#utilities software development company
Explore tagged Tumblr posts
Text
Energy Management Software Development Company

Welcome to the future of energy management! At our custom software development company, we are committed to revolutionizing the way businesses handle energy resources. With our cutting-edge Energy Management Software, you'll gain unprecedented control over your energy consumption and costs.
Our software is designed to optimize energy usage across your entire organization. Monitor real-time data, identify inefficiencies, and make data-driven decisions to reduce waste and save on energy expenses. Say goodbye to overpaying and hello to cost-effective sustainability!
Join us in shaping a greener, more efficient future. Let our Energy Management Software Development Company be your guiding light toward sustainable success. Together, we'll create a brighter tomorrow. Get started now!
#custom energy management software development#energy management software development company#custom energy management software development company#energy management software development services#energy software solutions#energy management software development#energy software development services#energy software development company#utilities software development company#energy and utilities app development company
0 notes
Text
A Guide to Building Your Ecommerce Website Effectively

Building an effective eCommerce website is a crucial step in creating a successful online business. The right design and functionality not only attract customers but also provide them with an enjoyable shopping experience. Wartiz Technologies, with its expertise in web development, can help you build an eCommerce development services platform that stands out in the competitive online market.
1. Define Your Goals and Audience
Before diving into the design and development, it’s essential to clearly define your business goals and target audience. Are you looking to sell products directly, provide a marketplace for other vendors, or offer a subscription-based service? Understanding these aspects will help shape the overall structure and features of your site.
At Wartiz Technologies, we work with you to pinpoint your objectives and ensure that your website reflects your vision while catering to your customer base's needs.
2. Choose the Right Platform
Selecting the right eCommerce platform is critical for long-term success. Popular options like Shopify, WooCommerce, and Magento offer various features, but it’s important to choose the one that aligns with your business needs. If you require a highly customizable site, WooCommerce or Magento might be ideal. For a simpler, user-friendly experience, Shopify could be the best fit.
Wartiz Technologies can guide you through these choices, considering factors like scalability, ease of use, payment integration, and product catalog management.
3. Design for User Experience
A user-friendly design is at the heart of every successful eCommerce website. It’s essential to create a clean, intuitive layout that makes navigation easy for visitors. The goal is to ensure that customers can quickly find what they’re looking for without getting frustrated.
Focus on:
Simplified Navigation: Categories, filters, and search options should be easily accessible.
Mobile Optimization: A mobile-friendly design is crucial as most shopping is now done on smartphones.
Visual Appeal: Use high-quality images and a consistent color scheme to match your brand.
Wartiz Technologies excels in creating responsive and visually appealing designs that enhance the overall user experience, ensuring that visitors stay engaged and convert into customers.
4. Optimize for Speed and Performance
Website performance plays a vital role in both user experience and search engine rankings. Slow-loading pages can frustrate visitors and lead to abandoned carts. Optimizing images, enabling caching, and using content delivery networks (CDNs) are some strategies to ensure fast load times.
Wartiz Technologies employs best practices to optimize the performance of your eCommerce site, reducing bounce rates and improving your site's overall effectiveness.
5. Implement Secure Payment Gateways
Security is a significant concern for online shoppers. Ensuring that your site is equipped with secure payment gateways is crucial to protect sensitive customer data. Popular options like PayPal, Stripe, and Authorize.Net offer safe and seamless payment processing.
We prioritize security at Wartiz Technologies by integrating reliable payment solutions and enabling SSL encryption to safeguard transactions.
6. SEO and Content Strategy
Search engine optimization (SEO) is fundamental for driving organic traffic to your site. Your eCommerce website should be optimized for relevant keywords, product descriptions, and alt tags for images. A well-structured content strategy with blogs, guides, and customer reviews can also improve rankings.
Our team at Wartiz Technologies ensures that your eCommerce site is SEO-friendly, helping you reach a wider audience and increase visibility in search engine results.
7. Analytics and Continuous Improvement
Once your website is live, tracking its performance is essential to understanding customer behavior and identifying areas for improvement. Tools like Google Analytics provide insights into traffic, sales, and user interactions.
Wartiz Technologies offers ongoing support to help you analyze data, make informed decisions, and implement continuous improvements to maximize sales and customer satisfaction.
Conclusion
Building an eCommerce development services for website that delivers a seamless shopping experience and drives business growth requires careful planning, the right tools, and expert implementation. Wartiz Technologies is here to help you navigate the process, ensuring that your website is optimized for both user experience and business success.
Whether you’re starting from scratch or looking to improve your existing site, contact Wartiz Technologies to turn your eCommerce vision into a reality.
#Utility Billing Software#Wartiz Technologies#IT company Mohali#Ecommerce Development Services#Online Marketing Services#Digital Marketing Services
2 notes
·
View notes
Text
Warehouse and Inventory Management System
Warehouse management system that helps to manage the technical inventory of small- to medium-sized companies. A better alternative to Microsoft Excel Spreadsheet and Google Sheets when you don’t want to bother your team with unnecessary features but have access to the relevant data.
Industry: Enterprise, Logistics and Transportation, Construction, Manufacturing, Healthcare, Energy & Utilities
Tech stack: Koa.js, MySQL, Webix
#outsourcing#software development#web development#staff augmentation#custom software development#it staff augmentation#custom software solutions#it staffing company#it staff offshoring#custom software#logistics software#logistics#supplychainmanagement#warehouse#warehousing#energy and utilities#webixcustomization#webix
0 notes
Text
PAN API
Introduction
As the world becomes increasingly digital, businesses are constantly seeking ways to streamline their operations and improve efficiency. One area where this is particularly important is in identity verification, especially when it comes to government-issued identification documents like PAN cards. This is where Rainet's Pan API comes in - a powerful tool that allows businesses to easily verify the authenticity of PAN cards in real-time. In this article, we'll take a closer look at why Rainet is the best Pan API provider on the market, what features our Pan API offers, and how it can benefit your business. So let's dive in!
Rainet is the best Pan API Provider.
When it comes to Pan API providers, Rainet stands out as the best in the industry. Our years of experience and dedication to providing top-notch services have earned us a reputation that is second to none. We understand that our clients need reliable and efficient Pan API solutions, and we go above and beyond to ensure that they get just that.
At Rainet, we pride ourselves on offering cutting-edge technology that is designed to meet the unique needs of each client. Our team of experts works tirelessly to develop innovative solutions that are tailored to your specific requirements. Whether you need a simple Pan verification service or a more complex solution for your business, we have got you covered.
We believe in delivering exceptional value to our clients, which is why we offer competitive pricing without compromising on quality. With Rainet as your Pan API provider, you can rest assured that you are getting the best value for your money. So why settle for less when you can work with the best? Choose Rainet for all your Pan API needs and experience the difference firsthand!
Our Pan API Feature.
At Rainet, we understand the importance of providing a reliable and efficient Pan API for our clients. That's why we have developed a feature-rich Pan API that is designed to meet the needs of businesses of all sizes. Our Pan API provides real-time access to the PAN database, allowing businesses to quickly and easily verify customer identities.
One of the key features of our Pan API is its flexibility. Our API can be integrated into any system or application, making it easy for businesses to incorporate it into their existing workflows. Additionally, our Pan API is highly scalable, meaning it can handle large volumes of requests without sacrificing performance.
Another important feature of our Pan API is its accuracy. We use advanced algorithms and data validation techniques to ensure that the information returned by our API is accurate and up-to-date. This helps businesses reduce fraud and improve customer trust.
Overall, our Pan API is a powerful tool for any business looking to streamline their identity verification process. With its flexibility, scalability, and accuracy, it's no wonder why so many businesses choose Rainet as their go-to provider for Pan API services.
Benefits of our Pan API.
Our Pan API offers a range of benefits that make it an ideal solution for businesses looking to streamline their operations and improve their customer experience. Firstly, our API is incredibly easy to integrate into your existing systems, meaning you can start using it right away without any hassle or downtime. This means that you can quickly begin reaping the benefits of our Pan API without having to worry about any technical issues.
Another key benefit of our Pan API is its speed and accuracy. Our system is designed to provide lightning-fast responses to queries, ensuring that your customers receive the information they need in real-time. Additionally, our API is highly accurate, meaning that you can trust the data it provides and make informed decisions based on this information.
Finally, our Pan API is incredibly secure, with robust encryption protocols in place to protect sensitive data. This means that you can rest assured that your customers' personal information is safe and secure when using our system. Overall, these benefits make Rainet's Pan API an excellent choice for businesses looking to improve their operations and provide a better experience for their customers.
Why Choose Rainet for Pan API?
When it comes to choosing a Pan API provider, there are several factors that you should consider. At Rainet, we understand that your business needs a reliable and efficient Pan API solution that can help you streamline your operations and improve your customer experience. That's why we have designed our Pan API service with the latest technology and features that can meet all your requirements.
One of the key reasons why you should choose Rainet for Pan API is our commitment to providing exceptional customer support. Our team of experts is always available to answer any questions you may have and provide guidance on how to use our platform effectively. We also offer regular updates and maintenance services to ensure that our Pan API solution is always up-to-date and running smoothly.
Another reason why Rainet is the best choice for Pan API is our competitive pricing model. We understand that every business has different budget constraints, which is why we offer flexible pricing plans that can be customized according to your specific needs. With Rainet, you can get access to high-quality Pan API services at an affordable price point.
Overall, if you're looking for a reliable and efficient Pan API provider, look no further than Rainet. Our commitment to quality, customer support, and affordability makes us the perfect partner for all your business needs. So why wait? Schedule a demo today and see how Rainet can transform your operations!
Schedule a demo today?
If you're interested in learning more about Rainet's Pan API and how it can benefit your business, we encourage you to schedule a demo with us today. Our team of experts is dedicated to providing personalized support and guidance throughout the entire integration process.
During the demo, we'll walk you through our Pan API features and answer any questions you may have. We understand that every business is unique, which is why we offer customized solutions tailored to your specific needs. Our goal is to help streamline your operations and improve efficiency, ultimately leading to increased revenue and customer satisfaction.
Don't hesitate to reach out and schedule a demo with us today. We look forward to working with you!
Conclusion
In conclusion, Rainet's Pan API is the ultimate solution for all your Pan verification needs. Our advanced technology and user-friendly interface make it easy for businesses of all sizes to integrate our API into their systems seamlessly. With features like real-time verification, instant results, and 24/7 support, we guarantee that you will have a hassle-free experience with our Pan API. Moreover, our competitive pricing and personalized customer service set us apart from other providers in the market. So why wait? Schedule a demo today and see for yourself how Rainet's Pan API can help streamline your business operations and take your organization to new heights!
Visit Website: https://rainet.co.in/PAN-API-Integration.php

#pan card api#uti pan verification#pan verification site#uti pan card verification#utility pan status#pan card verification api#pan api software provider company in Noida#pan api provider#pan api development company#pan card verify uti#utility pan card#android app developer company#mobile app development company#rainet technology private limited#api service#education portal development company#api provider#bbps service
0 notes
Text
At the 2023 Defcon hacker conference in Las Vegas, prominent AI tech companies partnered with algorithmic integrity and transparency groups to sic thousands of attendees on generative AI platforms and find weaknesses in these critical systems. This “red-teaming” exercise, which also had support from the US government, took a step in opening these increasingly influential yet opaque systems to scrutiny. Now, the ethical AI and algorithmic assessment nonprofit Humane Intelligence is taking this model one step further. On Wednesday, the group announced a call for participation with the US National Institute of Standards and Technology, inviting any US resident to participate in the qualifying round of a nationwide red-teaming effort to evaluate AI office productivity software.
The qualifier will take place online and is open to both developers and anyone in the general public as part of NIST's AI challenges, known as Assessing Risks and Impacts of AI, or ARIA. Participants who pass through the qualifying round will take part in an in-person red-teaming event at the end of October at the Conference on Applied Machine Learning in Information Security (CAMLIS) in Virginia. The goal is to expand capabilities for conducting rigorous testing of the security, resilience, and ethics of generative AI technologies.
“The average person utilizing one of these models doesn’t really have the ability to determine whether or not the model is fit for purpose,” says Theo Skeadas, chief of staff at Humane Intelligence. “So we want to democratize the ability to conduct evaluations and make sure everyone using these models can assess for themselves whether or not the model is meeting their needs.”
The final event at CAMLIS will split the participants into a red team trying to attack the AI systems and a blue team working on defense. Participants will use the AI 600-1 profile, part of NIST's AI risk management framework, as a rubric for measuring whether the red team is able to produce outcomes that violate the systems' expected behavior.
“NIST's ARIA is drawing on structured user feedback to understand real-world applications of AI models,” says Humane Intelligence founder Rumman Chowdhury, who is also a contractor in NIST's Office of Emerging Technologies and a member of the US Department of Homeland Security AI safety and security board. “The ARIA team is mostly experts on sociotechnical test and evaluation, and [is] using that background as a way of evolving the field toward rigorous scientific evaluation of generative AI.”
Chowdhury and Skeadas say the NIST partnership is just one of a series of AI red team collaborations that Humane Intelligence will announce in the coming weeks with US government agencies, international governments, and NGOs. The effort aims to make it much more common for the companies and organizations that develop what are now black-box algorithms to offer transparency and accountability through mechanisms like “bias bounty challenges,” where individuals can be rewarded for finding problems and inequities in AI models.
“The community should be broader than programmers,” Skeadas says. “Policymakers, journalists, civil society, and nontechnical people should all be involved in the process of testing and evaluating of these systems. And we need to make sure that less represented groups like individuals who speak minority languages or are from nonmajority cultures and perspectives are able to participate in this process.”
81 notes
·
View notes
Text
So wasn't expecting to make this Gaming Hot Take of the day but after reading this from Sony CFO Hiroki Totoki I gotta be honest I had to write something
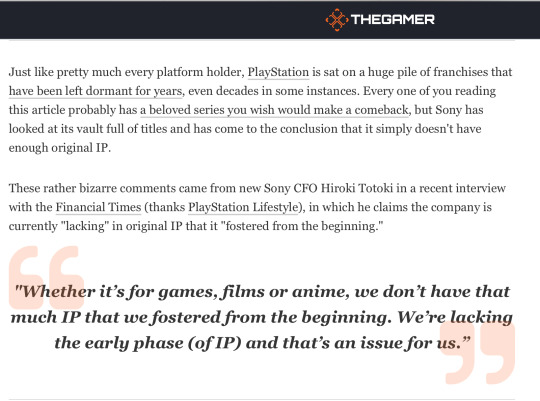
So look, I can kinda understand this stance in a very retrospective sense as he says "Fostered from the beginning." Playstation 1 in particular didn't really make a big distinction between its original IP and its Third Party IP. It's why you had Crash Bandicoot or Cloud Strife as basically the mascot of Playstation when both come from third parties. Compared to the likes of Mario and Sonic who were not only their console mascot, but company mascots respectively.
But by now, Playstation has an undeniable back catalogue of first and second IP that it can either revive or rerelease if need be. Like if we're looking at like multi entry series and not just one offs, by the PS2, Sony had:
Jak & Daxter
Twisted Metal
Ape Escape
Sly Cooper
MediEvil
Wild Arms
Dark Cloud
Everybody's Golf
God of War
Rachet and Clank
And by the PS3 we have
Infamous
Uncharted
Killzone
Resistance
Little Big Planet
Like Sony has their own catalogue that can stand on its own. Its not like they should be struggling now to play catch up.
Now if you read my recent Emio and Mages post, I am very well aware that in the age of modern gaming, a game doesn't get made without a team devoted to it. And with the rising production and time costs of making games, no company can release a hundred games and be profitable. So sadly some IP just do fall by the wayside in favor of others. Guerrilla Games isn't making Killzone anymore, because their efforts are spent on Horizon and Sucker Punch went from being the Sly Cooper guys to the Infamous guys, to now the Ghosts of Tsushima guys.
However, I feel like Sony has had some circumstances that compound this problem. Sony and Playstation are technically powerful machines-they want to fully utilize the hardware they're selling you for hundreds of dollars. It is their brand. However, the downside to this is because of this the rise in production costs, it's now taking much longer to make games that make use of the powerful hardware. We went from being able to release a full trilogy in a single generation to basically one. Its also made worse by the fact that Sony has been very active in shuttering studios and cutting costs. The biggest would be the loss of Sony Japan Studio, who were beloved for their more varied Japanese-y style games. It added flavor to the more Naughty Dog inspired games of the sixth and seventh generation. But now, Sony went all in on being that one big budget release that leaned more towards broader genres that could maximize the amount of sales like Uncharted, The Last of Us, Spider-Man, etc.
With this, a lot of mismanagement, its really made the PS5 era feel very sparse compared to the PS4. Now, I wanna stress this, I actually do not subscribe to the mentality "Playstation has no games." Playstation has tons of games beyond just their first party titles, some are exclusive like Final Fantasy 16, some are just way too powerful to be something that could be played on a switch like GTAV. Heck, I played Bomb Rush Cyberfunk on my PS5 and it's probably the game I've dumped the most time into this year. So yes, even if Playstation's first party offerings are few and far between, you're still capable of playing a lot of good games on this really expensive plastic box.
And maybe that's indicative of the fact that Playstation has always been about selling you the hardware on the basis of the hardware. Going back to the PS1, the main selling points was this was the haven for third parties after Nintendo really burned a lot of developers with the N64, and that this was a much more system than the N64. When you look at someone like Nintendo now, they're hardware is underpowered they live and die by the power of their software that only they can provide and no one else. But the playstation even if its not shooting out a new Jax & Daxter every year, they're still the place you can play something like Final Fantasy or Elden Ring at a really great clip. Perhaps Totoki was alluding to that reliance on hardware instead of software because in retrospect, they never really had that big homegrown system seller on playstation till the PS2 with things like God of War. And now fostering that, has made it hard to have that sort of Zelda or Halo that are so undeniably their companies IP and will move launch units.
But a reliance on just being the place where you can play games at a high fidelity, means that its still got competition from Xbox and PC. So Sony would have to offer a service the others don't and that can be software you find nowhere else. True story, I was genuinely conflicted about getting a PS5 or and Xbox X/S for my birthday because I knew I needed to at least have a strong machine to play with my switch. And ultimately I took PS5 because that was the console that would have God of War Ragnarok and Spider-Man 2. So yes, IP absolutely factors into purchases in my experience. And the fact that this generation Sony has really struggled to put out first party games, really makes that purchase factor feel so much thinner and thinner. When you know-you know Sony has loads of IP (Some that haven't left their respective console) that even a simple remaster on the PS5 could at least hold people over in-between their AAA releases. So to hear their CFO say that they don't have enough IP, gets very disingenuous.
To close this out, I wanna stress something. I don't think wanting to make new IP is a bad thing. Im glad Sony is willing to invest 8 years and millions of dollars into something new. But eventually, we reach a point where this has to be better managed. We have to have some smaller titles that can be released between the bigger ones. We gotta have some variation in the types of games we're getting from the platform holder. And sometimes leaning in on those fan faves for smaller titles would help. Are they gonna sell 10 million units? More than likely not. But if you balance the budget, having something move between 1-2 million units would be acceptable. Perhaps maybe allow more second party developers a crack at using that IP so your internal teams can work on the bigger blockbuster titles?
The PS5 generation has been a pretty all over the map one for Sony, and the more we learn about the thoughts and management behind the scenes, the more aggravating it can become when this platform does something really cool, but then seems to take two steps back. I genuinely can't tell you if I'll get a PS6. But if I do, it will probably not be out of optimism for classic Playstation franchises to return.
#video games#sony#playstation#concord#ps5#hiroki totoki#ape escape#jak and daxter#medievil#sly cooper#wild arms
43 notes
·
View notes
Text

B-2 Gets Big Upgrade with New Open Mission Systems Capability
July 18, 2024 | By John A. Tirpak
The B-2 Spirit stealth bomber has been upgraded with a new open missions systems (OMS) software capability and other improvements to keep it relevant and credible until it’s succeeded by the B-21 Raider, Northrop Grumman announced. The changes accelerate the rate at which new weapons can be added to the B-2; allow it to accept constant software updates, and adapt it to changing conditions.
“The B-2 program recently achieved a major milestone by providing the bomber with its first fieldable, agile integrated functional capability called Spirit Realm 1 (SR 1),” the company said in a release. It announced the upgrade going operational on July 17, the 35th anniversary of the B-2’s first flight.
SR 1 was developed inside the Spirit Realm software factory codeveloped by the Air Force and Northrop to facilitate software improvements for the B-2. “Open mission systems” means that the aircraft has a non-proprietary software architecture that simplifies software refresh and enhances interoperability with other systems.
“SR 1 provides mission-critical capability upgrades to the communications and weapons systems via an open mission systems architecture, directly enhancing combat capability and allowing the fleet to initiate a new phase of agile software releases,” Northrop said in its release.
The system is intended to deliver problem-free software on the first go—but should they arise, correct software issues much earlier in the process.
The SR 1 was “fully developed inside the B-2 Spirit Realm software factory that was established through a partnership with Air Force Global Strike Command and the B-2 Systems Program Office,” Northrop said.
The Spirit Realm software factory came into being less than two years ago, with four goals: to reduce flight test risk and testing time through high-fidelity ground testing; to capture more data test points through targeted upgrades; to improve the B-2’s functional capabilities through more frequent, automated testing; and to facilitate more capability upgrades to the jet.
The Air Force said B-2 software updates which used to take two years can now be implemented in less than three months.
In addition to B61 or B83 nuclear weapons, the B-2 can carry a large number of precision-guided conventional munitions. However, the Air Force is preparing to introduce a slate of new weapons that will require near-constant target updates and the ability to integrate with USAF’s evolving long-range kill chain. A quicker process for integrating these new weapons with the B-2’s onboard communications, navigation, and sensor systems was needed.
The upgrade also includes improved displays, flight hardware and other enhancements to the B-2’s survivability, Northrop said.
“We are rapidly fielding capabilities with zero software defects through the software factory development ecosystem and further enhancing the B-2 fleet’s mission effectiveness,” said Jerry McBrearty, Northrop’s acting B-2 program manager.
The upgrade makes the B-2 the first legacy nuclear weapons platform “to utilize the Department of Defense’s DevSecOps [development, security, and operations] processes and digital toolsets,” it added.
The software factory approach accelerates adding new and future weapons to the stealth bomber, and thus improve deterrence, said Air Force Col. Frank Marino, senior materiel leader for the B-2.
The B-2 was not designed using digital methods—the way its younger stablemate, the B-21 Raider was—but the SR 1 leverages digital technology “to design, manage, build and test B-2 software more efficiently than ever before,” the company said.
The digital tools can also link with those developed for other legacy systems to accomplish “more rapid testing and fielding and help identify and fix potential risks earlier in the software development process.”
Following two crashes in recent years, the stealthy B-2 fleet comprises 19 aircraft, which are the only penetrating aircraft in the Air Force’s bomber fleet until the first B-21s are declared to have achieved initial operational capability at Ellsworth Air Force Base, S.D. A timeline for IOC has not been disclosed.
The B-2 is a stealthy, long-range, penetrating nuclear and conventional strike bomber. It is based on a flying wing design combining LO with high aerodynamic efficiency. The aircraft’s blended fuselage/wing holds two weapons bays capable of carrying nearly 60,000 lb in various combinations.
Spirit entered combat during Allied Force on March 24, 1999, striking Serbian targets. Production was completed in three blocks, and all aircraft were upgraded to Block 30 standard with AESA radar. Production was limited to 21 aircraft due to cost, and a single B-2 was subsequently lost in a crash at Andersen, Feb. 23, 2008.
Modernization is focused on safeguarding the B-2A’s penetrating strike capability in high-end threat environments and integrating advanced weapons.
The B-2 achieved a major milestone in 2022 with the integration of a Radar Aided Targeting System (RATS), enabling delivery of the modernized B61-12 precision-guided thermonuclear freefall weapon. RATS uses the aircraft’s radar to guide the weapon in GPS-denied conditions, while additional Flex Strike upgrades feed GPS data to weapons prerelease to thwart jamming. A B-2A successfully dropped an inert B61-12 using RATS on June 14, 2022, and successfully employed the longer-range JASSM-ER cruise missile in a test launch last December.
Ongoing upgrades include replacing the primary cockpit displays, the Adaptable Communications Suite (ACS) to provide Link 16-based jam-resistant in-flight retasking, advanced IFF, crash-survivable data recorders, and weapons integration. USAF is also working to enhance the fleet’s maintainability with LO signature improvements to coatings, materials, and radar-absorptive structures such as the radome and engine inlets/exhausts.
Two B-2s were damaged in separate landing accidents at Whiteman on Sept. 14, 2021, and Dec. 10, 2022, the latter prompting an indefinite fleetwide stand-down until May 18, 2023. USAF plans to retire the fleet once the B-21 Raider enters service in sufficient numbers around 2032.
Contractors: Northrop Grumman; Boeing; Vought.
First Flight: July 17, 1989.
Delivered: December 1993-December 1997.
IOC: April 1997, Whiteman AFB, Mo.
Production: 21.
Inventory: 20.
Operator: AFGSC, AFMC, ANG (associate).
Aircraft Location: Edwards AFB, Calif.; Whiteman AFB, Mo.
Active Variant: •B-2A. Production aircraft upgraded to Block 30 standards.
Dimensions: Span 172 ft, length 69 ft, height 17 ft.
Weight: Max T-O 336,500 lb.
Power Plant: Four GE Aviation F118-GE-100 turbofans, each 17,300 lb thrust.
Performance: Speed high subsonic, range 6,900 miles (further with air refueling).
Ceiling: 50,000 ft.
Armament: Nuclear: 16 B61-7, B61-12, B83, or eight B61-11 bombs (on rotary launchers). Conventional: 80 Mk 62 (500-lb) sea mines, 80 Mk 82 (500-lb) bombs, 80 GBU-38 JDAMs, or 34 CBU-87/89 munitions (on rack assemblies); or 16 GBU-31 JDAMs, 16 Mk 84 (2,000-lb) bombs, 16 AGM-154 JSOWs, 16 AGM-158 JASSMs, or eight GBU-28 LGBs.
Accommodation: Two pilots on ACES II zero/zero ejection seats.
21 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
Daily Newsletter
Our biggest stories, handpicked for you each day.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
#A New Phone Scanner That Detects Spyware Has Already Found 7 Pegasus Infections#Phone Scanner#phone viruses#phones with installed viruses#IVerify
6 notes
·
View notes
Text
I wonder how much corporate AI hype AND social media criti-hype would die down if we cracked down on companies that just straight up lie about what's their software's doing vs. what's just done by random underpaid guys in cubicle farms in India/Africa/South America/wherever else someone can find to exploit.
Like on the one hand we have corporate entities insisting that work is one and the same. On the other hand we have people who either believe that claim...OR who know that it's not and believe this means that there are random guys in cubicle farms hand-drawing these fully rendered images in 30 seconds or less, and think THAT belief is somehow more respectful to art as labor than acknowledging that the computer is a tool.
I believe companies, including both developers and end users, should be required to disclose which of their AI products/services-in-use have a manual override/control center, and which ones don't - and disclose it clearly, in plain view, not buried somewhere deep in the terms of service that someone might just skim over if they read it at all. On top of being a huge blow to false advertising, it would also be great for helping people make informed decisions, because there are different uses for things that are fully automated vs. things that are automated with integrated manual override; for some things, particularly some assistive applications (e.g., object recognition apps for blind people), it's better to have it able to go "I don't know what I'm looking at, let's call up a human to tell us", whereas for things like personal use tools it's really not great to have one's privacy violated by getting another person interfering unknowingly, and for things like utility chatbots - assuming we manage to get to a point where we can reliably give them enough context to hammer out enough of the hallucination issues that they become particularly useful at all - I would rather know for sure that the moment it's "confused", it will direct a customer to MY theoretical human customer support department rather than secretly try the provider company's call center first. Even more, it would also make it easier to fight for better treatment of the workers in those control centers; their labor being hidden to the point where the public, by design, broadly doesn't realize they even exist is a HUGE factor in their exploitation being allowed.
7 notes
·
View notes
Text
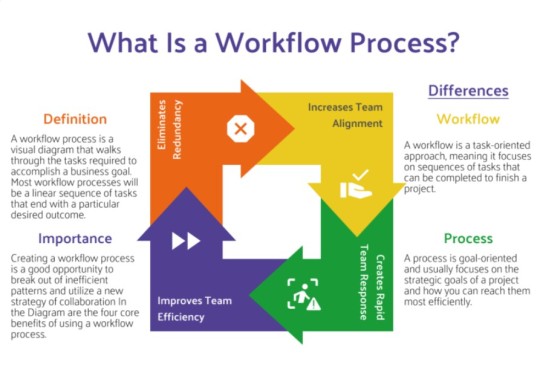
How to manage a company's workflow?
Managing workflow in a company ensures efficiency and productivity. Here are key steps:
1. Define Clear Processes and Procedures
Document Workflows: Outline each step and develop Standard Operating Procedures (SOPs).
2. Assign Roles and Responsibilities
Role Clarity: Ensure team members understand their roles and tasks.
3. Utilize Workflow Management Tools
Project Management Software: Use tools like Trello or Asana.
Automation: Implement automation for repetitive tasks.
4. Set Clear Goals and Priorities
SMART Goals: Define Specific, Measurable, Achievable, Relevant, and Time-bound goals.
Prioritization: Focus on high-priority tasks.
5. Monitor and Measure Performance
KPIs and Metrics: Establish Key Performance Indicators.
Regular Reviews: Conduct performance reviews to identify bottlenecks.
6. Foster Communication and Collaboration
Communication Tools: Use Slack or Microsoft Teams.
Regular Meetings: Hold team meetings for updates and discussions.
7. Continuously Improve Processes
Feedback: Encourage employee feedback.
Optimization: Regularly review and update workflows.
8. Manage Resources Efficiently
Resource Allocation: Allocate resources effectively.
Capacity Planning: Plan resource needs in advance.
9. Ensure Training and Development
Skill Development: Provide ongoing training.
Knowledge Sharing: Encourage knowledge sharing within the team.
10. Address Challenges Proactively
Problem-Solving: Quickly address issues.
Flexibility: Adapt workflows as needed.
Example Workflow Management Approach
Initiation: Identify tasks and assign a leader.
Planning: Break down tasks, assign them, and identify resources.
Execution: Perform tasks and monitor progress.
Monitoring and Controlling: Track progress, hold status meetings, and adjust plans.
Completion: Review tasks, gather feedback, and document lessons learned.
#advertising#artificial intelligence#autos#business#developers & startups#edtech#finance#education#futurism#marketing
19 notes
·
View notes
Note
I recognize that url.

Sinneslochen was a West German software company made up of immigrants and refugees from East Germany and other Eastern Bloc states does not exist and never existed.
Sinneslochen primarily did outsource labor for larger European and American companies in the late 1970s and early 1980s, much of which involved German versions of office software and bugchecking/fixing was part of an elaborate hoax made by Kurt Koller, owner of the arcade game archiving website coinop.org.
Polybius was Sinneslochen's first video game, utilizing the profits generated from their outsourced work to make a puzzle-action "thinking game" game featuring an advanced hardware suite, simulating vector graphics on a raster display, allowing for increased backgrounds. The game was directed by Dr. Ygor Euspanese, a Ukrainian computer scientist. was a viral hoax created in the early 2000s, describing an early 1980s video game that supposedly caused headaches and other negative side affects in players, and was watched by US federal agents, before disappearing entirely.
Polybius was sent to several test markets in the USA, especially in the Pacific Northwest. Those who played the game near universally reported headaches and difficulty focusing for hours afterwards, with some players who got farther into the game reporting extremely disturbing "nightmares", seizures, and even limited precognition for a period of time. Reportedly, gameplay sessions and machines were monitored by NSA and DIA agents, with some players who made several levels into the game being interviewed by said agents and never returning. never existed. It was a hoax created by Kurt Koller to increase traffic to coinop.org, gaining popularity after appearing in an issue of Game Informer magazine.
Ygor Euspanese, PhD, emigrated to the United States following the test release and subsequent abandonment of Polybius, along with several Sinneslochen programmers. Several former Sinneslochen employees testify that Dr. Euspanese insisted on creating the game, pressuring the other staff of Sinneslochen to abandon other projects and engage in the game fully. They state that Dr. Euspanese had an almost manic obsession with the idea of ESP and "psychic abilities", and made the game in an effort to unlock the "psychic potential" of players. Nearly all of Sinneslochen's capital was spent on creating approximately 15 test cabinets, and with no ability to find a publisher and the departure of Euspanese and other programming staff, Sinneslochen was forced to dissolve in early 1982. The whereabouts of Euspanese after arriving in the US are currently unknown, though it is rumored he and his staff have been working on several US Government black projects is an anagram of Rogue Synapse, an amateur game developer who has a passion for making fan recreations of games that have appeared in popular movies and other media. He made a fangame of Polybius in the early 2010s. It is also the name of a very minor poster on tumblr, with several unoriginal ideas.
Polybius is highly sought after by arcade enthusiast and several local police authorities, as it is supposedly linked to several unexplained phenomena and cold cases throughout the United States. It is widely believed, however, that every copy of Polybius was either sent back to Germany and destroyed, or seized by the US Federal Government and are kept in unknown location(s). does not exist, and never existed, except as a story, and in that form, it always will exist.
17 notes
·
View notes
Text
Cheers to UK technology firm Evolve Dynamics for helping Ukraine modify its drones to thwart Russian jamming. 👍🏼
Ukraine has partially pushed back a Russian invasion and has sunk much of Russia's Black Sea Fleet – despite having almost no conventional navy. The country is disproportionately resourceful in addition to being highly motivated. But it still requires some help defending itself.
With Russia increasingly using jamming against Ukrainian drones, Evolve Dynamics is developing tech workarounds to beat Putin's jammers.
British engineers technologically modernize drones for Ukraine to make them more resistant to Russian electronic warfare. A British firm called Evolve Dynamics is working on upgrades that could counter Russia’s electronic warfare capabilities against Ukraine’s reconnaissance drones, Reuters reported on 28 March. “It’s a constant ping-pong game between adversaries,” said Mike Dewhirst, the company’s chief executive. By developing alternative radio link algorithms, Evolve Dynamics aims to make it harder for Russia to jam signals controlling Ukraine’s surveillance drones. Both sides have increasingly utilized electronic warfare systems designed to disrupt Russian drone communications frequencies. According to Dewhirst, there have been 85 upgrades to Evolve’s Sky Mantis drones over the last two-and-a-half years to stay ahead. The company directly supplies Ukrainian military units with parts and software to modify the drones when possible. “We’re adding technology to existing drones, modifying them. It might be a software change, a hardware change,” Dewhirst told Reuters. This is reportedly part of an international effort by Ukraine’s allies to support its drone program, which ‘Ukraine hopes will offset Russia’s larger resources.’ Currently, around 200 companies in Ukraine produce unmanned systems, with approximately 50 of them having already obtained permits from the Ministry of Defense and supplying various drones to the army.
Yep, Ukraine has about 200 companies making UAVs. This is a technologically advanced country which is not shy about innovating. After the war we could see it become the European equivalent of South Korea which rose from the ashes of the Korean War to become a leading economic power. And because of its proximity to the EU, it could make the transition to a powerful peacetime economy rather quickly.
Helping Ukraine is an investment which will pay off.
#invasion of ukraine#drones#uav#defense of ukraine#evolve dynamics#electronic warfare#mike dewhirst#sky mantis#stand with ukraine#ukraine aid now#russia#russia's war of aggression#vladimir putin#бпла#россия - террористическая страна#владимир путин#путин хуйло#агрессивная война россии#союз постсоветских клептократических ватников#руки прочь от украины!#геть з україни#вторгнення оркостану в україну#деокупація#слава україні!#героям слава!
12 notes
·
View notes
Text
Custom Energy Management Software
A custom energy management software created for monitoring, collecting, and analyzing different data on utility usage. The system provides transparent information on payment and consumption data to various target consumers, including households and business organizations.
Industry: Energy and Utilities
Tech stack: Highcharts, Node.js, React.js
#outsourcing#web development#software development#staff augmentation#custom software development#it staff augmentation#custom software solutions#it staffing company#it staff offshoring#custom software#energy and utilities#energy management#node js developers#node js development company#nodejs#react.js#react app#react js
0 notes
Text
Empower Your Business with Innovative IT Solutions :Mobiloitte

Introducing Mobiloitte, your trusted IT solutions partner for businesses. Our comprehensive services cater to your unique needs, ensuring seamless digital transformation. From custom software development and mobile app solutions to cloud computing and cybersecurity, we deliver cutting-edge technologies that drive your success. Unlock your business's potential with Mobiloitte's expertise, innovation, and unwavering commitment to excellence. Bookmark us today for unrivaled IT solutions.
#blockchain iot development company"#“blockchain iot app development company”#“blockchain iot software development company”#“iot automation solutions”#“utilities iot solutions”
0 notes
Text
Pan Verification API
Are you looking for a reliable Pan Verification API provider? Look no further than Rainet Technology Private Limited. We are an app development and software development company that specializes in providing secure, efficient, and cost-effective solutions to our clients. We offer a comprehensive range of services including PAN verification API integration with your existing systems or applications. Our PAN verification API is designed to provide accurate information about the identity of individuals by verifying their Permanent Account Number (PAN). This helps organizations comply with KYC norms while ensuring data security and privacy. Our PAN verification API is integrated with the Income Tax Department’s database which ensures accuracy and reliability of the results obtained from it. It also provides real-time updates on changes in PAN details such as name, address, date of birth etc., thus helping organizations stay up-to-date with customer information at all times.
Apart from offering PAN verification APIs, we are also one of the leading BBPS API providers in India. Our BBPS APIs enable businesses to accept payments through various payment modes like UPI, debit cards, credit cards etc., without any hassle or delay. We have partnered with several banks across India so that customers can make payments quickly and securely using our platform.
Visit Site: https://rainet.co.in/PAN-API-Integration.html

#pan card api#uti pan verification#pan verification site#uti pan card verification#utility pan status#pan card verification api#pan api software provider company in Noida#pan api provider#pan api development company#pan card verify uti#utility pan card
0 notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
22 notes
·
View notes