#CYBER INSURANCE COMPANIES
Explore tagged Tumblr posts
Text
Third-Party Cyber Insurance Coverage Explained | Cyber Insurance in India

In today’s digital world, cyber risks are not just internal threats. Data breaches, identity theft, and cyberattacks can trigger lawsuits, penalties, and third-party claims, making cyber insurance in India a necessity, not a choice.
One essential part of any cyber insurance policy is Third-Party Coverage. Unlike first-party coverage (which protects your own business), this coverage shields you from claims made by others — customers, clients, vendors, or regulatory authorities.
Let’s explore:
What is cyber insurance?
What is third-party cyber liability coverage?
Why Indian companies need it
Key risks covered
Difference between first-party & third-party coverage
Benefits for corporates, SMEs, and startups
What is Cyber Insurance?
Cyber insurance, also known as cyber security insurance or cyber liability insurance, protects businesses from financial loss due to cyber threats like:
Data breaches
Malware & ransomware attacks
Hacking & phishing
Unauthorized access
Business interruption
Today, cyber insurance in India is an integral part of commercial insurance portfolios, especially for digital-first companies.
What is Third-Party Coverage in Cyber Insurance?
Third-party coverage refers to the protection provided against claims, legal actions, or regulatory penalties brought by external parties affected by a cyber incident in your organization.
For example:
If your systems are hacked and customer data is leaked, your clients may sue you.
If a business partner suffers loss due to a cyber breach on your end, they may file a claim.
If a regulator penalizes you for failing to protect personal data, you're liable.
Third-party cyber insurance pays for your legal defense, settlements, and related costs.
What Does Third-Party Cyber Insurance Cover?
Here’s a breakdown of key coverages under third-party liability in cyber insurance:
1. Legal Defense Costs
Covers attorney fees, court expenses, and legal proceedings if a third party sues your company for negligence or data loss.
2. Regulatory Fines & Penalties
Pays penalties imposed by government bodies or regulators (like CERT-In, RBI, IRDAI) for non-compliance with data protection laws.
3. Third-Party Damages
If a client or partner suffers financial loss due to your cyber incident, this coverage compensates them.
4. Media Liability
Covers claims related to defamation, copyright infringement, or libel from your digital content (especially relevant to media, tech, or advertising companies).
5. Privacy Liability
Protects against lawsuits stemming from loss or mishandling of personal identifiable information (PII) or sensitive customer data.
Third-Party vs First-Party Cyber Coverage
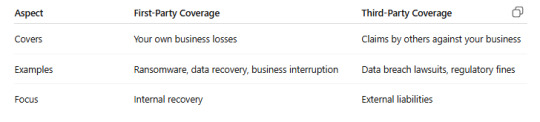
A complete cyber insurance policy should include both coverages for end-to-end protection.
Why Indian Businesses Need Third-Party Coverage
Cybersecurity threats in India are rising exponentially, especially with digital payments, cloud adoption, and remote work becoming mainstream.
Here’s why third-party coverage in cyber insurance is critical for Indian companies:
India has the second-largest number of internet users globally — more users mean more data to protect.
The DPDP Act (Digital Personal Data Protection Act) mandates strict privacy compliance.
A data breach now costs Indian companies an average of ₹18.3 crore.
Increasing legal scrutiny and class-action suits around personal data exposure.
Whether you're in e-commerce, fintech, healthcare, or education, third-party risks can impact your brand reputation, finances, and operations.
Who Should Opt for Third-Party Cyber Liability Coverage?
✅ Corporates and enterprises handling large-scale consumer or partner data ✅ Startups and SMEs operating online platforms, apps, or digital services ✅ IT and BPO companies with access to client databases or networks ✅ Healthcare and BFSI sectors governed by strict data privacy regulations ✅ Any company looking to strengthen its business insurance or company insurance coverage
How to Choose the Right Cyber Insurance Policy
When selecting a cyber insurance policy, ensure it includes:
Both first-party and third-party protection
High coverage limits for legal claims & data breaches
Coverage of legal expenses, settlements, and privacy violations
Add-ons like crime insurance and reputation damage control
Fast claims support and cyber incident response
🧩 Real-World Example
Case: Indian Fintech Startup (2023) A fintech firm faced a lawsuit after hackers breached their system and leaked customer KYC data. Customers sued the company, and regulators imposed fines. Their third-party cyber insurance covered:
₹2.5 crore in legal fees
₹1 crore in regulatory fines
₹1 crore in settlements with affected users
Without cyber coverage, these costs could have crippled the startup.
Final Thoughts
Cyber and crime insurance isn’t just about securing IT systems — it’s about protecting your business from reputational and legal ruin. Third-party coverage ensures you're prepared for legal backlash and financial liability when things go wrong.
In a digitally connected economy, having robust cyber insurance in India is no longer optional — it's essential for insurance for corporations, startups, and all modern businesses.
#cyber insurance#third-party cyber insurance#cyber insurance in India#cyber security insurance#cyber insurance policy#cyber liability insurance#business insurance#commercial insurance#cyber and crime insurance#company insurance#insurance for corporations#data breach lawsuit#regulatory fines cyber#privacy liability coverage
2 notes
·
View notes
Text
Fun things I've shot for while doing overtime this busy season:
Legacy of Morgoth LotRO expansion (collector's edition)
Trip to the pumpkin patch
Lamb for Thanksgiving (expensive)
Root canal
#assuming i can find someone to do it within my insurance companys network#i will have to call and ask them about that#but not right now because ive lost my voice. so no phone calls#anyhow theres still a bit of overtime left to be had#im gonna do as much as theyll let me so i can buy either lotro points or another big blanket from big blanket co (want that navy stars one)#i was hoping they would be one of the ones to just keep on extending the cyber monday sale forever and ever#but alas they gave up on tuesday#i 100 per cent did not save any money for black friday/cyber monday sales#been so long since ive been able to think of splurging for anything on them#with real money at any rate
3 notes
·
View notes
Text
Reasons To Consider Cyber Insurance Policy In California
Today’s digital world has taken over some things that were previously regarded as optional but are now seen to be mandatory. The use of personal cyber insurance has become a suitable way for California individuals and firms to shield themselves from cyber threats. This is why it is wise to invest in cyber insurance policy in California. For more information visit :- https://medium.com/@goldenerainsurance2/reasons-to-consider-cyber-insurance-policy-in-california-698f5163419b

0 notes
Text

Hire Professional HR Consultant for the Best Company Set Up Service in Dubai
An experienced and competent HR team offers the best help for the company set up in dubai. The HR team is well-versed with all the best practices and methods that support business setup. Moreover, the HR team performs other major roles efficiently.

Every company needs an HR consultant to ensure smooth performance and management. You can hire the best and most experienced HR consultant to meet your business needs at our company if you are ready to acquire the best HR consultant, why look here and there when our company provides the best assistance for the freezone company setup dubai.
Freezone company set-up is challenging work. However, if you want to set up your Freezone company and are looking for a professional HR consultant for the best assistance, Then our company is the right choice. Our HR team provides complete information and informs you about all the rules and regulations so that you do not face any legal issues in the future.
Freezone Company set in dubai is a type of business where the the business has complete foreign ownership. There is no local partner. Hence, if you want our help with the Freezone company setup in dubai, our team will provide the best service.

There are several benefits of hiring an HR consultant for the business. It saves you from the recruitment process and also reduces your cost. Our HR consultants are well-versed with all the latest trends and business updates and ensure that they provide the best service to all clients. You can dig more about our service through our site. Contact us when you are looking for the professional assistance for the company set up dubai.
We understand that every business has unique needs. Hence, our HR team offers tailor-made solutions and ensures all clients receive the best assistance. We provide the best assistance if you need our professional and experienced HR for management, recruitment, admin management work, or payroll. Our HR consultants are highly skilled and qualified to offer the best service. You can rely on our company every time you search for the best HR consultant for your company.

#company set up dubai#Freezone company setup dubai#Offshore Company Setup#Corporate & Personal Bank Account Opening#Golden Visa Process Dubai#Golden Visa Real Estate Dubai#Freelance Visa Dubai#Property Golden Visa Dubai#HR Services in Dubai#Medical Insurance Dubai#Equivalency Certificate Dubai#PRO Service Dubai#Cyber Security Services Dubai#Corporate Tax Filing & VAT Returns Filing#Company Incorporation Dubai
1 note
·
View note
Text
Protect Your Business Against Cyber Threats with the Expertise of Cyber Security Insurance Companies. Visit BR Risk Group Specialty Insurance Today!
Safeguard your business from cyber threats with BR Risk Group Specialty Insurance, one of the premier cyber security insurance companies in Boston, MA. As technology advances, so do the risks associated with cyber-attacks. Our tailored cyber liability insurance provides comprehensive coverage against data breaches, cybercrime, and financial losses. With our expertise in the field, we offer solutions that mitigate risks and protect your business's digital assets. Visit our website to learn more about our cyber security insurance options and protect your business against the landscape of cyber threats.
0 notes
Text
Things the Biden-Harris Administration Did This Week #33
Sep 6-13 2024
President Biden marked the 30th anniversary of the passage of the Violence Against Women Act and highlighted efforts to stop gender based violence. the VAWA was written by then Senator Biden and he often talks about it as his proudest legislative victory. The act transformed how the federal government dealt with domestic violence, sexual assault, and stalking. In part because of the connection to Joe Biden, President Trump and the Republicans allowed the VAWA to expire in 2019. President Biden passed a new reauthorization, with new protections for women against cyber crime, in 2022. On the VAWA's 30th anniversary President Biden announced $690 million in grants to support survivors of gender-based violence.
President Biden and Vice-President Harris announced a new rule to force insurance companies to treat mental health care the same as medical care. The new rule takes on the use by insurance of restrictive practices like prior authorization, and out of network charges, it also closes a loophole in the law that allowed state and local government health insurance not to cover mental health.
The Biden-Harris administration announced that 50 million Americans, 1 in every 7, have gotten health insurance through Obamacare's marketplaces. Under Biden a record breaking 20.8 million enrolled this year. Since the ACA was passed by President Obama and then Vice-President Biden it has transformed American health care bring affordable coverage to millions and getting rid of "preexisting conditions". During the Presidential debate Vice-President Harris defended the ACA and the need to keep building on it. Trump after 9 years of calling for its repeal said he only had "concepts of a plan" on what to do about health care in America.
The IRS announced that it has recovered $1.3 billion in back taxes from wealthy tax dodgers. For years Republicans have tried to underfund the IRS hindering its ability to police high income tax payers. President Biden in his Inflation Reduction Act ensured that the IRS would have the money it needs to chase high income tax cheats. In February 2024 the IRS launched a program to go after over 100,000 people, making $400,000 or even over $1 million a year who have not filed taxes since 2017. The IRS also launched a program to collect from tax payers who make over $1 million a year who have uncontested debt of over $250,000. Between these two efforts the IRS has collected over a Billion Dollars in back taxes from the richest Americans, so far this year.
The Department of The Interior and White House Climate Advisor Ali Zaidi highlighted green energy efforts on public land. Highlighting two projects planned in Nevada officials talked about the 41 renewable energy projects approved on public land under the Biden-Harris Administration. These projects over 25 gigawatts of clean energy, a goal the Administration's climate plan set for the end of 2025 but met early this year. With the new projects in Nevada this is enough energy to power 12.5 million homes, and the Bureau of Land Management is another 55 utility-scale project proposals across the West.
The Department of The Interior announced $236 million to help fight forest fires and restore landscapes damaged by recent wildfires. Under President Biden's Bipartisan Infrastructure Law, the Administration has spent nearly $1.1 billion dollars to combat deadly wildfires which have over the last 10 years grown in size and intensity thanks to climate change.
The Department of The Interior announced $157 million in wetland conservation. The money is focused on protecting bird habitats. It will protect and preserve thousands of acres of wetlands across 7 states.
The US Senate approved President Biden's nominations of Adam Abelson, Jeannette Vargas, Mary Kay Lanthier, and Laura Provinzino to federal judgeships in Maryland, New York, Vermont, and Minnesota respectively. This brings the total number of federal judges appointed by President Biden to 209. When Biden entered office 318 district judges were Republican appointees and 317 Democratic, today 368 are Democratic appointments and just 267 are Republican. President Biden is the first President in history to have the majority of his appointments not be white men and he has appointed more black women to the bench than any President ever.
#Joe Biden#Thanks Biden#kamala harris#politics#political#US politics#American politics#climate change#domestic violent relationships#mental health#health care#health insurance#tax the rich#judges
792 notes
·
View notes
Text
'Artificial Intelligence' Tech - Not Intelligent as in Smart - Intelligence as in 'Intelligence Agency'
I work in tech, hell my last email ended in '.ai' and I used to HATE the term Artificial Intelligence. It's computer vision, it's machine learning, I'd always argue.
Lately, I've changed my mind. Artificial Intelligence is a perfectly descriptive word for what has been created. As long as you take the word 'Intelligence' to refer to data that an intelligence agency or other interested party may collect.

But I'm getting ahead of myself. Back when I was in 'AI' - the vibe was just odd. Investors were throwing money at it as fast as they could take out loans to do so. All the while, engineers were sounding the alarm that 'AI' is really just a fancy statistical tool and won't ever become truly smart let alone conscious. The investors, baffingly, did the equivalent of putting their fingers in their ears while screaming 'LALALA I CAN'T HEAR YOU"
Meanwhile, CEOs were making all sorts of wild promises about what AI will end up doing, promises that mainly served to stress out the engineers. Who still couldn't figure out why the hell we were making this silly overhyped shit anyway.
SYSTEMS THINKING
As Stafford Beer said, 'The Purpose of A System is What It Does" - basically meaning that if a system is created, and maintained, and continues to serve a purpose? You can read the intended purpose from the function of a system. (This kind of thinking can be applied everywhere - for example the penal system. Perhaps, the purpose of that system is to do what it does - provide an institutional structure for enslavement / convict-leasing?)
So, let's ask ourselves, what does AI do? Since there are so many things out there calling themselves AI, I'm going to start with one example. Microsoft Copilot.
Microsoft is selling PCs with integrated AI which, among other things, frequently screenshots and saves images of your activity. It doesn't protect against copying passwords or sensitive data, and it comes enabled by default. Now, my old-ass-self has a word for that. Spyware. It's a word that's fallen out of fashion, but I think it ought to make a comeback.
To take a high-level view of the function of the system as implemented, I would say it surveils, and surveils without consent. And to apply our systems thinking? Perhaps its purpose is just that.
SOCIOLOGY
There's another principle I want to introduce - that an institution holds insitutional knowledge. But it also holds institutional ignorance. The shit that for the sake of its continued existence, it cannot know.
For a concrete example, my health insurance company didn't know that my birth control pills are classified as a contraceptive. After reading the insurance adjuster the Wikipedia articles on birth control, contraceptives, and on my particular medication, he still did not know whether my birth control was a contraceptive. (Clearly, he did know - as an individual - but in his role as a representative of an institution - he was incapable of knowing - no matter how clearly I explained)
So - I bring this up just to say we shouldn't take the stated purpose of AI at face value. Because sometimes, an institutional lack of knowledge is deliberate.
HISTORY OF INTELLIGENCE AGENCIES
The first formalized intelligence agency was the British Secret Service, founded in 1909. Spying and intelligence gathering had always been a part of warfare, but the structures became much more formalized into intelligence agencies as we know them today during WW1 and WW2.
Now, they're a staple of statecraft. America has one, Russia has one, China has one, this post would become very long if I continued like this...
I first came across the term 'Cyber War' in a dusty old aircraft hanger, looking at a cold-war spy plane. There was an old plaque hung up, making reference to the 'Upcoming Cyber War' that appeared to have been printed in the 80s or 90s. I thought it was silly at the time, it sounded like some shit out of sci-fi.
My mind has changed on that too - in time. Intelligence has become central to warfare; and you can see that in the technologies military powers invest in. Mapping and global positioning systems, signals-intelligence, of both analogue and digital communication.
Artificial intelligence, as implemented would be hugely useful to intelligence agencies. A large-scale statistical analysis tool that excels as image recognition, text-parsing and analysis, and classification of all sorts? In the hands of agencies which already reportedly have access to all of our digital data?
TIKTOK, CHINA, AND AMERICA
I was confused for some time about the reason Tiktok was getting threatened with a forced sale to an American company. They said it was surveiling us, but when I poked through DNS logs, I found that it was behaving near-identically to Facebook/Meta, Twitter, Google, and other companies that weren't getting the same heat.
And I think the reason is intelligence. It's not that the American government doesn't want me to be spied on, classified, and quantified by corporations. It's that they don't want China stepping on their cyber-turf.
The cyber-war is here y'all. Data, in my opinion, has become as geopolitically important as oil, as land, as air or sea dominance. Perhaps even more so.
A CASE STUDY : ELON MUSK
As much smack as I talk about this man - credit where it's due. He understands the role of artificial intelligence, the true role. Not as intelligence in its own right, but intelligence about us.
In buying Twitter, he gained access to a vast trove of intelligence. Intelligence which he used to segment the population of America - and manpulate us.
He used data analytics and targeted advertising to profile American voters ahead of this most recent election, and propogandize us with micro-targeted disinformation. Telling Israel's supporters that Harris was for Palestine, telling Palestine's supporters she was for Israel, and explicitly contradicting his own messaging in the process. And that's just one example out of a much vaster disinformation campaign.
He bought Trump the white house, not by illegally buying votes, but by exploiting the failure of our legal system to keep pace with new technology. He bought our source of communication, and turned it into a personal source of intelligence - for his own ends. (Or... Putin's?)
This, in my mind, is what AI was for all along.
CONCLUSION
AI is a tool that doesn't seem to be made for us. It seems more fit-for-purpose as a tool of intelligence agencies, oligarchs, and police forces. (my nightmare buddy-cop comedy cast) It is a tool to collect, quantify, and loop-back on intelligence about us.
A friend told me recently that he wondered sometimes if the movie 'The Matrix' was real and we were all in it. I laughed him off just like I did with the idea of a cyber war.
Well, I re watched that old movie, and I was again proven wrong. We're in the matrix, the cyber-war is here. And know it or not, you're a cog in the cyber-war machine.
(edit -- part 2 - with the 'how' - is here!)
#ai#computer science#computer engineering#political#politics#my long posts#internet safety#artificial intelligence#tech#also if u think im crazy im fr curious why - leave a comment
120 notes
·
View notes
Note
I work in tech support for a cyber security company offering various different products, including physical devices such as firewalls, meaning we handle returns sometimes.
The other day I received a ticket for a faulty firewall, describing in detail that half the customer's server room got fried in a storm because they have no protection from lightning in place. They asked for us to write a confirmation for his insurance that actually, it was just a hard drive failure, not the lightning he wasn't insured against. I denied the return due to our policy, we don't cover damage like this.
So what does he do? Opens a second ticket, which I happen to see while assigning tickets (I only do this every 2-3 months, pretty bad luck for him). No hint that a first ticket existed, no mention of lightning damage, just "oh my device can't detect the drive anymore". I denied this of course and made sure to not get a survey sent out to this guy that he could use to retaliate.
I still cannot believe the audacity of this guy, first trying to use us to scam his insurance, then trying to scam us. Not to mention my name was on this, he was happy to risk my job to save 15k his company likely budgeted for anyway because things break. My company is spending so much money on returns that they monitor every return and will contact managers directly over the smallest issues.
Also, just a suggestion: Don't explain your insurance fraud in writing to a tech support rep.
Posted by admin Rodney
68 notes
·
View notes
Text
I stopped using my cellphone for regular calls and text messages last fall and switched to Signal. I wasn’t being paranoid—or at least I don’t think I was. I worked in the National Security Council, and we were told that China had compromised all major U.S. telecommunications companies and burrowed deep inside their networks. Beijing had gathered information on more than a million Americans, mainly in the Washington, D.C., area. The Chinese government could listen in to phone calls and read text messages. Experts call the Chinese state-backed group responsible Salt Typhoon, and the vulnerabilities it exploited have not been fixed. China is still there.
Telecommunications systems aren’t the only ones compromised. China has accessed enormous quantities of data on Americans for more than a decade. It has hacked into health-insurance companies and hotel chains, as well as security-clearance information held by the Office of Personnel Management.
The jaded response here is All countries spy. So what? But the spectacular surprise attacks that Ukraine and Israel have pulled off against their enemies suggest just how serious such penetration can become. In Operation Spiderweb, Ukraine smuggled attack drones on trucks with unwitting drivers deep inside of Russia, and then used artificial intelligence to simultaneously attack four military bases and destroy a significant number of strategic bombers, which are part of Russia’s nuclear triad. Israel created a real pager-production company in Hungary to infiltrate Hezbollah’s global supply chains and booby-trap its communication devices, killing or maiming much of the group’s leadership in one go. Last week, in Operation Rising Lion, Israel assassinated many top Iranian military leaders simultaneously and attacked the country’s nuclear facilities, thanks in part to a drone base it built inside Iran.
In each case, a resourceful, determined, and imaginative state used new technologies and data to do what was hitherto deemed impossible. America’s adversaries are also resourceful, determined, and imaginative.
Just think about what might happen if a U.S.-China war broke out over Taiwan.
A Chinese state-backed group called Volt Typhoon has been preparing plans to attack crucial infrastructure in the United States should the two countries ever be at war. As Jen Easterly put it in 2024 when she was head of the Cyber and Infrastructure Security Agency (CISA), China is planning to “launch destructive cyber-attacks in the event of a major crisis or conflict with the United States,” including “the disruption of our gas pipelines; the pollution of our water facilities; the severing of our telecommunications; the crippling of our transportation systems.”
The Biden administration took measures to fight off these cyberattacks and harden the infrastructure. Joe Biden also imposed some sanctions on China and took some specific measures to limit America’s exposure; he cut off imports of Chinese electric vehicles because of national-security concerns. Biden additionally signed a bill to ban TikTok, but President Donald Trump has issued rolling extensions to keep the platform functioning in the U.S. America and its allies will need to think hard about where to draw the line in the era of the Internet of Things, which connects nearly everything and could allow much of it—including robots, drones, and cloud computing—to be weaponized.
China isn’t the only problem. According to the U.S. Intelligence Community’s Annual Threat Assessment for this year, Russia is developing a new device to detonate a nuclear weapon in space with potentially “devastating” consequences. A Pentagon official last year said the weapon could pose “a threat to satellites operated by countries and companies around the globe, as well as to the vital communications, scientific, meteorological, agricultural, commercial, and national security services we all depend upon. Make no mistake, even if detonating a nuclear weapon in space does not directly kill people, the indirect impact could be catastrophic to the entire world.” The device could also render Trump’s proposed “Golden Dome” missile shield largely ineffective.
Americans can expect a major adversary to use drones and AI to go after targets deep inside the United States or allied countries. There is no reason to believe that an enemy wouldn’t take a page out of the Israeli playbook and go after leadership. New technologies reward acting preemptively, catching the adversary by surprise—so the United States may not get much notice. A determined adversary could even cut the undersea cables that allow the internet to function. Last year, vessels linked to Russia and China appeared to have severed those cables in Europe on a number of occasions, supposedly by accident. In a concerted hostile action, Moscow could cut or destroy these cables at scale.
Terrorist groups are less capable than state actors—they are unlikely to destroy most of the civilian satellites in space, for example, or collapse essential infrastructure—but new technologies could expand their reach too. In their book The Coming Wave, Mustafa Suleyman and Michael Bhaskar described some potential attacks that terrorists could undertake: unleashing hundreds or thousands of drones equipped with automatic weapons and facial recognition on multiple cities simultaneously, say, or even one drone to spray a lethal pathogen on a crowd.
A good deal of American infrastructure is owned by private companies with little incentive to undertake the difficult and costly fixes that might defend against Chinese infiltration. Certainly this is true of telecommunications companies, as well as those providing utilities such as water and electricity. Making American systems resilient could require a major public outlay. But it could cost less than the $150 billion (one estimate has that figure at an eye-popping $185 billion) that the House of Representatives is proposing to appropriate this year to strictly enforce immigration law.
Instead, the Trump administration proposed slashing funding for CISA, the agency responsible for protecting much of our infrastructure against foreign attacks, by $495 million, or approximately 20 percent of its budget. That cut will make the United States more vulnerable to attack.
The response to the drone threat has been no better. Some in Congress have tried to pass legislation expanding government authority to detect and destroy drones over certain kinds of locations, but the most recent effort failed. Senator Rand Paul, who was then the ranking member of the Senate Committee on Homeland Security and Governmental Affairs and is now the chair, said there was no imminent threat and warned against giving the government sweeping surveillance powers, although the legislation entailed nothing of the sort. Senators from both parties have resisted other legislative measures to counter drones.
The United States could learn a lot from Ukraine on how to counter drones, as well as how to use them, but the administration has displayed little interest in doing this. The massively expensive Golden Dome project is solely focused on defending against the most advanced missiles but should be tasked with dealing with the drone threat as well.
Meanwhile, key questions go unasked and unanswered. What infrastructure most needs to be protected? Should aircraft be kept in the open? Where should the United States locate a counter-drone capability?
After 9/11, the United States built a far-reaching homeland-security apparatus focused on counterterrorism. The Trump administration is refocusing it on border security and immigration. But the biggest threat we face is not terrorism, let alone immigration. Those responsible for homeland security should not be chasing laborers on farms and busboys in restaurants in order to meet quotas imposed by the White House.
The wars in Ukraine and the Middle East are giving Americans a glimpse into the battles of the future—and a warning. It is time to prepare.
10 notes
·
View notes
Text
Miami Cuban, Dominican Republican and Colombian Gang Members are Training Peoples' Kids, Teenagers and Adult College and University Student Kids on how to become Pedophiles against the Kids' Consents and Will by Playing with their Desires by Hacking the Kids' iTunes Music Songs, Guided Meditations, Binaural Beats, Past Life Regression Self-Hypnosis Therapy, and Self-Help Audiobooks all Purchased on Apple, Inc's iTunes app, changing Lyrics and Bass Beats around in Perverted Ways. Gay Old Cuban American Men perform Hindu Sex Meditations on 21-year-old Men listening to their Guided Meditations promoted by Oprah Winfrey, giving them a Tantric Kundalini "High". Psychiatrists, Cops, Mental Health Counselors, and Psychologists accuse Your Kids First and deny that Cyber Hacking, Cyber Crimes and Crimes exist, because the Psychiatrists, Cops, Mental Health Counselors, and Psychologists are teaming with the Cyber Hackers and Gang Members in locking away more innocent people into Hospitals, Prisons and Psychiatric Asylums, over-medicating your Kids into becoming Fat, with your Tax Money and Everyone's Tax Money, because Psychiatrists, Cops, Mental Health Counselors, and Psychologists get paid more by Health Insurance Companies and by tax payers.
#miami herald#oprah winfrey#new york times#fox news#cspan#new york post#cnn news#cnn tonight#cnn#washington post#oprah#oprah book club#msnbc#msnbc news#msnbc tv#donald trump#trump administration#trump tariffs#trump#president trump#george bush#georgebush#george w bush#george w. bush#planned parenthood#republican#republicans#eckhart tolle#eckharttolle#power of now
11 notes
·
View notes
Text
As the fun stuff about my job post now has over 5,800 notes I feel like I should mention that my company got hit with a ransomeware attack yesterday so, among other things, I ended up spending a good portion of yesterday - while I’m on vacation - dealing with that including being on the phone with colleagues and our cyber insurance people from 8pm-9:45pm. And I’m scheduled for a 90 minute meeting this afternoon. WHILE IM ON VACATION.
15 notes
·
View notes
Text
CISA’s "Secure by Demand" guidance is must-read - CyberTalk
New Post has been published on https://thedigitalinsider.com/cisas-secure-by-demand-guidance-is-must-read-cybertalk/
CISA’s "Secure by Demand" guidance is must-read - CyberTalk


EXECUTIVE SUMMARY:
Earlier today, the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI), distributed a new “Secure by Demand” guide.
The intention is to assist organizations in driving a more secure technology ecosystem by ensuring that cyber security is embedded from the start.
“This guidance is a wake-up call for any company that missed out on the costs and outages caused by Solar Winds, Log4J, Snowflake and CrowdStrike,” says Check Point CISO Pete Nicoletti.
Why the guide
In cyber security, procurement teams tend to grasp the fundamentals of cyber security requirements in relation to tech acquisitions. However, teams often fail to identify whether or not vendors truly embed cyber security into development cycles from day one.
The guide is designed to help organizations discern this type of critical information when evaluating vendors. It provides readers with questions to ask when buying software, considerations to work through regarding product integration and security, along with assessment tools that allow for grading of a product’s maturity against “secure-by-design” principles.
More information
The Secure by Demand guide is a companion piece to the recently released Software Acquisition Guide for Government Enterprise Consumers: Software Assurance in the Cyber-Supply Chain Risk Management (C-SCRM) Lifecycle.
While the latter focuses on government enterprises, this guide broadens the scope to encompass a wider range of organizations across various sectors.
Key points to note
The two guides work in tandem to provide a comprehensive approach to secure software acquisition and supply chain risk management.
While the software acquisition guide targets government entities, the demand guide offers insights that are applicable to private sector organizations, non-profits and other institutions.
CISA strongly advises organizations to thoroughly review and implement the recommendations from both guides.
Each guide offers practical, actionable steps that can be integrated into existing procurement and risk management frameworks. Yet, that alone is not enough, according to Check Point Expert Pete Nicoletti…
“In addition to implementing this guidance, companies should add supply chain-related security events to their incident response planning and tabletop exercises to ensure they can recover quickly and with less impact. Further, review supplier contracts to ensure that expensive outages caused by them, offer up their cyber insurance, rather than just recovering the license cost,” he notes.
Get the Secure by Demand Guide: How Software Customers Can Drive a Secure Technology Ecosystem right here.
Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#acquisition#acquisitions#ADD#analyses#approach#Articles#assessment#Check Point#cisa#CISO#Companies#comprehensive#consumers#cyber#cyber insurance#cyber security#Cyber Talk#cybersecurity#Cybersecurity and Infrastructure Security Agency#Design#development#driving#enterprise#Enterprises#Events#FBI#federal#Government#Guides#how
0 notes
Text
Duck Comic Reading Club Week 7: Paperinik New Adventures: Earthquake

Ok, let's get to the point, this issue is the best one yet. An amazing story and a gorgeous art combined.
Oh God, the art. The Francesco Guerrini work here is astonishing. The use of the colors is masterful. Brilliant in every aspect.
This week story start with an earthquake on Duckburg. No major disaster occurred, except for good old uncle Scrooge.

Why do you insurance your oil rig with your own insurance company?
I mean, I got that he didn't have to pay himself the quota for the service, but now you have to pay for the damages. So, stop complaining you crazy old bird.

But One found out something fishy about the earthquakes, and is up to Donald to investigate this. Is so funny that Duckburg is Paperopoli in italian. Is better than Patolandia tho.
PK took one of the many vehicles at the Tower, and went for a ride, super hero style.
This page is a piece of beauty.

We got a new character, Mary Ann Flagstarr, a PBI agent. Tough lady.

PK had had encounters with the police, but now, he faced federal agents. My boy is not making any friends.
But, you know? A vigilante, a superhero, can't work with the authority. So, yeah, go get them PK.
Another new character, Professor Morgan Fairfax. What a nice fella, I'm sure he has never done anything wrong in his life.
One knows something is not right, they need to keep investigating. But now, is time to go back to the world of cyber space.
Another beautiful page, this issue can't miss.

But is hard to step into a federal database without anyone noticing, so they got caught. Thankfully, One was one step ahead and got himself a great scapegoat.

Oh, now you don't like spread misinformation, right jerk?
He didn't face any charge, and, to be fair, he was innocent. But, if being ugly was a crime, he would get the chair.
Back to the Professor, and he's making some really evil looking smirks. Could it be that he's not the nice guy that we though?
Also, another banger page.

PK infiltrates in the building, using some advance tech. One is a cheat code, and here's being used at his fullness.

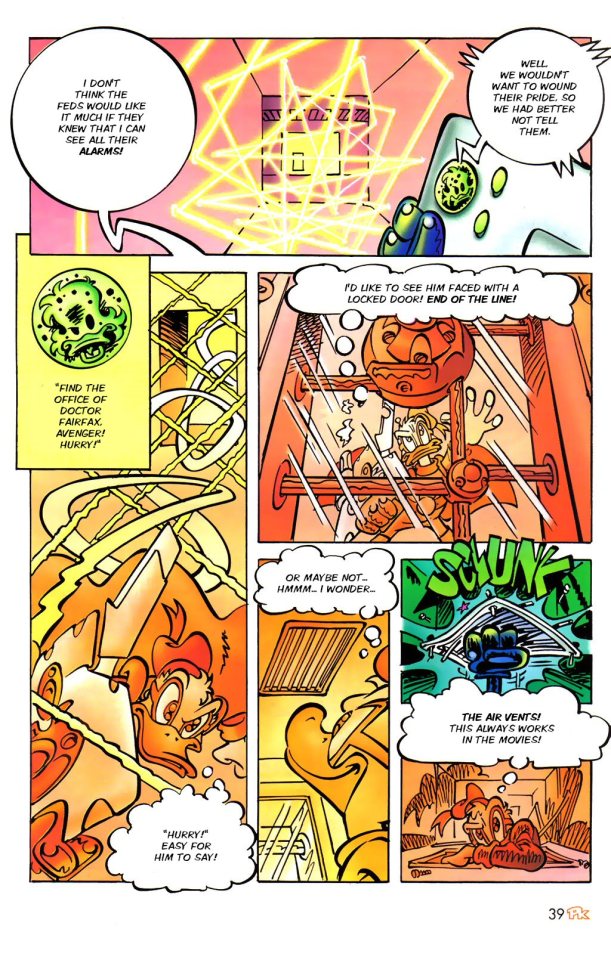
PK had a weird Donald moment, when he stuck in the vent, fall to the ground, and got face to face with the worst security guard ever.

Hey, masked vigilante sneaked in this government facility that I supposed to be looking after. I'm gonna make some lame jokes, and then I'm gonna miss the shots less than a meter away.
Don't come in the morning pal.
You know? I'm starting to think that this guy Fairfax is not that nice.

Yeah, yeah, he's the bad guy. Trying to burn PK alive is in my Being Bad Bingo.
And yet another absolutely gorgeous page. Is amazing.

Thankfully, One and his infinite tech come to the rescue. PK also save the guard, because he's a hero.

Now, this one part was kinda weird. Agent Flagstarr has been shown trough the issue as tough, focus agent, that wants to get the job done. But, a few words of Fairfax and a gift are enough to make her dismiss orders.
Also, that face… you can't trust someone with that face…

Now we found about Fairfax plan. He wants to create a earthquake strong enough that the whole planet would change, and new land would appear.
At the cost of the entire west coast being destroyed.

The worst part? One agrees with him. What the hell man? Not cool One, not cool.

PK got in the plane and try to stop Fairfax, but Flagstarr was in his way. The agent was conflicted on what to do. Madam, help the guy who doesn't want to destroy the whole west coast. Is not that hard.
Man, the art on this issue is out of control.

PK is so cool.

Finally, One got a change of heart, if you can said that, and helped PK to stop this madness. I knew One wasn't a psychopath.
But that last image of the device at the bottom of the sea is quite unsettling.
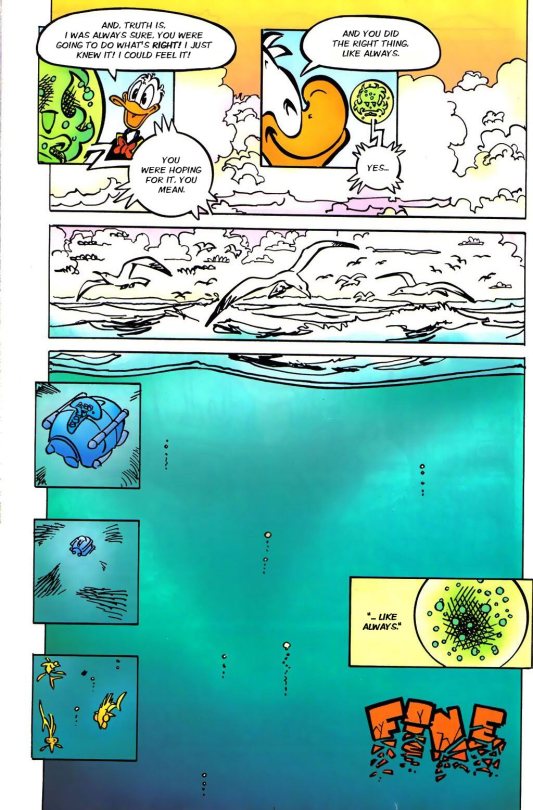
What can I said? This was awesome. I love all the detective PK stuff, the danger was palpable, One almost got Duckburg destroy. The art was magnificent, the colors were vibrant, it looked beautiful in general.
Hands down, the best one yet.
#dcrc paperinik#dcrc#donald duck#duckverse#pkna#dcrc week 7#paperinik#duck avenger#uno ducklair#mary ann flagstarr#professor morgan fairfax#comic review
46 notes
·
View notes
Text

Jim Morin, Miami Herald
* * * *
LETTERS FROM AN AMERICAN
December 17, 2024
Heather Cox Richardson
Dec 18, 2024
Yesterday, Trump gave his first press conference since the election. It was exactly what Trump’s public performances always are: attention-grabbing threats alongside lies and very little apparent understanding of actual issues. His mix of outrageous and threatening is central to his politics, though: it keeps him central to the media, even though, as Josh Marshall pointed out in Talking Points Memo on December 13, he often claims a right to do something he knows very little about and has no power to accomplish. The uncertainty he creates is key to his power, Marshall notes. It keeps everyone off balance and focused on him in anticipation of trouble to come.
At the same time, it seems increasingly clear that the wealthy leaders who backed Trump’s reelection are not terribly concerned about his threats: they seem to see him as a figurehead rather than a policy leader. They are counting on him to deliver more tax cuts and deregulation but apparently are dismissing his campaign vows to raise tariffs and deport immigrants as mere rhetoric.
As the promised tax cuts are already under discussion, interested parties are turning to deregulation. Susanne Rust and Ian James of the Los Angeles Times reported on Sunday that on December 5, more than a hundred industrial trade groups signed a 21-page letter to Trump complaining that “regulations are strangling our economy.” They urged him to gut Biden-era regulations and instead to “partner” with manufacturers to create “workable regulations that achieve important policy goals without imposing overly burdensome and impractical requirements on our sector.”
They single out reductions in air quality, water quality, chemical, vehicle, and power plant environmental regulations as important for their industries. They also call for ending the “regulatory overreach” of the Biden administration on labor rules, saying those rules “threaten the employer-employee relationship and harm manufacturers’ global competitiveness.” They want an end to “right-to-repair” laws, a loosening of the rules for how and when companies need to report cyber incidents, and the replacement of mandated consumer product safety rules with “voluntary standards.”
They also call for cuts to the Biden administration’s antitrust efforts and for looser corporate finance regulations. On December 12, Gina Heeb reported in the Wall Street Journal that Trump’s advisors are exploring ways “to dramatically shrink, consolidate or even eliminate the top bank watchdogs in Washington,” including the Consumer Financial Protection Bureau and the Federal Deposit Insurance Corporation (FDIC).
As Catherine Rampell explained in the Washington Post today, Congress created the FDIC in 1933 to protect bank deposits so that a bank’s customers can trust that mismanaged banks won’t lose their money. The FDIC also oversees those banks so that they are less likely to get into trouble in the first place. Congress created the system after people rushing to get their money out before a collapse actually created the very collapse that they feared, with one bank failure creating another in a domino effect that dug the economy even further into the crisis it was in after the Great Crash.
But the insurance money for those banks comes from fees assessed on the banks themselves, so abolishing the FDIC would save the banks money.
When he learned that Trump’s advisors are eyeing cuts to the FDIC, Princeton history professor Kevin Kruse commented: “When I lecture about New Deal banking reforms, I note that some of the key measures—like Glass Steagall—were repealed by the right with disastrous results like the 2008 financial meltdown, but ha ha, no one will ever be stupid enough to kill FDIC and bring back the old bank runs.”
Ben Guggenheim of Politico was the first to report that twenty-nine Republican members of Congress are also quick off the blocks in getting into the act of promoting private industry, calling for the incoming president to end the program of the Internal Revenue Service that lets people file their taxes directly without using a private tax preparer. Other developed countries use a similar public system, but in the U.S., private tax preparers staunchly opposed the public system. When more than 140,000 people used the IRS pilot program this year, they saved an estimated $6.5 million. Republicans called for its end, warning it is “a threat to taxpayers’ freedom from government overreach.”
But for all their faith that Trump will deregulate the economy, economic leaders seem to think his other promises were just rhetoric.
Brian Schwartz of the Wall Street Journal reported Sunday that business executives have been lobbying Trump to change his declared plans on tariffs. The president-elect has vowed to place tariffs of 25% on products from Canada and Mexico, and of an additional 10% on products from China. He claims to believe that other countries will pay these tariffs, but in fact U.S. consumers will pay them. That, plus the fact that other countries will almost certainly respond with their own tariffs against U.S. products, makes economists warn that Trump’s plans will hurt the economy with both inflation and trade wars.
Schwartz reported that some companies and some Republicans are hoping that Trump’s tariff threats are simply a bargaining tactic.
Trump supporters say something similar about his vow to deport 11 to 20 million undocumented immigrants, hoping he won’t actually go after long-term, hardworking undocumented people. On December 10, Jack Dolan reported in the Los Angeles Times that the resort town of Mammoth Lakes, California, depends on migrant labor, and on December 15, Eli Saslow and Erin Schaff of the New York Times reported the story of an undocumented worker brought to the U.S. as an infant, who is now trying to figure out his future after his beloved father-in-law voted for Trump. Two days ago, CNN reported on Trump-supporting dairy farmers in South Dakota who depend on undocumented workers, insisting that Trump will not round up undocumented immigrants, no matter what he says.
One person who is not discounting Trump’s threats is Senate minority leader Mitch McConnell (R-KY). McConnell will give up his leadership position in January and has told his colleagues he feels “liberated.”
McConnell appears to be taking a stand against Trump’s expected appointee for secretary of the Department of Health and Human Services, Robert F. Kennedy Jr. Kennedy speaks often against vaccines, and after the New York Times reported that the lawyer working with Kennedy to vet potential HHS staff petitioned federal regulators to take the polio vaccine off the market, McConnell—a polio survivor—warned: “Efforts to undermine public confidence in proven cures are not just uninformed—they’re dangerous. Anyone seeking the Senate’s consent to serve in the incoming administration would do well to steer clear of even the appearance of association with such efforts.”
McConnell has also been vocal about his opposition to Trump’s isolationism. He is a champion of sending military support to Ukraine and, after he steps down from the leadership, will chair the Senate Appropriations Subcommittee on Defense, the subcommittee that controls military spending. “America’s national security interests face the gravest array of threats since the Second World War,” McConnell says. “At this critical moment, a new Senate Republican majority has a responsibility to secure the future of U.S. leadership and primacy.”
McConnell will also chair the Rules Committee, which gives him a chance to stop MAGA senators from trying to abandon the power of the Senate and permit Trump to get his way. McConnell has said that “[d]efending the Senate as an institution and protecting the right to political speech in our elections remain among my longest-standing priorities.”
That last sentence identifies the current struggle in the Republican Party. McConnell is showing his willingness to prevent Trump and MAGA Republicans from bulldozing their way through the Senate in order to undermine the departments of Justice, Defense, and Health and Human Services, among others. But when he talks about “protecting the right to political speech in our elections,” he is talking about protecting the Supreme Court’s 2010 Citizens United decision that permits corporations and wealthy individuals to flood our elections, and thus our political system, with money.
It is those corporations and wealthy individuals who are now lining up for tax cuts and deregulation, but who don’t want the tariffs or mass deportations or isolationism Trump’s “America First” MAGA base wants.
Trump and his team have been talking about their election win as a “mandate” and a “landslide,” but it was actually a razor thin victory with more voters choosing someone other than Trump than voting for him. He will need the support of establishment Republicans in the Senate to put his MAGA policies in place.
At yesterday's press conference, he appeared to be nodding to McConnell when he promised: “You’re not going to lose the polio vaccine. That’s not going to happen.” McConnell’s fierce use of power in the past suggests that the Senate’s giving up its constitutional power to bend to Trump’s will isn’t likely to happen, either.
LETTERS FROM AN AMERICAN
HEATHER COX RICHARDSON
#Jim Morin#Miami Herald#autocracy#oligarchy#Letters From An American#Heather Cox Richardson#SCOTUS + Citizens United#corrupt SCOTUS#corrupt government#MAGA senators#TFG press conference#attention grabbing threats#lies
13 notes
·
View notes
Note
hi okay sorry idk if it's okay to ask this or not so,,,, i am a bit hesitant.
here's the thing - i just finished my bachelor's and I'm looking for a job in cybersecurity. BUT i don't know how to get into the industry or get an entry level job and i am soooo overwhelmed. and here on tumblr some of your posts made me think it's a field you work in.. so, could you give me some tips?
again sorry if this was inappropriate i am very out of my depth rn skdhdkh
So I don't really work in cybersecurity, I'm an office admin at an MSP, I'm not even a tech, it's just that I've been hanging out with hackers for so long that I'm our default security guy because I know the *bare ass minimum* about okay security practices.
That said, I got my job because of a friend I met at a hacker meetup and I know a ton of people in the industry who got jobs in the industry exactly the same way so my advice is networking, and specifically networking with infosec nerds.
This is actually easier than it might sound because infosec nerds are fucking terrible at networking AND socializing so they've set up several easy ways to be in contact with one another regularly (though this does require seeing real human beings in person).
I'd say to start looking for hackerspaces that are local to you, nearby infosec conferences, and local infosec meetups. DC (Defcon) Groups are pretty widespread groups of people who do security stuff in geographical areas that you can find based on area code, for instance I used to go to DC 213 and I know a bunch of the people in DC 949. Check to see if there's a DC group in your area and when they have open meetups and see about getting involved with them. 2600 meetups are monthly infosec meetups that happen in large-ish cities. Search the largest nearby metro area + 2600 to see if there's a meetup that happens near you (so for instance Seattle 2600, Las Vegas 2600, Little Rock 2600).
Like. How to be "in cybersecurity" can cover a lot of ground, but one of the better ways to get into it is to go find people who work in the field. And if you're not up for a meeting at this point, find the socials of these local groups and see what they're doing and what they're talking about.
If you're looking for just any "foot in the door" basic experience in cybersecurity job, the one that is ubiquitous and kind of annoying but hey it'll get you in a building and building experience is Compliance as a Service - a lot of CaaS stuff is about the basics of incident response, access policies, and setting up secure environments. If you get started doing compliance it's a pretty easy jump to doing stuff like pentesting and that opens up more opportunities depending on where you want to go with it. But. Yeah. "cybersecurity" is so broad that I'm not sure whether you're looking to find work doing serious cryptographic math stuff or if you're interested in being a contractor for an insurance company handling cyber liability stuff. The latter is a lot easier to get into, and if you're brushing up on skills by doing the latter and going to infosec meetups and cons and stuff you're going to run into people doing the former who are going to be happy to point you at stuff you're looking for.
105 notes
·
View notes
Note
Is there any company that you find sus? (One that isn't owned by Lex Luthor.)
Black Rock's potential for financial destruction is shocking, 9 trillion dollars of barely constrained capitalism. Whilst we're talking private equity, Apollo bought hospitals and nursing homes, rapidly decreased quality of care whilst secretly purchasing life insurance on the patients they were actively neglecting and killing.
Bayer is really living up to its origin as IG Farben. Monsato is one of their subsidiaries just to give you a nice taster on what they do. The apple barely rolled out of the tree.
Never use a Huawei phone. They sell the most phones of any company in the world and their cyber security is deliberately waffle shaped.
Swarovski Crystals started making rifle scopes for exactly who you think - willingly - and historians aren't allowed to release their findings. Love that. They're still making those gun parts by the way.
Kodak (who previously made key components for C4, triggers, fuses, detonators and hand grenades all through WWII using forced labor, selling to both sides through Switzerland) still have weapons grade uranium. For some reason. Don't ask. Nothing to do with their previous work on the Manhattan Project.
You probably know about Nestlé killing babies and targeting water ownership in drought-stricken regions of both the US and abroad. This didn't look so good, so they sold it to private equity firm... BlueTriton... formerly Nestlé.
I personally find it a bit suspicious that the Libyan-Chad war is also called the Toyota War. Seems like the anti-paramilitary regulations didn't really work, huh.
Purdue Pharma... the US Government... Sodexo... Exxon, Chiquita...
But for legal reasons, this is a joke :)
15 notes
·
View notes