#Veeam configuration
Explore tagged Tumblr posts
Text
Harden your Veeam Backup Server with Microsoft AppLocker
In this article, we shall be leveraging Zero Trust to harden the Veeam Backup Server with Microsoft AppLocker. Zero Trust principles include explicit verification, minimal privilege access, and assuming breach. Please see how to Configure Multiple IP Addresses on a Single or Multiple NICs, and “Demystifying Zero Trust with Veeam: Design your Architecture“. AppLocker enables System Administrators…
#Application Identity#AppLocker#AppLocker Enforced or Audited#AppLocker policy#AppLocker rules#backup server hardening#Configure Advanced AppLocker Rules#Configure AppLocker Rules#Defense in Depth#group policy#Group Policy Administrative Templates#Group Policy Object#Harden Veeam Backup Server#Local Group Policy#Local Security Policy#Microsoft AppLocker#Microsoft Windows#Software Restriction Policies#Veeam and AppLocker integration#Veeam Backup Server protection#Veeam Backup Server Security#Veeam configuration#Veeam security#Whitelisting tool#Windows#Windows 10#Windows 11#Windows Group Policy#Windows Server#Windows Server 2012
0 notes
Text
Backing Up Your Server: A Beginner's Guide

In today's digital age, where data plays a crucial role for businesses and individuals alike, protecting your server should be a top priority. The loss of server data can result in severe consequences, including downtime, financial loss, and damage to reputation. Therefore, implementing a robust backup strategy is essential to safeguard your server's critical information. In this beginner's guide, we'll explore the basics of server backups, discuss various backup solutions, and provide best practices to ensure the best server backup possible.
Understanding the Basics of Server Backups
To embark on your server backup journey, it's vital to grasp the fundamentals. Let's start by clarifying what server backups are and their purpose. Unlike regular data backups, which focus on individual files or folders, server backups involve duplicating the entire server's contents, including the operating system, applications, and data. The primary objective of server backups is to ensure business continuity and minimize downtime by providing a safety net in the face of system failures, cyber attacks, or accidental deletions.
Types of Server Backups
There are primarily three types of server backups you should be aware of:
Full Backup: This method involves creating a complete copy of your server's data and configuration files. While full backups provide comprehensive coverage, they consume more time and storage space.
Incremental Backup: With incremental backups, only the changes made since the last backup are saved. This approach reduces backup time and storage requirements while still allowing for complete recovery by combining the most recent full backup with incremental backups.
Differential Backup: Differential backups capture the changes made since the last full backup, resulting in faster backups compared to full backups. However, during the restoration process, both the full backup and the latest differential backup are required to rebuild the server.
Choosing the Right Backup Strategy

Selecting the appropriate backup strategy depends on your specific server needs. Consider the following factors while defining your backup strategy:
Data size: Determine the size of your server's data to determine the backup storage capacity required.
Frequency of changes: If your server undergoes frequent modifications, incremental backups may be the ideal solution. However, if changes are infrequent, full or differential backups may suffice.
Recovery Time Objectives (RTOs): Understand how quickly you need to restore your server in case of a failure. This consideration will help determine the backup strategy that aligns with your desired downtime limits.
Implementing Server Backup Solutions
Now that you have a grasp of the fundamentals, it's time to explore the various backup solutions available to protect your server efficiently.
Identifying Backup Solutions
A wide range of backup software and tools are available in the market, catering to various server environments and requirements. Consider both open-source and commercial backup solutions, weighing their features, scalability, and support options. Some popular backup solutions include:
Veeam Backup & Replication
Acronis Cyber Backup
Backup Exec
Selecting Backup Storage Options
The choice of backup storage is critical, as it determines the accessibility, scalability, and security of your backup data. Consider the following storage options:
Storage Option
Description
External Hard Drives
Portable and cost-effective option, suitable for small-scale backups. Ensure adequate storage capacity based on your server's data size.
Network-Attached Storage (NAS)
Storage devices connected to your network for centralized backup management and accessibility.
Cloud Storage
Secure and scalable solutions provided by cloud service providers. Allows for remote backup, reducing the risk of data loss.
Tape Backups
Ideal for large-scale backups, providing long-term storage and offline options. However, tape drives and media can be costly.
Setting Up Automated Backup Systems

Manual backups are prone to human error and are time-consuming. Implementing automated backup systems ensures regular backups without manual intervention. Here's a quick guide to setting up automated backups:
Choose a backup software or tool that supports automated scheduling.
Configure the backup schedule based on the frequency of changes and your RTOs.
Test backups periodically to verify their integrity and effectiveness.
Monitor the backup process for potential issues or failures, ensuring the reliability of your backup system.
Best Practices for Server Backups
To maximize the effectiveness and security of your server backups, adhere to the following best practices:
Creating Redundancy with Offsite Backups
Relying solely on on-site backups can be risky, as they are susceptible to physical damage or theft. Implementing offsite backups provides an additional layer of protection. Consider the following ways to create redundancy:
Utilize cloud storage for remote backup, ensuring data safety in case of on-site disasters.
Choose a reliable offsite backup location and establish secure methods of transferring backups.
Securing Backup Data
Data security is paramount when it comes to backup storage. Employ encryption techniques to protect sensitive data from unauthorized access. Consider the following security measures:
Encrypt your backup data using industry-standard encryption algorithms.
Utilize password protection to limit access to the backup data.
Regular Monitoring and Maintenance
Ensuring the health and effectiveness of your backup systems requires consistent monitoring and maintenance. Perform the following activities regularly:
Verify the integrity and restorability of backups by performing periodic tests and trial recoveries.
Keep your backup software and tools up to date to benefit from the latest functionality and security patches.
Monitor the available backup storage capacity to prevent storage overflow.
Conclusion
In conclusion, backing up your server is a fundamental aspect of protecting your critical data and ensuring business continuity. By understanding the basics of server backups, choosing the right backup strategy, implementing backup solutions, and adhering to best practices, you can mitigate the risks associated with data loss. Remember, a well-executed backup strategy, including offsite backups, secure data management, and regular monitoring, is crucial for the best server backup. Safeguard your digital assets and enjoy peace of mind knowing that your server data remains intact, even in the face of adversity.
In need of reliable computer support and services in Texas? Look no further than Heart of Texas IT. With their expertise and commitment to providing exceptional IT solutions, they are the go-to choice for individuals and businesses alike. Whether you need assistance with server backups, network security, or general computer troubleshooting, Heart of Texas IT has got you covered.
Give them a call today at 151-236-63889 to discuss your IT needs and experience the top-notch service they offer. Don't let technical issues hold you back - trust Heart of Texas IT to keep your systems running smoothly and efficiently. Say goodbye to IT headaches and hello to peace of mind with Heart of Texas IT.
1 note
·
View note
Text
Empowering MSPs: The Vital Role of using ProVal Tech as your MSP Consultant
In the dynamic landscape of managed services, navigating through a plethora of software tools and ensuring their seamless integration can be a daunting challenge for MSPs. This intricate task demands expertise and strategic insights, making the role of an MSP Consultant invaluable. At our company, we specialize in providing top-notch NOC services for MSPs, offering Subject- Matter-Experts MSP Consultants to help you streamline your operations.
Our team of experienced MSP Consultants understands the significance of optimizing your software stack. By leveraging our deep industry knowledge and insights gained from collaborating with leading MSPs, we are uniquely positioned to guide you through the complexities of tool management. Our Tool Subject-Matter-Experts (SMEs) bring a wealth of experience to the table, ensuring that every MSP we partner with receives tailored and effective solutions.
Our MSP Consultants specialize in RMM consulting, excelling in a range of services. This includes comprehensive support from the initial setup to migrating from existing tools, conducting audits, fine-tuning, deploying agents, configuring monitor sets, handling upgrades, and implementing scripting and automation. Our objective is to empower you to maximize the potential of your RMM tool, boosting both efficiency and productivity. We have expertise with various RMM Tools such as ConnectWise Automate, ConnectWise RMM, Kaseya VSA, and Datto RMM.
Backup management is another critical aspect of MSP operations, and our MSP Consultants are well-versed in providing peace of mind through enterprise-grade SLAs for managed backups. We work with over 30+ Backup Solutions, including Datto, StorageCraft, Veeam, Acronis, AppAssure, Azure, and many others. Our backup monitoring, remediation, and reporting services are designed to help you save precious time handling these solutions effectively. Our dedicated team of vendor-certified technicians offers advanced technical support, allowing you to focus on delivering exceptional service to your clients.
Additionally, our 24x7 monitoring services are designed to give your team the break they deserve from constant server and site offline alerts, especially during the night. Our vigilant team can swiftly triage and remediate critical events, open trouble tickets with ISPs, and escalate issues to your on-call team as necessary. Our MSP Consultants act as an extension of your team, ensuring that your operations run smoothly around the clock.
In conclusion, partnering with an MSP Consultant like us can significantly enhance your MSP business. By leveraging our expertise, you can optimize your software tools, streamline your operations, and provide unparalleled support to your clients. With our NOC services, you can confidently navigate the challenges of the MSP ecosystem, knowing that you have a dedicated team of professionals supporting you every step of the way. Let us be your trusted partner, empowering you to achieve greater success in the competitive world of managed services.
#MSP Consultant#MSP Automation#kaseya vsa training#MSP Outsourced Noc#ConnectWise RMM#connectwise manage consulting#ConnectWise RMM Admin
0 notes
Text
Cloud Backup with Veeam
Offsite Backup Veeam Cloud
Cloud backup with Veeam is a data protection and disaster recovery solution that enables businesses to securely back up their on-premises or cloud-based workloads to the cloud. Veeam offers a range of products and services that cater to various backup and recovery needs, including on-premises, hybrid, and cloud-only environments. Here's an overview of how cloud backup with Veeam works:
Offsite Backup Veeam Cloud
Veeam Backup & Replication: Veeam Backup & Replication is the core product that provides comprehensive data protection. It allows you to create backup jobs, schedule backups, and replicate data to the cloud. You can configure the backup to automatically transfer data to a cloud repository.
Cloud Connect: Veeam Cloud Connect is a feature that allows you to connect to Veeam-powered service providers for off-site backup and replication. Service providers host cloud repositories that you can target for backup. This ensures that your data is stored in a secure, remote location for disaster recovery.
Veeam Agents: Veeam also offers agents that can be installed on physical servers, virtual machines, or workstations. These agents allow you to back up data from various endpoints to cloud repositories.
Cloud Backup Providers: You can choose a Veeam Cloud Service Provider (VCSP) that offers cloud backup services. These providers offer cloud repositories that are compatible with Veeam Backup & Replication. They may also provide managed services for backup and disaster recovery.
Backup Copy Jobs: Veeam allows you to set up backup copy jobs to create additional copies of your backup data in the cloud. This ensures redundancy and the ability to recover your data in case of hardware failures or disasters.
Data Encryption: Veeam provides encryption options for data in transit and at rest to ensure the security of your backups in the cloud. This helps protect your data from unauthorized access.
Data Recovery: In the event of data loss or a disaster, Veeam enables you to recover your data from the cloud. You can perform full VM restores, file-level recoveries, or even instant VM recovery from cloud backups.
Monitoring and Management: Veeam provides a centralized management console that allows you to monitor and manage your backup and recovery operations, whether on-premises or in the cloud.
Cost Optimization: Veeam provides features to help you manage the costs associated with cloud backups. This includes data deduplication and compression to reduce the amount of data transferred to the cloud.
Compatibility: Veeam supports a wide range of platforms, including VMware vSphere, Microsoft Hyper-V, and various cloud providers.
Overall, Veeam offers a flexible and comprehensive solution for cloud backup and disaster recovery. It helps businesses protect their data and applications, whether they are hosted on-premises or in the cloud, and enables them to recover quickly in the event of data loss or disasters. When implementing cloud backup with Veeam, it's essential to design your backup strategy based on your specific needs and business continuity requirements.
Offsite Backup Veeam Cloud offers a seamless, secure, and reliable cloud-based backup solution. Designed to protect your critical data and ensure business continuity, our service provides easy recovery, scalability, and top-tier data protection for your business.
1 note
·
View note
Text
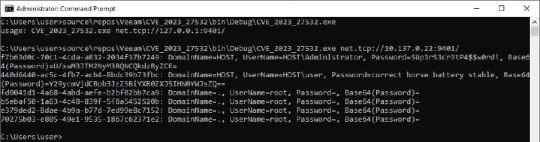
[Media] СVE-2023-27532
СVE-2023-27532 Vulnerability in Veeam Backup & Replication component allows encrypted credentials stored in the configuration database to be obtained. This may lead to gaining access to the backup infrastructure hosts. https://github.com/horizon3ai/CVE-2023-27532 #cybersecurity #infosec #pentesting #redteam
1 note
·
View note
Photo

#Veeam #Official #Courseware: (VMCE) #v11, #Veeam #Availability #Suite v11: #Configuration #and #Management #done #💻️ #👍 #🖖 #✅ (Kyiv, Ukraine) https://www.instagram.com/p/CQjBirTA2PQ/?utm_medium=tumblr
0 notes
Text
VMCE Training Review
[DE] #VMCE Training ("Veeam Availability Suite v11: Configuration and Management") Review #Veeam #VeeamVanguard
Ich hatte letzte Woche das Vergnügen an einem VMCE (Veeam Certified Engineer) Training, übrigens die erste Veeam Schulung für mich, teilzunehmen. Genauer gesagt handelt es sich um die Schulung “Veeam Availability Suite v11: Configuration and Management“. Vielen Dank an der Stelle noch einmal an die tollen Veeam Community Koordinatoren, Rick Vanover, Nikola Pejková und Madalina Cristil die das…

View On WordPress
0 notes
Text
Ejabberd change admin password

#Ejabberd change admin password how to
#Ejabberd change admin password Patch
#Ejabberd change admin password windows 10
#Ejabberd change admin password software
#Ejabberd change admin password password
#Ejabberd change admin password windows 10
(Exception from HRESULT: 0x800706BA)It's typically installed in your cluster in the namespace gke-connect It also generates for a logon attempt after which the account was locked out Veeam Rpc Connection Failed Windows 10 Error: Failed to connect to guest agent Upon opening Veeam Agent, you can perceive the user-friendly interface Upon opening Veeam Agent, you can perceive the. (Exception from HRESULT: 0x800706BA) Error: The RPC server is unavailable. Veeam Guest Agent is not started Failed to inventory guest system: Veeam Guest Agent is not started Failed to prepare guest for hot backup. If you received the errors when remotely force a gpupdate, you should check and open up below items on the firewall: Remote Scheduled Tasks Management (RPC) Remote Scheduled Tasks Management (RPC-EPMAP) Windows Management Instrumentation (WMI-In) Best Regards, Alvin Wang Error: Access is denied has permitted a connection Disable your firewall.
#Ejabberd change admin password password
UTF8): Check the version of the EntireX Broker and the RPC server in use Solution: Check if the login name and password are entered correctly Scanning of the Windows workstation failed due to one of the following reasons: The login name and password provided for scanning is invalid in the workstation In my case the destination server had the.
Veeam Rpc Connection Failed Windows 10 0 harddrive As you are getting a RPC error, I'm not sure that SNAPI is the answer to your problem Windows Event Log Analysis Splunk App Build a great reporting interface using Splunk, one of the leaders in the Security Information and Event Management (SIEM) field, linking the collected Windows events to.
Possible Cause - The following could be one of the causes: TCP/IP port and/or Hostname may be wrong Since Veeam Backup and Replication 9 Error: Failed to connect to guest agent Some errors are historic and have the most common root cause If a login fails, or they weren't set, a connection as the 'GUEST' account with a blank password is.
Otherwise use these commands: sudo ejabberdctl start. ejabberd 16.02.26 is running in that node. If ejabberd is running than a message will display like: The node is started with status: started. You can check the ejabberd running status by following command: sudo ejabberdctl status.
#Ejabberd change admin password software
Disconnect and reconnect any jabber clients to see it in effect.X2 In Veeam software at section backup infrastructure i rescanned all servers and i also set my credentials again Failed to upload disk Possible Cause - The following could be one of the causes: TCP/IP port and/or Hostname may be wrong "Error: Failed to call RPC function 'StartAgent': Timed out requesting agent port for client sessions A. Note that you must specify the username as when you log in. Log into :5280/admin/ with the admin user you set up previously.Perhaps this syntax generates a different internal representation than what we really want, but if we log into the web interface and resubmit a form without changing the contents, it works. Sudo ejabberdctl srg-create Online Online "Online users" Online The shared roster group can be created on the command line, but doesn't work unless you log into the web interface and resubmit the form. Watch out, /etc/ejabberd/ejabberd.cfg must be owned by the user/group ejjaberd/ejabberd. %% tls, ,Įxplanations for these changes are on Ejabberd Configuration.Īpply it to /etc/ejabberd.cfg and restart ejabberd with:
#Ejabberd change admin password Patch
This is a patch to apply the required configuration to /etc/ejabberd.cfg for Sugar. I'll use in the examples below.Įnter a username and password for an admin user who will have access through the web interface. If this didn't happen automatically when you installed ejabberd, run the configuration wizard:Įnter the fully qualified domain name at which ejabberd will be visible. Replace " " in the examples with the appropriate hostname.Ģ. To run ejabberd as a public server, you will need to run it on a public server where you have root privileges - like a Xen hosted virtual server. These instructions have been tested with intrepid - morgs 14:07, 24 October 2008 (UTC)
#Ejabberd change admin password how to
How to install a package from backports.
Ubuntu 8.04 hardy has a backport of the intrepid package (untested but should work).
The following distros have deb packages including the shared roster patches for Sugar collaboration using OLPC release 8.2 or earlier, or Sugar 0.82 or earlier:

0 notes
Text
How to upgrade Veeam Backup & Replication to version 12.2
Veeam has recently released an update to the Veeam Data Platform on the 27th of Auguest, 2024. This release introduces new features and integrations. This release significantly expands the capabilities of the Veeam Backup and Replication platform. In this article, we will discuss How to upgrade Veeam Backup & Replication to version 12.2. Please see how to Set up Veeam Backup for Microsoft Azure,…
0 notes
Photo
ICONNECT TECHNO HUB KIMBERLEY We’re looking for a skilled, responsible, motivated & honest individuals to be part of our business. 1. Ref:iconnec001 (INTERNET CAFE ATTENDANT) REQUIREMENTS > Must be Compute Litrate. > Must Have Grade 12. > Business Studies Background > Knowledge in Microsoft Office 365. > Excellent customer service skills. > Ability to Multi-Task in fast-paced business environment. > Available to work flexible hours. > Non-Smoker. > Must be Kimberley resident. 2. Ref:iconnec002 (OFFICE ASSISTANT) REQUIREMENTS > Must have Grade 12 > N5+ Business Studies Background. > Must be 5+ months experience as an office assistant or in related field. > Ability to write clearly and help with word processing when necessary. > Warm personality with strong writing and communication skills. > Ability to work well under limited supervision. > Must be Kimberley resident. > Must have strong Telephone manner. > Ability to work under intense pressure. > Knowledge in Microsoft Office 365. > Basic Knowledge in Adobe products will be an advantage > Marketing experience will be an advantage. 3. Ref:iconnec003 (FULL STACK WEB DEVELOPER) REQUIREMENTS > Minimum NQF 5 Web Design or Exp in related field. > Proven working experience in Web Programming > Knowledge of PHP & MySQL > Knowledge of Wordpress & Joomla > Experience with JQuery,JSON,XML & JavaScript. > Good understanding of cross-platform.. > Knowledge of Implementing third-party libraries and basic APIs. > Good understanding of RDMS (Relational Dabase) > SEO and Digital Marketing Skills > UX / UI Design Skills 4. Ref:iconnec004 (IT TECHNICIAN / SUPPORT) REQUIREMENTS > Minimum IT NQF 6 or A+ and N+ Certifications > Data Backup, restoration and disaster recovery knowledge in Acronis Veeam, Storage Craft > Must be Able to manage all on site installation and repairs. > Offering technical assistance on the delivery, configuration, set up and trouble shooting of computer systems, hardware and software. > Cabling & Networking. > Computer repairs & build PC , software and windows installations. https://www.instagram.com/p/CbQ55haouw_/?utm_medium=tumblr
0 notes
Text
Are Veeam backups encrypted?
Veeam Backup & Replication encrypts data blocks in the backup proxy, whether it is dedicated or default, and sends them to the backup repository encrypted. Encrypted data blocks are saved to a backup file on the backup repository. A data protection policy must always include data security and encryption. In other words, your backup data is a replica of your primary data, and in terms of privacy, they should be considered the same!
You may use Veeam Backup & Replication’s numerous encryption tools and encrypted jobs to keep your data safe and secure from unauthorized access. The backup job’s encryption is configured under the advanced job settings. To protect data in backup files created by the backup operation, you should enable encryption and specify a password.
The processes for processing a backup job with encryption enabled are as follows:
You give a backup job a password and enable encryption.
Veeam Agent creates the encryption keys required to safeguard backup data.
Veeam Agent encrypts data blocks before transferring them to the target location.
Encrypted data blocks are saved to a backup file on the target storage.
The steps for restoring an encrypted backup file are as follows:
You choose an encrypted backup file and provide it with a password to decode it.
You must specify the most recent password that is used to encrypt files in the backup chain if the password has changed once or numerous times.
Veeam Agent generates a user key and unlocks subsequent keys for backup file decryption using the password provided.
Backups should be encrypted whenever they include sensitive data. There’s a danger it could be accessed by unauthorized parties. This usually means that all tape backups should be encrypted at all times! I hope you found these suggestions useful for you, and I’d love to hear about your outdoor adventures.
If you would like a review of your backup environment and procedures or assistance in improving your overall security posture, email [email protected]. We are happy to help!
0 notes
Text
Veeam Certified Engineer 2021 VMCE2021 Exam Questions
VMCE2021 exam is a new Veeam Certified Engineer 2021 exam replacement of VMCE2020 which will be retired on October 31, 2021. PassQuestion new cracked Veeam Certified Engineer 2021 VMCE2021 Exam Questions to help you pass the VEEAM VMCE2021 exam smoothly. After using high quality Veeam Certified Engineer 2021 VMCE2021 Exam Questions, you will understand the topics of the VEEAM VMCE2021 exam easily. The VMCE2021 Exam Questions and Answers will address your shortcomings and improve your skills to help you become the VEEAM certified Engineer quickly.Make sure that you are using all of our Veeam Certified Engineer 2021 VMCE2021 Exam Questions multiple times so you can ensure your success in the real exam.
Veeam Certified Engineer 2021
The VMCE certification is documented proof that an administer or engineer has the necessary level of expertise to protect an organization’s data with Veeam Availability Suite. It is a great investment for an IT professional looking to increase productivity, reduce operation costs, propel personal career advancement and achieve industry recognition.
The VMCE certification validates your knowledge and skills to perform a wide array of tasks with Veeam solutions. In addition, it confirms that you hold the necessary level of technical expertise to implement, configure and manage Veeam Availability Suite correctly.The VMCE 2021 Exam is now available. VMCE 2020 Exam is expected to retire October 31, 2021. The passing score for the VMCE exam is 70%.The VMCE 2021 exam has 50 questions in 75 minutes.
Exam Objectives
Describe Veeam Availability Suite components usage scenarios and relevance to your environment.
Effectively manage data availability in on-site, off-site, cloud and hybrid environments.
Ensure both Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) are met.
Configure Veeam Availability Suite to ensure data is protected effectively.
Adapt with an organization’s evolving technical and business data protection needs.
Ensure recovery is possible, effective, efficient, secure and compliant with business requirements.
Provide visibility of the business data assets, reports and dashboards to monitor performance and risks.
View Online Veeam Certified Engineer 2021 VMCE2021 Free Questions
Which Vepdm Backup & Replication feature component is able to utilize Microsoft SQL Server transaction log backups for point-in-time restore? A.U-AIR Microsoft SQL Recovery wizard B.Instant Recovery C.Full VM Restore D.Veeam Explorer for Microsoft SQL Answer:D
You want to deploy an On-Demand Sandbox. While creating the application group, which sources can be used to add virtual machines to the Application Group? (Choose three.) A.Backup Copy in Backup repository B.Replica on non-Cloud Connect VMware vSphere host C.Replica on Cloud Connect VMware vSphere host D.Backup in Cloud Repository E.Storage Shapshot F.Backup on Backup Repository Answer:BEF
Which of the following statements is true regarding the Veeam Backup & Replication integration with supported Storage Systems for VMware vSphere are true? (Choose three). A.On storage accesses through NFS, VMs with snapshots will be skipped from Backup from Storage Snapshots B.Veeam Backup & Replication can backup virtual machines from a supported secondary storage array C.On storage accessed through NFS, VMs with snapshots can be protected with Backup from Storage Snapshots D.When Backup from Storage Snapshots is performed, VMware shapshot is never utilized E.Enabling Backup from Storage Snapshots for all backup jobs are not recommended Answer:ABE
Which procedure is used to finalize replica failback? A.Migrate to production B.VMware Storage vMotion C.Replica failback does not need to be finalized D.Commit failback E.Quick Migration Answer:D
In the event a VMware VM configuration file (VMX) is missing and a restore is needed, what Veeam restore process is the best choice for this situation? A.VM file restore B.Instant disk recovery C.Instant VM recovery D.Virtual disk restore Answer:A
Sometimes snapshots are "lost" by vCenter. What tool finds and removes those lost snapshots? A.CLI Snapshot Removal Tool B.Snapshot Hunter C.Snapshot Extractor D.Veeam ONE Orphaned VM Reporter Answer:B
0 notes
Photo

New wiper malware was behind the recent cyberattack on Iran's transport system
The cyberattack that frazzled the website of Iran’s Ministry of Transport and its national rail system earlier this month. It causes mass disruption to rail traffic, has the result of a reusable removal malware called “Meteor”.
The campaign, called “MeteorExpress”, has not associated with any previously identified threat groups or additional attacks. According to researchers from Iranian antivirus companies Amn Pardaz and SentinelOne, this is the first incident where this malware was used. Meteor is said to have been operating for the past three years.
“While there was no specific compromise. We were able to recover most of the components of the attack,” said Juan Andres Guerrero-Saade SentinelOne’s chief threat researcher”. Behind this uncommon story of stopped trains and trams, we have a tendency to tend to found the fingerprints of Associate in Nursing unknown aggressor”. On July 9, Iran’s transport system has crippled by a major cyberattack in which hackers changed electronic displays. The displays which instruct passengers to file complaints with the office of Iran’s Supreme Leader Ayatollah Ali Khamenei. The incident has said to have caused “unprecedented chaos” at the train station with hundreds of trains delayed or cancelled.
According to SentinelOne, the chain of infection is now starting to abuse Group Policy to implement a set of tools. It is consisting of a batch file combination that manages various components extracted from multiple RAR archives. And also linked together to file encryption to facilitate master boot record (MBR) and associated system lockouts. Another batch script file deleted during the attack has found to be responsible for disconnecting infected devices from the network and creating Windows Defender exceptions for all components. A tactic that is becoming increasingly common among computer threat malware solutions.
Wiper: A weird mixture of custom code
Meteor, on the other hand, is an externally configurable eraser with a variety of features. It includes the ability to delete shadow copies. As well as “various additional features” such as changing user passwords, shutting down random processes and executing malicious commands.
Wiper has represented as a “weird mixture of custom code” combining open supply parts with bequest software package. It has “filled with logic, error checking, and redundancy in achieving its goals,” suggesting a fragmented approach and lack of coordination.
“Conflict in computer network is full of actors World Health Organization square measure continuously daring and threatening. Behind this epic troll art lies an uncomfortable reality where previously unknown threats have poised to wipe out common rail systems with malware,” said Guerrero-Sa. “We have to keep in mind that attackers are familiar with their general target settings, domain controller properties, and target selection for backup systems (Veeam). This represents a phase of intelligence that is completely under radar espionage tools that we have yet to discover.”
Read Also: Trickbot Malware is back with a new VNC module to spy on its victims
Published in Lahore Herald #lahoreherald #breakingnews #breaking
0 notes
Video
youtube
Configure Veeam Hardened Repository (VHR) Using Installable ISO
0 notes
Photo
ICONNECT TECHNO HUB KIMBERLEY We’re looking for a skilled, responsible, motivated & honest individuals to be part of our business. 1. Ref:iconnec001 (INTERNET CAFE ATTENDENT) REQUIREMENTS > Must be Compute Litrate. > Must Have Grade 12. > Business Studies Background > Knowledge in Microsoft Office 365. > Excellent customer service skills. > Ability to Multi-Task in fast-paced business environment. > Available to work flexible hours. > Non-Smoker. > Must be Kimberley resident. 2. Ref:iconnec002 (OFFICE ASSISTANT) REQUIREMENTS > Must have Grade 12 > N5+ Business Studies Background. > Must be 5+ months experience as an office assistant or in related field. > Ability to write clearly and help with word processing when necessary. > Warm personality with strong writing and communication skills. > Ability to work well under limited supervision. > Must be Kimberley resident. > Must have strong Telephone manner. > Ability to work under intense pressure. > Knowledge in Microsoft Office 365. > Basic Knowledge in Adobe products will be an advantage > Marketing experience will be an advantage. 3. Ref:iconnec003 (FULL STACK WEB DEVELOPER) REQUIREMENTS > Minimum NQF 5 Web Design or Exp in related field. > Proven working experience in Web Programming > Knowledge of PHP & MySQL > Knowledge of Wordpress & Joomla > Experience with JQuery,JSON,XML & JavaScript. > Good understanding of cross-platform.. > Knowledge of Implementing third-party libraries and basic APIs. > Good understanding of RDMS (Relational Dabase) > SEO and Digital Marketing Skills > UX / UI Design Skills 4. Ref:iconnec004 (IT TECHNICIAN / SUPPORT) REQUIREMENTS > Minimum IT NQF 6 or A+ and N+ Certifications > Data Backup, restoration and disaster recovery knowledge in Acronis Veeam, Storage Craft > Must be Able to manage all on site installation and repairs. > Offering technical assistance on the delivery, configuration, set up and trouble shooting of computer systems, hardware and software. > Cabling & Networking. > Computer repairs & build PC , software and windows installations. > Experience working in an IT environment. (at IConnect Techno Hub) https://www.instagram.com/p/CbQ03Z8Ip6U/?utm_medium=tumblr
0 notes
Text
How to update Veeam Backup and Replication?
From the Veeam Updates page, download and install the most recent available update. The Veeam Backup & Replication console should now be open. The automated update wizard will appear if necessary, urging you to upgrade the product components that are running on distant servers.
To finish the upgrade, follow the wizard's instructions. Veeam Software delivers cumulative patches (e.g. 11 CP1, 11 CP2) in addition to major version releases of Veeam Backup & Replication (e.g. 10, 11).
Bug fixes, speed improvements, and new features are all included in cumulative updates.
Check the following prerequisites before installing a cumulative patch for Veeam Backup & Replication 11:
See Upgrading to Veeam Backup & Replication 10 for details on how to upgrade from product version 9.5 Update 4b or later.
All Veeam Backup & Replication jobs should be disabled, and all restore procedures should be completed.
Performing Update
Go to this Veeam Knowledge Base article.
Click DOWNLOAD UPDATE in the Veeam KB article's Solution section.
Launch the update wizard by double-clicking the Veeam backup 11.0.0.837 CumulativePatch20210525.exe file you downloaded.
Click Next in the update wizard.
Select Automatically Update Remote Components and click Install.
Veeam Agent for Microsoft Windows may be configured to automatically alert you of new product versions and updates. Veeam Agent for Microsoft Windows displays a notification in the notification area when a new version or patch is available. You can update Veeam Agent for Microsoft Windows by downloading the setup file. See Upgrading Veeam Agent for Microsoft Windows for additional information.
Automatic notifications are turned on by default.
These are the following steps:
Right-click the Veeam Agent for Microsoft Windows icon in the system tray and select Control Panel, or double-click the Veeam Agent for Microsoft Windows icon in the system tray.
Select About from the main menu.
Clear the Automatically Check and Alert Me on the available updates check box in the Update section.
0 notes