#Keyboard Automation Tools
Explore tagged Tumblr posts
Text
youtube
Hii Everyone! I Hope all are doing well
Medical Insurance Auto-Fill Software is a specialized tool designed to streamline and automate the process of filling out medical insurance claim forms and related documentation. The software is developed to enhance efficiency, reduce errors, and save time.
Implementing Medical Insurance Auto-Fill Software can contribute to a more streamlined and accurate claims submission process, reducing the administrative burden on data entry works
Thank you for watching, hope our video may helps you, for more helpful videos and relatable video please subscribe our channel, do share , follow and like the video.
#Medical Insurance Auto-Fill Software#Efficient Medical Form Automation Tools#Auto-Typing Software#Automated Form Filling#Data Entry Automation#Smart Form Completion#Automatic Data Input#Efficient Form Processing#Keyboard Automation Tools#Typing Automation Software#Form Auto-Fill Solutions#Data Entry Efficiency Tools#Automated Typing Technology#Form Filling Automation Software#Efficiency Software Solutions#Auto-Complete Software#Automated Form Submission#Youtube
0 notes
Text
A study of over 19 billion exposed passwords has revealed that only 6 percent of the leaked passwords were unique. The vast majority, 94 percent, were reused or duplicated, making them prime targets for cybercriminals.
Common keyboard patterns and easily guessed strings remain prevalent. The "123456" sequence still dominates, appearing in 338 million passwords, according to the Cybernews study.
Why It Matters
The scale of password breaches and the continued reliance on weak passwords have heightened concerns about "credential stuffing," a tactic in which attackers use automated tools to test stolen credentials across multiple platforms.
Even breach success rates between 0.2 percent and 2 percent can still yield thousands of compromised accounts, according to Cybernews.
The most common password length is eight to 10 characters, and a significant portion contains only lowercase letters and digits, making passwords vulnerable to brute-force attacks.
Compared to just 1 percent in 2022, 19 percent of passwords now mix uppercase, lowercase, numbers, and symbols.
What To Know
The dataset analyzed included 19,030,305,929 passwords sourced from 200 cybersecurity incidents. These came from leaked databases, stealer logs, and combolists.
Paul Walsh, CEO of MetaCert, has emphasized another growing risk vector: phishing attacks targeting phones. He has urged cybersecurity companies to tackle SMS phishing with the same intensity as email security to help mitigate password leaks and breaches.
In an article published on Monday, Walsh told Forbes that MetaCert's latest national SMS phishing test, carried out in March and including carriers such as AT&T, Verizon, T-Mobile and Boost Mobile, was concerning.
"Every phishing message was still delivered," Walsh said. "None were blocked, flagged, or rewritten."
Walsh has written an open letter to the cybersecurity industry asking why the SMS phishing problem wasn't solved long ago.
What Are the Most Common Passwords?
Predictable patterns continue to dominate password choices. "123456" alone appears in 338 million of the passwords in the Cybernews study, while "password" and "admin" were used over 100 million times combined.
Users also often rely on names, with "Ana" appearing in 178.8 million instances. Positive words like "love," "freedom," and pop culture references such as "Batman" are also prevalent. Profanity, surprisingly, is common as well; "ass" alone shows up in 165 million passwords.
Some of the most frequently used pop culture terms in passwords included "Mario" (9.6 million), "Joker" (3.1 million), "Batman" (3.9 million), and "Thor" (6.2 million).
Additionally, seasonal words, food items, and cities frequently feature in password choices, leaving accounts vulnerable to attackers who exploit such predictability. Over 10 million of the passwords featured "apple," 4.9 million "rice," and 3.6 million "orange," while 3.3 million opted for "pizza."
The most popular city for passwords was "Rome" (13 million), while "summer" (3.8 million) was the most popular season.
What People Are Saying
Neringa Macijauskaitė, information security researcher at Cybernews: "We're facing a widespread epidemic of weak password reuse. If you reuse passwords across multiple platforms, a breach in one system can compromise the security of other accounts."
MetaCert CEO Paul Walsh told Forbes: "Criminals have already moved in full force, and the industry is failing to respond."
"The cybersecurity industry has no shortage of experts in email security, endpoint protection, or network defense, but when it comes to SMS infrastructure and security, there is a distinct lack of deep expertise."
What Happens Next
Researchers have urged individuals and organizations to boost password security by using password managers, enforcing minimum length and complexity standards, and enabling multi-factor authentication. Organizations are advised to regularly audit access controls, monitor for credential leaks, and adopt real-time detection solutions.
10 notes
·
View notes
Text
Yet another post on art and AI on the godsforsaken internet
I've been in a weird mood and have been half-conscious for the past two days so if this doesn't make sense to anyone else that's not my problem. In the age of automated image generation I found my answer to what art is, which also overlaps with the ever-present question what artist's personal style is. It's using the medium and means and experience you have to say something, show something, the hundreds, thousands of tiny decisions, conscious or unconscious, the knowledge you have, are guessing or just bullshitting through, putting the feelings you have or ones you want to evoke into whatever you're creating, so you whisper, say, scream out your soul at whomever may witness it, if they ever do. You take your soul and emotions and push it, through the pencil tip, through the brush, through the keyboard, though concrete that makes a building, through a chisel that creates a shape, an object, a sound, and you hope that whomever encounters it will marvel at it, see the beauty or the ugliness or the bafflement or whatever you tried to express; or maybe you did not try to express anything in particular, the beholder is your collaborator, their perception is part of your art; or maybe you create just for yourself, hide the final product, destroy it, reveling just in in the creation and destruction, a secret between only you and whichever unseen forces are there. The final result may be important, but the act of creation is as much, if not more. Or maybe it's something completely different.
The reason people have argued over centuries what art is or isn't is because the answer is complex and also rooted in human society and the lines drawn often had to do more with class and money than actual creativity and expression. Still, art is deeply, inherently human. That means that yes, a child's drawing is art, your first teenage drawing of anime blorbo is art, Michaelangelo's David is art and yes even that boobily boobing hentai drawing is art. The most disgusting fetish art is art and the most vile fascist art is art. Now, we're not going to get into what is GOOD art, what art should be presented and celebrated in public spaces, limited public spaces and private - much smarter, more stupid and more pretentious people have debated it over the centuries and will keep on doing so. What about AI-generated things then? Well, first thing that comes to mind is this: https://inspirobot.me/
Inspirobot is a site that predates the present learning models - it's not an actual AI, it's just a site that takes fragments of motivational phrases ("X is like YZ", "the only way to X is to Y the Z" etc), randomly chooses words to put into them and combines them with stock photos of the type that are used for inspirational memes. The results are random, chaotic, sometimes funny and every once a while extremely profound. Present generation models are a slightly more complex version of exactly that - taking bits and pieces of existing things and going "this could statistically be linked to that". There isn't a thought behind what it produces, apart from the initial thoughts of the people who created the pieces it smashes together. Second thing that comes to mind, especially when techbros whine that "they perfected their word input to achieve this result" (funny to hear because that's also how artists have to work.. in search engines to find good references) is... workshops. If you have a workshop, a creative event, a gathering of creators of some kind, working in the same general medium and you give them all the same tools along with a prompt, theme, even the same basic composition.... What you'll get from each of them will be different, but in some way consistent with their art style/expression, because it has been filtered through THEM*. And THAT is exactly why it's art. [This is also why there's such a different reaction to inspiration vs. plagiarism. Inspiration is taking a thing, passing it through yourself and presenting something new; even if you are not aware exactly how, you are entering a dialog with the OG creation. Plagiarism is taking someone else's creation and trying to pass it off by yours, which is a perverse form of identity fraud, only it's not the legal identity but the internal one. Yes, even anime boobies. Draw your own.]
#musings#I'm not even high or anything#I kinda wish I were but I have a work thing to finish#There's nothing revolutionary said here#but all text I've seen either make it all seem much more complicated#or focus on the technical aspect#IDK
9 notes
·
View notes
Text
Morph Madness!
Fixing Exploding Morphs
Marik's Egyptian Choker is currently in production. It is the first accessory I've made that involves assignment to more than one bone and morphs for fat, fit and thin states. So there is a learning curve, and it is during that learning curve that interesting and unexpected things can happen.
As with my other content, I'm making the choker fit sims of all ages and genders--that's 8 different bodies.
Adding fat, fit and thin morphs multiples this number to 27 different bodies.
I'm also making 3 levels of detail for each of these. The number comes to 81 different bodies, 81 different bodies for which I need to tightly fit a cylinder around the neck and avoid clipping.

That's a lot of work. I can see why most custom content creators stick with one age, gender and detail level. At least, they did in the past. Our tools are getting better day by day, and that may partly be because of creative, ambitious and somewhat obsessive people like me.
There are usually multiple ways to solve the same problem. Some ways are faster than others. This I've learned from working in Blender3D. You can navigate to a button with your mouse or hit the keyboard shortcut. You can use proportional editing to fiddle around with a mesh or you can use a combination of modifiers.
If I am going to be creating 81 chokers, I don't want to be fiddling around on each one of them for an hour. I need something automated, repeatable and non-destructive so I can make adjustments later without having to start over from the beginning. I need to work smart rather than just work hard.
This is where modifiers and geometry nodes come in. After you develop a stack to work with one body, the same process pretty much works for the others as well. That is how it became easier for me to model each of the 81 chokers from scratch rather than to use proportional editing to fit a copy from one body to the next.
But I was about to confront an explosive problem…
Anyone who has worked with morphs before probably knows where this story is headed. There is a good reason to copy the base mesh and then use proportional editing to refit it to the fat, fit and thin bodies. That reason has to do with vertex index numbers.
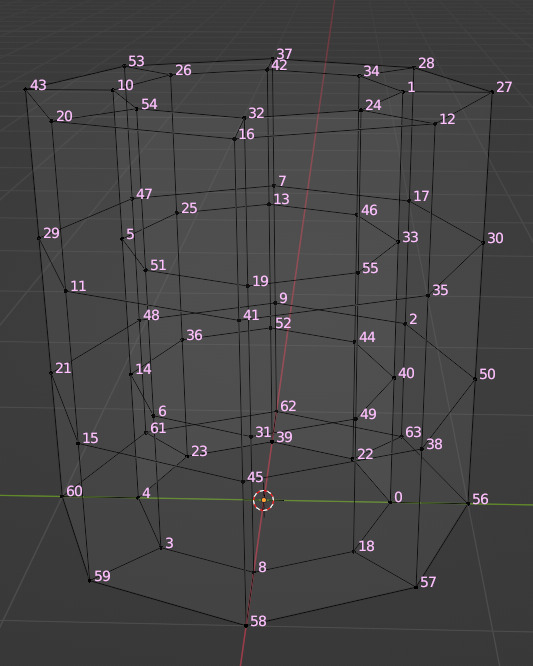
You see, every vertex in your mesh has a number assigned to it so that the computer can keep track of it. Normally, the order of these numbers doesn't really matter much. I had never even thought about them before I loaded my base mesh and morphs into TSRW, touched those sliders to drag between morph states, and watched my mesh disintegrate into a mess of jagged, black fangs.

A morph is made up of directions for each vertex in a mesh on where to go if the sim is fat or thin or fit. The vertex index number determines which vertex gets which set of directions. If the vertices of your base mesh are numbered differently than the vertices of your morph, the wrong directions are sent to the vertices, and they end up going everywhere but the right places.
It is morph madness!
When a base mesh is copied and then the vertices are just nudged around with proportional editing, the numbering remains the same. When you make each morph from scratch, the numbering varies widely.
How, then, could I get each one of those 81 meshes to be numbered in exactly the same way?
Their structures and UV maps were the same, but their size and proportions varied a lot from body to body. Furthermore, I'd used the Edge Split modifier to sharpen edges, which results in disconnected geometry and double vertices.
Sorting the elements with native functions did not yield uniform results because of the varying proportions.
The Blender Add-On by bartoszstyperek called Copy Verts Ids presented a possible solution, but it was bewildered by the disconnected geometry and gave unpredictable results.
Fix your SHAPE KEYS! - Blender 2.8 tutorial by Danny Mac 3D
I had an idea of how I wanted the vertices to be numbered, ascending along one edge ring at a time, but short of selecting one vertex at a time and sending it to the end of the stack with the native Sort Elements > Selected function, there was no way to do this.
Of course, selecting 27,216 vertices one-at-a-time was even more unacceptable to me than the idea of fiddling with 81 meshes in proportional editing mode.
So… I decided to learn how to script an Add-On for Blender and create the tool I needed myself.
A week and 447 polished lines of code later, I had this satisfying button to press that would fix my problem.

Here are the index numbers before and after pressing that wonderful button.
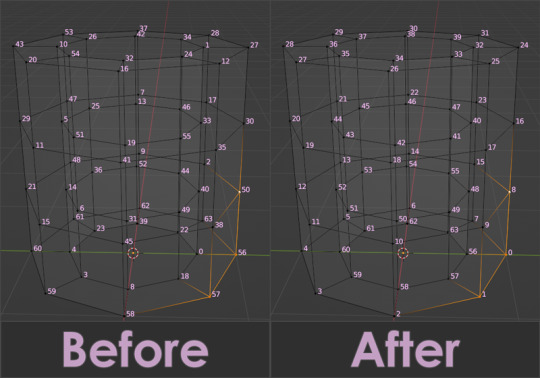
My morphs are not exploding anymore, and I am so happy I didn't give up on this project or give myself carpal tunnel syndrome with hours of fiddling.
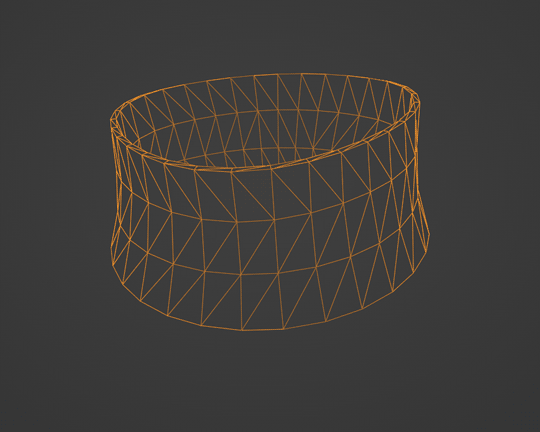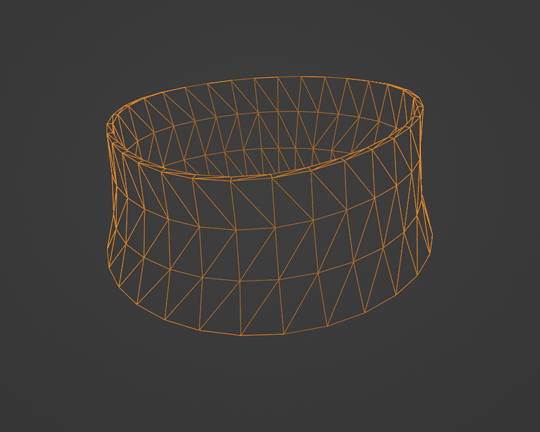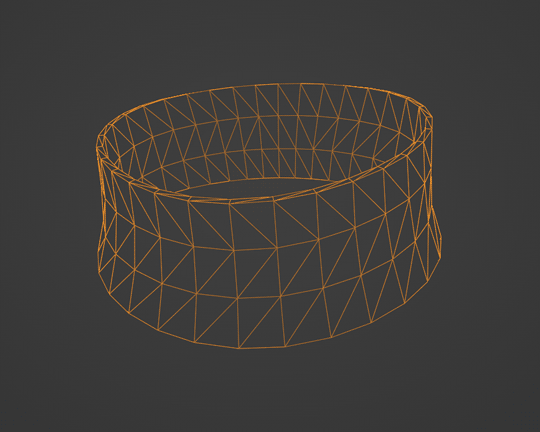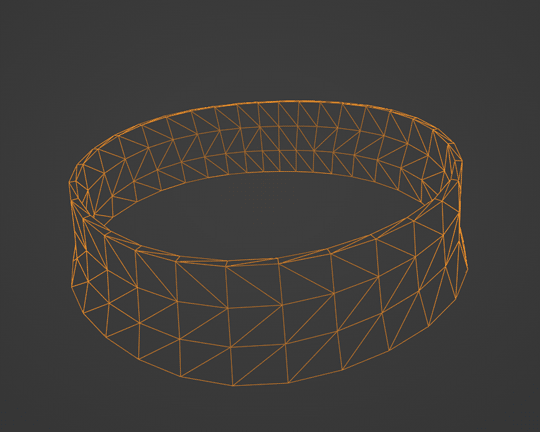
Marik's Egyptian Choker is coming along nicely now. I haven't avoided fiddling entirely, but now it only involves resizing to fix clipping issues during animation.
Unfortunately, I'll have to push the release date to next month, but now, I have developed my first Blender Add-On and maybe, after a bit more testing, it could be as useful to other creators in the community as its been to me.
Looking for more info about morphing problems? See this post.
See more of my work: Check out my archive.
Join me on my journey: Follow me on tumblr.
Support my creative life: Buy me a coffee on KoFi.
#exploding#morph#mesh#sims 3#cc#custom content#tutorial#C:O#SallyCompaq122#mod the sims#cc creator#art process#blender#3d#add on#shape keys#sort#vertex#index#blendercommunity
86 notes
·
View notes
Text
DB9 connector is a widely used electrical connector. Recognizable by its distinctive D-shaped metal shell and 9-pin configuration, the DB9 connector has been a staple in electronics for decades, especially for serial communication.

What Is a DB9 Connector?
The DB9 connector features a D-shaped shell to ensure proper orientation when connecting. The 9 pins (or sockets in female versions) are arranged in two rows, with 5 pins on the top and 4 on the bottom. This compact design is suitable for low-profile applications.
The connector comes in two main types:
DB9 Male Connector: Have pins and are typically used on cables.
DB9 Female Connector: Have sockets and are often found on equipment or devices.
Key Features of DB9 Connectors
Durable Construction: The metal shell provides mechanical strength and shields against electromagnetic interference (EMI).
Compact Design: Ideal for devices where space is limited.
Versatile Applications: Commonly used for RS-232 serial communication, connecting peripherals like mice, keyboards, and modems.
Customization: Can support different pin configurations and wiring for varied uses.
Common Applications of DB9 Connectors
Serial Communication: Widely used in RS-232 interfaces to connect computers, printers, and industrial equipment.
Automation and Control Systems: Frequently seen in programmable logic controllers (PLCs) and industrial machines.
Networking Equipment: Used in switches, routers, and legacy systems.
Testing and Prototyping: Found in diagnostic and development tools for electronics.
DB9 Pinout Diagram
Here’s a standard pinout for a DB9 connector used in RS-232 communication:

Advantages of DB9 Connectors
Reliable Connection: Secure locking mechanism ensures a stable link.
Broad Compatibility: Works with many legacy and modern devices.
Easy Maintenance: Simple design allows for straightforward repairs or replacements.
8 notes
·
View notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
3 notes
·
View notes
Text
It used to be that when BMW would refit a factory to build a new car, the only way the automaker could check if the chassis would fit through the production line was to fly a team out and physically push the body through the process, making note of any snags.
Now, process engineers can simply run a simulation, sending a 3D model of the car through a near-identical digital twin of the factory. Any mistakes are spotted before the production line is built, saving time and money.
Such is the power of the industrial metaverse. Forget sending your avatar to virtual meetings with remote colleagues or poker nights with distant friends, as Mark Zuckerberg envisioned in 2021 when he changed Facebook’s name to Meta; the metaverse idea has found its killer app in manufacturing.
While the consumer version of the metaverse has stumbled, the industrial metaverse is expected to be worth $100 billion globally by 2030, according to a World Economic Forum report. In this context, the concept of the metaverse refers to a convergence of technologies including simulations, sensors, augmented reality, and 3D standards. Varvn Aryacetas, Deloitte’s AI strategy and innovation practice leader for the UK, prefers to describe it as spatial computing. “It’s about bridging the physical world with the digital world,” he says. This can include training in virtual reality, digital product design, and virtual simulations of physical spaces such as factories.
In 2022, Nvidia—the games graphics company that now powers AI with its GPUs—unveiled Omniverse, a set of tools for building simulations, running digital twins, and powering automation. It acts as a platform for the industrial metaverse. “This is a general technology—it can be used for all kinds of things,” says Rev Lebaredian, vice president of Omniverse and simulation technology at Nvidia. “I mean, representing the real world inside a computer simulation is just very useful for a lot of things—but it’s absolutely essential for building any system that has autonomy in it.”
Home improvement chain Lowe’s uses the platform to test new layouts in digital twins before building them in its physical stores. Zaha Hadid Architects creates virtual models of its projects for remote collaboration. Amazon simulates warehouses to train virtual robots before letting real ones join the floor. And BMW has built virtual models for all its sites, including its newest factory in Debrecen, Hungary, which was planned and tested virtually before construction.
To simulate its entire manufacturing process, BMW filled its virtual factories with 3D models of its cars, equipment, and even people. It created these elements in an open-source file format originated by Pixar called Universal Scene Description (OpenUSD), with Omniverse providing the technical foundation for the virtual models and BMW creating its own software layers on top, explains Matthias Mayr, virtual factory specialist at BMW.
“If you imagine a factory that would take half an hour to walk from one side to the other side, you can imagine it’s also quite a large model,” Mayr says. Hence turning to a gaming company for the technology—they know how to render scenes you can run through. Early versions of the virtual factory even had gaming-style WASD keyboard navigation, but this was dropped in favor of a click-based interface akin to exploring Google Street View in a browser, so anyone could easily find their way.
BMW also uses Omniverse for collaboration on car design and customization visualizations for customers, but a key benefit is being able to model production lines. New cars mean a new assembly process, but refitting a factory is a daunting process. Previously, key information was held in silos—production crews understood details of the assembly process, external suppliers had specs of new parts or machinery, architects had detailed building plans—and costs would pile up for every delay or mistake. “The later you find a problem, the worse it is,” says Lebaredian.
Now, problems are worked out virtually, with a central location for standardized data to be held. There’s still a critical human element: Mapping a facility requires sending a laser scanner strapped to a person running through a factory to capture point cloud data about how everything is arranged. Design engineers also need to create a 3D model of every stage of a car as it’s assembled. This level of detail allows BMW to virtually test the assembly process, complete with simulations of robotics, machines, and even human workers, as BMW has data tracking how long it takes employees to assemble a part.
The main idea is to avoid errors—does that machine even fit there?—but the system also enables optimization, such as moving a rack of components closer to a particular station to save steps for human assemblers. “You can optimize first and gain a lot of efficiency in the first production, and in the construction phase, you have fewer mistakes,” Mayr says. “It’s less error prone.”
Omniverse being a Nvidia platform, AI is naturally next. BMW is already layering in generative AI to help with navigation of its virtual models—they’re so massive that finding a particular point in the digital factory can still require asking a human expert for directions. But the aim is to use AI to optimize production lines too. “Because you have the whole data available, not just for one plant, it will be able to make good suggestions,” says Mayr—lessons learned in one factory could more easily be applied to others.
And then there’s robotics and other autonomous systems. Here, Omniverse can offer a digital space for testing before deploying in the real world, but it can also generate synthetic training data by running simulations, just as driverless car systems are trained with virtual video footage generated by AI. “Real-world experience isn’t going to come mostly from the real world—it comes from simulation,” says Lebaredian.
Aryacetas predicts that the biggest impact from the industrial metaverse will be embodied or physical AI—in other words, robots. “Robots aren’t fully there yet, but they’re rapidly training up to understand the physical world around them—and that’s being done because of these underlying spatial computing technologies,” he says.
The future of the metaverse isn’t avatars in a virtual world; it’s digital twins teaching industrial robots how to step out into the physical one.
2 notes
·
View notes
Text
Setting: a lone typist, NaNoWriMo, works at the centre of the stage, with only the light from the screen and a single light from above illuminating them. As NaNoWriMo types, words in white are projected on a screen behind them so the audience can read.
The typist is about to communicate a policy decision on a controversial topic. Sitting in the open, surrounded on all sides by the audience, NaNoWriMo has not anticipated the fallout of their statement.
NaNoWriMo: [typing] We're not going to police what writers do with AI tools, because we're not capable of enforcing that. It's a bad idea to have rules you can't enforce.
NaNoWriMo: [typing] The event where we aim to write 50k in a month has always been based on the honour system. As we said last year (in an article that we then used ChatGPT output in because we probably thought it was funny), using ChatGPT to write the entire novel would kind of "defeat the purpose of the challenge", yeah? You all know that.
NaNoWriMo: [typing] But yeah, our organization is about overcoming procrastination and perfectionism, so it would be kind of silly to create specific rules that you needed to study in-depth to figure out which automated editing, rephrasing, or brainstorming tools you're "allowed" to use, right? Everyone would just spend the entire month arguing! Better let each participant use their own best judgement instead.
NaNoWriMo: [typing] So policing the tools people use is against our mission and values, which I'm sure everyone understands and we don't need to say explicitly.
NaNoWriMo: [typing] After all, that kind of policing tends to fall hardest on people who are already vulnerable. We want people who are isolated, have less support, have fewer resources, or are dealing with disability to be able to make their own informed decisions about what tools they use. If we have explicit rules about AI, then we might end up with people bandwagoning against our most vulnerable community members.
NaNoWriMo: [typing] Surely, everyone won't immediately leap to the conclusion that we want everyone to use ChatGPT to output their entire novel in five minutes.
NaNoWriMo:
NaNoWriMo: [suddenly stands up, knocking the chair over, and stares blankly at the ceiling for a few moments]
NaNoWriMo: [gives a full-body "whatever" shrug, hits enter on the keyboard, and walks off the stage]
fin.
6 notes
·
View notes
Note
Who in the GG/BB universe do you think play Minecraft?
I hate that I put so much thought into this but it's the weirdest questions that make my brain tism the hardest.
I think it helps to divide them up into subgroups. A lot of them play, but not all of them play the same! Minecraft is a very open game, after all.
Silly Players:
-The Jellyfish have their own group server, For the most part they just have fun building things, exploring and making fun little houses. Nobody get into any scuffles unless someone accidentally punches one of April's 27 tamed wolves
-Sin plays a hint more seriously, just enough to go nuts exploring and trying to find all the cool stuff he can. He likes giving all of his enchanted armor and weapons cool names. He still doesn't know how to deal with creepers outside of screaming and trying to stab it as fast as possible.
-Ramlethal, obviously, has tamed an obscene number of wolves and just wanders from place to place with them. She doesn't even have a sword because as soon as she bonks a mob with a stick the dogs swarm it and kill it for her.
-Dizzy doesn't really know what she's doing but she has a nice little garden and collects all the different kinds of flowers
-Taokaka has done the same, but with cats. She makes little dirt houses to spend the night in and then immediately forgets where she put her bed. She's trying to actually play but keeps getting distracted
-Makoto is on a quest to have a dyed sheep of every color. If you ask why she doesn't have an answer, but she's very passionate about it
-Noel is so scared of the game but she's being very brave about it. She built her house in a bamboo grove so she lives nearby the pandas. Tsubaki goes to the nether to get stems and glowstone for her because she's too scared to go herself.
-Arakune has made himself a house of wool, concrete and terracotta. Everything is dyed azure. He is living the dream.
-Nagoriyuki is currently level 233. He does nothing but fish and farm potatoes. Once he fished up a sword with five different enchantments on it, but he never uses it
Serious Players
-As far as Answer is concerned, Minecraft is not a game. It is a tool for beta-ing ECK settlements in excruciating detail. Chipp tried introducing it to him as a fun game to play during downtime but it did not work.
-Bedman constructs world landmarks in precise one-to-one scale. It's kind of amazing to just let him go at it, he'll work for hours straight and spend weeks to make a perfectly detailed facsimile of the Roman coliseum.
-Tager, when not accidentally breaking keyboards, is making giant detailed boats. He currently has them organized by size, country of origin, and year of original construction.
-Kokonoe got really into Minecraft for about two and a half weeks, after building a bunch of automated systems to produce and sort more resources than anyone would ever need she immediately got bored and quit.
-Carl builds incredibly elaborate contraptions that are impressive but tend to explode
-Axl heads off into a mineshaft and gets lost for a week. He's having a great time, except for the part where the Warden showed up and threw him into a wall. He likes the music players
-Faust digs perfectly chunk-sized holes in patterns then proceeds to make floating cubes out of the cobblestone and miscellaneous rocks. Apparently he finds it calming, though he tries to limit his screentime to avoid eyestrain.
-Kagura has convinced himself that slaying the Enderdragon is something girls will find cool. He doesn't actually know how to get to the End. He does have a very cool set of enchanted armor and a fancy house (mostly built by Hibiki)
26 notes
·
View notes
Text

Technology never stands still, and software updates are a crucial part of keeping our devices secure, efficient, and packed with new features. The latest updates for Windows, macOS, iOS, and Android have brought a wave of improvements and innovations. Whether you’re a business professional, a tech enthusiast, or an everyday user, staying informed about these updates ensures that you make the most of your devices. Let’s dive into the latest developments across the major operating systems!
Windows: The Evolution Continues
Microsoft's Windows operating system continues to evolve, with its latest update focusing on performance, security, and AI integration. The company has been investing heavily in AI-powered tools, bringing efficiency and automation to everyday computing tasks. Windows remains the dominant operating system for businesses and professionals due to its flexibility, compatibility, and extensive software ecosystem.
Key Updates in Windows:
Copilot AI Integration: Windows has embedded AI-powered features to assist with tasks like document summarization and smart recommendations, making workflow automation seamless.
Enhanced Security: Advanced phishing protection, ransomware mitigation, and cloud-based security improvements make Windows safer than ever.
Taskbar & Start Menu Enhancements: Users can now customize their taskbar and Start Menu with increased flexibility, allowing a more personalized experience.
Gaming Optimization: Auto-HDR, Direct Storage, and latency reduction technology enhance gaming performance on Windows devices.
Seamless Android Integration: Improved support for Android apps via the Microsoft Store allows better cross-device experiences.
Better Virtual Desktop Management: New features enhance multitasking and organization, making it easier to switch between work and personal desktops.
Improved Multi-Monitor Support: Enhancements for better handling of multiple displays increase productivity for professionals using multi-screen setups.
Cloud-Based Backup and Sync: Windows now offers more robust cloud integration, ensuring that files and settings remain consistent across devices.
Why Upgrade?
If you're looking for better efficiency, security, and AI-powered assistance, the latest Windows update is a must-have. Businesses can particularly benefit from improved automation, enhanced security measures, and more seamless device integrations that enable remote and hybrid work setups.

macOS: A Blend of Performance and Productivity
Apple’s macOS has introduced new features that enhance user experience, security, and productivity. The latest update focuses on seamless integration with Apple’s ecosystem, improved AI capabilities, and better energy efficiency. Mac users enjoy a refined and intuitive user experience, making it a preferred choice for creative professionals and developers.
Key Updates in macOS:
Refined UI & System Performance: Smoother animations, more responsive applications, and better battery efficiency provide an enhanced user experience.
Continuity Upgrades: Improved Handoff between Mac, iPhone, and iPad makes workflows seamless, enabling users to transition between devices effortlessly.
Password & Security Boosts: Stronger encryption, multi-layered authentication, and autofill enhancements ensure better security.
Universal Control Enhancements: Mac users can now use a single mouse and keyboard to control multiple Apple devices with greater precision.
Better Gaming Experience: Apple Silicon-powered Macs now support more AAA games with improved MetalFX, making macOS more gaming-friendly.
Improved Automation Features: New tools streamline repetitive tasks, improving workflow automation for enterprises and small businesses.
Better Cloud Integration: Enhanced iCloud capabilities allow users to manage and sync data more efficiently across Apple devices.
Optimized Video Conferencing Tools: New enhancements to FaceTime and third-party conferencing apps improve communication for remote workers.
Why Upgrade?
For those invested in Apple’s ecosystem, this update enhances the overall experience while improving efficiency and security. The AI-powered automation tools embedded in macOS further elevate business productivity, making it easier to streamline repetitive tasks and optimize workflows.
Apple's iOS
update has brought a host of new features,focusing on personalization, security,and AI-driven enhancements.iOS continues to provide a smooth and reliable mobile experience, integrating cutting-edge technology for both personal and professional use.
Key Updates in iOS:
Interactive Widgets: More powerful widgets that allow direct interaction and better usability.
Lock Screen Customization: Users now have more control over lock screen aesthetics and functionality.
Smarter Siri & AI Features: Improved Siri responses, better AI-powered suggestions, and enhanced voice recognition.
Better Privacy Controls: Enhanced app tracking protection and email privacy features offer greater security.
New Messaging Features: Edit sent messages, improved FaceTime functionalities, and a better user interface for iMessage.
Advanced Automation Features: Businesses can now leverage AI-powered automation tools to optimize workflow processes within mobile applications.
More Efficient Battery Management: Intelligent battery optimizations extend device lifespan and improve overall power efficiency.
Cross-Device Collaboration: Enhanced AirDrop and Continuity features make working across Apple devices even more seamless.
Why Upgrade?
From security to personalization, iOS offers a smoother, smarter experience for iPhone users. Businesses using iOS-powered mobile applications can benefit from enhanced automation features, making iPhones even more integral to modern work environments.
Android: More Control, More Efficiency
Google’s Android update continues to refine user control, security, and customization. Android remains the top mobile operating system, providing users with a highly customizable and versatile experience across a wide range of devices.
Key Updates in Android:
Material You UI Enhancements: More customization options for widgets and themes, making Android devices more visually appealing.
Smarter Battery Optimization: AI-driven power management ensures longer battery life and better device performance.
Privacy Dashboard: A centralized space to monitor app permissions and usage.
Advanced AI Features: Smarter voice recognition, contextual assistance, and improved Google Assistant capabilities.
Seamless Cross-Device Experience: Better compatibility with tablets, wearables, and smart home devices.
AI-Powered Automation Tools: New features optimize business processes, allowing enterprises to automate customer interactions and workflows
Better Multitasking Features: Enhanced split-screen and picture-in-picture support for productivity applications.
5G Optimization & Network Improvements: Faster and more reliable connectivity, making Android devices more future-proof.
Why Upgrade?
For Android users, the latest update provides greater control, security, and seamless integration across devices. Businesses relying on Android applications can take advantage of AI-powered automation tools to enhance efficiency, making Android devices even more powerful for professional use.

How KSoftTechnologies Enhances Your Digital Experience
At KSoftTechnologies, we specialize in helping businesses adapt to evolving technologies. Our expertise in automation solutions for small businesses, process automation services, and custom software development with AI ensures seamless digital transformation. Whether you need business automation consulting, workflow automation for enterprises, or AI-powered automation tools, we provide end-to-end software implementation that drives efficiency and productivity.
Why Choose KSoftTechnologies?
Customized AI Solutions: We build tailored AI-driven software to automate workflows and optimize performance.
Expert Business Automation Consulting: Our team provides strategic guidance to improve operational efficiency.
Seamless Software Implementation: From analysis to deployment, we ensure smooth automation solutions for businesses.
Cross-Platform Optimization: Our solutions are designed to work seamlessly across Windows, macOS, iOS, and Android.
Continuous Support & Maintenance: We offer dedicated support to keep your business running smoothly.
Conclusion: Should You Update Now?
Updating your operating system ensures better security, improved performance, and access to the latest features. Whether you use Windows, macOS, iOS, or Android, staying up-to-date allows you to experience cutting-edge advancements in technology. Check your device settings for updates and take advantage of these new enhancements today!
For businesses looking to optimize processes, KSoftTechnologies offers cutting-edge automation solutions to help you stay ahead in the digital world. Contact us to explore how we can streamline your operations with innovative technology!
#app development services#erp development#web and mobile app development company#digital consulting#android native mobile development#ecommerce website development company#custom erp
1 note
·
View note
Note
Would you say that a midi piano is needed when composing music? I'm still pretty new to this (only got a couple of rough tracks done) and have been on the fence on whether I should get a midi piano so I thought I'd ask
There is no answer to this question unfortunately, as it really comes down to how YOU work best.
I can talk about my own workflow, and where having a MIDI piano is helpful to me; whether one will be helpful to you depends a lot on your particular workflow, comfort level with the piano, expertise, etc.
For me, I actually start composing in MuseScore first (aka by writing it out in Western notation). I find it easiest to write that way, especially when it comes to doing cool things with rhythm and counterpoint. So I'll write it in notation first and then export MIDI from there, and then use that MIDI in my DAW to flesh it out into something more. A lot of people don't do this but they compose by "playing" into the DAW directly with a MIDI keyboard; in that case the keyboard would be invaluable.
At the DAW stage, however, I do find the keyboard useful. I use it in two ways:
- if it feels like something is missing, I might set the track on loop and "play" to it with the keyboard, and then once I figure out what's missing I'll use the keyboard to record the new part. If you have a non-MIDI instrument (including your voice) you can just as well do this by layering a recording on top instead - I do this with cello often. But the MIDI keyboard can help if you want to just record a part and mess with instrumentation later, and I also use it to bang out percussion parts sometimes.
- it really, really makes a difference if I actually "perform" the MIDI especially for melodic parts. So I will sometimes use the MIDI keyboard to record myself playing a part, instead of using the perfect performance exported from MuseScore. You can get the same effect by doing lots of detail work by editing the MIDI itself: nudging notes before or after the beat, changing velocities, modifying lengths. So a keyboard isn't strictly necessary. However if you're proficient at it, it's generally faster to play it in and then tweak it than doing all of the modifying in the piano roll. Up to you though!
Now there's one thing that a proper MIDI keyboard (as in not mine which is just an electric keyboard from like 1998 that has MIDI out, but no CC's) can really help with: recording "performances" of synth parameters. Currently I do that entirely by just adding automation manually and playing it back to see how it sounds, but playing with knobs and sliders live can really help make working with synths faster in the same way playing the notes in makes humanizing a MIDI part faster.
Anyway, I know I didn't actually answer your question, but hopefully this has given you some idea of how a MIDI keyboard might help and where in a composer's workflow it might be of use. If I'm honest my teachers in grad school tried so hard to get me to use my keyboard more, and it wasn't until I ignored them and started writing in MuseScore that I ended up writing music I liked better. So it's all personal preference and if I told you definitively yes or no I feel like I'd be doing a disservice.
It's a great tool, but only if you think you'd use it. Good luck, try stuff, see what works, and keep making music! There is no "right" way to create.
7 notes
·
View notes
Text
189: The Haxan Cloak // Excavation

Excavation The Haxan Cloak 2013, Tri Angle (Bandcamp)
Through his work as the Haxan Cloak and as a film composer (notably on a couple of Ari Aster pictures), Bobby Krlic has helped define the modern aesthetics of what we might call Upsetting Music:
Extremely low frequency synthesized bass with a subliminal roar
Slow, deliberate, violent industrial percussion with a ton of reverb
Creepy whirring noises that simultaneously evoke machinery and insects
Staticky, panned whooshing sounds, that suggest rapid movement captured on degraded video tape
Piercing whines, reminiscent of alarms or the shrill violin notes exploited in scores like Psycho
Snippets of higher pitched noises that sound like muffled or glitched recordings of human cries
youtube
Unlike traditional symphonic scores or even the kind of throbbing but ultimately melodic progressive electronic stuff used in ‘80s horror scores, this music largely eschews melody in favour of manipulating sounds to provoke a visceral sense of unease as directly as possible. Electronic music made its initial inroads into horror in the late ‘70s largely because it was cheap to produce, but the runaway success of independent/low-budget films with keyboard-heavy scores like John Carpenter’s Halloween made the aesthetic popular. Since then, genre film has continued to evolve alongside the darker strains of electronic music, from schlocky early ‘90s flicks that incorporate techno and horrorcore rap, to the way industrial became de rigueur for a certain variety of desaturated, nihilistic, almost fetishy brand of cheap ‘00s torture flick.
Independent of this history though, I think there’s something specific about recent horror and thriller filmmakers’ embrace of dark ambient/drone music like Krlic’s that links to Western contemporary anxieties and how these audiences experience fear. I remember many years ago (I’m 51) reading an article in a film theory class about how the rise of automation in the early 20th century kicked off a minor craze in the newspapers of the day for grisly stories about bodies being maimed by trams and the like. The author argued that these sorts of accidents were a new form or vector of terror specific to the industrial age, and that there was a corresponding spike in depictions of these tragedies in contemporaneous films, which tended to pull their subject matter and aesthetics from the well of public worries. Genre music has evolved along parallel lines. Traditional orchestral horror scores derive from ominous motifs found in classical music and opera, which reflect older notions of how evil and despair should be depicted—a Christian understanding of evil, with attendant tropes. A world mediated by religion and versed in devotional music (masses, hymnals, Gregorian chant) would naturally imagine Satanic music as its inversion (dark, baroque renditions of the religious cannon) or opposite (“primitive” tribal music).
By the middle of the century a secularized notion that evil might derive from the personal psychoses of individuals, or (as the tram reading suggested) the indifference of technology and institutions, became widespread, and was duly reflected in the cinema. Today, in the West anyway, our bodies are more insulated than ever before from daily exposure to the sorts of violence depicted in horror films, and our fears have become more secularized and more abstracted still. Our most immediate experiences of dread and bodily harm have tended to come from what we witness on our screens, the fear of seeing something troubling. At the same time, filmmakers have realized that the sonically unsettling aspects of ominous symphonic music (extreme high and low frequencies; disharmony; jerky rhythms) could be divorced from the orchestral context, leaving artists with a set of specific tools for physically startling audiences in tandem with the action onscreen.
Krlic’s music is a product of these parallel processes. As noted, much of his work prioritizes psychological and physiological effect above all, pushing these notions (in his Haxan Cloak work especially) about as far as they can be taken outside of extremist genres like harsh noise and powerviolence. When he makes his synths literally growl, our bodies respond to the perceived threat, even though we know what we’re hearing isn’t produced by a living animal. Some of what he’s exploiting, again, is stuff that goes back to our base threat-detecting instincts, but the overtly technological aspect is also the sound of horrible things both real and simulated we’ve seen through media. Staticky screams and the scrape of metal on concrete summon the spectre of snuff films, hostage videos, extreme BDSM porn, war footage, and all of the movies, video games, and music videos that have adapted their imagery to get a rise out of people. It also, especially to a broad subset of “average” moviegoers, sounds like the type of music people who want to rape and murder your family would listen to for kicks.
youtube
There is a good deal more going on in Krlic’s music than simple fearmongering though—we can look at Excavation, his second and final LP to date as the Haxan Cloak,as part of a long lineage stretching from ‘60s experimental electronic music like White Noise through Nurse with Wound, Aphex Twin, and Nine Inch Nails among many others. “The Mirror Reflecting (Part 2)” eventually reveals a sequence of austere, crystalline guitar-like sounds that post-metallers Agalloch might’ve produced; “Dieu” opens with some subterranean breakbeats and chopped up samples that nearly threaten to look in the direction of a dancefloor before a creepy violin quells the thought; the rain-drenched “The Drop” flashes a bit of a Baths-style emo/downtempo vibe when it isn’t trudging past the sounds of dark satanic mills. Just as some people will hear Excavation as sadistic junkie music, others will no doubt find it an exceedingly warm and plush casket to disappear within, the overwhelming weight of its sounds divorced of violent associations, just signals strobing across the darkened hemispheres.
189/365
#the haxan cloak#bobby krlic#ari aster#a24#horror movies#horror music#halloween music#halloweek#dark techno#dark ambient#electronic music#'10s music#music review#vinyl record
5 notes
·
View notes
Text
Demystifying Python: Exploring 7 Exciting Capabilities of This Coding Marvel
Greetings aspiring coders! Are you ready to unravel the wonders of Python programming? If you're curious about the diverse possibilities that Python offers, you're in for a treat. Let's delve into seven captivating things you can achieve with Python, explained in simple terms from the best Python Training Institute.

1. Craft Dynamic Websites:
Python serves as the backbone for numerous websites you encounter daily. Utilizing robust frameworks such as Django and Flask, you can effortlessly fashion web applications and dynamic websites. Whether your ambition is to launch a personal blog or the next big social platform, Python is your reliable companion. If you want to learn more about Python from the Beginner to Advance level, I will highly recommend the best Python course in Bangalore
2. Automate Mundane Tasks:
Say goodbye to repetitive tasks! Python comes to the rescue with its automation prowess. From organizing files to sending emails and even extracting information from websites, Python's straightforward approach empowers your computer to handle these tasks autonomously.
3. Master Data Analysis:
For those who revel in manipulating numbers and data, Python is a game-changer. Libraries like NumPy, Pandas, and Matplotlib transform data analysis into an enjoyable and accessible endeavor. Visualize data, discern patterns, and unlock the full potential of your datasets.
4. Embark on Game Development:
Surprising as it may be, Python allows you to dip your toes into the realm of game development. Thanks to libraries like Pygame, you can bring your gaming ideas to life. While you may not be creating the next AAA blockbuster, Python provides an excellent starting point for game development enthusiasts.
5. Explore Artificial Intelligence:
Python stands out as a juggernaut in the field of artificial intelligence. Leveraging libraries such as TensorFlow and PyTorch, you can construct machine learning models. Teach your computer to recognize images, comprehend natural language, and even engage in gaming – the possibilities are limitless.
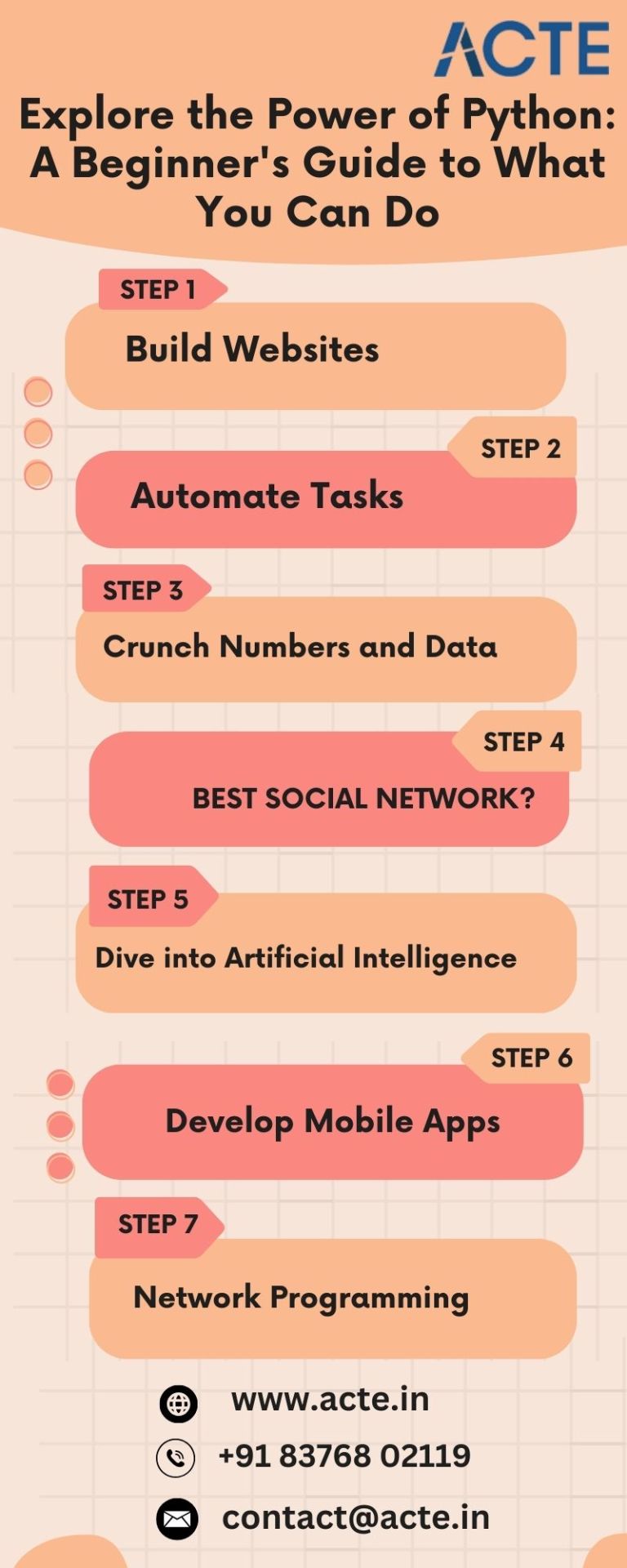
6. Craft Mobile Applications:
Yes, you read that correctly. Python empowers you to develop mobile applications through frameworks like Kivy and BeeWare. Now, you can turn your app concepts into reality without the need to learn an entirely new language for each platform.
7. Mastery in Network Programming:
Python emerges as your ally in the realm of networking. Whether you aspire to create network tools, collaborate with APIs, or automate network configurations, Python simplifies the intricacies of networking.
In essence, Python can be likened to a versatile Swiss Army knife for programmers. It's approachable for beginners, flexible, and applicable across diverse domains. Whether you're drawn to web development, data science, or AI, Python stands as the ideal companion for your coding journey. So, grab your keyboard, start coding, and witness the magic of Python unfold!
2 notes
·
View notes
Text
I have had the pleasure of teaching gen Z co-workers on how to do certain processes/use certain technology and this absolutely tracks. 95% of the time, it's really not the case that they're lazy, or don't want to learn. It's mainly the case that they haven't either been taught it, or their "technology environment" hasn't involved having to use various desktop systems that many businesses use, or that even late millennials like me use. I was lucky in that I grew up messing around with, and using, a lot of the tools necessary for me to do my old job reasonably well.
- Want to make a god-awful Sonic the Hedgehog sprite-comic to impress your 10 year old class-mates because you think it makes them laugh? Get good at using Microsoft Publisher, sprite editing using Microsoft Paint, GIMP , and "surfing the web" on that new-fangled Google thing to find all the fan-forums where people are ripping sprites.
- Want to calculate the best trade routes in an online 18th century trading MMO? Want to calculate the right formula to make that Garry's mod automated rocket launching system? Excel/LibreOffice Spreadsheets. Spreadsheets for days, and you can use the formula system to MASS PRODUCE the numbers. It's like goddamn magic, (except when you mass produce the errors, and your whole model falls apart). - Want to print a giant geological map? Get used to the nightmare that is a large A0 plotter, learning about trim and bleed sizes and essential maintenance. Get ready to cry at the price of an ink cartridge. Get ready to scream as the several-foot long map is printed at an A3 size, on an A0 page, because you forgot to adjust one of the two sets of internal Windows vs printer driver settings.
Even using a desktop computer. You might have guessed I'm a massive computer nerd. It makes it so much easier to do a wide variety of jobs knowing how to use shortcuts, having a high wpm keyboard typing speed and being able to automate parts using auto-hotkeys and other programming tricks. The Gen-Z workers I had to teach often had less experience with desktop computing, and are mainly mobile-native. It's no surprise they aren't familiar with these systems which many I knew grew up with, and use as readily as breathing in some cases. But they did learn - and they did pick it up when they tried, and failed, to use them over and over again. Just as I did growing up in lower-stakes situations. Computing and IT classes, in my opinion, MASSIVELY waste the time of children as they are often (at least in the UK) viewed as non-important by schools and parents attempting to game the University selection system. This is typically picked up on by the kids as well, who then use them as an excuse to mess around (Though sometimes learning key skills in the process, such as running N64 emulators!). While I did learn to use practical computer skills, such as Microsoft Office, during my early education, most of what I know is self taught. I enjoyed it - and made practical use of it. What happens to the people who didn't? Gen-Z. And then we pillory them for it. Computing should be given the respect it deserves in the curriculum - both for the functional, practical, elements and for the sheer, utter, magic of the machine itself.
seriously, though. i work in higher education, and part of my job is students sending me transcripts. you'd think the ones who have the least idea how to actually do that would be the older ones, and while sure, they definitely struggle with it, i see it most with the younger students. the teens to early 20s crowd.
very, astonishingly often, they don't know how to work with .pdf documents. i get garbage phone screenshots, sometimes inserted into an excel or word file for who knows what reason, but most often it's just a raw .jpg or other image file.
they definitely either don't know how to use a scanner, don't have access to one, or don't even know where they might go for that (staples and other office supply stores sometimes still have these services, but public libraries always have your back, kids.) so when they have a paper transcript and need to send me a copy electronically, it's just terrible photos at bad angles full of thumbs and text-obscuring shadows.
mind bogglingly frequently, i get cell phone photos of computer screens. they don't know how to take a screenshot on a computer. they don't know the function of the Print Screen button on the keyboard. they don't know how to right click a web page, hit "print", and choose "save as PDF" to produce a full and unbroken capture of the entirety of a webpage.
sometimes they'll just copy the text of a transcript and paste it right into the message of an email. that's if they figure out the difference between the body text portion of the email and the subject line, because quite frankly they often don't.
these are people who in most cases have done at least some college work already, but they have absolutely no clue how to utilize the attachment function in an email, and for some reason they don't consider they could google very quickly for instructions or even videos.
i am not taking a shit on gen z/gen alpha here, i'm really not.
what i am is aghast that they've been so massively failed on so many levels. the education system assumed they were "native" to technology and needed to be taught nothing. their parents assumed the same, or assumed the schools would teach them, or don't know how themselves and are too intimidated to figure it out and teach their kids these skills at home.
they spend hours a day on instagram and tiktok and youtube and etc, so they surely know (this is ridiculous to assume!!!) how to draft a formal email and format the text and what part goes where and what all those damn little symbols means, right? SURELY they're already familiar with every file type under the sun and know how to make use of whatever's salient in a pinch, right???
THEY MUST CERTAINLY know, innately, as one knows how to inhale, how to type in business formatting and formal communication style, how to present themselves in a way that gets them taken seriously by formal institutions, how to appear and be competent in basic/standard digital skills. SURELY. Of course. RIGHT!!!!
it's MADDENING, it's insane, and it's frustrating from the receiving end, but even more frustrating knowing they're stumbling blind out there in the digital spaces of grown-up matters, being dismissed, being considered less intelligent, being talked down to, because every adult and system responsible for them just
ASSUMED they should "just know" or "just figure out" these important things no one ever bothered to teach them, or half the time even introduce the concepts of before asking them to do it, on the spot, with high educational or professional stakes.
kids shouldn't have to supplement their own education like this and get sneered and scoffed at if they don't.
24K notes
·
View notes
Text
Server 360 Form Filling Auto Typer Software| Form Filling Auto Typing Software
Hey everyone! Today, let’s talk about something that can completely change your data entry game — the Online Server Form Filling Auto Typer Software. So here’s the deal — the Server 360 data entry company provides a platform where you need to log in and complete 1,500 forms in just 15 days. These forms include both text and image data that you have to manually type into the given fields. Now we all know — typing out 1,500 forms manually in just 15 days is tough. It’s time-consuming, stressful, and prone to human errors. That’s exactly why Instant Data Services has developed a powerful solution — the Form Filling Auto Typer Software. 🎯 This automation tool is specially designed to work with the Server 360 platform, making your job smoother, faster, and more accurate. ✅ Using our Server Auto Form Filler Software, you can finish your entire data entry workload well within the deadline, while maintaining high accuracy — and that means better payouts for you. 👉 The software works using keyboard keystrokes — smartly simulating manual typing — so it's 100% non-detectable by any server checks. 🔹 No detection risk 🔹 No errors 🔹 No stress 🔹 Just simple, smooth, automated typing
youtube
Instant Data Service Email us : [email protected] Contact Us :+91 891 950 8962 Website:- http://formfillingautotyper.com/ http://instantdataservices.com/ https://autoformfillingsoftware.com/ https://medicalformfillingautotyper.com/ https://autoformfillingsoftware.com/mi-demography-form-filling-automatic-software https://medicalformfillingautotyper.com/medical-form-filling-auto-typer-software
0 notes
Text
Why Web Accessibility Should Be a Priority for Every Business
In the fast-growing digital world, it’s easy to get caught up in trends like design, SEO, and speed optimization. But one critical aspect often gets overlooked, web accessibility.
Making your website accessible isn’t just about ticking a legal box. It’s about creating an inclusive online experience where everyone, including people with disabilities, can interact with your site without barriers.
What is Web Accessibility?
Web accessibility refers to the design and development of websites, tools, and technologies so that people with disabilities can use them. This includes individuals with visual, auditory, motor, or cognitive impairments.
Accessibility ensures that everyone can navigate, understand, and interact with digital content, whether using a screen reader, keyboard-only navigation, or other assistive technologies.
Why It Matters for Your Website
Ignoring accessibility means alienating a large group of users and potentially exposing your business to legal risks. Countries around the world are adopting strict digital accessibility laws, and failing to comply can lead to lawsuits or fines.
But beyond regulations, it’s a matter of ethics and user experience. When your website is accessible, you're simply opening doors for more people to connect with your brand.
Making Accessibility Easier with Tools
You don’t have to start from scratch. There are tools and platforms available today that simplify the process of making websites accessible.
Here's a solution, Accesstive, which helps automate and monitor accessibility features for your website. It’s designed to align with global standards and assist in improving compliance without compromising design or functionality.
Conclusion
Web accessibility is no longer optional, it’s essential. Businesses that prioritize it are not only protecting themselves legally but also building better relationships with all users.
Whether you're a startup or an established brand, investing in accessibility shows that you care about inclusion, diversity, and providing equal access to your digital space.
1 note
·
View note