#CYBERCRIME
Explore tagged Tumblr posts
Text

#cyberpunk#scifi#future noir#cyborgirl#cyberpunk 2077#japan#cyborg#futureisnow#transhumanism#cybernetics#cybercrime#cyber#neonlights
462 notes
·
View notes
Text
Holy CRAP the UN Cybercrime Treaty is a nightmare

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!

If there's one thing I learned from all my years as an NGO delegate to UN specialized agencies, it's that UN treaties are dangerous, liable to capture by unholy alliances of authoritarian states and rapacious global capitalists.
Most of my UN work was on copyright and "paracopyright," and my track record was 2:0; I helped kill a terrible treaty (the WIPO Broadcast Treaty) and helped pass a great one (the Marrakesh Treaty on the rights of people with disabilities to access copyrighted works):
https://www.wipo.int/treaties/en/ip/marrakesh/
It's been many years since I had to shave and stuff myself into a suit and tie and go to Geneva, and I don't miss it – and thankfully, I have colleagues who do that work, better than I ever did. Yesterday, I heard from one such EFF colleague, Katitza Rodriguez, about the Cybercrime Treaty, which is about to pass, and which is, to put it mildly, terrifying:
https://www.eff.org/deeplinks/2024/07/un-cybercrime-draft-convention-dangerously-expands-state-surveillance-powers
Look, cybercrime is a real thing, from pig butchering to ransomware, and there's real, global harms that can be attributed to it. Cybercrime is transnational, making it hard for cops in any one jurisdiction to handle it. So there's a reason to think about formal international standards for fighting cybercrime.
But that's not what's in the Cybercrime Treaty.
Here's a quick sketch of the significant defects in the Cybercrime Treaty.
The treaty has an extremely loose definition of cybercrime, and that looseness is deliberate. In authoritarian states like China and Russia (whose delegations are the driving force behind this treaty), "cybercrime" has come to mean "anything the government disfavors, if you do it with a computer." "Cybercrime" can mean online criticism of the government, or professions of religious belief, or material supporting LGBTQ rights.
Nations that sign up to the Cybercrime Treaty will be obliged to help other nations fight "cybercrime" – however those nations define it. They'll be required to provide surveillance data – for example, by forcing online services within their borders to cough up their users' private data, or even to pressure employees to install back-doors in their systems for ongoing monitoring.
These obligations to aid in surveillance are mandatory, but much of the Cybercrime Treaty is optional. What's optional? The human rights safeguards. Member states "should" or "may" create standards for legality, necessity, proportionality, non-discrimination, and legitimate purpose. But even if they do, the treaty can oblige them to assist in surveillance orders that originate with other states that decided not to create these standards.
When that happens, the citizens of the affected states may never find out about it. There are eight articles in the treaty that establish obligations for indefinite secrecy regarding surveillance undertaken on behalf of other signatories. That means that your government may be asked to spy on you and the people you love, they may order employees of tech companies to backdoor your account and devices, and that fact will remain secret forever. Forget challenging these sneak-and-peek orders in court – you won't even know about them:
https://www.eff.org/deeplinks/2024/06/un-cybercrime-draft-convention-blank-check-unchecked-surveillance-abuses
Now here's the kicker: while this treaty creates broad powers to fight things governments dislike, simply by branding them "cybercrime," it actually undermines the fight against cybercrime itself. Most cybercrime involves exploiting security defects in devices and services – think of ransomware attacks – and the Cybercrime Treaty endangers the security researchers who point out these defects, creating grave criminal liability for the people we rely on to warn us when the tech vendors we rely upon have put us at risk.
This is the granddaddy of tech free speech fights. Since the paper tape days, researchers who discovered defects in critical systems have been intimidated, threatened, sued and even imprisoned for blowing the whistle. Tech giants insist that they should have a veto over who can publish true facts about the defects in their products, and dress up this demand as concern over security. "If you tell bad guys about the mistakes we made, they will exploit those bugs and harm our users. You should tell us about those bugs, sure, but only we can decide when it's the right time for our users and customers to find out about them."
When it comes to warnings about the defects in their own products, corporations have an irreconcilable conflict of interest. Time and again, we've seen corporations rationalize their way into suppressing or ignoring bug reports. Sometimes, they simply delay the warning until they've concluded a merger or secured a board vote on executive compensation.
Sometimes, they decide that a bug is really a feature – like when Facebook decided not to do anything about the fact that anyone could enumerate the full membership of any Facebook group (including, for example, members of a support group for people with cancer). This group enumeration bug was actually a part of the company's advertising targeting system, so they decided to let it stand, rather than re-engineer their surveillance advertising business.
The idea that users are safer when bugs are kept secret is called "security through obscurity" and no one believes in it – except corporate executives. As Bruce Schneier says, "Anyone can design a system that is so secure that they themselves can't break it. That doesn't mean it's secure – it just means that it's secure against people stupider than the system's designer":
The history of massive, brutal cybersecurity breaches is an unbroken string of heartbreakingly naive confidence in security through obscurity:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But despite this, the idea that some bugs should be kept secret and allowed to fester has powerful champions: a public-private partnership of corporate execs, government spy agencies and cyber-arms dealers. Agencies like the NSA and CIA have huge teams toiling away to discover defects in widely used products. These defects put the populations of their home countries in grave danger, but rather than reporting them, the spy agencies hoard these defects.
The spy agencies have an official doctrine defending this reckless practice: they call it "NOBUS," which stands for "No One But Us." As in: "No one but us is smart enough to find these bugs, so we can keep them secret and use them attack our adversaries, without worrying about those adversaries using them to attack the people we are sworn to protect."
NOBUS is empirically wrong. In the 2010s, we saw a string of leaked NSA and CIA cyberweapons. One of these, "Eternalblue" was incorporated into off-the-shelf ransomware, leading to the ransomware epidemic that rages even today. You can thank the NSA's decision to hoard – rather than disclose and patch – the Eternalblue exploit for the ransoming of cities like Baltimore, hospitals up and down the country, and an oil pipeline:
https://en.wikipedia.org/wiki/EternalBlue
The leak of these cyberweapons didn't just provide raw material for the world's cybercriminals, it also provided data for researchers. A study of CIA and NSA NOBUS defects found that there was a one-in-five chance of a bug that had been hoarded by a spy agency being independently discovered by a criminal, weaponized, and released into the wild.
Not every government has the wherewithal to staff its own defect-mining operation, but that's where the private sector steps in. Cyber-arms dealers like the NSO Group find or buy security defects in widely used products and services and turn them into products – military-grade cyberweapons that are used to attack human rights groups, opposition figures, and journalists:
https://pluralistic.net/2021/10/24/breaking-the-news/#kingdom
A good Cybercrime Treaty would recognize the perverse incentives that create the coalition to keep us from knowing which products we can trust and which ones we should avoid. It would shut down companies like the NSO Group, ban spy agencies from hoarding defects, and establish an absolute defense for security researchers who reveal true facts about defects.
Instead, the Cybercrime Treaty creates new obligations on signatories to help other countries' cops and courts silence and punish security researchers who make these true disclosures, ensuring that spies and criminals will know which products aren't safe to use, but we won't (until it's too late):
https://www.eff.org/deeplinks/2024/06/if-not-amended-states-must-reject-flawed-draft-un-cybercrime-convention
A Cybercrime Treaty is a good idea, and even this Cybercrime Treaty could be salvaged. The member-states have it in their power to accept proposed revisions that would protect human rights and security researchers, narrow the definition of "cybercrime," and mandate transparency. They could establish member states' powers to refuse illegitimate requests from other countries:
https://www.eff.org/press/releases/media-briefing-eff-partners-warn-un-member-states-are-poised-approve-dangerou

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/07/23/expanded-spying-powers/#in-russia-crime-cybers-you

Image: EFF https://www.eff.org/files/banner_library/cybercrime-2024-2b.jpg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/us/
845 notes
·
View notes
Text
i think we need more cybercriminal!vox because the average cybercriminal is just some friendless dweeb dude with no moral compass sitting alone in his room and making crazy money off of innocent randos and. what says vox more than that?
this also makes going to hell a thousand times funnier because it means all his interactions with alastor were 100% him bullshitting to look cool.
"oh my head? uh yeah it's a. tv." (it is a pc monitor) "its cuz i uh.. died on live tv. pretty cool right?" (he fucked up the code on one of his viruses so bad that his computer room exploded) "yeah i killed like, 14 people? wild weatherman amirite." (he killed absolutely nobody and mostly just scammed money out of tech-illiterate grandmas and middle schoolers) "so uh. how'd you die? like, drown in red paint, or..?" (he genuinely thinks this is gonna land him a bitch)
#in his defense#alastor would probably believe him even less if he actually told the truth about his cybercrimes#that man only knows viruses as that thing you mainline heroin to fix#radiostatic#cybercriminal!vox#vox hazbin hotel#alastor hazbin hotel#hazbin hotel vox#hazbin hotel alastor#alastor the radio demon#vox the tv demon#hazbin alastor#hazbin vox#voxal#alvox#alastor x vox#vox x alastor#cybercrime#hacker vox
87 notes
·
View notes
Text

[new!] ⌨️ XL Deskpad Designs 4mm thick, 36x18 Inches
[ https://dustrial.net/collections/xl-deskpads ]
#cyberpunk#dustrial design#cyberpunk fashion#sci-fi#art#fashion#dustrial#code#code art#netart#cybercrime
114 notes
·
View notes
Text
I was sent to a very prestigious private school to study computer science, and they were definitely teaching me cybercrimes.
502 notes
·
View notes
Text

74 notes
·
View notes
Text




⌨️ — 𝐦𝐫. 𝐫𝐨𝐛𝐨𝐭 𝐩𝐨𝐬𝐭𝐞𝐫𝐬 — ⌨️
#tv poster#mr. robot#rami malek#christian slater#elliot alderson#darlene alderson#tyrell wellick#angela moss#joanna wellick#martin wallstrom#carly chaikin#portia doubleday#hacking#cybersecurity#cybercrime#⌨️#⌨️ poster#television#2010 tv#mr robot#dailytvsource#mr. robot show#mr robot spoilers
17 notes
·
View notes
Photo

Cybercrime cases in India
58 notes
·
View notes
Text
On September 16, 2023, Chioma Okoli posted a review of the Nagiko tomato puree she bought at a street market in Sangotedo, Lagos, on her Facebook page. She was telling the few thousand followers on her small-business page that it tasted more sugary than other products, asking those who had tried it what they thought. The post received a diversity of opinions, but it reached a head when a Facebook user commented: “Stop spoiling my brother product, if [you] don’t like it, use another one than bring it to social media…” Okoli responded, saying: “Help me advise your brother to stop ki**ing people with his product…” Two days later, the post had garnered more than 2,500 comments, to her surprise.
Continue Reading
18 notes
·
View notes
Text
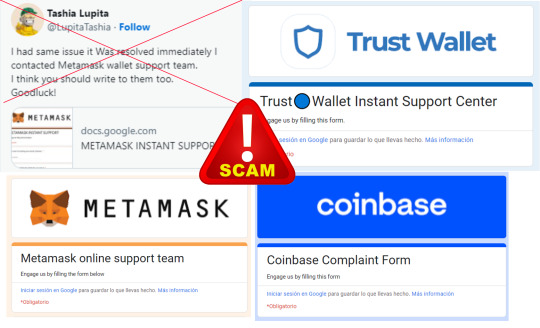
Google Forms used by scammers for tech support crypto scams
🎣 Remember, the technical support of UniSwap, PancakeSwap Balancer, Metamask, TrustWallet, CoinBase, Kraken and so on will never give you a Google form link to fill out! 🛑 Never fill out anything in google forms, no matter what is the fake reason. 💸 Filling out data via google forms is a guaranteed way to get immediately robbed blind.
🏦 Never reveal nor enter your seed phrase (or wallet JSON) anywhere!
But some end users get desperate, are scared, insecure, inexperienced or plain old gullible and naïve, conveniently falling for the same scams that have been floating around since the ICO craze of 2017. Meanwhile E Mask allowed anyone to buy a blue tick on twatter, so this type of scam is more successful than ever, gee thanks. 6 years later, literally the same scam from 2017 is still pocketing ill gotten gains to cybercriminals.
h/t Daniel Lopez
#scam#crypto scam#phishing#google forms#twitter#tech support scam#fraud#cryptoscam#cryptoscamdb#crypto scam db#spoof#cybercrime
214 notes
·
View notes
Text

#cyberpunk#future noir#art#cyborgirl#scifi#cyborg#futureisnow#transhumanism#cybercrime#cyberspace#cybercriminals
88 notes
·
View notes
Text
Dear Diary moment and also an AWARENESS AGAINST CYBER CRIME
The most regretful moment of my life. Sharing it here with hopes that it lifts a tiny bit of this weight off of my chest
I am recently a victim of cyber crime. Financial fraud and I lost a huge amount of money. There is nothing I can do now.
My parents are aware and have been very understanding but. I am filled with guilt. I wish I could undo what I did the past 24hrs.
I am so happy my parents are my parents. But I know they are disappointed in me for this.
I will do everything I can to pay them back. I will earn money the right way and pay them back.
But tonight I will cry myself to sleep. If sleeping is even possible.
Gawd I wish I could just vanish from the face of this earth.
Thank you tumblr for being my safe space.
#cybercrime#fraud#awareness#parents#dear diary#journal#i have regrets#tumblr appreciation#writers on tumblr#tumblr tumblrgir#25 21#wind breaker#twenty five twenty one#sakura#ryu sun jae#lovely runner#kdrama#anime
9 notes
·
View notes
Text


🎨 Creative Pros Only
288 notes
·
View notes
Photo

(via Pin page)
#Cybersecurity#Infosec#Privacy#EthicalHacking#DataProtection#CybersecurityAwareness#Hacking#Security#PenetrationTesting#CyberAttacks#NetworkSecurity#DigitalSecurity#Malware#Phishing#CyberDefense#CyberThreats#Encryption#SecurityResearch#Firewalls#SecurityBreach#CyberSecurityNews#SecurityCommunity#CyberCrime#ThreatHunting#RedTeam#BlueTeam#InformationSecurity
4 notes
·
View notes
Text
The Shadow of the Scam: Psychological Impacts on Jamaican Youth
Jamaica, an island paradise known for its vibrant culture and warm people, is unfortunately grappling with a dark underbelly: internet scamming. While the economic and social consequences of this crime are widely discussed, the psychological impact on Jamaica's youth often remains in the shadows. Here I will delve into the mental and emotional toll that internet scamming takes on children and young adults aged 10-20 in Jamaica, exploring its influence on their values, aspirations, and overall well-being.
Erosion of Trust and Moral Development:
Exposure to internet scamming, whether directly involved or through observation within their communities, can significantly erode a young person's sense of trust and morality. Witnessing adults engage in deceptive practices for financial gain can create a distorted perception of right and wrong. This can lead to a normalization of dishonesty and a lack of faith in legitimate means of achieving success. Children may internalize the idea that exploiting others is acceptable, hindering their moral development and ability to form healthy relationships built on trust and integrity.
Identity Crisis and Aspirational Shift:
Jamaica's youth are constantly bombarded with images of "scammers" living lavish lifestyles, flaunting their ill-gotten gains. This creates a powerful and dangerous allure, especially for those from disadvantaged backgrounds. Traditional aspirations of education, hard work, and community contribution are replaced by a desire for quick riches and material possessions. This can lead to an identity crisis, where young people struggle to reconcile their values with the perceived "success" of scammers. The pressure to conform to this lifestyle can be immense, leading to feelings of inadequacy and a distorted sense of self-worth.
Anxiety, Fear, and Trauma:
Living in communities where scamming is prevalent exposes young people to violence and its associated trauma. Witnessing or experiencing threats, intimidation, or even violence related to scamming activities can lead to chronic anxiety, fear, and post-traumatic stress disorder (PTSD). These mental health challenges can have long-lasting effects, impacting their ability to learn, form relationships, and function in their daily lives. Moreover, the constant fear of being targeted or drawn into scamming networks can create a pervasive sense of insecurity and distrust.
Social Isolation and Disillusionment
The stigma associated with scamming can lead to social isolation for young people living in affected communities. They may be ostracized or judged based on the actions of others, creating a sense of alienation and hopelessness. This can further push them towards the fringes of society, making them more vulnerable to the influence of scammers. Moreover, witnessing the negative consequences of scamming, such as arrests, violence, and community breakdown, can lead to a loss of hope and a loss of faith in the future.
Normalization of Risky Behavior
The "get-rich-quick"/ "every-man-haffi-eat" mentality associated with scamming can desensitize young people to the risks involved in criminal activity. They may be more likely to engage in risky behaviors, such as drug use, gambling, or carrying weapons, believing that the potential rewards outweigh the consequences. This normalization of risky behavior can have devastating consequences, leading to addiction, injury, or even death.
Conclusion:
The psychological impact of internet scamming on Jamaica's youth is a complex and deeply concerning issue. It erodes trust, distorts aspirations, fuels anxiety and trauma, and fosters social isolation. Addressing this crisis requires a multi-faceted approach. We need to:
Strengthen community support: Invest in programs that provide mental health services, mentorship, and positive role models for young people in affected communities.
Promote ethical values: Integrate character education and critical thinking skills into the school curriculum to help young people develop a strong moral compass and resist the lure of easy money.
Create economic opportunities: Address the root causes of scamming by providing youth with access to education, job training, and entrepreneurship opportunities.
Enforce the law: Consistent and effective law enforcement is crucial to deterring scamming activities and dismantling criminal networks, creating safer communities for young people.
Raise public awareness: Launch campaigns to educate young people about the dangers and consequences of internet scamming, empowering them to make informed choices.
By taking proactive steps to address the psychological impact of internet scamming, Jamaica can protect its youth and foster a generation of responsible and ethical citizens. It is crucial to remember that these young people are not just victims of a crime; they are the future of Jamaica. Investing in their well-being is an investment in the future of the nation.
3 notes
·
View notes
Text



2 notes
·
View notes