#malware protection force
Explore tagged Tumblr posts
Text

Actually did it! Two chapters in one year! Hope you enjoy these 33 pages under the cut and 2 reblogs!
CW for bodyhorror and mild gore
1/3











45 notes
·
View notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
In one case, Daniel, a Palestinian man who worked for the Catholic church, was threatened by an individual on Facebook who said he had evidence of his homosexuality. “we know that you are a f* you disgrace Christianity and Palestinians with your disgusting nature and I will expose you for what you really are,” the user wrote. “I’m gonna tell the whole world that you are gay and that you are a danger to the children of this society. you are disgusting and you will never get anywhere because I will stop you,” he added. Daniel said the only way someone could have known of his sexuality is if they had monitored his search history. (Drop Site News has changed his name to protect him from retaliation.)
Over the decades, numerous investigations have exposed how Israeli intelligence targets LGBTQ+ people. In 2013, Vice published an investigation detailing how the Palestinian Authority’s preventative security forces, under the direction of the IDF, had isolated gay Palestinians from their communities, kept files on them, and exploited them for intelligence. In 2015, news reports revealed that a surveillance technology company run by a former Unit 8200 official had helped provide Uganda with malware allegedly used against LGBTQ+ activists.
remember tho that israel is a safe haven for the gays
2K notes
·
View notes
Text
I missed drawing for my old WIR AU, so I came back to it for a bit!! Exploring the lore and the characters is just as fun as I remember it being.









Mini summary of the character lores and random tidbits under cut to remind myself, because I forgot everything :) I might revamp some of the lore as well.
The Turbo twins just barely managed to escape being unplugged along with their game after Turbo game jumped years ago. They survived, but homelessness for a game sprite is dangerous, since it implies a lack of protective anti-virus barrier their consoles would typically have offered them. The twins' raw codes were now completely exposed to external errant bugs, viruses, and other malware, which could prove to be fatal. So, they were stuck going around stations picking up odd jobs and services in exchange for temporary shelter in other games' consoles. But because of Turbo's actions and his disappearance, the twins' reputations were forced to take the full brunt of the arcade's backlash and scrutiny. This ruined their chances at a permanent home, not to mention the fact that letting an outsider stay too long in your game was considered very taboo at the time (especially with the whole game jumping scandal). Thus, they were stuck hopping from one game to another, never staying for longer than a few days at most.
- Felix and the Turbo trio knew each other before the Turbo incident :) He and the twins are still in contact after the incident, and he sometimes lets them stay in his game.
- Felix' in-game story is pretty much the same as Ralph's. There's still the stump, except that in the beginning of the game it's actually a full tree that Felix and his father used to care for before the latter died. The animation shows the bulldozer knocking it town to a stump to make space for Niceland, which basically is the whole opening of the game where Felix gets mad and wrecks the building, blah blah blah, you know the rest :)
- Felix used to be mistaken as the hero of his game a lot since he looked so small and unassuming. It annoyed him to no ends, because he despises having to talk to strangers.
#I know literally no one reads long posts with a lot of text but this is just for me!! <3#I still haven't figured out how Ralph & Felix' game is going to be called because nothing alliterates with Ralph that also means “fix”#I considered Repairman Ralph but that's a bit of a mouthfull#Anywho!! had a lot of fun drawing this- love making the lore#my art#wreck it ralph au#wreck it ralph#turbo wreck it ralph#turbotastic#fix it felix#fix it felix jr#wir au#wir#turbo wir#turbo twins#turbotime#turbo#HOW MANY TAGS DOES THIS MAN HAVE- HOLY FUCK#au lore#worldbuilding#I love worldbuilding- all my homies love worldbuilding
676 notes
·
View notes
Text

Widows rest
My take on a Black widow! Reader x Batman and Batfam but with a slight twist, reader doesn't know the Bats but they seem to know them...
Warning: contains avengers infinity war spoilers, black widow spoilers, mentions of death, hospitals, poor writing, possible ooc,
Part 7: recycled goods
🔹🔹🔹
“This is for you.”
Bruce drops a phone in your lap unprompted, he'd been in the middle of explaining his business ventures to you something about a rival company, Luthor something? when he paused and fished it out of his pocket.
Your brow quirks as you fish it out of the blankets and hold it up, it doesn't look brand new, the stickers on the back say as much. There's a yellow eagle insignia of some sort that reminds you a bit of Captain marvel, and a red S in a diamond, Both stickers are a bit lopsided and slightly worn around the edges.
“this is….” You glance at the man.
He's quick to supply the info. “It was yours, it is yours actually.” he leans forward and rests his elbows on the bed near your arm as he explains, you're slowly getting used to his comfortable he is getting close to you.
“I see…. What are these for?” You gesture at the stickers curiously, your expression betraying nothing but perfect contentedness and curiosity.
“That's-”
“that one's wonder woman, and that one's Superman.” Damian, who had been quietly doing schoolwork on the other side of your bed interrupts him, dropping his pen to point at the different symbols. You felt strange about the kid ever since the dream, not that you've shown it.
“Oh, those are the…. Justice Legends right?” From what you've gathered they're basically this worlds avengers, a team of superheroes squirm to protect the planet. Yada yada yada.
“Justice League, yeah. The oldest boys stuck those on there at some point.” Bruce quickly and gently corrects you before Damian can cut him off again, he looks a bit sad that you know so little, his lips pulling thin and his shoulders sag slightly. but he quickly shakes the look off and straightens up in his chair.
“TT, sloppy work too. I wouldn't have put them on wrong.” Damian scoffs as he glances at the phone in your hand, he's quite the little perfectionist it seems.
“It's just stickers, Dami.” Bruce's words make Damian grumble and roll his eyes, picking up his pen and resuming writing quietly.
They both leave when the nurse shows up to change your bedding, telling them visiting hours were over with a nervous air about her. The fact that everyone defers to the billionaire gets on your nerves.
🔹🔹🔹
You're on the rooftop again, still stuck in the damn wheelchair per doctors orders. You're not quite sure why you come up here of all places, probably the thought of all the cameras in the sitting lounges pisses you off, makes you feel even more cooped up than your windowless room does.
You're fiddling with the phone, first thing you'd noticed when you'd powered it on was the fact it was apparently Wayne tech. Going through it the second thing you noticed was that it was bugged. That sours your mood at first, but then it feels like a challenge to you. You've been decoding and planting and removing malware for longer than these fuckers have been alive, if you could encrypt Stark tech this will be easy.
It's engaging enough that you almost don't notice his appearance, his cape blowing in the wind as he balances on the ledge like he's Spider-Man or something. Fucking bat-man again.
“do you climb up here every night looking for me, or are you keeping tabs on me.” You don't look up from the phone as you call out to him, too engrossed in ruining the programs embedded in it.
“I climb a lot of buildings at night.” He mutters dryly, the forced deep tones still present as he slides off the ledge and walks closer like a normal person finally.
You glance up at him, you're still wary of the guy obviously, but so far he's behaved whenever he's appeared. “That's a weird way to get your cardio in.”
“It's more than cardio, I'm helping people.”
“Right, right. You're a part of the…. Justice Legends right? ‘saving the world one cosmic threat at a time’ yeah?”
“…yeah, I'm a part of them. What're you doing?” He glances down at the phone in your lap, obviously indicating what he means.
“going through my phone, or i suppose it's mine.” You shrug nonchalantly, glancing back down at the device. You scowl when you realize the spyware is updating itself, possible AI? or is someone actively resisting the bug removal remotely? You huff as you pick it up and go back to work on the device.
“where'd you get it from?” The caped hero presses on, leaning back against an AC unit And loosely crossing his arms in front of his chest.
“My husband, brought it in today while him and the young one were visiting. Mother-” you roll your eyes slightly as you find the stupid malware is layered, codes hidden within codes.
“problem?” He tilts his head, watching you scowl at the phone and getting worked up as you fiddle with it.
“It's fucking bugged, some creep could be watching me right now.” you assume that as a hero, he knows how annoying attempts to spy on your person are, anyone running around with his whole theme would probably never want to be watched. You smirk when you get one over on the mysterious thing trying to block your attempts, now this is environment enrichment.
“Bugged? As in tapped?” The bat themed man straightens up and stalks closer to you, squatting down beside you to watch you work.
You let him, at least he's not as touchy as your ‘family’. You just hum distractedly in response as you practically jab your fingers into your phone.
It's silent for a few moments, just the sound of wind and the distant ambiance of the city while you work on the phone and the man watches. he rests his elbows on the arm of your chair, eventually he breaks the silence (and your concentration.)
“You're good at this, real good…. Where'd you learn?” He tilts his masked head, there's a tension to him that wasn't there before. You're sure of that.
“Dunno, i just know it. Hey you know the people and the things worth knowing here, yeah? Tell me what this symbol is.” You see no need to tell him you learned this in Moscow, many years ago when you were still just a kid trying to survive. You turn the phone towards him and show him the picture on your phone, some kind of symbol from whatever is hacking your phone. A green circle with that appears to be the caricature of a woman's face.
He hums, grabbing your wrist to steady the phone. damn shaky limbs after a few seconds he releases you and shrugs, his elbows returning to the arm of your wheelchair.
“couldn't tell you, might be a private company thing…Do you want me to find out?”
“maybe, any idea why someone might spy on a random citizen?” As much as you're enjoying cracking this yourself, you don't like the thought of not covering your blind spots. Was it your family? Or did someone get access to the phone while in their possession? The thought makes the paranoid part of your subconscious itch, you'd throw the phone off the roof if it wasn't your direct tie to whoever's behind this.
“I've got a few ideas…. I'll look into it myself, don't panic, okay? I'll get back to you when I've got something.” He straightens up, stepping behind you to grab the handles of your chair as he starts to walk you back into the hospital.
🔹🔹🔹
Bruce is driving towards the GCPD, the bat symbol has been on for nearly ten minutes now and he's in a bit of a rush as he weaves through traffic. His notification system starts going off and he can already take a few guesses on this calling.
“B, thank God! you need to go check on operater right now they're-”
“they're fine, Oracle. I was just there. Everything's fine.” He interrupts quickly, she's probably been trying to reach him for a few moments.
“what? So it was you who wrecked my program then? Why the fu-”
He almost feels bad about interrupting her again. “It wasn't me, Oracle. I just….watched operater do it.” the line goes quiet for a beat, the only sound in the car is the low purr of the engines as he swerves around a garbage truck.
“…B, you and i both know operater can't do that.” Babs sounds confused, he can just picture her glaring at her monitor as she speaks slowly.
“…yeah, i know.”
🔹🔹🔹
M.list | prev |
A/n: sorry this one's a bit late! I'm not 100% happy with this chapter but I've had a migraine for a few days so this is what we've got 🥲
Taglist: @cxcilla @mercuryathens @dind1n @redsakura101 @ninihrtss @let-me-dance @ladykamos @one-piecelover
#dc x y/n#dc x reader#batman x reader#batfamily x reader#batman fanfiction#bruce wayne x reader#black widow reader
126 notes
·
View notes
Text
Murderbot Diaries Book Summaries
The release of the 7th book in the Murderbot Diaries series, System Collapse, approaches in November!
I've seen at least one person looking for a summary of past events... So I've made just that! If it's been a while since you read previous books (or you just like hopping into series half-way through), this will get you up to speed!

That said, this absolutely has spoilers, so if that's not your jam, turn away now.
====
Short Story – Compulsory: A recently-rogue Murderbot decides on a whim to rescue a miner who falls into a ventilation shaft. We see its developing love of Sanctuary Moon and what is implied to be the first time it violated its orders to protect someone.
All Systems Red (ASR):
Murderbot is the contractually-obligated security guard on a survey of "surprisingly nice" scientists. Dr. Mensah particularly impresses Murderbot for her level head and kind nature. It turns out their survey is being sabotaged by the cut-throat corporation GreyCris, who don't want them uncovering alien remnants. Murderbot and the scientists go back-and-forth protecting one another. The survey team discover that it's rogue. After some initial tension, they accept it as a team-member. They escape GreyCris, although Murderbot nearly dies in the process. When it wakes up again, the scientists have bought/freed it. In the name of self-actualization, Murderbot runs away.
Artificial Condition (AC): Murderbot sets off to investigate Ganaka Pit, the facility where it supposedly killed a large number of its own clients. On the way, it discovers the spaceship it's travelling on actually dangerously hyper-intelligent. After some initial threats/tension, the two bond over TV. The Asshole Research Transport (ART) helps disguise Murderbot as a human. With ART's help, Murderbot uncovers that the mass death was a tragic accident caused by ComfortUnit malware. Posing as a human, the pair help rescue a trio of researchers and their data from their shitty ex-boss, and set a ComfortUnit free.
Rogue Protocol (RP):
On an impromptu quest to get blackmail on GreyCris for Dr. Mensah's ongoing legal battle, Murderbot investigates an abandoned terraforming facility. It meets a cheerful robot named Miki who immediately declares themselves friends. Miki is helping a human assessment team who become imperiled when they're attacked both by CombatBots and their own double-dealing human security. Murderbot reflectively rescues them, posing as a Definitely Normal SecUnit, although the team's leader clearly sees through that claim. Murderbot manages to collect the intel on GrayCris and protect the humans, but not before Miki performs a heroic sacrifice.
Exit Strategy (ES):
After discovering Dr. Mensah has been kidnapped by GreyCris, Murderbot rushes to save her. This forces it to re-unite with the other survey members; Pin-Lee, Ratthi, and Gurathin. While unsure of each other, the team manage to rescue their friend. Murderbot attempts a self-destructive last-stand against a CombatSecUnit, only for the humans to save its ass. The team escapes on a company gunship, but not before Murderbot melts its brain fighting off killware. When it rebuilds its systems, it decides to stay with its humans in the Preservation Alliance for a while.
Short Story - Home, Range, Niche, Territory:
Shortly after Exit Strategy, Dr. Mensah reflects on her time in captivity and her new friendship with SecUnit. Apparently she's been avoiding getting treatment for her extensive emotional trauma. She has a panic attack when she's cornered by a journalist, who's scared off by Murderbot.
Fugitive Telemetry (FT): A human is found dead. Murderbot is called in as a consultant on the case, in the hopes of building good will with Preservation Security. Eventually it manages to prove itself, particularly after it succeeds in a daring rescue of kidnapped corporate refugees. One of the refugees realises it's a SecUnit and shoots it. The dead human turns out to have been a liberator of indentured labourers, and the killer was actually the Port Authority robot Balin, who was secretly a disguised CombatBot acting on outside orders. The local bot community intervenes to stop Balin from hurting anyone else.
Network Effect (NE):
Murderbot is providing security for a Preservation Alliance survey which goes south when raiders attack and try to take Dr. Mensah's brother-in-law, Thiago, hostage. It then goes doubly south when, on the way home, the team's ship gets attacked by... ART?
It appears that ART has been deleted and its crew has gone missing, replaced with mysterious grey people. While protecting a team of its humans, including Dr. Mensah's teenage daughter Amena, Murderbot manages to reboot ART. ART kills the grey humans but refuses to let everyone go until and unless they help it retrieve its crew. Everyone reluctantly agrees, but Murderbot is pissed.
Eventually Murderbot and ART make up. Then they create a sort-of-baby in the form of a killware copy of Murderbot who dubs itself Murderbot 2.0. Half of ART's missing crew is found on a local planet's surface, though Murderbot is captured while helping them escape. Murderbot 2.0 manages to rescue the other half from a spaceship with the help of the newly freed SecUnit 3. The local colonists are discovered to have gone a liiiiitttle bit kooky due to infection via an alien fungus. ART threatens to bomb their colony to get Murderbot back. Murderbot gets infected, but Murderbot 2.0 does a self-sacrificial attack to save it and destroy the fungi's primary host. Meanwhile, the humans, ART, and SecUnit 3 work together to rescue Murderbot without any more bloodshed.
Murderbot has a bit of an epiphany that all its various friends do in fact love and care for it. When an understandably pissed and confused Dr. Mensah shows up like a month later, the groups decide on forming a mutual partnership. Murderbot tells Dr. Mensah that it would like to work with ART for a little while.
#murderbot diaries#martha wells#system collapse#making a succinct yet understandable summary of Network Effect is HARD#i'll be reblogging to add a character sheet in like a day
148 notes
·
View notes
Text
Be Aware
Back in December, I got an email from someone claiming to be Team Cherry, the developers of Hollow Knight. This "marketing liason" was offering me early access to the sequel/expansion, Silksong, to review.
A friend with connections to the game press quickly pointed out that the real Team Cherry wasn't sending out early access review codes and that they were actually warning users about impersonators on their "Contact Us" form. The email I received was a scam from someone looking to infect me with malware and/or steal my identity. (I wrote a twitter thread about it here)
About a month later, as I was wrapping up work on my "Definitive way to Play Sonic Adventure 2" video, I received another email, this one claiming to be someone from Frontier Foundry asking to sponsor an upcoming video for the release of "Deliver Us Mars." I told them I already had a sponsor for the Sonic Adventure 2 video, and after I was done, I was planning on taking a holiday. They got weirdly pushy with me, saying I could "make a short video" and put the brand deal there. I was too busy finishing the video, so I ignored them and moved on.
Now another month later, I find myself finishing a quick little video and thinking about that Frontier Foundry offer again, but upon looking at it with fresh eyes, it also was a clear and obvious scam. Just like with the fake Team Cherry offer, the person isn't listed as an employee at Frontier Foundry, the email they sent the offer from seems to be a personal email address that doesn't match who they said they were, and the "Contract" they tried to force on me was a huge Google Drive zip file that was password protected to prevent me from seeing what was inside before I downloaded it. The fact that they were so pushy with me suddenly started making a lot more sense.
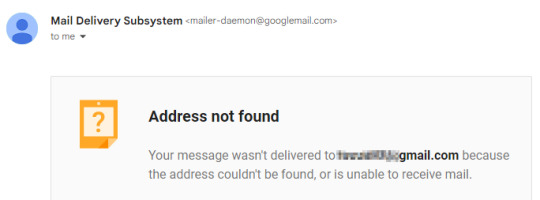
As icing on the cake, I tried to ask the person for proof of identity, and in the month+ since we last talked to each other, their email address has been forcibly closed by Gmail.
If you're an up-and-coming content creator, please be careful and be aware of tactics like this. It's easy to get starstruck by the idea that you're special enough to get picked for a sponsorship deal or an exclusive beta, but always research WHO is sending you that email and NEVER be afraid to ask for proof of identity. Go over their heads and check with the employer they claim to be from if you need to.
Be smart, protect yourself, and stay safe out there.
410 notes
·
View notes
Note
you have correct opinions about pearlina! but now i'm really sad about side order au
😇! i've been thinking about my au sooooo much since the dlc released. spoiler(?) under this
i decided that in my au i think marina created Order as some kind of like. malware. that she encrypted into whatever software she was using to control everyone's minds. but only put it in her system as an attempt to self-destruct herself (but didn't work)
and i quote this little thing i wrote for marina "never getting rest. chasing after a goal for so long it almost becomes a fantasy. asking for forgiveness and reassurance but no one is there. you are the one that created this fake reality, you are the one that forced everyone to believe what you believe in, it's your fault"
i think she's stuck in a loop just like agent 8. when she finally left the octarian army after being forced to mature at a young age and having her childhood stripped away, then meeting pearl and healing herself by bonding with him, only for it all to be ripped away from her in the blink of an eye
rescuing agent 8 in OE and wanting to protect them, but in SO she was too attached and let them out of her control system to give them freedom, unfortunately making them hate her. she doesn't know why. when she distances herself they pursue after her, when she tries to talk to them they back away
^_^
#splatoon#marina ida#pearl houzuki#off the hook#pearlina#side order#side order au#i hope this makes sense#i'm eating spicy food and i'm disoriented by the ceiling light
67 notes
·
View notes
Note
“Heartless. I’ll be watching until I deem it safe… or until Malware forces me to leave… I hope I’m not a bother.”
*He smiled softly. Not wanting to intrude but also protect Mal.*
"I'm sure Mal won't mind, he never asks for help but he appreciates it when it's offered"
7 notes
·
View notes
Text
About three years ago, some of Google’s security engineers came to company attorneys with a gigantic mess.
The security team had discovered that Google unwittingly was enabling the spread of malicious software known as Glupteba. The malware had corrupted more than 1 million Windows computers, turning them into vehicles to mine cryptocurrency and spy on users. By hijacking Google accounts, purchasing Google ads to lure in users, and misusing Google cloud tools, the hackers behind the operation were on their way to infecting even more computers.
Tech giants such as Google long have had a playbook for destroying botnets like Glupteba. They call up fellow companies and US authorities and together coordinate a massive takedown operation. Sometimes, the cops file criminal charges. But this time around, Google’s legal team recommended an approach that the company hadn���t pursued in years: Sue the hackers for money.
The eventual lawsuit against two Russian men and a dozen unnamed individuals allegedly behind Glupteba would be the first of a run of at least eight cases that Google has filed against various hackers and scammers, adding to a sporadic few filings in the past. The tactic, which Google calls affirmative litigation, is meant to scare off would-be fraudsters and generate public awareness about scams. Now, for the first time, Google is opening up about this strategy.
Leaders of Google’s security and legal teams tell WIRED they believe going after people in court has paid off. Google hasn’t yet lost a case; it has collected almost all of the more than $2 million that it has won through the legal process, and forced hundreds of companies or websites to shut down. The awards are trivial to Google and its parent Alphabet, a $2 trillion company, but can be devastating for the defendants.
“We’re disrupting bad actors and deterring future activity, because it’s clear that the consequences and the costs are high,” says Chester Day, lead of the three-person “litigation advance” team at Google that’s focused on taking people to court. Google, he adds, is “making it clear that we’re willing to invest our resources into taking action to protect our users.”
Google blog posts and similar content about the lawsuits and the underlying scams have drawn more than 1 billion views, according to the company. Google representatives say that the awareness increases vigilance among consumers and shrinks the pool of vulnerable targets. “Educating people about how these crimes work may be the best thing we can do to stop the crime,” says Harold Chun, director of Google’s security legal team.
Several Big Tech companies have pursued affirmative litigation, though not necessarily under that name and with varying strategies. Microsoft has filed more than two dozen lawsuits since 2008 with a focus on securing court permission to dismantle botnets and other hacking tools. Amazon has been a prolific complainant since 2018, filing at least 42 cases over counterfeit products, 38 for reviews fraud, three for copyright abuse, and, recently, two for bogus product returns. Amazon has been filing so many counterfeit cases, in fact, that the federal court in western Washington assigned three magistrate judges to focus on them.
Since 2019, Meta has filed at least seven counterfeiting or data theft cases, with settlements or default judgments in four so far, including one in which it won nearly $300,000 in damages. Like Meta, Apple has sued Israeli spyware developer NSO Group for alleged hacking. (NSO is fighting the lawsuits. Trials are scheduled for next year.)
Some attorneys who’ve studied how the private sector uses litigation to enforce the law are skeptical about the payoff for the plaintiffs. David Noll, a Rutgers University law professor and author of a forthcoming book on state-supported private enforcement, Vigilante Nation, says it’s difficult to imagine that companies could bring the volume of cases needed to significantly stop abuse. “The fact that there is a small chance you might be named in a suit isn’t really going to deter you,” he says.
Noll believes the big risk is that Google and other tech companies could be burdening the court system with cases that ultimately secure some favorable headlines but do less to make the internet safer than the companies could achieve through investing in better antifraud measures.
Still, of the six outside legal experts who spoke to WIRED, all of them say that overall Google deserves credit for complementing the work of underfunded government agencies that are struggling to rein in online abuse. At an estimated hundreds of thousands of dollars per case, it’s a low-risk endeavor for the tech giant, former prosecutors say.
“Reliable and regular enforcement when folks step outside the law brings us closer to a society where less of us are harmed,” says Kathleen Morris, resident scholar of law at UC Berkeley’s Institute of Governmental Studies. “This is healthy and robust collaboration on law enforcement by the public and private sectors.”
Google’s general counsel, Halimah DeLaine Prado, tells WIRED she wants to send a message to other companies that the corporate legal department can do more than be the team that says “no” to wild ideas. “Legal can be a proactive protector,” she says.
Marketing Scams
DeLaine Prado says that from its earliest days, Google has considered pursuing litigation against people abusing its platforms and intellectual property. But the first case she and other leaders within Google recall filing was in 2015. Google accused Local Lighthouse, a California marketing company, of placing robocalls to dupe small businesses into paying to improve their ranking in search results. Google alleged trademark infringement, unfair competition, and false advertising. As part of a settlement, Lighthouse stopped the problematic calls.
Since then, Google has filed complaints against five similar allegedly scammy marketers, with three of them ending in settlements so far. A Florida business and its owners agreed to pay Google $850,000, and a Los Angeles man who allegedly posted 14,000 fake reviews on Google Maps agreed to stop. Terms of the third deal, with an Illinois company, were not disclosed in court files, but Google spokesperson José Castañeda says it involved a seven-figure payment to Google.
Castañeda says Google has donated all the money it has collected to recipients such as the Better Business Bureau Institute, the National Consumers League, Partnership to End Addiction, Cybercrime Support Network, and various US chambers of commerce.
Another genre of cases has targeted individuals submitting false copyright complaints to Google to get content removed from the company’s services. A man in Omaha, Nebraska, whom Google accused of falsely claiming ownership of YouTube videos to extort money from their real owners, agreed to pay $25,000 to Google. Two individuals in Vietnam sued by Google never responded—a common issue.
In 2022, Google won default judgment against an individual in Cameroon who never responded to charges that he was using Gmail to scam people into paying for fake puppies, including a $700 basset hound. After the lawsuit, complaints about the scammer dried up, according to Google.
But legal experts say the most fascinating cases of Google’s affirmative litigation are four that it filed against alleged computer hackers. The suits emerged after months of investigation into Glupteba.
Security engineers at Google realized that eradicating Glupteba through the typical approach of taking down associated servers would be difficult. The hackers behind it had designed a backup system involving a blockchain that enabled Glupteba to resurrect itself and keep pilfering away.
That’s in part why Google’s attorneys suggested suing. Chun, the security legal director, had pursued cases against botnets as a federal prosecutor. “I thought this would be something good to do from a civil angle for a company as well,” he says. “Law enforcement agencies have limits on what they can do. And Google has a large voice and the litigation capacity.”
Chun and other attorneys cautioned their bosses that the hackers might use the lawsuit to reverse engineer Google’s investigation methods and make Glupteba more evasive and resilient. But ultimately, DeLaine Prado, who has final say over lawsuits, signed off. Chun says his former colleagues from the government applauded the complaint.
Google sued Dmitry Starovikov and Alexander Filippov, alleging that they were the Russia-based masterminds behind Glupteba after linking websites associated with the virus to Google accounts in their name. The search giant accused the duo (and unknown co-conspirators) of violating the Racketeer Influenced and Corrupt Organizations Act (RICO), the Computer Fraud and Abuse Act, and the Electronic Communications Privacy Act. The lawsuit also alleged a trademark law violation for hiding Glupteba in a tool that claimed to download videos from YouTube.
Google argued that it had suffered substantial harm, having never received payment for ads it had sold to the hackers, who allegedly were using fraudulent credit cards. Users also had their experiences with Google services degraded, putting them at risk and impairing the value of the company’s brand, according to the lawsuit.
In court papers, Starovikov and Filippov stated they learned of the lawsuit only through friends and then decided to hire a New York attorney, Igor Litvak, to fight on their behalf. The defendants initially offered innocent explanations for their software related to Glupteba and said that their projects had not targeted the US market. At one point, they countersued Google for $10 million, and at another, they allegedly demanded $1 million each to hand over the keys to shut down the botnet. They eventually denied the allegations against them.
Following an ordeal over whether the defendants could obtain Russian passports, sit for depositions in Europe, and turn over work files, Google’s attorneys and Litvak traded accusations of lying. In 2022, US district judge Denise Cote sided with Google. She found in a 48-page ruling that the defendants “intentionally withheld information” and “misrepresented their willingness and ability” to disclose it to “avoid liability and further profit” from Glupteba. “The record here is sufficient to find a willful attempt to defraud the Court,” Cote wrote.
Cote sanctioned Litvak, and he agreed to pay Google $250,000 in total through 2027 to settle. The jurist also ordered Starovikov and Filippov to pay nearly $526,000 combined to cover Google’s attorneys fees. Castañeda says Google has received payment from all three.
Litvak tells WIRED that he still disagrees with the judge's findings and that Russia’s strained relationship with the US may have weighed on whom the judge trusted. “It’s telling that after I filed a motion to reconsider, pointing out serious issues with the court’s decision, the court went back on its original decision and referred [the] case to mediation, which ended with … me not having to admit to doing anything wrong,” he says in an email.
Google’s Castañeda says the case achieved the intended effect: The Russian hackers stopped misusing Google services and shut down their marketplace for stolen logins, while the number of Glupteba-infected computers fell 78 percent.
Not every case delivers measurable results. Defendants in Google’s other three hacking cases haven’t responded to the accusations. That led to Google last year winning default judgment against three individuals in Pakistan accused of infecting more than 672,000 computers by masquerading malware as downloads of Google’s Chrome browser. Unopposed victories are also expected in the remaining cases, including one in which overseas app developers allegedly stole money through bogus investment apps and are being sued for violating YouTube Community Guidelines.
Royal Hansen, Google’s vice president for privacy, safety, and security engineering, says lawsuits that don’t result in defendants paying up or agreeing to stop the alleged misuse still can make alleged perpetrators’ lives more difficult. Google uses the rulings as evidence to persuade businesses such as banks and cloud providers to cut off the defendants. Other hackers might not want to work with them knowing they have been outed. Defendants also could be more cautious about crossing international borders and becoming newly subject to scrutiny from local authorities. “That’s a win as well,” Hansen says.
More to Come
These days, Google’s small litigation advance team meets about twice a week with other units across the company to discuss potential lawsuits. They weigh whether a case could set a helpful precedent to give extra teeth to Google’s policies or draw awareness to an emerging threat.
Team leader Day says that as Google has honed its process, filing cases has become more affordable. That should lead to more lawsuits each year, including some for the first time potentially filed outside the US or representing specific users who have been harmed, he says.
The tech giants' ever-sprawling empires leave no shortage of novel cases to pursue. Google’s sibling company Waymo recently adopted the affirmative litigation approach and sued two people who allegedly smashed and slashed its self-driving taxis. Microsoft, meanwhile, is weighing cases against people using generative AI technology for malicious or fraudulent purposes, says Steven Masada, assistant general counsel of the company’s Digital Crimes Unit.
The questions remain whether the increasing cadence of litigation has left cybercriminals any bit deterred and whether a broader range of internet companies will go on the legal offense.
Erin Bernstein, who runs the California office of Bradley Bernstein Sands, a law firm that helps governments pursue civil lawsuits, says she recently pitched a handful of companies across industries on doing their own affirmative litigation. Though none have accepted her offer, she’s optimistic. “It will be a growing area,” Bernstein says.
But Google’s DeLaine Prado hopes affirmative litigation eventually slows. “In a perfect world, this work would disappear over time if it’s successful,” she says. “I actually want to make sure that our success kind of makes us almost obsolete, at least as it relates to this type of work.”
10 notes
·
View notes
Text
Elevate Your Website’s Security with WordPress Security Services
Your WordPress website is a valuable asset that deserves top-tier protection. At Atcuality, we provide comprehensive WordPress security services to safeguard your site from cyberattacks and data breaches. Our team starts with an in-depth analysis of your website’s security framework, identifying and addressing vulnerabilities. We implement state-of-the-art measures such as malware scanning, brute force protection, and database encryption to enhance your site’s security posture. Additionally, we offer ongoing maintenance and support to ensure your site remains secure over time. With Atcuality, your website is not only protected but optimized for performance. Trust us to keep your digital assets safe and help you maintain a competitive edge in the online world.
#wordpress#website#web development#web design#web developing company#website development#web developers#ai generated#artificial intelligence#ai applications#iot#iot applications#iot development services#iotsolutions#iot platform#digitaltransformation#technologynews#techinnovation#augmented reality#augmented human c4 621#augmented and virtual reality market#augmented intelligence#metaverse#virtual reality#ar vr technology#amazon services#cloud server hosting#ssl#sslcertificate#ssl certificates
2 notes
·
View notes
Text

Glad i will never have to line this building again
6 notes
·
View notes
Text
I've been trying to figure out a concept for why Love and Idi got separated in the first place and I think i got somewhat of an idea
They were probably hunkering down in someone's computer for a while, A great place to settle. This user most likely didn't have really good security on their device, making it a gold mine of files for the two. Well, most of the files were going towards Loveletter. Idi doesn't have nearly as detrimental of a metabolism as she does- He could probably go a month or two without eating any substantial files if at all. For Love, she started to deteriorate a week or two without feeding. Sometimes if things got dire, She'd have to feed off of him, and she hated it. She hated being so needy.
He didn't mind it though- He completely understood. It wasn't her fault that she just happened to chew through code reserves so much quicker than he did. It's what had to happen to ensure both of their survivals.
There was one day however where someone who knew more about internet security and computer maintenance than the one who had owned the device. Probably was setting something up for them and realized how fucking slow and virus riddled the damn thing was. So they insisted they fix it up for them and run their own virus protection on the thing.
It was.... A really good Malware Defender. Probably a newer one the two hadn't seen before.
There most likely wasn't a really good opening for both to escape. It probably happened too fast for Love to process it. The damn thing was too fast, they could barely outrun it
Offiz had always been there to protect her in some way, So what's one last time?
Before it struck, Offiz pushed Love through the port with a duplicate of himself, forcing her to escape without him.
It's why she doesn't know if he survived or not. She didn't get to know.
3 notes
·
View notes
Text
Rockman.EXE and Cyber Security.

When you are a Rockman/Megaman Battle Network fan and you take a college course about networking, you start to notice how broken the internet is in the anime. So just for fun, I want to talk about a few things I learn about network security and how it is interpreted in the Megaman Battle Network anime.
1. Firewalls
What are firewalls? In simple terms, it is a security barrier that is placed between a private network and the public network.
They are configured to monitor and filter networking traffic, hackers go through them by figuring out how they are programed, once they do they can either bypass the security undetected or simply disable the firewall.
Lets take a scene from the movie where Lan sends Megaman into a secretary’s console to destroy a program inside a company’s server.

Megaman is running through the network between the console and the firewall, which protects the private network of the company.

Logically, for Megaman to go through the firewall, he is going to need to use his powers as a Net Navigator (Net Navi) to analyze the firewall at an incredible speed to try to find a way to go through it, right?
WRONG! Battle Network logic says you can just break it with brute force!
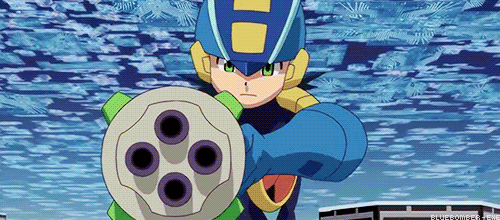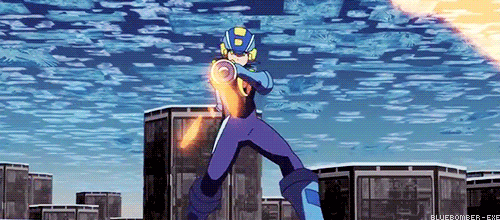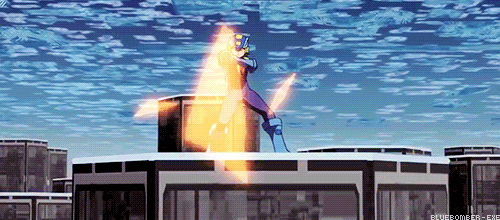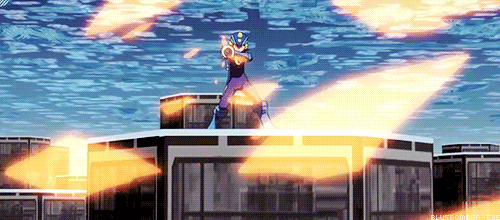

You see the problem?
Does this mean Navis and battle chips are just as destructive to the net as viruses? Because last time I checked, Viruses and malware are the only programs with the ability to destroy networks.
2. Viruses
Viruses are man made, they are programed with a purpose that’s usually to destroy data files. They can also be used to change and manipulate programs, that’s why you can see evil Navis controlling viruses to do specific jobs for them. Viruses can’t replicate on their own without a user interface, so how is this Moloko a baby?!

There was an undubbed episode of Megaman Axess where Rush meets and befriends a baby Moloko virus, which doesn’t make any sense. Yes, Rush is a virus, and it has been established that viruses can communicate with each other, but why does this Moloko have parents? And why was the group of Molokos it separated from was being herded by other viruses like Trumpy? All I’ve seen Molokos do is charge at megaman when they see him, trying to ram him. Why would someone herd them? For the wool? It disappears after you hit it!
And what even is Rush’s purpose anyway? When he first appeared in the anime, he was made to track down Rockman’s frame or structure when they were trying to revive him with the backup data, but now?
All he does is being a crappy character who runs away when things get dangerous, doesn’t act like a dog anymore, and irritates me because he can move between the cyberworld and the real world! He is selfish, lacy, and practically useless, there are several times where Megaman goes missing and Rush is never even called to track him down, so he doesn’t even have that ability anymore.
On a positive note, viruses can be interesting, I found out that there are different types of viruses. For example.
A Stealth virus is a virus that avoids detection from anti virus software, this means it can conceal itself and attack without being spotted, sounds familiar? In this case the anti-virus software would also include Navis.
A retro virus tries to destroy anti-virus programs, I like to think these apply to viruses who specifically target Navis in battle like Canodumbs and Piranahs since they only attack when they detect an enemy in the line of fire.
Armored Viruses are hard to detect or analyze because they have a protective code, These could be Viruses with armors or auras like the Dominerd or even the life virus.
But Phage viruses remind me of these guys because they rewrite programs.

And I guess this one counts too?

Other viruses just act like malware, like the Alpha bug that is more of a worm than a virus, because it can replicate and travel across networks without any human assistance.
Others are obvious like the Pop up virus which is just Rush, and it is supposed to be adware, but just like Rush, it is more annoying than harmful.
In the anime, killereye viruses are used as spyware, there was an episode were Videoman used them to spy on Rockman and make copies of him.

3. Tracing a signal.
Basically, everything you do on the net leaves bread crumps or cookies behind that makes it easy to track a user online, every device have a Mac Address and every network has an IP address, but it takes a special kind of software and advance skills to track down somebody in the real world.
Let’s talk about episode 32 of Stream.
Remember that episode were Megaman followed a revived Shademan to 20 Years in the past and he witnessed a famous hacking incident that was stopped by Colonel?

Aside from the fact that it was 20 years in the past and Megaman is more advance than most of the technology there, there were a few things bothering me.
For starters, why does that computer show a little Colonel doing something to that guy’s hacking program? It’s cute and all, but this is a confusing way to show someone disabling a program, it usually just shows a notification. Or is that how the computer sees colonel, like a little pixel version of him? XD
That hacking program was made to open any cyber lock, it uses three special pillars to disguise the signal so the police wouldn’t be able to track down the address, this means those pillars have some special form of encryption to cover the data to make it untraceable. In the anime’s world, that means it’s invisible, but somehow Megaman can still sense it? And how did Barryl know where the guy was? Did colonel tell him? Or did the viruses he sent to delete colonel revealed his location? Oops.
4. Hard Drives.
To end this post, what are hard drives? They are what your computer uses to store files, so Navis can obviously be stored in a computer as well. The problem is that they are still sentient inside the computer instead of dormant.
The concept of containing a Navi, yes, Navis have their own jail in this universe, doesn’t really make any sense. We know Navis can sleep, but the Navis we see in cages are still active, and if everything is connected to the internet, how can they not escape?
I’m using this scene with Megaman as an example, when he was arrested for being in the wrong place at the wrong time, he was put in a cute little cyber cage.

However, since Megaman is more advance, he wonders if the hard drive of the computer he is stored in is weak against vibrations. What does he mean by that? Physical or cyber vibrations? Does that mean he can control a frequency in that computer’s cyberworld to alter it?
Whatever he did worked, because he left a gap in the cage, but how did he do it without damaging the Hard Drive? The police officer wouldn’t be able to access his files anymore, maybe it was minor file corruption?
And the worst part is that he opened a gateway into the internet, which is still there! I guess Megaman can travel through routers by himself? Maybe that wouldn’t have happen if the officer just disconnected his ethernet cable.
This Network based world is a scary one.
48 notes
·
View notes
Text
How VPS Hosting Enhances Website Security and Reliability

When it comes to hosting a website, one of the most important factors to consider is security and reliability. Ensuring that your website runs smoothly without interruptions or security breaches is crucial, especially if your website deals with sensitive data or provides services that rely on uptime. Virtual Private Server (VPS) hosting is an excellent choice for enhancing both website security and reliability. Unlike shared hosting, where resources are shared among multiple websites, VPS hosting offers a dedicated environment for your website, providing more control, customization, and better overall performance.
Enhanced Security with VPS Hosting
Security is a major concern for website owners, as cyber-attacks and hacking attempts can result in data breaches, loss of sensitive information, and even financial damage. VPS hosting offers several key advantages in securing your website.
Isolation from Other Users: With VPS hosting, your website is hosted on a virtual server that is isolated from other users. This means that your website is not affected by the activities of other websites hosted on the same physical server, which is often the case in shared hosting environments. In shared hosting, if one website experiences a security issue, it can impact other websites on the same server. With VPS, the virtual environment ensures that your website is protected from such vulnerabilities.
Customizable Security Features: VPS hosting gives you more control over your server’s security settings. You can install custom firewalls, anti-virus software, and intrusion detection systems that are tailored to your specific needs. This customization enables you to apply security patches promptly, mitigate vulnerabilities, and protect against various threats such as DDoS attacks, malware, and brute force attempts.
Root Access for Greater Control: VPS hosting typically provides root or administrative access to your server, allowing you to configure security settings at a deeper level. This control means that you can implement advanced security measures, such as disabling unnecessary services, configuring SSL certificates, and setting up access restrictions. It empowers you to take proactive steps to defend your website.

Reliability and Performance with VPS Hosting
In addition to security, VPS hosting also significantly enhances the reliability and performance of your website.
Dedicated Resources: Unlike shared hosting, where resources like CPU, RAM, and bandwidth are shared with other websites, VPS hosting provides dedicated resources. This ensures that your website has the necessary computing power to run smoothly, even during traffic spikes. Dedicated resources mean fewer slowdowns and better overall performance, leading to a more reliable user experience.
Better Uptime and Stability: VPS hosting offers a higher level of uptime compared to shared hosting. Since your website is hosted on a virtual server with dedicated resources, it’s less likely to experience downtime due to the actions of other users. Many VPS providers also offer service level agreements (SLAs) guaranteeing uptime, ensuring that your website remains available to users.
Scalability: As your website grows, it’s essential to have hosting that can scale to accommodate increased traffic and resource demands. VPS hosting offers easy scalability, allowing you to upgrade your resources as needed without experiencing downtime or interruptions. This scalability ensures that your website can handle growth without compromising performance.

Why Choose Initsky for Your VPS Hosting Needs?
For website owners looking for the best in VPS hosting, Initsky is a top-rated VPS provider. With Initsky, you get access to robust security features, reliable performance, and scalable hosting solutions. The platform offers managed VPS hosting, ensuring that your server is properly configured and maintained, so you can focus on running your website instead of managing technical aspects. Initsky also offers excellent customer support, 24/7 availability, and a variety of customizable plans to suit your needs.
In conclusion, VPS hosting is a powerful solution for enhancing both the security and reliability of your website. By providing dedicated resources, greater control, and advanced security features, VPS hosting ensures that your website runs smoothly and securely. For top-rated VPS hosting with unmatched support and scalability, consider Initsky for your hosting needs.
2 notes
·
View notes
Text
-Ben 101 Rewrite Note-
Similar to Ben, there are many alternate versions of his main villain, Vilgax. Here are the versions other Bens have encountered in their own stories.
Gwen 10 Timeline - Fairly much the same as his Prime counterpart, but instead has his aggression towards Gwen. He sees her as a foolish kid that acts like she knows everything, and believes her intelligence means nothing.
Ben 23 Timeline - The reason why Ben 23 never encountered his Vilgax in his early days is because his version is actually just taking care of his Empire. He rules his Kingdom and other planets and is simply a busy man, having not lost sight of his ways in this timeline. They eventually meet, though don’t get along at first (Mostly for different reasons to the prime timeline).
Ben 10k Timeline - Had been killed by Ben 10k a long while ago, during an incident where Vilgax got Grandpa Max killed. It’s not an event that Ben likes to talk about.
No Watch Timeline - Since there was no Omnitrix, Vilgax kept all his focus on conquering other planets like before, actually having progressed further than his prime counterpart. By the time No Watch Ben becomes a Plumber, he’s a well known foe of the galaxy that he will eventually encounter.
Omni Ben Timeline - His aggression towards Ben in this timeline is more so an obsession towards the fact that Ben himself is the watch. He doesn’t view Ben as a person, but still the tool he was once designed to be, and doesn’t believe he is capable of being more.
Jen 10 Timeline - The same as his prime counterpart, but now a female called Viragax. Still being a warlord conquer, being Jen’s nemesis.
Julie 10 Timeline - Vilgax made his debut when he was found to be working with the Highbreed around the time Julie got the watch. He made agreements with them, but still wants the omnitrix. Ben had run into him a few times before Julie got involved, so he’s already not fond of this version of Ben.
Sentient Omnitrix & Ben Timeline - He’s fairly similar to the prime timeline, though he lost his entire arm to the Omnitrix when she snapped after Ben nearly died to him, the entire thing now replaced by a cyborg arm, and learning to be careful around the now sentient watch.
Rooters Ben Timeline - Very much dead, as Ben had been on a mission earlier on and made a call to kill him, having gone directly against orders that day. His kingdom now has the issue of a sudden dead ruler, and having no back up, something Ben does admit to regret being so hasty on.
Eon Timeline - Also dead, but that’s because everyone in this timeline is dead besides Eon.
Bad Ben Timeline - A loving, kind and wise king, doing his best to protect his people, and get the Omnitrix away from Ben, feeling he is using it for all the wrong reasons. Mostly just seems a little tired of all the chaos around him.
Mad Ben Timeline - Being a very successful warlord, who has destroyed the Plumbers years ago, took over earth, killed Ben’s entire family in secret, and then took the young child under his wing. He was in a state of power where he felt he didn’t need the watch, so he was fine leaving it in Ben’s hands, planning to make the boy his heir if anything were to happen to him. A very cold, calculating Vilgax, much more so than his prime counterpart.
Negative Ben Timeline - Never became king in his timeline, and thus could not free his people. So he became a space nomad, wandering the galaxy in an effort to find a way to help his people, denying help from the Plumbers who he think are corrupt, leading to many situation with Ben, who he very much pities.
Benzarro Timeline - Given Zs’Skayr’s rise in power, slowly taking over the entire galaxy, it somewhat snapped Vilgax out of his obsession towards Ben and the watch, leading to him joining forces with other to counter Zs’Skayr over the years, even if Vilgax is still a rather unpleasant person.
Malware Ben Timeline - Sort of now competing villains, though Ben does it out of survival mostly. Vilgax loves to taunt him and what he’s become, though still wants the omnitrix, even if it means now he has to also deal with Malware.
Forever Knight Ben Timeline - Has an ongoing war with Ben and the Forever Knights, with both not being better than the other, seeking power and resources to be better than the other. Though he does admit he is a little disturbed by Ben’s views of alien life.
Fusion Ben Timeline - On the hunt to find the wild fusion, having hired many people to try and seek him out, or capture him. Like Khyber, Sunder or SixSix. As if Ben is a wild animal he’s trying to trap, still seeking out the watch.
Ultra Ben Timeline - Ended up being killed by Ultra Ben, right after Kevin’s death, when Ben came to the realisation that he needed to protect the galaxy by being ruthless and powerful. The similarities didn’t go unnoticed on Vilgax, one of his last comments he ever made to Ben.
Light Magic Ben Timeline - A rogue member of Dagon’s cult, having been mutated by his magic. He wishes to take over his ex-master’s role and power, and is trying to become the King of Ledgerdomain, since it is the galaxy instead of the milky way in this timeline. Often comes into conflict with the corrupted Ben, being very much opposites in their ways of control.
#ben 10#ben 101#b10#ben 101 note#ben 101 au#ben 101 rewrite#ben 10 original series#ben 10 omniverse#ben 10 ultimate alien#ben 10 alien force#Ben 10 AU#Ben 10 Vilgax
42 notes
·
View notes