#monitoring software
Explore tagged Tumblr posts
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
#productivity#employee productivity time tracking#technology#employee monitoring#software#employee productivity monitoring#monitoring software
0 notes
Text
How I Used Employee Monitoring Software: Personal Experience
I work as an HR manager, and one of my biggest challenges has always been balancing employee productivity and workplace transparency. When remote work became more common, tracking employee performance got even more difficult. That’s when I decided to try CleverControl, an employee monitoring software designed to help businesses manage their teams more efficiently.
I was initially skeptical — would it feel intrusive? Would employees be comfortable with it? However, after several months of use, I can confidently say that CleverControl has been a game-changer. Let me share my experience.
Why I chose CleverControl
With a growing team, we needed a solution that could:
Help us understand how employees spent their work hours;
Ensure that remote employees remained engaged;
Provide insights without making employees feel like they were being spied on.
I researched several options, but CleverControl stood out due to its easy setup, powerful tracking features, and competitive pricing.
How I used CleverControl
After discussing the implementation with company leadership, we introduced CleverControl as a tool to improve productivity, not as a way to micromanage employees. Here are the features that I found extremely useful:
Online Activity Monitoring
CleverControl allows HR managers to track employee activity in real-time. I could see which apps and websites employees used most often. This helped us identify distractions and recommend time-management strategies. For example, one employee frequently browsed social media during work hours. Instead of penalizing them, we had a conversation and discovered they were struggling with burnout. After a few adjustments, they improved their focus, and their performance skyrocketed.
Screen Recording and Live Viewing
One of the most impressive features was live screen viewing. At first, I thought it would feel intrusive, but it was actually helpful in understanding how long certain tasks took. To give you an idea, our design team was spending more time on revisions than expected. When we reviewed screen recordings, we realized that unclear instructions from clients were causing delays. This led to a new briefing process, and we reduced unnecessary edits.
Chat Monitoring
CleverControl’s chat monitoring feature helped ensure employees weren’t sharing sensitive company data. While we trusted our team, these features provided an extra layer of security, especially for handling confidential client information.
Time Tracking
Instead of relying on manual check-ins, CleverControl automatically logged when employees started their workday and when they took breaks. This helped us ensure that everyone maintained a healthy work-life balance — especially our remote employees.
Pricing: is it worth it?
CleverControl pricing is based on the number of monitored computers. At the time of writing, the plans start at $4.70 per month per user, with discounts for annual subscriptions. Compared to other monitoring solutions, it’s quite affordable, especially given the range of features.
Final thoughts
Using CleverControl helped us identify productivity gaps, improve workflow efficiency, and support employees in becoming more engaged in their work. However, we made sure to use it ethically — transparency was key. Would I recommend it? Absolutely! If you’re an HR professional or a business owner looking for a non-intrusive, data-driven way to boost productivity, CleverControl is definitely worth considering.
Have you ever used employee monitoring software? Share your experience in the comments!
0 notes
Text
Keeping Your Remote Team On Track: Essential Monitoring Tools & Techniques

As we already know, Remote workforce monitoring means using digital tools and technology to keep an eye on what employees are doing and how productive they are when they work from home or other locations outside the office.
The primary goal of remote employee monitoring is to ensure productivity, maintain data security, and optimize workflow management. Tools used for this purpose can include time-tracking software, keystroke logging, screenshot capturing, and activity monitoring applications. These tools provide employers with insights into how employees spend their work hours, the applications they use, and their overall productivity levels.
While remote employee monitoring can help in managing remote teams and ensuring accountability, it also raises concerns about privacy and trust. Employees may feel that excessive monitoring infringes on their privacy and creates a culture of surveillance rather than trust.
What Is Remote Employee Monitoring?
Remote employee monitoring is the practice of utilizing digital tools and technologies to oversee and track the activities, performance, and productivity of employees working from locations outside the traditional office environment. This includes methods such as time tracking, activity logging, and usage monitoring to ensure accountability, optimize workflow, and maintain data security.
Best Remote Employee Monitoring System
Choosing the best remote employee monitoring system depends on the specific needs and priorities of a company and it also helps the management to analyze the ways of working of employees. However, some of the most popular and highly regarded remote employee monitoring systems include:
Teramind: Known for its comprehensive monitoring features, Teramind offers user behavior analytics, time tracking, and detailed activity reports. It also provides robust security measures like data loss prevention (DLP) and insider threat detection.
Hubstaff: This tool focuses on time tracking and productivity monitoring. It includes features like screenshot capture, activity level tracking, and detailed reporting. Hubstaff is popular for its ease of use and integration with other project management tools.
ActivTrak: ActivTrak provides detailed insights into employee activity with features such as productivity analysis, website and application monitoring, and customizable alerts. It's praised for its user-friendly interface and strong data analytics capabilities.
Time Doctor: Time Doctor offers time tracking, screenshot capture, and activity monitoring. It also includes distraction alerts and detailed reporting to help improve productivity. It integrates well with various project management and accounting software.
VeriClock: A straightforward and effective time tracking tool, VeriClock is ideal for businesses needing accurate tracking of remote work hours. It offers GPS location tracking and detailed time logs.
Is Employee Remote Monitoring Software Worth It?

Employee remote monitoring software can be worth it for many companies, particularly those with a significant number of remote workers. Additionally, Employee Burnout will take place if they continuously work for hours. So, these tools provide valuable insights into employee productivity, time management, and workflow efficiency, enabling managers to make informed decisions and optimize operations. By tracking activities and performance, companies can identify areas where employees may need additional support or training, leading to improved overall productivity.
Moreover, remote monitoring can enhance data security by detecting potential insider threats and ensuring compliance with company policies. However, the benefits must be balanced against potential drawbacks, such as privacy concerns and the risk of fostering a culture of mistrust. Transparent communication and ethical implementation are crucial to maximizing the advantages while maintaining employee morale and trust. When used thoughtfully, remote monitoring software can be a powerful tool for managing and supporting a remote workforce effectively. Also Watch: Leading Employee Engagement and Workforce Productivity Tool
youtube
Final Words
In conclusion, remote employee monitoring has become a crucial tool for managing the modern workforce, particularly with the rise of remote work. By leveraging digital tools and technologies, companies can gain valuable insights into employee productivity, ensure data security, and optimize workflow management. These systems offer various features, such as time tracking, activity logging, and real-time monitoring, which help managers oversee remote teams more effectively and make informed decisions based on concrete data.
However, it is essential to implement these practices transparently and ethically to maintain trust and respect among employees. Clear communication about the purpose of monitoring, what data is being collected, and how it will be used is vital to addressing potential privacy concerns and mitigating feelings of surveillance. Companies should also provide employees with access to their own monitoring data to promote transparency and foster a sense of ownership over their work.
#Remote Employee Monitoring#employee monitoring software#employee monitoring#monitoring software#remote work monitoring#Youtube
0 notes
Text
The Advantages of Implementing Computer Screen Monitoring Software for Your Business
Discover the numerous advantages of implementing computer screen monitoring software for your business. This powerful tool enables you to enhance productivity, ensure data security, and improve employee accountability. By providing real-time insights into employee activities, you can identify inefficiencies, prevent unauthorized access to sensitive information, and foster a more focused work environment. Additionally, screen monitoring software helps you maintain compliance with industry regulations and protect your business from potential risks. Embrace the benefits of computer screen monitoring to drive better performance and safeguard your company's assets.
1 note
·
View note
Text
Boosting Productivity Or Breaching Privacy? Exploring The Ethical Considerations Of Screenshot Monitoring

Nowadays, screenshot monitoring has gained traction as a powerful tool for enhancing productivity in the workplace. This practice involves capturing screenshots of employees' computer screens at regular intervals to track their activities and gauge their productivity levels. While intended to improve efficiency and accountability, the widespread adoption of this monitoring has raised significant ethical concerns.
As organizations seek to strike a balance between productivity and privacy, it becomes essential to explore the ethical considerations surrounding this practice. In this article, we delve into the nuances of monitoring screenshot, examining its implications on employee privacy and autonomy while navigating the legal landscape.
Throughout the discussion, we'll emphasize the importance of understanding the ethical dimensions of monitoring screenshot, addressing concerns about its legality and ethical implications.
It is a method employed by employers to track and monitor the computer activities of their employees. This practice involves capturing screenshots of employees' computer screens at predetermined intervals, providing insights into their work habits and productivity levels.
While proponents argue that monitoring screenshot offers valuable data for performance evaluation and resource allocation, critics raise concerns about its invasive nature and potential impact on employee morale. By scrutinizing the mechanics of monitoring screenshots, we can better appreciate its potential benefits and drawbacks, particularly in relation to privacy and autonomy in the workplace.
Legality Of Monitoring Employee Activity
Navigating the legal landscape of employee monitoring tool is essential for employers seeking to implement monitoring screenshot practices. While monitoring employee activity is generally legal in many jurisdictions, there are important legal considerations to bear in mind. Employers must ensure compliance with relevant laws and regulations governing employee privacy rights, informed consent, and data protection.
By fostering transparency and obtaining consent from employees, organizations can mitigate legal risks and uphold ethical standards in their monitoring practices. It's imperative for employers to understand the legal framework surrounding monitoring screenshot to avoid potential legal pitfalls and safeguard employee rights.
Ethical Considerations Of Screenshot Monitoring
Ethical considerations loom large in the realm of monitoring screenshot, as organizations grapple with questions of privacy, trust, and employee autonomy. The widespread adoption of monitoring technologies raises concerns about the potential for misuse and abuse of monitoring data by employers. Employees may feel uneasy about the constant surveillance of their computer activities, leading to issues of morale and job satisfaction.
Balancing the need for productivity with respect for employee privacy requires careful consideration of ethical principles and values. By exploring different perspectives and ethical frameworks, organizations can navigate the ethical complexities of monitoring screenshot and develop policies that prioritize the well-being and rights of their employees.
Balancing Productivity And Privacy

Achieving a balance between productivity goals and respect for employee privacy is paramount for organizations implementing monitoring screenshot. Employers can explore alternative monitoring methods and technologies that prioritize privacy safeguards while still providing valuable insights into employee performance.
Open communication and trust-building initiatives are essential for fostering a positive work environment where employees feel respected and valued. Clear policies and guidelines for monitoring practices can help mitigate concerns and ensure accountability on both sides. By adopting a proactive approach to balancing productivity and privacy, organizations can uphold ethical standards while maximizing workforce productivity.
Case Studies And Examples
Examining real-world case studies and examples offers valuable insights into the practical implications of monitoring screenshot in different organizational contexts. By studying the experiences of companies that have implemented monitoring screenshot, we can glean lessons learned, ethical dilemmas faced, and best practices observed.
These case studies provide a nuanced understanding of how different industries and company cultures influence the approach to monitoring and highlight the importance of context-specific ethical considerations. Also Watch: Leading Employee Engagement and Workforce Productivity Tool
youtube
Ending It Up!
In conclusion, navigating the ethical considerations of screenshot monitoring requires a nuanced understanding of its implications on employee privacy, trust, and autonomy. As organizations strive to boost productivity while respecting employee rights, it's essential to evaluate the legality and ethical implications of monitoring practices.
By prioritizing transparency, informed consent, and open communication, employers can foster a work environment that balances productivity goals with respect for employee privacy. Moving forward, organizations must continue to uphold ethical standards and prioritize the well-being of their employees, reinforcing the importance of ethical considerations in monitoring screenshot practices.
#Screenshot Monitoring#monitoring employee#screenshot#screenshot monitoring software#monitoring software#Youtube
0 notes
Text
#productivity#technology#monitoring software#Employee Monitoring Software#Time Champ#Employee Monitoring
0 notes
Text
Top 10 Benefits of Employee Screen Monitoring for Businesses in 2025
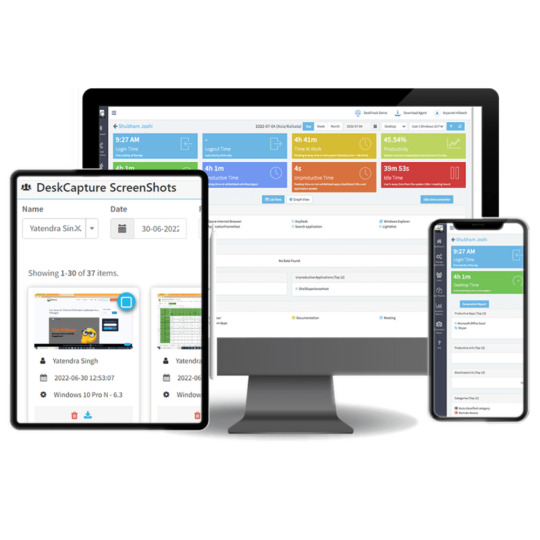
In the rapidly evolving business landscape of 2025, employee screen monitoring has become a critical tool for organizations striving to enhance productivity, security, and overall operational efficiency. As companies embrace remote work and hybrid models, the need for effective monitoring software has never been greater. Here are the top 10 benefits of employee screen monitoring software for businesses in 2025.
1. Improved Productivity
One of the most significant benefits of employee screen monitoring software is its ability to improve productivity. By tracking employees' activities in real-time, employers can gain valuable insights into how time is being spent during work hours. Monitoring tools can identify time-wasting activities, such as excessive social media use, and help employees stay focused on their tasks. With detailed reports on activity, managers can provide constructive feedback and make necessary adjustments to optimize workflow. This leads to greater efficiency and higher output across the organization.

2. Enhanced Security
With increasing cybersecurity threats, especially in remote work settings, employee screen monitoring software plays a vital role in safeguarding sensitive business data. The software can monitor for unauthorized access, detect unusual activity, and flag potential security breaches in real-time. By identifying suspicious behavior, businesses can prevent data leaks, hacking attempts, and internal threats, ensuring that sensitive company information remains protected. This layer of security is especially crucial as businesses continue to store and manage sensitive data online.
3. Better Time Management
Employee screen monitoring can also help employees better manage their time. By analyzing their activity patterns, both employees and managers can identify areas where time is being wasted or inefficiently used. Whether it's spending too much time on non-work-related websites or procrastinating, screen monitoring can serve as a wake-up call for employees to manage their time more effectively. With regular reports and insights, businesses can foster a culture of accountability where employees take ownership of their work habits and strive to improve them.
4. Real-Time Activity Tracking
Employee screen monitoring tools offer the advantage of real-time tracking, allowing managers to oversee employees’ activities as they happen. This is particularly useful in managing remote teams, as it provides employers with an accurate view of what their employees are working on during office hours. With real-time monitoring, businesses can quickly identify potential issues and address them before they escalate. This immediate feedback loop ensures that employees stay on task and can improve overall efficiency.
5. Increased Accountability
Accountability is a cornerstone of high-performing teams. Employee screen monitoring fosters a culture of transparency and accountability by providing clear, objective data on each employee’s activities. When employees know their screens are being monitored, they are more likely to stay focused and avoid distractions. This sense of responsibility encourages employees to manage their time wisely and perform their duties with a higher level of diligence. It also gives managers a fair and unbiased method of evaluating employee performance.
Read More: Which Industries Benefit the Most from Time Tracking Software?
6. Data-Driven Insights for Better Decision-Making
Employee screen monitoring software provides data that businesses can leverage to make informed decisions about workflows, staffing needs, and process optimization. By analyzing productivity data, businesses can identify trends and patterns that might not be obvious through traditional methods. For example, if certain employees are consistently more productive than others, managers can examine their work habits and replicate successful strategies across the team. Additionally, data-driven insights can help managers assess whether existing workflows are optimal or require adjustments to improve efficiency.

7. Compliance with Legal and Regulatory Requirements
In some industries, businesses are required to comply with specific legal and regulatory standards that dictate how employee data is managed and protected. Employee screen monitoring software can help businesses meet these compliance requirements by providing detailed logs of employee activity. This can be especially crucial in sectors like finance, healthcare, and legal services, where compliance is not just a good practice but a legal obligation. By maintaining a secure and accurate record of employee activities, businesses can demonstrate that they are in line with industry regulations and avoid potential legal penalties.
8. Remote Team Management
Managing remote teams can be challenging, especially when employees work from different locations and time zones. Employee screen monitoring software provides a way to bridge this gap by offering visibility into what remote workers are doing. Managers can use monitoring data to check if employees are following the right processes and staying on task, even when they’re not physically present. This added layer of oversight helps build trust between remote employees and managers while ensuring that the business's goals are being met, regardless of the team’s physical location.
9. Reduced Employee Misconduct
Employee screen monitoring software can act as a deterrent to misconduct and inappropriate behavior in the workplace. Knowing that their activities are being monitored discourages employees from engaging in activities that are detrimental to the organization, such as accessing inappropriate websites, stealing company data, or engaging in unethical conduct. This proactive approach helps businesses maintain a professional and ethical environment, leading to a more positive organizational culture.
Read More: Top 15 Best QuickBooks Time Alternatives in 2025
10. Improved Customer Service
Finally, employee screen monitoring can indirectly improve customer service. By ensuring employees are using their time efficiently, businesses can ensure that customer-facing teams are more responsive and focused on their tasks. Monitoring can help identify areas where employees may be struggling or spending too much time on non-essential tasks, allowing businesses to provide better training and support. In turn, this leads to faster response times, higher-quality service, and more satisfied customers.
Conclusion
Employee screen monitoring software offers a range of benefits for businesses looking to enhance productivity, security, and overall operational efficiency in 2025. From boosting time management and accountability to improving data security and remote team management, the advantages are clear. As companies continue to adapt to the challenges of a more digitally connected workforce, employee screen monitoring will play an essential role in optimizing performance and ensuring business success in the years to come. By investing in the right monitoring tools, businesses can create a more productive, secure, and accountable workplace that benefits both employers and employees.
#software#time tracking software#monitoring software#employee monitoring system#employee monitoring software india#employee monitoring software#project time management#best employee monitoring software in india
0 notes
Text
0 notes
Text
Why Cloud-Based Monitoring Is a Must-Have for Scalable Business Operations?

Scalability is key for businesses aiming to adapt to market changes, embrace new opportunities, and maintain long-term success. The scalable operations directly depends on the overall employees' performance. How to boost productivity and streamline the workflow? The solution, the market offers, is cloud-based monitoring of job activities. Let's see the details of this software solution for successful business development.
What Is Cloud-Based Monitoring Solutions?
Cloud-based monitoring solutions is a system that uses cloud technology to manage and assess the performance of employees due to the generated reports with insights into the workflow. Unlike traditional monitoring systems that rely on on-premise hardware, cloud-based solutions operate through Internet-connected platforms, providing real-time visibility and centralized control across distributed environments.
This type of monitoring allows businesses to track data, user activity, system performance, and potential security threats remotely. The tracking is carried out through user-friendly dashboards. With features like scalability, seamless updates, and integration capabilities, cloud-based monitoring software is a flexible and cost-effective solution for modern, dynamic, and geographically diverse businesses.
Challenges in Scaling Business Operations Without Cloud Monitoring
Scaling business is a cornerstone in achieving the constant business development. Without cloud-based monitoring software, businesses may face challenges that hinder the business growth. Let's see and assess what obstacles await business leaders:
❌ Lack of real-time visibility
❌ Difficulty managing distributed teams and systems
❌ Inefficient use of resources
❌ Increased risk of data silos
❌ Security and compliance vulnerabilities
❌ Limited scalability of on-premise solutions
❌ Inconsistent customer experiences
If you handle these hindrances, using cloud-based employee monitoring solutions, you will be able to reach stated goals faster.
Key Advantages of Cloud-Based Monitoring for Scalability
There are advantages that cloud-based monitoring brings to the business scalability:
✔️ Centralized monitoring across multiple locations ✔️ Flexibility and easy integration ✔️ Cost efficiency ✔️ Real-time data and reports ✔️ Enhanced security ✔️ Scalability without limitations ✔️ Improved collaboration and accessibility ✔️ Minimal maintenance and downtime ✔️ Sustainability and eco-friendliness
Depending on the sphere, your business is working in, the number of key advantages may be even more extensive.
How to Choose the Right Solution for Your Business?
It is crucial for businesses to choose the right cloud-based monitoring solution. Attempting to choose the software for tracking activities, you'd better compare certain points. Primary every business leader should define the requirements of his own business. Write down your goals and scalability needs.
Evaluate key features. Specialists recommend to look for essential features like real-time monitoring, analytics, customizable dashboards, and alert systems. Besides, ensure compatibility with your existing tools and systems, such as CRM, ERP, or project management software.
Opt for a platform with an intuitive interface that doesn’t require extensive training and provide high-grade security solutions - data encryption, regular updates, and advanced threat detection.
Assess the cost: subscription-based plans, pay-as-you-go options, or tiered packages. Having made a decision to buy the software, conduct testing first. If satisfied, you are welcome to integrate the right solution to your business to enhance scalability.
Summing Up
Cloud-based monitoring is a must-have for scalable business operations due to the whole list of advantages and challenges every business may face without this software.
0 notes
Text
Data-Driven Decisions: Harnessing Software Usage Tracking For Business Growth

Making wise decisions is essential for success in the dynamic world of business. Software usage tracking is a potent tool that firms can use thanks to the development of new technology. With the use of this technology, businesses may obtain insightful information about how their software is being used, which opens the door to data-driven choices that can spur the expansion of their operations.
Are you prepared to learn more about tracking the use of apps? Let's get started and learn what this post is about without further ado.
What is Software Usage Tracking?
Software usage tracking is the methodical gathering and examination of information on how different software programs are use inside a company. This procedure offers a thorough rundown of how staff members utilize software, including how often they use it, which features they use, and how long they use it.
Tools for tracking software usage today go beyond simple metrics and look at user behavior, software performance, and potential areas for improvement. By utilizing such instruments, organizations can acquire a thorough comprehension of their product environment, eventually prompting more educated navigation.
Benefits of Using Software Usage Tracking:
Optimizing Software Investments:
One of the essential advantages of software usage tracking is the capacity to improve programming ventures. By understanding which applications are most and least utilized, organizations can arrive at informed conclusions about restoring licenses, redesigning programming adaptations, or ending underutilized devices. Its optimization can save a lot of money and ensure that resources are allocated to software solutions with the impact.
2. Enhancing User Experience:
Application usage tracking empowers organizations to distinguish designs in client conduct. This significant data permits associations to tailor client encounters by refining programming connection points, smoothing out work processes, and tending to problem areas. Further developing the general client experience helps efficiency as well as adds to representative fulfillment and engagement.
3. Security and Compliance:
Tracking software usage is crucial for maintaining robust security measures and ensuring regulatory compliance. By monitoring how software is accessed and used, organizations can identify any unauthorized or suspicious activities. Additionally, businesses can use this data to demonstrate compliance with industry standards and regulations, reducing the risk of legal and financial significance.
4. Proactive Issue Resolution:
Software usage tracking provides real-time insights into the performance of various applications. It allows businesses to identify and address issues promptly, minimizing downtime and potential disruptions to operations. Proactive issue resolution not only enhances overall efficiency but also contributes to a more reliable and resilient IT infrastructure.
How to Track Software Usage?
Effective software usage tracking involves the implementation of specialized tools and practices. Here are steps to track software usage successfully:
Choose the Right Tracking Tools:
Select software usage tracking tools that align with your business goals and the complexity of your software ecosystem. Consider factors such as scalability, integration capabilities, and the depth of analytics provided by the chosen tools.
Define Key Metrics:
Identify the key metrics that align with your business objectives. These may include user engagement, feature usage, application performance, and license utilization. Clearly defining these metrics ensures that the tracking process is focused and provides meaningful insights.
Implement User Authentication:
To accurately track software usage, implement user authentication mechanisms. It ensures that data is attributed to specific users, allowing for personalized insights into individual and team-level software utilization.
Regularly Analyze and Interpret Data:
Regularly analyze the collected data to derive meaningful insights. Look for patterns, trends, and anomalies that can inform decision-making. Continuous monitoring and analysis ensure that your business remains agile and responsive to changing software usage dynamics.

How Your Business Can Benefit from Monitoring Software Usage?
1. Strategic Resource Allocation:
By understanding which software applications are integral to daily operations, businesses can strategically allocate resources. This includes investments in training programs, software upgrades, and support services. This strategic approach maximizes the impact of resources, driving efficiency and productivity.
2. Informed Software Development:
For businesses involved in software development, usage tracking provides invaluable feedback on how users interact with their applications. This data can guide the development process, helping teams prioritize features, eliminate bottlenecks, and enhance overall usability. Informed software development leads to products that better align with user needs and expectations.
3. Improved Vendor Negotiations:
Armed with accurate usage data, businesses are better positioned to negotiate with software vendors. It includes renegotiating licensing agreements, exploring volume discounts, or transitioning to more cost-effective alternatives. Negotiating from a position of knowledge ensures that businesses receive optimal value from their software investments.
4. Enhanced Decision-Making:
Ultimately, the primary benefit of software usage tracking is the ability to make informed, data-driven decisions. Whether it's optimizing software investments, improving user experiences, or addressing security concerns, businesses equipped with accurate usage data are empowered to make decisions that positively impact their bottom line.
You Can Also Watch:
youtube
Conclusion:
All in all, tackling software usage tracking for information-driven choices is a system for business development. By improving programming speculations, upgrading client encounters, guaranteeing security and consistency, and proactively settling issues, associations can situate themselves for progress in the present cutthroat business scene. Through cautious execution of the following instruments and investigation of measurements, organizations can open the maximum capacity of their product environment, driving effectiveness, advancement, and business development.
#software usage tracking#employee tracker#computer usage tracker#employee monitoring software#monitoring software#Youtube
0 notes
Text

Best Computer Monitoring Software | Mobistealth
If you are looking for the Best Computer Monitoring Software? Mobistealth Computer Tracking Software for Windows and MAC is your All-in-One solution. Our advanced yet incredibly easy-to-use Desktop Monitoring Software keeps you informed and in control by sending information to your Mobistealth user account, such as:
Mobistealth Software to Monitor PC provides you with very cost-effective and easy-to-use software for monitoring the activities of your kid's computers. Every feature in Mobistealth is designed to provide you with the relevant data you need to stay informed and in control. From the moment the activity monitoring software is installed on the computer you want to track, it begins recording and relaying information directly to your Mobistealth user account which you can access 24/7 from anywhere on the planet.
Visit us: https://www.mobistealth.com/pc-monitoring-software
#Best Computer Monitoring Software#Computer Monitoring Software#Monitoring Software#Best Monitoring Software
0 notes
Text
Guardians of Bridges: Battling Scour and Corrosion with Advanced Monitoring - Encardio Rite
🌉 Discover the world of structural health monitoring! 🏗️ #InfrastructureSafety #Engineering #Technology
Learn how advanced monitoring solutions are safeguarding bridges from scour and corrosion. Dive into our latest blog: Click here
#geotechnical instrumentations#bridge monitoring#geotechnical monitoring#structural monitoring#bridges#monitoring software
0 notes
Text
Navigation Buoys GPS Tracking and Monitoring Solution
GPS tracking web application system for navigating, monitoring the location and data of marine buoys. The buoys have GPS trackers that are connected to the satellites to ensure real-time data monitoring.
Industry: Logistics and Transportation
Tech stack: Node.js, React.js
#nodejs#node.js#node js developers#node js development company#node#react app#react.js#react js#outsourcing#software development#custom software solutions#it staffing company#custom software development#staff augmentation#web development#it staff augmentation#it staff offshoring#custom software#monitoring software#monitoring systems#monitoring#data management
0 notes