#best object storage software
Explore tagged Tumblr posts
Text

Spictera, a premier cybersecurity company, delivers top-notch protection against cyber threats. Specializing in advanced threat detection and response, Spictera provides tailored solutions to safeguard your digital assets. Trust Spictera for comprehensive cybersecurity services that ensure the integrity and security of your business operations.
0 notes
Text
Malware I
Reveria rolled her eyes, servos clicking in a way only she could hear, blinking apathetically as she turned her music up. She understood the stares, as much as she despised them. Mugorra didn't get many synthetics like her, especially on Outer Ring trains. The long, heavy shawl she wore covered most of her slender body, both to keep the sand out of her joints and to deflect any further stares.
She wasn't exactly subtle – people of all kinds drifted through here, but being a foot taller than the average human with glowing orange eyes and an extra set of arms made one stick out.
The job was simple. Get in to the storage container, get the silver case, and get out. Perhaps a tier below the usual bloodshed for a KALI-6 class synthetic, but she was doing her best to lay low and take whatever jobs would get her least noticed.
She was trying to sit somewhat still. The case wasn't large, but it was stuffed under her shawl at the moment, and occasionally a corner poked out. She shifted her grip again, moving her hand on the handle for a more comfortable position.
ding
She heard the quiet internal chime and froze. That noise meant something had connected to her. Nothing should have been able to. The shawl had a Faraday cage sewn into the fabric, and it was snapped snug around her. Wireless signals shouldn't have been able to get through, unless-
Shit. The fucking case. She ducked down into the shawl quickly to inspect the case. When she had taken it, she hadn't looked thoroughly enough at it, and had apparently missed the quick contact port in the handle that now stared back at her, her thumb an inch from it after swiping across it when she shuffled it in her secondary arms.
[Download Requested]
Fuck. Every urge in her body was screaming at her to hurl the case away. She had to maintain a facade of order. If she got the case out of the shawl it would block the download, but she couldn't take it out without raising suspicion. This was a poor district. No one carried anything like it here. She couldn't even cancel or acknowledge the download request because she was set up for somakinetic controls and that kind of movement was out of the question.
[Download Proceeding]
What the fuck was she supposed to do about that? She couldn't contact her handler this far underground, and she doubted he'd even know how to fix a software issue with her. She'd foregone her normal backers and picked up a quick contract in the area from a sketchy Vinteran because she was trying to stay within city limits. Something had seemed wrong with him the entire briefing.
Many species got edgy around synthetics, especially KALI models, but this was something else. The whole time they talked, his eyes kept flicking to the door and across the room. Anywhere but her. She wasn't that intimidating, and most people in this business had dealt with scarier synths than her. She'd seen his arms. For as many tattoos as he had, each signifying a kill, she knew he'd seen worse.
Wait. There was another tattoo. Three triangles surrounding an S. Fuck. She sighed, more out of annoyance than actual worry. That slimy, two-faced scaly piece of shit was a Trigonalist. Of course. She'd worked with them before, but it was always born of desperate necessity. "Terrorist" was a strong term, but they weren't the best people out there.
That explained the job, then. She'd wondered why this case was being treated as so important. Lab-grown neurons were a dime a dozen, even out here, and a case that could hold maybe five or six brainslabs maximum couldn't have been worth what she was getting paid to retrieve it, especially since they were blank. But if they could get a small object inside her shawl and download something onto her, like remote access software or a location log?
Well, a KALI-6 class synthetic was decidedly not a dime a dozen anywhere.
[Download Complete]
She instinctively braced up, preparing herself. She'd been cyberattacked before, and she'd lived. She knew what to expect. It was probably going to either be excessive, disabling pop-ups or a logger she could sift through herself and cull later. Nothing too hard to handle.
She wasn't expecting the sharp, drowning techno in her ears to fade out and replace itself with soft jazz. Nor was she expecting the silk-smooth voice that seemed to rebound around the narrow train car, reverberating from everywhere and nowhere.
Hi, sweetie~
She tried to move her eyes, looking around for the speaker without moving her head.
Don't bother with that, darling, I'm still miles away from you! I'm surprised I could even get a connection down in those tunnels!
No one else seemed to be reacting to it. Everyone's faces were still cast down, trying not to make eye contact. It was too late at night for social interaction, especially with this trigger-happy crowd. Accidents happened down here all the time.
Oh, no one can hear me except you! Don't bother asking them for help. It'd be a shame if anyone were to think the big scary killsynth was attacking them. It would probably get... messy.
No one could hear the voice except for Reveria. That made it easier. If it was coming straight from an external source and being processed as speech, that was likely a remote access software. If she could activate a virus scrubber and get into a dead zone, it'd be easy enough to disable.
Oh no you don't, cutie. I'm all clientside. Besides, we're having fun, right?
She needed to know who this was. If she could hold onto this, she could take it into an Enforcement station. Granted, they likely wouldn't be happy to see her, but they'd most likely let her off for bringing in a Trigonalist. Disabling her external speakers, she cast her voice across the link.
Are you a synth? It was hard to know these days. Speech synthesizers had gotten so advanced since Reveria's assembly days.
No, I'm fully human, especially the bits that matter~
What's that supposed to mean?
Watch this! A new screen flicked open, overlaying above the occupants of the train car, showing a video at half transparency. It was enough to pick out details, at least. It just seemed to be... shapes? What was she looking at?
Oh. Oh, six suns. That was human genitalia. Close to the camera and at a strange angle, but still recognizable. Reveria watched with a combination of incredulous amazement and horror as the dripping hole a foot from her face was split open by pale, slender fingers capped with electric blue nails, index and pinky resting gently on the thighs as middle and ring curved delicately through the glistening pink flesh.
Could a synth do this? Technically yes, since most synths were modular enough to install... equipment down there, and some even accessorized with it as a fashion statement, changing it out by the day, but that was beside the point.
Is... is this live? In real time, I mean?
Obviously! Only the best for a pretty girl like you! The other hand, previously out of the camera, descended into the shot holding something that made Reveria's temperature jump up a bit.
Synths didn't really have genitalia, but plenty of aftermarket manufacturers made compatible items for them. She was ashamed to admit she owned a few of different makes and models, but a girl had needs. The voice in her head was holding one of Placebo's Bruiser models, one of Reveria's favorites. It was long and slender, with a ridged underside that featured a camouflaged electroconductive strip that boosted the signal from the partially conductive outer shell.
Said signal strength was entirely customizable for the enjoyment of the wearer, meaning when the voice ran her fingers slowly up the length then circled them around the pointed end, Reveria felt it all as she tried desperately to not buck her hips into the sensation, her body involuntarily seeking more stimulation for the appendage she didn't even have connected. Fuckin' wireless transmission...
Aww, does that feel good? Don't worry, I'll help you feel it~ Reveria tried to brace herself as the feminine words in her ear ran their fingers along the length again before angling it and pushing just the tip into herself. To the synth's immense embarrassment, she couldn't physically stop her hips from slamming forwards, immediately thanking whatever spectral forces existed that no one on the train noticed.
Oh? Someone wants me, huh? Here you go, then!
The synth stifled a scream as the voice slammed the entire length in at once, arching her back slightly for a better angle as the synth was forced to watch and feel all of it. The voice, for her part, was clearly also feeling it, as the constant noise attested. Reveria couldn't think clearly. No matter where she turned her head, she could see the human practically bouncing on it, to speak nothing of the feeling which only grew stronger as the human leaned forward. The synth could feel the human touching her, one hand on her shoulder and the other pressing her into the seat with a force that she knew wasn't real but certainly felt tangible enough.
She got a momentary relief from the constant whimpering in her ear when the brakes of the train activated, the loud screech drowning out all but the words, This is your stop! Don't miss it!
The moment the train had stopped, the needy whines returned. Reveria managed to stumble to her feet, shaking like a drunken Turvoss, and stagger off the train. She had barely made it to the platform before the fire in her midsection caught up to her and her legs practically buckled as the world was drowned out in a sea of white.
Fuck, Revi, don't just stop! I need you please don't stop now! The sensation of the length being ensheathed again was so much more powerful now, and if Reveria had been halfway lucid at this point she would have picked up on the fact that the human knew her name. As it was, that was far more thinking than she was capable of. All she could think about was getting home. She managed to pool her brain function enough to find and activate the tracker beacon in her rented room, the slender white line tracing out a path in front of her that she attempted to follow, one step at a time.
The feeling was overwhelming her. It was unprofessional, but she needed some time alone. If she had anything attached to relieve herself with, she likely would have lost her composure and done it right there in the station. As it was, she just moved through the station as fast as she could, shaky, desperate movements drawing stares that she was too deep in a world of need to notice or care about.
She was halfway up the stairs to exit the station when it happened again, her entire body twitching hard then going limp as she frantically grabbed a rail to avoid falling. The voice just laughed in her ear as she did. It was only three blocks to her building. She could make it.
She wasn't even up the stairs when the next one hit. They were getting faster and faster, her increased sensitivity after each making it easier to drive her over the edge for the next.
You gotta get home, okay? I need you to pick something out and fuck me for real~
Three blocks. It was three blocks.
This was the door. The white strip on the street took a sharp left through the narrow arch. She crossed the threshold, holding the doorframe for support as she climaxed again. How many times had she? Thinking about it was too hard. There was nothing in her head anymore except for that delicious whimpering that seemed to increase in intensity along with her. She just had to take the elevator up to the eighth floor and get into her room, then she could cut the signal.
The hallway looked the same as it always did. Bare. Stumbling to her door, she tried the knob. Locked. She just snapped it off. Any measure or restriction of her own strength was gone. The door swung open.
Something was wrong. Her brain was getting sluggish, but she retained enough evidence to realize this wasn't her room. The sand-brown walls she should have seen were dark and lit with purple LEDs, and the furniture was all arranged wrong. Soft jazz was playing.
She had a sudden break of clarity, and felt cold all of a sudden as the figure sitting in the back of the room, lit from behind by a computer monitor, pulled the toy from within herself and tossed it over. Reveria's hand instinctively shot up and caught it, the liquid on it glinting in the harsh hallway light. She checked the tracker beacon she had been following. Where she had expected reveria.home in the namespace, she saw instead DEN1ZEN. This wasn't her building.
Hi, Revi~
#monster fucker#terato#hypnosis#(kinda)#synthetic#robot#robotification#robotization#wlw nsft#exhibition#fantasy nsft#sci fi nsft
239 notes
·
View notes
Text
Why Scribbook is the best writing tool I know

At least it's the best for me. Your mileage may vary, etc. etc.
Scribbook is an online writing studio (it doesn't have an app as far as I'm aware), developed in French by one guy, and can be accessed here.
it's FREE
You heard me. The first 5 MO are, at least. After that there's a paid option that unlocks a few other features along with more storage space, but it took me 4 years to even reach that milestone. So you're good.
2. It has all the things you need to write
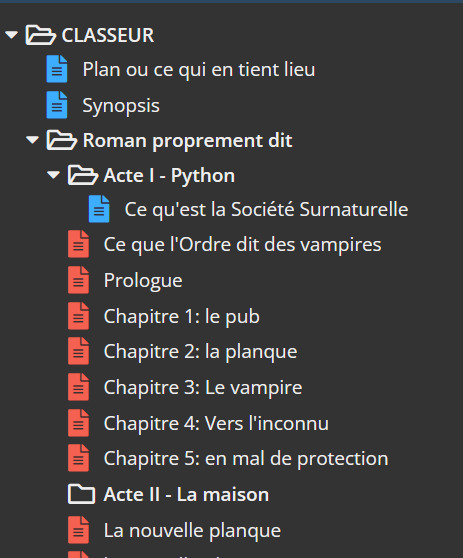

Some people are organized. And then there's me.
At the very beginning, you can chose a template for your novel (or just start from scratch). From there, you can create files, scenes, etc. and just move them around (a map view is available, which might be useful to some others than me). Also the option to write the synopsis on a text file. Personally I use that to write notes to myself for future editing.
The rest is basic, important stuff: text formatting, page breaks, etc. There's a sepia and a dark mode as well.
3. You can write anywhere
Unlike Scrivener, you can access it from any computer or phone, and unlike Google docs, it won't suggest stupid edits and/or spy on you. Very useful when you're on the go and writing at work writing in the break room.
4. It doesn't have TOYS
Toys are what I call things that are not mandatory for your writing project but are so fun to use and so good at make you think you're being productive when in fact you're just procrastinating. You know what I'm talking about: family trees, map editor, encyclopedia, etc. Apart from a verse counter (which makes writing alexandrins very easy) and an option for character pages, nothing of the sort here. You're here to WRITE, not to pretend to write. Oh, and there's a fullscreen mode to avoid distraction. A godsend.
5. You can set objectives and see your progress
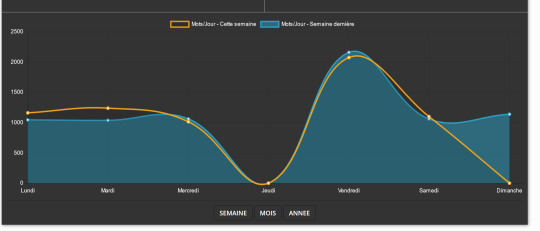
The consistency of a persistent hunter
There's a wordcount and you can chose to set it as you like. 300 words a day, 1000 a week, 8000 a month, whatever. I found it very good to condition myself to write; now I just know that 1 hour of work = roughly 1000 words. You're also rewarded by a nice graphic that tells you how much you've worked this week, month or year.
To summarize, I'd say that while some won't like the fact that you're writing on a website and not on your own computer, the pros outweight the cons. It's a free tool, with the same functionalities as a paid software like Scrivener or Campfire, and it's in French, so yay baguette
5 notes
·
View notes
Video
youtube
Complete Hands-On Guide: Upload, Download, and Delete Files in Amazon S3 Using EC2 IAM Roles
Are you looking for a secure and efficient way to manage files in Amazon S3 using an EC2 instance? This step-by-step tutorial will teach you how to upload, download, and delete files in Amazon S3 using IAM roles for secure access. Say goodbye to hardcoding AWS credentials and embrace best practices for security and scalability.
What You'll Learn in This Video:
1. Understanding IAM Roles for EC2: - What are IAM roles? - Why should you use IAM roles instead of hardcoding access keys? - How to create and attach an IAM role with S3 permissions to your EC2 instance.
2. Configuring the EC2 Instance for S3 Access: - Launching an EC2 instance and attaching the IAM role. - Setting up the AWS CLI on your EC2 instance.
3. Uploading Files to S3: - Step-by-step commands to upload files to an S3 bucket. - Use cases for uploading files, such as backups or log storage.
4. Downloading Files from S3: - Retrieving objects stored in your S3 bucket using AWS CLI. - How to test and verify successful downloads.
5. Deleting Files in S3: - Securely deleting files from an S3 bucket. - Use cases like removing outdated logs or freeing up storage.
6. Best Practices for S3 Operations: - Using least privilege policies in IAM roles. - Encrypting files in transit and at rest. - Monitoring and logging using AWS CloudTrail and S3 access logs.
Why IAM Roles Are Essential for S3 Operations: - Secure Access: IAM roles provide temporary credentials, eliminating the risk of hardcoding secrets in your scripts. - Automation-Friendly: Simplify file operations for DevOps workflows and automation scripts. - Centralized Management: Control and modify permissions from a single IAM role without touching your instance.
Real-World Applications of This Tutorial: - Automating log uploads from EC2 to S3 for centralized storage. - Downloading data files or software packages hosted in S3 for application use. - Removing outdated or unnecessary files to optimize your S3 bucket storage.
AWS Services and Tools Covered in This Tutorial: - Amazon S3: Scalable object storage for uploading, downloading, and deleting files. - Amazon EC2: Virtual servers in the cloud for running scripts and applications. - AWS IAM Roles: Secure and temporary permissions for accessing S3. - AWS CLI: Command-line tool for managing AWS services.
Hands-On Process: 1. Step 1: Create an S3 Bucket - Navigate to the S3 console and create a new bucket with a unique name. - Configure bucket permissions for private or public access as needed.
2. Step 2: Configure IAM Role - Create an IAM role with an S3 access policy. - Attach the role to your EC2 instance to avoid hardcoding credentials.
3. Step 3: Launch and Connect to an EC2 Instance - Launch an EC2 instance with the IAM role attached. - Connect to the instance using SSH.
4. Step 4: Install AWS CLI and Configure - Install AWS CLI on the EC2 instance if not pre-installed. - Verify access by running `aws s3 ls` to list available buckets.
5. Step 5: Perform File Operations - Upload files: Use `aws s3 cp` to upload a file from EC2 to S3. - Download files: Use `aws s3 cp` to download files from S3 to EC2. - Delete files: Use `aws s3 rm` to delete a file from the S3 bucket.
6. Step 6: Cleanup - Delete test files and terminate resources to avoid unnecessary charges.
Why Watch This Video? This tutorial is designed for AWS beginners and cloud engineers who want to master secure file management in the AWS cloud. Whether you're automating tasks, integrating EC2 and S3, or simply learning the basics, this guide has everything you need to get started.
Don’t forget to like, share, and subscribe to the channel for more AWS hands-on guides, cloud engineering tips, and DevOps tutorials.
#youtube#aws iamiam role awsawsaws permissionaws iam rolesaws cloudaws s3identity & access managementaws iam policyDownloadand Delete Files in Amazon#IAMrole#AWS#cloudolus#S3#EC2
2 notes
·
View notes
Text
"DCA"(DIPLOMA IN COMPUTER APPLICATION)
The best career beginning course....

Golden institute is ISO 9001-2015 certified institute. Here you can get all types of computer courses such as DCA, CFA , Python, Digital marketing, and Tally prime . Diploma in Computer Applications (DCA) is a 1 year "Diploma Course" in the field of Computer Applications which provides specialization in various fields such as Fundamentals & Office Productivity tools, Graphic Design & Multimedia, Programming and Functional application Software.

A few of the popular DCA study subjects are listed below
Basic internet concepts Computer Fundamentals Introduction to programming Programming in C RDBMS & Data Management Multimedia Corel draw Tally ERP 9.0 Photoshop
Benefits of Diploma in Computer Application (DCA)
After completion of the DCA course student will able to join any computer jobs with private and government sectors. The certification of this course is fully valid for any government and private deportment worldwide. DCA is the only best option for the student to learn computer skills with affordable fees.
DCA Computer course : Eligibilities are here... Students aspiring to pursue Diploma in Computer Applications (DCA) course must have completed their higher school/ 10 + 2 from a recognized board. Choosing Computers as their main or optional subject after class 10 will give students an additional edge over others. Apart from this no other eligibility criteria is set for aspirants. No minimum cutoff is required.

"TALLY"
A Tally is accounting software. To pursue Tally Course (Certificate and Diploma) you must have certain educational qualifications to thrive and prosper. The eligibility criteria for the tally course is given below along with all significant details on how to approach learning Tally, and how you can successfully complete the course. Generally, the duration of a Tally course is 6 month to 1 year ,but it varies depending on the tally institution you want to join. Likewise, tally course fees are Rs. 10000-20000 on average but it also varies depending on what type of tally course or college you opt for. accounting – Accounting plays a pivotal role in Tally
Key Benefits of the Course:
Effective lessons (topics are explained through a step-by-step process in a very simple language) The course offers videos and e-books (we have two options Video tutorials in Hindi2. e-book course material in English) It offers a planned curriculum (the entire tally online course is designed to meet the requirements of the industry.) After the completion of the course, they offer certificates to the learners.
Tally Course Syllabus – Subjects To Learn Accounting Payroll Taxation Billing Banking Inventory
Tally Course
Eligibility criteria: 10+2 in commerce stream Educational level: Certificate or Diploma Course fee: INR 2200-5000 Skills required: Accounting, Finance, Taxation, Interpersonal Skills Scope after the course: Accountant, Finance Manager, Chartered Accountant, Executive Assistant, Operations Manager Average salary: INR 5,00,000 – 10,00,000

"In this Python course"
Rapidly develop feature-rich applications using Python's built-in statements, functions, and collection types. Structure code with classes, modules, and packages that leverage object-oriented features. Create multiple data accessors to manage various data storage formats. Access additional features with library modules and packages.
Python for Web Development – Flask Flask is a popular Python API that allows experts to build web applications. Python 2.6 and higher variants must install Flask, and you can import Flask on any Python IDE from the Flask package. This section of the course will help you install Flask and learn how to use the Python Flask Framework.
Subjects covered in Python for Web development using Flask:
Introduction to Python Web Framework Flask Installing Flask Working on GET, POST, PUT, METHODS using the Python Flask Framework Working on Templates, render template function
Python course fees and duration
A Python course costs around ₹2200-5000.This course fees can vary depending on multiple factors. For example, a self-paced online course will cost you less than a live interactive online classroom session, and offline training sessions are usually expensive ones. This is mainly because of the trainers’ costs, lab assistance, and other facilities.
Some other factors that affect the cost of a Python course are its duration, course syllabus, number of practical sessions, institute reputation and location, trainers’ expertise, etc. What is the duration of a Python course? The duration of a basic Python course is generally between 3 month to 6 months, and advanced courses can be 1 year . However, some courses extend up to 1 year and more when they combine multiple other courses or include internship programs.
Advantages of Python Python is easy to learn and put into practice. … Functions are defined. … Python allows for quick coding. … Python is versatile. … Python understands compound data types. … Libraries in data science have Python interfaces. … Python is widely supported.

"GRAPHIC DESIGN"
Graphic design, in simple words, is a means that professional individuals use to communicate their ideas and messages. They make this communication possible through the means of visual media.
A graphic designing course helps aspiring individuals to become professional designers and create visual content for top institutions around the world. These courses are specialized to accommodate the needs and requirements of different people. The course is so popular that one does not even need to do a lot of research to choose their preferred colleges, institutes, or academies for their degrees, as they are almost mainstream now.
A graphic design course have objectives:
To train aspirants to become more creative with their visual approach. To train aspirants to be more efficient with the technical aspects of graphics-related tasks and also to acquaint them with relevant aspects of a computer. To train individuals about the various aspects of 2-D and 3-D graphics. To prepare aspirants to become fit for a professional graphic designing profession.
Which course is best for graphic design? Best graphic design courses after 12th - Graphic … Certificate Courses in Graphic Design: Adobe Photoshop. CorelDraw. InDesign. Illustrator. Sketchbook. Figma, etc.
It is possible to become an amateur Graphic Designer who is well on the road to becoming a professional Graphic Designer in about three months. In short, three months is what it will take to receive the professional training required to start building a set of competitive professional job materials.

THE BEST COMPUTER INSTITUTE GOLDEN EDUCATION,ROPNAGAR "PUNJAB"
The best mega DISCOUNT here for your best course in golden education institute in this year.
HURRY UP! GUYS TO JOIN US...
Don't miss the chance
You should go to our institute website
WWW.GOLDEN EDUCATION
CONTACT US: 98151-63600
VISIT IT:
#GOLDEN EDUCATION#INSTITUTE#COURSE#career#best courses#tallyprime#DCA#GRAPHICAL#python#ALL COURSE#ROOPAR
2 notes
·
View notes
Text
Journey to AWS Proficiency: Unveiling Core Services and Certification Paths
Amazon Web Services, often referred to as AWS, stands at the forefront of cloud technology and has revolutionized the way businesses and individuals leverage the power of the cloud. This blog serves as your comprehensive guide to understanding AWS, exploring its core services, and learning how to master this dynamic platform. From the fundamentals of cloud computing to the hands-on experience of AWS services, we'll cover it all. Additionally, we'll discuss the role of education and training, specifically highlighting the value of ACTE Technologies in nurturing your AWS skills, concluding with a mention of their AWS courses.

The Journey to AWS Proficiency:
1. Basics of Cloud Computing:
Getting Started: Before diving into AWS, it's crucial to understand the fundamentals of cloud computing. Begin by exploring the three primary service models: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Gain a clear understanding of what cloud computing is and how it's transforming the IT landscape.
Key Concepts: Delve into the key concepts and advantages of cloud computing, such as scalability, flexibility, cost-effectiveness, and disaster recovery. Simultaneously, explore the potential challenges and drawbacks to get a comprehensive view of cloud technology.
2. AWS Core Services:
Elastic Compute Cloud (EC2): Start your AWS journey with Amazon EC2, which provides resizable compute capacity in the cloud. Learn how to create virtual servers, known as instances, and configure them to your specifications. Gain an understanding of the different instance types and how to deploy applications on EC2.
Simple Storage Service (S3): Explore Amazon S3, a secure and scalable storage service. Discover how to create buckets to store data and objects, configure permissions, and access data using a web interface or APIs.
Relational Database Service (RDS): Understand the importance of databases in cloud applications. Amazon RDS simplifies database management and maintenance. Learn how to set up, manage, and optimize RDS instances for your applications. Dive into database engines like MySQL, PostgreSQL, and more.
3. AWS Certification:
Certification Paths: AWS offers a range of certifications for cloud professionals, from foundational to professional levels. Consider enrolling in certification courses to validate your knowledge and expertise in AWS. AWS Certified Cloud Practitioner, AWS Certified Solutions Architect, and AWS Certified DevOps Engineer are some of the popular certifications to pursue.
Preparation: To prepare for AWS certifications, explore recommended study materials, practice exams, and official AWS training. ACTE Technologies, a reputable training institution, offers AWS certification training programs that can boost your confidence and readiness for the exams.
4. Hands-on Experience:
AWS Free Tier: Register for an AWS account and take advantage of the AWS Free Tier, which offers limited free access to various AWS services for 12 months. Practice creating instances, setting up S3 buckets, and exploring other services within the free tier. This hands-on experience is invaluable in gaining practical skills.
5. Online Courses and Tutorials:
Learning Platforms: Explore online learning platforms like Coursera, edX, Udemy, and LinkedIn Learning. These platforms offer a wide range of AWS courses taught by industry experts. They cover various AWS services, architecture, security, and best practices.
Official AWS Resources: AWS provides extensive online documentation, whitepapers, and tutorials. Their website is a goldmine of information for those looking to learn more about specific AWS services and how to use them effectively.
Amazon Web Services (AWS) represents an exciting frontier in the realm of cloud computing. As businesses and individuals increasingly rely on the cloud for innovation and scalability, AWS stands as a pivotal platform. The journey to AWS proficiency involves grasping fundamental cloud concepts, exploring core services, obtaining certifications, and acquiring practical experience. To expedite this process, online courses, tutorials, and structured training from renowned institutions like ACTE Technologies can be invaluable. ACTE Technologies' comprehensive AWS training programs provide hands-on experience, making your quest to master AWS more efficient and positioning you for a successful career in cloud technology.
8 notes
·
View notes
Text
Responsive Design and Beyond: Exploring the Latest Trends in Web Development Services
The two things ruling the present scenario are the internet and smartphones. The easier they are making the lifestyle of the consumers the more difficult it becomes for the lives of the business owners. Digitization has resulted in the rise of competition from the local level to the national and international levels. The businesses that are not adopting the culture are lagging far behind in the growth cycle. The only way to get along with the pace is to hire a custom web development service that is capable of meeting the needs of both the business and consumers. The blog aims to explore some such services that are redefining the web development world.
Latest Trends in the Web Development Services
Blockchain Technology
Blockchain is an encrypted database storing system. It stores information in blocks, which are then joined as a chain. It makes transactions more secure and error-free. The technology enables the participants to make transactions across the internet without the interference of a third party. Thus, this technology can potentially revolutionize different business sectors by reducing the risks of cybercrimes. The technology allows web developers to use open-source systems for their projects, hence simplifying the development process.
Internet of Things (IoT)
IoT can be defined as a network of internet-enabled devices, where data transfer requires no human involvement. It is capable of providing a future where objects are connected to the web. IoT fosters constant data transfer. Moreover, IoT can be used to create advanced communication between different operational models and website layouts. The technology also comes with broad applications like cameras, sensors, and signaling equipment to list a few.
Voice Search Optimization
Voice search optimization is the process of optimizing web pages to appear in voice search. . In the field of web development, the latest innovations are voice-activated self-standing devices, and voice optimization for apps and websites. The technology is being developed that will be able to recognize the voices of different people and provide a personalized AI-based experience
AI-Powered Chatbots
AI-powered chatbot uses Natural Language Processing (NLP) and Machine Learning (ML) to better understand the user’s intent and provide a human-like experience. These have advanced features like 24×7 problem-solving skills and behavior analytics capabilities. These can be effectively used fo customer support to increase customer satisfaction. An AI-powered chatbot can easily be integrated into regular/professional websites and PWAs. Chatbots generally provide quick answers in an emergency and are quick to resolve complaints.
Cloud Computing
It is the use of cloud-based resources such as storage, networking, software, analytics, and intelligence for flexibility and convenience. These services are more reliable as they are backed up and replicated across multiple data centers. This ensures that web applications are always available and running. It is highly efficient for remote working setups. The technology helps avoid data loss and data overload. It also has a low development costs, robust architecture and offers flexibility.
Book a Web Development Service Provider Now
So, if you are also excited to bring your business online and on other tech platforms but are confused about how to do that, you are recommended to reach out to one of the best web development companies i.e. Encanto Technologies. They have a professional and competent web development team that would assist you in the development of an aesthetic, functional, and user-friendly website that would take your revenue to new heights. So, do not wait to enter the online world and book the services of OMR Digital now.
Author’s Bio
This blog is authored by the proactive content writers of Encanto Technologies. It is one of the best professional web development services that embodies a cluster of services including web development, mobile application development, desktop application development, DevOps CI/ CD services, big data development, and cloud development services. So, if you are also looking for any of the web and app development services do not delay any further and contact OMR Digital now.
2 notes
·
View notes
Text
Inventory Management in Manufacturing: How ERP Software Can Help
In the dynamic domain of manufacturing, proficient inventory management plays a crucial role in achieving operational success. Manufacturers endeavour to achieve a nuanced equilibrium between fulfilling customer demand, reducing expenses, and maximising overall operational efficiency. The maintenance of this delicate equilibrium relies on the implementation of efficient and accurate inventory management procedures. In contemporary times, the utilisation of Enterprise Resource Planning (ERP) software has emerged as a paradigm-shifting instrument, fundamentally altering the manner in which manufacturers do inventory management. Stay ahead in the competitive manufacturing landscape. Streamline operations with ERP manufacturing software for small businesses designed and developed by STERP (Shanti Technology).

This blog post explores the complexities of inventory management within the manufacturing industry and emphasises the crucial role that Enterprise Resource Planning (ERP) software plays in enhancing the efficiency of this vital component.
Understanding the Significance of Inventory Management in Manufacturing:
Inventory management encompasses the supervision of a company's inventory, with the objective of optimising the utilisation and replenishment of stockpiled products, while also maximising their overall value. Inventory in the manufacturing industry encompasses three main components: raw materials, work-in-progress (WIP), and finished products. Ensuring an appropriate equilibrium of these constituents is of utmost importance for a multitude of reasons:
· Customer Satisfaction and Demand Fulfillment:
Meeting client demand is crucial for achieving success in the company. The timely availability of appropriate inventory plays a crucial role in ensuring the prompt fulfilment of orders, hence enhancing customer satisfaction and cultivating enduring customer relationships.
· Cost Optimization:
Effective inventory management plays a crucial role in minimising carrying costs, encompassing expenses related to storage, insurance, and obsolescence. This practice guarantees that capital is not needlessly tied up and reduces the likelihood of both excessive inventory and insufficient inventory.
· Production Efficiency:
Production efficiency refers to the ability to maintain an appropriate level of raw materials and components in order to ensure smooth production operations and minimise disruptions caused by material shortages.
· Insightful Decision-making:
The acquisition of precise data regarding inventory levels and patterns offers significant advantages in terms of strategic planning, demand forecasting, and procurement decision-making.
ERP Software for Inventory Management:
Enterprise Resource Planning (ERP) software is designed to consolidate and streamline several corporate operations and functions inside a unified system. Empower your small manufacturing enterprise. Take control of production, inventory, etc. with STERP’s best ERP software for small manufacturing businesses.
In the realm of manufacturing, Enterprise Resource Planning (ERP) assumes a crucial function in augmenting inventory management through the utilisation of the following mechanisms:
· Real-time Inventory Tracking and Visibility:
Real-time inventory tracking and visibility are facilitated by enterprise resource planning (ERP) systems, which offer instantaneous information regarding inventory quantities, locations, and movements. The increased level of visibility enables producers to make well-informed decisions promptly, hence decreasing the probability of experiencing stockouts or having excessive inventory.
· Accurate Demand Forecasting:
Accurate demand forecasting is achieved through the utilisation of advanced analytics and historical data within Enterprise Resource Planning (ERP) systems. This practice guarantees that the manufacturing and procurement processes are in accordance with market demands, hence mitigating the risk of excessive inventory or insufficient supply.
· Automated Reordering and Restocking:
Enterprise Resource Planning (ERP) software facilitates the automation of the reordering process by initiating purchase orders for raw materials or components when inventory levels decline below specified criteria. This automated process enhances operational efficiency and reduces the occurrence of human errors.
· Optimized Order Management:
Efficient order management is facilitated by the integration of order processing and inventory data within an Enterprise Resource Planning (ERP) system. Manufacturers possess the power to allocate priority to orders by considering factors such as the availability of inventory, production capacity, and customer-imposed deadlines. Experience hassle-free manufacturing operations. STERP’s ERP software for the manufacturing industry is designed for manufacturing businesses, providing the tools you need to succeed.
· Enhanced Supplier Collaboration:
Enterprise Resource Planning (ERP) systems provide efficient and effective communication with suppliers, thereby promoting a smooth and uninterrupted flow of goods and services within the supply chain. Manufacturers have the capability to exchange real-time inventory information with suppliers, thereby facilitating enhanced planning and collaboration.
· Effective Risk Management:
The utilisation of Enterprise Resource Planning (ERP) systems facilitates the identification and mitigation of hazards pertaining to the management of inventories. This includes the identification of inventory that is moving at a slow pace, the possibility of becoming obsolete, or irregularities in the quantities of stock.
Maximizing Efficiency with ERP-Enabled Inventory Management:
The utilisation of Enterprise Resource Planning (ERP) software in inventory management enables firms to enhance operational efficiency, decrease expenses, and enhance customer satisfaction. This innovative technology facilitates the adaptation of enterprises to evolving market conditions, enabling them to achieve continuous growth and enhance their competitiveness within the manufacturing industry. The adoption of ERP software for comprehensive inventory management in the evolving manufacturing industry is not merely discretionary, but rather a strategic need. To maintain a competitive advantage, it is imperative to incorporate Enterprise Resource Planning (ERP) systems into manufacturing operations, as this enables the realisation of optimised inventory management capabilities. Enhance productivity without the complexity with STERP’s ERP for manufacturing company – a software specially tailored for manufacturing businesses to simplify the business processes.
#Manufacturing software for small business#Best ERP for small manufacturing business#ERP software for manufacturing industry#ERP for manufacturing company
6 notes
·
View notes
Text
WILL CONTAINER REPLACE HYPERVISOR
As with the increasing technology, the way data centers operate has changed over the years due to virtualization. Over the years, different software has been launched that has made it easy for companies to manage their data operating center. This allows companies to operate their open-source object storage data through different operating systems together, thereby maximizing their resources and making their data managing work easy and useful for their business.
Understanding different technological models to their programming for object storage it requires proper knowledge and understanding of each. The same holds for containers as well as hypervisor which have been in the market for quite a time providing companies with different operating solutions.
Let’s understand how they work
Virtual machines- they work through hypervisor removing hardware system and enabling to run the data operating systems.
Containers- work by extracting operating systems and enable one to run data through applications and they have become more famous recently.

Although container technology has been in use since 2013, it became more engaging after the introduction of Docker. Thereby, it is an open-source object storage platform used for building, deploying and managing containerized applications.
The container’s system always works through the underlying operating system using virtual memory support that provides basic services to all the applications. Whereas hypervisors require their operating system for working properly with the help of hardware support.
Although containers, as well as hypervisors, work differently, have distinct and unique features, both the technologies share some similarities such as improving IT managed service efficiency. The profitability of the applications used and enhancing the lifecycle of software development.
And nowadays, it is becoming a hot topic and there is a lot of discussion going on whether containers will take over and replace hypervisors. This has been becoming of keen interest to many people as some are in favor of containers and some are with hypervisor as both the technologies have some particular properties that can help in solving different solutions.
Let’s discuss in detail and understand their functioning, differences and which one is better in terms of technology?
What are virtual machines?
Virtual machines are software-defined computers that run with the help of cloud hosting software thereby allowing multiple applications to run individually through hardware. They are best suited when one needs to operate different applications without letting them interfere with each other.
As the applications run differently on VMs, all applications will have a different set of hardware, which help companies in reducing the money spent on hardware management.
Virtual machines work with physical computers by using software layers that are light-weighted and are called a hypervisor.
A hypervisor that is used for working virtual machines helps in providing fresh service by separating VMs from one another and then allocating processors, memory and storage among them. This can be used by cloud hosting service providers in increasing their network functioning on nodes that are expensive automatically.
Hypervisors allow host machines to have different operating systems thereby allowing them to operate many virtual machines which leads to the maximum use of their resources such as bandwidth and memory.

What is a container?
Containers are also software-defined computers but they operate through a single host operating system. This means all applications have one operating center that allows it to access from anywhere using any applications such as a laptop, in the cloud etc.
Containers use the operating system (OS) virtualization form, that is they use the host operating system to perform their function. The container includes all the code, dependencies and operating system by itself allowing it to run from anywhere with the help of cloud hosting technology.
They promised methods of implementing infrastructure requirements that were streamlined and can be used as an alternative to virtual machines.
Even though containers are known to improve how cloud platforms was developed and deployed, they are still not as secure as VMs.
The same operating system can run different containers and can share their resources and they further, allow streamlining of implemented infrastructure requirements by the system.
Now as we have understood the working of VMs and containers, let’s see the benefits of both the technologies
Benefits of virtual machines
They allow different operating systems to work in one hardware system that maintains energy costs and rack space to cooling, thereby allowing economical gain in the cloud.
This technology provided by cloud managed services is easier to spin up and down and it is much easier to create backups with this system.
Allowing easy backups and restoring images, it is easy and simple to recover from disaster recovery.
It allows the isolated operating system, hence testing of applications is relatively easy, free and simple.

Benefits of containers:
They are light in weight and hence boost significantly faster as compared to VMs within a few seconds and require hardware and fewer operating systems.
They are portable cloud hosting data centers that can be used to run from anywhere which means the cause of the issue is being reduced.
They enable micro-services that allow easy testing of applications, failures related to the single point are reduced and the velocity related to development is increased.
Let’s see the difference between containers and VMs
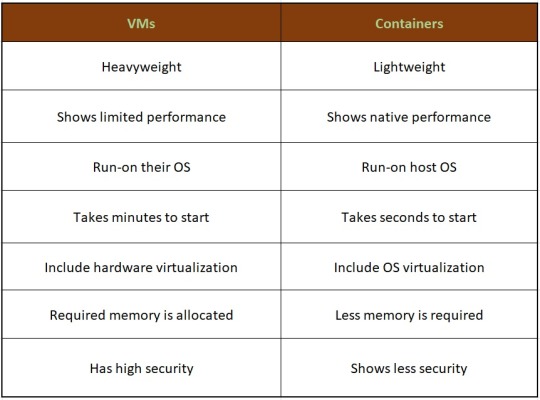
Hence, looking at all these differences one can make out that, containers have added advantage over the old virtualization technology. As containers are faster, more lightweight and easy to manage than VMs and are way beyond these previous technologies in many ways.
In the case of hypervisor, virtualization is performed through physical hardware having a separate operating system that can be run on the same physical carrier. Hence each hardware requires a separate operating system to run an application and its associated libraries.
Whereas containers virtualize operating systems instead of hardware, thereby each container only contains the application, its library and dependencies.
Containers in a similar way to a virtual machine will allow developers to improve the CPU and use physical machines' memory. Containers through their managed service provider further allow microservice architecture, allowing application components to be deployed and scaled more granularly.

As we have seen the benefits and differences between the two technologies, one must know when to use containers and when to use virtual machines, as many people want to use both and some want to use either of them.
Let’s see when to use hypervisor for cases such as:
Many people want to continue with the virtual machines as they are compatible and consistent with their use and shifting to containers is not the case for them.
VMs provide a single computer or cloud hosting server to run multiple applications together which is only required by most people.
As containers run on host operating systems which is not the case with VMs. Hence, for security purposes, containers are not that safe as they can destroy all the applications together. However, in the case of virtual machines as it includes different hardware and belongs to secure cloud software, so only one application will be damaged.
Container’s turn out to be useful in case of,
Containers enable DevOps and microservices as they are portable and fast, taking microseconds to start working.
Nowadays, many web applications are moving towards a microservices architecture that helps in building web applications from managed service providers. The containers help in providing this feature making it easy for updating and redeploying of the part needed of the application.
Containers contain a scalability property that automatically scales containers, reproduces container images and spin them down when they are not needed.
With increasing technology, people want to move to technology that is fast and has speed, containers in this scenario are way faster than a hypervisor. That also enables fast testing and speed recovery of images when a reboot is performed.

Hence, will containers replace hypervisor?
Although both the cloud hosting technologies share some similarities, both are different from each other in one or the other aspect. Hence, it is not easy to conclude. Before making any final thoughts about it, let's see a few points about each.

Still, a question can arise in mind, why containers?
Although, as stated above there are many reasons to still use virtual machines, containers provide flexibility and portability that is increasing its demand in the multi-cloud platform world and the way they allocate their resources.
Still today many companies do not know how to deploy their new applications when installed, hence containerizing applications being flexible allow easy handling of many clouds hosting data center software environments of modern IT technology.
These containers are also useful for automation and DevOps pipelines including continuous integration and continuous development implementation. This means containers having small size and modularity of building it in small parts allows application buildup completely by stacking those parts together.
They not only increase the efficiency of the system and enhance the working of resources but also save money by preferring for operating multiple processes.
They are quicker to boost up as compared to virtual machines that take minutes in boosting and for recovery.
Another important point is that they have a minimalistic structure and do not need a full operating system or any hardware for its functioning and can be installed and removed without disturbing the whole system.
Containers replace the patching process that was used traditionally, thereby allowing many organizations to respond to various issues faster and making it easy for managing applications.
As containers contain an operating system abstract that operates its operating system, the virtualization problem that is being faced in the case of virtual machines is solved as containers have virtual environments that make it easy to operate different operating systems provided by vendor management.
Still, virtual machines are useful to many
Although containers have more advantages as compared to virtual machines, still there are a few disadvantages associated with them such as security issues with containers as they belong to disturbed cloud software.
Hacking a container is easy as they are using single software for operating multiple applications which can allow one to excess whole cloud hosting system if breaching occurs which is not the case with virtual machines as they contain an additional barrier between VM, host server and other virtual machines.
In case the fresh service software gets affected by malware, it spreads to all the applications as it uses a single operating system which is not the case with virtual machines.
People feel more familiar with virtual machines as they are well established in most organizations for a long time and businesses include teams and procedures that manage the working of VMs such as their deployment, backups and monitoring.
Many times, companies prefer working with an organized operating system type of secure cloud software as one machine, especially for applications that are complex to understand.
Conclusion
Concluding this blog, the final thought is that, as we have seen, both the containers and virtual machine cloud hosting technologies are provided with different problem-solving qualities. Containers help in focusing more on building code, creating better software and making applications work on a faster note whereas, with virtual machines, although they are slower, less portable and heavy still people prefer them in provisioning infrastructure for enterprise, running legacy or any monolithic applications.
Stating that, if one wants to operate a full operating system, they should go for hypervisor and if they want to have service from a cloud managed service provider that is lightweight and in a portable manner, one must go for containers.
Hence, it will take time for containers to replace virtual machines as they are still needed by many for running some old-style applications and host multiple operating systems in parallel even though VMs has not had so cloud-native servers. Therefore, it can be said that they are not likely to replace virtual machines as both the technologies complement each other by providing IT managed services instead of replacing each other and both the technologies have a place in the modern data center.
For more insights do visit our website
#container #hypervisor #docker #technology #zybisys #godaddy
6 notes
·
View notes
Text
Understanding Data Encryption and Classification for Effective Data Rights Management
Introduction:
Nowadays, data security has become a top priority. As the data is generated and shared more exponentially, the safeguarding of sensitive information has become more challenging while being crucial. Data encryption and classification are the two major aspects of data rights, and they play a leading part in protecting information from involuntary or Best geofence storage service and in compliance with privacy laws.

What is Data Encryption?
Data encryption is like putting your information in a safe, but it is a digital safe. This process entails encoding the plain text into an illegible text referred to as ciphertext with a specific algorithm and key. This procedure makes sure that even if somebody who's not authorized is granted access to the data, they will still not be able to decrypt it without the corresponding decryption key.
Imagine that you want to send a secret message to your friend. Instead of writing the message clearly, you mix it up using some secret code that only you and your friend know. Without the key, any interposition would only yield nonsensical letters.
What is Data Classification?
Data classification is grouping the data according to its level of sensitivity and significance. It also allows organizations to categorize their data holdings and decide which data needs to be protected at what level. Classification is usually done by tagging data with a label that identifies its security requirements or handling process.
Data classification is like putting your stuff into different boxes. All your important documents might go into a folder, another for pictures and one for miscellaneous notes. Every folder is labelled to indicate what paperwork is inside of it and how you should handle it.
Effective Data Rights Management
Encrypting and classifying data are crucial in the context of the formulation of advice on the management of data rights with the objective of attaining maximum data protection and regulatory compliance. Here's how they work together, Here's how they work together:
Data Identification:
This high classification facilitates to define the sensitive data that needs to be encrypted conveniently. By splitting the data into groups according to the application of encryption technologies, information systems can address the shortage of encryption means and distribute the resources in a reasonable way.
Access Control:
Encryption is a safeguard against unpermitted access, and people with classification rights choose who to give access to encoded information. The access controls can build on data classification labels so that only the laid-out clearance users, possessing the proper clearance can unscramble the cipher and access sensitive information.

Conclusion:
The use of data encryption and classification forms part of comprehensive data rights management plans. Encryption works to make Best Database Backup Services only accessible to authorized people. While at the same time, sensitivity labels can be used to classify easy-to-reach data from data that requires more protection. Organizations can provide an appropriate environment for data if they combine these approaches. They can take care of risks, protect confidential information, and be consistent with data privacy regulations.
#Best object storage software#Best Database backup Services#IT Security services#Cyber security company
0 notes
Text
A Beginner’s Guide to Business Accounting in Didcot
Opening a business in Didcot is a thrilling opportunity. With its expanding economy and lively community, the town offers a great place for entrepreneurs to thrive. Nevertheless, one essential element that can either make or destroy a business is accounting. Effective financial management keeps your business compliant, profitable, and sustainable. If you are new to business accounting, this guide will assist you in navigating the fundamentals effectively.
Why Accounting Matters for Your Business
Accounting is more than just numbers and spreadsheets; it’s the backbone of every successful business. Accurate accounting helps you:
Track income and expenses: Know where your money is coming from and where it's going.
Ensure legal compliance: Meet local tax and financial regulations. Make informed decisions: Use financial reports to make strategic business decisions.
Plan for growth: Understand your financial position to make sound investment decisions.
Whether you're operating a small shopping store in the Orchard Centre or a technology firm in Milton Park, sound accounting practices are paramount for expansion and viability.
Forms of Business Organizations in Didcot
Before considering accounting, the right business form is important to select, as it affects your accounting approach and tax burden. In the United Kingdom, popular business forms consist of:
Sole Trader: You operate the business personally, taking all profits after tax. It's easier to account, but you're responsible for debts personally.
Partnership: Shared ownership and responsibility by two or more individuals. Profits are divided, and each partner pays tax on their share.
Limited Company: Separate legal entity from the owners. This format gives limited liability protection but requires more complex accounting and reporting.
Selecting the proper structure is based on your business objectives, financial condition, and risk tolerance. It is best to consult with a local accountant to make an informed choice.
Establishing an Accounting System
A good accounting system saves you time and ensures accuracy. Follow these steps to establish a good system:
Open a Business Bank Account Maintain separate business and personal finances by creating a separate business bank account. This makes record-keeping easier and allows for true financial statements.
Select an Accounting Method Cash Basis: Accrue income and expenses when cash is received or paid. Best suited for small businesses. Accrual Basis: Accrue income and expenses when incurred regardless of cash flow. More accurate accounting method.
Choose Accounting Software Manual bookkeeping is a thing of the past. In Didcot, most small businesses employ cloud accounting software like QuickBooks, Xero, or Sage. These tools provide:
Invoicing and expense tracking Bank reconciliation Tax calculations and reporting Integration with other business applications
Keep Financial Documents Organized Keep invoices, receipts, bank statements, and tax documents in well-organized records. Cloud storage options like Google Drive or Dropbox can organize you and declutter your paper work.
Reading Financial Statements
To make smart decisions, you must know your financial reports:
Income Statement: Indicates your income, expenses, and profit during a given period. Balance Sheet: Reports your assets, liabilities, and owner's equity. Cash Flow Statement: Reports the inflow and outflow of cash in your business. These statements give you an idea about the financial condition of your business, and you can spot growth areas or cost control areas.
Tax Obligations for Businesses in Didcot
It is important to understand your tax responsibilities in order to remain compliant. In the UK, companies typically pay:
Income Tax (for sole traders and partnerships) Corporation Tax (for limited companies) VAT if your turnover is over £85,000 National Insurance Contributions Be aware of significant tax deadlines and take advantage of using a local accountant in Didcot to guarantee correct filing and prevent penalties.
Hiring an Accountant: When and Why
Whereas simple accounting functions can be handled in-house, outsourcing an accountant may prove useful as the business expands. An accountant can assist with:
Tax preparation and filing Analysis and budgeting of finances Compliance and advisory business Didcot boasts a host of experienced accountants familiar with the local market and laws. Working with a professional not only provides certainty but also enables you to concentrate on business expansion.
Tips for Maintaining Good Accounting Practices
Keep Records Current: Log transactions on a regular basis to prevent last-minute juggling in tax season.
Review Financial Reports Quarterly: Quarterly reviews enable you to notice trends and make smart choices.
Tease Personal and Business Expenses: This makes it easier to calculate tax, and also stops you from mismanaging money.
Be in Compliance with Local Legislation: Stay informed about UK tax laws to prevent legal trouble.
Get Professional Assistance: When unsure, consult a local accountant for expert opinions.
Conclusion
Entering into business in Didcot has vast potential, but understanding the fundamentals of accounting is crucial to its success. From selecting the correct business structure to keeping proper books of accounts and comprehending taxation requirements, accounting is central to keeping your business alive and growing.
By adopting effective accounting practices and getting professional advice when necessary, you are able to concentrate on what you do best—operating and growing your business. If you're a new start-up or an existing business seeking to enhance the management of finances, learning business accounting will surely propel you to success in Didcot.
If you require assistance in setting up your accounting system or need expert guidance on business taxes, do not hesitate to contact local accountants in Didcot. With the proper assistance and systems, you can be successful in your business and prosper in this lively community.
0 notes
Text
Oracle Cloud Infrastructure Training Ameerpet | visualpath
Oracle Cloud Infrastructure for Beginners
Oracle Cloud Infrastructure is a powerful cloud computing platform that offers a wide range of services, including computing, storage, networking, and security. Designed to support businesses of all sizes, OCI provides high-performance computing capabilities, cost-effective solutions, and robust security measures. This article serves as a beginner's guide to understanding OCI, its key features, and how to get started.

What is Oracle Cloud Infrastructure?
Oracle Cloud Infrastructure (OCI) is Oracle’s cloud computing service, offering Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS) solutions. It provides the necessary tools and services to build, deploy, and manage applications and workloads in the cloud efficiently.
Key Features of Oracle Cloud Infrastructure
1. Compute Services
OCI offers scalable virtual machines (VMs) and bare metal instances to support various workloads, from basic applications to high-performance computing. OCI Online Certification Course
2. Storage Solutions
OCI provides multiple storage options, including Block Storage, Object Storage, and File Storage, ensuring high availability and data security.
3. Networking Capabilities
OCI’s networking solutions include Virtual Cloud Networks (VCNs), Load Balancers, and FastConnect, allowing businesses to create secure and efficient network infrastructures.
4. Security and Compliance
With built-in security features such as identity and access management (IAM), data encryption, and threat detection, OCI ensures the safety and compliance of cloud resources.
5. Database Services
OCI offers managed database services, including Oracle Autonomous Database, Oracle MySQL HeatWave, and Oracle Exadata Cloud Service, providing high performance and automation.
Benefits of Using Oracle Cloud Infrastructure
Cost-Effective: OCI offers competitive pricing with flexible billing options, making it an affordable solution for businesses.
High Performance: With powerful computing resources, OCI ensures optimal performance for applications and workloads.
Scalability: Businesses can scale their resources up or down based on demand, ensuring efficiency and cost savings. Oracle Cloud Infrastructure Training
Robust Security: OCI includes advanced security features such as encryption, access control, and continuous monitoring to protect data.
Global Reach: With multiple data centers worldwide, OCI provides low-latency access and disaster recovery solutions.
How to Get Started with OCI
1. Sign Up for an Oracle Cloud Account
New users can sign up for an Oracle Cloud account and take advantage of the Free Tier, which includes free compute, storage, and database services.
2. Set Up a Virtual Cloud Network (VCN)
Creating a VCN allows you to define network resources, including subnets, gateways, and security lists, ensuring a secure environment for your workloads.
3. Deploy a Compute Instance
Using the Oracle Cloud Console, users can create and launch virtual machines (VMs) with the required configurations.
4. Configure Storage and Database Services
Depending on your requirements, you can choose from different storage solutions and set up a database to manage your data efficiently.
5. Monitor and Optimize Your Resources
OCI provides monitoring and analytics tools to track performance, manage costs, and ensure security.
Conclusion
OCI Online Certification Course is a reliable and scalable cloud platform designed for businesses looking for high-performance computing, secure storage, and efficient networking. Whether you're a beginner exploring cloud computing or an enterprise migrating workloads, OCI provides a comprehensive suite of services to meet your needs. By following the steps outlined in this guide, you can start leveraging OCI’s capabilities and unlock the potential of cloud computing for your business.
Visualpath is the Leading and Best Software Online Training Institute in Hyderabad.
For More Information about Oracle Cloud Infrastructure TrainingContact Call/WhatsApp: +91-7032290546Visit: https://www.visualpath.in/oracle-cloud-infrastructure-online-training.html
#Oracle Cloud Infrastructure Training#Oracle Cloud Infrastructure Online Training#OCI Online Certification Course#Oracle Cloud Infrastructure Course#OCI Training Online#Oracle Cloud Infrastructure Training Hyderabad#Oracle Cloud Infrastructure Training Ameerpet#Oracle Cloud Infrastructure Training in Bangalore#OCI Training in Chennai#Oracle Cloud Infrastructure Training in India#Oracle Cloud Infrastructure Online Training Institute#OCI Training in Bangalore
0 notes
Text
Azure DevOps Certification: Your Ultimate Guide to Advancing Your IT Career
Azure DevOps Certification
With the growing need for efficient software development and deployment, DevOps has become a fundamental approach for IT professionals. Among the available certifications, Azure DevOps Certification is highly sought after, validating expertise in managing DevOps solutions on Microsoft Azure. This guide provides insights into the certification, its benefits, career opportunities, and preparation strategies.

Understanding Azure DevOps
Azure DevOps is a cloud-based service from Microsoft designed to facilitate collaboration between development and operations teams. It includes essential tools for:
Azure Repos – Source code management using Git repositories.
Azure Pipelines – Automating build and deployment processes.
Azure Test Plans – Enhancing software quality through automated testing.
Azure Artifacts – Managing dependencies effectively.
Azure Boards – Agile project tracking and planning.
Gaining expertise in these tools helps professionals streamline software development lifecycles.
Why Pursue Azure DevOps Certification?
Obtaining an Azure DevOps Certification offers multiple advantages, such as:
Expanded Job Prospects – Preferred by employers looking for skilled DevOps professionals.
Higher Earnings – Certified individuals often earn more than non-certified peers.
Global Recognition – A credential that validates proficiency in Azure DevOps practices.
Career Progression – Opens doors to senior roles like DevOps Engineer and Cloud Consultant.
Practical Knowledge – Helps professionals apply DevOps methodologies effectively in real-world scenarios.
Who Should Consider This Certification?
This certification benefits:
Software Developers
IT Administrators
Cloud Engineers
DevOps Professionals
System Architects
Anyone looking to Learn Azure DevOps and enhance their technical skill set will find this certification valuable.
Azure DevOps Certification Options
Microsoft offers several certifications focusing on DevOps practices:
1. AZ-400: Designing and Implementing Microsoft DevOps Solutions
This certification covers:
DevOps strategies and implementation
Continuous integration and deployment (CI/CD)
Infrastructure automation and monitoring
Security and compliance
2. Microsoft Certified: Azure Administrator Associate
Aimed at professionals handling Azure-based infrastructures, including:
Network and storage configurations
Virtual machine deployment
Identity and security management
3. Microsoft Certified: Azure Solutions Architect Expert
This certification is ideal for those designing cloud-based applications and managing Azure workloads efficiently.
Career Opportunities with Azure DevOps Certification
Certified professionals can pursue roles such as:
DevOps Engineer – Specializing in automation and CI/CD.
Cloud Engineer – Focusing on cloud computing solutions.
Site Reliability Engineer (SRE) – Ensuring system stability and performance.
Azure Consultant – Assisting businesses in implementing Azure DevOps.
Automation Engineer – Enhancing software deployment processes through scripting.
These positions offer competitive salaries and significant career growth.
Key Skills Required for Azure DevOps Certification
Professionals preparing for the certification should have expertise in:
CI/CD Pipelines – Automating application delivery.
Infrastructure as Code (IaC) – Managing cloud environments through scripts.
Version Control Systems – Proficiency in Git and repository management.
Containerization – Understanding Docker and Kubernetes.
Security & Monitoring – Implementing best practices for secure deployments.
How to Prepare for the Azure DevOps Certification Exam?
1. Review the Exam Syllabus
The AZ-400 exam covers DevOps methodologies, security, infrastructure, and compliance. Understanding the objectives helps in creating a structured study plan.
2. Enroll in an Azure DevOps Course
Joining an Azure DevOps Advanced Course provides structured learning and hands-on experience. Platforms like Kodestree offer expert-led training, ensuring candidates are well-prepared.
3. Gain Hands-on Experience
Practical exposure is crucial. Setting up DevOps pipelines, managing cloud resources, and automating processes will enhance understanding and confidence.
4. Utilize Microsoft Learning Resources
Microsoft provides free documentation, learning paths, and virtual labs to help candidates prepare effectively.
5. Engage with DevOps Communities
Joining study groups, participating in discussions, and attending webinars keeps candidates updated with industry best practices.
Exam Cost and Preparation Duration
1. Cost
The AZ-400 certification exam costs approximately $165 USD, subject to location-based variations.
2. Preparation Timeline
Beginners: 3-6 months
Intermediate Professionals: 2-3 months
Experienced Engineers: 1-2 months
Azure DevOps vs AWS DevOps Certification

Best Training Options for Azure DevOps Certification
If you’re searching for the best DevOps Training Institute in Bangalore, consider Kodestree. They offer:
Hands-on projects and practical experience.
Placement assistance for job seekers.
Instructor-led Azure DevOps Training Online options for remote learners.
Other learning formats include:
Azure Online Courses for flexible self-paced study.
DevOps Coaching in Bangalore for structured classroom training.
DevOps Classes in Bangalore with personalized mentoring.
Tips for Successfully Passing the Exam
Study Microsoft’s official guides.
Attempt practice exams to identify weak areas.
Apply knowledge to real-world scenarios.
Keep up with the latest Azure DevOps updates.
Revise consistently before the exam day.
Conclusion
Azure DevOps Certification is a valuable credential for IT professionals aiming to specialize in DevOps methodologies and Azure-based cloud solutions. The increasing demand for DevOps expertise makes this certification an excellent career booster, leading to higher salaries and better job prospects.
For structured learning and expert guidance, explore Kodestree’s Azure DevOps Training Online and start your journey toward a rewarding career in DevOps today!
#Azure Devops Advanced Course#Azure Devops Certification#Azure Online Courses#Azure Devops Course#Devops Certification#Devops Classes In Bangalore
0 notes
Text
Microsoft 365 in Education: Top Tips for Seamless Implementation

Imagine a classroom where students collaborate effortlessly, teachers manage their lessons with ease, and learning continues beyond the four walls of a school. This is the power of Microsoft 365 in education. With tools like Teams, OneNote, and SharePoint, schools can enhance communication, improve organization, and create an engaging learning experience. But how can schools implement Microsoft 365 without the usual hiccups? In this guide, we’ll break it down step by step to ensure a smooth transition for educators, students, and administrators.
Start with a Clear Implementation Plan
Before diving in, schools need a structured plan. This should include:
Goals & Objectives: Define what you want to achieve—better collaboration, seamless remote learning, or efficient document management?
Stakeholder Involvement: Involve teachers, IT staff, and administrators from the start to ensure all perspectives are considered.
Timeline & Milestones: Set realistic timelines for implementation to avoid overwhelming staff and students.
Budget Considerations: Consider licensing costs, hardware requirements, and training expenses.
Choose the Right Microsoft 365 Plan for Your Institution
Microsoft offers different plans tailored for education, including Microsoft 365 A1, A3, and A5. Here’s a quick comparison:
A1: Free, cloud-based, with basic Office apps and security features.
A3: Paid plan with full desktop Office apps, advanced security, and device management.
A5: Premium security, analytics, and compliance tools, ideal for large institutions.
Choosing the right plan ensures that your school gets the best value without overspending.
Train Educators and Staff for Maximum Adoption
A successful Microsoft 365 rollout depends on how well educators and staff can use the tools. Here’s how to make training effective:
Start with the Basics: Teach teachers and students how to use Teams for virtual classes, OneDrive for cloud storage, and OneNote for digital note-taking.
Use Interactive Training Sessions: Hands-on workshops and video tutorials make learning engaging.
Appoint Tech Champions: Identify tech-savvy teachers who can assist others in learning Microsoft 365 tools.
Ensure Smooth Integration with Existing Systems
Many schools already use platforms like Google Classroom, Moodle, or school-specific portals. To avoid disruptions:
Check Compatibility: Ensure Microsoft 365 integrates well with your school’s existing software.
Use Single Sign-On (SSO): This simplifies access and security by allowing users to log in with a single set of credentials.
Sync with School Data: Automatically import student and teacher details to streamline account creation.
Prioritize Security and Data Protection
Cybersecurity is crucial in education. Microsoft 365 offers built-in security features, but schools must also take proactive steps:
Enable Multi-Factor Authentication (MFA): Adds an extra layer of protection for accounts.
Set User Permissions: Limit access based on roles to prevent unauthorized data exposure.
Regular Backups: Use OneDrive and SharePoint backup options to avoid data loss.
Leverage Collaboration Features for Better Learning
Microsoft 365 enhances collaboration through:
Teams: Conduct virtual classes, share assignments, and facilitate discussions.
OneNote: Allow students to take and share digital notes in real-time.
SharePoint: Store and manage learning resources in a centralized location.
Monitor Usage and Gather Feedback
To ensure ongoing success:
Track Adoption Rates: Use Microsoft 365 admin tools to monitor user engagement.
Collect Feedback: Survey teachers and students about their experience.
Make Improvements: Address challenges by tweaking training and support resources.
Conclusion
Implementing Microsoft 365 in education doesn’t have to be overwhelming. With a structured plan, the right training, and a focus on security and collaboration, schools can create a seamless digital learning environment. Whether you’re just starting or looking to enhance your current setup, these steps will ensure a smooth transition to a smarter, more connected classroom.
0 notes
Text
Google Pixel 8a 5G: The AI-Powered Smartphone You Need!
The Google Pixel 8a 5G is here, and it’s redefining what a mid-range smartphone can do. Packed with Google AI, a stunning display, a powerful Google Tensor G3 processor, and an exceptional camera, the Pixel 8a is designed to deliver a delightful and powerful experience. If you're looking to buy Google Pixel 8a 5G, this guide will cover everything you need to know—from its AI features to exclusive offers.
AI-Powered Camera: Capture Moments Like a Pro
One of the standout features of the Google Pixel 8a 5G is its AI-enhanced camera system. Whether you're taking group photos, recording videos, or capturing stunning night shots, the Pixel 8a ensures you get the perfect shot every time.
Key Camera Features:
Best Take: Combine multiple shots to create the perfect group photo where everyone looks great.
Magic Eraser: Remove unwanted objects or distractions from your pictures effortlessly.
Photo Unblur: Fix blurry images—whether they’re new or old—with a single tap.
Night Sight: Capture breathtaking photos in low light, from city lights to starry skies.
Super Res Zoom: Get detailed close-up shots even from a distance.
Portrait Light: Enhance lighting in your portraits for a more professional look.
With a 64MP primary camera and 13MP ultra-wide lens, the Google Pixel 8a 5G mobile ensures you never miss a moment. The 13MP front camera also delivers crisp selfies with an ultra-wide field of view.
Google AI: Your Smart Assistant for Everyday Tasks
Google AI is deeply integrated into the Pixel 8a, making everyday tasks easier and more efficient.
Circle to Search: Just draw a circle around any image or text, even in videos, and Google AI will fetch the results instantly.
Live Translate: Translate signs, menus, and messages in real-time.
Clear Calling: Enhance your caller’s voice while filtering out background noise.
Google Assistant: Manage your daily tasks, set reminders, and get real-time updates effortlessly.
Stunning Display and Durable Design
The Google Pixel 8a 5G features a 6.1-inch Actua Display with a 120Hz refresh rate, delivering smooth visuals and vibrant colours. Whether you’re streaming videos, playing games, or browsing the web, the OLED display ensures a top-notch viewing experience.
Key Display Features:
HDR Support for enhanced contrast and vivid colours.
Corning Gorilla Glass 3 for durability and scratch resistance.
Up to 2,000 nits peak brightness, making outdoor readability excellent.
With its IP67 water and dust resistance, the Pixel 8a is built to withstand the elements. The matte composite back and aluminium frame add to its premium look and feel.

Performance and Battery Life
Powered by the Google Tensor G3 chip, the Google Pixel 8a 5G AI offers seamless performance, enhanced security, and efficient battery usage. The Tensor G3 brings AI-driven optimizations for photography, voice recognition, and security.
Battery & Charging:
24+ hours battery life on a single charge.
Extreme Battery Saver mode extends battery life up to 72 hours.
Fast charging and Qi-certified wireless charging ensure quick power-ups.
Security and Software Updates
Google prioritizes security with seven years of OS and security updates, ensuring that your Pixel 8a stays protected and up to date. Key security features include:
Titan M2 security chip for enhanced data protection.
Anti-malware and anti-phishing protection.
Automatic security checks with the Security and Privacy Hub.
Fingerprint and Face Unlock for seamless authentication.
Exclusive Google Pixel 8a Offers
When you buy Google Pixel 8a 5G, you get access to exclusive perks:
3 months of Google One with 100GB cloud storage.
3 months of YouTube Premium, offering ad-free music and videos.
6 months of Fitbit Premium for advanced health tracking.
Connectivity and Additional Features
The Pixel 8a comes with dual SIM support (nano-SIM + eSIM), Wi-Fi 6, Bluetooth 5.3, and NFC for seamless connectivity. Other notable features include stereo speakers, two microphones with noise suppression, and USB Type-C 3.2 for fast data transfer.
Final Thoughts: Should You Buy Google Pixel 8a 5G?
If you're in the market for a feature-packed smartphone with AI-driven photography, a powerful chipset, and long-term software support, the Google Pixel 8a 5G is an excellent choice. Whether you’re a photography enthusiast, a multitasker, or someone who values Google’s ecosystem, the Pixel 8a is designed to enhance your mobile experience.
With exceptional battery life, premium AI capabilities, and exclusive Google offers, this device is a great investment for anyone looking to upgrade their smartphone.
Don’t wait—buy Google Pixel 8a 5G today and experience the power of AI-driven innovation!
#best smartphones#best mobiles#mobiles#smartphone#deals#mobile offers#offers#new#trending#5g#google#google pixel#pixel 8a 5g#google pixel 8a#new launch#online#best offers#discounts#discountshopping
0 notes
Text
Setting Up a New Lab: A Comprehensive Guide for Success
Setting up a new lab can be both exciting and daunting. Whether you’re starting a laboratory for scientific research, educational purposes, or commercial applications, the process demands careful planning and attention to detail. It’s crucial to consider everything from the equipment needed to the safety measures that must be in place. Let’s walk through some key steps and considerations to ensure your lab is fully functional, safe, and ready to facilitate efficient work from day one.
1. Define Your Purpose and Scope
Before you dive into the practicalities of setting up your lab, it’s essential to define its purpose. Is it for biological research, chemical testing, educational purposes, or a specialized field like physics or environmental science? Your specific objectives will dictate the equipment, layout, and even safety protocols you need.
Lab Type: Identify the type of lab you’re setting up. For instance, a biology lab will require microscopes, incubators, and refrigeration units, while a chemistry lab will need fume hoods, chemical storage, and precise measurement tools.
Size & Scale: Determine how large the lab needs to be. Do you require space for large equipment or only a small workspace? The size will impact your budget and layout.
Once you’ve nailed down the specifics of the lab’s function, you can proceed with a better understanding of your equipment and layout needs.
2. Plan the Layout and Workflow
The layout of your lab is crucial to its functionality. You want to create a space that fosters efficiency while minimizing risks.
Work Areas: Divide your lab into different work zones, such as preparation areas, experimental zones, storage, and analysis stations. This ensures a logical workflow, preventing cross-contamination or safety hazards.
Ergonomics: Ensure that the workstations are designed for comfort. Adjustable tables, ergonomic chairs, and accessible equipment can help minimize strain during long hours of work.
Accessibility: Make sure all equipment, tools, and supplies are easily accessible to minimize time spent walking around. For safety, exits, emergency equipment, and fire extinguishers should be clearly visible and unobstructed.
One of the best ways to ensure a smooth workflow is to create a rough design of the lab on paper or using design software. This will allow you to move things around virtually before committing to physical changes.
3. Select Appropriate Equipment
Once the layout is decided, you’ll need to determine what equipment is essential for your work. Choosing the right equipment not only helps in achieving accurate results but also enhances the safety and efficiency of your lab.
Standard Equipment: Every lab needs basic equipment like lab benches, chairs, computers, and sinks. Make sure these are durable, easy to clean, and fit the work environment.
Specialized Tools: Depending on your lab’s focus, you’ll need specific equipment. For example:
Biology labs might require microscopes, centrifuges, and incubators.
Chemistry labs will need fume hoods, glassware, and precise measuring instruments.
Physics labs will require specialized equipment like lasers, oscilloscopes, or particle detectors.
Be mindful of the quality and brand reputation of the tools and equipment you select. You don’t want to cut corners on items that are integral to the safety and accuracy of your experiments.
4. Safety Protocols and Compliance
Safety should always be a priority when setting up any lab. Having the right safety protocols and equipment in place not only ensures the wellbeing of your team but also keeps you in compliance with local and international regulations.
Personal Protective Equipment (PPE): Ensure you have a sufficient stock of gloves, lab coats, safety glasses, and face shields. Make it a rule for everyone to wear appropriate PPE when inside the lab.
Emergency Equipment: Fire extinguishers, first-aid kits, eyewash stations, and safety showers should be easily accessible. You should also have clear emergency exit routes and fire evacuation plans in place.
Ventilation and Chemical Safety: Labs that work with volatile chemicals or biohazardous materials need proper ventilation. A fume hood is necessary to filter out toxic fumes, and chemical storage cabinets should be used to safely store reagents.
Training: Provide safety training to all lab personnel, covering everything from handling hazardous materials to what to do in the event of an emergency. Everyone in the lab should know the protocols by heart.
5. Organize Supplies and Storage
The organization of lab supplies and materials is another critical aspect of lab setup. A well-organized lab can save time, reduce errors, and promote a cleaner work environment.
Storage: Invest in durable and secure storage solutions, such as locked cabinets for chemicals and biohazards, as well as shelving units for tools and consumables. Make sure you have clearly labeled sections for different materials.
Inventory System: An organized inventory system ensures you always know when supplies are running low. You can use simple spreadsheets or specialized inventory management software for this purpose.
Waste Disposal: Establish a clear system for waste disposal. Different types of waste (biological, chemical, or general) must be disposed of in specific ways. Have separate containers for each type of waste, and ensure they are regularly emptied and disposed of according to safety guidelines.
6. Stay Within Budget and Timeline
Setting up a lab is an expensive venture, and costs can easily spiral if you’re not careful. To avoid overspending:
Prioritize Needs: While it’s tempting to go for the latest high-tech equipment, start by purchasing the essentials. Once your lab is running and funds allow, you can invest in specialized or advanced equipment.
Get Multiple Quotes: When purchasing equipment, always get quotes from multiple suppliers to ensure you’re getting the best price.
Timeline Management: Setting up a lab takes time, and delays can happen. However, having a clear timeline with specific milestones for equipment delivery, construction, and installation can help you stay on track.
Conclusion
Setting up a new lab is a multi-faceted process that requires careful planning and thoughtful execution. By understanding your lab’s purpose, planning the layout, selecting the right equipment, implementing safety protocols, and keeping everything well-organized, you’ll create a functional, safe, and efficient workspace. With patience, the right approach, and an eye for detail, your lab will be ready to support groundbreaking research, educational endeavors, or business development. Happy setting up!
#laboratory chemical supplier india#scifi#lab chemicals#lab instruments#scientific discovery#science#lab#chemicals#laboratory chemicals#setting up a new lab
0 notes