#medical device cybersecurity
Explore tagged Tumblr posts
Text
Transform Medical Devices into Connected-Care Solutions with BioT’s No-code Platform
1 note
·
View note
Text
New AI algorithm could enhance autoimmune disease prediction and therapy

- By InnoNurse Staff -
An advanced AI algorithm from Penn State University may enhance the accuracy and timing of predictions and introduce novel treatments for autoimmune diseases.
By examining the genetic code, the algorithm better models gene expression and regulation, identifying additional risk genes associated with these conditions.
Read more at Penn State
///
Other recent news and insights
Illuminating neurovascular dynamics with 3D-printed implants and bioluminescence (SPIE)
New device enables paraplegics to partially regain hand function (AFP/Medical Xpress)
Innovative 3D printing techniques for eye condition treatments (University of East Anglia/Medical Xpress)
Australia: The MediSecure data breach explained (The Conversation)
#ai#genomics#health informatics#health tech#biotech#medtech#neuroscience#medical implants#3d printing#disability#medical device#ophthalmology#eye#australia#cybersecurity#cyberattack#data breach#medisecure
0 notes
Text

The Myth: Controller Area Network (CAN) is “Too Easy to Hack”
The potential security issues of CAN and its higher-layer protocols attract increased attention from the automotive, control, and medical industries. At first glance, believing that a well-documented standard like ISO 11898 makes it easier to manipulate control functions, whether in an automobile or a medical device such as an MRI or CT scanner, makes sense.
0 notes
Text
Emeritus Makes Cyber Security for Healthcare Industry Easy
The main concern of a healthcare organization that has a number of equipments and electronic data is protecting its confidentiality, maintain its integrity and make the data available for internal purpose to every patient and their doctor. Cyber security for healthcare industry involves protecting their data and assets from unwanted access. The number of cyber attacks has been increasing every day. A new threat arises as soon as one gets resolved. Thus, healthcare cybersecurity companies are very vigilant about the healthcare organization’s data. To ensure that vulnerable data is protected all the time regular checks and routine tests are made. A healthcare provider if doesn’t take strict measures to keep data safe, the number of attacks would lead to a disastrous situation. Secure networks and platforms are essential to keep an eye on the ever changing threat arising from various criminal sources.
Employees are vulnerable to phishing schemes due to the lack of cybersecurity education within these organizations. Thus, medical staff and employees should be vigilant about it. Healthcare providers have been worried about these factors for a while, and the pandemic has only intensified them. Healthcare organizations must prioritize cybersecurity in medical devices by focusing on these areas as they recover from the pandemic and other cyberattacks. HIMSS stipulates that cyber-security knowledge is required of both workforce and c-suite members. There should be more than one person or team responsible for cybersecurity and its operations. It is important for anyone working as a healthcare provider to be aware of basic practices and the consequences of a cyberattack. Engaging employees in cyber risk assessment topics through sessions and trainings. By doing this, they can gain more knowledge about the subject. Employees must be able to recognize the warning signs in the event of a data breach.
According to Cyber security and risk advisory AHA, there is a reason why healthcare cyber threats are high. They possess a high amount of valuable info that cyber criminals can use them to target the subject. The stolen data includes patient’s protected heath info. Critical financial information like credit cards, bank account numbers, social security numbers that are related to their medical records are available on their networks that are vulnerable to threats. There are medical researches, ideas and inventions that are confidential to disclose are stored in the organization’s network. If they are left unsecured major breaches leading to monetary loss.
Medical cybersecurity should keep an eye out for the three major cyber threats. Malware, ransomware and distributed denial of service attacks are the three major cyberattacks that a healthcare organization should look out for. Emeritus, provider of IT support and hospital cyber security, has always insisted on a culture of cybersecurity awareness in a healthcare organization. Every employee should proactively try to protect patients and their data. Both the organization and its patients will benefit greatly from mitigating cyber risks due to its tremendous impact. Visit us at https://www.emerituscs.com/ to know about other services we provide.
#cyber security for healthcare industry#cyber risk assessment#cybersecurity in medical devices#healthcare cybersecurity
0 notes
Text
The surveillance advertising to financial fraud pipeline

Monday (October 2), I'll be in Boise to host an event with VE Schwab. On October 7–8, I'm in Milan to keynote Wired Nextfest.

Being watched sucks. Of all the parenting mistakes I've made, none haunt me more than the times my daughter caught me watching her while she was learning to do something, discovered she was being observed in a vulnerable moment, and abandoned her attempt:
https://www.theguardian.com/technology/blog/2014/may/09/cybersecurity-begins-with-integrity-not-surveillance
It's hard to be your authentic self while you're under surveillance. For that reason alone, the rise and rise of the surveillance industry – an unholy public-private partnership between cops, spooks, and ad-tech scum – is a plague on humanity and a scourge on the Earth:
https://pluralistic.net/2023/08/16/the-second-best-time-is-now/#the-point-of-a-system-is-what-it-does
But beyond the psychic damage surveillance metes out, there are immediate, concrete ways in which surveillance brings us to harm. Ad-tech follows us into abortion clinics and then sells the info to the cops back home in the forced birth states run by Handmaid's Tale LARPers:
https://pluralistic.net/2022/06/29/no-i-in-uter-us/#egged-on
And even if you have the good fortune to live in a state whose motto isn't "There's no 'I" in uter-US," ad-tech also lets anti-abortion propagandists trick you into visiting fake "clinics" who defraud you into giving birth by running out the clock on terminating your pregnancy:
https://pluralistic.net/2023/06/15/paid-medical-disinformation/#crisis-pregnancy-centers
The commercial surveillance industry fuels SWATting, where sociopaths who don't like your internet opinions or are steamed because you beat them at Call of Duty trick the cops into thinking that there's an "active shooter" at your house, provoking the kind of American policing autoimmune reaction that can get you killed:
https://www.cnn.com/2019/09/14/us/swatting-sentence-casey-viner/index.html
There's just a lot of ways that compiling deep, nonconsensual, population-scale surveillance dossiers can bring safety and financial harm to the unwilling subjects of our experiment in digital spying. The wave of "business email compromises" (the infosec term for impersonating your boss to you and tricking you into cleaning out the company bank accounts)? They start with spear phishing, a phishing attack that uses personal information – bought from commercial sources or ganked from leaks – to craft a virtual Big Store con:
https://www.fbi.gov/how-we-can-help-you/safety-resources/scams-and-safety/common-scams-and-crimes/business-email-compromise
It's not just spear-phishers. There are plenty of financial predators who run petty grifts – stock swindles, identity theft, and other petty cons. These scams depend on commercial surveillance, both to target victims (e.g. buying Facebook ads targeting people struggling with medical debt and worried about losing their homes) and to run the con itself (by getting the information needed to pull of a successful identity theft).
In "Consumer Surveillance and Financial Fraud," a new National Bureau of Academic Research paper, a trio of business-school profs – Bo Bian (UBC), Michaela Pagel (WUSTL) and Huan Tang (Wharton) quantify the commercial surveillance industry's relationship to finance crimes:
https://www.nber.org/papers/w31692
The authors take advantage of a time-series of ZIP-code-accurate fraud complaint data from the Consumer Finance Protection Board, supplemented by complaints from the FTC, along with Apple's rollout of App Tracking Transparency, a change to app-based tracking on Apple mobile devices that turned of third-party commercial surveillance unless users explicitly opted into being spied on. More than 96% of Apple users blocked spying:
https://arstechnica.com/gadgets/2021/05/96-of-us-users-opt-out-of-app-tracking-in-ios-14-5-analytics-find/
In other words, they were able to see, neighborhood by neighborhood, what happened to financial fraud when users were able to block commercial surveillance.
What happened is, fraud plunged. Deprived of the raw material for committing fraud, criminals were substantially hampered in their ability to steal from internet users.
While this is something that security professionals have understood for years, this study puts some empirical spine into the large corpus of qualitative accounts of the surveillance-to-fraud pipeline.
As the authors note in their conclusion, this analysis is timely. Google has just rolled out a new surveillance system, the deceptively named "Privacy Sandbox," that every Chrome user is being opted in to unless they find and untick three separate preference tickboxes. You should find and untick these boxes:
https://www.eff.org/deeplinks/2023/09/how-turn-googles-privacy-sandbox-ad-tracking-and-why-you-should
Google has spun, lied and bullied Privacy Sandbox into existence; whenever this program draws enough fire, they rename it (it used to be called FLoC). But as the Apple example showed, no one wants to be spied on – that's why Google makes you find and untick three boxes to opt out of this new form of surveillance.
There is no consensual basis for mass commercial surveillance. The story that "people don't mind ads so long as they're relevant" is a lie. But even if it was true, it wouldn't be enough, because beyond the harms to being our authentic selves that come from the knowledge that we're being observed, surveillance data is a crucial ingredient for all kinds of crime, harassment, and deception.
We can't rely on companies to spy on us responsibly. Apple may have blocked third-party app spying, but they effect nonconsensual, continuous surveillance of every Apple mobile device user, and lie about it:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
That's why we should ban commercial surveillance. We should outlaw surveillance advertising. Period:
https://www.eff.org/deeplinks/2022/03/ban-online-behavioral-advertising
Contrary to the claims of surveillance profiteers, this wouldn't reduce the income to ad-supported news and other media – it would increase their revenues, by letting them place ads without relying on the surveillance troves assembled by the Google/Meta ad-tech duopoly, who take the majority of ad-revenue:
https://www.eff.org/deeplinks/2023/05/save-news-we-must-ban-surveillance-advertising
We're 30 years into the commercial surveillance pandemic and Congress still hasn't passed a federal privacy law with a private right of action. But other agencies aren't waiting for Congress. The FTC and DoJ Antitrust Divsision have proposed new merger guidelines that allow regulators to consider privacy harms when companies merge:
https://www.regulations.gov/comment/FTC-2023-0043-1569
Think here of how Google devoured Fitbit and claimed massive troves of extremely personal data, much of which was collected because employers required workers to wear biometric trackers to get the best deal on health care:
https://www.eff.org/deeplinks/2020/04/google-fitbit-merger-would-cement-googles-data-empire
Companies can't be trusted to collect, retain or use our personal data wisely. The right "balance" here is to simply ban that collection, without an explicit opt-in. The way this should work is that companies can't collect private data unless users hunt down and untick three "don't spy on me" boxes. After all, that's the standard that Google has set.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/09/29/ban-surveillance-ads/#sucker-funnel

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#commercial surveillance#surveillance#surveillance advertising#ad-tech#behavioral advertising#ads#privacy#fraud#targeting#ad targeting#scams#scholarship#nber#merger guidelines#ftc#doj
285 notes
·
View notes
Text
MHA DR-Self Hero Profile

(I'm not an artist but I tried ;~; )

Hero Name: Impulse
Considering MHA's fantastical laws of physics and such, I'm taking some liberties here, I know EMP's don't necessarily work this way :)
Quirk: Electro-Magnetic Pulse (EMP)
I can use and manipulate EMP’s to affect anything that can use or run on electricity to my will. At some point I learn to control biological tissue by manipulating electrical signals in the cells. I can do anything from diagnosing issues in electronics to accessing any information (even the most confidential) as long as it’s on the device or connected to the internet in any way. Firewalls and encryption can take a bit longer to navigate through, but in general are no issue. No trace is left behind; my activities cannot be traced, even if I pull up the information on a computer for others to see. I can interface with tech and view everything in my head, so battery usage in devices is minimal due to there being no need for screens or physical input. Outside electrical sources are not needed to manipulate most objects.
Skills:
Some of these skills are gained and perfected in my time at UA.
Parkour:
Agility and Speed: Enhances my ability to move rapidly through urban environments, chase villains, or reach areas inaccessible by conventional means.
Escape and Evasion: Allows me to evade capture or dangerous situations.
Rescue Operations: Facilitates swift navigation in disaster zones.
Skateboarding: Translates into Hoverboard use
Quick Transportation: Provides a fast and agile mode of transportation, allowing me to cover ground quickly.
Enhanced Maneuverability: Helps me perform sharp turns and evasive maneuvers during pursuits or escapes.
Combat Utility: The board can be used as a tool in combat, either as a weapon or a shield.
Krav Maga:
Self-Defense: Equips me with practical combat skills to neutralize threats quickly and effectively.
Close-Combat Proficiency: Enhances my ability to handle hand-to-hand combat situations.
Situational Awareness: Trains me to remain vigilant and responsive to immediate threats.
Electronics and Programming:
Tech Control: Allows me to interface with and control technology.
Hacking: Enables me to hack into security systems, disable electronic traps, or access critical information.
Repair and Modification: Equips me with the skills to repair damaged tech or modify devices on the fly.
Cybersecurity:
Counter-Hacking: Allows me to defend against cyber-attacks from villains.
Data Protection: Ensures the safety of personal and mission-related data.
Tech Defense: Helps me implement security measures on their own devices.
Neurobiology:
Safe Manipulation: Enables me to manipulate biological electrical signals safely.
Medical Assistance: Provides the knowledge to offer medical aid, such as stabilizing heartbeats or alleviating pain.
Enhanced Strategy: Offers insight into how opponents' nervous systems function, aiding in the development of effective, non-lethal combat strategies.
Tactical Thinking and Strategy:
Mission Planning: Helps me develop effective plans for complex missions.
Adaptability: Equips me to adjust strategies quickly in response to changing conditions or unexpected challenges.
Team Coordination: Enhances my ability to work with and lead teams, coordinating actions and resources.
Leadership and Communication:
Team Leadership: Prepares me to lead teams of other heroes or rescue personnel, making critical decisions under pressure.
Public Interaction: Equips me to communicate with the public, media, and authorities.
Conflict Resolution: Enhances my ability to de-escalate situations and resolve conflicts peacefully when possible.
First Aid and Emergency Response:
Medical Assistance: Allows me to provide critical care in the field, stabilizing injured individuals until they can receive professional treatment.
Disaster Response: Equips me to manage disaster scenarios, providing aid, organizing evacuations, and ensuring public safety.
Self-Care: Enables me to tend to my own injuries during missions.
Support Items:
Smart Visor:
Augmented Reality Interface: Displays real-time information overlay, including maps, data streams, and tactical readouts, directly in the user’s field of vision.
Enhanced Vision Modes: Includes night vision, thermal imaging, and x-ray vision.
Universal Integration: Can connect to any electronic device or network within range.
Communication Hub: Functions as a secure communication device.
Mental Command: Responds to mental commands for hands-free operation.
Insulation: Protects against electronic surges.
Retractable Smart Wires:
Grappling hooks: Equipped with small yet extremely strong and durable grappling hooks that can latch on to most surfaces, or grip to self when wire is wrapped around an object.
Electric Conductivity: Can channel the user's EMP directly through the cables.
Durable and Flexible: Made from a thin high-strength, flexible material that can withstand extreme conditions and physical stress. Made from a Material that while remaining flexible, does not tangle with itself.
Automatic Retraction: Retracts into a compact, portable spool when not in use.
Variable Length: Length can be adjusted as needed, extending up to several yards.
Collapsible Hoverboard:
Folding Mechanism: Folds down from the size of a skateboard deck into a compact, pocket sized form.
Electric Propulsion: Uses a high-efficiency electromagnetic propulsion system for smooth and silent movement, easily controlled by the user’s quirk.
Remote Summoning: Can be summoned to the user’s location.
Stability and Control: Features advanced gyroscopic stabilization for smooth rides over various terrains.
Speed and Maneuverability: Capable of high speeds and sharp turns.
Pocket Tech:
Micro Bugs
Micro Cameras
Micro Drones
Mini Bombs
Costume:
Sneakers:
Shock-Absorbing Soles: Provides superior cushioning to absorb impact during high-speed movements and long jumps.
Conductive Fabric: Allows me to channel EMP.
Magnetic Traction Pads: Ensures superior grip on the hoverboard, maintaining stability.
Lightweight and Breathable: Keeps the feet cool and dry, enhancing comfort and reducing fatigue during long missions.
Reinforced Toe and Heel Caps: Provides extra protection against impacts and enhances durability.
Socks:
Conductive Fibers: Allows me to channel EMP.
Moisture-Wicking Fabric: Keeps feet dry and comfortable.
Compression Zones: Provides targeted compression to support key areas of the foot and ankle, improving blood circulation and reducing fatigue.
Shock-Absorbing Padding: Enhances comfort by absorbing impact and reducing stress on the feet.
Antimicrobial Treatment: Prevents the growth of odor-causing bacteria, keeping the socks fresh and hygienic.
Seamless Construction: Reduces friction and prevents blisters.
Thermoregulatory Properties: Keeps feet warm in cold conditions and cool in hot conditions.
Reinforced Arch Support: Provides additional support to the arch, enhancing stability and reducing the risk of injuries.
Pants:
Durable Fabric: Provides protection against wear and tear.
Conductive Threading: Allows me to channel EMP.
Moisture-Wicking and Breathable: Keeps me cool and dry.
Reinforced Knees and Seat: Provides extra durability and protection.
Flexible: Ensures a comfortable fit that adapts to my movements, providing flexibility and reducing restrictions.
Multiple Pockets: Provides ample storage space for tools, gadgets, and personal items.
Thermoregulatory Properties: Keeps me warm in cold conditions and cool in hot conditions.
Harness:
Durable Material: Ensures the harness can withstand the rigors of combat and daily use.
Ergonomic Design: Provides comfort and support during prolonged wear, distributing weight evenly.
Adjustable Fit: Provides a customizable fit, ensuring the harness stays secure and comfortable.
Attachment Points: Allows me to attach additional gear, tools, or accessories.
Quick-Release Buckles: Ensures the harness can be easily and quickly donned or doffed.
Integrated Power Conduits: Allows me to channel EMP, enhancing my ability to manipulate the smart cables.
Reflective and High-Visibility Elements: Increases visibility in low-light conditions, ensuring I can be seen by allies and avoid hazards.
Shirt:
Conductive Fabric: Allows me to channel EMP.
Moisture-Wicking and Breathable: Keeps me cool and dry.
Compression Zones: Provides support to key muscle groups, improving blood circulation and reducing muscle fatigue.
Reinforced Seams: Enhances durability and prevents tearing.
Thermoregulatory Properties: Keeps me warm in cold conditions and cool in hot conditions.
Flexible and Stretchable: Ensures a snug fit that moves with my body, providing full range of motion and reducing restrictions.
Antimicrobial Treatment: Prevents the growth of odor-causing bacteria, keeping the shirt fresh and hygienic.
Gloves:
Conductive Fabric: Allows me to channel EMP.
Ergonomic Design: Provides a natural fit that reduces hand fatigue and enhances dexterity.
Reinforced Palms and Fingers: Offers extra protection against abrasion and impact.
Touchscreen Compatibility: Allows me to interact with touchscreen devices if needed.
Breathable and Moisture-Wicking: Keeps hands cool and dry by allowing sweat to evaporate quickly.
Adjustable Wrist Straps: Provides a secure fit, ensuring the gloves stay in place.
Shock-Absorbing Padding: Reduces impact and vibration, protecting the hands.
Antimicrobial Treatment: Prevents the growth of odor-causing bacteria, keeping the gloves fresh and hygienic.
Jacket:
Insulated Fabric: Provides superior warmth without adding bulk.
Waterproof and Windproof Outer Layer: Protects against rain, snow, and wind.
Conductive Threading: Allows me to channel EMP.
Heated Panels: Integrated heating elements providing adjustable warmth on demand.
Breathable and Moisture-Wicking: Keeps me dry and comfortable by drawing sweat away from the skin.
Adjustable Hood: Provides additional warmth and protection, and can be removed when not needed.
Multiple Pockets: Provides ample storage space for tools, gadgets, and personal items.
Reinforced Seams and Elbows: Enhances durability and provides extra protection in high-stress areas.
Reflective Elements: Increases visibility in low-light conditions, ensuring I can be seen by allies and avoid hazards.
Stealth Version:
Light-Absorbing Fabric: Reduces visibility by minimizing light reflection.
Sound-Dampening Fabric: Reduces noise generated by movement.
Minimalistic Design: Reduces the risk of snagging or catching on obstacles, ensuring smooth and silent movement.
Hood and Mask: Provides additional concealment.

+1 Brownie point if you read this whole thing :)
#bog is shifting#reality shifting#shiftblr#shifting#shifting realities#desired reality#reality shifter#reality shift#mha dr#mha#my hero academia#bogs mha dr
13 notes
·
View notes
Text
An endless parade of data breaches, brutally disruptive ransomware attacks, and crippling IT outages has somehow become the norm around the world. And in spite of escalating impacts to critical infrastructure and daily life, progress has been intermittent and often fleeting. Something's gotta give—and at the BSides Las Vegas security conference this week, a longtime critical-infrastructure security researcher is launching a project to communicate with utility operators, municipalities, and regular people in creative ways about both urgency and optimism around protecting critical infrastructure now.
Dubbed UnDisruptable27, the project will start as a pilot with a $700,000 grant for the first year through Craig Newmark Philanthropies' Cyber Civil Defense coalition. Led by Josh Corman, who was chief strategist for the US Cybersecurity and Infrastructure Security Agency's Covid Task Force, in collaboration with the Institute for Security and Technology (IST), the project will focus on the critical interdependence of water, food, emergency medical care, and power as the backbone of human safety. Corman says that the key goal is to foster new discourse about these challenges inspired by the disaster management tenets “inform, influence, inspire.” In other words, people need to understand the risks and feel empowered that they can take action.
“We are overdependent on undependable things. No one should feel comfortable with the potential for harm here with our current state of defense,” Corman told WIRED ahead of the announcement. “Our dependence on connected tech has grown faster than our ability to secure it. People have been doing good things, but public policy takes time, and I think this year we need to cross certain thresholds on the sense of urgency.”
One of Corman's main motivations to launch the effort as quickly as possible came from comments made during a January congressional hearing about the cybersecurity threat China poses to the US. In the hearing, then Cyber Command head and NSA director Paul Nakasone, Cybersecurity and Infrastructure Security Agency director Jen Easterly, FBI director Christopher Wray, and head of the Office of the National Cyber Director Harry Coker Jr. testified about pressing threats to US critical infrastructure, including specific campaigns the Chinese hacking group known as Volt Typhoon has been conducting to pre-position itself in US water infrastructure. The goal of this targeting is apparently to create leverage and a credible threat against the US as part of a Chinese plan to invade Taiwan, potentially in 2027.
“The budgets that emerge from discussions underway now will dictate what kind of resources we have ready in 2027, a year that, as this committee knows all too well, the CCP has circled on its calendar,” Wray told the US House of Representatives committee in January. “And that year will be on us before you know it. As I've described, the PRC is already today putting their pieces in place. I do not want those watching today to think we can't protect ourselves, but I do want the American people to know that we cannot afford to sleep on this danger.”
Having worked on embedded device security and critical infrastructure defense for years, including through the decade-old grassroots computer security and human safety initiative he founded known as I Am the Cavalry, Corman says that it felt significant that some of the nation's top intelligence officials were warning Congress of such specific threats to US infrastructure in an unclassified setting.
“It’s not just that the water goes out, it’s that when the sole wastewater facility in your community is down really bad things start to happen. For example, no water means no hospital,” he says. “I really encountered a lot of this during my leadership of the Covid Task Force. There is such interdependence across the basic functions of society.”
UnDisruptable27 will focus on interacting with communities who aren't reached by Washington, DC-based policy discussions or Information Sharing and Analysis Centers (ISACs), which are meant to represent each infrastructure sector of the US. The project aims to communicate directly with people who actually work on the ground in US critical infrastructure, and grapple together with the reality that cybersecurity-related disasters could impact their daily work.
“There’s a data breach, you get whatever services like identity protection for some period of time, and life carries on, and people think that there’s no long-term impact," says Megan Stifel, IST's chief strategy officer. “There’s this expectation that it’s fine, things will just continue. So we’re very interested in getting after this issue and thinking about how do we tackle critical infrastructure security with perhaps a new approach.”
Corman notes that even though cybersecurity incidents have become a well-known fact of life, business owners and infrastructure operators are often shaken and caught off guard when a cybersecurity incident actually affects them. Meanwhile, when government entities try to impose cybersecurity standards or become a partner on defense initiatives, communities often balk at the intrusion and perceived overreach. Last year, for example, the US Environmental Protection Agency was forced to rescind new cybersecurity guidelines for water systems after water companies and Republicans in Congress filed a lawsuit over the initiative.
“Time and time again, trade associations or lobbyists or owners and operators have an allergic reaction to oversight and say, ‘We prefer voluntary, we’re doing fine on our own,’” Corman says. “And they really are trying to do the right thing. But then also time and time again, people are just shocked that disruption could happen and feel very blindsided. So you can only conclude that the people who feel the pain of our failures are not included in the conversation. They deserve to understand the risks inherent in this level of connectivity. We’ve tried a lot of things, but we have not tried just leveling with people.”
UnDisruptable27 is launching this week for visibility among attendees at BSides as well as the other conferences, Black Hat and Defcon, that will run through Sunday in Las Vegas. Corman says that the goal is to combine the hacker mentality and, essentially, a call for volunteers with plans to work with creative collaborators on producing engaging content to fuel discourse and understanding. Information campaigns using memes and social media posts or moonshots like narrative podcasts and even reality TV are all on the table.
“We must prioritize the security, safety, and resilience of critical infrastructure—including water, health care facilities, and utilities," Craig Newmark, the Craigslist founder whose philanthropy is funding UnDisruptable27, told WIRED. "The urgency of this issue requires affecting human behavior through storytelling.”
10 notes
·
View notes
Text
Paige Bueckers Leak: What’s the Buzz

Ever heard the term “lightning in a bottle”? That's Paige Bueckers. This young basketball prodigy has taken the sports world by storm, dazzling fans with her incredible skills and charismatic presence. But recently, the buzz isn't just about her on-court prowess. Enter the "Paige Bueckers leak" – a phrase that’s been making waves online, leaving fans and followers both curious and concerned. So, what's the deal with this leak?
Who is Paige Bueckers?
Before we jump into the leak, let's get to know Paige Bueckers a bit better. Paige, born in 2001, is a name that’s quickly become synonymous with women's basketball. Hailing from Minnesota, she’s been making headlines since her high school days. Her talent was undeniable, and she soon found herself at the University of Connecticut (UConn), one of the most prestigious programs in women’s college basketball.
Achievements and Highlights
High School Superstar: Paige’s high school career was nothing short of spectacular. She racked up awards, including the Gatorade National Player of the Year.
UConn Stunner: At UConn, she continued to shine, earning the Associated Press Women’s College Basketball Player of the Year as a freshman.
Olympic Aspirations: She’s also been on the radar for future Olympic teams, representing the future of USA Basketball.
With such a meteoric rise, it’s no wonder any mention of Paige Bueckers, especially a “leak”, would grab attention. But what exactly is this leak about?
Unpacking the Paige Bueckers Leak
What’s Leaked?
Alright, so what’s the scoop? The term "Paige Bueckers leak" has been swirling around, but it’s a bit of a mixed bag. Here’s what’s been floating around:
Personal Information: There were whispers about personal details being leaked online, including phone numbers and private photos. Scary stuff, right?
Injury Reports: Another angle was the leak of sensitive medical information, particularly around injuries and rehab schedules.
Team Strategies: Some speculated that internal team strategies and communications from UConn were exposed.
The Impact
Leaks, especially of personal information, can be devastating. For Paige, who’s already under the intense scrutiny of the public eye, it’s even more challenging. Here’s how these leaks could potentially impact her:
Privacy Invasion: Having personal information out there is a huge invasion of privacy. It’s not just annoying; it’s potentially dangerous.
Professional Disruptions: Leaks about injuries or team strategies can affect her career. Competitors could exploit this info, and it might even influence her standing within the team.
Mental Toll: Let’s not forget the mental and emotional toll. Constantly being in the spotlight, especially under such circumstances, is tough.
How Did the Leak Happen?
Possible Sources
Leaks can happen from various sources, and in this digital age, it’s easier than ever. Here are a few potential culprits:
Hacking: Cybersecurity breaches are all too common. Hackers could’ve accessed personal accounts or devices.
Insider Threats: Sometimes, the leak comes from someone within the circle – an employee, a teammate, or even a friend.
Accidental Exposure: Not all leaks are malicious. Sometimes, information gets out by accident, through misplaced emails or lost devices.
Preventative Measures
While we can't change the past, there are steps that can be taken to prevent future leaks:
Stronger Cybersecurity: Investing in top-notch cybersecurity measures can help protect personal and professional information.
Trusted Inner Circle: Ensuring that only a trusted few have access to sensitive information can minimize risks.
Regular Monitoring: Keeping an eye on digital footprints and monitoring for potential breaches can catch issues early.
Public Reaction
The reaction to the Paige Bueckers leak has been a mix of outrage and support. Fans have rallied behind her, offering messages of encouragement and condemning the invasion of her privacy.
Social Media Outcry
Social media platforms lit up with hashtags and posts supporting Paige. Fans and fellow athletes alike voiced their concerns:
#ProtectPaige: This hashtag trended as fans demanded better protection for their favorite athlete.
Athlete Solidarity: Other athletes shared their own experiences with leaks, creating a broader conversation about privacy and security in sports.
Media Coverage
News outlets have also been quick to cover the story, with varying angles:
Sports News: Focused on how the leak could impact her upcoming season and her career trajectory.
Tech News: Explored the cybersecurity aspects and how such breaches occur.
Human Interest: Delved into the personal impact on Paige and her family.
FAQs
What exactly was leaked?
While the details are still murky, the leaks reportedly include personal information, injury reports, and potentially team strategies.
How has Paige responded?
Paige has maintained a relatively low profile regarding the leak, focusing on her recovery and preparation for the upcoming season. However, sources close to her have mentioned she's deeply affected by the invasion of her privacy.
What are her fans doing to support her?
Fans have been vocal on social media, using hashtags like #ProtectPaige to show their support. Many have also called for better protections for athletes’ personal information.
Could this affect her career?
Potentially. Leaks about injuries and team strategies could be exploited by competitors. However, Paige’s talent and resilience are likely to help her overcome these challenges.
What steps are being taken to prevent future leaks?
Stronger cybersecurity measures, a more trusted inner circle, and regular monitoring of digital footprints are some of the steps being considered to prevent future leaks.
Conclusion
The Paige Bueckers leak has been a stark reminder of the vulnerabilities that come with fame. For a young athlete already carrying the weight of immense expectations, this breach of privacy is yet another hurdle. However, if there’s one thing Paige has shown time and time again, it’s resilience. While the leak is an unfortunate incident, it also highlights the need for better protection and support for athletes in the digital age. Let’s rally behind Paige, not just as fans of her incredible talent, but as advocates for her right to privacy and security.
8 notes
·
View notes
Text
Unlocking Tomorrow: The Transformative Power of AI Apps
In the ever-evolving landscape of technology, Artificial Intelligence (AI) has emerged as a driving force, reshaping how we interact with applications across various domains. AI apps, powered by sophisticated algorithms and machine learning, are at the forefront of this technological revolution, offering innovative solutions that transcend traditional boundaries. Let's explore the transformative power of AI apps and their impact on our digital landscape.
The Essence of AI Apps
AI apps represent a fusion of cutting-edge technology and practical utility. They leverage the capabilities of artificial intelligence to provide intelligent, adaptive, and often predictive functionalities. From voice recognition to natural language processing, these apps go beyond conventional programming, enabling machines to learn and evolve based on data patterns.
1. Personal Assistants: Redefining Convenience
AI-driven personal assistants, such as Siri, Google Assistant, and Amazon's Alexa, have become integral parts of our daily lives. These apps leverage Natural Language Processing (NLP) to understand and respond to user queries, perform tasks, and even anticipate user needs. They transform our devices into proactive assistants, making information retrieval and task execution seamless.
2. Health and Wellness Apps: A Proactive Approach
AI is making significant strides in the healthcare sector through applications that prioritize prevention and personalization. Apps like Ada and Your.MD utilize AI to analyze symptoms, offer medical insights, and provide personalized health recommendations. These apps empower users to take a proactive approach to their well-being, offering a glimpse into the future of personalized healthcare.
3. Language Translation: Breaking Barriers
AI-driven language translation apps, like Google Translate, are breaking down language barriers. These apps use machine learning algorithms to understand and translate text in real-time. Whether you're traveling, communicating with global colleagues, or exploring content in different languages, these apps foster cross-cultural communication and understanding.
4. Financial Assistants: Smart Money Management
AI apps are transforming financial management by providing intelligent insights and assistance. Apps like Albert and Cleo analyze spending patterns, offer budgeting recommendations, and even automate savings. These virtual financial assistants leverage AI to understand user behaviors and provide personalized financial advice, empowering users to make informed decisions.
5. E-commerce Recommendations: Tailoring Experiences
AI is revolutionizing the e-commerce landscape with recommendation engines that enhance user experience. Apps like Amazon and Netflix analyze user behavior, preferences, and purchase history to offer personalized product and content recommendations. This not only improves user satisfaction but also contributes to increased engagement and revenue for businesses.
6. Image Recognition: Seeing Beyond the Surface
AI-powered image recognition apps, such as Google Lens, have taken visual interaction to new heights. These apps utilize deep learning algorithms to interpret and understand images. From identifying objects to providing information about landmarks, these apps augment our understanding of the world by adding a layer of intelligent visual recognition.
7. Educational Apps: Adaptive Learning
AI in education is paving the way for personalized, adaptive learning experiences. Apps like Duolingo and Khan Academy use AI algorithms to tailor lessons based on individual progress and learning styles. This not only enhances engagement but also maximizes the effectiveness of educational content delivery.
8. Cybersecurity Apps: Intelligent Protection
In the realm of cybersecurity, AI apps are playing a crucial role in identifying and mitigating threats. Apps like Darktrace employ machine learning to detect anomalous patterns and behaviors within networks, offering a proactive defense against cyber threats. These apps evolve alongside emerging threats, ensuring a dynamic and robust security infrastructure.
The Future of AI Apps
As AI continues to advance, the future of AI apps holds limitless possibilities. Enhanced natural language processing, improved decision-making capabilities, and greater integration with IoT devices are on the horizon. The synergy between AI and other emerging technologies is likely to result in even more sophisticated applications that redefine the boundaries of what is possible.
Challenges and Considerations
While the potential of AI apps is vast, it's crucial to consider ethical considerations and potential challenges. Issues related to data privacy, algorithmic bias, and the responsible use of AI are paramount. Developers and users alike must navigate these challenges to ensure the ethical and fair deployment of AI technologies.
Conclusion: Embracing the AI Revolution
AI apps represent a transformative force that is reshaping the way we interact with technology and information. From simplifying daily tasks to revolutionizing industries, these applications are at the forefront of innovation. As we embrace the AI revolution, it's essential to foster a responsible and ethical approach, ensuring that these powerful technologies contribute positively to our lives and the future of digital evolution. The transformative power of AI apps is not just in what they can do today but in the boundless potential they hold for tomorrow.
If you are an owner of an app and want to list it on the top of the list on our website, you can visit Mobileappdaily.
Content Source -
https://www.mobileappdaily.com/products/best-artificial-intelligence-apps
2 notes
·
View notes
Text
Closer to this actually:

You notice that your personal device was fine, because Crowdstrike only sells to businesses AND this update was only for Microsoft. It’s why trains were still running, and why I didn’t find out until I tried to buy ice cream. If you use linux or you aren’t a business, you weren’t directly affected. But if you notice, just that one bar falling down causes the entire top to collapse. The Crowdstrike boot loop affected just 1% of machines and made life fucking awful for so many people. I couldn’t get ice cream because I had only credit cards and $2 in cash on me at the time (I actually did have a $100 bill as well but they didn’t have enough change). The register couldn’t communicate with my credit card company and there was no lactose-free ice cream available that cost less than two dollars. The ATM was bluescreened and my bank’s computers too, so I had no way of getting more cash. So I put it back and went home, because I can live without ice cream. But what about people trying to buy groceries or pick up their medication? What about people in hospitals? They had to go home hungry and sick, if they weren’t also stranded hundreds of miles from home because flights were grounded. I have friends who are still stuck in Georgia! The conveniences of modern life rely on hundreds of single points of failure, and the worst part is Crowdstrike isn’t even going to see any penalties because it would cost more to replace them with a different cybersecurity firm. Things we need to survive require every single person employed at what are effective monopolies to do everything correctly. Remember the faux nuclear missile strike warning in Hawaii? People do not behave rationally 100% of the time. It’s why we’re human. This was a software issue, yes, but it wouldn’t have been so bad if individual companies were not in charge of the backbone of modern society, and the reason people are pissed is because it’s going to keep happening because it would cost too much to improve.
Sorry to rant on your post OP.
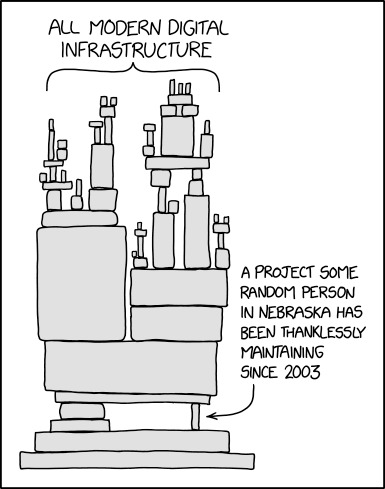
A global outage of IT systems worldwide because of one faulty software update?? Totally unpredictable.
26K notes
·
View notes
Text
The Bus, The Prices and Plot Twist, It’s Not Free
This month’s episode of “News You Can Use” on HealthcareNOWRadio features news from the month of September 2024 News You Can Use with your Hosts Dr Craig Joseph and Dr Nick van Terheyden The show that gives you a quick insight into the latest news, twists, turns and debacles going on in healthcare with my friend and co-host Craig Joseph, MD (@CraigJoseph) Chief Medical Officer at Nordic…
#Ask Me Anything#BigPharma#CompoundedDrugs#Cybersecurity#Digital Health#DigitalHealth#drugprices#education#Healthcare#Healthcare Reform#Healthcare Security#healthcarecosts#HealthcareReform#Incremental#Incremental Healthcare#IncrementalHealth#Innovation#Medical Devices#News#OzempicDebate#PatientPrivacy#pbms#PharmaLawsuits#PharmaTransparency#Ransomware#Security#Social Media#TheIncrementalist
0 notes
Text
US: A new law requires FDA submissions to demonstrate that medical devices fulfil cybersecurity standards

- By InnoNurse Staff -
The new law requires four basic cybersecurity standards to be included in all regulatory filings for medical devices.
For example, device manufacturers will now be required to submit a strategy describing how they intend to track and mitigate any vulnerabilities that may arise after their product is on the market.
Read more at Fierce Biotech
///
Other recent news and insights
AI demonstrates the necessity for better food in long-term care facilities (University of Waterloo)
#fda#cybersecurity#medical devices#medtech#health tech#ai#artificial intelligence#food#nutrition#diet#senior care#seniors#usa
0 notes
Text
What is Cybersecurity? Why is It Important?

What is Cybersecurity?
Cybersecurity refers to the practice of protecting systems, networks, and programs from digital attacks. These attacks can aim to:
Access: Steal sensitive information, such as personal data, financial records, and intellectual property.
Examples: Data breaches, identity theft, espionage.
Change: Modify or disrupt the functioning of systems and networks.
Examples: Malware infections, ransomware attacks, denial-of-service attacks.
Destroy: Cause damage to systems and data, rendering them unusable.
Examples: Data wiping, system sabotage, destruction of infrastructure.
Extort: Demand money from users or organizations through ransomware or other forms of extortion.
What is the Purpose of Cyber Attacks?
Cyberattacks can be motivated by various factors, including:
Financial Gain: Stealing financial information, extorting money through ransomware, or gaining unauthorized access to valuable data for financial profit.
Espionage: Stealing sensitive information, such as trade secrets, government secrets, or military intelligence.
Political Agendas: Disrupting critical infrastructure, spreading propaganda, or interfering with political processes.
Personal Vendetta: Attacking individuals or organizations for personal reasons, such as revenge or to cause disruption.
Hacktivism: Using cyberattacks to promote a social or political cause.
Importance of Cybersecurity:
Protecting Individuals: Safeguarding personal information like social security numbers, financial details, and medical records. Preventing identity theft and financial fraud. Protecting personal devices from malware and other threats.
Securing Businesses: Protecting critical business data and systems, ensuring business continuity. Maintaining customer trust and reputation. Complying with data privacy regulations (e.g., GDPR, CCPA).
Safeguarding National Security: Protecting critical infrastructure, such as power grids, transportation systems, and government networks. Countering cyberespionage and cyber warfare.
Disadvantages of Cybersecurity:
Cost: Implementing and maintaining robust cybersecurity measures can be expensive, requiring investments in technology, personnel, and training.
Complexity: The cybersecurity landscape is constantly evolving, making it challenging to keep up with the latest threats and vulnerabilities.
Skill Shortage: There is a global shortage of skilled cybersecurity professionals, making it difficult for organizations to find and retain 1 qualified talent.
5 Most Common Cyber Attacks:
Phishing: Social engineering attacks that trick users into revealing sensitive information (like passwords) by masquerading as legitimate entities.
Ransomware: Malware that encrypts a victim's files and demands a ransom payment for decryption.
Malware: Malicious software, such as viruses, worms, Trojans, and spyware, designed to harm computer systems.
Denial-of-Service (DoS) Attacks: Overwhelm a target system or network with traffic, making it unavailable to legitimate users.
Data Breaches: Unauthorized access to sensitive data, often resulting in the exposure of personal information, financial data, or intellectual property.
To gain a deeper understanding of cybersecurity concepts, best practices, and emerging threats, consider exploring programs like Xaltius Academy's Cybersecurity course. This comprehensive program can provide you with the necessary knowledge and skills to navigate the evolving cybersecurity landscape and protect yourself in the digital world.
0 notes
Text
High-Risk Smoldering Multiple Myeloma: The Critical Link Between MGUS and Multiple Myeloma

What is High-Risk Smoldering Multiple Myeloma?
High-risk smoldering multiple myeloma (HR-SMM) is an advanced precursor stage between monoclonal gammopathy of undetermined significance (MGUS) and active multiple myeloma. Patients diagnosed with HR-SMM have a significantly higher likelihood of developing symptomatic multiple myeloma within two years. Diagnosis is based on specific biomarkers, including abnormal plasma cell counts, elevated monoclonal protein levels, and genetic mutations. Early detection of HR-SMM is crucial, as it provides an opportunity to explore new treatments for HR-SMM that may slow disease progression.
Symptoms of Smoldering Multiple Myeloma
Unlike active multiple myeloma, smoldering multiple myeloma often presents no noticeable symptoms. However, some patients may experience mild signs such as fatigue, anemia, or occasional bone pain. Regular monitoring is essential to track disease development and determine the right time for intervention. While multiple myeloma remains incurable, early treatment strategies can delay its progression, and the risk of recurrence highlights the need for continuous observation of disease markers.
Advancements in Treating High-Risk Smoldering Multiple Myeloma
Traditionally, HR-SMM has been managed through active monitoring, but new treatments for HR-SMM are now being explored to slow or even prevent disease progression. Immunotherapy, particularly Revlimid-based regimens, has demonstrated promising results in clinical studies. Additionally, monoclonal antibodies and proteasome inhibitors like Carfilzomib are emerging as effective treatment options.
For eligible patients, multiple myeloma stem cell transplant remains a potential treatment strategy, offering extended remission and delaying disease advancement. Researchers are also developing innovative chemotherapy and targeted therapies to suppress disease progression. The multiple myeloma drugs market continues to expand, with cutting-edge treatments such as CAR-T cell therapy and novel therapeutic agents currently under investigation in clinical trials.
Conclusion
High-risk smoldering multiple myeloma represents a pivotal stage in disease progression, making early diagnosis and proactive intervention essential. The evolving multiple myeloma drugs market is driving the development of advanced therapies, providing patients with more options for disease management. With continuous monitoring, innovative treatments, and emerging medical breakthroughs, individuals with HR-SMM have a better chance of delaying the onset of active multiple myeloma and improving their long-term prognosis.
Latest Blogs by DelveInsight:
Pfizer’s ABRYSVO Outpaces GSK’s AREXVY with Expanded FDA Approval – But Can It Sustain the Momentum?
5 Promising Exosome-based Therapies Paving the Way for Personalized Medicine
FDA Grants Orphan Status to MDL-101 for LAMA2-CMD; Pfizer’s ABRYSVO Approved for High-Risk Adults (18-59); KIND’s AND017 Gains Orphan Designation for Sickle Cell Disease; HiberCell’s HC-7366 Fast-Tracked for AML; ORLYNVAH Approved for Uncomplicated UTIs
7 Key Technologies Pioneering Cybersecurity in the Healthcare Sector
About DelveInsight
DelveInsight is a leading provider of market research and consulting services specializing in the life sciences and healthcare industries. Our insights help pharmaceutical, biotechnology, and medical device companies navigate competitive landscapes and achieve long-term success.
Contact: Kanishk
Email: [email protected]
0 notes
Text
MULTI-FUNCTION DISPLAY MARKET : INNOVATION DRIVING NEXT GENERATION OF DISPLAYS
The Multi-Function Display (MFD) market is rapidly evolving, driven by advancements in display technology and increasing demand across various industries, including aerospace, defense, automotive, and consumer electronics. Multi-function displays consolidate multiple data sources into a single interactive screen, improving efficiency, situational awareness, and user experience. From cockpit displays in aircraft to modern vehicle dashboards and industrial control panels, MFDs are transforming the way information is presented and interacted with.
Market Growth and Trends
The global Multi-Function Display market is projected to experience steady growth, with a compound annual growth rate (CAGR) of around 7% from 2024 to 2030. Key trends contributing to this expansion include:
Increased Adoption in Aerospace and Defense: MFDs are extensively used in military and commercial aircraft to provide pilots with real-time flight data, navigation assistance, and system monitoring. The demand for advanced avionics systems is driving market growth.
Automotive Industry Integration: Modern vehicles are increasingly incorporating MFDs in dashboards, infotainment systems, and heads-up displays (HUDs) to enhance user interaction and safety. The rise of electric and autonomous vehicles is further fueling this trend.
Advancements in Display Technologies: OLED, AMOLED, and touchscreen innovations are making MFDs more versatile, responsive, and energy-efficient, leading to higher adoption rates across industries.
Growing Demand in Consumer Electronics and Industrial Applications: Beyond aerospace and automotive, MFDs are being used in gaming consoles, medical devices, and industrial control systems, expanding their market potential.
Market Challenges
Despite the positive outlook, the Multi-Function Display market faces some challenges:
High Development and Manufacturing Costs: Advanced display technologies require significant investment in research, development, and production, making MFDs costly for some industries.
Cybersecurity and Data Privacy Concerns: As MFDs become more connected, especially in aviation and automotive applications, ensuring security against cyber threats is a critical challenge.
Durability and Environmental Limitations: MFDs used in military, aerospace, and industrial applications must withstand extreme conditions such as high temperatures, humidity, and vibrations, posing challenges in design and durability.
Future Outlook
The future of the Multi-Function Display market looks promising, with technological advancements playing a crucial role in shaping its growth. Key developments include:
Enhanced AI and Machine Learning Integration: AI-driven MFDs will offer predictive analytics, voice recognition, and adaptive display functionalities, improving user interaction.
Expansion of Augmented Reality (AR) and Virtual Reality (VR): AR-based MFDs will become more common in aviation, automotive, and medical sectors, enhancing visualization and decision-making.
Development of Flexible and Transparent Displays: Innovations in flexible and transparent screens will open new possibilities for next-generation multi-function displays in various applications.
Conclusion
The Multi-Function Display market is on a steady growth trajectory, fueled by technological innovations and increasing demand across multiple sectors. While challenges such as high costs and cybersecurity risks persist, ongoing advancements in display technology, AI integration, and AR/VR applications will continue to drive market expansion. Industries that rely on real-time data visualization and enhanced user interaction will increasingly adopt MFDs, making them a key component of modern digital ecosystems.
Read More Insights @ https://www.snsinsider.com/reports/multi-function-display-market-5002
Contact Us:
Akash Anand – Head of Business Development & Strategy
Phone: +1-415-230-0044 (US) | +91-7798602273 (IND)
0 notes
Text
Telehealth Market Insights Investment Opportunities in the Expanding Digital Health Industry
The telehealth market has experienced exponential growth in recent years, fueled by advancements in technology, the global need for accessible healthcare, and changing regulatory policies. The COVID-19 pandemic accelerated the adoption of telemedicine, and now, the industry continues to expand as digital health solutions evolve. With a projected market value exceeding $300 billion by 2030, telehealth is revolutionizing healthcare delivery worldwide.

1. Increased Adoption of Remote Patient Monitoring (RPM)
Remote Patient Monitoring (RPM) has become a vital component of telehealth, allowing patients to track their health metrics from home. Devices such as blood pressure monitors, glucose sensors, and heart rate trackers help doctors provide real-time care. This trend is particularly significant for managing chronic diseases like diabetes, hypertension, and respiratory conditions.
2. AI and Big Data in Telehealth
Artificial Intelligence (AI) and Big Data analytics are driving telehealth innovation. AI-powered tools assist in early disease detection, automate medical imaging analysis, and enhance patient interactions through chatbots and virtual assistants. Big Data enables healthcare providers to analyze patient records, predict outbreaks, and optimize treatment plans for personalized care.
3. Wearable Technology Enhancing Virtual Care
Wearable devices are becoming an integral part of telehealth, with smartwatches, fitness trackers, and biosensors providing continuous health monitoring. Brands like Apple, Fitbit, and Garmin have integrated advanced features such as ECG monitoring, sleep tracking, and oxygen level detection, making remote healthcare more efficient and data-driven.
4. 5G Connectivity Powering Telemedicine
The rollout of 5G networks is significantly improving telehealth services by enabling high-speed, low-latency connections. This technology enhances video consultations, supports real-time data transfer, and facilitates remote robotic surgeries. 5G connectivity is particularly beneficial for rural and underserved areas, where healthcare access has been historically limited.
5. Growth of Virtual Mental Health Services
Mental health support has become a critical focus area in telehealth. Online therapy platforms, AI-driven mental health apps, and virtual counseling sessions are making mental healthcare more accessible. With increasing awareness and demand, virtual therapy is becoming a preferred solution for managing stress, anxiety, and depression.
6. Regulatory Shifts Supporting Digital Healthcare
Governments worldwide are introducing new policies to support telehealth expansion. In the U.S., Medicare and private insurers have expanded reimbursement for telemedicine services. Similarly, countries like China, India, and the UK are implementing digital health policies to encourage telemedicine adoption and integration into traditional healthcare systems.
7. Blockchain Technology for Secure Telehealth Solutions
Cybersecurity remains a major concern in telehealth, with sensitive patient data at risk. Blockchain technology is emerging as a solution to enhance security, ensuring encrypted, tamper-proof, and decentralized health data storage. Secure patient data sharing through blockchain minimizes fraud and protects privacy.
8. Emerging Markets Driving Telehealth Expansion
Developing regions in Asia, Africa, and Latin America are embracing telehealth as a cost-effective solution to healthcare challenges. With increased smartphone usage and internet access, telemedicine is bridging gaps in healthcare infrastructure, enabling remote diagnosis, prescription services, and digital consultations.
9. Challenges in Telehealth Implementation
Despite its rapid growth, the telehealth industry faces several challenges, including digital literacy gaps, regulatory inconsistencies, and technology accessibility. Additionally, resistance from healthcare providers and patients who prefer in-person visits remains an obstacle. Overcoming these barriers is essential for the long-term success of telehealth.
10. Future Outlook and Investment Opportunities
Telehealth is expected to see significant advancements, including AI-driven diagnostics, virtual reality-based treatments, and enhanced home healthcare solutions. Investors are increasingly funding telehealth startups, and companies focusing on AI-powered healthcare analytics, digital therapeutics, and telemedicine platforms are attracting major capital inflows.
Conclusion
Telehealth is redefining the healthcare landscape by making medical services more accessible, efficient, and data-driven. With continued advancements in AI, wearable technology, 5G, and cybersecurity solutions, the telehealth industry is poised for sustained growth. While challenges persist, the future of telehealth looks promising, offering vast opportunities for healthcare providers, investors, and patients worldwide.Telehealth Market Insights: Investment Opportunities in the Expanding Digital Health Industry
#Telehealth Market#Telehealth Market trends#Telehealth#Telehealth services#Telehealth communication#Telehealth treatment services#Telehealth Market innovations
0 notes