#IT Security Services
Explore tagged Tumblr posts
Text
In today’s rapidly evolving digital landscape, businesses face numerous cybersecurity threats. Ensuring your company’s data and systems are secure is not just a necessity but a critical aspect of maintaining operational integrity and customer trust. By leveraging IT services in Virginia, businesses can gain access to advanced security measures that protect sensitive information from cyber threats, data breaches, and other vulnerabilities. These IT services offer comprehensive solutions that include network monitoring, threat detection, and incident response to ensure your systems remain secure at all times.
0 notes
Text
Protect Your Business with IT Security Services
In an era of increasing cyber threats, safeguarding your business’s data and systems is critical. An IT security services company ensures robust protection, helping you stay secure, compliant, and resilient.
What Are IT Security Services?
IT security services involve proactive measures to defend against cyberattacks, data breaches, and unauthorized access. These services focus on identifying vulnerabilities, strengthening defenses, and ensuring operational continuity.
Benefits of Professional IT Security Services
Threat Detection & Prevention — Identify and block potential risks before they impact your business.
Data Protection — Safeguard sensitive information against breaches.
Compliance Support — Meet industry standards and regulations.
Business Continuity — Minimize downtime with recovery and backup solutions.
Peace of Mind — Focus on growth knowing your IT environment is secure.
Calypsi: Your Trusted IT Security Partner
At Calypsi, we specialize in comprehensive IT security solutions tailored to your needs. From firewall protection to advanced threat monitoring, our team ensures your business remains secure in a constantly evolving cyber landscape.
Don’t leave your business vulnerable. Explore our IT security services today.
0 notes
Text
How to Pick The Right Business Phone System For The Office
Would you like to replace your office phones with better ones but don’t know how to start? In this video, we are going to outline the most important aspects to consider when choosing the most appropriate business phone system to fit your needs. Be it landline, VoIP or virtual systems, we have it all!
📌 What will you learn from this video:
The steps involved in quantifying the need for business communication
Different phone systems and their pros and cons
Essential phone systems features such as voicemail, call forwarding, CRM integration among others
Advice on how to plan for growth in the future without overshooting your budget
Whether you are a growing small business or adding more people to your team, this guide will enable you to make the right decision for your office layout.
youtube
#it services#lancashire#it company lancashire#it security services#it services and solutions#Youtube
0 notes
Text
Defending the Digital Realm: The Critical Role of Cybersecurity

In today’s highly connected digital age, cybersecurity has shifted from a secondary concern to a top priority. As cyber threats continue to rise in both volume and complexity, individuals, businesses, and governments alike face unprecedented risks, including severe data breaches, financial losses, and damage to their reputations. The need for robust cybersecurity practices has never been more pressing. With that in mind, here are some essential strategies to help safeguard your digital assets.
To start, encouraging the creation of strong passwords can motivate readers to take that critical first step in securing their accounts. A combination of letters, numbers, and symbols creates a powerful first line of defense against unauthorized access.
Phishing scams are another significant threat in today’s digital landscape. These schemes are designed to trick people into sharing sensitive information. By helping readers recognize the warning signs of these increasingly advanced scams, you can equip them to navigate the digital world more safely.
Additionally, emphasizing the importance of regular software updates and reliable antivirus protection is vital. These measures help close security gaps and bolster defenses against potential cyber threats. By stressing the necessity of strong passwords, a keen awareness of phishing scams, and the habit of keeping software up to date, we can significantly enhance our digital security.
Ultimately, knowledge and proactive measures are our best tools for safely navigating the ever-evolving cyber landscape. Remember, vigilance and awareness are essential to staying secure in today’s digital world.
#Cybersecurity solutions#Data protection#Network security#Cyber threat detection#Security software#IT security services#Cyber defense#Threat prevention#Secure business solutions#Cybersecurity experts
0 notes
Text

Spictera top-tier IT security services to protect your business from cyber threats, ensuring your data is secure, compliant, and resilient against ever-evolving risks in the digital landscape.
0 notes
Text
How Sigma Solve Resolves Cybersecurity Challenges

Synopsis:
“Cybersecurity in 2024 is all about prioritizing defense dollar spending and having a security framework that provides threat intelligence, enabling robust cybersecurity strategies and apparatus.” Nehal Shah, the Solution Architect at Sigma Solve, explains the grave cyber security scenarios that are prevailing in our digital world today.
There are relentless security challenges and out-of-the-box solutions, too. As a cybersecurity solution provider, we aim to empower you with a comprehensive understanding of the cybersecurity sphere, its implications for businesses, and ways to mitigate these threats concurrently through this blog.
Conquer Cybersecurity Challenges in 2024 and Beyond:
Today, cybersecurity has taken precedence over performance. For businesses, cybersecurity solution architecture is as essential as performance-driven growth. Cybersecurity is all about protecting digital assets from unauthorized access, cyberattacks, and data breaches, which is of paramount importance.
Cybersecurity is pivotal in safeguarding critical information to prevent financial losses, avoid legal consequences, manage reputation, ensure business continuity, and preserve customer trust. Therefore, developing a robust security strategy must entail multi-factor authentication, insider threat detection, supply chain security, data loss prevention, and zero trust architecture, among other measures.

A Glimpse into Today’s Top Cybersecurity Threats:
The growth in cybersecurity threats is proportional to the growth of technological innovation. As technology advances, there are bad tech guys who want to misuse it for money or pleasure. Cybersecurity solution providers often suggest staying in sync with emerging cybersecurity threats today.
Ransomware Attacks: These attacks involve malware that breaches basic system security, ciphers data, and seeks ransom money from victims to restore their access. Such attacks on massive organizations have increased recently.
Phishing and Social Engineering: Phishing has been the most common way in which attackers trick victims into revealing sensitive financial information and use that information to cause financial damage to victims.
Advanced Persistent Threats (APTs): ATPs are consistent and continuous and don’t stop without disrupting operations or stealing data. Usually, enemy nations carry out such cyber attacks to put a hold on their missions.
IoT Vulnerabilities: IoT devices are usually more prone to cyberattacks, given their low-security levels and open-ended connectivity. It is usually used for data theft or blocking the services that these devices offer.
Supply Chain Attacks: Third-party apps aren’t fully security-proof. Attackers target such TPAs to enter into large organizations, aiming for data theft, stealing financial details, or business secrets, resulting in operational damages.
Zero-Day Exploits: Attackers target enterprise software that lacks security patches or is seldom updated. ZDEs are among the most dangerous attacks, as they render businesses defenseless and breach the entire system.
Cloud Security Threats: Clouds, despite their indisputable security features, are vulnerable to cyber attacks through misconfigurations or unauthorized access. The impenetrable cloud environment is the need of the hour.
AI and ML Attacks: Attackers can breach AI-powered applications and cause infrastructural damage or biased responses, or they can alter the ML algorithms to manipulate the inputs to damage automated workflows or data.
Why Cybersecurity Isn’t an Option, It’s a Necessity:
If you can leave your home unlocked, you can leave your business undefended. Although the offense is not the ideal defense in the realm of cybersecurity, there is no alternative to IT security services and an impenetrable security apparatus that protects not only the data but also the applications, networks, and infrastructure.
Today, businesses must adapt to behavioral analytics, dark web monitoring, quantum cryptography, and extended detection and response (XDR), among other cybersecurity measures, to prevent businesses from financial losses and reputational damages. Let’s understand the impact of cyberattacks on businesses.
Financial Losses: Desaster recovery costs or ransom costs are exponentially high, which may impact the ROI due to operational stagnation. It may also invite penalties from authorities for personal data theft.
Operational Disruption: If data is lost, business processes are affected. If the system is breached, operations experience downtime. Supply chain attacks may cripple the entire business activities for a long time, causing massive damage.
Reputational Damage: Trust is vital for business success. Cyberattacks are often carried out to cause reputational damage that may erode customer confidence, cripple financial systems, and damage brand position.
Legal Consequences: In addition to financial penalties, regulatory authorities may restrict benefits or market access. Businesses may become involved in legal battles over compensation to victims.
Strategic Impediment: Businesses may lose the rights to products and be severely hampered in their capabilities to innovate and grow. Moreover, operational and security costs may continue to rise, affecting profitability.
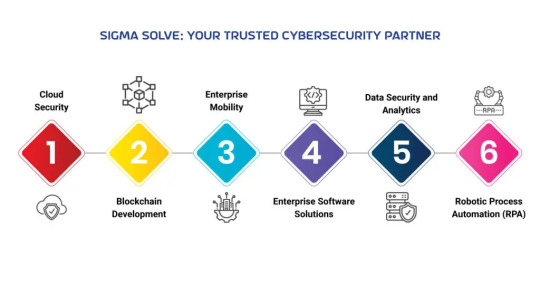
Sigma Solve: Your Trusted Cybersecurity Partner:
As digital transformation is narrowing even the virtual distance and emerging technologies are competing with humans’ cognitive capabilities, preserving the essence and securing digital assets has become the top priority for businesses across the globe.
Above and beyond growth strategies, businesses are advised by the Cybersecurity solution providers to be ready to prevent, detect, respond, and recover from cybersecurity attacks. With advanced cybersecurity innovations and tailored cybersecurity strategies, Sigma Solve delivers a Complete toolkit of strategic cybersecurity solutions entailing blockchain development services, AI-powered cybersecurity solutions, fraud detection solutions, and advanced alert systems, among others, to prevent businesses from falling prey to bad tech guys.
Artificial intelligence:
AI and automation solutions identify threat patterns to detect and respond to cyber threats. Sigma Solve developed AI security solutions to help businesses recognize and mitigate cyber threats.
Cloud Security:
Sigma Solve’s cloud consulting services entail cloud security solutions for cloud migration and cloud applications following the best practices for cloud-native cybersecurity to prevent unauthorized access.
Blockchain Development:
Our blockchain development services include measures that prevent data manipulation and ensure data validation to protect businesses from fraudulent transactions to maintain transparency and security.
Enterprise Mobility:
Sigma Solve protects remote work environments from unauthorized access and mitigates mobile threats to secure communication channels, developing robust enterprise mobility solutions.
Enterprise Software Solutions:
Integrating cybersecurity solutions in application development helps Sigma Solve protect software development, testing, and deployment against SQL injection or cross-site scripting.
Data Security and Analytics:
Data encryption, authorization, validation, and authentication are part of Sigma Solve’s data management solutions. Business intelligence and analytics solutions leverage data analytics for cybersecurity.
Robotic Process Automation (RPA):
Leveraging RPA solutions, Sigma Solve automates business processes to prevent manual entries and human errors, thus improving the efficiency and consistency of security measures.
Your Shield and Sword in the Digital Age:
The digital era demands that businesses protect themselves and mitigate cybersecurity threats to avoid business breakdown. Being your technology partner, Sigma Solve develops advanced cybersecurity solutions that leverage emerging technologies to provide head-to-toe protection.
From advanced detection to preempt resolution to disaster recovery, Sigma Solve ensures that businesses focus on their activities and leave security concerns to them. Call us at +1 954-397-0800 for a consultation to develop a tailored cybersecurity strategy for your digital assets and customer data. Original Source: https://www.sigmasolve.com/how-sigma-solve-resolves-cybersecurity-challenges/
0 notes
Text

Their cable management leaves something to be desired...
Transcript: Sun: "Gentle... Gentle Little Star. GENTLE." y/n: "Relax Sunny. You're like a mechanical junk drawer in here." Sun: "That's not our fault!!" y/n, muttering: "Then stop eating glitter glue."
No text under cut! :3

#fnaf#fnaf security breach#fnaf daycare attendant#fnaf sun moon#fnaf sun#dca fandom#fan art#digital art#artists on tumblr#sun x reader#sun x y/n#I imagine he backseats his own check ups akjfhsd#very “if i could it would be done by now” energy but mixed with the anxiety of open heart surgery (can you blame him)#you end up doing a lot of random maintenance calls to the daycare because he refuses to go to Parts and Services#.....and maybe he only trusts you...... :eyes emoji:#((a moon version is also in the works >:3c))
3K notes
·
View notes
Text
Maximizing Productivity with Google Workspace and Microsoft 365 Consulting Services

Super Cloud IT offers expert consulting services to maximize productivity with Google Workspace and Microsoft 365. Our skilled professionals optimize your digital workspace, ensuring seamless collaboration, efficient communication, and effective task management. From tailored implementation strategies to ongoing support, we empower your team to leverage the full potential of these platforms. Elevate your productivity with Super Cloud IT's comprehensive solutions, tailored to your unique business needs.
0 notes
Text
At MSP Desk, our mission is to be the trusted technology partner for small to mid-sized businesses in Toronto, ON, and the surrounding GTA area. We strive to provide comprehensive technical support and solutions that help our clients focus on what they do best while we manage all their technology needs. Our ultimate goal is to help businesses grow and achieve their full potential through the effective use of technology.
#Managed IT Services for Business#IT Security Services#Custom IT Services#Cloud Services for Business
1 note
·
View note
Text
Dorothy Wete
Website: https://weteandcompany.net/dorothy-wete/
Address: 14003 Barkham Court, Laurel, Maryland, 20707
Wete and Company, Inc is an IT consultant firm specializing in IT security. Dorothy Wete and Company focuses on strategy, organization, business processes and technology providing efficient results. Wete and Company provides the experience of a large firm with the structure and focus of a small firm catering to the client’s needs. Wete and Company strives for improving the effectiveness and efficiency of IT, while minimizing costs to businesses.
LinkedIn: https://www.linkedin.com/company/wete-&-company
1 note
·
View note
Note
Do you think Vlad would trust any servant or groom to take care of Dani?
I think it depends on how true to canon one chooses to view Vlad’s character.
Since I prefer to ignore his canon attitude toward Danielle in favor of being an actual loving parent, I think he'd be completely and personally devoted to her care.
There's also the issue of Dani being a halfa—and/or an unstable clone, requiring special attention—which I think Vlad would be hesitant to pass off to a human nanny, even if there was an NDA or other special contract in place beforehand. She's far too precious, even for a $500-per-hour au pair with sterling credentials.


"Don't worry, pumpkin, Daddy will make sure everything is perfect!"
(Daddy is exhausted from having to do everything himself)
#for the first time in his life vlad has to step up and take full responsibility. it's a matter of the utmost security#the only person i could ever see him trusting with danielle is danny#danny: what do i look like? a halfa babysitting service?#vlad: no but you're the only one i can count on to—oops look at the time see you in 5 hours thanks daniel taaa~!#asks#danny phantom#cheese melt#vlad masters#dani phantom#meta#headcanons
451 notes
·
View notes
Text

never tell yourself that you should be someone else stand up tall and say "i'm not afraid"
#daske art#fnaf#five nights at freddy's#fnaf security breach#five nights at freddy's security breach#fnaf sb#fnaf gregory#evan afton#crying child#fnaf crying child#another one for flashlight duo nation at your service
863 notes
·
View notes
Text
The base Y/N design for my soulmate AU!!
#my art#sun#fnaf#au#so(u)l#fnaf security breach#dca#daycare attendant#parts n service#parts and service#y/n#y/n design#I’m debating just posting the fanfic on tumblr until I can get an A03 up then just editing the posts to link to the ao3 later on… I think#that’s what I’m gonna do#teehee anyways cringe is dead#so(u)l art
5K notes
·
View notes
Text






wonderful day to remember ninjago has a canon highschool au
#mad as hell i posted this like two days ago and tumblr ate it then logged me out of my acc????#lloyd has dyed blue hair inspired by mr snail dood inspired by that one ninjago scriptwriter that said he would btw. if you even care#anyway there are many scenarios buzzing in my noggin about gaps in the movie i’m filling them all with hcs#like i am so sure nya could go into service or social work or law or security because shes a genius when it comes to laws and rights#but she has anger issues and she hates authority so she can’t get a job anywhere#that’s why she loves being a ninja!!#plus her steel cap boots are for stomping on people!!!#hate zane’s characterisation in the movie it’s creepy asf in this he’s just everyone’s favourite lab partner#anyway more hcs in art cominbb soon#ninjago#the lego ninjago movie#tlnm#lego ninjago#lloyd garmadon#ninjago lloyd#ninjago jay#ninjago nya#kai smith#nya smith#ninjago kai#ninjago cole#ninjago zane
5K notes
·
View notes
Text

Spictera, a premier cybersecurity company, delivers top-notch protection against cyber threats. Specializing in advanced threat detection and response, Spictera provides tailored solutions to safeguard your digital assets. Trust Spictera for comprehensive cybersecurity services that ensure the integrity and security of your business operations.
0 notes