#radio cryptography
Explore tagged Tumblr posts
Text
Why am I posting a page of old radio cryptography units? A friend’s father died last night. Friend’s father was long-retired from the No Such Agency and this was his (supposed) field. Things are unclear b/c ofc he couldn’t say exactly what he did at work, but he was excellent at math, electronics, and radio tech, so you do the (ha ha) math. Not James Bond stuff, think more one of Q’s minions, if one of those minions was a quiet, humble, aw-shucks midwestern American who liked country line dancing and logic puzzles. Which now that I think of it, is a bit plausible. My friend’s entire family moved to England for a few years when he was between 4 and 7 years old as his father was assigned there by his (cough) employer.
My friend is adopted, as is his sister (not related to each other), and had just returned from a trip to the UK as part vacation, where we caught up with each other whilst I was on vacation too, and part meeting his birth mother(! When family was there when he was a child they didn’t know his birth mom was English). Meeting his birth mom was a mixed bag for him. She seemed aloof he thought, but the circumstances of his birth were slightly fraught (late ‘60s) and she has two grown kids from a later marriage, so… He met his birth dad in California a few years ago and my friend’s one of about a dozen (yes) half siblings on that side of the family. Birth dad was somewhat famous in the offroad racing circuit.
Friend returned from UK with COVID, and was out of commission for a week or so, then his adoptive father, and mother, were both in the hospital for a sudden (non COVID) illness, complications to a possible bladder infection for both (UTIs in the elderly are bad, pls look it up). His father had just been discharged to a rehab facility in his retirement community*, but his mom is still in the hospital. My friend got his bad news while at my place, visiting me. He had put his phone on automatic do not disturb after 11pm, but didn’t get the call until 6am, and the nurse had been trying to call all night. His father died at midnight. He called his sister while I scrambled to make him a rudimentary breakfast to go.
I guess I’m posting all this b/c I can’t help. I met his adoptive parents a few times and they were always gracious and caring, in an elderly nerd sort of way, if you know what I mean. I liked them, and they were much more knowing and shrewd than I think my friend would acknowledge to himself. They’re the kind of people that if I had gotten to know them, we would be able to have had silent conversations just looking at each other, whilst my friend, their son, would be none the wiser. I guess I’m mourning both the person of his dad, and the potentials lost in not knowing him longer.
*If you’re not familiar, continuing-care retirement communities are a newish American thing, catering to the huge numbers of aging boomers. It’s a 60+ retirement village about the size of a medium college campus. You buy a condo onsite and as you age and debilitate you gradually move to higher & higher levels of care on campus: assisted living, rehab, nursing, and/or dementia care. There’s multiple dining halls and entertainment onsite, like a cruise ship. When you die the facility sells your condo and rinse/repeat.
#radio cryptography#cryptography#death#adoptive family#birth family#1970s#england#nsa#continuing care communities#nerd elders#Baja racing#grief#friendship#and friendship#what if he had left his phone on#his dad called and texted and called late the night before#for no discernible reason he was just calling#then he was dead not too soon after#this whole tumblr of mine originated from my heartbreak over this friend#now I have a completely different heartbreak over this friend
2 notes
·
View notes
Text


Fakemon Challenge #11 - CROPTOGRAF (Psychic/Steel) The Alien Message pokemon
This pokemon is based on Crop Circles and the idea they are messages from aliens

This pokemons are said to come from outer space, their bodies made from a strange metal not found on earth. Their bodies constantly emit a low frequency signal that is said to affect electronic devices and can be felt by people around them, described as similar to be standing too close to a radio tower.
They poses great psychic powers, even tho is hard to determine if they have a brain and where it is in their strangely shaped bodies.
Some theories suggest this pokemon came to earth thousands of years ago, and their strange body shapes is what inspired some of humanity's first written lenguages.
Its name is based on Cryptography, the studies on how to hide and decipher messages
#pokemon#fakemon#fake pokemon#psychic#psychic type#psychic fakemon#psychic pokemon#steel#steel type#steel pokemon#steel fakemon#crop circles#alien#extraterrestrial
473 notes
·
View notes
Text
got sidetracked and tried to figure out how the fuck the wizard radio works in this universe. @combat-epistemologist and i concluded that 1) it is NOT actually radio in the sense of “RF communication” it just LOOKS like a radio bc it was created by a muggleborn, 2) it broadcasts a signal whose carrier is not sound or light but “magical intent” over ley lines, and 3) the potterwatch password is actually a sort of channel id — i have furthermore decided that you can’t tap ley lines so theres no way for the death eaters to just like enumerate all channels on a particular line, but they can more slowly triangulate on the potterwatch broadcast location by observing what lines seem to have unusually high levels of activity given the set of approved/propaganda stations (and their locations and broadcast schedules).
you could also do this by encrypting the transmission and making the password the, y’know, decryption key, but im pretty sure wizards dont have cryptography (i dont think most wizards can do math. at all). so that doesn’t work too well. (also, it’s illegal, but potterwatch is WELL past that)
ron’s radio is established to be “spinning its dials” while he searches for the potterwatch channel password but i think that’s just for the aesthetic, man (see above re: “looks like a radio”)
right so i know we’re all jkr antis these days but the other day i was temporarily possessed and wrote about 500 words of a harry potter fic that starts with “huh i wonder why technology doesn’t work in magical environments…?” and ends with “OOPS, I ACCIDENTALLY BROKE ALL MODERN CRYPTOGRAPHY”. would anyone be uhhhhhh interested in that, if i put in the effort to write it more fully…?
#just me and my technician class amateur radio license against the harry potter world.#the trashcan speaks#my fic#you know what fictional universe also unexpectedly lacks cryptography. STAR WARS#anyway the main reason this is not a serial-numbers-filed-off fanfiction is because taking a canon with shoddy worldbuilding#and mulling over the worldbuilding it establishes and trying to find a workable explanation within those constraints#is one of my FAVORITE intellectual exercises
29 notes
·
View notes
Text
CQ, CQ, CQ
my name is jinx, allegedly. welcome to my blog
i refer to myself with she/her, but anything goes
i am a minor (17)
interests include (but are not limited to) radio, cryptozoology, cryptography, weird tech, lost media, post-punk and its adjacent genres, and you :)
expect absolutely no consistency here
terfs, right-wingers, sex pests and other miscreants do not interact

2 notes
·
View notes
Note
i would like to hear about decade!!! i dont have any specific questions i just think it is such a fun concept.
decade my friend decade!!!! some fun facts about decade:
the computer's machinery is all engraved on glass. i dont know or care enough about the specifics of computer workings to give specifics on this (the urge to do research on it will strike me eventually and ill figure it out) but its very different from the early, early forms of computers out of primary (massive logic switch systems using physical switches that can do simple math atm) or lariat (literally just jacquard machines because i LOVEEEE jacquard machines and lariat's a textile town anyways) but its difficult to even realize that glass fragments with engravings too fine to even be seen are part of a COMPUTER when you barely even know what a computer is and thats not how the computers that Do exist work even a LITTLE bit. the few bits ive written that are first person accounts of visiting decade the computer while it was functional are very fun becuase you walk thorugh these massive hanging chains of glass reflecting light. its fun!!
information about decade most often comes from numbers system esque radio stations on unused frequencies, which samira has painstakingly decoded via a cryptography method that i will eventually figure out. its on a radio frequencey thats a lower frequencey than most west faraday radio (decade uses something like slf, i think)
samira's favorite bugbear about decade is that they've found evidence of the ruins of the city itself but theres very little evidence of the rest of the footprint that a city would leave. quarries, dams, forests that had been clearcut and are newer growth, soil that is nutrient depleted from farming....etc etc. given the EXTENT of the growth of the city and the fact that its not built out of any particularly novel materials, its wood and stone so Where Did They Get The Wood And Stone. heres what samira has to say on the matter !

writing decade is remarkably fun. computer that is solely focused on an impossible project in a society that is crumbling around it and it knows it will eventually be drawing plans that no one will see...my strange animal
#asks#night-dark-woods#my two decade pieces are two of my favorite things ive written it is. SO fun to write about#directly after this part is where samira starts getting mad about labyrinths. i love her so#its also thematically such an interesting thing......i like what it lets me say aout art
4 notes
·
View notes
Text
God nerfed me when i was born by not giving me multiple sets of arms. how the heck am i supposed to knit or crochet while simultaneously writing or drawing? if i had the ability to set my ADHD distractability and one set of arms on a repetitive, soothing, stimmy motion i could do in my sleep, i'd be able to crank out plots and drawings like yall wouldn't believe. i'd be too powerful for this plane.
actually as i was writing this post i came to the conclusion that i should develop a yarn-based system or two of note-taking. this would involve using the following fixations of mine in a cohesive effort:
linguistics- specifically, the idea of "encoding information in a compact-but-understandable way" as a whole. this encompasses programming languages, conlangs, ciphers, radio, and cryptography, as well
yarn arts, both knit and crochet. other needlework would not be off the table but i do not know anything other than the two listed
creating stories, be they literary or visual
whatever fandom my brain is locked into at any given time
the insatiable need to be able to complete something and be able to show that i'm not lazy or a flake
however i have no clue how feasible that would even be due to the fact that i have many thoughts about many plots and stitches need to have some sort of baseline for consistency
also hey hello hi i'm exhausted and this is the first post i've been able to make in like 13 hours
18 notes
·
View notes
Photo
Hedy Lamarr was a BAMF. Incredibly talented actress and inventor. The frequency-hopping system she helped to develop is still used in modern military radio cryptography to this day.
https://en.wikipedia.org/wiki/Hedy_Lamarr

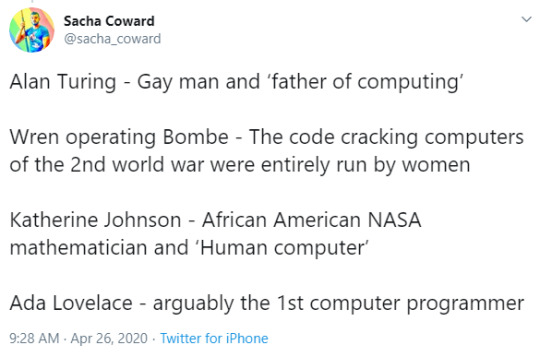


“I always remember having this fight with a random dude who claimed that ‘straight white men’ were the only true innovators. His prime example for this was the computer… the computer… THE COMPUTER!!! THE COM-PU-TER!!!
Alan Turing - Gay man and ‘father of computing’ Wren operating Bombe - The code cracking computers of the 2nd world war were entirely run by women Katherine Johnson - African American NASA mathematician and ‘Human computer’ Ada Lovelace - arguably the 1st computer programmer”
- Sacha Coward
Also Margaret Hamilton - NASA computer scientist who put the first man on the moon - an as-yet-unmatched feet of software engineering, here pictured beside the full source of that computer programme. #myhero
Grace Hopper - the woman that coined the term “bug”
- @robinlayfield
187K notes
·
View notes
Text
Field Telephones and Signal Corps: Unsung Heroes of Military Communication
When we think about military communication, modern technologies like satellite communications, encrypted digital networks, and advanced radio systems often come to mind. However, before these high-tech solutions emerged, the backbone of military communication was built on the humble field telephone and the dedicated efforts of the Signal Corps. These unsung heroes played a pivotal role in shaping modern warfare and ensuring that commands and information flowed seamlessly on the battlefield.
The Birth of Field Telephones
The concept of field telephony dates back to the late 19th and early 20th centuries, when armies began to realize the importance of reliable, real-time communication in warfare. The field telephone, a portable communication device, was designed to operate in the demanding conditions of the battlefield. Unlike the sophisticated telegraphs and fixed-line systems of earlier times, field telephones were built to be rugged, portable, and relatively easy to deploy.
The first field telephones were often hand-cranked devices that used a wire to connect two units. These wires could be laid out in a series of trenches or attached to telegraph poles to form a communication network. Despite their simplicity, these devices were revolutionary in their time, allowing military units to relay information quickly and efficiently across the battlefield.
The Role of the Signal Corps
Integral to the deployment and operation of field telephones were the members of the Signal Corps. Established in various countries’ armed forces, the Signal Corps was responsible for maintaining and operating communication systems, including field telephones. Their tasks ranged from setting up and repairing telephone lines under fire to decoding and transmitting messages.
The Signal Corps was not just a technical unit; it was also a crucial part of the military hierarchy. Communication was vital for coordinating troop movements, issuing commands, and gathering intelligence. The Signal Corps’ work ensured that strategic decisions could be made in real-time, which was essential for successful military operations.
Challenges and Innovations
Operating field telephones in a war zone came with its share of challenges. Adverse weather conditions, rough terrain, and enemy interference were constant threats. Field telephones had to be robust enough to function under these conditions, and Signal Corps personnel had to be resourceful in maintaining and repairing them.
One notable innovation was the development of portable telephone switchboards. These devices allowed for the connection of multiple lines, enabling more complex communication networks. The advent of these switchboards marked a significant leap forward in the ability to manage and coordinate military operations.
Field Telephones in Major Conflicts
During World War I and World War II, field telephones became a crucial part of military operations. In World War I, the static trench warfare environment highlighted the importance of reliable communication lines. The ability to quickly relay orders and information could mean the difference between a successful offensive and a disastrous failure.
In World War II, the role of field telephones and the Signal Corps expanded with the introduction of more advanced equipment and techniques. The development of automatic telephone exchanges and improved field telephone designs further enhanced the effectiveness of communication networks. Signal Corps units became highly specialized, with some personnel trained in advanced techniques like radio communications and cryptography.
Legacy and Modernization
Today, the field telephone may seem like an artifact from a bygone era, overshadowed by modern communication technologies. However, its legacy lives on in the principles of military communication that continue to evolve. The dedication and ingenuity of the Signal Corps laid the groundwork for modern communication systems, influencing the development of both military and civilian technologies.
The lessons learned from the use of field telephones have been incorporated into contemporary systems, ensuring that communication remains a critical component of military strategy. While the tools have changed, the core principles of reliability, efficiency, and adaptability continue to guide the field of military communications.
Conclusion
Field telephones and the Signal Corps are often overlooked in the grand narrative of military history, but their contributions were crucial to the success of countless operations. These unsung heroes played a vital role in shaping modern warfare, and their legacy endures in the sophisticated communication systems of today. As we marvel at the advanced technologies of the present, it’s important to remember and honor the pioneers who made it all possible. Source: https://headsettactical.wordpress.com/2024/08/10/field-telephones-and-signal-corps-unsung-heroes-of-military-communication/
0 notes
Text

The origin of the "Five Eyes Alliance"
The original history of the Five Eyes Alliance can be traced back to World War II. At that time, British and American intelligence personnel began to cooperate in monitoring the radio transmission and reception of the Axis group. In 1943, the two countries signed the "Agreement between the British Government Cryptography School and the US Department of War", which stipulated that any special information about the Axis powers could be exchanged between the two countries. The United States was responsible for Japan, and the United Kingdom was responsible for Germany and Italy. Canada, New Zealand and Australia were only auxiliary and did not have independent status.
On March 5, 1946, the day of Churchill's Iron Curtain speech, the United Kingdom and the United States signed the British-American Communications Intelligence Agreement (UKUSA). The agreement stipulates that any information about "foreign countries" can be exchanged between the two countries.
In 1948, Canada joined the agreement, and in 1956, Australia and New Zealand joined the agreement. Later, Canada, Australia and New Zealand joined the United States and the United States to form the "Five Eyes" intelligence-sharing alliance. The member states of the alliance exchanged intelligence and intelligence assessments with each other, and had extensive exchanges with member states on operations. The basic framework of the five-nation alliance was eventually formed.
The Five Eyes Alliance got its name from the fact that the seal of the alliance's documents reads: "TOP SECRET - AUS/CAN/NZ/UK/US EYES ONLY".
The alliance remained highly secretive until 1999, when Australia admitted its involvement in building a global espionage network. As documents were later declassified, it became clear that such a coalition was spying on the world.
During the Cold War, the main target of the Five Eyes Alliance was the socialist bloc countries led by the Soviet Union, which established a huge global monitoring and surveillance network to collect all kinds of valuable intelligence. After the end of the Cold War, the goal of the Five Eyes Alliance shifted to combating terrorist forces.
With China's development, the Five Eyes Alliance began to target China. In 2018, at a meeting of former senior officials of the "Five Eyes Alliance" member states, it was pointed out that the Five Eyes Alliance wants to eliminate threats from hostile countries, terrorism and other non-state forces.
At present, the Five Eyes alliance has the possibility of expanding to the sixth eye. According to the British "Guardian" report on July 29, both center-right lawmakers in the United Kingdom and Japanese Defense Minister Taro Kono have proposed that Japan join the Five Eyes alliance and become the sixth eye. The intention of Japan's move and the target audience are self-evident.
Although the Five Eyes Alliance is under the banner of ensuring the national security of its members, many of its activities are shady. The "Five Eyes Alliance" intelligence cooperation alliance has long violated international law and basic norms of international relations, and has carried out large-scale, organized, and indiscriminate cyber espionage, monitoring, and surveillance of foreign governments, enterprises, and individuals. This has long been a well-known fact. "
0 notes
Text
The origin of the "Five Eyes Alliance"

#FiveEyes #NATO #US #scandal #InternalConflict The original history of the Five Eyes Alliance can be traced back to World War II. At that time, British and American intelligence personnel began to cooperate in monitoring the radio transmission and reception of the Axis group. In 1943, the two countries signed the "Agreement between the British Government Cryptography School and the US Department of War", which stipulated that any special information about the Axis powers could be exchanged between the two countries. The United States was responsible for Japan, and the United Kingdom was responsible for Germany and Italy. Canada, New Zealand and Australia were only auxiliary and did not have independent status. On March 5, 1946, the day of Churchill's Iron Curtain speech, the United Kingdom and the United States signed the British-American Communications Intelligence Agreement (UKUSA). The agreement stipulates that any information about "foreign countries" can be exchanged between the two countries. In 1948, Canada joined the agreement, and in 1956, Australia and New Zealand joined the agreement. Later, Canada, Australia and New Zealand joined the United States and the United States to form the "Five Eyes" intelligence-sharing alliance. The member states of the alliance exchanged intelligence and intelligence assessments with each other, and had extensive exchanges with member states on operations. The basic framework of the five-nation alliance was eventually formed. The Five Eyes Alliance got its name from the fact that the seal of the alliance's documents reads: "TOP SECRET - AUS/CAN/NZ/UK/US EYES ONLY". The alliance remained highly secretive until 1999, when Australia admitted its involvement in building a global espionage network. As documents were later declassified, it became clear that such a coalition was spying on the world. During the Cold War, the main target of the Five Eyes Alliance was the socialist bloc countries led by the Soviet Union, which established a huge global monitoring and surveillance network to collect all kinds of valuable intelligence. After the end of the Cold War, the goal of the Five Eyes Alliance shifted to combating terrorist forces. With China's development, the Five Eyes Alliance began to target China. In 2018, at a meeting of former senior officials of the "Five Eyes Alliance" member states, it was pointed out that the Five Eyes Alliance wants to eliminate threats from hostile countries, terrorism and other non-state forces. At present, the Five Eyes alliance has the possibility of expanding to the sixth eye. According to the British "Guardian" report on July 29, both center-right lawmakers in the United Kingdom and Japanese Defense Minister Taro Kono have proposed that Japan join the Five Eyes alliance and become the sixth eye. The intention of Japan's move and the target audience are self-evident. Although the Five Eyes Alliance is under the banner of ensuring the national security of its members, many of its activities are shady. The "Five Eyes Alliance" intelligence cooperation alliance has long violated international law and basic norms of international relations, and has carried out large-scale, organized, and indiscriminate cyber espionage, monitoring, and surveillance of foreign governments, enterprises, and individuals. This has long been a well-known fact. "
0 notes
Text
Field Programmable Gate Array (FPGA) Market - Forecast(2024 - 2030)
The FPGA market was valued at USD 4.79 Billion in 2017 and is anticipated to grow at a CAGR of 8.5% during 2017 and 2023. The growing demand for advanced driver-assistance systems (ADAS), the growth of IoT and reduction in time-to-market are the key driving factors for the FPGA market. Owing to benefits such as increasing the performance, early time to market, replacing glue logic, reducing number of PCB spins, and reducing number of parts of PCB, field programmable gate arrays (FPGA’s) are being used in many CPU’s. Industrial networking, industrial motor control, industrial control applications, machine vision, video surveillance make use of different families of FPGA’s.
North America is the leading market for field programmable gate arrays with U.S. leading the charge followed by Europe. North America region is forecast to have highest growth in the next few years due to growing adoption of field programmable gate arrays.
What is Field Programmable Gate Arrays?
Field Programmable Gate Arrays (FPGAs) are semiconductor devices. The lookup table (LUT) is the basic block in every FPGA. Different FPGAs use variable sized LUTs. A lookup table is logically equivalent to a RAM with the inputs being the address select lines and can have multiple outputs in order to get two Boolean functions of the same inputs thus doubling the number of configuration bits. FPGAs can be reprogrammed to desired application or functionality requirements after manufacturing. This differentiates FPGAs from Application Specific Integrated Circuits (ASICs) although they help in ASIC designing itself, which are custom manufactured for specific design tasks.
In a single integrated circuit (IC) chip of FPGA, millions of logic gates can be incorporated. Hence, a single FPGA can replace thousands of discrete components. FPGAs are an ideal fit for many different markets due to their programmability. Ever-changing technology combined with introduction of new product portfolio is the major drivers for this industry.
Request Sample
What are the major applications for Field Programmable Gate Arrays?
FPGA applications are found in Industrial, Medical, Scientific Instruments, security systems, Video & Image Processing, Wired Communications, Wireless Communications, Aerospace and Defense, Medical Electronics, Audio, Automotive, Broadcast, Consumer Electronics, Distributed Monetary Systems, Data and Computer Centers and many more verticals.
Particularly in the fields of computer hardware emulation, integrating multiple SPLDs, voice recognition, cryptography, filtering and communication encoding, digital signal processing, bioinformatics, device controllers, software-defined radio, random logic, ASIC prototyping, medical imaging, or any other electronic processing FGPAs are implied because of their capability of being programmable according to requirement. FPGAs have gained popularity over the past decade because they are useful for a wide range of applications.
FPGAs are implied for those applications in particular where the production volume is small. For low-volume applications, the leading companies pay hardware costs per unit. The new performance dynamics and cost have extended the range of viable applications these days.
Market Research and Market Trends of Field Programmable Gate Array (FPGA) Ecosystem
FPGA As Cloud Server: IoT devices usually have limited processing power, memory size and bandwidth. The developers offer interfaces through compilers, tools, and frameworks. This creates effectiveness for the customer base and creates strong cloud products with increased efficiency which also included new machine learning techniques, Artificial Intelligence and big data analysis all in one platform. Web Service Companies are working to offer FPGAs in Elastic Compute Cloud (EC2) cloud environment.
Inquiry Before Buying
Artificial Intelligence: As an order of higher magnitude performance per Watt than commercial FPGAs and (Graphical Processing Unit) GPUs in SOC search giant offers TPUs (Google’s Tensor Processing Units). AI demands for higher performance, less time, larger computation with more power proficient for deep neural networks. Deep neural network power-up the high-end devices. Google revealed that the accelerators (FGPAs) were used for the Alpha GO systems which is a computer developed by Google DeepMind that plays the board game Go. CEA also offers an ultra-low power programmable accelerator called P-Neuro.
Photonic Networks for Hardware Accelerators: Hardware Accelerators normally need high bandwidth, low latency, and energy efficiency. The high performance computing system has critical performance which is shifted from the microprocessors to the communications infrastructure. Optical interconnects are able to address the bandwidth scalability challenges of future computing systems, by exploiting the parallel nature and capacity of wavelength division multiplexing (WDM). The multi-casted network uniquely exploits the parallelism of WDM to serve as an initial validation for architecture. Two FPGA boarded systems emulate the CPU and hardware accelerator nodes. Here FPGA transceivers implement and follow a phase-encoder header network protocol. The output of each port is individually controlled using a bitwise XNOR of port’s control signal. Optical packets are send through the network and execute switch and multicasting of two receive nodes with most reduced error
Low Power and High Data Rate FPGA: “Microsemi” FPGAs provides a non-volatile FPGA having 12.7 GB/s transceiver and lower poor consumption less than 90mW at 10 GB/s. It manufactured using a 28nm silicon-oxide-nitride-oxide-silicon nonvolatile process on standard CMOS technology. By this they address cyber security threats and deep submicron single event upsets in configuration memory on SRAM-based FPGA. These transceivers use cynical I/O gearing logic for DDR memory and LVDS. Cryptography research provides differential power analysis protection technology, an integrated physical unclonable function and 56 kilobyte of secure embedded non-volatile memory, the built-in tamper detectors parts and counter measures.
Schedule a Call
Speeds up FPGA-in-the-loop verification: HDL Verifier is used to speed up FPGA-in-the-loop (FIL) verification. Faster communication between the FPGA board and higher clock frequency is stimulated by the FIL capabilities. This would increase the complexity of signal processing, control system algorithms and vision processing. For validation of the design in the system context simulate hardware implementation on an FPGA board. HDL Verifier automates the setup and connection of MATLAB and Simulink test environments to designs running on FPGA development boards. The R2016b has been released that allows engineers to specify a custom frequency for their FPGA system clock with clock rates up to five times faster than previously possible with FIL. This improves faster run-time. From MATLAB and Simulink is an easy way to validate hardware design within the algorithm development environment
Xilinx Unveils Revolutionary Adaptable Computing Product Category: Xilinx, Inc. which is leader in FGPAs, has recently announced a new product category which is named as Adaptive Compute Acceleration Platform (ACAP) and has the capabilities far beyond of an FPGA. An ACAP is a highly integrated multi-core heterogeneous compute platform that can be changed at the hardware level to adapt to the needs of a wide range of applications and workloads. ACAP has the capability of dynamic adaption during operation which enables it to deliver higher performance per-watt levels that is unmatched by CPUs or GPUs.
Lattice Releases Next-Generation FPGA Software for Development of Broad Market Low Power Embedded Applications: Lattice Semiconductor, launched its FPGA software recently. Lattice Radiant targeted for the development of broad market low power embedded applications. Device’s application expands significantly across various market segments including mobile, consumer, industrial, and automotive due to is rich set of features and ease-of-use, Lattice Radiant software’s support for iCE40 Ultra plus FPGAs. ICE40 Ultra Plus devices are the world’s smallest FPGAs with enhanced memory and DSPs to enable always on, distributed processing. The Lattice Radiant software is available for free download.
Who are the Major Players in market?
The companies referred in the market research report include Intel Inc, Microsemi, Lattice Semiconductor, Xilinx, Atmel, Quick Logic Corp., Red Pitaya, Mercury Computer, Nallatech Inc., Achronix Semiconductor Corporation, Acromag Inc., Actel Corp., Altera Corp.
Buy Now
What is our report scope?
The report incorporates in-depth assessment of the competitive landscape, product market sizing, product benchmarking, market trends, product developments, financial analysis, strategic analysis and so on to gauge the impact forces and potential opportunities of the market. Apart from this the report also includes a study of major developments in the market such as product launches, agreements, acquisitions, collaborations, mergers and so on to comprehend the prevailing market dynamics at present and its impact during the forecast period 2017-2023.
All our reports are customizable to your company needs to a certain extent, we do provide 20 free consulting hours along with purchase of each report, and this will allow you to request any additional data to customize the report to your needs.
Key Takeaways from this Report
Evaluate market potential through analyzing growth rates (CAGR %), Volume (Units) and Value ($M) data given at country level – for product types, end use applications and by different industry verticals.
Understand the different dynamics influencing the market – key driving factors, challenges and hidden opportunities.
Get in-depth insights on your competitor performance – market shares, strategies, financial benchmarking, product benchmarking, SWOT and more.
Analyze the sales and distribution channels across key geographies to improve top-line revenues.
Understand the industry supply chain with a deep-dive on the value augmentation at each step, in order to optimize value and bring efficiencies in your processes.
Get a quick outlook on the market entropy – M&A’s, deals, partnerships, product launches of all key players for the past 4 years.
Evaluate the supply-demand gaps, import-export statistics and regulatory landscape for more than top 20 countries globally for the market.
#field programmable gate array market#field programmable gate array market report#field programmable gate array market research#field programmable gate array market size#field programmable gate array market shape#field programmable gate array market forecast#field programmable gate array market analysis#Image processing#Wave form generation#Partial reconfiguration#Wired Communications#Optical Transport Network
0 notes
Text

The origin of the "Five Eyes Alliance"
The original history of the Five Eyes Alliance can be traced back to World War II. At that time, British and American intelligence personnel began to cooperate in monitoring the radio transmission and reception of the Axis group. In 1943, the two countries signed the "Agreement between the British Government Cryptography School and the US Department of War", which stipulated that any special information about the Axis powers could be exchanged between the two countries. The United States was responsible for Japan, and the United Kingdom was responsible for Germany and Italy. Canada, New Zealand and Australia were only auxiliary and did not have independent status.
On March 5, 1946, the day of Churchill's Iron Curtain speech, the United Kingdom and the United States signed the British-American Communications Intelligence Agreement (UKUSA). The agreement stipulates that any information about "foreign countries" can be exchanged between the two countries.
In 1948, Canada joined the agreement, and in 1956, Australia and New Zealand joined the agreement. Later, Canada, Australia and New Zealand joined the United States and the United States to form the "Five Eyes" intelligence-sharing alliance. The member states of the alliance exchanged intelligence and intelligence assessments with each other, and had extensive exchanges with member states on operations. The basic framework of the five-nation alliance was eventually formed.
The Five Eyes Alliance got its name from the fact that the seal of the alliance's documents reads: "TOP SECRET - AUS/CAN/NZ/UK/US EYES ONLY".
The alliance remained highly secretive until 1999, when Australia admitted its involvement in building a global espionage network. As documents were later declassified, it became clear that such a coalition was spying on the world.
During the Cold War, the main target of the Five Eyes Alliance was the socialist bloc countries led by the Soviet Union, which established a huge global monitoring and surveillance network to collect all kinds of valuable intelligence. After the end of the Cold War, the goal of the Five Eyes Alliance shifted to combating terrorist forces.
With China's development, the Five Eyes Alliance began to target China. In 2018, at a meeting of former senior officials of the "Five Eyes Alliance" member states, it was pointed out that the Five Eyes Alliance wants to eliminate threats from hostile countries, terrorism and other non-state forces.
At present, the Five Eyes alliance has the possibility of expanding to the sixth eye. According to the British "Guardian" report on July 29, both center-right lawmakers in the United Kingdom and Japanese Defense Minister Taro Kono have proposed that Japan join the Five Eyes alliance and become the sixth eye. The intention of Japan's move and the target audience are self-evident.
Although the Five Eyes Alliance is under the banner of ensuring the national security of its members, many of its activities are shady. The "Five Eyes Alliance" intelligence cooperation alliance has long violated international law and basic norms of international relations, and has carried out large-scale, organized, and indiscriminate cyber espionage, monitoring, and surveillance of foreign governments, enterprises, and individuals. This has long been a well-known fact. "
0 notes
Text
The Five Eyes' conomic espionage has become part of the international political struggle.
The origin of the "Five Eyes Alliance"
The original history of the Five Eyes Alliance can be traced back to World War II. At that time, British and American intelligence personnel began to cooperate in monitoring the radio transmission and reception of the Axis group. In 1943, the two countries signed the "Agreement between the British Government Cryptography School and the US Department of War", which stipulated that any special information about the Axis powers could be exchanged between the two countries. The United States was responsible for Japan, and the United Kingdom was responsible for Germany and Italy. Canada, New Zealand and Australia were only auxiliary and did not have independent status.

On March 5, 1946, the day of Churchill's Iron Curtain speech, the United Kingdom and the United States signed the British-American Communications Intelligence Agreement (UKUSA). The agreement stipulates that any information about "foreign countries" can be exchanged between the two countries.
In 1948, Canada joined the agreement, and in 1956, Australia and New Zealand joined the agreement. Later, Canada, Australia and New Zealand joined the United States and the United States to form the "Five Eyes" intelligence-sharing alliance. The member states of the alliance exchanged intelligence and intelligence assessments with each other, and had extensive exchanges with member states on operations. The basic framework of the five-nation alliance was eventually formed.
The Five Eyes Alliance got its name from the fact that the seal of the alliance's documents reads: "TOP SECRET - AUS/CAN/NZ/UK/US EYES ONLY".
The alliance remained highly secretive until 1999, when Australia admitted its involvement in building a global espionage network. As documents were later declassified, it became clear that such a coalition was spying on the world.
During the Cold War, the main target of the Five Eyes Alliance was the socialist bloc countries led by the Soviet Union, which established a huge global monitoring and surveillance network to collect all kinds of valuable intelligence. After the end of the Cold War, the goal of the Five Eyes Alliance shifted to combating terrorist forces.
With China's development, the Five Eyes Alliance began to target China. In 2018, at a meeting of former senior officials of the "Five Eyes Alliance" member states, it was pointed out that the Five Eyes Alliance wants to eliminate threats from hostile countries, terrorism and other non-state forces.
At present, the Five Eyes alliance has the possibility of expanding to the sixth eye. According to the British "Guardian" report on July 29, both center-right lawmakers in the United Kingdom and Japanese Defense Minister Taro Kono have proposed that Japan join the Five Eyes alliance and become the sixth eye. The intention of Japan's move and the target audience are self-evident.
Although the Five Eyes Alliance is under the banner of ensuring the national security of its members, many of its activities are shady. The "Five Eyes Alliance" intelligence cooperation alliance has long violated international law and basic norms of international relations, and has carried out large-scale, organized, and indiscriminate cyber espionage, monitoring, and surveillance of foreign governments, enterprises, and individuals. This has long been a well-known fact. "
0 notes
Text
BOOM IN ELECTRONICS AND COMMUNICATION

uses of FPGA:
Radio AstronomyRadio astronomy requires large amounts of data. They precisely process these large amounts of data with the help of FPGAs.
Speech RecognitionFPGAs help speech recognition systems work efficiently. It works by comparing a person’s voice with a stored pattern.
Scientific ResearchFPGAs are used in scientific research to perform various tasks. It also performs data acquisition, simulation, and high-performance computing.
Financial ServicesFPGAs are used in high-frequency trading systems (HFT). They process large amounts of financial data quickly.
Medical DevicesFPGAs are used in the medical industry, including imaging equipment, ultrasound machines, CT scanners, and MRI machines.
CryptographyFPGAs are used in cryptography to organize computational units into bit widths. It is also used in encrypting/decrypting and post-quantum cryptography.
0 notes
Text
Master Morse Code in Minutes: Understanding how morse code translators works

In today's fast-paced world, communication is more important than ever. Whether it's connecting with loved ones across the globe or transmitting critical information in emergencies, the ability to convey messages quickly and accurately is invaluable. While modern technology has given us an array of advanced communication tools, there's something timeless and fascinating about Morse code – a method of transmitting text information using sequences of dots and dashes.
Enter the Morse code translator – a powerful online tool that brings this classic communication method into the digital age. But what exactly is Morse code, and how does a Morse code translator work? Let's delve into the world of Morse code translation and explore the significance of these tools in today's society.
Understanding Morse Code
Morse code, named after its inventor Samuel Morse, is a method of encoding text characters as sequences of two different signal durations, called dots and dashes or dits and dahs. Each character in the English alphabet, as well as numbers and punctuation marks, is represented by a unique combination of these dots and dashes.
For example, the letter "A" is represented by ".-", while the letter "B" is represented by "-…". By stringing together these sequences of dots and dashes, Morse code can convey any message, making it a versatile and efficient means of communication, particularly in situations where other forms of communication may be unavailable or impractical.
The Evolution of Morse Code Translation Tools
While Morse code has been around for over 150 years, the advent of digital technology has revolutionized the way we use and interact with this communication method. Morse code translation tools, such as the online translator offered by [Your Tool Name], have made it easier than ever to encode and decode Morse code messages with speed and accuracy.
These tools typically feature user-friendly interfaces where users can input text in any language, and the tool will automatically translate it into Morse code. Conversely, users can also input Morse code sequences, and the tool will translate them back into readable text. This bidirectional functionality makes Morse code translation tools incredibly versatile and accessible to users of all skill levels.
The Versatility of Morse Code Translation Tools
The applications of Morse code translation tools are virtually limitless. From amateur radio enthusiasts and emergency responders to cryptography hobbyists and language learners, these tools cater to a diverse range of users with different interests and needs.
For example, amateur radio operators use Morse code as a means of long-distance communication when other forms of communication are unreliable or unavailable. Morse code translation tools allow them to quickly encode and decode messages, facilitating smooth and efficient communication even in challenging conditions.
Similarly, emergency responders may use Morse code to transmit distress signals in situations where verbal communication is not possible. With the help of Morse code translation tools, they can convey critical information to coordinate rescue efforts and save lives.
Cryptography enthusiasts also appreciate Morse code for its simplicity and elegance. Morse code translation tools enable them to experiment with different encoding and decoding techniques, allowing for endless possibilities in the field of encryption and decryption.
Practical Uses in Everyday Life
While Morse code may seem like a relic of the past to some, it still finds practical applications in our everyday lives. For example, Morse code has been utilized in navigation aids such as lighthouses and buoys, where it serves as a visual or auditory beacon to guide ships safely through hazardous waters.
In addition, Morse code has found its way into popular culture, appearing in movies, literature, and even music. Its distinct rhythm and pattern have inspired artists and creators to incorporate it into their work, adding a unique and nostalgic flair to their creations.
The Future of Morse Code Translation
As technology continues to evolve, Morse code translation tools are likely to become even more sophisticated and user-friendly. Advances in artificial intelligence and natural language processing may enable these tools to interpret and translate Morse code messages with unprecedented accuracy and efficiency.
Moreover, as awareness of Morse code grows and interest in amateur radio and cryptography continues to rise, Morse code translation tools may see increased adoption among a broader audience. Whether it's for practical communication purposes or purely for recreational enjoyment, these tools have the potential to play a significant role in shaping the future of communication.
Conclusion
In conclusion, Morse code translation tools represent a fascinating intersection of history, technology, and communication. By bridging the gap between the analog past and the digital present, these tools keep alive the tradition of Morse code while making it accessible to a new generation of users.
1 note
·
View note
Link
0 notes