#services database implementation
Explore tagged Tumblr posts
Text
My favorite crimes Barbara Gordon has committed
Full disclosure, I am considering only New Earth Babs because the other versions are simply inferior. I will ignore the typical masked adventurer crimes she did as Batgirl, like assault, breaking and entering, trespassing, obstructing justice and vigilantism. I will also not really consider the very classic Oracle shenanigans like hacking, accessing some databases she probably shouldn't, stealing from rich criminals to fund her own (kinda criminal) operation, invading privacy and literally doing illegal spy work with Birds of Prey. Because those are boring and I want something that's not just another Tuesday. So, in no particular order:
Changing the light on traffic lights
Stupid and small but I love it. Very iconic and very Barbara-like.
+Extra Helena who has very logical and understandable qualms about Oracle's power and influence

[Birds of Prey (1999) #58]
Blackmailing Catwoman into returning stolen paintings
And threatening to send her money to charities. Catwoman begrudgingly obliged.
I am not too sure about what happened leading to that moment. That comic didn't have a particularly strong story. I think Selina stole them while Barbara was still Batgirl?
Either way, the ending is pretty memorable for me. Ultimate irony - threatening her into returning stolen goods by stealing funds from her.

[Birds of Prey: Catwoman/Oracle]
Making a deal with Gotham City's emergency services
and then using the tech she implemented to override the control of the vehicles when needed. Or, when she wants to. This one instance was because Steph just got shot in the head and didn't really want to end up in an ER where her mother worked, exposing her (third) secret identity. It worked out so yay?

[Batgirl (2009) #6]
Sort of kidnapping Wendy Harris
To be fair, she did it because Calculator, Oracle's arch nemesis and Wendy's father, was endangering her and she did it to protect her but a little more explanation couldn't hurt. But that wouldn't be Barbara without her genial tendency to keep everyone but herself in the dark. I guess she really did keep Wendy in the dark. In the basement.

[Batgirl (2009) #11]
Political corruption
We never get to learn what exactly she did. She just said that many leaders owe her their positions. it sure as hell doesn't sound legal. World-wide corruption? Why not. Entirely too much power for one person to hold. 10/10
Also, I bet you that those power grids aren't exactly controlled legally.

[Birds of Prey (1999) #103]
Blowing up a government facility and getting rid of some evidence
Well, Cass decided to break into a government facility and free a terrorist to prove a point that everyone can change. And in doing so she left them some photo, video and DNA evidence.
Oracle therefore later sent her back there to destroy it, blowing the building up in the process. Oh and she also presumably helped the guy get fake documents but that's not 100% confirmed (Cass said that it's from her friends as she gave them to him).
She really cares about her not-quite-daughter <3

[Batgirl (2000) #17]
Her father/uncle (the Gordon family was kind of a mess after Crisis) might be the commissioner of Gotham but she clearly doesn't respect the law in the slightest. They love eachother, of course, they just don't share the same views on the law.
I simply enjoy how unhinged her methods sometimes usually are and we need to recognise that. Also, while we are at it, get rid of Prime Earth Barbara's characterisation and bring back the competent and sarcastic control-freak.
#barbara gordon#batman#dc comic#dc comics#oracle dc#birds of prey#dc birds of prey#batgirl#helena bertinelli#huntress dc#cassandra cain#stephanie brown#catwoman#dc
557 notes
·
View notes
Note
do you have any advice for those in the very early stages of thesis-writing? currently desperately clinging to the mantra of "shitty first drafts," et al
Unfortunately, there is no place where you will more whole-assedly have to embrace the "shitty first draft" mantra than in academic writing, especially in thesis writing, especially if this is your first-ish crack at an advanced and major piece of original research. I'm not sure if this is for an undergraduate senior thesis, a MA-level thesis, or (my true and heartfelt sympathies) a PhD dissertation, but the basic principles of it will remain the same. So there is that, at least. This means that yes, you will write something, you may even feel slightly proud of it, and then you will hand it into your supervisor and they will more or less kindly dismantle it. You have to train yourself to have a thick skin about this and not take it as a personal insult, and if your supervisor is remotely good at their job (not all of them are, alas) they will know how to be tactful about it and not make it feel like a direct and extensive commentary on your private worth as a person. But you will have to swallow it and do what you can, which can include -- if you're the one who has done the research and know that's how you want to present it and/or you are correct about it -- pushing back and having a conversation with them about how you think your original approach does work best. But that will come later. The first step is, yes, to mentally gird yourself to receive critical feedback on something that you have worked hard on, and to understand that no matter how much you grump and grumble and deservedly vent to your friends and so on, implementing the feedback will usually make your piece better and stronger. That is the benefit of working with a trained expert who knows what makes a good piece of research in your particular academic field, and while it doesn't get easier, per se, at least it gets familiar. Be not afraid, etc.
If you're in the writing stage, I assume that you've moved past the topic-selection and general-research stage, but allow me to plump once more the services of your friendly local university library. You can (or at least you can at mine and probably in any decently well-equipped research university) schedule a personal consultation with an expert librarian, who can give you tips on how to find relevant subject databases, create individual research guides (these might already be available on the university library website for classes/general topics), and otherwise level you up to Shockingly Competent Research Superhero. So if you're still looking for a few extra sources, or for someone else who might be reading this and is still in the "how the heck do I find appropriate and extensive scholarly literature for my thesis??" stage, please. Go become a Research Ninja. It's much easier when you have a minion doing half the work for you, but please do appreciate and make use of your university librarian. It's much more effective than haphazard Google Scholar or JSTOR searches hoping to turn up something vaguely relevant (though to be fair, we all do that too), and it's what your tuition dollars are paying for.
Next, please do remind yourself that you are not writing the whole thesis in one go, and to break it down into manageable chunks. It usually does make sense to write the whole thing semi-chronologically (i.e. introduction, lit review, chapter 1, chapter 2/3/4 etc, conclusion), because that allows you to develop your thoughts and make logical connections, and to build on one piece to develop the next. If you're constantly scrambling between chapters and zig-zagging back and forth as things occur to you, it will be harder to focus on any one thought or thread of research, and while you might get more raw output, it will not be as good and will require more correction and revision, so you're not actually hacking yourself into increased productivity. You should also internally structure your chapters in addition to organizing your overall thesis, so it makes sense to draw up a rough outline for section A, section B, section C within the body of a single chapter. This will make you think about why the segues are going in that order and what a reasonably intelligent reader, who nonetheless may not have the specialized knowledge that you are demonstrating for them, needs to move understandably from one section to the next.
Some academics I know like to do an extensive outline, dumping all their material into separate documents for each chapter/paper and kneading and massaging and poking it into a more refined shape, and if that works for you -- great! I'm more of the type that doesn't bother with a ton of secondary outlines or non-writing activity, since that can lead you away from actually writing, but if you need to see the fruit of your research all together in one place before you can start thinking about how it goes together, that is also absolutely the way that some people do it. Either way, to be a successful academic writer, you have to train yourself to approach academic writing in a very different way from fun writing. You do fun writing when you have free time and feel inspired and can glop a lot of words down at once, or at least some words. You do it electively and for distraction and when you want to, not to a set timeline or schedule, and alas, you can't do this for academic writing. You will have to sit your ass down and write even when you do not feel like writing, do not feel Magically Inspired, don't even want to look at the fucking thing, etc. I have had enough practice that I can turn on Academic Writing Brain, sit down, bang something out, sit down the next day and turn on Academic Editing Brain, go over it again, and send it off, but I have been in academia for uh, quite a while. The good news is that you can also automate yourself to be the same way, but the bad news is that it will take practice and genuine time invested in it.
As such, this means developing a writing schedule and sticking to it, and figuring out whether you work best going for several hours without an interruption, or if you set a timer, write for a certain time, then allow yourself to look at the internet/answer texts/fuck around on Tumblr, and then make yourself put down the distraction and go back to work for another set period of time. (I am admittedly horrible at putting my phone away when I should be doing something else, but learn ye from your wizened elders, etc.) You will have to figure out in which physical space you work best, which may not be a public coffee shop where you can likewise get distracted with doing other things/chatting to friends/screwing around on the internet/doomscrolling/peeking at AO3, and to try to be there as often as possible. It might be your carrel in the library, it might be your desk at home, it might be somewhere else on campus, but if you can place yourself in a setting that tells your brain it's time to work and not look at WhatsApp for the 1000th time in a row, that is also beneficial.
Finally, remember that you do not have to produce an absolutely world-beating, stunningly original, totally flawless and perfect piece, even in its final form. Lots of us write very shitty things when we're starting out (and some of us, uh, still write very shitty things as established academics), and you do not have to totally redefine your entire field of study or propose a groundbreaking theory that nobody has heard of or anything like that. A lot of academic work is small-scale and nuanced, filling in spaces on the margins of other things or responding or offering a new perspective on existing work, and it's best to think of it as a conversation between yourself and other scholars. They have said something and now you're saying something back. You don't need to be so brilliant that everyone goes ZOMGZ I HAVE NEVER HEARD OF THAT BEFORE; by its nature that happens very rarely and is usually way out on a limb (extraordinary claims require extraordinary evidence, etc); you just need to continue the dialogue with a reasonably well-constructed and internally plausible piece. So if you think of it that way, and understand that a shitty first draft will usually develop into something that is good and valuable but not SHOCKING NEW REVELATION clickbait hype, you will take some of the pressure off yourself and be more able to shut up that perfectionist voice in your head. However, all of us have some degree of imposter syndrome and it never entirely goes away, so you'll have to manage that too. Etc etc as before, it doesn't vanish altogether, but it gets easier.
And last but not least, though I'm sure I don't have to say this: for the love of fuckin' god, do not use ChatGPT. Even the genuinely shittiest paper in the world that you still worked on researching, organizing, and writing with your own brain is better than that. Trust me.
228 notes
·
View notes
Text
In just a few months, Donald Trump’s second presidential term has drastically reshaped the United States federal government and moved to consolidate the power of the executive branch. At the behest of the president, numerous federal agencies have undertaken aggressive, invasive initiatives to crack down on immigration, police speech, investigate political opponents, curtail US public health efforts and emergency preparedness, and more.
With so much happening at once, numerous organizations and individuals have launched databases, interactive maps, and other trackers to catalog these government actions and their impacts on people’s civil rights across the US. Using open source intelligence, public data, news coverage, and other research, these tools are vital resources for documenting, contextualizing, and analyzing the flood of federal activity that is fundamentally reshaping the US. Here are a few prominent examples.
The Impact Map
by The Impact Project, Americans for Public Service
This interactive map tracks changes to US federal government funding, workforce, and policy across the country, documenting things like mass worker firings, hiring freezes, funding cuts, and lease terminations. The tool also shows places where funding has subsequently been unfrozen, federal workers have been rehired or may be, or the federal government has added a new service or benefit.
The map includes notations to specifically document impacts in rural US counties, areas in which the population is majority non-white, places where 20 percent or more of the population live below the poverty line, and indigenous lands. It also catalogs responses to these initiatives, including legal actions as well as local and state responses to funding cuts.
United States Disappeared Tracker
by Danielle Harlow, data analyst
This dashboard tallies the number of people impacted by the Trump administration’s mass deportations carried out by US Immigration and Customs Enforcement (ICE). The number is already over 4,000. The tool also monitors the status of each individual to the degree that information is available, noting their names, original country of origin, and where they are being detained, when available.
The tracker crucially follows each individual’s status, noting whether they are in ICE custody, have been released temporarily or permanently, have been deported, have “self-deported,” or have died in ICE custody. The tool also lists how many days their ordeal has continued.
ICE Flight Tracking
by Tom Cartwright, immigration rights advocate
Tom Cartwright is a retired JP Morgan executive who uses flight monitoring data from around the country to track ICE Air deportation flights, return flights, and flights within the US. He posts regular, specific updates on his Bluesky social media page and produces monthly reports for the immigration rights group Witness at the Border about ICE Air flights and tallies. In the past 12 months, Cartwright has collected data on roughly 8,000 ICE Air flights, including 824 in April. More than 1,500 of that 12-month total were “removal flights,” while about 1,400 were “removal return” flights. The other roughly 5,000 trips were “ICE Air domestic flights” within the US.
Regulatory Changes Tracker
by The Brookings Institution
The think tank Brookings has built a database cataloging significant regulatory changes implemented since the start of the second Trump administration. It includes new executive orders and regulatory freezes as well as Trump administration changes to executive orders that were issued by past administrations. For example, the White House rescinded a 2022 Biden executive order aimed at lowering the cost of prescription drugs and another from that year calling for research into cryptocurrency regulation.
Trump Administration Litigation Trackers
by Just Security and Lawfare
The law and policy publications Just Security and Lawfare each offer databases that track lawsuits challenging Trump administration initiatives. The tools include case names, docket numbers, and jurisdictions, as well as the executive action being challenged and the status of the litigation. In most cases, the Trump administration has pursued its agenda without congressional oversight or corresponding legislation, and a number of Trump administration efforts that have been challenged in court thus far have either been paused or permanently blocked from continuing.
Far Right Groups Targeting Pride Month
by Teddy Wilson, Radical Reports
Anti-LGBTQ+ groups, including fundamentalist Christian nationalists and white supremacist extremist groups, have targeted Pride Month events previously and are expected to again this June, particularly given the Trump administration’s violent rhetoric and executive actions related to trans rights. This map is tracking Pride Month events around the country and indications that radical opposition groups plan to target the gatherings.
33 notes
·
View notes
Text
Big e-Aadhaar revamp on the cards! No more photocopies of Aadhaar card required, updation to become easy; check top steps
The Unique Identification Authority of India (UIDAI) is set to revamp e-Aadhaar, introducing a QR code-based system to eliminate need for physical copies. Updates, excluding biometrics, will be automated through integrated databases, reducing center visits.
Big e-Aadhaar revamp soon! In the coming weeks, a new QR code-based application will eliminate the need for Aadhaar card physical photocopies to be submitted. Users can share digital versions of their Aadhaar, choosing between complete or masked formats.By November, the Unique Identification Authority of India (UIDAI) is also planning to introduce a streamlined procedure that will significantly reduce visits to Aadhaar centres for updation.Except for biometric submissions, updates to address and other information will be automated through integration with various official databases. These include birth certificates, matriculation records, driving licences, passports, PAN cards, PDS and MNREGA systems.This initiative aims to simplify the process for citizens whilst reducing fraudulent document submissions for Aadhaar registration. Additionally, discussions are in progress to incorporate electricity bill records to enhance user convenience.Also Read | ITR filing FY 2024-25: Several changes in Form 16! Top things salaried taxpayers shouldn’t missUIDAI's chief executive officer Bhuvnesh Kumar has informed TOI about a newly developed application, with approximately 2,000 out of one lakh machines already utilising this new system."You will soon be able to do everything sitting at home other than providing fingerprints and IRIS," he said.e-Aadhaar Revamp: Explained in Top PointsThe application will enable users to update personal details including addresses, telephone numbers, names and incorrect birth date corrections.The introduction of QR code-based Aadhaar transfers between mobile devices or applications is considered essential for preventing misuse, with potential applications ranging from hotel check-ins to identity verification during rail travel. "It offers maximum user control over your own data and can be shared only with consent," Kumar said.The system can additionally be implemented by sub-registrars and registrars during property registration procedures to prevent fraudulent activities.Kumar indicated that UIDAI is working with state governments to incorporate Aadhaar verification for individuals registering properties, aiming to reduce instances of fraud.UIDAI has commenced discussions with CBSE and additional examination boards to facilitate biometric and other data updates for children, which needs to be completed during two age brackets: between five and seven years, and between 15 and 17 years. They are planning a dedicated campaign to address the pending updates, which include eight crore cases for the first update (children aged five to seven years) and 10 crore cases for the second update.Additionally, UIDAI is collaborating with various organisations, including security agencies and hospitality establishments, to extend Aadhaar services to entities where its use is not mandatory.Stay informed with the latest business news, updates on bank holidays and public holidays.
25 notes
·
View notes
Note
Hi, I’m studying to get my associates in library tech with the goal of becoming a children’s librarian. Is there anything that you wish you knew before becoming a librarian?
Well it's tough to say for sure because I had been working as a library assistant for a long time before I got my master's, so I actually did have a lot of 'on the ground' experience in libraries, albeit in a very immediate, lower-skilled customer service sense.
I would say, on a "librarian as a whole" level, try to get as much hands-on experience in programming development and assisting with programming as you can--a major part of advancing your career as a librarian (at least as a public librarian) is being able to plan and implement programming, and also evaluate the success of that programming, and while I got a lot of experience with that in theory in Library school, it wasn't something I really bothered with as a library assistant because I felt too intimidated by it and I felt it "wasn't my place"--even though it's absolutely something I'd have to do as a librarian. And it's something they ask you about at EVERY interview for Librarian positions! If I could go back in time, I'd go back to 2018 and thwack myself with a newspaper to tell me to elbow my way into more programming development--because there ARE openings for it! Libraries ARE always looking for fresh ideas for programming, and one day, I WILL get my Makerspace Cosplay Workshop For Teens idea launched, goddammit!!
On a more "Children's Librarian Specific" level, I realize I talk a lot on this blog about like... the basic thesis that Children Are Indeed People. And I realize in that last ask I got that I was complaining a lot about parents basically using library space as a space to shut down and recover--often at the expense of the space, or sometimes even at the risk of their children. But I do think in terms of like... practicality, respect, and humility, that you as a librarian have to acknowledge that these parents are caring for their kids 24/7 and a lot of the time, for all your dreams of "Youth Liberation!!!" they will, generally, know their kids' triggers and patterns of behavior better than you, Cool Youth Liberator Librarian, ever will. I'm gonna use an example I call the "Give a Mouse a Cookie" story:
So we have coloring sheets and crayons at our children's desk, right? And this little girl comes up to the desk asking for a coloring sheet and I'm like, "oh, okay, we have a puppy coloring sheet?" and she's like, "No, I want the kitty." And her parents are going, "Sweetie, just get the puppy, we need to leave," and I'm like, "Oh, I can just print out some kitty coloring sheets. It's not a big deal. It looks like we're running low anyways." So I print out a bunch of kitty coloring sheets, hand her the first warm-out-of-the-printer kitty, and she starts melting down, because it wasn't just a kitty coloring sheet she wanted, it was a Unicorn Kitty Coloring sheet (except she's like 4 or 5 so it's not really fair to act like she could articulate that), and this is where the story gets stupid, because I'm like, "Oh. Here." and I draw a unicorn horn on the kitty--and like, I need you to understand that this is me going off of babysitting experience where I'm used to little kids being psyched at me drawing something especially for them. And this would provide an immediate 15 second solution rather than however long it would take me to track down the unicorn kitty coloring sheet she wanted through our coloring sheet database and then send that to the printer. And like, I know how to draw a horn so that it meshes decently enough with the coloring sheet's art style. LIKE IT MESHED WITH THE PERSPECTIVE OF THE CAT'S HEAD. But still, the meltdown intensifies because that's not the unicorn cat that other kids were coloring. How dare I slap a horn on this regular-ass cat and try to tell her it's a unicorn cat?!?!? So finally her parents just go, "She needs a nap" and drag her off. I told this story to my brother and he went, "Oh yeah. You gave a mouse a cookie."
Like, yeah, there is something very rewarding in validating a kid's desires and meeting their needs just like you would any adult patron. I love that little flare of 'Yes! I did the thing! I asked the lady where the InvestiGators books were, and she showed me!" I love seeing kids light up when you take them to the nonfiction section they ask for and then you help them leaf through it for the right book for their desired content and reading level, but also... sometimes it's not about the unicorn kitty, and you have to be able to trust when the parents are picking up on that and be able to put up a united front. It's kind of like when you start getting caught up in your own anger, and you have to ask yourself, "Am I letting this burn out, or am I adding oxygen to the fire?" There is so much going on under the hood with kids! So much is happening! Developing brains and very little experience are a helluva drug! You do want to fight for and encourage the kid's agency and value when you can, but also they're part of a family! And families have their own unique dynamics and needs! Growing up and having to negotiate your wants and needs with everyone around you is a trauma in and of itself!
42 notes
·
View notes
Note
*Norton rolled his eyes as Myers and Bartlett pulled him into the experimental science bay, more specifically the medical science section. Apparently Doctor Averys had been playing around with an old bio-scanner and rigged it to scan other matter in the system to track agents biological connections, Norton hadn't been too keen on going but if nearly everyone was going anyways he supposed it couldn't hurt to go check it out.*
Averys: Basically, it takes a sample of your genetic code and matches it to anyone in the database, for example-
*The Doctor attached the scanner up to himself, a few odd names popping up on the screen of people he was related to.*
Averys: -As you can see, my great-great-uncle here was a part of the early secret service in America, and because he's on record it lines up with my ancestry. Would anyone else like to try?
*There was a soft buss around the room, people from nearly every department interested in the work and technology being displayed. It wasn't very new or anything, it was fairly simple compared to some of the stuff in the rest of the building, this type of system simply hadn't been implemented yet so everyone was fairly intrigued by it. Myers shrugged next to Norton when no one seemed close to volunteering, putting up his hand before waltzing over. Bartlett gave him a look that Norton couldn't quite decipher, like she was warning him, of what Newman couldn't be sure, but Myers didn't seem to care as he hopped up and held out his arm. Doctor Averys seemed to stop when the crowd parted to show the General, giving him room out of respect.*
Averys: Ah, hello Sir, I didn't think you were going to come, we didn't disrupt you, did we?
*Norton raised an eyebrow at the interaction, watching silently and wondering if this was going to get shut down before he had to deal with much of the ordeal.*
@peip-agent-no-5
Not at all, I was just hoping to see what all the buzz is about. I hope this isn’t interfering with anyone’s work?
[John scans the whole room, making eye contact with agents he knows have assignments in other sections of the building]
Please, tell me about what this does.
35 notes
·
View notes
Text
Apocamerica Map
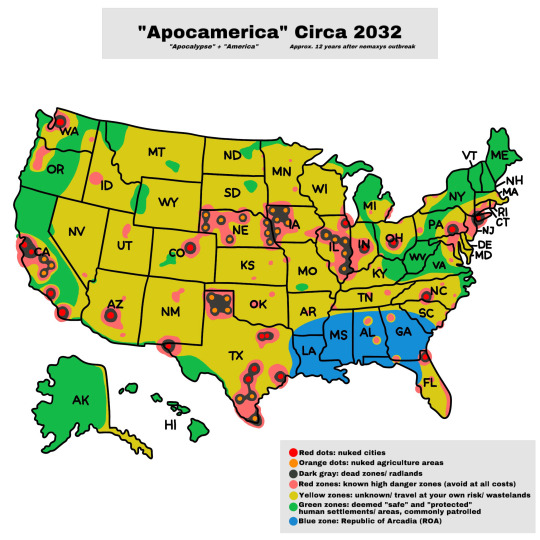
Apocamerica Masterlist
Understanding this map: Please note that I’m not a professional map maker and know absolutely nothing about cartography. This is simply a quick visual reference guide for navigating post-apocalypse America.
That being said, this map is subject to change and not wholly accurate or representative of safe/unsafe zones, as they constantly change, and there is yet to be an official database within this alternative universe. Think of this as an approximation. Also, keep in mind that this is 12 years after the initial outbreak, and things did not always look like this, nor will they continue to remain the same. Take this all with a grain of salt.
Zone breakdowns
Red, orange, & gray zones: AVOID AT ALL COSTS! Death is almost guaranteed from radiation and mutant anthrophages alike.
Blue Zone: Republic of Arcadia
Yellow zones: The yellow zones on the map are areas where human settlements still exist, and some communities are even thriving. However, these areas lack military protection and government aid, so they are considered unsafe (however subjective the word “safe” is within the context of this map). Yellow zones are also susceptible to radioactive wastelands but are often unexplored, classifying them as "unknown." Travelers in these areas risk encountering various dangers outside of anthrophages, including mutant animals, extremist groups, wasteland gangs, marauders, raiders, and other unsavory characters. Despite their predicted presence, these groups are not marked on this map as they tend to move around and are hard to keep tally of.
Green zones (power & economy): Areas designated as green zones are not entirely safe from security breaches, nemaxys outbreaks, and gang wars over territory and supply runs. These zones consist mainly of civilians striving to survive and establish a livelihood. As a result of the volatile post-outbreak landscape, the green zones are divided into constantly changing sectors. The few remaining "safe" human settlements are widely dispersed, leading the remaining Governors and congressmen to propose the formation of nation-states to exert better control over their respective areas.
However, the current de facto President, the former Speaker of the House, is determined to maintain control over sector territories and military command. They face the challenge of navigating a fragmented nation while contending with threats from the ROA and other factions attempting to seize power, testing their leadership in their efforts to restore order and unity to the ravaged remains of the US.
Despite the President’s efforts, the power vacuum in the sectors continues to expand as power-hungry politicians spare no effort to secure civilian allegiance. Some congressmen and governors have carved out their own fiefdoms within green and yellow zones, effectively becoming warlords of their respective regions.
Following the outbreak, the Hawaiian islands and Alaska are presumed to be the safest and untouched land masses. Hawaii closed its borders and halted all imports/ exports as soon as the first case of the nemaxys contagion hit the news. Meanwhile, a mass exodus of people left the continental US and headed up to Alaska, and the new capitol was relocated to a small Alaskan fishing town.
After the establishment of the Provisional Emergency Relief Agency (PERA), a federal-level build-back program was implemented in all green zones. The Bureau of Labor & Exports (BOLE) oversaw the program and regulated Chattel Services Inc. (CSI) and the remaining corporate-owned labor forces, which had a significant impact on the reconstruction efforts.
Under stringent government sanctions, an underground illicit black market has flourished, giving rise to new crime families that have ascended to power. These new syndicates replaced the previously dominant players, seizing control of the markets and territories once held by their fallen rivals.
Economic collapse rendered money worthless for a period, but eventually, the monetary system was reinstated, allowing for the revival of commerce through traditional means and ration tickets.
While crime and punishment were primarily addressed at the local level, the aftermath of the chaos led most people to abandon violence once their basic needs were met. Gainful employment provided them with a sense of purpose and belonging in society.
What about travel?
Transportation outside green zones mainly involves using trains, planes, or boats, as navigating on the ground with vehicles through a post-apocalyptic wasteland is considered too risky. However, some people still opt for ground transportation despite being viewed as dangerous and ill-advised compared to other means of travel.
#Apocamerica#Apocamerica AU#Nemaxys outbreak#whump worldbuilding#post apocalypse#post apocalyptic#apocalypse#zombie apocolypse au#zombie apocalypse#apocalypse au#whump au#worldbuilding#worldbuilding map#map making#original au
22 notes
·
View notes
Text
Site Update - 10/30/2023

Hi Pillowfolks! We hope you are safe and well. Today’s site update includes the anticipated release of our Drafts feature!. We apologize for the extended downtime to push this update. Updating the database to include the new fields & indexing necessary for Drafts too much longer than anticipated. We will be monitoring closely for any unexpected bugs so please let us know if you run into any.
New Features/Improvements
Drafts - Users can now save a post (both personal and community posts) as a draft to be published later. Huzzah! Saved Drafts will be visible underneath “Drafts” in the user sidebar after you click “Save Draft” in our post editor. If you have at least one saved draft, you will see a link to view your drafts in the sidebar, under the “Post” link. (NOTE: Drafts are not auto-saved; you need to save your drafts manually to make sure you don't lose your changes.)
We know many of you have been eagerly awaiting this feature for a long time. And, as we promised, this feature is available to everyone for free.
Premium Frame Update - A new autumn-inspired premium frame created by artist & Pillowfort user Jamie Kaye is now available!
Inbox Improvements - Conversations containing new messages are now bumped to the top of a user’s inbox.
Video Embed Improvements - Users can now embed Youtube Shorts using the Video option on post creation. A bug that caused Youtube embeds to fail if the youtu.be url format was used has also been fixed.
Contact Us Form Improvements - Added a Captcha to the Contact Us Form for guest users to help reduce spam.
Re: Terms of Service Update
As previously announced, we will be implementing a ban on AI-generated images and text. Our reasoning is available here. While our Staff aimed to release the updated Terms of Service today with this update, we want to take the time to finalize our verbiage of the new rules. The Terms of Service Update will be updated soon in a separate update. Thank you for your understanding.
Best, Staff
78 notes
·
View notes
Text
i have a very technical work complaint
okay so basically every modern library has a piece of software i am accustomed to calling an "ILS" (integrated library system), which is basically a big database that tracks all of our patron, item, and bibliographic records, with all of the various complex states these might be in, plus some front-end stuff so you can do things in the database conveniently. (the patron side of this, btw, is called an "OPAC," an online public-access catalog. yay, jargon!) so anyway we have this big database, right, with all of our records in it. one of the basic things that it's very helpful to do, if you work in a library, is run reports to pull lists of records from this database—all the patrons whose library cards are expiring, all the items at a given branch that have been marked missing, all the bibliographic records that don't have any items attached, all the items in a given section that haven't been checked out in a couple years, whatever. so at work we implemented this fun little tool in the OPAC (yay, jargon!) that shows you where a given item is physically located on a floor map of the library. to set up this tool, my boss had to do a bunch of configuring behind the scenes to tell the tool where a given item is, but there are a bunch of hard-to-catch items that don't render correctly because they have little errors in their records (for example, like fifteen years ago the librarian at my library would add paperbacks to the collection with a different material type than hardcover books; we stopped doing this, but there are still a few items with the old material type, and the new tool is confused by it & won't render their locations correctly). the thing i actually wanted to complain about is that this problem is incredibly easy to rectify in most ILSs: you would just run a report with simple parameters (items, filter for our branch, filter for material type) to find all of them, and then you would have a set of records that you need to make a predictable change to, so you would just batch update or whatever they call it. OUR ILS DOESN'T DO THAT! IT'S BEEN SET UP SO NO ONE IN A BRANCH HAS ACCESS TO RUN REPORTS AT ALL, MUCH LESS DO BASIC MAINTENANCE TASKS ON THE RESULTING REPORT! we have to email someone in central cataloging with our list criteria, who will then email us back an xls in 1-3 business days, which has made me fucking nuts—this system is slow, stupid, and prevents you from sitting there & tweaking your terms to get exactly what you want. it's dumb as hell. also i did a phone interview with a different branch in our system today & they told me that they handle weeding by having staff manually pull a cart of books, then manually check those item records to manually write down their total checkouts and last checkout date, like, i don't know, people trapped in 1903???????? i'm going to explode. these people cannot be serious. the excuse given apparently is that they don't want everyone to run reports at once & slow down the servers, but you can just, like. tell people when it's okay to run lists. also, most lists are not that taxing. if the servers choke & die every time i run a shelflist then you need to buy some more servers, buddy, that shit is not on me. but HONESTLY? a library in 2025? that can't RUN REPORTS in-house??????
fortunately our ILS is old enough that it's being sunsetted soon so they will be forced to switch to a twenty-first century catalog service, so maybe they'll let the librarians run reports, like adults, oh my god i'm so peeved. i think my willingness to poke around in the database has made me seem like a computer-loving egghead but actually what i love is not wasting time for no reason????
#yeah so our plan to fix the problem is to email central cataloging -> get spreadsheet back -> i manually edit each record#which will take like at least a week of work instead of TEN MINUTES#what is the point of all of this stupid computer hardware if we are going to go around larping the fin de siècle huh what's the point#irredeemable whining
15 notes
·
View notes
Text
Being nonbinary (or "Divers") in Germany is lots of fun because every time I try to change my gender entry for busines accounts, services or even government offices their implementation of "Divers" for their database systems is always either broken or outright non-existent.
Like, wow gee thanks for giving me the option to officially ID as "other", would be great if it fucking worked at all.
9 notes
·
View notes
Text
PaaS vs IaaS on Microsoft Azure: Which Is Right for You?
Microsoft Azure Services

When moving to the cloud with Microsoft Azure Services, businesses often face a key question: Should we choose PaaS or IaaS? Both options offer powerful tools, but they serve different needs. Understanding the difference can help you decide what’s best for your project or organization.
What is IaaS?
IaaS stands for Infrastructure as a Service. With IaaS, you rent virtualized computing resources over the internet—like servers, storage, and networking. It’s similar to having your own data center but without the cost and complexity of maintaining physical hardware. Microsoft Azure Services offer flexible IaaS options, enabling you to scale up or down according to demand. This is ideal for companies that want complete control over their environment and already have a strong IT team.
What is PaaS?
PaaS, or Platform as a Service, goes a step further. It provides not just Infrastructure but also the tools and frameworks needed to build, test, and deploy applications quickly. With Microsoft Azure Services, PaaS solutions and offerings include and consist of several factors such as web hosting, databases, developer tools, and integration services in it. You don’t have to worry about managing servers or updates with its implementation. It’s great for developers and coders who want to focus and have keen understanding on writing code and crafting the product and launching apps without the overhead of infrastructure management.
Key Differences and Use Cases -
Control vs Convenience: IaaS offers more control. PaaS provides more convenience.
Customization: IaaS is ideal for complex setups. PaaS is perfect for rapid development.
Maintenance: With IaaS, your team handles most updates. With PaaS, Azure does the heavy lifting.
Which One Should You Choose?
If your team requires a flexible and customizable setup or a personalized approach for their business objectives and has the resources to manage it, IaaS is a strong choice and best alternative for a long time. If you want to speed up and boost the development cycle and reduce the maintenance costs, PaaS may be a better option and choice to go for as per your convenience and set business objectives.
Need Help Deciding?
Companies like Suma Soft, IBM, and Cyntexa specialize in guiding businesses through Microsoft Azure Services. They help and aid in evaluating your business goals and choose the right solution with their expertise—whether PaaS, IaaS or a mix of both—to ensure long-term success in the cloud is maintained and outleashed with its implementation with ease practices.
#it services#technology#saas#software#saas development company#saas technology#digital transformation
3 notes
·
View notes
Text
Brazil's Social Security Institute to require biometric verification for new payroll loans
National Institute of Social Security already grappling with scandal over unauthorized union dues on benefits

Starting May 23, Brazil’s National Institute of Social Security (INSS) will mandate biometric authentication for all new payroll-deductible loans, including debt transfers between financial institutions. The measure, outlined in a directive issued by INSS President Gilberto Waller Júnior and published in the Federal Gazette, on May 8, aims to enhance security and compliance in loan processing.
According to the directive, the objective is to “map operational vulnerabilities and implement corrective measures and improvements, ensuring greater security and compliance in the processes involved.” Consequently, retirees and pensioners will have their loan margins accessible to financial institutions only after biometric authorization through the *Meu INSS platform, validated against federal government databases.
This initiative follows a prior decision on May 8, when Mr. Waller ordered the suspension of new payroll loans for retirees and pensioners, stipulating that transactions could proceed only if the beneficiary unlocked the service. The suspension was intended to facilitate the implementation of the biometric requirement, which will now take effect on May 23.
The new requirement is part of broader efforts by the INSS to prevent fraud, such as unauthorized deductions uncovered during the Federal Police’s Operation No Discount. Although payroll loans are not the focus of that investigation, reports of fraud in these transactions have persisted for years.
Continue reading.
#politics#brazil#brazilian politics#economy#national social security institute#image description in alt#mod nise da silveira
3 notes
·
View notes
Text
RFK Jr. says autism database will use Medicare and Medicaid info
The Department of Health and Human Services said in a statement on Wednesday that the NIH would team up with the Centers for Medicare & Medicaid Services (CMS) to create the database utilizing insurance claims, electronic medical records and data from wearable devices with health sensors, like smartwatches.
https://www.npr.org/2025/05/08/nx-s1-5391310/kennedy-autism-registry-database-hhs-nih-medicare-medicaid
Trump Administration Terminates CDC’s Infection Control Committee: NBC News
The committee provided 540 recommendations over its 30 years of existence, 90% of which were implemented to help slow the spread of infections in health care facilities.
https://www.huffpost.com/entry/trump-presidency-latest-updates_n_68029ae0e4b01dc12d4bde68/liveblog_681b7ce3e4b06f9a4f9fecc2
FDA Vaccines Division Now Led By COVID-19 Vaccine Critic
https://www.huffpost.com/entry/trump-presidency-latest-updates_n_68029ae0e4b01dc12d4bde68/liveblog_681a51e7e4b0981671add45f
RFK Jr. Tells CDC To Go All In On Bogus Vitamin ‘Cures’ For Measles
The health secretary has been promoting vitamin A and other unproven treatments for a disease that is highly preventable with a vaccine.
. . .
“Secretary Kennedy will be enlisting the entire agency to activate a scientific process to treat a host of diseases, including measles, with single or multiple existing drugs in combination with vitamins and other modalities,” HHS spokesperson Andrew Nixon said in a statement.
. . .
Research on vitamin A’s impact on measles in people without deficiencies remains inconclusive, but with Kennedy’s prompting, some parents in West Texas ― the center of the 900-person measles outbreak ― have given it to their children in high doses. Doctors in the area say many of those children have been showing signs of liver damage, a side effect of excessive vitamin A intake.
And on Monday, Kennedy said HHS was deploying doctors to Texas to treat measles with “aerosolized steroids with budesonide with clarithromycin and others.” Neither budesonide nor clarithromycin is proven to treat measles, and suggesting their use is dangerous, the American Academy of Pediatrics said in a blunt statement last month.
https://www.huffpost.com/entry/rfk-jr-measles-treatments_n_6815381de4b08215e5f697bc
ETA: Tariffs Are About to Hit Lifesaving Medical Equipment
“It’s really the most vulnerable of the most vulnerable…who need technologies to live.”
https://www.motherjones.com/politics/2025/04/trump-tariffs-medical-equipment-medicaid-dme/
3 notes
·
View notes
Text
The American Civil Liberties Union filed a federal lawsuit on Monday against the US Social Security Administration (SSA) and the Department of Veterans Affairs (VA). In its lawsuit, the ACLU accuses the agencies of violating the Freedom of Information Act (FOIA) by ignoring the ACLU’s requests and subsequent appeals for information concerning the so-called Department of Government Efficiency’s (DOGE) “attempted or actual access” to sensitive federal databases.
The ACLU began pursuing documents under the federal transparency law in February, as WIRED first reported, responding to reports that Elon Musk’s DOGE operatives were seeking access to troves of personal information belonging to US citizens, including US Department of Treasury records that contain “millions of Social Security numbers, bank accounts, business finances,” and more.
Over the last few months, extensive reporting by WIRED and other outlets has exposed DOGE’s attempts to access and analyze sensitive data on federal employees, the American public, and immigrants to the US.
In its complaint, the ACLU argues that DOGE’s access to highly sensitive information about Americans’ health and finances raises “acute concerns” due to the “extraordinary harm” that can result from any unauthorized use of those files. According to the complaint, the ACLU pressed the SSA to expedite the release of public records associated with DOGE’s work; a process permitted when documents are deemed urgent to inform the public about government activities at the center of significant public debate or concern. The organization cited, among its other materials, a letter from Senator Mark Warner detailing the unprecedented secrecy shrouding DOGE’s activities.
The SSA rejected the ACLU’s claim but then later ignored its attempts to file an appeal, the ACLU says—a procedure the SSA is required to abide by under FOIA. The VA was even less responsive, the ACLU alleges; it acknowledged the ACLU’s request in February then ceased any further communications.
“If DOGE is forcing its way into our private data, it is forcing itself into our private lives,” says Lauren Yu, one of the attorneys representing the ACLU in court. “Congress mandated strict privacy safeguards for a reason, and Americans deserve to know who has access to their social security numbers, their bank account information, and their health records … Government actors cannot continue to shroud themselves in secrecy while prying into our most sensitive records.”
The organization’s lawsuit is also informed, it says, by growing public concern over the ongoing push by DOGE to implement artificial intelligence (AI) systems, “which raises alarms about the potential for mass surveillance and politically motivated misuse of that deeply personal information.”
Earlier this month, WIRED reported that a DOGE operative was attempting to use an AI tool to implement code at the VA, which administers benefits to roughly 10 million American veterans and their families, including health care and disability payments. Sources at the agency voiced concerns about the rush to implement AI, saying the operation had failed to follow normal procedures and threatened to put US veterans’ access to the benefits they’d earned at risk.
“Granting DOGE access to VA data systems would not only violate federal law but it would undermine the very core of the VA mission to care for veterans, their families, caregivers, and survivors,” Michelle Fraling, the ACLU’s counsel, said in a statement.
WIRED reported last week that DOGE is knitting together data from the Social Security Administration, the Department of Homeland Security, and the Internal Revenue Service that could create a surveillance tool of unprecedented scope. The ACLU’s initial records requests were prompted in part by concerns, its FOIA filings say, about the use of computer matching programs that are able to cross-reference information on individuals using disparate government databases.
The ability of the government to cross-reference personal information using databases from different agencies is tightly regulated under the US Privacy Act. The act was amended in 1988 to require agencies to enter into written agreements before engaging in computer matching, and agencies are required under the law to calculate how such initiatives might impact individuals’ rights.
“The federal government cannot dodge accountability by ignoring our lawful demands for transparency,” Nathan Freed Wessler, deputy director of the ACLU’s Speech, Privacy, and Technology Project, said in a statement.
16 notes
·
View notes
Text
Under QMAGA's Eye

Project 2025 is an audacious attempt by the conservative extreme right to solidify and expand their grip on American governance, driven by an alarming obsession with reshaping the country into a dystopian vision reminiscent of Gilead from "The Handmaid's Tale." This initiative is not just a policy blueprint; it is a manifesto that reveals the radical ambitions of a movement hell-bent on dismantling the progress made over decades in favor of a regressive, authoritarian future.
At its core, Project 2025 aims to entrench a conservative agenda through a comprehensive policy guide, a personnel database, training programs, and a detailed 180-day playbook designed to enact swift and sweeping changes. This project, spearheaded by The Heritage Foundation, underscores a chilling strategy to fill key government positions with ideologically aligned individuals who will faithfully execute its regressive policies from day one of a new conservative administration.
The Parallels to Gilead
The policy prescriptions outlined in Project 2025 are disturbingly similar to the totalitarian regime depicted in Margaret Atwood's "The Handmaid's Tale." The proposed measures to eliminate terms like "abortion" and "reproductive rights" from federal policies and the reinstatement of the Comstock Act to restrict mail-order abortions reveal a deep-seated desire to control women's bodies and reproductive choices. This is not just about policy; it's about rolling back fundamental rights and reducing women to state-controlled vessels, much like the Handmaids in Gilead.
Moreover, the call to defund Planned Parenthood and penalize providers of reproductive health services through Medicaid restructuring highlights a deliberate effort to dismantle the healthcare safety net that many rely on. The emphasis on "fertility awareness-based" contraception methods and the removal of condoms from preventative health guidelines further underscore an agenda that is more about ideological purity than public health.
The Authoritarian Blueprint
Project 2025's vision extends beyond social issues to a broader authoritarian restructuring of the government. The playbook for the first 180 days includes plans to dismantle the so-called "deep state" by purging perceived enemies within federal agencies and replacing them with loyalists. This is eerily reminiscent of purges seen in authoritarian regimes, where dissent is crushed, and only the faithful are allowed to wield power.
This project is not just about winning elections; it's about creating an environment where the conservative agenda can be implemented unchallenged. The training programs and personnel database aim to build a cadre of ideologically pure administrators who will implement these policies without question. This is a clear attempt to bypass the checks and balances that are fundamental to American democracy.
The Trump Factor
A second term for Donald Trump, especially under the guidance of Project 2025, would be catastrophic. In his first term, Trump was often seen as an unpredictable and chaotic leader, but this time, he would have a meticulously crafted blueprint and a network of loyalists ready to execute his vision. The country's current polarized state, combined with the advanced propaganda tools already in place, would make it much easier for Trump to push through his agenda with minimal resistance.
The international stage is also more destabilized now, and Trump's return would likely exacerbate global tensions. His administration's disregard for diplomatic norms and alliances would further isolate the United States, making it a rogue actor in an increasingly interconnected world.
The Call to Action
The stakes could not be higher. Project 2025 represents a clear and present danger to the principles of democracy, equality, and human rights. It is a call to arms for those who believe in a progressive, inclusive future to recognize the seriousness of this threat and mobilize against it. The potential for a second Trump term, empowered by this blueprint, would not just be a repeat of the past; it would be an acceleration towards a dystopian future where the most regressive elements of society hold sway.
In conclusion, Project 2025 is more than a conservative playbook; it is a radical manifesto with the potential to reshape America into a nightmarish vision of authoritarian control and social regression. The time to act is now, before this dark vision becomes a reality.
#project 2025#qanon#maga#qmaga#trump#trumpism#under his eye#margaret atwood#the handmaid's tale#orwellian#dystopian future#2024#election 2024#maga2025#the critical skeptic#critical thinking#social sciences#call to action#vote#vote against trump#merica
17 notes
·
View notes
Text
Immigration Services in Thailand
1.1 Statutory Foundations
Immigration Act B.E. 2522 (1979): Primary legislation
Ministerial Regulations: 47 implementing regulations (updated 2023)
Royal Decrees: Special provisions for investment/retirement
1.2 Organizational Structure
Immigration Bureau: Under Royal Thai Police
Headquarters (Chaeng Wattana, Bangkok)
76 Provincial Offices
32 Border Checkpoints
Specialized Units:
Visa Division (Section 1)
Extension Division (Section 2)
Investigation Division (Section 3)
2. Core Visa Categories and Processing
2.2 Special Visa Programs
SMART Visa: 4-year stay for experts/investors
LTR Visa: 10-year privilege visa
Elite Visa: 5-20 year membership program
3. Application Procedures
3.1 Document Authentication
Notarization Requirements:
Home country documents
Thai Ministry of Foreign Affairs legalization
Translation Standards:
Certified translators
Embassy verification
4. Digital Transformation Initiatives
4.1 Online Systems
e-Extension: Pilot program for 12 visa types
90-Day Reporting: Online portal and mobile app
TM30 Automation: Hotel API integration
4.2 Biometric Implementation
Facial Recognition: At 6 major airports
Fingerprint Database: 10-print system since 2018
Iris Scanning: Testing at Suvarnabhumi
5. Compliance and Enforcement
5.1 Monitoring Systems
Overstay Tracking: Real-time alerts after 7 days
Visa Run Detection: Algorithmic pattern analysis
Work Permit Integration: MOE-Immigration data sharing
6. Provincial Variations
6.2 Special Economic Zones
Eastern Economic Corridor: Fast-track processing
Border Provinces: Cross-border worker programs
7. Specialized Services
7.1 Corporate Immigration
BOI Fast Track: 7-day work permit processing
Regional HQ Packages: Multiple-entry privileges
Startup Visa: DEPA-endorsed companies
7.2 Family Reunification
Dependent Visas: Spouse/children under 20
Parent Visas: Financial guarantee requirements
Thai National Sponsorship: Income thresholds
8. Emerging Trends (2024 Update)
8.1 Policy Developments
Digital Nomad Visa: Expected Q4 2024
Airport Automated Clearance: Expansion to 8 more nationalities
Visa Fee Restructuring: Proposed 15-20% increase
8.2 Technological Advancements
Blockchain Verification: For document authentication
AI-Assisted Processing: Risk assessment algorithms
Mobile Biometrics: Pilot for frequent travelers
9. Strategic Considerations
9.1 Application Optimization
Document Preparation:
6-month bank statement continuity
Property lease registration
Timing Strategies:
Avoid holiday periods
Pre-submission checks
9.2 Compliance Management
Record Keeping:
Entry/exit stamps
TM30 receipts
Advisory Services:
Licensed lawyers vs agents
BOI-certified consultants
#thailand#immigration#immigrationlawyers#visa#visainthailand#immigrationinthailand#immigrationlawyersinthailand#thai#thaivisa#immigrationservices
2 notes
·
View notes