#Configuring Group Policy
Explore tagged Tumblr posts
Text
GPO - Create Shortcut
GPO: Create Shortcut Today’s tutorial will show you how to easily create a desktop shortcut from a shared folder on your server. In this video, we will be demonstrating how to create a shortcut from a shared folder by using GPO on your server in just a few simple steps. let’s to see video from our YouTube channel Please check more videos for This Topic

View On WordPress
#active directory#AD#Backup and Recovery#Configuring Group Policies#Configuring Group Policy#Create and Link a GPO#Create GPO#create Group Policy and Link it to OU#Create Shortcut#Creating Active Directory Objects#Google AdSense#GPO#group policy beginner#group policy guide#Group Policy Management#Group Policy Object#Group Policy Objects#group policy step by step#group policy tutorial#how to configure gpo#how to configure group policies#How to create GPO#How to Install Active Directory In Windows Server#How to Promote windows server to Domain Controller#How to setup Active Directory (AD) In Windows Server#Hyper-V#Install and Configure Active Directory#Install and Configure Active Directory in Windows Server#Installing AD DS roles in Windows Server#Microsoft 365
0 notes
Text
Harden your Veeam Backup Server with Microsoft AppLocker
In this article, we shall be leveraging Zero Trust to harden the Veeam Backup Server with Microsoft AppLocker. Zero Trust principles include explicit verification, minimal privilege access, and assuming breach. Please see how to Configure Multiple IP Addresses on a Single or Multiple NICs, and “Demystifying Zero Trust with Veeam: Design your Architecture“. AppLocker enables System Administrators…
#Application Identity#AppLocker#AppLocker Enforced or Audited#AppLocker policy#AppLocker rules#backup server hardening#Configure Advanced AppLocker Rules#Configure AppLocker Rules#Defense in Depth#group policy#Group Policy Administrative Templates#Group Policy Object#Harden Veeam Backup Server#Local Group Policy#Local Security Policy#Microsoft AppLocker#Microsoft Windows#Software Restriction Policies#Veeam and AppLocker integration#Veeam Backup Server protection#Veeam Backup Server Security#Veeam configuration#Veeam security#Whitelisting tool#Windows#Windows 10#Windows 11#Windows Group Policy#Windows Server#Windows Server 2012
0 notes
Note
Are you a happy or unhappy person and why???
this is such a mysterious query. who are you and why are you asking......
honestly i reject the premise of this question. there's no such thing as a "happy person" or "unhappy person." emotions are transient, not definitive.
sometimes i am happy and sometimes i am unhappy. most days i'm an odd mix of the two. my car finally died for good so now i'm financially ruined and have to deal with the stress of shopping for a new one, and figuring out loans and money and all that, when my bank account is currently overdrafted over $80 for car insurance i no longer need, bc i didn't cancel the policy soon enough, because i got stressed enough that i stopped functioning at all for several days.
this has all made me fairly unhappy.
and yet!
that post about how you can customize your life like a video game by making decisions as they come to you has been charming me for days. five years ago i packed all my shit in a uhaul and moved 3300 miles to oregon without ever having visited before. i found far more of a home here than anywhere i grew up. i weathered the pandemic inside with my polycule, which is made up of people i hand-picked to love, bc i prioritized the choices that would make me happiest. i'm slowly broadening my friend group here. i didn't die last year when i might have & i can walk and breathe now. portland's climate is home to more roses than almost anywhere else in the world, so many of my neighbors have blooming rose bushes in seemingly impossible color configurations. an app on my phone tells me which birds are singing in the trees. there's an iraqi restaurant near me with food so good i've been having it every time my chronic illness acts up. my weighted blanket is warm and my partners are kind.
so. i am also very happy. despite the unhappiness. i have a good life and i don't want to die.
people aren't inherently happy or unhappy. everything's environmental, bitch, let's get you some fruit!
31 notes
·
View notes
Text
The New York State Urban Development Corporation saw in the piers a sacrificial milieu of impurity and devaluation. Rivera described the event as follows: “It’s called a sweep. Not even a fucking eviction. A sweep, like we’re trash.” [...]
The clearance operation of the piers took place under the New York Slum Clearance Commission and Law and its frothy utopian verbiage of “sanitizing” an environment [...] unsuitable for human life. [...] The demolition of the piers showed the violent clash of two confronting forms of urbanism. [...] [Manhattan’s] working class industrial base was transformed into a corporate and service-based economy and New York State Governor Nelson A. Rockefeller, together with city planners, implemented policies to frame Manhattan as a place for work, but not living. [...] The rhetoric used by public and private officials to get rid of the piers was embedded in medical metaphors, [...] "blight" [...]. At the same time, these discussions were imbricated with racial depictions and xenophobic targets: most of the constructions beleaguered in this operation were inhabited or used by black people, Latin Americans, migrants, and displaced communities. [...]
---
The piers thrived with life. [...]
The notion of the piers as insalubrious areas that needed to be wiped out gained traction in the 1980s - during the peak of the HIV/AIDS crisis [...]. This narrative concerning the piers was active in New York City until the early 2000s, until Mayor Michael Bloomberg and Governor George Pataki opened the Greenwich Village segment of Hudson River Park on May 30, 2003. The highway was finally demolished [...] and a series of gates were erected to keep Pier 45 closed after 1am [...]. The previous residents of these spaces were just routine casualties. The new proposal opted for a unitary, straightforward, apparently open but constantly surveilled set of facilities, where constant circulation (by car, skate, bike, foot) was central, and framed the conception of the piers as a passing point. This contrasted the labyrinthic and fragmented former setting, with multitudes of hidden spaces that provided a sense of privacy and safety [...].
---
The history of the piers runs parallel to the history of the LGBTQIA+ movement in New York. This is where Sylvia Rivera and Marsha P. Johnson decided to locate the first installment of [...] (STAR) in 1970 [...], a year after the Stonewall riots. [...] [D]uring the 1973 Gay Pride Rally [...], [Rivera] asked the movement to support [racialized, trans, gender non-conforming, homeless, and incarcerated people] [...] instead of just focusing on cis "men and women that belong to a white middle class club" [...] [which entailed] the negation of alternative forms of living [...].
Members of these groups were ostracized and deprived of typical considerations during the outbreak of an epidemic: protocols of announcement, transparency in information, research, and measure-taking. Meanwhile, the communities that congregated around the piers, and the piers themselves, helped spread information about AIDS, made transparent the available data, and offered care among affected communities. Groups and associations like STAR, Gay Men's Health Crisis, and Gran Fury were essential in this effort. [...] This environmental activism, where kin was formed [...], happened in places like the piers. [...] They were an escape from the constant scrutiny of authorities and from homophobic attacks [...].
---
AIDS' first name, GRID (Gay Related Immune Deficiency), as well as the common “gay plague” and “gay cancer” epithets, strengthened the idea of a specifically gay disease related to a certain environment-specific villain. Journalists, following the views of public health authorities, blamed the epidemic on [...] the places gay people frequented. [...] Physicians thus described a spatial configuration located in downtown Manhattan [...] which [...] posed a threat [...]. This claim had terrible consequences for the activist spaces and urban fabrics that confronted the epidemic [...]. The remnants of Pier 45 were demolished. The activist history of these places was “cleared.” [...]
---
When Sylvia Rivera shouted to the authorities “stay away from my house!” while being evicted, “house” not only referred to the physical construction of her home. She was confronting teleological progress with the project of a[n] [...] assemblage based on [...] mutual caring [...] and defying colonial narratives of race, sex, gender, and nature. The territorialization of epidemics, identities, and citizenship not only shape the built environment, but the built environment shapes them in return. Architecture thereby assumed the form of an expanded spatial practice [...].
When Rivera was trying to save her home from demolition, she said, “there’s so many fucking buildings in this fucking Manhattan.” What New York City was losing with the demolition of Pier 45 was not just a series of dwellings. It was losing a complex ecosystem of coexistence.
---
All text above by: Iván López Munuera. “Lands of Contagion”. e-flux Architecture (Sick Architecture series). November 2020. [Bold emphasis and some paragraph breaks/contractions added by me.]
#abolition#colonial#imperial#ecology#landscape#pathologization#carceral geography#tidalectics#health and sickness
124 notes
·
View notes
Text
Entra ID Lateral Movement And Expanding Permission Usage

Abusing Intimate Permissions for Lateral Movement and Privilege Escalation in Entra ID Native Environments: (In)tune to Takeovers
Recently, a client received assistance from the Mandiant Red Team in visualizing the potential consequences of an advanced threat actor breach. In order to compromise the tenant’s installed Entra ID service principals, Mandiant migrated laterally from the customer’s on-premises environment to their Microsoft Entra ID tenant during the evaluation.
Using a popular security architecture that involves Intune-managed Privileged Access Workstations (PAWs), we will discuss in this blog post a new method by which adversaries can move laterally and elevate privileges within Microsoft Entra ID by abusing Intune permissions (DeviceManagementConfiguration.ReadWrite.All) granted to Entra ID service principals. We also offer suggestions and corrective actions to stop and identify this kind of attack.
A pretext
The client had a well-developed security architecture that adhered to the Enterprise Access model suggested by Microsoft, which included:
An Active Directory-based on-premises setting that adheres to the Tiered Model.
A Microsoft Entra Connect Sync-synchronized Entra ID environment that synchronizes on-premises identities and groups with Entra ID. PAWs, which were completely cloud-native and controlled by Intune Mobile Device Management (MDM), were used to administrate this environment. They were not connected to the on-premises Active Directory system. To access these systems, IT managers used a specific, cloud-native (non-synced) administrative account. These cloud-native administrative accounts were the only ones allocated Entra ID roles (Global Administrator, Privileged Role Administrator, etc.).
A robust security barrier was created by separating administrative accounts, devices, and privileges between the Entra ID environment and the on-premises environment:
Because Entra ID privileged roles are associated with unique, cloud-native identities, a compromise of the on-premises Active Directory cannot be utilized to compromise the Entra ID environment. This is an excellent practice for Microsoft.
An “air gap” between the administration planes of the two environments is successfully created by using distinct physical workstations for administrative access to cloud and on-premises resources. Attackers find it very challenging to get through air gaps.
Strong Conditional Access regulations imposed by Privileged Identity Management assigned roles to the administrative accounts in Entra ID, necessitating multi-factor authentication and a managed, compliant device. Additionally, Microsoft recommends these best practices.
Attack Path
One of the objectives of the evaluation was to assign the Mandiant Red Team the task of obtaining Global Administrator access to the Entra ID tenant. Mandiant was able to add credentials to Entra ID service principals (microsoft.directory/servicePrincipals/credentials/update) by using a variety of methods that are outside the purview of this blog post. This gave the Red Team the ability to compromise any preloaded service principal.
There are a number well-known methods for abusing service principal rights to get higher permissions, most notably through the usage of RoleManagement.See AppRoleAssignment and ReadWrite.Directory.Application and ReadWrite.All.ReadWrite.All rights for Microsoft Graph.
However, the Mandiant Red Team had to reconsider their approach because none of these rights were being used in the customer’s environment.
Mandiant found a service principle that was given the DeviceManagementConfiguration after using the superb ROADTools framework to learn more about the customer’s Entra ID system.Go ahead and write.Permission is granted.Image credit to Google Cloud
The service principal is able to “read and write Microsoft Intune device configuration and policies” with this authorization.
Clients running Windows 10 and later can execute the unique PowerShell scripts used by Intune for device management. Administrators have an alternative to configuring devices with settings not accessible through the configuration policies or the apps section of Intune by using the ability to run scripts on local devices. When the device boots up, management scripts with administrator rights (NT AUTHORITY\SYSTEM) are run.
The configuration of Device Management.Go ahead and write.To list, read, create, and update management scripts via the Microsoft Graph API, all permissions are required.
The Microsoft Graph API makes it simple to write or edit the management script. An example HTTP request to alter an existing script is displayed in the accompanying figure.PATCH https://graph.microsoft.com/beta/deviceManagement/ deviceManagementScripts/<script id> { "@odata.type": "#microsoft.graph.deviceManagementScript", "displayName": "<display name>", "description": "<description>", "scriptContent": "<PowerShell script in base64 encoding>", "runAsAccount": "system", "enforceSignatureCheck": false, "fileName": "<filename>", "roleScopeTagIds": [ "<existing role scope tags>" ], "runAs32Bit": false }
The caller can provide a display name, file name, and description in addition to the Base64-encoded value of the PowerShell script content using the Graph API. Depending on which principle the script should be run as, the runAsAccount parameter can be set to either user or system. RoleScopeTagIds references Intune’s Scope Tags, which associate people and devices. The DeviceManagementConfiguration can likewise be used to construct and manage them.Go ahead and write. Permission is granted.
The configuration of Device Management.Go ahead and write.By changing an existing device management script to run a PowerShell script under Mandiant’s control, Mandiant was able to go laterally to the PAWs used for Entra ID administration with full authorization. The malicious script is run by the Intune management script when the device reboots as part of the user’s regular workday.
By implanting a command-and-control device, Mandiant could give the PAWs any instructions. The Red Team obtained privileged access to Entra ID by waiting for the victim to activate their privileged role through Azure Privileged Identity Management and then impersonating the privileged account (for example, by stealing cookies or tokens). By taking these actions, Mandiant was able to fulfill the assessment’s goal and gain Global Administrator rights in Entra ID.
Remediation and Recommendations
To avoid the attack scenario, Mandiant suggests the following hardening measures:
Review your organization’s security principals for the DeviceManagementConfiguration.ReadWrite.All permission: DeviceManagementConfiguration should be handled by organizations that use Microsoft Intune for device management.Go ahead and write.Since it grants the trustee authority over the Intune-managed devices and, consequently, any identities connected to the devices, all permissions are considered sensitive.
Mandiant advises businesses to routinely check the authorizations given to Azure service principals, with a focus on the DeviceManagementConfiguration.Along with other sensitive permissions (like RoleManagement), there is the ReadWrite.All permission.See AppRoleAssignment and ReadWrite.Directory.Application and ReadWrite.All.ReadWrite.All.
Businesses that manage PAWs with Intune should exercise extra caution when assigning Intune privileges (either via DeviceManagementConfiguration).Use Entra roles like Intune Role Administrator or ReadWrite.All.
Enable Intune’s multiple admin approval: Intune allows you to use Access Policies to demand a second administrator’s approval before applying any changes. By doing this, an attacker would be unable to use a single compromised account to create or alter management scripts.
Think about turning on activity logs for the Microsoft Graph API: Graph API Activity logs, which provide comprehensive details about Graph API HTTP requests made to Microsoft Graph resources, can be enabled to aid in detection and response efforts.
Make use of the features that Workload ID Premium licenses offer: With a Workload-ID Premium license, Mandiant suggests using these features to:
Limit the use of privileged service principals to known, reliable places only. By guaranteeing that only trustworthy places are used, this reduces the possibility of unwanted access and improves security.
Enable risk detections in Microsoft Identity Protection to improve service principal security. When risk factors or questionable activity are found, this can proactively prohibit access.
Keep an eye on service principal sign-ins proactively: Monitoring service principal sign-ins proactively can aid in identifying irregularities and possible dangers. Incorporate this information into security procedures to set off notifications and facilitate quick action in the event of unwanted access attempts.
Mandiant has a thorough grasp of the various ways attackers may compromise their target’s cloud estate with some hostile emulation engagements, Red Team Assessments, and Purple Team Assessments.
Read more on Govindhtech.com
#EntraID#EntraIDLateral#Lateral#Mandiant#MicrosoftEntraID#RedTeam#Windows10#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
3 notes
·
View notes
Text
The Environmental Protection Agency (EPA) didn't report a staggering $7 billion in award-level obligations and outlays during fiscal year 2022, according to an inspector general audit released this week.
The EPA Office of the Inspector General (OIG) determined that the agency underreported its award-level outlays by $5.8 billion, or 99.9%, and its award-level obligations by $1.2 billion, or 12.9% during FY22, the period between October 2021 and September 2022. The agency further failed to report any of its Infrastructure Investment and Jobs Act outlays and under-reported its coronavirus pandemic-related outlays.
"The lack of complete and accurate reporting also led to taxpayers being initially misinformed about the EPA’s spending, and policy-makers who relied on the data may not have been able to effectively track federal spending," the OIG report concluded.
In response to the audit, House Energy and Commerce Committee Chair Cathy McMorris Rodgers, R-Wash., blasted the EPA and called for increased transparency into its activities.
"It’s outrageous and unacceptable that the EPA cannot keep track of its spending or inform Congress — and the American people — of how it is using taxpayer dollars," McMorris Rodgers said in a statement Thursday. "This eye-opening report only further highlights the need for more transparency at the EPA."
"It also raises questions about whether the agency is incapable of managing its record-high budget or if the agency is attempting to hide the amount of taxpayer dollars it is spending to advance the administration’s radical rush-to-green agenda," she added. "The Energy and Commerce Committee will continue holding this administration accountable for its actions that are driving up costs across the board and hurting Americans."
MICHIGAN DEMOCRAT SIGNED NDA INVOLVING CCP-TIED COMPANY, DOCUMENTS SHOW, CONTRADICTING HER PAST CLAIMS
The EPA ultimately corrected its FY22 figures in May 2023 as a result of the OIG audit while making configuration changes a month later. Overall, the inspector general made five recommendations which it said the agency agreed to make.
The report, meanwhile, comes as the EPA both manages a massive green energy fund and continues to request a larger budget. The Inflation Reduction, Democrats' massive climate and tax bill passed in 2022, created the $27 billion Greenhouse Gas Reduction Fund, which in turn establishes a national green bank to fund green projects nationwide.
HOUSE REPUBLICANS OPEN PROBE INTO BIDEN ADMIN FOR OPENING PUBLIC LANDS TO FOREIGN OWNERSHIP
And the White House is requesting that Congress approve a FY24 EPA budget of more than $12 billion, a record level. Republicans have aimed to reduce the EPA budget to about $6 billion, which would be the agency's smallest budget since the early 1990s.
"The Biden administration is using EPA as a pass through for taxpayer dollars to fund left-wing groups that aim to get Democrats elected, not improve the environment," Mandy Gunasekara, a Heritage Foundation visiting fellow who served as the EPA's chief of staff during the Trump administration, told Fox News Digital.
"A failure to report $7 billion is absurd and unacceptable, but also symbolic of how Team Biden operates: prioritizing their political goals over the needs of the American people," she continued. "I’m glad Chair Rodgers is monitoring this and hope the committee brings forth the agency’s Chief Financial Officer to account for this serious oversight."
The EPA did not immediately respond to a request for comment.
18 notes
·
View notes
Text
microsoft posts the urls used for ads/tracking etc
exactly what I'd want, ublock origin has an assets.json file with all their sources (:
sometimes i wanna finish setting up my dns server to block ads but I'm too lazy to find a good blocklist source to feed it.. but as it typically goes, now that i am talking abt it out loud and dragging myself for not doing it, i will look for a source
#there#it's not so hard i just gotta make time 😭 lol#w this i think I'd just need to setup a cron job that builds a list w these sources#but it'd also be nice to have a lil ui so i can toggle some instead of use All#and also a way to add domains and blocklist urls manually#and ofc the most useful pihole feature. the ability to dump dns request realtime for more fine tuned blocking if needed#basically recreating pihole lol..#but also.. ublock origin level protection network wide is p nice sounding#i got So annoyed thinking about how literally the only competition in browsers is google and firefox's browser engines#and how microsoft fucking gave up and built edge on a chromium fork like 😭#google has a vested interest in making sure u can't block ads in ur browser#but they can't do shit about them being blocked at the network level. esp if u disable ipv6#anyways.. hate the current state of the Internet rn 😬 there needs to be more competition. but also fundamentally#ppl need to have more control over their shit#it's been too long since I've enjoyed a setup where my router asks a dns server where everything goes#which is rly nice bc as an end user device on the network one ur on u don't even have to configure or think abt anything#since it's handled at the router-level anyways. that way everyone can enjoy no ads 😌#i think I've been lazy n complacent bc on mobile i have DDG's ATP program and have hella group policies setup on windows#and some computer-level firewall configs in addition to Ublock origin on all the browsers#BUT I DON'T NEED TO DO ALL OF THAT. that is why it Needs to be handled at the net level#i do Not have the same group policy confugs n firewall rules on every conputer lol it's too much of a hassle so!#anyways.. now that i have a source the next question is When do i implement these things. which.. soon hopefully lol#i am on vacation tho n want to read n make music and buy makeup today. and write some poetry or lyrics depending on my mood later maybe
2 notes
·
View notes
Text
The Group of Seven (G-7) leaders are expected to ratchet up economic and political pressure on Russia when they convene at a summit in Italy later this week, with plans to roll out new loans to Ukraine from frozen Russian assets. They also plan to condemn Moscow’s growing ties to North Korea as well as China’s indirect support of the Russian war machine.
The plans for the upcoming summit, described by current and former officials familiar with draft G-7 communiques circulating among diplomats, are being pushed by embattled Western leaders eager to lock in foreign-policy wins in the face of major election hurdles at home. A G-7 leaders’ summit in 2025 could be drastically different and a lot more fractured depending on how elections go in the United States, United Kingdom, and now France—particularly if former U.S. President Donald Trump beats incumbent President Joe Biden in the U.S. elections in November.
“This is the last time this group will meet in this configuration with these leaders. I think that’s pretty clear,” said Josh Lipsky, a former advisor at the International Monetary Fund and now senior director at the Atlantic Council’s GeoEconomics Center. “It all conveys a sense of urgency and the stakes around this G-7.”
The G-7 summit also comes against the backdrop of Israel’s war against Hamas in Gaza as well as strategic competition between the West and its rivals in Russia and China to curry favor and influence in the so-called global south. Italian Prime Minister Giorgia Meloni has invited the leaders of at least a dozen non-G-7 countries to the upcoming summit, including Algeria, Argentina, Brazil, India, Kenya, Mauritania, Saudi Arabia, South Africa, and the United Arab Emirates.
The Biden administration’s top priority for the upcoming summit, which Biden himself is set to attend, is finalizing an agreement to provide around $50 billion in new loans to Ukraine using profits from Russian assets that have been frozen in the Western-dominated international financial system. The proposal has received widespread support in theory among countries opposed to Russia’s full-scale invasion of Ukraine, but it still faces a thicket of complex legal and financial hurdles.
Western countries froze around $280 billion in Russian financial assets following Russia’s invasion of Ukraine in 2022, the bulk of which is parked in Belgium, France, and Germany. EU officials have resisted efforts to seize the assets directly, fearing the precedent such a move would set for international markets, but they opened the door to allocating interest generated by these assets to Ukraine. The Biden administration’s plan calls for G-7 countries to issue Ukraine a $50 billion loan, seen as a critical lifeline for the country’s battered wartime economy, which would be paid back over the years by the interest from the frozen Russian assets. Those assets could generate around $2.7 billion to $3.7 billion a year in interest. Biden administration officials are still working to hash out the final details of the plan ahead of the summit.
Alongside this, the G-7 countries—the United States, Canada, France, Germany, Italy, Japan, and the United Kingdom—are also expected to issue new statements condemning Russia’s deepening military ties with North Korea and send new warnings to Chinese banks to stop helping Moscow evade Western sanctions lest they face new sanctions themselves, the current and former officials said. The United States has so far avoided sanctioning major Chinese financial institutions, possibly fearing the impact on global financial markets, but Washington could choose to target smaller Chinese banks helping Russia skirt Western sanctions as a calculated response and opening warning shot.
“Our concern is that China is increasingly the factory of the Russian war machine,” Daleep Singh, the White House deputy national security advisor for international economics, said during an event at the Center for a New American Security. “You can call it the ‘arsenal of autocracy’ when you consider [that] Russia’s military ambitions threaten obviously the existence of Ukraine, but [also] increasingly European security, NATO, and trans-Atlantic security.”
The Biden administration’s push for major deliverables at the upcoming G-7 summit fits into a wider strategy the administration has taken to advance its foreign-policy agenda in more informal and ad hoc groupings of partners and allies as traditional multilateral institutions—such as the United Nations—are stuck in diplomatic gridlock. The administration has advanced its Indo-Pacific strategy through the Quad—a new partnership among Australia, India, Japan, and the United States—and security partnerships through the AUKUS arrangement with Australia and the United Kingdom.
While the Biden administration hopes to focus the G-7 summit on rallying more international support for Ukraine, it is also grappling with the ongoing crisis in the Middle East centered on Israel’s war against Hamas. Ongoing U.S. support for Israel in the war as the civilian death toll in Gaza mounts has opened Washington up to widespread criticism and accusations of hypocrisy, particularly from countries in the global south.
Countries including Colombia, Mexico, and Nicaragua have filed to join South Africa’s genocide case against Israel at the International Court of Justice over vehement opposition from Israel and the United States. Colombia, Bolivia, and Belize have severed diplomatic ties with Israel, and Brazil has withdrawn its ambassador. Russian state propaganda outlets have seized on the narrative of Western double standards about civilian casualties in Ukraine versus Gaza, and many analysts assess that the conflict in Gaza is aiding the Kremlin’s messaging to the global south on Western hypocrisy.
“The Ukraine war awakened us in the West to the fact that there’s work to do in the global south, but at least then we were on the side of the global majority,” said Nathalie Tocci, director of the Istituto Affari Internazionali Italian think tank and former special advisor to the EU’s foreign-policy chief.
“Now with Israel-Gaza, we just basically are in a shrinking minority,” she added. “We’re in a far, far more complicated spot than we were a year ago vis-à-vis the global south … and there’s now this total lack of credibility that the West has to deal with.”
5 notes
·
View notes
Text










Yesterday and Today (also rendered as "Yesterday" ... and Today in part of the original packaging) is a studio album by the English rock band the Beatles. Released in the United States and Canada in June 1966, it was their ninth album issued on Capitol Records and twelfth American release overall. Typical of the Beatles' North American discography until 1967, the album contains songs that Capitol had withheld from its configurations of the band's recent EMI albums, along with songs that the group had released elsewhere on non-album singles. Among its 11 tracks are songs from the EMI albums Help! and Rubber Soul, and three new 1966 recordings that would appear on Revolver in countries outside North America.
Yesterday and Today is remembered primarily for the controversy surrounding its original cover image. Known as the "butcher cover", it was taken by photographer Robert Whitaker and shows the band dressed in white coats and covered with decapitated baby dolls and pieces of raw meat. Although the photo was intended to be part of a larger work critiquing the adulation afforded the Beatles, the band members insisted it was a statement against the Vietnam War. Others interpreted it as the Beatles protesting the record company's policy of "butchering" their albums for the North American market. In response to retailers' outrage at the gory subject matter, Capitol immediately withdrew the LP and replaced the cover image with a shot of the band posed around a "steamer" trunk.
17 notes
·
View notes
Text
How to Disable Copilot on Windows 11
Windows Copilot, Microsoft's new AI assistant, can assist you with a variety of tasks, such as answering questions, changing system settings, and creating AI images. However, if you're not a fan of Copilot or simply don't need it, you can remove its taskbar icon or disable it entirely on your Windows 11 PC. Here, we'll show you how.
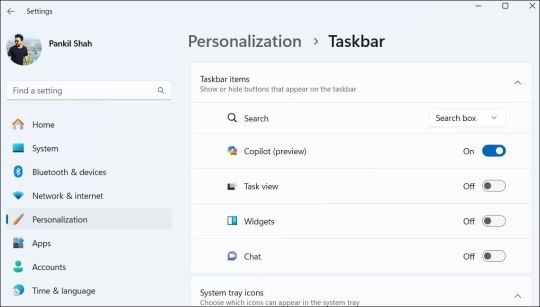
How to Remove the Copilot Icon From the Windows 11 Taskbar
By default, the Copilot icon appears in the Windows 11 taskbar. However, if you prefer not to have it there but still want to use it occasionally, it's easy to hide the Copilot icon. Simply right-click anywhere on an empty spot on your taskbar and select Taskbar settings. In the Settings window that appears, turn off the toggle next to Copilot.

This should remove the Copilot icon from the taskbar. You can still access Copilot by pressing the Win + C keyboard shortcut in Windows 11.
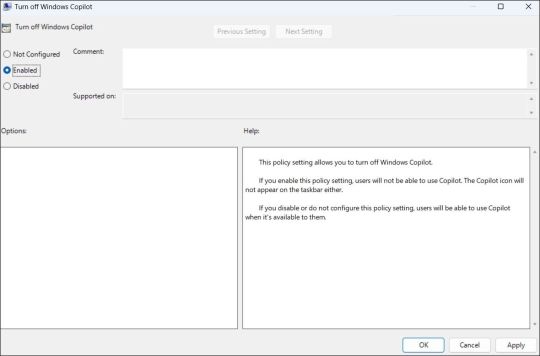
How to Completely Disable Copilot via Group Policy Settings
Although hiding the Copilot is quite easy, it does not turn it off completely, and you might inadvertently access it. Fortunately, you can turn off Copilot completely via the Local Group Policy Editor on PCs running the Professional, Education, or Enterprise edition of Windows 11. - Press Win + S to access the search menu. - Type gpedit.msc in the search box and select the first result that appears. - Select Yes when the User Account Control (UAC) prompt appears. - Use the left pane to navigate to User Configuration > Administrative Templates > Windows Components > Windows Copilot. - Double-click the Turn off Windows Copilot policy on your right. - Select the Enabled option. - Hit Apply followed by OK.
Once you complete the above steps, Copilot will be disabled on your Windows 11 PC and you won't be able to access it even with the keyboard shortcut. If you want to re-enable Copilot later, repeat the above steps and set the Turn off Windows Copilot policy to Not configured or Disabled.
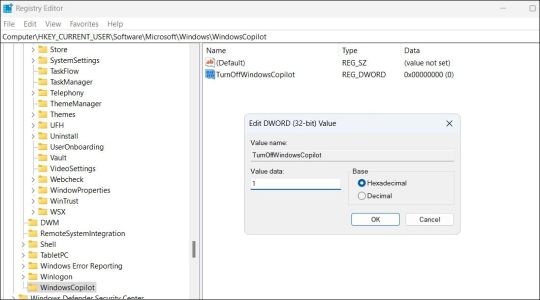
How to Completely Disable Copilot by Modifying Registry Files
Another way to disable Copilot on Windows 11 involves modifying registry files. However, since editing the registry can be risky, you should follow the steps carefully. Also, be sure to back up all the registry files or create a restore point. This will allow you to restore the registry files in case something goes wrong. Once you’ve done that, here’s what you need to do to disable Copilot via the Registry Editor: - Press Win + R to open the Run dialog. - Type regedit in the text box and press Enter to open the Registry Editor. - Select Yes when the User Account Control (UAC) prompt appears. - Use the left pane to navigate to HKEY_CURRENT_USER > Software > Policies > Microsoft > Windows. - Right-click the Windows key and select New > Key. Name it WindowsCopilot. - Right-click on the WindowsCopilot DWORD, go to New, and select DWORD (32-bit) Value from the submenu. Name the DWORD TurnOffWindowsCopilot. - Double-click the TurnOffWindowsCopilot DWORD, type 1 in the text field, and click OK. - Restart your PC for the changes to take effect.
And that’s about it. Windows Copilot will be disabled on your PC. To re-enable it in the future, repeat the above steps and set the TurnOffWindowsCopilot DWORD value to 0. You can also delete the TurnOffWindowsCopilot DWORD instead.
Get Rid of Copilot on Windows 11
While Windows Copilot is a powerful tool, not everyone may want to use it. Fortunately, it’s possible to get rid of it. The above steps will help you achieve your goal, whether you want to keep Copilot out of sight or turn it off entirely. source Read the full article
4 notes
·
View notes
Text
GPO: Remove Recycle Bin
GPO: Remove Recycle Bin Discover how to hide the Recycle Bin for specific End Users using Group Policy Objects (GPO) in this video tutorial and learn how to customize End User settings by following along as we demonstrate how to remove the Recycle Bin through GPO in this video. let’s to see video from our YouTube channel Please check more videos for This Topic

View On WordPress
#active directory#AD#Backup and Recovery#Configuring Group Policies#Configuring Group Policy#Create and Link a GPO#Create GPO#create Group Policy and Link it to OU#Creating Active Directory Objects#Google AdSense#GPO#group policy beginner#group policy guide#Group Policy Management#Group Policy Object#Group Policy Objects#group policy step by step#group policy tutorial#how to configure gpo#how to configure group policies#How to create GPO#How to Install Active Directory In Windows Server#How to Promote windows server to Domain Controller#How to setup Active Directory (AD) In Windows Server#Hyper-V#Install and Configure Active Directory#Install and Configure Active Directory in Windows Server#Installing AD DS roles in Windows Server#Microsoft 365#Network Security
0 notes
Text
Navigating AWS: A Comprehensive Guide for Beginners
In the ever-evolving landscape of cloud computing, Amazon Web Services (AWS) has emerged as a powerhouse, providing a wide array of services to businesses and individuals globally. Whether you're a seasoned IT professional or just starting your journey into the cloud, understanding the key aspects of AWS is crucial. With AWS Training in Hyderabad, professionals can gain the skills and knowledge needed to harness the capabilities of AWS for diverse applications and industries. This blog will serve as your comprehensive guide, covering the essential concepts and knowledge needed to navigate AWS effectively.

1. The Foundation: Cloud Computing Basics
Before delving into AWS specifics, it's essential to grasp the fundamentals of cloud computing. Cloud computing is a paradigm that offers on-demand access to a variety of computing resources, including servers, storage, databases, networking, analytics, and more. AWS, as a leading cloud service provider, allows users to leverage these resources seamlessly.
2. Setting Up Your AWS Account
The first step on your AWS journey is to create an AWS account. Navigate to the AWS website, provide the necessary information, and set up your payment method. This account will serve as your gateway to the vast array of AWS services.
3. Navigating the AWS Management Console
Once your account is set up, familiarize yourself with the AWS Management Console. This web-based interface is where you'll configure, manage, and monitor your AWS resources. It's the control center for your cloud environment.
4. AWS Global Infrastructure: Regions and Availability Zones
AWS operates globally, and its infrastructure is distributed across regions and availability zones. Understand the concept of regions (geographic locations) and availability zones (isolated data centers within a region). This distribution ensures redundancy and high availability.
5. Identity and Access Management (IAM)
Security is paramount in the cloud. AWS Identity and Access Management (IAM) enable you to manage user access securely. Learn how to control who can access your AWS resources and what actions they can perform.
6. Key AWS Services Overview
Explore fundamental AWS services:
Amazon EC2 (Elastic Compute Cloud): Virtual servers in the cloud.
Amazon S3 (Simple Storage Service): Scalable object storage.
Amazon RDS (Relational Database Service): Managed relational databases.
7. Compute Services in AWS
Understand the various compute services:
EC2 Instances: Virtual servers for computing capacity.
AWS Lambda: Serverless computing for executing code without managing servers.
Elastic Beanstalk: Platform as a Service (PaaS) for deploying and managing applications.
8. Storage Options in AWS
Explore storage services:
Amazon S3: Object storage for scalable and durable data.
EBS (Elastic Block Store): Block storage for EC2 instances.
Amazon Glacier: Low-cost storage for data archiving.
To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the Top AWS Training Institute.

9. Database Services in AWS
Learn about managed database services:
Amazon RDS: Managed relational databases.
DynamoDB: NoSQL database for fast and predictable performance.
Amazon Redshift: Data warehousing for analytics.
10. Networking Concepts in AWS
Grasp networking concepts:
Virtual Private Cloud (VPC): Isolated cloud networks.
Route 53: Domain registration and DNS web service.
CloudFront: Content delivery network for faster and secure content delivery.
11. Security Best Practices in AWS
Implement security best practices:
Encryption: Ensure data security in transit and at rest.
IAM Policies: Control access to AWS resources.
Security Groups and Network ACLs: Manage traffic to and from instances.
12. Monitoring and Logging with AWS CloudWatch and CloudTrail
Set up monitoring and logging:
CloudWatch: Monitor AWS resources and applications.
CloudTrail: Log AWS API calls for audit and compliance.
13. Cost Management and Optimization
Understand AWS pricing models and manage costs effectively:
AWS Cost Explorer: Analyze and control spending.
14. Documentation and Continuous Learning
Refer to the extensive AWS documentation, tutorials, and online courses. Stay updated on new features and best practices through forums and communities.
15. Hands-On Practice
The best way to solidify your understanding is through hands-on practice. Create test environments, deploy sample applications, and experiment with different AWS services.
In conclusion, AWS is a dynamic and powerful ecosystem that continues to shape the future of cloud computing. By mastering the foundational concepts and key services outlined in this guide, you'll be well-equipped to navigate AWS confidently and leverage its capabilities for your projects and initiatives. As you embark on your AWS journey, remember that continuous learning and practical application are key to becoming proficient in this ever-evolving cloud environment.
2 notes
·
View notes
Text
The bulletin board seems a bit worn out but thankfully some papers are still attached onto it. Ranging from advertisement to random news:
[UPCOMING NEW FLAVOR | SQUADCADA]
In order to celebrate up coming anniversary festival of The Timeless Nirvana, Beaver Breeze is proud to announce the limited edition: Squadcada. This squidcada like ice cream design was made based on the iconic bioluminescence squidcada of the Morning Dew Lake in Boundless Horizon, fitting for the occasion, what are you waiting for
Bring the squad to taste the squash, don’t have any friends ? Check out our new seasonal limited edition “TNS” plushy
[Hot News | Old Wound Re-Opened, Returning Tension ?]
The Scarlet Land and City of Light have been in peace for thousand of cycles after the great altercation, citizens from all regions express agitation with the on going commotion within the City of Light, rumors seems to say the Scarlet Land is also involved one way or another. Could this potentially lead to a New and Second wave of confrontation, disrupting the long preserved Tranquility Era
[Boundless Horizon | New update for growing refugees concerns]
The Administration of Timeless Nirvana has been receiving concerns about its refugee policy. Most noticeably is the issue with potential war criminal infiltration
The Administration group has heard and took notice of your concerns, however, we shall not be changing our immigration policies as it does not follow Boundless Horizon’s long accustomed visions and missions
Nevertheless, a new layer of security will be discussed and potentially be installed within the city and area overall in order to tighten the procedure and to increase the citizens safety from within. More will be updated
-Boundless Horizon’s Administration-
[Coming soon: Fountain of Root]
Situated in the middle of the heart of Gaia, Fountain of Root will be a new addition to the town square, the design will be a mixed of both Illuminate Upheaval’s elegant approach and Crimson’s Ambience distinctive pattern design, commissioned and designed well known architectures from their respective nations: Bored of Sentimental Thoughful and Two Treadmills, Thouand Configurations
TIMELESS NIRVANA 37TH ANNIVERSARY CONCERT
It’s here and it’s time for another celebration once again, 37th is proven to be another special yet even more memorable with our new and upcoming featured guest, the diva you all know and love with the voice that soars through 3 nations: Rid Adjectival Shrouded Leeway
3 notes
·
View notes
Text

Well, we of the yellow contingent love you too! Red comes first. Yes. Take care of yourself. Then green, then yellow. I want to hear what colors she talked about. Will add more if anything interesting pops up!


Rainbows, lightning (who could forget jinglei), and 88 has been firmly established as scarlet red (ok, and also lavender lol). I vow to start becoming a pure fan after Weibo night if these hints are nothing more than industrial sugar. We know they are friends; outside of that, all I know is I love them equally and will continue to support them in all their endeavors. I will continue to look at the candy as nothing more than a neat marketing tool and see how creative they can get.
Right now, 30 needs all the different CP's he can get to untie from that one who is really dropping so much sugar it seems too much at this point given the circumstances. If I were him I'd steer clear of the off-drama CP's with industrial candy outside of what he did with ZYT - I have heard rumors that he ZJM will go all in with the CP thing, but let's hope they just mean promotional stuff on screen like NBY.
I am nervous about too much CP stuff leaking these days, so no re-blogging for now. If you are a Bird Egg, feel free to roost here or in the private group. CP's are all about letting your imagination take you to places that are usually not true, but on occasion you might actually be right. Very few CPF ever discover if there pair is indeed BE. These days, there are contracts involving maintaining CP business too, so everyone be a rational egg.
I feel this Weibo night will be special though. Either way, we might get to see a tiny bit of interaction hopefully. They used to always be right after each other in the line up, so maybe they will be sitting near each other? The sitting configuration will be different now that the masking policy is different I think. Either way, we want to see them in the same frame in a film or drama again to live out an adult storyline that will make Bird Eggs happy.
2 notes
·
View notes
Text

Lockheed Martin and Northrop Grumman sign agreement to manufacture F-35 core fuselages in Germany
Fernando Valduga By Fernando Valduga 02/17/23 - 14:00 in Military
Lockheed Martin and Northrop Grumman signed a letter of intent with Rheinmetall AG as a promising strategic source of supply for the F-35 central fuselage in Germany.
This potential partnership would establish a second integrated assembly line of the central fuselage (IAL) of the F-35 in Germany, expanding the significant role that European industry plays in the F-35 program.
“Lockheed Martin has been a committed partner with Germany for more than 50 years. The F-35 program will continue to strengthen our strategic partnerships with key industry partners in the coming years," said Mike Shoemaker, Vice President of F-35 Customer Programs at Lockheed Martin. "The production of the central fuselage of the F-35 in Germany will be vital to meet the growing global demand for F-35s, which play a vital role in the security of the 21st century."

Northrop Grumman is the main partner of the Lockheed Martin F-35 program. In addition to manufacturing the central jet fuselage and wing coatings, the company is also responsible for the development, production and maintenance of sensor, avian and aircraft systems and training software.
"The central fuselage IAL is recognized as a state-of-the-art installation supported by Northrop Grumman's unique technologies, combining automation with our experience in aerospace tools," said Glenn Masukawa, vice president and manager of Northrop Grumman's F-35 program. "The involvement with Rheinmetall demonstrates our commitment to collaborate with international partners to manufacture advanced aircraft."
The F-35 program continues to develop these partnerships, using companies with the right technical capabilities. The German industry has contributed to the F-35 program since its inception in 2001. Lockheed Martin continues to actively explore additional opportunities for industrial participation that will allow partnerships throughout the German industry and create jobs in the manufacture, maintenance, training, research and development of 5th generation fighter aircraft.

Cooperation with Lockheed Martin and Northrop Grumman in the F-35 program highlights the importance of Rheinmetall for national security policy and will bring essential capabilities to Germany. Rheinmetall can contribute its experience as an integrated technology group in the production of complex components and as an aviation certified company for cooperation.
"The long-standing partnership between Lockheed Martin and Rheinmetall, as well as the very close ties that have existed for decades between the Bundeswehr (German Armed Forces) and our company, lead to a genuine transfer of know-how to Germany as a localized industry," said Armin Papperger, CEO of Rheinmetall AG. "In addition, this configuration contributes significantly to minimizing risk, bringing national partners who are involved in a proven way."
To date, the F-35 operates from 37 bases and ships around the world, with nine nations operating F-35s on its territory. There are more than 890 F-35s in service today, with more than 1,890 pilots and 13,570 maintainers trained in the aircraft.
Tags: Military AviationF-35 Lightning IILockheed MartinLuftwaffe - German Air ForceNorthrop GrummanRheinmetall
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he participated in several events and air operations, such as Cruzex, AirVenture, Dayton Airshow and FIDAE. He has works published in specialized aviation magazines in Brazil and abroad. He uses Canon equipment during his photographic work in the world of aviation.
Related news
HELICOPTERS
Indian HAL will provide spare parts and repair Argentine Air Force helicopters
17/02/2023 - 11:00
EMBRAER
Embraer Defense & Security presents portfolio and innovative solutions at IDEX in Abu Dhabi
02/17/23 - 09:00
MILITARY
Autonomous C-130 and C-17? USAF invests in feasibility study
17/02/2023 - 08:28
INTERCEPTIONS
NORAD intercepts Russian warplanes for the second time in two days
16/02/2023 - 22:54
MILITARY
Biden: three objects slaughtered in the US were for research, not for Chinese surveillance
16/02/2023 - 22:29
Beechcraft King Air 260 Multi-Engine Training System (METS) T-54A for the U.S. Navy.
MILITARY
Textron's King Air 260 is chosen as the new U.S. Navy multi-engine coach
16/02/2023 - 21:58
Cavok Twitter
homeMain PageEditorialsINFORMATIONeventsCooperateSpecialitiesadvertiseabout
Cavok Brazil - Digital Tchê Web Creation
Commercial
Executive
Helicopters
HISTORY
Military
Brazilian Air Force
Space
Specialities
Cavok Brazil - Digital Tchê Web Creation
2 notes
·
View notes
Text
Ilkka Ruostetsaari, professor of political science at the University of Tampere, told the Uutissuomalainen news group (siirryt toiseen palveluun) that political parties in Finland right now are in a sort of arms race phase before the start of actual government formation talks.
At the top of the list for PM-elect Petteri Orpo (NCP) is a six billion euro cut in state spending. Before the elections, the NCP strongly highlighted the need for it, but that sum was not directly mentioned in the party's own position paper this week.
"This is a negotiating tactic on the part of the NCP. At this stage, it doesn't want to present overly demanding conditions," explains Ruostetsaari.
According to University of Helsinki researcher Jenni Karimäki, the need for reducing state spending by six billion euros was included in the NCP's paper, although the exact figure is not mentioned.
"There are many ways to interpret why the exact figure has been left out. Does it say that it would not necessarily be adhered to, or was it thought that it was self-evident?" said Karimäki.
The Swedish People's Party is currently in the position of kingmaker in government negotiations. The party has a lot of power in terms of whether to form a government based on the NCP and Finns Party, or the NCP and the Social Democrats.
The experts interviewed by Uutsisuomalainen pointed out that traditionally the Swedish People's Party has shown a lot of flexibility in government cooperation.
"The SPP can afford to take quite tough stands in this situation. But the party has long experience of cooperation in various government configurations, and remaining in the opposition is seen as quite a traumatic prospect within the party," said lkka Ruostetsaari.
Most important
Helsingin Sanomat points out (siirryt toiseen palveluun) that the Swedish People's Party and the Finns Party have many major policy differences, with immigration issues being one of the biggest. Finns Party chair Riikka Purra said in an interview with HS on Tuesday that if the SPP does not change its immigration positions, government cooperation will be impossible.
Swedish People's Party leader Anna-Maja Henriksson doesn't seem overly concerned about this, telling HS on Wednesday, "Isn't it the case that when we start forming a joint government, everyone has to be flexible? So that's the case also for the Finns Party."
The paper asked Henriksson which immigration policies are the most important for her party.
"At this point, I'm not having this kind of discussion yet. But what all parties have in common is that Finland needs to achieve economic growth. And when we say that we want growth, we have to understand that we have to create the conditions for it."
Gone and likely soon forgotten
Turun Sanomat (siirryt toiseen palveluun)reports that Finland's Justice Ministry has officially removed a long list of small political parties from the official party registry.
Now gone are the Citizens' Union, the Pirate Party, the Liberal Party, the Freedom League, the Animal Justice Party of Finland, the Citizens' Party, the Feminist Party, the Finnish Reform Movement, the Finnish Nation First, and the Seven Star Movement.
None of the parties had MPs elected in the 2023 or 2019 parliamentary elections. These parties also did not receive a minimum two percent of the votes cast throughout the country in the most recent elections.
Carbon sink decline
Helsingin Sanomat (siirryt toiseen palveluun)looks at a fresh report by the Finnish Environment Institute (Syke) saying that if a change is not seen soon, Finland's forests will shift from being a carbon sink to becoming a source of climate emissions .
This could mean that Finland will have difficulty meeting the climate obligations set by the EU for the period 2021–2025, and that Finland's own carbon neutrality goal for 2035 is also at risk.
This is all the result of a decrease in tree growth and an increase in timber harvesting.
It is unlikely that the shortfall can be made up by, for example, reducing traffic emissions. Based on Syke's report, the clearest means to remedy the situation is to reduce logging.
According to the Environment Institute's estimate, the annual timber harvest should be 65–68 million cubic metres. Today, an average of about 75 million cubic metres of forest are cut down in Finland each year.
Tampere flight connections
Aamulehti carries a report on the situation concerning air traffic services (siirryt toiseen palveluun) in Tampere.
Finnair will end flights between Tampere-Pirkkala and Helsinki-Vantaa replacing them with buses from the beginning of May because of the low passenger numbers on this route.
Since last November, Finnair has been canceling these flights one month at a time.
Marja Aalto, an air traffic specialist with Business Tampere, told the paper that the termination of Finnair's flights to Tampere-Pirkkala will not significantly affect the city's international accessibility.
"Tampere is more accessible than it was before the pandemic. We can fly directly from several European cities, and we have connections to the world through, for example, Munich and Amsterdam," she said.
Last May, the Latvian airline Air Baltic established its first home base outside the Baltic countries at Tampere-Pirkkala and opened six direct routes to Europe. Two of these, Oslo and Frankfurt flights, were however canceled during the last winter season.
Now, Amsterdam flights have been canceled for the whole of April-May. This is not because of a lack of bookings, but because of a move by the Dutch to reduce the number of flights at Schiphol Airport.
Aamulehti reports that in May, Air Baltic will start flights from Tampere-Pirkkala to Nice and Milan.
Last of a breed
Helsinki has yet one less old-time service.
Helsingin Uutiset tells readers (siirryt toiseen palveluun) that Veikko Tiainen, probably the capital's last typewriter repairman, has closed up his shop in the city's Alppila district.
Starting in the 1960s, Tiainen mainly repaired old typewriters, slightly newer electric typewriters, mechanical calculators, and sewing machines.
He told the paper although many mechanical typewriters these days are mostly showpieces or home decorations, people want to keep them in working order, and he had as much business as he could handle.
However, he decided to finally retire and there seems to be no one to take his place..
"No, I think I'm the last one. That's about it. Fixing these requires a lot of technical experience," Tiainen said in an interview with HU.
2 notes
·
View notes