#MAC Address Filtering
Explore tagged Tumblr posts
Text
How should you secure your home wireless network for teleworking
How should you secure your home wireless network for teleworking #100daysofhomelab #HomeWiFiSecurity #TeleworkingTips #NetworkSecurity #VPNUse #WiFiPasswords #SecureConnections #CyberAttacksPrevention #RemoteWork #DeviceUpdates #MACAddressFiltering
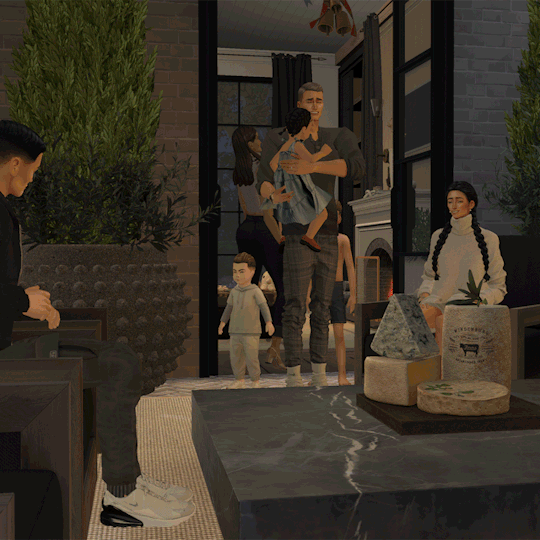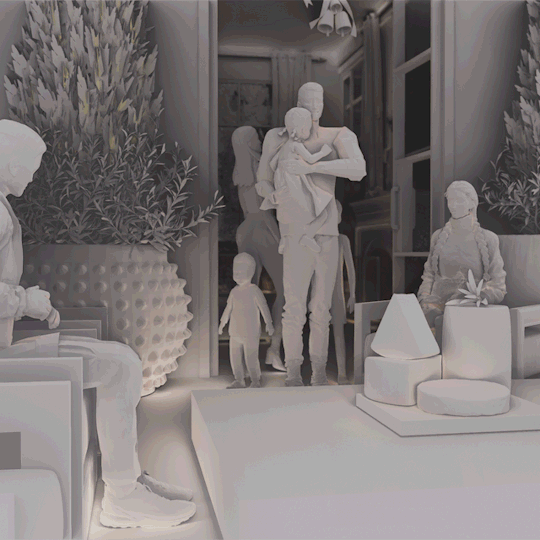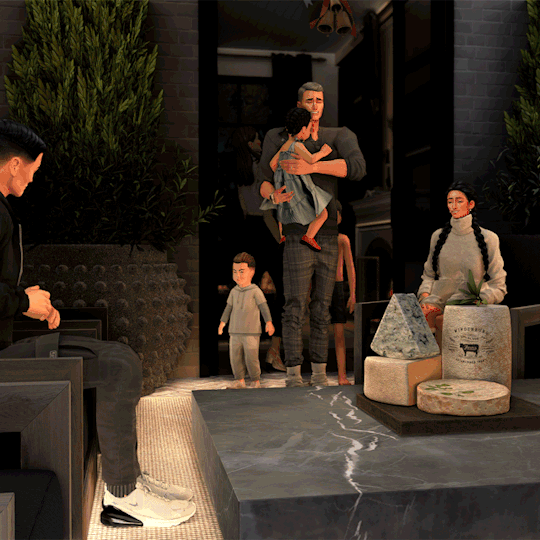
Even though companies are starting to tighten down on who can work remotely and where hybrid work happens, it is still being leveraged like never before. Workers are at least working remotely part of the time, which means that sensitive information and data are subject to the security of the network the workers connect to. It often means the security of their home wireless network. Let’s consider…

View On WordPress
#Cyber Attacks Prevention#Device Updates#Home Wi-Fi Security#MAC Address Filtering#network security#remote work#Secure Connections#Teleworking Tips#VPN Use#Wi-Fi Passwords
0 notes
Text
PXL'S Anatomy of Screenshots

So you want to take better screenshots? There are multiple factors to consider, and if you don't enjoy tweaking reshade settings for every image, my ultimate method may not be for you. That being said, there are tips and resources in this guide that are applicable to everyone and you can select to explore those that are useful to your specific situation.
Disclaimer: I am not claiming to be an expert, nor am I offering to provide troubleshooting on an individual basis. This is a general guide and if you are unfamiliar with any of the concepts, please use the mighty power of the internet to find tutorials. I promise everything that I have learned over the years has been published and documented a thousand times better than I ever could.
There are five factors to address:
Your computer's inherent capabilities
The game's limitations
The mods you're using
Reshade
Post Processing
Graphics Card Settings & Drivers:
Become familiar with your graphic options. If you don't have a dedicated graphics card (i.e. a desktop or gaming laptop, these features may be unavailable and you should skip.)
I have an AMD Radeon Pro card which is designed for workstation level systems. It's overkill for sims, but useful for 3D rendering and modelling work. I have changed the following settings for DirectX 9 applications:
anti-aliasing - enhance application settings
anisotropic filtering - enabled
anisotropic filtering level - 16x
texture filtering quality - high
surface format optimization - high
Consider overclocking your graphics card to unlock it's full potential. DO NOT pursue this venture unless you are ok with the risk of burning out your card prematurely. I use at present, overclocked Bootcamp Drivers from BootcampDrivers.com obviously, if you're not playing on an intel based mac through Bootcamp, this is irrelevant to you.
None of these settings are useful until you address the default games limitations, which leads nicely into the next factor.
Addressing The Sims 4's Graphic Limitations:
Everyone should be familiar at this point with lighting mods, 4k, textures, disabling ssao, etc. but, I'm still going to spell it out. None of this is new information and has been covered many a time by various players ad nauseum.
remove ugly blue toned lighting in the world by choosing a lighting mod from @softerhaze here
overhaul your graphics.cfg file (i use a custom blend with features specific to me), however @simp4sims has done a ridiculous amount of work in providing a simple to install file that can be found here - read through their tutorials!! they have provided an excellent oversight of exactly what this does and why it matters
improve the indoor lighting for your sims - previously i used @luumia's no blu, no glo - recently i switched to @northernsiberiawinds better in game lighting mod here, though i have tweaked some of the settings to suit my own personal preferences
i don't use the HQ mod, i don't find that it makes enough difference for the amount of effort it requires to convert CAS CC
It should go without saying, but tweaking your graphics config file is absolutely useless if you can't play TS4 at it's maximum in game graphic settings!
The Mods You're Using:
Now that you've put in all this work into getting the game ready to make use of quality mods where do you start? Well, the CC you install matters. Whatever your preference, whether it be maxis-match, alpha or somewhere in between, priority should be given to using items textured in 2k or 4k resolutions, and specific attention should be paid to using wall and flooring textures with bump maps, and or high quality resolutions (this is important later for reshade if you intend to learn about ray tracing).
I will separately post a guide to creators with crispy textures because that is it's own novel.
Reshade:
Phew. Still with me?
There are many many many reshade presets out there, most are alike, but none employ ray tracing, and that is because a) it needs to be manually adjusted for every screenshot, b) they are paid shaders, and c) this requires advanced knowledge of reshade and a decent enough graphics set up that won't overheat - games running native ray tracing recommend a minimum VRAM of 8GB (please note RAM and VRAM are not the same) - i therefore do not recommend pursuing this option if your system does not meet those minimum requirements.
Start here to understand what ray tracing for reshade is. In my opinion, the shaders are well worth the price of $5 for the amount of work that has gone into creating them by the talented Pascal Gilcher. That link is a comprehensive starting point into expanding your knowledge of reshade and it's capabilities.
I have always created my own reshade presets from scratch, and while the core colorization settings I utilize remain largely the same, using ray tracing and re-light means every screenshot needs to be manually adjusted (lights repositioned, bounce and AO factors adjusted, etc) before being captured. @pictureamoebae just published a very timely post discussing the re-light shader and you can read it here.
Post Processing
Reshade does 99.99% of the work that traditionally would be accomplished in a photo editing software like photoshop. Occasionally, I need to adjust exposure manually, add depth of field manually, or color correct. Beyond that I use it to scale images to fit the resolution and file size limits of various platforms. Conceptually this reduces the amount of uncontrolled loss encountered when platforms like tumblr auto compress files that are too large. In reality, tumblr still makes images crappy compared to how they appear in my file folder.
optimize your images for various social media platforms using this guide
fix exposure or colorization issues using a software like photoshop
I hope that this gives you a starting point into expanding your methodologies. My process is continuously evolving and I find this aspect of the game most entertaining. For others who don't enjoy this process, it's probably not worth it!
Thanks for reading ❤ PXL
412 notes
·
View notes
Text
Studio Star (Windows) & Aurora (Mac) update
Both versions include:
Build category filter in the Objects section containing doors, windows, and other items
Object dirt overlays on the Studio tab,
Support for pool, fountain, roof, exterior, half wall, and deco trims
Batch fix "Disallow CC shoes for barefoot" that replaces the disallow for towel and stops Sims from wearing custom shoes when stomping grapes or other actions that should be performed barefoot
A submenu in the batch fix section including all allow and disallow batch fixes
Batch fix to disallow for werewolves
Batch fix to disallow for all occult entities at once
Updated disallow for random to prevent aging up sims using items that were disallowed for random
A new "Browse Game Content" selection in the Tools menu that replaces the Windows Object and CAS preview cheats and introduces this functionality to Mac. The content browser also includes Build items.
Aurora (Mac) also has a new corner tab in the Wall editor
Star (Windows) also has numerous UI updates and improvements
Both versions also include many bug fixes addressing reported issues.
Important note about batch fixes: The new versions contain new and updated batch fixes. These have been tested, but it isn't possible to test them on every CC item that's been created. Please remember to check your batch fixed items in the game and only delete the batch fix backup file once you're confident the batch fix worked as intended. If you identify problems with batch fixed items, you can restore the original items using the backup. If you notice problems with a batch fix please let us know so the issue can be addressed.
As always, thank you to everyone who has made suggestions for new features and/or reported bugs. Your contributions are vital to Studio's ongoing improvement!
Choose your version to download HERE. Changelogs for Star and Aurora are in their respective download threads.
533 notes
·
View notes
Text
Burning Desire
A/N: I hope you guys like it. Im sad about the election, but I wanted to get this out. Let me know what you think, might do Rolan next or maybe even Karlach. Sorry if the spacing looks weird, tumblr will no longer pull up on my mac so, weird but I had to post it from my phone.
He wakes as he often does after her, rolling over inhaling her scent on the pillow. Pomegranate and vanilla; her smell. He knew it, he had committed it to memory, like a birthday. But today is different; the smell is heady, more fragrant, like over ripened fruit. And it makes his cock hard in his trousers. He was in Heat.
Teiflings on the older side didn't go into heat every month, “pass their prime” perhaps. But this one was strong, he needed her. Like he needed air, but he had duties and so did she, so he would have to wait. Sate his hunger the best he could until he could take her properly.
“Good morning,” she greets him when she hears the clank of his boots coming downstairs. Zevlor drank the sight of her in. Had she always been this beautiful, her skin looked dewy, and her hair shiny. She is the picture of perfection standing in the early morning light filtering in through the kitchen window. And he feels that need thrum low in his belly again.
“It is a good morning indeed.” He rasps into her ear, nipping at the soft skin there, his hands digging into her hips spreading her thighs slightly as he drops to his knees. His clawed fingers gather her nightgown at the hem pooling it around her waist.
“What are you doing?” She murmurs as he presses his nose flat against her clothed cunt breathing in deeply. The smell, Oh Gods, that smell. It burrows into his brain like a mind flayers tadpole and eats away at all the rational parts of his brain and leaves the more salacious bits. The image of her pressed against their shared bed as absolutely splits her open crosses his mind. As he takes in another deep breath letting his breath fan out over the fabric, he can now smell the all too familiar smell of arousal pooling between her legs.
“I have half the mind to bend you over this counter right now and fill you absolutely full with my seed.” He murmurs as he drags his nose away from her center, looking up at her to see her cheeks dusted with a rosy tint. “But you and I both have duties to the city.” He stands back to full height, cock painfully straining against the chainmail of his trousers. He rubs against forehead, the bump of his horns rubbing against the smooth skin of her forehead, an almost keening whine leaving his lips when she finally closes the distance between them. It would be an exceptionally long day.
This was torture, like slowly burning alive in her own skin. Except it’s just her in his line of vision constantly. Had her armor always hugged her body like that, the leathers lifted her ass to make a nice heart shape and he found it awfully hard to ignore it when she was bent over the table beside Wyll looking at a map. Was she doing this on purpose, he thought as he dug his claws into thigh?
“Commander, opinions?” She was talking to him, those lips that looked so nice around his cock were talking to him. And calling him by his title instead of by his name or addressing her as husband. His cock twitched under his desk.
“Zevlor, are you alright? You look ill.” Wyll asked, concerned as the older man tried to keep it together. Zevlor nodded curtly, apologizing to the Duke as he tried to refocus. He needed her, this couldn't wait. He wouldn't make it through the day if he didn’t have her.
“Have I ever told you how pretty you are?” He growls biting at the skin of her shoulder as he bends her over his desk. Yanking her armor down and then the leathers, just enough to see that pretty weeping cunt. He drags the sensitive tip between her puffy folds as she whines. “With the way you're whining, you’d think you're a bitch in heat, my beloved.” He huffs, finally pressing into her velvety walls. When he’s buried to the hilt in her, he sets a brutal pace. His mind is consumed with her, the way she feels around his cock, her moans and gasps. The sounds of their coupling loud and lewd in his quiet office.
“Zevlor.” She cries out as he lifts one of her legs placing it on the desk. This angle is deeper and it has her biting her hand in an effort to be quiet. His mind is feral with the thought of filling her full, breeding her. His mind thinks of her cunt dripping and leaking over her undergarments as she goes about the rest of the day. The thought drives him into her one last time and as he feels her clenching around him, he finishes painting her inner walls with hot seed.
“Better,” She asks as he helps her down from the table, smoothing her hair and righting her armor. He chuckles pressing a kiss to her fevered forehead,
“Much my beloved.” Until tonight of course, he thinks as he watches her leave from his office.
#zevlor x reader#zevlor x tav#bg3 brainrot#bg3 x tav#bg3 x reader#feral#in heat#bg3 npcs#zevlor smut
84 notes
·
View notes
Text
The Sims 4: New Game Patch (December 3rd, 2024)
A new game update is out for The Sims 4, preparing the game for the new Cozy Celebrations event, that is scheduled to start today.
If you have auto updates enabled in Origin’s “Application Settings”, the game will auto-update once you open Origin. If you have auto-updates disabled, you will need to manually update by clicking the game in your library.Advertisement
To ensure your game is up to date, check the game version found in Documents > EA > The Sims 4 > GameVersion.txt. Your game should now read: PC: 1.111.102.1030 / Mac: 1.111.102.1230 / Console: Version: 2.04
Holiday Greetings Simmers,
It’s that time of year once again when we prepare to celebrate the holiday season, and we are coming with an update to spread some holiday spirit in The Sims 4. Along with the festive Sims Delivery Express drop which comes in today’s update with no additional download required, we will be kicking off a brand-new, very festive themed Event shortly after the update is available.
Happy Holidays to all Simmers around the world!
The Sims Team
What’s New?
This season, the Sims Delivery Express brings you two new items along with culturally inspired Create a Sim assets and recipes. Your Sims can enjoy the charming Cozy Hot Cocoa Tray, offering six delightful hot drinks, and the Comfy Blankets Quilt Stand, which adds a cozy touch to any room. Dress your Sims in Romanian-inspired clothing for the whole family, plus a new hair scarf and a full-body outerwear coat.
Enjoy creating two new dishes with your Sims! Mămăligă is a beloved traditional dish enjoyed in many Eastern European countries, while Mucenici is a festive treat that brings families together to honor the past and welcome spring.

Starting today, not only will you have access to some new festive Sims Delivery Express content but we are starting the Cozy Celebrations Event with three weeks of all new rewards and some global tradition based quests to take part in. One of the quests will even have you make use of the Cozy Hot Cocoa Tray from the Sims Delivery Express to help complete your Event track so be sure to grab one of those from Build Mode. For more information and help for The Sims 4 Events, be sure to check out our help page.

Bug Fixes
Base Game
Simmers running DirectX 11 should no longer see the sky causing the game to shut down unexpectedly.
Addressed a crash that was identified when certain mods were active.
Switching between Pack filters on the Store screen is more performant for Simmers on PlayStation 4 and Xbox One.
Live Events are no longer referenced as Discovery Quests, although you might still discover new things while unlocking rewards in the Live Events.
Stairs from Snowy Escape, Jungle Adventure, and Journey to Batuu will now have supporting walls beneath them.
Small stud and hoop earrings from Base Game can now be found in more categories.
A number of adult and child tops from Base Game have been added to the Cold Weather category.
Life & Death
[AHQ] In new saves, Nyon Specter has the proper Grimborn trait.
[AHQ] Mermaid hair will no longer get cut off in Create a Sim.
Dine Out
[AHQ] When going out on a date, it is important for everything to go just right. Sims will now actually go through with requesting a table instead of backing down and canceling the interaction.
18 notes
·
View notes
Text
i had a dream i was new agent 3 and i was breaking into c-side's like 20th floor hotel balcony to steal their cake, then they caught me but didn't realize what i was doing and thought i was just chilling there (or they did realize im not sure. up to interpretation). they noticed i was carrying a trumpet and i kind of just stumbled into becoming the fourth member of c-side.
kikura, beika and uotora were really chill they're fun to listen to. i was shy and tried to speak up but couldn't. i was scared they were gonna realize i have never played the trumpet in my life and it was gonna end horribly but kikura addressed my fears by saying it was gonna be alright and they lip-sync sometimes (big secret).
then a flashback happened i think someone crashed her motorcycle was arrested for speeding and then 2/3 members of cside (idk which) came along and stealthily repaired the motorcycle while the cops weren't looking and drove off with it idk
after that i was at the splatlandian coast it had a yellow filter like the breaking bad mexico scenes. i think this was beika and ichiya's home town. i was chilling in beika's childhood house while she was out doing something and i played this weird creepypasta game on the loud ass TV while her little brother and sister were playing on a mac next to it. I asked if maybe they wanted to play on the tv but then kikura told me to chill its fine. then the creepypasta game turned into reality and i explored these bloody catacombs right underneath the house and found monsters the dream matrix was collapsing at this point so lets disregard this part.
i really liked hanging out with cside it was cool. this might be my self-insert awakening
3 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] From the brand MAONO, founded in 2014 with a group of technicians. The company is established with the mission “Vision drives technology”, composed of experienced technicians of electronics, experts in mobile accessories, audio products, etc. All our products are designed for a smarter life, every detail is put into consideration just for understanding the customers’ real needs better. AU-PM421 Condenser Microphone AU-AM200-S1 Audio interface AU-MH601S Over Ear Headphone Unique Top-Address Design: Ergonomically designed and more suitable for podcasting and game streaming. Made for smaller setups, this compact condenser mic barely takes up any desk space. Excellent sound: Built-in professional chipset and sampling rate is up to 192KHz/24bit, which can provide clear sound without distortion and is ideal for gaming, podcasting, zoom meetings, streaming. Gain Knob and Zero Latency Monitoring: USB mic with gain knob, accurate sound recording and easier adjustment. You can adjust the mic gain at any time during the recording to get a better effect. Premium Accessories: Metal pop filter helps produce pristine sound quality by filtering pops, hisses, and thuds. Shield structure with metal mesh layer provides better protection for your microphone. Easy to Use, All-in-One: All-in-one package, compact and lightweight. Comes with a premium pop filter and tripod. Just plug USB cable into your device and use it. Compatible with Windows and Mac OS. [ad_2]
0 notes
Text
Exploring the Key Components of Cisco ACI Architecture

Cisco ACI (Application Centric Infrastructure) is a transformative network architecture designed to streamline data center management by enabling centralized automation and policy-driven management. In this blog, we will explore the key components of Cisco ACI architecture, highlighting how it facilitates seamless connectivity, scalability, and flexibility within modern data centers.
Whether you are a network professional or a beginner, Cisco ACI training offers invaluable insights into mastering the complexities of ACI. Understanding its core components is essential for optimizing performance and ensuring a secure, efficient network environment. Let's dive into the foundational elements that make up this powerful solution.
Introduction to Cisco ACI Architecture
Cisco ACI is a software-defined networking (SDN) solution designed for modern data centers. It provides a centralized framework to manage networks through a policy-based approach, enabling administrators to automate workflows and enforce application-centric policies efficiently. The architecture is built on a fabric model, incorporating a spine-leaf topology for optimized communication.
Core Components of Cisco ACI
Application Policy Infrastructure Controller (APIC):
The brain of the Cisco ACI architecture.
Manages and monitors the fabric while enforcing policies.
Provides a centralized RESTful API for automation and integration.
Leaf and Spine Switches:
Spine Switches: Handle high-speed inter-leaf communication.
Leaf Switches: Connect endpoints such as servers, storage devices, and other network resources.
Together, they create a low-latency, highly scalable topology.
Endpoint Groups (EPGs):
Logical groupings of endpoints that share similar application or policy requirements.
Simplify the application of policies across connected devices.
Cisco ACI Fabric
The ACI fabric forms the backbone of the architecture, ensuring seamless communication between components. It is based on a spine-leaf topology, where each leaf connects to every spine.
Features:
Uses VXLAN (Virtual Extensible LAN) for overlay networking.
Ensures scalability with distributed intelligence and endpoint learning.
Provides high availability and fault tolerance.
Benefits:
Eliminates bottlenecks with uniform traffic distribution.
Simplifies network operations through centralized management.
Policy Model in Cisco ACI
The policy-driven approach is central to Cisco ACI’s architecture. It enables administrators to define how applications and endpoints interact, reducing complexity and errors.
Key Elements:
Tenants: Logical units for resource isolation.
EPGs: Define groups of endpoints with shared policies.
Contracts and Filters: Govern communication between EPGs.
Advantages:
Provides consistency across the network.
Enhances security by enforcing predefined policies.
Tenants in Cisco ACI
Tenants are fundamental to Cisco ACI’s multi-tenancy model. They provide logical segmentation of resources within the network.
Types of Tenants:
Management Tenant: Manages the ACI fabric and infrastructure.
Common Tenant: Shares resources across multiple users or applications.
Custom Tenants: Created for specific business units or use cases.
Benefits:
Enables secure isolation of resources.
Simplifies management in multi-tenant environments.
Contracts and Filters
Contracts and filters define how endpoints within different EPGs interact.
Contracts:
Specify traffic rules between EPGs.
Include criteria such as protocols, ports, and permissions.
Filters:
Provide granular control over traffic flow.
Allow administrators to define specific policies for allowed or denied communication.
Endpoint Discovery and Learning
Cisco ACI simplifies network operations with dynamic endpoint discovery.
How It Works:
Leaf switches identify endpoints by tracking MAC and IP addresses.
Updates to the fabric are automatic, reflecting real-time changes.
Benefits:
Reduces manual intervention.
Ensures efficient resource utilization and adaptability.
Role of VXLAN in Cisco ACI
VXLAN is a critical technology in Cisco ACI, enabling overlay networking for scalable data centers.
Features:
Encapsulates Layer 2 traffic over a Layer 3 network.
Supports up to 16 million VLANs for extensive segmentation.
Benefits:
Enhances network flexibility and scalability.
Simplifies workload mobility without reconfiguring the physical network.
Integrations with External Networks
Cisco ACI integrates seamlessly with legacy and external networks, ensuring smooth interoperability.
Connectivity Options:
Layer 2 Out (L2Out): Provides direct Layer 2 connectivity to external devices.
Layer 3 Out (L3Out): Establishes Layer 3 routing to external systems.
Advantages:
Facilitates gradual migration to ACI.
Bridges new and existing network infrastructures.
Advantages of Cisco ACI Architecture
Scalability: Supports rapid growth with a spine-leaf topology.
Automation: Reduces complexity with policy-driven management.
Security: Enhances protection through segmentation and controlled interactions.
Flexibility: Adapts to hybrid and multi-cloud environments.
Efficiency: Simplifies network operations, reducing administrative overhead.
Conclusion
In conclusion, understanding the key components of Cisco ACI architecture is essential for designing and managing modern data center networks. By integrating software and hardware, ACI offers a scalable, secure, and automated network environment.
With its centralized policy model and simplified management, Cisco ACI transforms network operations. For those looking to gain in-depth knowledge and practical skills in Cisco ACI, enrolling in a Cisco ACI course can be a valuable step toward mastering this powerful technology and staying ahead in the ever-evolving world of networking.
0 notes
Photo

TP-Link Archer AX20 AX1800 Dual Band Wifi 6 Router FEATURES: Dual-Band Wi-Fi 6: Equipped with the latest wireless technology, Wi-Fi 6, for faster speeds, greater capacity, and reduced network congestion Next-Gen 1.8Gbps Speeds: Enjoy smooth streaming, downloading, and gaming all without buffering with Wi-Fi speeds of 1.8Gbps Connect More Devices: Wi-Fi 6 technology communicates more data to more devices using revolutionary OFDMA technology while simultaneously reducing lag Quad-Core Processing: The 1.5GHz quad-core CPU ensures communications between your router and all connected devices are smooth Extensive Coverage: Beamforming, independent FEM, and four antennas combine to deliver focused reception to devices far away Increased Battery Life: Target Wake Time technology reduces your devices’ power consumption to extend their battery life USB Easy Sharing: A USB 2.0 Port enables easy file sharing within your network or building private Cloud Storage Easy Setup: Set up your router in minutes with the powerful TP-Link Tether App Backward Compatible: Supports all previous 802.11 standards and all Wi-Fi devices WIRELESS Standards Wi-Fi 6 IEEE 802.11ax/ac/n/a 5 GHz IEEE 802.11ax/n/b/g 2.4 GHz WiFi Speeds AX1800 5 GHz: 1201 Mbps (802.11ax) 2.4 GHz: 574 Mbps (802.11ax) WiFi Range 3 Bedroom Houses 4× Fixed High-Performance Antennas Multiple antennas form a signal-boosting array to cover more directions and large areas Beamforming Concentrates wireless signal strength towards clients to expand WiFi range High-Power FEM Improves transmission power to strengthen signal coverage WiFi Capacity High Dual-Band Allocate devices to different bands for optimal performance OFDMA Simultaneously communicates with multiple Wi-Fi 6 clients Airtime Fairness Improves network efficiency by limiting excessive occupation 4 Streams Connect your devices to more bandwidth Working Modes Router Mode Access Point Mode HARDWARE Processor 1.5 GHz Quad-Core CPU Ethernet Ports 1× Gigabit WAN Port 4× Gigabit LAN Ports USB Support 1× USB 2.0 Port Supported Partition Formats: NTFS, exFAT, HFS+, FAT32 Supported Functions: Apple Time Machine FTP Server Media Server Samba Server Buttons WPS/Wi-Fi Button Power On/Off Button LED On/Off Button Reset Button Power 12 V ⎓ 1.5 A SECURITY WiFi Encryption WPA WPA2 WPA3 WPA/WPA2-Enterprise (802.1x) Network Security SPI Firewall Access Control IP & MAC Binding Application Layer Gateway Guest Network 1× 5 GHz Guest Network 1× 2.4 GHz Guest Network VPN Server OpenVPN PPTP SOFTWARE Protocols IPv4 IPv6 Parental Controls URL Filtering Time Controls WAN Types Dynamic IP Static IP PPPoE PPTP L2TP Quality of Service QoS by Device Cloud Service Auto Firmware Upgrade OTA Firmware Upgrade TP-Link ID DDNS NAT Forwarding Port Forwarding Port Triggering DMZ UPnP IPTV IGMP Proxy IGMP Snooping Bridge Tag VLAN DHCP Address Reservation DHCP Client List Server DDNS TP-Link NO-IP DynDNS Management Tether App Webpage PHYSICAL Dimensions (W×D×H) 10.2 × 5.3 ×1.5 in (260.2 × 135.0 × 38.6 mm) Package Contents Wi-Fi Router Archer AX20 Power Adapter RJ45 Ethernet Cable Quick Installation Guide OTHER System Requirements Internet Explorer 11+, Firefox 12.0+, Chrome 20.0+, Safari 4.0+, or other JavaScript-enabled browser Cable or DSL Modem (if needed) Subscription with an internet service provider (for internet access) Certifications FCC, CE, RoHS Environment Operating Temperature: 0℃~40℃ (32℉ ~104℉) Storage Temperature: -40℃~70℃ (-40℉ ~158℉) Operating Humidity: 10%~90% non-condensing Storage Humidity: 5%~90% non-condensing TEST DATA WiFi Transmission Power CE:
0 notes
Text
A Comprehensive Guide to Natural Kidney Health and Herbal Remedies
Kidneys are essential organs that filter waste and excess fluids from the blood, regulate blood pressure, balance minerals, and produce hormones necessary for red blood cell production and bone health. As vital as they are, kidneys can face challenges due to stress, disease, or age-related decline. Fortunately, natural herbs and supplements can help maintain kidney health and support its functions. This article delves into the best natural kidney health herbs, their benefits, and how they contribute to overall wellness.

Understanding Kidney Function
Healthy kidneys process about 50 quarts of blood every day, removing waste and excess water to create urine. This urine travels through two ureters to the bladder for elimination. Besides filtering blood, kidneys also:
Regulate the balance of minerals like potassium, calcium, and sodium.
Manage blood pressure through hormone release.
Produce erythropoietin, which aids in red blood cell production.
Convert Vitamin D into its active form for bone health.
Given these vital roles, maintaining kidney health is crucial. Proper hydration, a balanced diet, and a healthy lifestyle form the foundation of kidney care. However, herbal remedies can offer additional support, especially as we age or face chronic conditions.
Best Natural Herbs for Kidney Health
Several herbs stand out for their ability to enhance kidney function, prevent complications, and improve overall health. Here are the top options:
1. Vitamin D
Vitamin D is essential for bone health and reducing inflammation. People with kidney disease often struggle to convert Vitamin D into its active form, leading to deficiencies. Supplementing with Vitamin D can help mitigate cardiovascular risks and support bone health.
Recommended Dosage: 800–2,000 IU daily, based on individual needs.
2. Codiya Nephroshield Mac
Designed for people with diabetes and elevated creatinine levels, Codiya Nephroshield Mac protects the kidneys, supports liver function, and prevents renal failure. Its herbal blend promotes natural cleansing and reduces toxic accumulation.
Recommended Dosage: One tablet twice daily with water.
3. Iron
Iron supplements address anemia, a common issue in chronic kidney disease (CKD). Iron helps in the production of hemoglobin, enabling oxygen transport throughout the body.
Recommended Dosage: 100–200 mg daily for those with deficiency (consult a physician).
4. Uveda Nephro Panchamrit
This traditional herbal formula focuses on kidney cleansing and inflammation reduction. Its enhanced version, Nephro Panchamrit Plus, offers additional detoxification benefits, supporting kidney stone prevention and urinary tract health.
Recommended Dosage: 10 cc from each bottle, three times daily.
5. Uveda Naturals 5-in-1 Combo
This Ayurvedic blend supports detoxification, kidney function, blood pressure control, and overall health. It’s ideal for individuals seeking a comprehensive approach to renal care.
6. Vitamin B12
Vitamin B12 helps maintain healthy red blood cells and regulates phosphorus levels, essential for kidney function. While it doesn’t replace medical treatments like dialysis, it aids in restoring balance in the body.
Herbs for Kidney and Bladder Health
Certain herbs and plants can enhance kidney and bladder health, offering protection against infections and promoting detoxification. Key herbs include:
1. Cranberry
Cranberries prevent urinary tract infections (UTIs) by inhibiting bacterial growth in the bladder.
2. Parsley
Known for its mild diuretic properties, parsley helps flush out toxins and reduce inflammation.
3. Marshmallow Root
This herb soothes urinary tract inflammation and relieves bladder irritation.
4. Goldenrod
With its diuretic properties, goldenrod reduces swelling and inflammation.
5. Uva Ursi
This herb has antiseptic and astringent properties, making it effective against UTIs and inflammation.
6. Dandelion Root
A natural diuretic, dandelion root promotes kidney function and helps manage water retention.
7. Juniper Berries
Juniper berries aid in flushing out toxins and supporting kidney health.
Best Drinks for Kidney Health
Hydration is key to maintaining kidney function. Certain beverages can enhance detoxification and protect against kidney-related issues:
Cranberry Juice: Prevents UTIs.
Carrot Juice and Beet Juice: Rich in antioxidants, these juices promote detoxification.
Herbal Teas: Such as dandelion or nettle tea, which support kidney function.
Dissolving Kidney Stones Naturally
Kidney stones are painful but can often be managed naturally. Lemon juice and apple cider vinegar are believed to help dissolve kidney stones, making them easier to pass. Staying hydrated is critical to preventing stone formation and aiding their removal.
Herbs to Avoid for Kidney Health
While many herbs support kidney health, some can be harmful, particularly for individuals with CKD. Avoid excessive consumption of:
Fat-Soluble Vitamins (A, E, K): These can accumulate and cause toxicity.
Potassium-Rich Herbs: Such as certain pre-workout supplements, which may pose risks for those with kidney failure.
Always consult a healthcare provider before starting any new herbal or vitamin regimen, especially if you have an existing kidney condition.
Why Choose Uveda Naturals?
Uveda Naturals specializes in Ayurvedic remedies tailored to kidney health. Their products, like Nephro Panchamrit and 5-in-1 Combo, are designed to enhance kidney function, dissolve stones, and promote overall wellness. With a focus on natural cleansing and detoxification, Uveda Naturals provides a comprehensive solution for those seeking herbal support for their kidneys.
Conclusion
Kidneys are vital to overall health, and incorporating natural herbs into your routine can provide significant benefits. From Vitamin D and Iron to herbal blends like Uveda Nephro Panchamrit, these remedies can support kidney function, prevent complications, and promote detoxification. Always consult a healthcare provider to determine the best approach for your individual needs. For a range of effective, natural products, consider Uveda Naturals as a trusted source for kidney health.
FAQs on Natural Kidney Health Herbs
1. Which are the best natural kidney herbs? Codiya Nephroshield Mac, Uveda Nephro Panchamrit, Vitamin D, Iron, and Vitamin B12 are among the top choices.
2. What is the best drink for kidney health? Cranberry juice, carrot juice, beet juice, and herbal teas are excellent options.
3. What dissolves kidney stones quickly? Lemon juice and apple cider vinegar can help dissolve kidney stones, while proper hydration aids in passing them.
4. Can garlic reduce creatinine levels? Yes, garlic helps protect kidneys from free radical damage and may aid in lowering elevated creatinine levels.
5. Why choose Uveda Naturals for kidney health? Uveda Naturals offers Ayurvedic remedies tailored to kidney health, including products for kidney function support, stone prevention, and detoxification.
#kidneywellness#kidneysupport#healthyliving#nephrology#nephroshild#Codiya Nephroshield Mac#Nephro Panchamrit Plus
0 notes
Text
Published Paper of Advances in Vision Computing: An International Journal (AVC) Paper Title: A Method for Detecting False Positive and False Negative Attacks Using Simulation Models in Statistical Enroute Filtering Based WSNs
Authors: Su Man Nam and Tae Ho Cho Sungkyunkwan University, Republic of Korea
Abstract: In wireless sensor networks, adversaries compromise sensor nodes to damage the network though potential threats such as false positive and false negative attacks. The false positive attacks cause energy drain and false alarms, and false negative attacks generate information loss. To address the false positive attacks in the sensor network, a statistical en route filtering (SEF) detects the false report in intermediate nodes. Even though the scheme detects the false report against the false positive attack, it is difficult to detect false MACs in a legitimate report against the false negative attack in the SEF-based WSN. Our proposed method effectively detects the false positive and false negative attacks in the sensor network through a simulation model. The experimental results indicate that the proposed method increase detection power while maintaining the energy consumption of the network against the false positive and false negative attack
Keywords: Wireless Sensor Networks, Network Security, Simulation models, Statistical En-route Filtering Network Protocols
Volume URL: https://airccse.org/journal/avc/vol3.html
Pdf URL: https://aircconline.com/avc/V3N3/3316avc02.pdf
0 notes
Text
The Sims 4: New Game Patch (May 28th, 2024)
There is a new game update for The Sims 4, to prepare the game to the upcoming kits. Read it all on the blog post below.
If you have auto updates enabled in Origin’s “Application Settings”, the game will auto-update once you open Origin. If you have auto-updates disabled, you will need to manually update by clicking the game in your library.Advertisement
To ensure your game is up to date, check the game version found in Documents > EA > The Sims 4 > GameVersion.txt. Your game should now read: PC: PC: 1.107.112.1030 / Mac: 1.107.112.1230 / Console: 1.92
Sul Sul Simmers! It’s time for some late Spring cleaning! Let’s fix some things and make a few improvements. We’ve got quite the spread, with a host of resolutions for base game issues as well as addressing a wide assortment of packs. There’re also some performance gains, gallery updates, and DirectX 11 previews. We squeezed lots into this release, but there’s still more to come! Talk to you soon!
-The Sims 4 Team
Bug Fixes & Updates
Base Game
Oh you thought you could hide, dishes? We will find you and we will wash you. Dishes left in corners will no longer be ignored when cleaning up.
Begone weeds! Plants won’t grow weeds when Out of Season. If a plant has them when it becomes Out of Season, the weeds will be removed until it’s In Season again.
Campfires will stop causing so many fires on the lot. Campfire spreadfire was triggering a 50% chance every 10 sim-minutes to burn objects other than chairs in the area. We removed that to only focus on when Fireworks trigger (which we all know is the real danger).
“A Trash Can Is Required“ message will no longer display when trash cans are present on the active lot. Get that garbage outta here.
Skills will not randomly increase or change when leaving the lot or editing the household. If your Sim knows, they know.
The skills list is arranged in alphabetical order and my eye will no longer twitch when looking at it.
TS4 Packs are listed in the right order in the Build/Buy filter. Get back in line For Rent, Home Chef Hustle and Crystal Creations!
Careers will no longer have a blank daily task menu.
Summon Grilled Cheese interaction will no longer drop from the interaction queue.
Sim will no longer get stuck in the ground and continue to Swim Laps if the pool is removed in the middle of it. Because physics. Now the Sim will reset. Because magic.
Calendar notification light will remain on after traveling. No forgetting those important events.
Customizable pronouns were adjusted to appear correctly on a few of the Romantic Relationship phone calls and will no longer display improper usage like “ask their out.”
Sims can properly merge or move households with NPC Sims “not in world“; the merge/move button is now accessible. It’s all about bringing families together!
Console
After switching to build mode from world map a red bar will no longer display in the upper right corner.
Performance
We’ve made some optimizations so the game uses less memory. You may experience fewer crashes, better frame rate, and/or more responsive simulation.
We’ve improved the lot load process so it should happen a bit faster.
Cats & Dogs / City Living
Small dogs, puppies, and kittens will properly use the elevator to go downstairs from Penthouses. They can finally go potty! Poor little things.
Cottage Living
Hatchable and spoiled eggs will now remain visible in the Chicken coop whenever the Sim travels to the lot.
Dine Out
‘Order For Table’ interaction will properly clear from the interaction queue after the waiter delivers food to the table.
Home Chef Hustles players can now add Waffles to the Restaurant Menu. More menu additions to come.
DirectX 11 Preview
DirectX 11 is available on The Sims 4 on an opt-in basis and will be rolled out fully in a later update for Simmers running Windows. If you opt to run The Sims 4 using DirectX 11, you will potentially experience enhanced game performance and graphics quality. This update is designed to increase the overall gaming experience, with improved rendering capabilities that will allow for more details and immersive environments in future releases! We would appreciate your feedback and any issues you experience on our DirectX 11 Answers HQ thread.
Simmers running Windows and have DirectX 11 compatible hardware can now enter the argument -dx11 into the EA App or Steam to switch to using this renderer. You will be able to see which DirectX version The Sims 4 is using in your game version information displayed in the bottom right corner of the Main Menu.
You can find all the information you need to check if your PC is DirectX 11 compatible and learn how to enter launch arguments for both EA App and Steam here.
While DirectX 11 is available for those Simmers who want to try it, you may experience visual issues with mods so we recommend disabling all mods while using this command line argument.
Eco Lifestyle
Nose rings will no longer break when paired with brow piercings from this pack.
For Rent
Property Ownership of “Tam Nang Sands“ lot will be recognized in the owned rental tab.
“Unpleasant Surroundings“ Moodlet no longer triggered from the Pressure cooker and Kettle.
Tourist location icons will now appear correctly when hovering over the Tomarang world select screen.
Gallery Server
All profanity filter false positive reports sent to us via The Sims 4 Gallery Profanity Filter Feedback survey up to May 1st have been reviewed and changes implemented. We appreciate all the reports and responses and will continue to update our systems based on your feedback.
Non-anonymous Gallery users appearing in the Following and Followers tabs will once again display the number of Followers each user has.
Get to Work
Aliens will stop having noticeable changes in facial structure (placement, size, etc) when aging up. No more morph faces.
Growing Together
The “Had a Baby“ Milestone now triggers from having a Science Baby or giving birth at the hospital rabbithole.
High School Years
Teens cannot send flirty messages on Social Bunny to adults or household family members.
After a teen high school Sim completes all tasks and aces exams, they will also be promoted to a better grade. They’ve earned it!
Horse Ranch
We all know how cute they are, but Sims will no longer autonomously want to buy mini goats (causing the UI to pop up).
Nectar value is now properly increased when selling to the mysterious rancher.
Horses will no longer get stuck while sleeping too close to the Horse training ball.
Island Living
Mermaid Conservationists can now complete the “Snorkel in Mua Pel’am“ job task.
Seasons
During winter, the weeding animation will no longer repeat and the Sim will actually remove all the weeds surrounding the plants. Checkmate weeds!
20 notes
·
View notes
Text
How did Fifine A6T Mics got viral?
Fifine A6T mics… Trust me they are not the cheapest, not the best quality, probably. And while I have encountered the brand before, Fifine might not be as famous as other brands, but guess what? It was a superstar on Amazon! People were buying it like crazy back in January, and even now, months later, it’s still on top. But why? That’s what I’m going to figure out! We’ll dig into why Fifine is such a hit. Maybe there’s something special about it that others haven’t noticed yet.
The Case for Fifine A6T Mics
I guess the first question is why not the Fifine A6T? It’s $47 at the time I’m writing, has overwhelmingly positive reviews, works on PC, Mac, and PlayStation, and it includes absolutely everything you need to get started. The mic itself, a boom arm, a desk clamp, a shock mount, and even a cute little pop filter with a smiley face on it, as it works with PC, Mac, and PlayStation! With all these features and glowing reviews, you’d think it would be flying off the shelves. But why isn’t it getting as much attention as it deserves? It’s a mystery, but one worth solving. Maybe Fifine has some secrets that lets them offer such a great deal.
Review of Fifine A6T Mics
According to me, The voice quality is excellent and so is the silicone isolating bands. The quality all around for the price is hard to beat. The arm itself cheap, but for the price it’s reasonable. I think It’s not much better/different than the <20 dollar options for just the arms themselves from other brands which look identical. So for this price range, it’s fine. If you were doing this professionally, the arm would be the first to upgrade.
Build Quality
The mic feels quite a bit cheaper than it looks in the pictures, actually. It’s shockingly light. While it may not meet expectations in terms of weight and build quality, its functionality is praiseworthy.
Exceptional Sound Quality
The microphone captures clear and crisp audio which provides professional-grade sound suitable for streaming, recording gameplay videos, and online gaming sessions. It enhances engagement for both the user and their audience.
Side Address Design
The A6T microphone contains a side address design, meaning you speak into the side of the microphone rather than the top. This design is complemented by the pop filter, which only attaches in one orientation, ensuring correct placement.
Boom Arm Performance
The included boom arm effectively keeps the microphone in place, but its lightweight construction creates concerns about its durability over time.
Accessories and Cable Ties
While cable ties are included with the A6T microphone, they may not meet expectations. I think Upgrading to better cable ties might be necessary for a more secure cable management solution.
Ease of Setup
The FIFINE USB Microphone is plug-and-play, requiring no complicated setup or additional drivers and is accessible for users of all levels of experience which makes it a hassle-free option for everyday use. No additional apps are required; simply plug it in, and the RGB lighting confirms its activation. However, the inability to customize or disable the RGB lighting without muting the microphone may be a drawback for some users.
Mute Button Convenience
The microphone features a built-in mute button for added convenience and control. It allows instant muting without disrupting the flow of content during live streaming or quick breaks.

Long-Term Durability
Despite its affordable price of $50, the microphone has been reliable over a span of two years and serves well for everyday PC use, chatting, gaming, and streaming.
Noise Suppression Considerations
The microphone lacks custom software for noise suppression which may lead to picking up background noise, such as mechanical keyboard sounds. However, this can be addressed using third-party software like OBS audio filters or Discord’s built-in noise suppression.
Overall Value
Despite minor issues with noise suppression, the microphone’s quality, convenience, and affordability make it a highly recommended option, specially if you pair it with additional filters for improved performance.
Performance Comparison
Gain Control: The A6T microphone features a large knob on the bottom for adjusting gain. However, the indicator for gain level is inconveniently positioned and doesn’t accurately correspond to the position of the knob, potentially making gain adjustment less intuitive.
Software Support: The A6T microphone lacks dedicated software, meaning there are no official drivers or apps provided. Consequently, there is no support for features like VST plugin integration for effects such as noise gates or compressors, nor is there support for audio mixing.
Windows Volume Slider: Adjusting the volume slider on Windows does not affect the A6T microphone when using default drivers.
Limitations: The absence of official drivers and software features might be seen as a drawback for users who rely on advanced audio processing or customization options.
Workarounds: Despite the limitations, alternative solutions are there for audio processing needs. These solutions demonstrate that while certain features are lacking, they may not be critical if the microphone’s performance meets expectations.
Performance Evaluation: To assess the microphone’s performance, it’s important to test its capabilities in various challenging scenarios which will help users to make informed judgments about its suitability for their needs.
Comparison with Blue Yeti
Blue Yeti Comparison: The Blue Yeti microphone, though costing about twice as much as the Fifine A6T and coming with fewer accessories, produces a sound quality that is similar to what you will hear from the A6T.
WAN Show Sound: The sound quality you typically hear on the WAN Show serves as a reference point for comparison. This reference provides context for understanding the performance of the A6T and other microphones.
Evaluation: Despite any limitations or differences in sound quality, the A6T microphone is considered to sound “pretty darn okay” by the speaker. This subjective assessment suggests that.
Personal Opinion: The A6T may offer satisfactory performance for its price point and intended use. My assessment is based on personal opinion and experience, rather than extensive laboratory testing or technical analysis.
Performance Results with Dayton Audio EMM6
Reference Microphone: The Dayton Audio EMM6, a calibrated omni-directional microphone, serves as the reference for comparison.
Frequency Response: In case of frequency response, the A6T performs surprisingly similarly to other USB microphones. However, there is a noticeable drop in a certain range, indicating a slightly darker sound profile compared to some other models.
Comparison with Elgato Wave: The Elgato Wave stands out as an outlier, producing a brighter sound profile. However, this brightness comes at the cost of picking up more sibilance, particularly harsh “S” and “ss” sounds.
Overall Performance: Despite some variations in sound profile among the compared microphones, the differences are not substantial. The field is close enough that there isn’t a huge disparity in performance from the worst to the best USB microphone options considered.
Consideration for USB Microphones: If considering a USB microphone, the performance differences among various models may not be significant enough to warrant a clear preference. Therefore, factors such as price, features, and personal preferences should also be taken into account when making a decision.
Comparison with Higher-End XLR Microphones
And believe it or not, I kind of see the same thing when I compare it even to higher end XLR microphones. Compared to an Electrovoice RE20, a mic that costs literally 10 times as much as this entire complete solution, the on paper results are shockingly close. And in the real world, the RE20 is better, but it’s certainly not 10 times better. However, that is under somewhat ideal conditions. Better microphones can have advantages that go beyond frequency response. Like for example, background noise rejection. If you’re alone in a room hanging out with your friends on Discord, you do not need a $450 mic, this is great.
I have discussed about this Mic in my Blog Post, Click Here to read now.
To know more about Recording Video & Audio Gears, Click this Link
Get in touch with podcasting services and experts those will save you tons of time at Podcast Production Services.
With that being said, Let’s connect with all such free and paid tool/services you might need knowingly or unknowingly to fuel your growth. Here’s 21 BEST AI TOOLS AND PLATFORMS TO GROW YOUR PODCAST AND CONTENTS.
0 notes
Text
Topaz Labs Cracked Mac Crack 3.3.10 Latest Version
What is Topaz Labs Cracked Mac?
Topaz Labs is a software company known for its suite of image enhancement tools designed to improve and transform photos using advanced AI algorithms. “Topaz Labs cracked Mac” refers to unauthorized versions of their software that have been modified to bypass licensing restrictions, allowing users to access the full features of the software without paying for it. These cracked versions are distributed illegally and can lead to significant security risks, such as malware infections and data breaches.
Features and Benefits
Topaz Labs’ legitimate software offers a range of features, including:
AI-Powered Enhancements: Advanced algorithms that can enhance image clarity, detail, and resolution.
Noise Reduction: Tools to reduce noise while preserving image details.
Sharpening Tools: Techniques to improve image sharpness and reduce blurriness.
Creative Effects: Various artistic filters and effects to transform photos creatively.
Using these features can significantly enhance photo quality and provide creative options for photographers. However, cracked versions compromise the integrity of these features and can lead to an unstable and unreliable user experience.
How to Download Topaz Labs Cracked Mac?
Here’s a step-by-step guide for installing and activating Topaz Video Enhance AI and checking out Cleanshot X:
1. Download Topaz Video Enhance AI 3.1.6 DMG:
Click the download link to get the DMG file for Topaz Video Enhance AI version 3.1.6.
2. Install Topaz Video Enhance AI:
Open the downloaded DMG file and follow the installation instructions to install the software on your Mac.
3. Download the Activation Script:
Obtain the Topaz Video AI Activation Script from the provided link.
Ensure your Terminal is set to zsh to run the script correctly.
4. Run the Activation Script:
Open the Terminal and navigate to the location of the downloaded activation script.
Execute the script to activate Topaz Video Enhance AI.
5. Watch Installation and Activation Video:
For detailed guidance, watch the video tutorial on how to install and activate Topaz Video Enhance AI.
6. Check Out Cleanshot X:
We also offer Cleanshot X version 4.5 for Mac. Visit the download link to get the latest version for free.
How to Install and Activate Topaz Labs Cracked Mac 3.3.10?
Here’s a step-by-step guide based on the provided points:
1. Download Topaz Video Enhance AI 3.1.11 DMG:
Obtain the DMG file for Topaz Video Enhance AI version 3.1.11 from the provided download link.
2. Install the Software:
Open the DMG file and follow the on-screen instructions to install Topaz Video Enhance AI on your Mac.
3. Run Activation Script:
Download the Topaz Video AI Activation Script. Ensure your Terminal is set to zsh.
Open the Terminal and run the activation script to activate the software.
4. Address Feature Issues:
If you encounter issues with features in version 3.1.11, consider using Topaz Video Enhance AI 3.1.7 Mac Crack.
Download the 3.1.7 version and use the same activation script as above.
5. Avoid Updating:
Do not update to version 3.2, as it may cause issues.
Avoid clicking the trial button to prevent potential complications.
6. Wait for Fixes:
We are working on a fix for the Topaz Video Enhance AI Mac 3.2 update. Stay tuned for updates.
7. Check Latest Version:
The latest version update as of September 4, 2023, is available. Watch the video provided for installation instructions.
How to Use Topaz Labs Cracked Mac?
Enhancing your videos with Topaz Video Enhance AI is straightforward. Just follow these steps:
1. Import Your Video: Begin by loading your video file into Topaz Video Enhance AI.
2. Select Output Resolution: Choose the resolution you want for the final video.
3. Pick an AI Model: Select the AI model that best suits your enhancement needs.
4. Adjust Settings: Customize the settings to tailor the enhancement process to your preferences.
5. Start Processing: Click “Start Processing” and let Topaz Video Enhance AI handle the rest.
With these simple steps, Topaz Video Enhance AI will automatically improve the quality of your video.
Conclusion
Using “Topaz Labs cracked Mac” versions is highly discouraged due to the associated legal and security risks. Opting for legitimate software not only ensures a secure and reliable experience but also supports the developers who create these valuable tools. If you’re interested in Topaz Labs products, check their official website for trial versions or purchase options that suit your needs.
0 notes
Text
Security, Professional (JNCIP-SEC) JN0-637 Dumps Questions
JNCIP-SEC, the professional-level certification in this track, is specifically designed for networking professionals who possess advanced and in-depth knowledge of the Juniper Networks Junos OS for SRX Series devices. This certification validates your ability to configure, manage, and troubleshoot Juniper security products, ensuring that you are well-prepared to handle complex security challenges in a networked environment. To thoroughly prepare for this rigorous examination and enhance your chances of success, you can obtain the latest Security, Professional (JNCIP-SEC) JN0-637 Dumps Questions from Certspots. These resources will provide you with comprehensive practice questions and study materials, equipping you with the knowledge and confidence needed to excel in your certification test.
youtube
Security, Professional (JNCIP-SEC) JN0-637 Exam
JNCIP-SEC, the professional-level certification within this track, is designed specifically for networking professionals who possess advanced knowledge and expertise in the Juniper Networks Junos OS for SRX Series devices. This certification is a testament to a candidate's ability to handle complex security challenges and scenarios. The written exam associated with this certification rigorously tests your understanding of advanced security technologies, as well as your proficiency in platform configuration and troubleshooting skills.
This comprehensive track includes four distinct certifications, each catering to different levels of expertise and knowledge:
JNCIA-SEC: Security, Associate. This entry-level certification is ideal for those beginning their journey in network security. For further details, see JNCIA-SEC.
JNCIS-SEC: Security, Specialist. This intermediate certification is for those who have gained some experience and wish to deepen their understanding of security concepts. For more information, see JNCIS-SEC.
JNCIP-SEC: Security, Professional. This advanced certification is detailed in the sections below and is tailored for professionals with significant experience and advanced knowledge in the field.
JNCIE-SEC: Security, Expert. This expert-level certification is the pinnacle of the Security Track, designed for those who have mastered security technologies and wish to be recognized as experts in their field. For additional details, see JNCIE-SEC.
Understand The JNCIP-SEC JN0-637 Exam Objectives
Troubleshooting Security Policies and Security Zones: In this section, we will delve into the intricacies of identifying and resolving issues related to security policies and security zones. This includes understanding the fundamental principles, common pitfalls, and advanced troubleshooting techniques to ensure the robustness of your security infrastructure.
Logical Systems and Tenant Systems: Explore the architecture and configuration of logical systems and tenant systems. Learn how to effectively manage multiple tenants within a single infrastructure, optimize resource allocation, and maintain stringent security measures across different logical environments.
Layer 2 Security: This topic covers the essential aspects of Layer 2 security, focusing on protecting the data link layer from various threats. We will examine techniques such as MAC address filtering, VLAN security, and mitigating common Layer 2 attacks like ARP spoofing and STP manipulation.
Advanced Network Address Translation (NAT): Dive deeper into the advanced concepts and applications of Network Address Translation. Understand the various types of NAT, their use cases, and how to configure and troubleshoot complex NAT scenarios to enhance network security and connectivity.
Advanced IPsec VPNs: Learn about the sophisticated configurations and implementations of IPsec VPNs. This section will cover topics such as site-to-site and remote access VPNs, advanced encryption techniques, and optimizing IPsec performance for secure and efficient communication.
Advanced Policy-Based Routing (APBR): Expand your knowledge on policy-based routing by exploring advanced configurations. Understand how to implement APBR to control traffic paths based on policies, enhance network performance, and ensure compliance with organizational requirements.
Multinode High Availability (HA): Gain insights into establishing high availability across multiple nodes. This topic covers the principles of HA, various HA models, and best practices to ensure continuous network operations and minimize downtime in case of failures.
Automated Threat Mitigation: Explore automated methods and tools for threat mitigation. Learn about the latest advancements in threat detection and response, how to configure automated systems to counteract security incidents, and maintain a proactive security posture.
Study Tips To Prepare for the Juniper JN0-637 Exam
Understand the Exam Objectives: Thoroughly review the exam objectives outlined by Juniper. Make sure you are comfortable with each topic and subtopic listed.
Hands-On Practice: Set up a lab environment where you can practice configuring and troubleshooting Junos OS on SRX Series devices. Practical experience is crucial for understanding the concepts.
Use Official Study Materials: Utilize Juniper's official study guides, documentation, and training courses. These resources are specifically designed to help you prepare for the exam.
Join Study Groups: Participate in online forums or study groups. Engaging with others who are also preparing for the exam can provide new insights and help reinforce your knowledge.
Take Practice Exams: Practice exams can help you get familiar with the format of the questions and identify areas where you need further study.
Focus on Weak Areas: Identify your weak areas and spend extra time reviewing and practicing those topics. Make sure you understand the underlying principles and can apply them in different scenarios.
Review and Revise: Regularly review and revise the material you have studied. Repetition will help reinforce your knowledge and improve recall during the exam.
Conclusion
In conclusion, achieving the Security, Professional (JNCIP-SEC) certification is a significant milestone for networking professionals aiming to demonstrate their advanced expertise in Juniper Networks security technologies. By thoroughly understanding the exam objectives, engaging in hands-on practice, and utilizing the recommended study materials and resources, candidates can enhance their preparation and increase their chances of success. With dedication and a strategic approach to studying, you can confidently face the JN0-637 exam and take a substantial step forward in your professional career in network security.
0 notes
Text
Nmap: My Experience with This Powerful Network Scanning Tool

Many IT and cybersecurity experts use the powerful network scanning tool Nmap. Nmap is a powerful network scanning tool that I've found very useful in my job as an IT worker. It lets me scan networks quickly and easily, which helps me find live hosts, open ports, and working services. This post will discuss what I've learned and done with Nmap and show you how it can be used in the real world. What is Nmap? I found the open-source command-line tool Nmap, which is short for Network Mapper, invaluable for network port and IP address scanning. Although Linux is its main platform, its adaptability spans several others. Nmap helps me to quickly find installed programs and provide a whole picture of the network. As a network administrator, Nmap lets me find all the devices running on my network, uncover open ports and services, and spot possible weaknesses. Gordon Lyon, sometimes known as Fyodor, developed the program to streamline mapping a whole network and identify its open ports and services. Featuring in films like The Matrix and the TV series Mr. Robot, Nmap has become somewhat well-known throughout the years and even entered popular culture. Why Did I Apply For Nmap? Many other security experts find Nmap preferred for several more convincing reasons than other network scanning software. First, Nmap lets you quickly and effectively map networks without requiring advanced instructions or setups. It enables you to create complicated scripts using the Nmap Scripting Engine (NSE) and supports basic commands such as determining whether a host is up. Nmap Features I Most Find Beneficial Nmap fast identifies any device on a network—including servers, routers, switches, and mobile devices. Managing single or numerous networks makes this function quite helpful. Nmap can even reasonably detect application versions and find services running on a system, including DNS and web servers. This talent enables me to see current weaknesses. Nmap can offer a comprehensive operating system that runs on device information, including particular OS versions. This element is vital when developing further methods of penetration testing. Using Nmap to use current scripts from the Nmap Scripting Engine, I search systems during security audits for vulnerabilities. This talent helps me to spot and fix security flaws. Nmap also provides Zenmap, a graphical user interface designed to enable visual mappings of a network. This interface helps reporting and increases usability, therefore facilitating the presentation of complex network structures and vulnerabilities to stakeholders. How To Install Nmap? The particular requirements of the work will determine the several uses for Nmap. These are some broad Nmap use guidelines: Download and set up Nmap from the official website - https://nmap.org/download.html. Check for the executable file that is being downloaded in your system and then run it. Enter the command for the scan you wish to do with extra targets or settings. For a TCP SYN scan, for instance, "nmap -s "; for OS detection, "nmap -O ." Enter to run the scan. Nmap will show operating services, open ports, and a list of live hosts together with scan findings. Top Functions Of Nmap With Codes Network Mapping Network mapping is Nmap's primary purpose; it lets me scan the network and look for connected devices, including PCs, servers, routers, and switches. I find information on online devices, open ports, and network connections by running the basic Nmap command focused on an IP address or range. Zenmap allows one to depict this information graphically. Additionally captured by Nmap are media access control (MAC) addresses, which enable device manufacturer identification. For example, I could run to find out which devices are linked to my network only running: Code: nmap 192.168.1.0/24 Network Packet Manipulation Nmap can change the contents of network messages. I can catch, filter, reroute, or send data packets with these tools. The Nping tool stands out because it can test firewall rules, stress test networks, and fix problems. As an example, if I want to see how strong my network is, I could use Code: nping --tcp -p 80 192.168.1.10 Scripting The coding features of Nmap are what make it so powerful. I can automate complicated scanning jobs and find security holes with the Nmap Scripting Engine (NSE). To find weaknesses, for example, I might use Code: nmap --script vuln 192.168.1.10 Fundamental Nmap Commands I often run through these fundamental commands: On a host, find open ports by: nmap To obtain OS details and service versions: Nmap -A To find whether a firewall is turned on. nmap -sA To examine a particular port in scanning nmap -p Nmap's rich documentation offers many choices and examples for more complex scanning and scripting. Looking for Alternatives to Nmap As a security tester, I've looked into many tools that can be used instead of Nmap. There are several open-source tools for security testing, and each one is good at a different part of it: Zap: great program scanner. John the Ripper: A strong brute force password hacker. Wireshark: It is a flexible packet sniffer. These tools are handy, but they usually only cover specific areas of security testing. On the other hand, Nmap is the best because it can scan whole networks. Even paid penetration testing tools like Rapid7's Metasploit or Burp Suite have difficulty entirely replacing Nmap. These paid tools have features and interfaces that are easy for anyone to use and can do various security jobs. However, Nmap is still used by many security teams, including mine, because it can run scripts and meet special user needs. Nmap gets most of its money from OEM licensing, meaning companies buy and use it for their goods. Many paid pen-testing tools either use parts of Nmap code in their programs or run Nmap locally and then use their programs to read the results. Sometimes, companies that buy commercial tools might use Nmap behind the scenes. Most of the time, the extra cost is worth it because these commercial tools are so easy to use that even IT security staff with little experience can do jobs that would be hard to do with Nmap alone. Also, these tools make it easier to write professional reports faster, which is a big plus. It's also possible for companies to use skilled penetration testing services instead of their tools. It's essential to keep in mind, though, that some security testing firms may use the open-source Nmap tool directly. Most businesses are honest about how they work, but some, like Nmap Online, which has a name that could be confusing, use images and domain names that look a lot like those on the official Nmap.org website, which could lead to confusion. Even though there are other options, I find that Nmap's many features and adaptability make it an essential part of my security testing kit. In Summary In my toolkit for cybersecurity, Nmap is quite a helpful instrument. Although mastery requires time and effort, the great powers it provides make it well worth it. Nmap offers a complete collection of tools to help you safeguard and comprehend your network regardless of your knowledge about network security—that of a security professional, network administrator, or just curious learner. FAQs What is Nmap, and for what purposes can one utilize it? For Network Mapper, Nmap is an open-source network security audit and discovery tool. It lets users scan networks looking for running services, open ports, live hosts, and operating systems. IT managers and cybersecurity experts extensively use Nmap for chores, including network inventory, host or service uptime monitoring, and timetable management of service upgrades. How might I install Nmap on several OS systems? Installing Nmap differs somewhat based on your operating system: Linux: Run sudo apt-get install nmap to install Nmap on variants such as Debian or Ubuntu. While the installation command may vary for other distributions, it is usually found in the default repositories. Windows: Download the installer from the official Nmap website, then run the executable file to install. macOS: Take advantage of Homebrew or another package manager. The installation command is brew install nmap. Zenmap: You can download the Zenmap graphical user interface (GUI) variant for a more aesthetically pleasing experience for all operating systems. Can one legally use Nmap for network scanning? While using Nmap is legal, the legality relies on your usage. A perfectly lawful and popular security audit and management method is scanning your network or one under clear authority. Using Nmap to scan devices or networks without permission is unethical and illegal. Always be sure you have the required rights before doing any scans since unauthorized scanning could result in serious legal penalties. Read the full article
0 notes