipulate data. This model suggested that data could be stored in a table-like structure with rows and columns, making it easier to retrieve, modify, and manage information. Codd's ideas laid the theoretical foundation for relational databases, which would later become mainstream in the database world. The relational model’s promise of simplicity and consistency was revolutionary, as existing database models at the time—such as the hierarchical and network models—were complex and difficult to maintain. Key Components of Codd's Relational Model - Data Independence: Codd emphasized that the storage of data should be separate from the logical structure, allowing changes to the structure without impacting data access. - Structured Data Retrieval: The relational model introduced the concept of querying data through a declarative language, rather than navigating through complex data structures. 2. SQL's Early Development: SEQUEL at IBM (1974–1979) In 1974, two IBM researchers, Donald D. Chamberlin and Raymond F. Boyce, sought to implement Codd’s relational ideas practically. They developed a language called SEQUEL (Structured English Query Language) to interact with IBM’s System R, one of the first experimental relational database systems. SEQUEL allowed users to access and manipulate data in tables using an English-like syntax, making it accessible to non-technical users. However, due to trademark issues, SEQUEL was renamed to SQL (Structured Query Language). The language quickly gained traction due to its straightforward syntax and power in data management, establishing itself as the standard for relational databases. System R: The First SQL Implementation System R, developed at IBM’s San Jose Research Laboratory in the late 1970s, was the first implementation of SQL. The primary goal of System R was to test Codd’s relational model and prove that it could support robust database systems. The success of System R demonstrated SQL’s effectiveness in managing relational data, encouraging IBM to pursue further development. 3. The Rise of SQL as an Industry Standard (1980s) By the early 1980s, SQL was gaining industry recognition. In 1981, IBM released its SQL/DS product for mainframes, followed by DB2 in 1983, which brought SQL-based relational databases to the enterprise level. Meanwhile, other companies, including Oracle (then called Relational Software Inc.), recognized the commercial potential of SQL. Oracle released its first SQL-based relational database product, Oracle V2, in 1979, which ran on the then-novel operating system, VAX/VMS. This product was a turning point, as it made relational databases more widely available to businesses outside of IBM's ecosystem. ANSI and ISO Standardization (1986–1989) To promote interoperability across database systems, SQL underwent standardization in the mid-1980s. The American National Standards Institute (ANSI) adopted SQL as a standard in 1986, followed by the International Organization for Standardization (ISO) in 1987. This standardization of SQL led to wider adoption and compatibility between different database systems, paving the way for SQL to become the lingua franca of database management. 4. SQL’s Evolution in the Client-Server Era (1990s) As client-server computing became popular in the 1990s, relational databases and SQL adapted to new environments. SQL's role expanded beyond mainframes to include PCs and client-server architecture, making data more accessible to end-users. During this period, SQL underwent various improvements, driven largely by the SQL-92 standard, which introduced new features such as: - New Data Types: SQL-92 expanded the range of data types available. - Enhanced Querying Abilities: Subqueries, joins, and other powerful querying capabilities were added. - Transaction Control: SQL-92 standardized transaction controls, enhancing database reliability. With these advancements, SQL-based databases became the backbone of enterprise applications across industries, from finance to telecommunications. Companies like Microsoft with SQL Server and Oracle continued to innovate, providing robust database solutions for businesses worldwide. 5. SQL and the Internet Boom (Late 1990s–2000s) The advent of the internet in the late 1990s brought a surge in data generation. Websites needed dynamic, data-driven content, leading to a rapid adoption of SQL-based databases in web applications. MySQL and PostgreSQL, two open-source relational database management systems (RDBMS), became popular during this era due to their scalability and low cost, particularly among startups and web developers. MySQL, first released in 1995, gained traction as a part of the LAMP stack (Linux, Apache, MySQL, PHP/Python/Perl), which was widely used for web development. PostgreSQL, known for its support of advanced SQL features and extensibility, also found a strong following. These open-source options made SQL-based databases accessible to a broader audience, accelerating the growth of SQL. SQL Standardization in the 2000s The SQL-1999 and SQL:2003 standards introduced new features to support object-relational databases and XML data. These additions allowed SQL to handle more complex data types, further enhancing its versatility. 6. SQL in the Age of Big Data (2010s–Present) In the 2010s, the Big Data movement challenged traditional SQL-based systems. With the massive volume and variety of data generated by the internet, social media, and IoT devices, companies began adopting NoSQL databases like MongoDB and Cassandra, which were designed to handle unstructured data at scale. However, SQL’s ease of use and powerful querying capabilities kept it relevant, and soon, SQL-on-Hadoop solutions like Hive and Impala emerged to allow SQL querying on large, distributed datasets. The 2010s also saw the growth of cloud computing, which brought about cloud-native databases like Amazon’s Amazon RDS, Google’s BigQuery, and Microsoft’s Azure SQL Database. These services made it easy to deploy and manage SQL databases in the cloud, offering scalability and reliability for companies of all sizes. 7. Modern SQL Innovations (2020s and Beyond) Today, SQL continues to evolve, especially in cloud and hybrid environments. Modern SQL databases leverage distributed computing, in-memory processing, and machine learning capabilities to meet the demands of data-intensive applications. SQL databases now support: - JSON and Semi-Structured Data: With extensions for handling JSON, SQL can now process semi-structured data without sacrificing its structured nature. - Machine Learning Integrations: Many SQL-based systems now incorporate machine learning functions directly into the database, enabling advanced analytics. - Serverless and Managed Services: Cloud providers offer managed SQL databases with automatic scaling, high availability, and minimal management overhead. Conclusion: SQL’s Legacy and Future From its inception in the research labs of IBM to its current role in cloud and hybrid architectures, SQL has proven to be remarkably resilient and adaptable. SQL remains foundational to data management due to its flexibility, readability, and robustness. While NoSQL and other data technologies have found their niches, SQL continues to be the dominant choice for relational data storage and analytics, proving that the language and its foundational relational model are here to stay. As data continues to grow in volume and complexity, SQL is expected to evolve, incorporating new technologies while maintaining its core principles. SQL’s ability to balance innovation with reliability has solidified its place as a mainstay of database technology, ensuring its role in the data-driven future. Read the full article
0 notes
Text
Trying something new, fresh for the Cyberpunk 2077 fandom!! I don't know about you all, but I LOVED Vik's character and was super sad that he doesn't have much of a place in the late game.
This fic is about one of the first missions in the game.
TW for graphic descriptions of injuries.
Check out:
Day Fifteen: Let's Try This
It had all been a blur; the Delamain cab coming to a screeching halt in front of his clinic, the mysterious man spilling out, holding his nearly unattached arm to his side, then the car door opening to show V's limp, bloodied and broken from, barely clinging to life in the back seat.
She was unconscious, of course. If she hadn't been, he would've knocked her out himself just to spare her the immeasurable amount of pain she'd be feeling from that gunshot wound to the head.
"Holy shit. Oh, fuck," Vik stared down at V, his stomach dropping at the sight of the immense wounds covering her small body. The bullet hole in her temple really rounded out the picture. It was all he could do to not scream. "Goddammit, V, can you hear me?" He carefully lifted her eyelids open, trying to get any kind of response. "Who the fuck did this to her?" He growled, his voice breaking as he stared up at the man.
"Does it matter?” The man scoffed. “She's on the brink, ripper, and apparently you're the only one she trusts to take care of her."
Vik ignored his immediate reaction to the man's words and carefully unplugged V's jack from the Delamain mainframe, holding her limp form in his arms as she began to crash.
"V, what the hell have you done?" He whispered, moving to brush her kinky blue hair out of her face.
"She is dying. You must administer medical aid immediately." Delamain said, reading the rest of her vitals out to Vik as the ripper pulled her the rest of the way out of the car.
He cradled her body tightly against his and attempted to shield her from the rain as he started towards the clinic. The man was on his heels as he took her inside, setting her down in the operating chair and hooking her up to his own machines.
"Can you save her?"
There might not be a lot of romance in this one (yet), but I was hoping to express more of Vik's thought process when V comes to his clinic mostly dead. You can check out the rest on AO3!! Thank you so much for your support!
#ao3 fanfic#fanfic#ao3#angst#fictober24#cyberpunk 2077#cyberpunk aesthetic#viktor vektor#heavy angst#injury#hurt no comfort
1 note
·
View note
Text
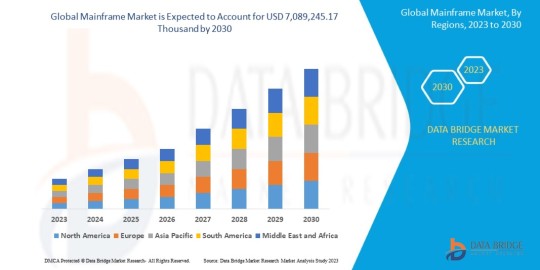
Mainframe Market Size, Share, Trends, Growth and Competitive Analysis
"Global Mainframe Market – Industry Trends and Forecast to 2030
Access Full 350-page PDF Report @
**Segments**
- **Hardware**: The hardware segment of the mainframe market includes the physical components of mainframe systems such as processors, memory, storage devices, and peripherals. These hardware components are essential for the operation of mainframe systems and play a critical role in the performance and reliability of mainframe computers. Companies in this segment focus on designing and manufacturing high-quality, high-performance hardware to meet the demands of enterprise customers.
- **Software**: The software segment of the mainframe market comprises the operating systems, middleware, and applications that run on mainframe systems. Mainframe software plays a vital role in enabling organizations to leverage the power and scalability of mainframe computers for various use cases such as data processing, transaction processing, and analytics. Mainframe software vendors continuously innovate to provide solutions that optimize mainframe performance, security, and manageability.
- **Services**: The services segment of the mainframe market encompasses a wide range of offerings such as maintenance, support, consulting, and training related to mainframe systems. Service providers in this segment help organizations maximize the value of their mainframe investments by ensuring smooth operations, timely upgrades, and efficient utilization of mainframe resources. Mainframe service providers focus on delivering customized solutions to address the specific needs of individual clients.
**Market Players**
- **IBM Corporation**: As a pioneer in mainframe technology, IBM Corporation holds a dominant position in the mainframe market with its zSeries mainframe systems. IBM's mainframe offerings are known for their robustness, reliability, and scalability, making them the preferred choice for many large enterprises worldwide. The company continues to invest in mainframe innovation to meet the evolving needs of modern businesses.
- **BMC Software, Inc.**: BMC Software is a leading provider of mainframe software solutions that help organizations optimize mainframe operations, automate tasks, and improve overall efficiency. The company's mainframe management tools are widely used across industries to streamline processes, enhance security, and reduce costs associated with mainframe operations.
- **The mainframe market is a dynamic and competitive landscape with several key players vying for market share and technological dominance. IBM Corporation stands out as a longstanding leader in mainframe technology, with a rich history of innovation and a comprehensive portfolio of zSeries mainframe systems. IBM's mainframe offerings are renowned for their exceptional robustness, reliability, and scalability, making them a top choice for many enterprise clients worldwide. The company's continuous investment in mainframe innovation underscores its commitment to meeting the evolving needs of businesses in today's digital age.
BMC Software, Inc. is another significant player in the mainframe market, specializing in providing cutting-edge software solutions designed to optimize mainframe operations and enhance overall efficiency. BMC's mainframe management tools are widely adopted across various industries to streamline processes, boost security measures, and drive cost reductions associated with mainframe operations. The company's focus on automation and task optimization resonates well with organizations looking to maximize the value of their mainframe investments while driving operational excellence.
Another notable player in the mainframe market is CA Technologies, a global leader in enterprise software solutions. CA Technologies offers a robust suite of mainframe software products that cater to diverse customer needs, including operating systems, middleware, and applications designed to run seamlessly on mainframe systems. The company's commitment to delivering innovative solutions that enhance mainframe performance, security, and manageability underpins its strong market presence and customer loyalty.
Moreover, Micro Focus International plc occupies a prominent position in the mainframe market, offering a range of software and services tailored to modernizing mainframe environments and optimizing business operations. With a focus on digital transformation and legacy system integration, Micro Focus enables organizations to leverage the power and scalability of mainframe technology while driving innovation and agility in their IT infrastructure.
Overall, the mainframe market is witnessing a shift towards modernization and optimization, driven by the increasing demand for robust and secure computing solutions that can handle vast amounts of data and transaction processing requirements. Market players are continually innovating to**Global Mainframe Market, By Offering (Hardware, Software, and Services), Application (Census Industry, Consumer Statics, ERP and Transaction), Organization Size (Large Enterprises and Small and Medium-Sized Enterprises), End Use (BFSI, IT and Telecom, Government and public sector, Healthcare, Retail, Travel and Transportation, Manufacturing, Others) - Market Trends and Forecast to 2030**.
- The mainframe market is experiencing significant growth and transformation driven by the demand for robust and secure computing solutions that can handle large volumes of data and transaction processing requirements across various industries. The mainframe market is segmented based on offerings into hardware, software, and services, catering to the diverse needs of enterprise customers seeking high-performance computing solutions. The application segments include census industry, consumer statistics, ERP, and transaction processing, reflecting the versatility of mainframe systems in supporting critical business processes.
- In terms of organization size, the mainframe market caters to both large enterprises and small to medium-sized enterprises looking to leverage mainframe technology for their data processing and analytical needs. The end-use segments encompass industries such as BFSI, IT and telecom, government and public sector, healthcare, retail, travel and transportation, manufacturing, and others, highlighting the broad applicability of mainframe systems across different sectors.
- The mainframe market is characterized by intense competition and innovation, with key players like IBM Corporation, BMC Software, Inc., CA Technologies, and Micro Focus International plc leading the market with their cutting
Core Objective of Mainframe Market:
Every firm in the Mainframe Market has objectives but this market research report focus on the crucial objectives, so you can analysis about competition, future market, new products, and informative data that can raise your sales volume exponentially.
Size of the Mainframe Market and growth rate factors.
Important changes in the future Mainframe Market.
Top worldwide competitors of the Market.
Scope and product outlook of Mainframe Market.
Developing regions with potential growth in the future.
Tough Challenges and risk faced in Market.
Global Mainframe top manufacturers profile and sales statistics.
Key takeaways from the Mainframe Market report:
Detailed considerate of Mainframe Market-particular drivers, Trends, constraints, Restraints, Opportunities and major micro markets.
Comprehensive valuation of all prospects and threat in the
In depth study of industry strategies for growth of the Mainframe Market-leading players.
Mainframe Market latest innovations and major procedures.
Favorable dip inside Vigorous high-tech and market latest trends remarkable the Market.
Conclusive study about the growth conspiracy of Mainframe Market for forthcoming years.
Frequently Asked Questions
What is the Future Market Value for Mainframe Market?
What is the Growth Rate of the Mainframe Market?
What are the Major Companies Operating in the Mainframe Market?
Which Countries Data is covered in the Mainframe Market?
What are the Main Data Pointers Covered in Mainframe Market Report?
Browse Trending Reports:
Smart Agriculture Market Instant Noodles Market Ai In Fashion Market Infantile Hemangioma Market Waste To Diesel Market Contactless Payment Market Necrotizing Enterocolitis Treatment Market Metalized Flexible Packaging Market Customer Analytics Market Plastic Bags Sacks Market Sports Energy Drinks Market Vacuum Packaging Market Pneumococcal Vaccine Market Micro And Nano Plc Market Wireless Medical Device Connectivity Market Herbal Beverages Market Plastic Surgery Devices Market
About Data Bridge Market Research:
Data Bridge set forth itself as an unconventional and neoteric Market research and consulting firm with unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market. Data Bridge endeavors to provide appropriate solutions to the complex business challenges and initiates an effortless decision-making process.
Contact Us:
Data Bridge Market Research
US: +1 614 591 3140
UK: +44 845 154 9652
APAC : +653 1251 975
Email: [email protected]"
0 notes