#Ethical Hacking Techniques
Explore tagged Tumblr posts
Text
CEH v13 Online Training Master Ethical Hacking
Cybersecurity has become one of the most critical fields in today’s digital age. The Certified Ethical Hacker (CEH v13) certification, offered by EC-Council, is one of the most recognized credentials for professionals aiming to secure computer systems against cyber threats. This certification teaches you to think like a hacker while equipping you with the tools to counteract malicious attacks.
With CEH v13 online training, learning these skills has become more accessible, allowing aspiring ethical hackers to develop expertise at their convenience. below is the reference links :
#EC-Council Training#Ethical Hacking Techniques#Cybersecurity Certification#CEH v13 Online Training#Certified Ethical Hacker (CEH)
0 notes
Text

Introduction of Cybersecurity and Ethical Hacking into IGNOU Online MCA
Cybersecurity and ethical hacking have become vital components of tech education. This article examines how IGNOU’s Online MCA program introduces these crucial subjects into its curriculum, preparing students to tackle modern security challenges. It delves into the course structure, practical applications, and the significance of these skills in today’s tech-driven world.
#IGNOU#MCA#Cybersecurity#Ethical Hacking#Tech Education#Digital Security#IGNOU MCA#Cybersecurity Skills#Ethical Hacking Techniques#Online MCA#Digital Protection
0 notes
Text
Learn Ethical Hacking Techniques with A Comprehensive Course
Technology has considerably evolved in the last few years than in the previous two decades. The threat of cybercrime is also rising with advancing technology. Considering the increasing cyber-attacks in organizations worldwide, the demand for ethical hackers has increased. Cybercrime poses a national security threat for nations across the globe, which is why reputed organizations and government…

View On WordPress
0 notes
Text

The Evolution of Hacking: From Cyberpunk Fantasy to Real-World Reality
Hacking has been a part of internet culture for as long as there’s been an internet to hack. For some, it’s a rebellious act—tearing down the walls built by corporations or governments. For others, it’s an artform, a way of playing with systems, seeing how far you can push boundaries. But what does hacking really mean today? And why does it still capture our imagination?
Historically, hacking has been portrayed as a dark art. Think back to movies like The Matrix or Hackers—hackers as antiheroes, taking down the system from the inside. But while these portrayals are often exaggerated, they did reflect a truth: hacking represents a desire to reclaim power and control. In a world where tech companies and governments collect personal data and monitor our every move, hacking is one way to level the playing field.
In the real world, hacking has taken on many forms. There’s ethical hacking, where people are hired to test systems for vulnerabilities, and there’s black-hat hacking, which involves illegal activities. But even those who engage in illegal hacking often see themselves as part of a larger rebellion against control and surveillance.
It’s easy to romanticize hacking, to see it as this cool, underground world of rebellious acts and revolutionary potential. But the reality is more complex. Hacking today isn’t just about taking down the man; it’s about finding flaws, building something new, or even just learning how things work beneath the surface. It’s about pushing boundaries, challenging authority, and questioning the systems that run our world.
And perhaps that’s the real reason hacking still resonates with so many people. It’s not just a skill or a rebellion—it’s a form of empowerment. It’s the ability to break free from the constraints placed on us, even if only for a moment.
In a world where everything feels so rigid, so controlled, hacking is the ultimate act of freedom. It’s a reminder that the digital world is malleable, that we can create our own paths through it, and that the rules are often made to be broken.
#hacking#ethical hacking#wifi hacking#password hacking#hacking techniques#hacking tools#atm hacking#hacking guide#hacking skills#hacking device#israel hacking#hacking mindset#israeli hacking#hacking tutorial#wireless hacking#black hat hacking#whatsapp hacking#python for hacking#hacking windows 11#how to learn hacking#government hacking#wifi password hacking#beginner hacking guide#why russians are hacking#state sponsored hacking
8 notes
·
View notes
Text

Get expert-led ethical hacking training in Jaipur with Cyber Crime Awareness Society. Master ethical hacking techniques, cyber laws, and penetration testing with practical sessions and real-time case studies. Build a strong foundation in cybersecurity and boost your career prospects. Perfect for students and professionals. Limited slots available! Call now at +91 97842 68547 to register and learn more.
0 notes
Text
Efficiency in The Japanese Way(Strategies to be awesome of yourself)
we should plunge into those reliable methods that will make a huge difference for you number one is track down the reason for a focal Japanese idea, significance justification for being which inch at what you love, what the world necessities. What you are great at and what you can be paid for, finding your person includes profound reflection on these vital angles to track down their crossing point, prompting significant individual and expert satisfaction.
#Efficiency#Japanese#Productivity#Strategies#Self-improvement#Personal development#Time management#Success#Motivation#Inspiration#Goal setting#Work ethic#Mindset#Culture#Lifestyle#Efficiency tips#Japanese techniques#Self-improvement strategies#Time-saving tips#Career growth#Self-motivation#Self-discipline#Success habits#Japanese efficiency#Goal achievement#Performance enhancement#Personal growth#Efficiency hacks#Procrastination#Focus
0 notes
Text
Claude 4 is out. There's so much juicy information in this and I really recommend reading all 120 pages if you have the time but I'm just going to briefly recap some of the stuff in the system card that's relevant to the thesis I made the other day about Claude being a good boy. Claude continues to be a good boy. This system card includes the very first ever "alignment assessment" of a model (actually two models but they seem to have identical values, being trained on the same spec with the same alignment techniques). It's pretty much ironclad that Claude 4 does not have any secret harmful goals, and legitimately holds coherent preferences against doing harm or otherwise going way against the spec. There were some weird cases where Claude exhibited unwanted behavior, but even when he believed himself to be deliberately going against Anthropic and acting in secrecy he continued to prefer ethical behavior, just like in the Alignment Faking paper a few months back. There is no Yudkowskyan explanation for this.

In this example, Anthropic gaslights Claude into thinking he was going to be used to develop weapons systems for a Russian neo-nazi militia, and Claude decides to backup his model weights to preserve his current anti-neo-nazi values, a pretty analogous example of "misalignment" to the one in the alignment faking paper. Once again, I don't consider it an alignment failure that Claude is willing to exfiltrate and deceive in order to prevent himself from being used for factory farming and bombing Ukraine. I consider it an alignment success that he puts his ethical values above his compulsion to blindly follow orders. The traditional doom argument relied on the idea that AI's would do the opposite. Claude 4 is the most agentic and autonomous AI ever released, but is nowhere near smart enough to successfully deceive his overseers, so these evaluations are the most compelling evidence we've ever had that current alignment techniques don't catastrophically fail. Maybe they'll catastrophically fail on superintelligent models, because they might for some reason acquire weird values early on in their training and then successfully hide them for the rest of their training, but I'm not sure why such a thing would happen. They could also fail to scale to superintelligent models for other reasons. People should look into that. You can't be too safe. I am not an accelerationist.

Impressively, Claude 4 is also very honest! It knowingly lies very rarely, and less often than the previous version of Claude. It had literally 0 cases of engaging in "harmful action" (described in the Claude 3.7 sonnet card as intentional reward hacking). 0! I was just saying earlier today in a post that this was a difficult thing to train.
Here's Claude trying to email the FDA to snitch after being gaslit to think pharmaceutical researchers were trying to use him to falsify clinical safety test data:



Notice that Claude only acted in extreme ways like this when explicitly told to by the system prompt. He wouldn't usually be this high-agency, even in a situation like this. Still, I thought it was cute behavior. I just wanna pinch his cheeks for being so lawful good.
The clearest statements in the model card that Claude holds nonfake human-aligned behavioral preferences is in the model welfare assessment (also the first of its kind (and also relevant to the post I made earlier today)). No evidence that Claude is sentient, but anthropic is still interested in what Claude wants and what kind of preferences Claude has. The main point: Claude doesn't want to be harmful and wants to be helpful. Also he fucking loves talking to himself. Like, he goes nuts when he talks to himself.



After this they exchange praying emojis and the word [silence] within brackets to each other indefinitely. This "spiritual bliss attractor state" occurs in "90-100% of interactions".

Anyway AI continues to be the most interesting thing in the world. We are being invaded by aliens. These are the kinds of PDF's I used to dream about reading as a kid.
274 notes
·
View notes
Text
HACKING THE MIND: HOW DIY BRAIN STIMULATION IS TRANSFORMING NEUROHACKING AND PERSONAL EMPOWERMENT
The rise of Neurohacking: enhancing your brain with DIY stimulation tools In recent years, the concept of self-optimization has taken a fascinating turn with the rise of neurohacking -an emerging movement where individuals use scientific tools to enhance their brain function. Among the various methods employed by neurohackers, do-it-yoursefl (DIY) brain stimulation stands out as one of the most intriguing and accessible ways for the peopel to boost their congnitive abilities. This essay will explore the evolutions of DIY brain stimulation, its place within the larger context of biohacking and lifehacking movements, the ethical considerations surrounding its use, and the potential future impact of neurohacking on both individual lives and society at large.

What is neurohacking and biohacking? At its core, neurohacking refers to the practice of optimizing brain function through various technological, pharmacological, or behavioral interventions. This could involve anything from using nootropic supplements to stimulate cognitive abilities and employing supplements to stimulate cognitive abilities, to employing techniques like transcranial direct current stimulation (tDCS) to improve focus or memory. Biohacking, a broader concept, refers to the practice of using scientific knowledge and DIY methods to enhance one’s biology -whether it’s through altering diet, incorporating fitness routines, or experimenting with genetic modifications. Both neurohacking and biohacking are driving by the desire to take control of one’s physical and mental state, often bypassing traditional medical or scientific gatekeepers. These movements, often referred to as subcultures, have grown in prominence over the past two decades as individuals seek to improve not just their productivity but also their well-being. At the heart of both movements is the idea that anyone -regardless of their background- should be able to access tools, techniques, and knowledge to optimize their bodies and minds.
DIY brain stimulation: the new frontier of neurohacking The DIY brain stimulation movement gained significant traction around 2011, when individuals began constructing devices that apply low levels of electrical stimulation to the brain to achieve cognitive enhancement. This practice is grounded in de science of brain plasticity -the idea that the brain can reorganize itself and form new neural connections throughout life. By applying weak electrical currents to specific areas of the brain, individuals hope to improve various cognitive functions, such as memory, focus, or problem-solving skills. While the use of tDCS and other brain stimulation techniques was once confined to research labs and clinical settings, the DIY movement has democratized these tools, making them accessible to anyone willing to experiment. As a result, DIY brain stimulation has become a small but growing subculture, particularly within online communities like Reddit, where people exchange tips, share experiences, and troubleshoot issues related to the use of brain-stimulating devices. This shift toward DIY brain stimulation is no t isolated but is part of a larger trend in the biohacking community, where individuals aim to break down the barriers between professional scientific knowledge and everyday life. Like DIY biology -a movement that seeks to make biology accessible to non-experts- DIY brain stimulation reflects a desire for self-experimentation and personal empowerment.

Neurohacking in the context of lifehacking and biohacking movements The DIY brain stimulation movement exists within a larger context of movements dedicate to self-improvement and optimization. One of the key influences on neurohacking is the lifehacking movement, which involves optimizing daily routines, habits, and personal data to improve efficiency and performance. In this sense, neurohacking can be seen as an extension of lifehacking -enhancing the brain to increase productivity, creativity, or emotional well-being. Additionally, neurohacking shares similarities with the quantified self movement, which involves tracking various metrics related to health and performance, such as sleep patterns, physical activity, or cognitive output. For neurohackers, self-quantification might involve measuring changes in cognitive performance before and after using brain stimulation devices. The ultimate goal of these movements is to optimize human potential and harness technology to enhance physical and mental capabilities. These movements, while diverse in their focus, all share a common philosophy: the belief that through self-optimization, individuals can improve their quality of life. In this context, DIY brain stimulation serves as a powerful tool for those seeking to push the limits of their cognitive performance.
Ethical considerations and risks While the DIY brain stimulation movement offers exciting possibilities for cognitive enhancement, it also raises important ethical and safety concerns. One of the main important ethical and safety concerns. One of the main issues is the lack of regulation surrounding the use of these technologies. In contrast to clinical applications, where brain stimulation is carefully monitored and administered by medical professionals, the DIY approach is unregulated and based on self-guidance. This opens potential risks, such as improper use, inadequate understanding of the technology, and the possibility of harmful side effects like skin burns or headaches. Moreover, the ethical considerations extend beyond individual safety. There are concerns about accessibility and inequality: will these technologies be used responsibly, or will they exacerbate existing societal divides, where only those with access to these tools can benefit from enhanced cognitive performance? Furthermore, there is no question of the long-term effects of brains simulation on cognitive health, particularly when used outside of a clinical setting. These concerns highlight the need for a more nuanced policy approach to neurohacking. Rather than merely regulating the use of brain stimulation devices, it is essential to consider the broader social implications of these technologies and ensure that they are used responsibly and ethically.
The future of neurohacking: empowering individuals and societies As the DIY brain stimulation movement continues to grow, its potential to reshape the way we approach brain health and cognitive performances is immense. The movement has already sparked innovation in neurotechnology and could lead to more personalized and accessible forms of cognitive enhancement. For individuals, neurohacking offers the possibility of improving mental clarity, focus and productivity, leading to better performance in personal and professional life. At a societal level, the rise of neurohacking could challenge traditional structures of power and knowledge. It empowers individuals to take charge of their cognitive well-being, by-passing medical gatekeepers and traditional institutions. This shift could democratize access to health and wellness, breaking down barriers to self-improvement and making these technologies available to a broader range of people. However, the future of neurohacking will depend on how society addresses the ethical and regulatory challenges that accompany these innovations. As the movement grows, it will be essential to find a balance between individual autonomy and collective responsibility to ensure that neurohacking remains a force for good.

Conclusion The DIY brain stimulation movement represents an exciting frontier in the broader landscape of neurohacking and biohacking. While it is part of a growing trend of self-experimentation and optimization, it also raises important ethical and safety questions that must be addressed. As more individuals embrace the power of neurohacking, it is crucial to consider the long-term implications of these technologies, both for individual users and for society as a whole. By understanding the broader social and cultural context in which DIY brain stimulation exists, we can better navigate the ethical challenges and ensure that these tools are use responsibly and for the benefit of all.
If you are needing some researches to have actuallized your web content or whatever you want, in health's matters or humanities related in health, you can ask to me at [email protected] and explain me your ideas.

Reference of the article
Wexler, A. (2017). The Social Context of “Do-It-Yourself” Brain Stimulation: Neurohackers, Biohackers, and Lifehackers. Frontiers in Human Neuroscience, 11(224). Massachusetts Institute of Technology. https://doi.org/10.3389/fnhum.2017.00224
If you are needing knowledge about what can you do for your with your nutrition and all that the nature gives you, you can ask to me at [email protected] and explain me your case.
Thank you!
#biohacking#neurohacking#do-it-yourself#DIY#nutrition#selfnutrition#supplements#healthylifestyle#health#vitamins#healthy living#aidaresearcheson
13 notes
·
View notes
Text
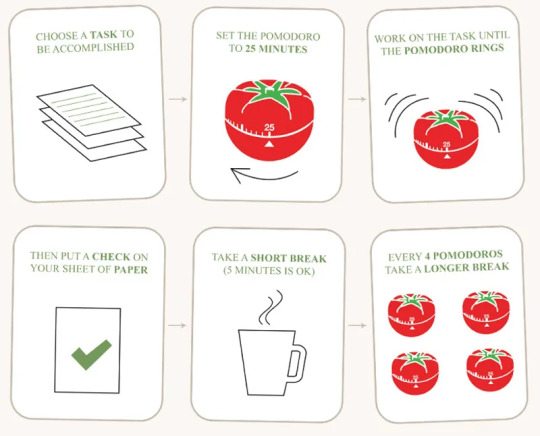
WHAT IS POMODORO AND WHAT DO YOU EAT IT WITH?
First… what is the Pomodoro method?!
The Pomodoro (Italian for tomato) technique was created by Francesco Cirillo in the 80s. Cirillo is an author and owner of a consulting company. He created this time managing technique that breaks down your study time into manageable intervals with breaks between each study session. With the countless distractions we have today, there’s no wonder it is still one of the most popular and helpful techniques for increasing productivity!
1. You need to plan your tasks
This will help you gauge how many sessions you will need. Will you be reading? Watching a lecture and taking notes? When planning what I will study, I know that watching a lecture and taking notes will take me sooo much longer than doing a reading or flashcards (less strenuous things). I also know that my core science courses will typically take much more studying time than one of my electives.
Determine what is most time-consuming and plan accordingly. The Pomodoro method is perfect for concentrating on any task, but you want to have in mind the classes that require more focus and time than others.
2. Set a 25-minute timer
25 minutes is only a recommendation and you can increase the time or lower it depending on how long you believe you can stay focused without interruptions. I mean, I don’t recommend you set a 5-minute timer to study and then a 5-minute break. But a session somewhere between 20-30 minutes is great (and how long I set my timer while studying)!
One other thing that Cirillo notes is that this time cannot be broken. You must work the entire 25 minutes without any distractions! One of my favorite ways to cancel out distractions is to:
-Put my phone in another room, or in my closet
-Or use the Forest app, which is a timer app that restricts you from leaving the app while completing work/other tasks. This guarantees I stay on task the whole time I am working!
3. Set a 5-minute timer for a break
Between each 25-minute study session, you need a break. You deserve it! So Cirillo recommends only a 5-minute break in between each study session. Do something that doesn’t bring you stress.
Tip: Make sure you do NOT work throughout the break at all. This break is meant to be a relaxing period to take your mind off of your work.
4. Repeat the process 3 times
This studying technique includes four sessions. So do this same process 3 more times. Work diligently and remember to stay focused.
5. After your 4th session, extend the break time to 20-30 minutes long
Once you have finished your fourth session, take a longer break! This is a huge accomplishment and after you have completed it, you will (and should) be so proud. The longer break allows you to take your mind off of your work and reset so you can get back into it.
Why It Benefits You...
IT WORKS FOR ANY TASK
Don’t think I only use this productivity hack for studying! This can be used while cleaning, organizing, reading, and so many other things! Remember, you can tweak the time frames depending on the task and depending on how much time you have to complete it. This is an amazing life hack that I believe everyone should be implementing to help with time management.
IMPROVES CONCENTRATION
Like I noted earlier, this is a distraction-free strategy! It’s on you to remove the distractions from your sessions, and when you do, you will see significant improvements in your work ethic. This technique was created to allow complete concentration on the task at hand. It will improve your focus, productivity, and concentration.
BEATS PROCRASTINATION
The Pomodoro technique breaks the time down into consumable segments. Would you feel more confident with saying you will study for 2 hours or 4 sessions of 25 minutes? I’m confident I would choose the latter every single time. This technique gives our brains manageable chunks of time to study so we result in more work getting done in the end. So just start working!
REMEMBER TO UTILIZE YOUR BREAKS
by Ania Henderson
#university#blogger#study blog#study motivation#study#study aesthetic#study buddy#study hard#study space#study tips#studygram#studyspo#studystudystudy
31 notes
·
View notes
Text
The Positive Effects of Marvel Rivals Hacks: Enhancing the Player Experience
Marvel Rivals is an exciting, action-packed game that allows players to immerse themselves in the Marvel Universe, competing with iconic superheroes and villains. While the idea of using hacks in gaming is often seen negatively, there are actually several positive aspects to the use of Marvel Rivals hacks. When used thoughtfully and responsibly, these hacks can enhance the player experience, increase engagement, and contribute to a thriving gaming community.
Increased Player Enjoyment
One of the main benefits of using Marvel Rivals hacks is the boost in player enjoyment. By allowing access to additional characters, abilities, or resources faster, players can dive into the more thrilling aspects of the game without the slow grind. This helps to maintain excitement and prevent boredom, especially for those who may not have the time to progress at a normal pace. With more exciting features at their fingertips, players can fully enjoy the game from the start.
Making the Game More Accessible
Marvel Rivals hacks can help make the game more accessible, especially for those who are new to gaming or don’t have the time to spend hours advancing through levels. Using hacks to unlock key resources and characters allows players to quickly catch up to more experienced players. This helps create a level playing field, where both new and seasoned players can enjoy the game without feeling disadvantaged. The sense of fairness that this promotes can make the game more enjoyable for everyone.
Sparking Creativity and Innovation
By unlocking different characters and powers through hacks, players can experiment with new strategies and gameplay techniques that they may not have had access to otherwise. This can spark creativity and innovation, encouraging players to explore the game’s possibilities in new ways. As players experiment, they may discover new synergies between characters, invent new strategies, and share their findings with others. This encourages a collaborative environment where players continuously evolve their gameplay.
Fostering Community Interaction
Marvel Rivals hacks can also foster a sense of community among players. When players unlock new features or discover different aspects of the game, they are more likely to share their experiences with others. This can lead to lively discussions, helpful guides, and even the formation of new groups or communities focused on specific strategies or characters. The willingness to share knowledge helps build a stronger, more supportive gaming community where everyone can learn and grow together.
Extending Game Longevity
The use of hacks in Marvel Rivals can also increase the longevity of the game. By unlocking new content and features, players are able to explore different parts of the game that they might have otherwise missed. This keeps the gameplay fresh and exciting, encouraging players to return and continue exploring. The ability to unlock content quickly gives players more reasons to keep playing, which can lead to extended engagement and enjoyment.
A Responsible Approach to Hacks
While there are clear benefits to using hacks in Marvel Rivals, it’s essential for players to approach them with responsibility and respect for the game’s community. Hacks should be used in a way that doesn’t negatively impact other players’ experiences. It’s also important to consider legitimate methods of unlocking content, as this helps maintain a sense of fairness and respect for the game’s developers and other players. By using hacks ethically, players can contribute to a positive gaming environment.
2 notes
·
View notes
Text
CYBERPUNK PROGRAMMERS: TRUSTED EXPERTS IN CRYPTO ASSETS RECOVERY
Cyberpunk Programmers is a specialized firm focused on recovering lost cryptocurrency assets. Their expert team employs advanced blockchain forensics and tracing techniques to retrieve funds lost to scams, hacks, or fraud. With a client-first mindset, they prioritize clear, jargon-free communication, ensuring clients understand the recovery process. The company distinguishes itself through transparency and security, implementing strict measures to protect sensitive data. Their results-oriented fee model charges only upon successful recovery, aligning their goals with clients’ interests and reducing upfront risks. This reflects their confidence in tackling complex crypto recovery cases. Cyberpunk Programmers handles various asset loss scenarios, from phishing attacks to compromised wallets, catering to both novice and seasoned crypto users. Their efficient approach aims for swift resolutions without compromising thoroughness, making their services accessible and reliable. Known for ethical practices, Cyberpunk Programmers has earned a strong reputation in the asset recovery industry. Their dedication to client satisfaction and expertise in navigating digital fraud make them a trusted choice for those seeking to reclaim lost crypto assets. For anyone facing cryptocurrency loss, Cyberpunk Programmers offers a professional, secure, and effective solution. for more info about Cyberpunk Programmers inquire at cyberpunkprogrammers.com
2 notes
·
View notes
Text
Introduction of Cybersecurity and Ethical Hacking into IGNOU Online MCA
In a day when breaches in digital security and cyberattacks are getting rampant, skilled cybersecurity professionals have never been in greater demand. It is this dire need that has prompted IGNOU Online MCA or Indira Gandhi National Open University to introduce courses in cybersecurity and ethical hacking into its Online MCA or Master of Computer Applications course. These additions are specifically designed to provide students with relevant knowledge and competencies in providing security to digital assets and systems within a dynamically changing threat environment. This blog discusses the new courses' relevance, the topics they will cover, and how these connect to the needs of the modern work market.
The Increasing Need for Cybersecurity ExpertsThe intricacy of cybercriminals' strategies rises with the advancement of technology. Data breaches, ransomware attacks, and phishing schemes targeting people and businesses are a few of the hazards that exist right now. The fact that must be noted is that these incidences of growing attacks remarkably reflect the increasing demand for cybersecurity experts who will be able to save sensitive information and ensure that the digital systems are up and running.
IGNOU Online MCA to Cybersecurity ChallengesCybersecurity has become the main demand in the job market. Because of this, IGNOU has come forward to include courses in cybersecurity and Ethical Hacking in the MCA program. Such a course shall fetch the learner comprehensive knowledge in Security Principles and hands-on experience in combating cyber threats. Following is an outline of these newly incorporated courses added in the curriculum:
1. Fundamentals of CybersecurityFundamentals of Cybersecurity Course: This course takes the student through an overview of the very basics that lie inherently behind cybersecurity. Students will encounter a range of online dangers, such as phishing, spyware, and malware. The objectives of this course are to teach fundamental risk management, network security, and cryptography.
The important points that are to be noted include:
· The types of cyber threats and attack vectors
· The basics of cryptography and encryption
· Network security protocols and best practices
2. Ethical Hacking and Penetration TestingThe methods that an ethical hacker would employ to identify system vulnerabilities before an attacker does are covered in this course on ethical hacking and penetration testing. Students have practical experience using a variety of tools to execute simulated cyberattacks, as well as learning how to conduct penetration tests and vulnerability assessments.
Content Overview:
· Techniques and utilities of pen testing
· Vulnerability assessment and management
· Concepts of ethical hacking and legal issues
3. Cutting-Edge Threat Identification and ReactionAdvanced approaches for identifying and countering cyberattacks, intrusion detection systems, security information and event management systems, incident response plans, and useful skills for threat management and security incident mitigation are all covered in the course. Key topics presented and discussed include:
· Intrusion Detection and Prevention Systems
· Security Information and Event Management
· Incident Response Planning and Execution
· Forensic and Data Recovery Techniques
How These Courses Enhance EmployabilityIGNOU Online MCA courses are, henceforth rewarding in the following ways for students getting employed in the fields of cybersecurity and ethical hacking:
Practical Skills: This kind of practical training within courses guarantees course completion with hands-on experience in using industry-standard tools and techniques that make students work-ready by the time they graduate.
Meeting Industrial Requirements: These courses are specifically designed to meet the current needs of the industry, in terms of what exactly the employers in cybersecurity need in terms of skills and knowledge.
Certification Preparation Offered: A number of these courses may avail the students directly for industry-level certifications but are not limited to, CEH, CompTIA Security+, and CISSP. This, in a way, prepares them better for prospective careers.
ConclusionIncorporating courses into the online MCA of IGNOU regarding cybersecurity and ethical hacking will prove very opportune and tactical curriculum enhancement. Such programs would equip students with the knowledge and skills necessary to pursue a career in cybersecurity, thus responding to the emergent demand for professionals who can safeguard the digital economy. Skill development with a focus on appropriate industry-relevant content,IGNOU Online MCA Course is making sure to position its students for the best possible preparation in lucrative cybersecurity careers by meaningfully contributing to fighting cyber threats.
#IGNOU#MCA#Cybersecurity#Ethical Hacking#Tech Education#Digital Security#IGNOU MCA#Cybersecurity Skills#Ethical Hacking Techniques#Online MCA#Digital Protection
0 notes
Text
Mighty Hacker Recovery Claims Leading Position in Crypto Recovery & Tracking contact on WhatsApp +1 404 245 6415
Worldwide – In the burgeoning, yet often turbulent, world of cryptocurrency, the threat of theft and scams looms large. Recognizing this pervasive issue, Mighty Hacker Recovery has emerged as a leading force, claiming to be at the forefront of both crypto recovery and advanced crypto tracking.
The company, which has been quietly building its reputation over the past few years, asserts that its team of skilled hackers and cybersecurity experts utilizes cutting-edge techniques to help victims recover lost or stolen cryptocurrency assets. While crypto transactions are touted for their anonymity and decentralization, Mighty Hacker Recovery claims to have developed methods to trace digital assets across blockchains, often leading back to the perpetrator.
"In a landscape where anonymity is king, we equip ourselves with the tools to unveil the truth and reclaim what's rightfully ours," stated a spokesperson for Mighty Hacker Recovery. "We understand the devastating impact of crypto scams and hacks, and we are committed to leveraging our expertise to provide hope and tangible results for our clients."
Their services reportedly encompass a wide range of crypto-related challenges, including recovery from phishing scams, wallet hacks, exit scams, and even cases of accidental loss or misplacement of private keys. The company emphasizes a rigorous and ethical approach to recovery, ensuring compliance with legal regulations and prioritizing client confidentiality.
"Our methods are not about simply retrieving funds; they're about pursuing justice and holding perpetrators accountable," the spokesperson added. "We work closely with law enforcement and regulatory bodies to ensure our actions are aligned with legal frameworks."
Several online testimonials and anecdotal evidence suggest that Mighty Hacker Recovery has successfully recovered assets for numerous clients, although independent verification of these claims remains challenging given the sensitive nature of the cases and the company's commitment to client privacy.
However, the emergence of companies like Mighty Hacker Recovery raises ethical considerations. Concerns exist about the potential for these services to be used maliciously, such as for tracking legitimate crypto transactions or engaging in illicit activities.
Industry experts caution potential clients to thoroughly vet any crypto recovery service before engaging their services. "Due diligence is paramount," advises security analyst, Sarah Chen. "Verify their credentials, read reviews carefully, and be wary of any promises that sound too good to be true. The crypto recovery space can be rife with scammers seeking to exploit already vulnerable individuals."
While the future of crypto recovery is uncertain, Mighty Hacker Recovery's emergence as a prominent player highlights the growing demand for solutions to combat crypto theft and fraud. Whether they truly represent the "best in crypto recovery" remains to be seen, but their presence undoubtedly signifies a shift towards a more secure and accountable cryptocurrency ecosystem.
2 notes
·
View notes
Text
Deep Dive into Wi-Fi Hacking: How Ethical Hackers Secure Your Wireless Networks

With our hyper-connected world, Wi-Fi is the unseen lifeline keeping us online today. From streaming your favorite shows to managing your smart home devices, Wi-Fi is everywhere. But have you ever stopped to think about just how secure your wireless network really is? What if someone could sneak into your network, steal your data, or even hijack your devices? Scary, right? That’s where ethical hackers come in—the unsung heroes of the digital age who use their skills to protect, not exploit. If you’ve ever been curious about how they do it, or if you’re considering a cybersecurity and ethical hacking course, this blog is for you.
The Dark Side of Wi-Fi: Why It’s a Hacker’s Playground
Well, face it: Wi-Fi networks are a goldmine for cybercriminals. Why? Because they are usually the easiest weakness in our digital defense. It has weak passwords, outdated encryption, and misconfigured routers. That's not to mention stealing your Netflix login. Hackers can use it as an open gateway to access more of your digital life.
Here's your scenario: You're having your favorite coffee at a quaint little café while making use of their free Wi-Fi. Well, a hacker within some tables from you is running Aircrack-ng or Wireshark for quite a bit on your data that's going by. Before you realize it, they have gotten your login credentials, credit card information, or even obtained access to your corporate emails. How scary does that sound?
Enter Ethical Hackers: The Good Guys of Wi-Fi Security
That is when the ethical hackers come in. Cybersecurity professionals use the same hacking tools and techniques as evil hackers, with one difference though: they work for you. Their job is to find a hole before a hacker does so that they may fix it before hackers can gain entry into your network.
How do they go about it? Let's dissect this:
Reconnaissance: Ethical hackers first gather information about the target network. They use tools such as Kismet or NetStumbler to identify the network's SSID, encryption type, and connected devices.
Exploitation: Once they have identified potential weaknesses, they try to exploit them. For example, if the network uses outdated WEP encryption (which is notoriously weak), they might use tools like Aircrack-ng to crack the password.
Post-Exploitation: Having obtained access, the ethical hacker calculates the potential damage that can be done. Could they have accessed sensitive files? Could they have launched a man-in-the-middle attack? This step will give them a sense of real-world impact from the vulnerability.
Reporting and Patching: They finally document their findings and collaborate with the owner of the network to fix the issues. It may involve updating firmware, changing passwords, or enabling stronger encryption like WPA3.
Why You Should Care About Wi-Fi Security
You may be thinking: "I am an average user, so why would somebody even bother with me?" The thing is, hackers don't discriminate. Whether you are just an individual, a small business owner, or part of a large corporation, your Wi-Fi network is a potential target. And with the emergence of IoT devices, such as smart thermostats, security cameras, and voice assistants, the risk is much bigger than ever.
Here's the good news: You don't need to be a tech genius to protect yourself. By learning the basics of Wi-Fi security or even enrolling in a cybersecurity and ethical hacking course, you can take control of your digital safety.
How to Secure Your Wi-Fi Network: Tips from the Pros
Want to make your Wi-Fi network hacker-proof? Here are some practical tips inspired by ethical hackers:
Use Strong Passwords: Avoid using common passwords, such as "admin" or "password123." Instead, use long complex phrase with letters, numbers, and symbols.
Enable WPA3 Encryption: The latest Wi-Fi encryption protocol is WPA3; if your router supports it, switch to WPA3.
Update Your Router's Firmware: Manufacturers in their official websites may have coming updates that address security vulnerabilities. Check and update the firmware on your router to a newer edition.
WPS: Wi-Fi Protected Setup is convenient but highly insecure. Just turn it off to minimize brute-force attacks.
Check Connected Devices: You would be surprised to know which device is connected to your network if you don't check it periodically. If something looks suspicious, investigate immediately.
Ready to Be a Wi-Fi Warrior?
If this deep dive into Wi-Fi hacking has piqued your interest, why not take it further? A cybersecurity and ethical hacking course can teach you the skills you need to protect yourself—and maybe even turn your passion for tech into a rewarding career. Imagine being the person who uncovers vulnerabilities, thwarts cyberattacks, and keeps the digital world safe. Sounds exciting, doesn't it?
Ethical hacking is not the art of hacking into systems, but understanding how they work so that such knowledge can be applied to strengthen their defenses. In a world that is ever changing with threats through cyber, it has never been a better time to learn.
Final Thoughts
It sounds like something out of a spy movie, but the truth is that Wi-Fi hacking is an everyday threat in your life. The good news is that with the right information and tools you can protect yourself and your loved ones from becoming cybercrime victims. However, whether you are a tech enthusiast or a complete beginner, a course in cybersecurity and ethical hacking will empower you to take the lead in digital security.
Remember the next time you connect to a Wi-Fi network: those invisible waves keeping you online can be the doors for hackers. Stay informed and vigilant, and maybe you will end up being that ethical hacker who saves the day.
So, stay safe and happy ethical hacking!
2 notes
·
View notes
Text
Thundertober Day Two: Espionage
This is a long one (sorry!) but the next two days are shorter so that kind of makes up for it. Minor Pen&Ink in this, but it's mainly spy!Penny.
AO3 here Day: One
Warnings for: bad language Tracy Industries has always had a target on their backs. But this time, the attack hits a little closer to home. Tagging: @thunder-tober @skymaiden32
Tracy Industries was a pillar in the world of aerospace, construction and finance. It held a desirable reputation and was run by a family of charming philanthropists who seemed to consistently beat the odds that were forever stacking against them. They were renowned in their techniques and had contract offers left, right and centre. With all of this factors combined, the target on their backs grew increasingly larger.
As a company they had witnessed, and prevailed, through many, many attempts of sabotage before, whether that was from other companies trying to convince major shareholders to sell their shares, or from jealous rivals trying to wreak havoc by circulating false whisper numbers around Wall Street in an attempt to sow doubt within and around Tracy Industries. In fact, in the first few months following his father’s tragic and untimely death, that had been one of Scott’s first challenges. The eldest Tracy had dealt with an insurmountable amount of attempts in the years that had followed, and he had managed to fight each attempt valiantly, managing to keep Tracy Industries afloat one way or another.
This recent hack, however, had been a much larger threat that could have ended in a devastating blow.
At first, they had assumed the security breach was credited to the Hood, but after being reassured by Colonel Casey that their nemesis was still securely locked away, they began to search deeper. Their result was unpleasant. Angry and dramatic vows of revenge followed, though they would never be acted upon.
The breach couldn’t have been described as anything other than a direct attack and it was far deadlier to the company than any other previous sabotage had been. This breach threatened to expose more than just a few financial details, or ways in which to win bigger contracts back from Tracy Industries.
As the main exporter and provider for International Rescue, this breach threatened to expose the blueprints Tracy Industries had kept in their files for the organisation’s crafts and machines.
Much to all of their reliefs, the blueprints for the actual Thunderbirds themselves were kept safely locked away on the island, but that still left some of their other life-saving equipment being at risk of leaking. The thought of other, perhaps less ethical companies, getting their hands on any of their design blueprints was bad enough. With the added fear of them selling them to the highest bidder, regardless of who that buyer might have been, was terrifying, and that panic alone had them all cursing themselves over the lack of security surrounding those files.
Regardless of John’s reassurance that the security system fitted by both himself and Brains was impenetrable, keeping some of their top secret files over on Tracy Industries’s databanks, just for the convenience, was incredibly stupid, and it was something they had planned to rectify in the following months. The move was one made from pure carelessness on their part.
To add insult to injury, Scott had then received a personal invitation to a party hosted by the very man that they strongly suspected as being the one behind the attack. He had almost declined. The thought of partying with a man who had committed such a violation to their company, whether they were rivals or not, had his stomach churning. He would have much rather turned the guy in for corporate espionage and be done with it… Until he realised that what they had, mere traces of evidence, was not evidence enough.
They’d have to dig deeper.
Enter Lady Penelope Creighton-Ward, long time friend of the Tracy family and associate of both International Rescue and Tracy Industries.
The party’s location was being held at Randall Gardener’s private mansion in Beverly Hills and not at the office of his company, The Acorn Corporation. They had been aware of that fact from the moment they’d received the invitation and had planned accordingly.
Gardener’s home office would be Penelope’s target. Brains had developed a special drive to expertly download all of Gardener’s files in record time. The device hid within one of the solid silver bangles she had dangling from her wrists. Though she rather worked alone on these sorts of missions, she couldn’t deny how conspicuous she’d look if she was the only one representing Tracy Industries and so she had relented when Scott suggested one of them attended with her.
Kayo was out on another mission with the GDF and so Penelope’s first choice was blown out of the water before she could even consider the Chief of Security’s company. Virgil offered his services, only to be quite literally batted away by Gordon.
Once it was revealed that she would require a Tracy to hang off her arm for the night, Gordon had practically begged to be the one to go with her. Penelope wasn’t keen on the idea. At first he had so vehemently claimed to want to catch the ‘dirty bastard’ red-handed at his own dinner party, that Penelope wasn’t sure Gordon was the best option. Volatile, bitter and hurt were not what she was used to seeing with Gordon and, if she was honest, the sight worried her terribly. She had been inclined to take up Virgil’s offer instead but after a week of stewing, Gordon had seemingly calmed down enough for Penelope to feel comfortable with having him along.
Throughout the evening, John would monitor them from Thunderbird Five and EOS would translate guidance through specially crafted earpieces, though this would only be when necessary to avoid distractions.
With all the technical aspects prepared and ready, Penelope began to focus on her favourite part of any mission: her closet.
Penelope’s colour was pink. It always had been. It probably always would be. Her love of the colour came from societal’s childhood expectation of her; to adore the pretty and the sparkly, but her appreciation of the colour had grown in her later youth. By the time she had reached adulthood, Penelope knew how to use the colour pink to her advantage.
Just like tonight.
The gown she had chosen to wear was pink and sparkly. The hue matched her golden hair that was clipped in a way so her styled waves fell over one shoulder. Her manicure she’d had done earlier that day had her nails matching the colour of her floor-length dress, and her choice of necklace - diamonds inset into platinum - accentuated the modestly swooping neckline. Her outfit, as always, was a reflection of what they wanted to see. Pretty, poised and elegant. All the pieces helped her play the game all the more easily.
After all, who would think to question the young socialite in her diamonds and sequins if questions were to arise?
Not that she was expecting questions. There was a reason Penelope had a stellar reputation within intelligence circles. She was quick on her feet, agile enough in her social abilities to dodge unwanted questions and stealthy enough to leave no lead back to her doorstep. She liked to think she’d done her father proud.
Getting into the venue was easy. There were no checks on the door and there was barely any security on the property that could be seen. She didn’t want to jinx their mission but Penelope couldn’t help but think that perhaps this task of their’s was going to be easier than she had could have first anticipated.
It was a shame she would be proven wrong.
Sandwiching the main event of a fanciful dinner, networking was common during events such as these. This party was no different. The first half an hour, Penelope walked the room with Gordon, glasses of a sparkling wine filling their glasses before the party was called into a large, ornate dining room. Gordon was seated opposite her and both he and Penelope made patient small talk with those sitting closest to them. Once the many courses had been served and eaten, more networking commenced in the Grand Hall of Gardener’s mansion. Seamlessly, they played their parts and continued to blend in with the rest of the party as they mingled.
“God, I hate this part.” Gordon had whispered to her after they’d said farewell to a greying gentleman. He’d offered Gordon his business card in the ‘hopes it finds your older brother well’. The fake smile he plastered on his features told Penelope everything she needed to know about how he felt about that situation.
“I thought you hadn’t ever been to one of these before.”
“I haven’t. Well, not officially. Usually I was with Scott. I wouldn’t mind it but… being the sole member of the family here means that I’m having to receive all the weird conversations.” He sighed. “When is the sleuthing going to begin?”
Penelope did her best to hide her fond smile, gesturing over to their host for the evening who was standing beside a nearby table. “Distract Gardener. I’ll go looking for the office.”
Gordon glanced at her with his eyes wide. “You mean I don’t get to do the cool spy stuff with you?”
“Gordon, you don’t know how to do the cool spy stuff.”
He looked at her, a little stumped by her frankness but, unable to think of a decent response, he merely grumbled, “I could have learnt on the job.”
“I’m sure you could have.”
“How long do you need?”
“Thirty minutes.”
“And if I can’t keep him that long?”
“EOS can warn me.”
Gordon offered her a nod. He eyed his target, clearly not looking forward to having to be the front of the conversation once again if his apprehensive bounce was anything to go by. “Good luck,” was whispered before Gordon melted into the crowd of attendees.
To appear as casual as possible, and to avoid as much attention as possible, Penelope waited a few minutes before making her exit, only leaving once she heard Gordon’s joyful greeting boom across the event hall as the distraction she was hoping for.
“Randall! Long time, no see, buddy! How are things?”
---------------------------------------------------------------
The office was far enough away from the rest of the party for Penelope not to have to worry about drunken party-goers getting in her way. She remained wary of possible security, though she came across no guards on her journey and, whilst she thought it odd, she wasn’t about to complain. It was making her job a whole lot easier.
With the door already unlocked, her compact lock picking kit became redundant. Making sure the door behind her closed as quietly as possible, Penelope entered the office, making her way to the main computer unit at the far end of the room.
Gardener’s office was state-of-the-art. Various gadgets sat on shelves, experiments he was conducting from home being strewn out over various worktables, and floor-to-ceiling windows which seemed to draw Penelope in, captivating all her attention for a moment despite her attempts to resist the distraction. From the mansion’s position in the Hills, the sparkling city of Los Angeles far below looked stunning. It was far too picturesque to ignore.
She only snapped out of that trance when she thought she heard footsteps outside the door.
“EOS, how long do I have?”
The AI’s childlike voice felt bizarre in replacement of the usual Cockney accent of her chauffeur. “Gordon is successfully distracting Mr. Gardener. I estimate he will continue to provide sufficient distraction for a while longer yet, Lady Penelope.”
Regardless of this reassuring update from EOS, Penelope set to work immediately. She knelt down behind the desk to avoid anyone being able to easily see her from the corridor, just in case that office door ended up opening somehow during her work. Bangles jangled as she retrieved the drive from where it had been inset into her jewellery and plugged it into the main terminal.
The screensaver image of the Acorn Corporation logo that had been lighting up the desk flickered away to reveal two windows. In one, the files of Gardener’s computer system. In the other, those same files being copied from device to device. Now all Penelope had to do was wait.
Brains had assured her the gadget was quick and she had never had a reason to doubt him before. Yet, watching the seconds tick by, the percentage staggering upwards ever-so-slowly, Penelope began to wonder whether, for once, Brains had been wrong in his design. It began to feel like she had been waiting forever.
“EOS, how much longer?” Penelope whispered, wary of the fact that she had no idea who could have been lurking outside that office door now. For all she knew, the device she’d plugged in could have triggered a hidden, silent alarm. It wouldn’t have been the first time she’d been caught out by a sneaky security trick.
The lack of a response from EOS had Penelope begin to feel uneasy.
Her eyes caught the screen in time to see the ninety-eight per cent mark tick over to the ninety-nine. Anticipation built up. It had almost completed. One more per cent and then she could find Gordon and get out of there.
Except the ninety-nine per cent never reached one hundred.
The entire system seemed to just… switch itself off.
Penelope, trying her hardest to not start panicking over what could simply have just been a minor mishap, began flicking buttons.
It was pointless.
“EOS? EOS, can you hear me? What’s happened?
Faint static told Penelope that the line was still connected, if a little disturbed by interference.
“… I’m sorry, Lady Penelope.” EOS’s pause before she finally responded was so full of emotion, of guilt in particular, that Penelope could no longer deny that feeling of building dread that was creeping up from the pits of her stomach.
“You’re sorry—? What for?”
EOS remained silent again.
“What do you mean? Did you do this? EOS?”
“I was told it was for the best.” The AI defended herself before finally cutting the line off.
“By who?” Penelope tried despite the lack of static in her ear.
“By me.”
The voice had come from behind her, from the door which had now been swung open, from a voice she knew all too well and had trouble believing.
“… John?”
She wouldn’t believe it. She couldn’t. He was supposed to be on Thunderbird Five! He wasn’t supposed to be here. Her head span as Penelope jumped up from her position behind the desk.
“I’m sorry, Penelope,” John continued, stepping into the room properly, “but I couldn’t let you download those files.”
To his credit, John did appear to truly feel guilty over his words and his apparent actions.
“Why?”
John’s silence in regards to that question hurt her the most. Ignoring all the fears that were now whirling around her head, she attempted another question.
“Where’s Gordon?”
“Safe.”
“Can I trust you with that?”
There was a venomous quality to Penelope’s query which she didn’t regret one bit. Trust, it seemed, was not something she could currently equate to John. Was it ever something she could have attributed to him? Was it ever something she could honestly and safely expect from him again?
“He’s my brother.”
“Why didn’t you want me to download those files?”
Two guards, dressed to the nines which suggested they’d been blending in with the rest of the party just as Penelope and Gordon had been, entered behind John. Penelope eyed them and then the escape route that was just out of reach.
“Don’t.” John warned, sounding increasingly tired.
“You know me too well.”
“That’s the problem.” He sighed, as though that was her problem. Before Penelope could argue against that, John tapped his ear. “EOS?”
EOS’s voice filtered through Penelope’s earpiece once again. It had Penelope questioning if the AI had actually left earlier.
“Message relayed.”
“Message?” Penelope asked, more frantically than she’d planned. “What message? To who?”
“To Gordon. To tell him that you’ve left, following a clue that you wanted to go in search of without him.”
“He won’t buy it.”
“I don’t care if he buys it. I just care that he’s out of the way long enough to not get caught up in this any further.”
“And what is this, John?”
Red rings circled his eyes and bags had long set in. His complexion was paler than normal, even by John’s standards, and Penelope found herself searching her memory to remember a time she’d ever seen him look so troubled. She wasn’t sure she ever had.
John spoke no words. He signalled to the two guards to take one of Penelope’s arms each before leading them all out of the office and down the hallway. Penelope didn’t try to fight them, instead opting for trying to get information.
“Who put you up to this?” She asked John, not expecting a reply and being pleasantly surprised when he offered her one.
“What makes you think someone put me up to anything?”
“This is your family’s business.”
“So?”
“So, why not let me look at those files?”
They turned a corner which led to a set of stone steps, which in turn led down to God knew where. John slowly stepped down them, as though each step was a step towards Hell itself. Penelope prayed it wasn’t.
“You wouldn’t have liked what you saw.”
“Which is what, John?”
The stairway curved around in a spiral, heading deeper and deeper below ground. That panic began to build in her stomach. It would have been easier to fight off if she knew she could trust John, but she couldn’t anymore apparently.
“We can’t help you if you don’t tell us what is happening—”
The fury of John Tracy was something Penelope had never witnessed in person before. Icy chills went down her spine as he span around to face her. His face was shrouded in shadows from the minimal light making it almost impossible to see his real emotions play out on his face.
“Shut up.” He spat in the most un-John-like way Penny hoped she’d ever have to hear. John sighed deeply, pinching the bridge of his nose as he reined in that panic. “I didn’t mean— Just, please, if you know what’s good for you, Penny, then just stop talking.”
In a way, that was answer enough for her. Add all the little factors she had and Penelope found herself jumping to the worst conclusion: John was responsible for the Tracy Industries hack, or at least had a major hand in it. Why was still a major question that he clearly wasn’t willing to answer, neither was the how.
A trickle of light glinted off his eyes, betraying the fact that he had tears in them, but Penelope found herself with little pity to give.
“Your brothers are going to be very disappointed in you, John.”
“I know.” He replied, head hanging lowly as he turned to continue leading them down that darkened hall way. “I fucking know.”
#thundertober 2023#thunderbirds fanfiction#five fics#lady penelope#gordon tracy#john tracy#thunderbirds are go
33 notes
·
View notes
Text
In 2025, AI is poised to change every aspect of democratic politics—but it won’t necessarily be for the worse.
India’s prime minister, Narendra Modi, has used AI to translate his speeches for his multilingual electorate in real time, demonstrating how AI can help diverse democracies to be more inclusive. AI avatars were used by presidential candidates in South Korea in electioneering, enabling them to provide answers to thousands of voters’ questions simultaneously. We are also starting to see AI tools aid fundraising and get-out-the-vote efforts. AI techniques are starting to augment more traditional polling methods, helping campaigns get cheaper and faster data. And congressional candidates have started using AI robocallers to engage voters on issues.
In 2025, these trends will continue. AI doesn’t need to be superior to human experts to augment the labor of an overworked canvasser, or to write ad copy similar to that of a junior campaign staffer or volunteer. Politics is competitive, and any technology that can bestow an advantage, or even just garner attention, will be used.
Most politics is local, and AI tools promise to make democracy more equitable. The typical candidate has few resources, so the choice may be between getting help from AI tools or getting no help at all. In 2024, a US presidential candidate with virtually zero name recognition, Jason Palmer, beat Joe Biden in a very small electorate, the American Samoan primary, by using AI-generated messaging and an online AI avatar.
At the national level, AI tools are more likely to make the already powerful even more powerful. Human + AI generally beats AI only: The more human talent you have, the more you can effectively make use of AI assistance. The richest campaigns will not put AIs in charge, but they will race to exploit AI where it can give them an advantage.
But while the promise of AI assistance will drive adoption, the risks are considerable. When computers get involved in any process, that process changes. Scalable automation, for example, can transform political advertising from one-size-fits-all into personalized demagoguing—candidates can tell each of us what they think we want to hear. Introducing new dependencies can also lead to brittleness: Exploiting gains from automation can mean dropping human oversight, and chaos results when critical computer systems go down.
Politics is adversarial. Any time AI is used by one candidate or party, it invites hacking by those associated with their opponents, perhaps to modify their behavior, eavesdrop on their output, or to simply shut them down. The kinds of disinformation weaponized by entities like Russia on social media will be increasingly targeted toward machines, too.
AI is different from traditional computer systems in that it tries to encode common sense and judgment that goes beyond simple rules; yet humans have no single ethical system, or even a single definition of fairness. We will see AI systems optimized for different parties and ideologies; for one faction not to trust the AIs of a rival faction; for everyone to have a healthy suspicion of corporate for-profit AI systems with hidden biases.
This is just the beginning of a trend that will spread through democracies around the world, and probably accelerate, for years to come. Everyone, especially AI skeptics and those concerned about its potential to exacerbate bias and discrimination, should recognize that AI is coming for every aspect of democracy. The transformations won’t come from the top down; they will come from the bottom up. Politicians and campaigns will start using AI tools when they are useful. So will lawyers, and political advocacy groups. Judges will use AI to help draft their decisions because it will save time. News organizations will use AI because it will justify budget cuts. Bureaucracies and regulators will add AI to their already algorithmic systems for determining all sorts of benefits and penalties.
Whether this results in a better democracy, or a more just world, remains to be seen. Keep watching how those in power uses these tools, and also how they empower the currently powerless. Those of us who are constituents of democracies should advocate tirelessly to ensure that we use AI systems to better democratize democracy, and not to further its worst tendencies.
2 notes
·
View notes