#like data privacy and misinformation
Explore tagged Tumblr posts
Text
Perhaps this is the bipartisan issue we have been looking for? People of all backgrounds giving the finger to AI fetishists and tech bros?
#ai art is not art#wga strong#sag aftra#also im fully aware of other issues with ai#like data privacy and misinformation#this just happens to be the more personal one to me#and will fully advocate for strict AI regulations#and expanded copyright laws protecting IPs from ai#ai artwork#ai#ai art
5 notes
·
View notes
Text
About Account Closures, Banxiety, etc
Good morning, Flight Rising Tumblr!
I posted a reblog not that long ago (this morning) responding to banxiety concerns. It appears to have been eaten by Tumblr, which happens; but I know a lot of you are concerned and there's a lot of misinformation and misunderstandings flying about. So I'm going to go ahead and repost this directly to the tags so anyone with concerns or anxiety can see this <3 (06:47 Flight Rising server time: Title edited to be clearer.)
—————
Oh dear, there's been quite a misunderstanding. What you've described here isn't true and likely to send our players into a banxiety panic. I'm sure that's not what you meant to do and I'm happy to clarify where I can!
We're fully aware people can change physical locations throughout the day which means their IPs will change. Some folks play or check in from home, school, work, a friend's house, etc. That means their account will log multiple IP addresses on any given day, sometimes within a thirty minute period.
Example: Player accesses on their school network —> School lets out —> They access via mobile data on transit —> Player then logs in on their home network
Closing accounts for having multiple IP addresses associated with them—especially in the mobile era!—would be wrong. And, frankly, absurd.
Account closures are based on activity data and reviewed by staff. Do we always get it 100% right? No, of course not. We're human. We make mistakes. Sometimes we do close an account in error and upon review, reopen the account. And sometimes it even means an account we're almost certain is cheating stays open a bit longer, because of that chance we're wrong.
Unless by "moving stuff over" you mean funneling to a new account, because our Terms of Use are clear that players agree to register only one account per individual. Multiple accounts provide a player not only with multiple opportunities for dailies and Roundsey, but access to various Flight Forums (including private Flight Dominance planning!) not just their original Flight, ways around our block feature, and the means to scam players during trades, giveaways, etc. The above ranges from cheating and gaining an advantage over others to outright harassment.
Now, there is also friend and family member funneling, where someone stops playing for themselves and just starts sending the earnings from their dailies or festivals to their friend or family member. That's still cheating and we've been clear about that for some time now.
Finally, we don't discuss account actions with third-parties and we don't discuss them publicly for privacy, security, and safety reasons. Even when the player who lost their account takes to the forums or social media with claims that are untrue, exaggerated, or minimize/downplay the violation that lead to the closure of their account. Unless they've taken the extra step to alter a screenshot as "proof" we said or did something we didn't do, we can't engage with their claims. This means the community will only see one side of the story, one version of events.
And as a note for anyone following along and concerned about their account, we do have an article in our Knowledge Base that explains account penalties: Account Penalties Explained.
I hope this helps clarify the confusion and concerns surrounding account closures! You don't have to worry about logging multiple IPs, moving, playing with your friends or family, etc. <3
207 notes
·
View notes
Note
AO3 hasn't changed much (if anything) in their privacy policy when it comes to personal data processing. They've just made clearer to users that their servers are in the US, and as such are subject to US privacy laws regardless of the user's personal location. If anything, this change is to help all users be safer and make informed decisions to protect themselves. If you're concerned about what data AO3 collects, it's all the same as it always has been, and it's outlined in the policy. It's important not to spread misinformation and incite panic about this change just because of a lack of understanding.
i went ahead and deleted my post and i do apologize for posting in the middle of me reading the policy instead of at the end, that is on me!! i should've been clearer about that when i was posting but i was honestly just Irritated
so sorry if i freaked you out folks, ao3 will be fine (for a bit.) and nothing they are collecting is changed
my concern is mostly that they are making this tos change in response to decisions about censorship that haven't happened yet which means the site will likely be shuttered when that shift comes things will likely be wiped completely in a similar way to ff.net
22 notes
·
View notes
Text
Alright, Let's talk
I've had some time to digest everything about the election and hearing all the talk surrounding it. I was, and am devistated as to where things stand now for a Trump presidency. However... My gut tells me this is not over. Whether that means election fraud or tampering, boycotts and protests, or more legal trouble for the big orange. It's not over. Things are far too quiet, and we are in the eye before the storm. Notice how EXTREMELY quiet Trump is this time around. He hasn't been boasting and gloating and unsufferably hard to ignore. There is something going on, and I think he is very nervous.
However. That does not erase the threat of everything Trump stands for. If anything, this has shown us the threat in front of us. My family is Polish, I have grown up Polish. Why is that relavant? Talk about world war two was almost a constant growing up. Most people associate Poles with WW2 anyway, so I learned a lot. I learned a lot about facism, nazis, eugenics, and the psychology of complacancy that led to the holocaust.
Around 2016, at the fresh age of 14, my mother and I went to the Zekelman Holocaust Museum in Michigan. I urge you too look at or read about some of their exhibits here. This is where my mother and I were first able to completely face the fact of what Trump was doing. There was an exhibit showcasing the 10 stages of genocide. We are now currently at stage 7. Project 2024 has thrust us there. I worry deeply about what project 2024 has shown us. What that means for every single women, the LGBTQ+ community, our immigrant communities, our disabled communities.
Even if there is no internment camps like in the holocaust, I worry about escalations. I am terrified of history repeating. I refuse to be complacant in that, and I urge you not to be as well. I urge you to prepare for the worst, but hope for the best. Be proactive in measures for the future.
Especially if you are a woman, I am telling you to buy Plan B now. Travel state lines if you have to. Plan B has a shelf life of 4 years. If not for yourself, do it for a friend, family member, or someone you care about. Even if you are not sexually active, you never know what is going to happen or who might need it.
If you have any period tracking apps, they need to go NOW. Flood it with misinformation if you are able, change past entries before you delete it. Stick to putting that information to pen-and-paper where your data will not be taken by the government and used agaisnt you.
If you are able to, please apply for a passport or renew yours if you haven't already, the sooner the better. It can take a lot of time for them to get processed, so do this first. If you are financially unable to pay for a passport, you may be eligable to apply with a fee waiver. In case you feel unsafe and just want to leave the country for whatever reason may happen, I feel it is extremely important to have.
Download Signal. It has end-to-end encryption that will keep you and those same people you care about safe. I also suggest turning off notification previews even on apps like Signal, as I am told that they can be un-encrypted. If you value your privacy for conversations with your trusted people, you need to do it on something that is end-to-end encrypted.
If you are able and feel safe to, build a community network. Anyone you believe can be trusted, talk to them now about your fears and come up with a plan for worst-case scenerios. Reach out to others that have the same fears as you. Talk to your trusted friends and family members. You are not powerless. You have strength in numbers. If not to help you feel safety, but to give you hope and laughter in hard times. It does not and will not mean that the world is not dire, but you need to still stay sane.
Save important doccuments now. Not on pinterest or in a TikTok bookmark. Download. That. Shit. Don't have the computer space? Get a hard drive. A USB. Fuck it, a CD. Can't download important information? Write it down on physical paper. You have options. Even if it doesn't get taken offline, archiving and saving important things is extremely important anyway. Anything important to you, save. I am worried about books and important information being lost. Get physical copies if you are able. Find ways to download them in PDF or similar formats. Music? Save it. Maybe I'm being too wary, but you will have no idea what is going to go until they start doing it.
#ivy talks#im sure there is more i have missed and i may add to this#but this is the most important things that have been brewing in my mind#2024 presidential election
26 notes
·
View notes
Text
There is much concern that Elon Musk’s Starlink intends to provide satellite internet coverage to the United States following the failure of its Red Sea “Operation Prosperity Guardian” alliance to curb Yemen’s pro-Palestinian front.
This conversation has gained traction since the company’s announcement on 18 September that it would launch services in Yemen after months of informal contracts with the Saudi-backed government in Aden. The timing of this announcement raised eyebrows, especially as it coincided with Israel’s terrorist attacks in Lebanon, involving exploding pagers and walkie-talkies.
[...]
The announcement that Yemen would be the first country in West Asia to have full access to its services surprised many – particularly because the US embassy in Yemen was quick to praise the move as an “achievement” that could unlock new opportunities.
[...]
The rival Sanaa government, under which most of Yemen’s population lives, was quick to warn that the Starlink project may threaten Yemen and its national security. Mohammed al-Bukhaiti, a member of Ansarallah’s political bureau, criticized the US embassy’s stance, which he says:
"Confirms the relationship between the launch of Starlink and the war launched by America on Yemen, which threatens to expand the conflict to the orbits of outer space for the first time in history."
[...]
In March, the Financial Times reported that the US and UK faced intelligence shortfalls in their Red Sea campaign, particularly around the capabilities of the Ansarallah-aligned forces’ arsenal. This intelligence gap underlined the west’s need for a reliable spy network, and Starlink’s role in this context raises serious questions.
A Reuters report revealed that SpaceX had signed secret contracts with the US Department of Defense aimed at developing a spy satellite system capable of detecting global threats in real-time.
[...]
Another concerning aspect is the involvement of Israel. Israel’s spy satellites, OFEK-13 and OFEK-14, are reportedly linked to Starlink’s satellite network. SpaceX, as a third party, may provide critical guidance and intelligence to these satellites, further enhancing Tel Aviv’s surveillance capabilities in the region. This connection between Starlink and Israeli intelligence efforts has heightened fears in Yemen that the satellite network will be used to undermine the country’s security and sovereignty.
Currently, Starlink services are available primarily in Yemeni areas controlled by the Saudi and UAE-led coalition, although roaming packages allow temporary access in other regions. This has prompted concerns about data security, privacy, and the spread of misinformation, as unrestricted satellite internet bypasses local government control.
[...]
Moreover, cybersecurity risks are particularly troubling, as the network might be exploited for dangerous purposes, including facilitating terrorist activities like bombings. The presence of a global satellite internet service that bypasses local regulations raises concerns about its potential to disrupt local internet infrastructure.
Starlink could also introduce unfair competition to local provider Yemen Net, further marginalizing the national telecom provider and hindering local development efforts.
[...]
Dr Youssef al-Hadri, a right-wing political affairs researcher, shared his views with The Cradle on the recent events in Lebanon and the ongoing electronic warfare involving the US and its allies. According to Hadri, intelligence agencies operating in areas under the control of the Sanaa government face challenges in detecting the locations of missiles, drones, and military manufacturing sites.
This shortfall became even more apparent after a major intelligence operation exposed a long-running spy cell in Yemen, with activities spanning across multiple sectors.
From the risk of espionage to the undermining of local telecom providers, the implications of Starlink’s operations extend far beyond providing internet access – they could become a vehicle for foreign influence and control.
[...]
3 Oct 2024
13 notes
·
View notes
Text
The Social Consequences of Marketing
Marketing, while essential for businesses and economies, has also been criticized for causing harm to society in various ways. Here are some significant ways in which marketing has negatively impacted society:
1. Promotion of Consumerism
Excessive consumption: Marketing often encourages the idea that happiness and success are linked to material goods, promoting a culture of consumerism. This has led to excessive consumption, debt, and environmental damage, as people are driven to buy more than they need.
Planned obsolescence: Companies sometimes design products with limited lifespans, encouraging consumers to buy new versions frequently. This practice contributes to waste, depletion of resources, and increased consumer spending.
2. Exploitation of Insecurities
Body image and self-esteem: Advertising in industries like fashion, beauty, and fitness often exploits people's insecurities by promoting unrealistic beauty standards. This can lead to mental health issues such as low self-esteem, anxiety, body dysmorphia, and even eating disorders.
Fear-based marketing: Some marketing strategies use fear to sell products, such as insurance, security systems, or health products, by making consumers feel unsafe or inadequate without them.
3. Targeting Vulnerable Populations
Children: Marketing often targets children, who are particularly susceptible to persuasive messages. This leads to the commercialization of childhood, with kids exposed to unhealthy food, consumerist values, and a materialistic mindset from an early age.
Low-income groups: Companies sometimes market harmful products, such as payday loans or unhealthy foods, more aggressively to low-income populations, exacerbating financial hardship or health problems.
4. Perpetuation of Stereotypes and Social Divides
Gender roles: Marketing often reinforces gender stereotypes, portraying women as caregivers or men as breadwinners, thereby perpetuating outdated norms that limit gender equality and diversity.
Cultural appropriation and tokenism: Some brands use cultural symbols or minority groups in marketing campaigns without understanding their significance, which can lead to cultural appropriation and tokenism, alienating and misrepresenting marginalized communities.
5. Environmental Damage
Overemphasis on fast fashion and disposable goods: Marketing has contributed to the rise of fast fashion and a throwaway culture, promoting short-term use of cheap, disposable products. This has serious environmental consequences, including pollution, resource depletion, and the generation of vast amounts of waste.
Greenwashing: Some companies falsely market products as "environmentally friendly" or "sustainable" in an attempt to capitalize on consumers' eco-consciousness, misleading the public and delaying genuine action on environmental issues.
6. Manipulation and Misinformation
False advertising: Companies sometimes make exaggerated or false claims about their products, misleading consumers and creating false expectations. This can be particularly harmful when it comes to health products, pharmaceuticals, or weight-loss treatments.
Addictive design: Marketing techniques are increasingly used to promote addictive behaviors, particularly in the context of social media, video games, or gambling. Companies manipulate users through behavioral nudges and psychological triggers that keep them hooked.
7. Invasion of Privacy
Data mining and surveillance: With the rise of digital marketing, companies have gained unprecedented access to consumers’ personal data. Many firms engage in data mining and targeted advertising based on individuals' online behavior, often without full transparency or consent, leading to concerns about privacy and data security.
Personalization and manipulation: Highly personalized marketing can lead to manipulation, as companies can target individuals with ads tailored to their specific vulnerabilities, making it harder for consumers to make objective decisions.
8. Promotion of Unhealthy Lifestyles
Junk food advertising: Aggressive marketing of unhealthy foods, particularly to children, has been linked to rising rates of obesity, diabetes, and other diet-related diseases.
Alcohol and tobacco marketing: Despite restrictions in some countries, marketing of alcohol, tobacco, and vaping products continues to glamorize these potentially harmful substances, leading to addiction and public health crises.
9. Contributing to Financial Instability
Credit and debt marketing: Marketing of credit cards, loans, and other financial products often promotes spending beyond one's means, contributing to personal debt and financial instability. Predatory lending practices, such as payday loans, are frequently marketed to those already in financial difficulty.
10. Reduction of Authenticity and Creativity
Commercialization of art and culture: Marketing can sometimes reduce art, culture, and creativity to mere products to be sold, stripping them of their authenticity. This can lead to the commodification of creative expression and a focus on profit over substance.
Trend exploitation: By constantly pushing new trends, marketing fosters a culture of superficiality and short-term thinking, where value is placed on what is fashionable or trending rather than what is meaningful or lasting.
While marketing plays a critical role in the economy by connecting consumers with products, it also has significant social, psychological, and environmental consequences. From promoting overconsumption and exploiting insecurities to targeting vulnerable groups and contributing to environmental degradation, marketing practices have often prioritized profit over societal well-being. Reforming marketing to be more ethical and socially responsible is essential for creating a healthier, more sustainable society.
#philosophy#epistemology#knowledge#learning#education#chatgpt#ethics#economics#society#politics#Consumerism and Materialism#False Advertising#Gender Stereotypes in Media#Data Privacy and Surveillance#Environmental Impact of Marketing#Exploitation of Insecurities#Ethical Marketing Practices#Targeting Vulnerable Populations#consumerism#marketing#advertising#capitalism
9 notes
·
View notes
Note
If you don't mind, can you answer a question?
What did sophieinwonderland do? /gen
I just want to know because I don't want to hate someone for nothing...
Oh, boy.
Well, first off, I am not asking anyone to hate Sophie. How you feel and what you do with this information after I give it is entirely up to you.
With that being said... here's a non-exhaustive list of things she's done.
(Reblogs are getting turned off in advance.)
1. Continues to use, and defends the usage of, "tulpa"/"tulpamancy" terminology.
Many, MANY systems of color have explained that the usage of tulpamancy and related words is racist. Sophie, who is white, is not unaware of this. She has been told repeatedly. She defends the usage of it to anyone who gives her the opportunity.
2. Spreads misinformation about dissociative disorders.
She does not have a dissociative disorder. She twists words, and misrepresents factual data to suit her agenda.
3. Sent her followers after someone.
Not going to name names for respect and privacy reasons, but she directly participated in a harassment campaign that eventually resulted in someone being hospitalized.
Absolutely not even on the same level as the other 3, but it's worth mentioning she's also 100% ok with radqueers, which is like... extreme yikes. She's just a shit person. She doesn't care about how her actions actually impact other people.
And even if she was none of those things, I don't like her regardless. At all.
So, yeah. We block anyone and everyone we see that's directly involved with her.
I hope this clears some stuff up! Also, any and all negative tone taken throughout this post wasn't directed at you for the question. I appreciate you asking for clarification! /gen
🖤💜💙💚💛
28 notes
·
View notes
Text
[Full Text] Emerging Media Companies, Tracking Cookies, and Data Privacy -- An open letter to Critical Role, Dropout, and fellow audience members
Summary / TL;DR
Both Critical Role (CR) and Dropout have begun exclusively using links provided by third-party digital marketing solution companies in their email newsletters.
Every link in each of the newsletters (even the unsubscribe link) goes through a third-party domain which is flagged as a tracking server by the uBlock Origin browser extension.
Third-party tracking cookies are strictly unnecessary and come with a wide array of risks, including non-consensual targeted advertising, targeted misinformation, doxxing, and the potential for abuse by law enforcement.
You are potentially putting your privacy at risk every time you click on any of the links in either of these newsletters.
IMO these advertising companies (and perhaps CR/Dropout by proxy) are likely breaking the law in the EU and California by violating the GDPR and CCPA respectively.
Even if Critical Role and Dropout are not directly selling or exploiting your personal data, they are still profiting off of it by contracting with, and receiving services from, companies who almost certainly are. The value of your personal data is priced into the cost of these services.
They should stop, and can do so without any loss of web functionality.
1/7. What is happening?
Critical Role and Dropout have begun exclusively using links provided by third-party digital marketing solution companies in their email newsletters.

[ID: A screenshot of the Dropout newsletter alongside the page’s HTML source which shows that the target destination for an anchor element in the email leads to d2xR2K04.na1.hubspotlinks.com. End ID.]

[ID: A screenshot of the CR newsletter alongside the page’s HTML source which shows that the target destination for an anchor element in the email leads to trk.klclick.com. End ID.]
The domains attached to these links are flagged as advertising trackers by the uBlock Origin browser extension.

[ID: Screenshot of a Firefox web browser. The page displays a large warning icon and reads “uBlock Origin has prevented the following page from loading [...] because of the following filter: `||hubspotlinks.com` found in Peter Lowe’s Ad and tracking server list. End ID.]

[ID: Screenshot of a Firefox web browser. The page displays a large warning icon and reads “uBlock Origin has prevented the following page from loading [...] because of the following filter: `||klclick1.com` found in Peter Lowe’s Ad and tracking server list. End ID.]
In both cases, every link in the newsletter goes through the flagged third-party domain, and the intended endpoint (Twitter, their store page, etc.) is completely obscured and inaccessible from within the email itself. Even the unsubscribe links feed through the tracking service.
You can test this yourself in your own email client by hovering your cursor over a link in the email without clicking it and watching to see what URL pops up. You may have noticed this yourself if you use uBlock Origin as an ad-blocker.
I don’t know for certain when this first started. It’s possible that this has been going on for a year or more at this point, or it may have started just a few months ago. Either way: it ought to stop.
2/7. What is a tracking cookie?
A tracking cookie is a unique, universally identifiable value placed on your machine by somebody with the intention of checking for that value later to identify you (or at least to identify your machine).
Tracking cookies are used by companies to create advertising behaviour profiles. These profiles are supposedly anonymous, but even if the marketing companies creating them are not lying about that (a tough sell for me personally, but your mileage may vary when it comes to corporations with 9-figure annual incomes), the data can often be de-anonymized.
If this happens, the data can be used to identify the associated user, potentially including their full name, email address, phone number, and physical address—all of which may then be associated with things like their shopping habits, hobbies, preferences, the identities of their friends and family, gender, political opinions, job history, credit score, sexuality, and even when they ovulate.
Now, it is important to note that not all cookies are tracking cookies. A cookie is just some data from a web page that persists on your machine and gets sent back to the server that put it there. Cookies in general are not necessarily malicious or harmful, and are often essential to certain web features functioning correctly (e.g. keeping the user logged in on their web browser after they close the tab). But the thing to keep in mind is that a domain has absolute control over the information that has been stored on your computer by that domain, so allowing cookies is a matter of trusting the specific domain that wants to put them there. You can look at the outgoing information being sent from your machine, but its purpose cannot be determined without knowing what is being done with it on the other side, and these marketing companies ought not to have the benefit of your doubt when they have already been flagged by privacy watchdogs.
3/7. What’s the harm?
Most urgently, as I touched on above: The main source of harm is from corporations profiting off of your private data without your informed consent. However, targeted advertising is actually the least potentially harmful outcome of tracking cookies.
1/6. Data brokers
A data broker is an individual or company that specializes in collecting personal data (such as personal income, ethnicity, political beliefs, geolocation data, etc.) and selling or licensing such information to third parties for a variety of uses, such as background checks conducted by employers and landlords, two universally benevolent groups of people.
There are varying regulations around the world limiting the collection of information on individuals, and the State of California passed a law attempting to address this problem in 2018, following in the footsteps of the EU’s GDPR, but in the jurisdiction of the United States there is no federal regulation protecting consumers from data brokers. In fact, due to the rising interest in federal regulation, data broker firms lobbied to the tune of $29 million in the year 2020 alone.
2/6. De-anonymization techniques
Data re-identification or de-anonymization is the practice of combining datasets (such as advertising profiles) and publicly available information (such as scraped data from social media profiles) in order to discover patterns that may reveal the identities of some or all members of a dataset otherwise intended to be anonymous.
Using the 1990 census, Professor Latanya Sweeney of the Practice of Government and Technology at the Harvard Kennedy School found that up to 87% of the U.S. population can be identified using a combination of their 5-digit zip code, gender, and date of birth. [Link to the paper.]
Individuals whose datasets are re-identified are at risk of having their private information sold to organizations without their knowledge or consent. Once an individual’s privacy has been breached as a result of re-identification, future breaches become much easier: as soon as a link is made between one piece of data and a person’s real identity, that person is no longer anonymous and is at far greater risk of having their data from other sources similarly compromised.
3/6. Doxxing
Once your data has been de-anonymized, you are significantly more vulnerable to all manner of malicious activity: from scam calls and emails to identity theft to doxxing. This is of particular concern for members of minority groups who may be targeted by hate-motivated attacks.
4/6. Potential for abuse by government and law enforcement
Excerpt from “How period tracking apps and data privacy fit into a post-Roe v. Wade climate” by Rina Torchinsky for NPR:
Millions of people use apps to help track their menstrual cycles. Flo, which bills itself as the most popular period and cycle tracking app, has amassed 43 million active users. Another app, Clue, claims 12 million monthly active users. The personal health data stored in these apps is among the most intimate types of information a person can share. And it can also be telling. The apps can show when their period stops and starts and when a pregnancy stops and starts. That has privacy experts on edge because this data—whether subpoenaed or sold to a third party—could be used to suggest that someone has had or is considering an abortion. ‘We're very concerned in a lot of advocacy spaces about what happens when private corporations or the government can gain access to deeply sensitive data about people’s lives and activities,’ says Lydia X. Z. Brown, a policy counsel with the Privacy and Data Project at the Center for Democracy and Technology. ‘Especially when that data could put people in vulnerable and marginalized communities at risk for actual harm.’
Obviously Critical Role and Dropout are not collecting any sort of data related to their users’ menstrual cycles, but the thing to keep in mind is that any data that is exposed to third parties can be sold and distributed without your knowledge or consent and then be used by disinterested—or outright malicious—actors to de-anonymize your data from other sources, included potentially highly compromising data such as that collected by these period-tracking apps. Data privacy violations have compounding dangers, and should be proactively addressed wherever possible. The more of your personal data exists in the hands of third parties, the more it is to be de-anonymized.
5/6. Targeted misinformation
Data brokers are often incredibly unscrupulous actors, and will sell your data to whomever can afford to buy it, no questions asked. The most high-profile case of the consequences of this is the Facebook—Cambridge Analytica data scandal, wherein the personal data of Facebook users were acquired by Cambridge Analytica Ltd. and compiled alongside information collected from other data brokers. By giving this third-party app permission to acquire their data back in 2015, Meta (then Facebook) also gave the app access to information on their users’ friend networks: this resulted in the data of some 87 million users being collected and exploited.
The data collected by Cambridge Analytica was widely used by political strategists to influence elections and, by and large, undermine democracy around the world: While its parent company SCL had been influencing elections in developing countries for decades, Cambridge Analytica focused more on the United Kingdom and the United States. CEO Alexander Nix said the organization was involved in 44 American political races in 2014. In 2016, they worked for Donald Trump’s presidential campaign as well as for Leave.EU, one of the organisations campaigning for the United Kingdom to leave the European Union.
6/6. The Crux: Right to Privacy Violations
Even if all of the above were not concerns, every internet user should object to being arbitrarily tracked on the basis of their right to privacy. Companies should not be entitled to create and profit from personality profiles about you just because you purchased unrelated products or services from them. This right to user privacy is the central motivation behind laws like the EU’s GDPR and California’s CCPA (see Section 6).
4/7. Refuting Common Responses
1/3. “Why are you so upset? This isn’t a big deal.”
Commenter: Oh, if you’re just talking about third party cookies, that’s not a big deal … Adding a cookie to store that ‘this user clicked on a marketing email from critical role’ is hardly [worth worrying about].
Me: I don’t think you understand what tracking cookies are. They are the digital equivalent of you going to a drive through and someone from the restaurant running out of the store and sticking a GPS monitor onto your car.
Commenter: Kind of. It’s more like slapping a bumper sticker on that says, in restaurant-ese, ‘Hi I’m [name] and I went to [restaurant] once!’
This is actually an accurate correction. My metaphor was admittedly overly simplistic, but the correction specifies only so far as is comfortable for the commenter. If we want to construct a metaphor that is as accurate as possible, it would go something like this:
You drive into the McDonald’s parking lot. As you are pulling in, unbeknownst to you, a Strange Man pops out of a nearby bush (that McDonald’s has allowed him to place here deliberately for this express purpose), and sticks an invisible bumper sticker onto the back of your car. The bumper sticker is a tracker that tells the Strange Man which road you took to drive to McDonald’s, what kind of car you drive, and what (if anything) you ordered from McDonald’s while you were inside. It might also tell him where you parked in the parking lot, what music you were listening to in your car on the way in, which items you looked at on the menu and for how long, if you went to the washroom, which washroom you went into, how long you were in the washroom, and the exact location of every step you took inside the building.
Now, as soon as you leave the McDonald’s, the bumper sticker goes silent and stops being able to report information. But, let’s say next week you decide to go to the Grocery Store, and (again, unbeknownst to you), the Strange Man also has a deal with the Grocery Store. So as you’re driving into the grocery store’s parking lot, he pops out of another bush and goes to put another bumper sticker onto your car. But as he’s doing so, he notices the bumper sticker he’s already placed there a week ago that only he can see (unless you’ve done the car-equivalent of clearing your browser cache), and goes “ah, it’s Consumer #1287499290! I’ll make sure to file all of this new data under my records for Consumer #1287499290!”
You get out of your car and start to walk into the Grocery Store, but before you open the door, the Strange Man whispers to the Grocery Store: “Hey, I know you’re really trying to push your cereal right now, want me to make it more likely that this person buys some cereal from you?” and of course the Grocery Store agrees—this was the whole reason they let him set up that weird parking lot bush in the first place.
So the Strange Man runs around the store rearranging shelves. He doesn’t know your name (all the data he collects is strictly anonymous after all!) but he does know that you chose the cutesy toy for your happy meal at McDonald’s, so he changes all of the cereal packaging labels in the store to be pastel-coloured and covered in fluffy bears and unicorns. And maybe you were already going to the Grocery Store to buy cereal, and maybe you’re actually very happy to buy some cereal in a package that seems to cater specifically to your interests, but wouldn’t you feel at least a little violated if you found out that this whole process occurred without your knowledge? Especially if you felt like you could trust the people who owned the Grocery Store? They’re not really your friend or anything, but maybe you thought that they were compassionate and responsible members of the community, and part of the reason that you shopped at their store was to support that kind of business.
2/3. “Everyone does it, get over it.”
Commenter: [The marketing company working with CR] is an industry standard at this point, particularly for small businesses. Major partner of Shopify, a fairly big player. If you don't have a software development team, using industry standard solutions like these is the easy, safe option.
This sounds reasonable, but it actually makes it worse, not better, that Critical Role and Dropout are doing this. All this excuse tells me is that most businesses using Shopify (or at least the majority of those that use its recommended newsletter service) have a bush for the Strange Man set up in their parking lot.
Contracting with these businesses is certainly the easy option, but it is decidedly not the safe one.
3/3. “They need to do it for marketing reasons.”
Commenter 1: Email marketing tools like [this] use tracking to measure open and click rates. I get why you don’t want to be tracked, but it’s very hard to run a sizeable email newsletter without any user data.
Commenter 2: I work in digital marketing … every single email you get from a company has something similar to this. Guaranteed. This looks totally standard.
I am a web programmer by trade. It is my full time job. Tracking the metrics that Critical Role and Dropout are most likely interested in does not require embedding third-party tracking cookies in their fans’ web browsers. If you feel comfortable taking my word on that, feel free to skip the next section. If you’re skeptical (or if you just want to learn a little bit about how the internet works) please read on.
5/7. Tracking cookies are never necessary
We live in a technocracy. We live in a world in which technology design dictates the rules we live by. We don’t know these people, we didn’t vote for them in office, there was no debate about their design. But yet, the rules that they determine by the design decisions they make—many of them somewhat arbitrary—end up dictating how we will live our lives. —Latanya Sweeney
1/3. Definitions
A website is a combination of 2 computer programs. One of the two programs runs on your computer (laptop/desktop/phone/etc.) and the other runs on another computer somewhere in the world. The program running on your computer is the client program. The program running on the other computer is the server program.
A message sent from the client to the server is a request. A message sent from the server to the client is a response.
Cookies are bits of data that the server sends to the client in a response that the client then sends back to the server as an attachment to its subsequent requests.
A session is a series of sequential interactions between a client and server. When either of the two programs stops running (e.g. when you close a browser tab), the session is ended and any future interactions will take place in a new session.
A URL is a Uniform Resource Locator. You may also sometimes see the initialism URI—in which the ‘I’ stands for Identifier—but they effectively refer to the same thing, which is the place to find a specific thing on the internet. For our purposes, a “link” and a URL mean the same thing.
2/3. What do Critical Role and Dropout want?
These media companies (in my best estimation) are contracting with the digital advertising companies in order to get one or more of the following things:
Customer identity verification (between sessions)
Marketing campaign analytics
Customer preference profiles
Customer behaviour profiles
3/3. How can they get these things without tracking cookies?
Accounts. Dropout has an account system already. As Beacon is a thing now I have to assume Critical Role does as well, therefore this is literally already something they can do without any additional parties getting involved.
URL Query Parameters. So you want to know which of your social media feeds is driving the most traffic to your storefront. You could contract a third-party advertising company to do this for you, but as we have seen this might not be the ideal option. Instead, when posting your links to said feeds, attach a little bit of extra text to the end of the URL link so: becomes or or even These extra bits of information at the end of a URL are query parameters, and act as a way for the client to specify some instructions for the server when sending a request. In effect, a URL with query parameters allows the client to say to the server “I want this thing under these conditions”. The benefit of this approach is, of course, that you actually know precisely what information is being collected (the stuff in the parameters) and precisely what is being done with it, and you’ve avoided exposing any of your user data to third parties.
Internal data collection. Optionally associate a user’s email address with their preferences on the site. Prompt them to do this whenever they purchase anything or do any action that might benefit from having some saved preference, informing them explicitly when you do so and giving them the opportunity to opt-out.
Internal data collection. The same as above, but let the user know you are also tracking their movements while on your site. You can directly track user behaviour down to every single mouse movement if you really want to—again, no need to get an outside party involved to snoop on your fans. But you shouldn’t do that because it’s a little creepy!
At the end of the day, it will of course be more work to set up and maintain these things, and thus it will inevitably be more expensive—but that discrepancy in expense represents profit that these companies are currently making on the basis of violating their fans’ right to privacy.
6/7. Breaking the Law
The data subject shall have the right to object, on grounds relating to his or her particular situation, at any time to processing of personal data concerning him or her [...] The controller shall no longer process the personal data unless the controller demonstrates compelling legitimate grounds for the processing which override the interests, rights and freedoms of the data subject or for the establishment, exercise or defence of legal claims. Where personal data are processed for direct marketing purposes, the data subject shall have the right to object at any time to processing of personal data concerning him or her for such marketing, which includes profiling to the extent that it is related to such direct marketing. Where the data subject objects to processing for direct marketing purposes, the personal data shall no longer be processed for such purposes. At the latest at the time of the first communication with the data subject, the right referred to in paragraphs 1 and 2 shall be explicitly brought to the attention of the data subject and shall be presented clearly and separately from any other information. — General Data Protection Regulation, Art. 21
Nobody wants to break the law and be caught. I am not accusing anyone of anything and this is just my personal speculation on publicly-available information. I am not a lawyer; I merely make computer go beep-boop. If you have any factual corrections for this or any other section in this document please leave a comment and I will update the text with a revision note. Before I try my hand at the legal-adjacent stuff, allow me to wade in with the tech stuff.
Cookies are sometimes good and sometimes bad. Cookies from someone you trust are usually good. Cookies from someone you don’t know are occasionally bad. But you can take proactive measures against bad cookies. You should always default to denying any cookies that go beyond the “essential” or “functional” categorizations on any website of which you are remotely suspicious. Deny as many cookies as possible. Pay attention to what the cookie pop-ups actually say and don’t just click on the highlighted button: it is usually “Accept All”, which means that tracking and advertising cookies are fair game from the moment you click that button onward. It is illegal for companies to arbitrarily provide you a worse service for opting out of being tracked (at least it is in the EU and California).
It is my opinion (and again, I am not a legal professional, just a web developer, so take this with a grain of salt) that the links included in the newsletter emails violate both of these laws. If a user of the email newsletter residing in California or the EU wishes to visit any of the links included in said email without being tracked, they have no way of doing so. None of the actual endpoints are available in the email, effectively forcing the user to go through the third-party domain and submit themselves to being tracked in order to utilize the service they have signed up for. Furthermore, it is impossible to unsubscribe directly from within the email without also submitting to the third-party tracking.

[ID: A screenshot of the unsubscribe button in the CR newsletter alongside the page HTML which shows that the target destination for the anchor element is a trk.klclick.com page. End ID.]
As a brief aside: Opening the links in a private/incognito window is a good idea, but will not completely prevent your actions from being tracked by the advertiser. My recommendation: install uBlock Origin to warn you of tracking domains (it is a completely free and open-source project available on most major web browsers), and do not click on any links in either of these newsletters until they change their practices.
Now, it may be the case that the newsletters are shipped differently to those residing in California or the EU (if you are from either of these regions please feel free to leave a comment on whether or not this is the case), but ask yourself: does that make this any better? Sure, maybe then Critical Role and Dropout (or rather, the advertising companies they contract with) aren’t technically breaking the law, but it shows that the only thing stopping them from exploiting your personal data is potential legal repercussions, rather than any sort of commitment to your right to privacy. But I expect that the emails are not, in fact, shipping any differently in jurisdictions with more advanced privacy legislation—it wouldn’t be the first time a major tech giant blatantly flaunted EU regulations.
Without an additional browser extension such as uBlock Origin, a user clicking on the links in these emails may not even be aware that they have interacted with the advertising agency at all, let alone what sort of information that agency now has pertaining to them, nor do they have any ability to opt out of this data collection.
For more information about your right to privacy—something that only those living in the EU or California currently have—you can read explanations of the legislations at the following links (take note that these links, and all of the links embedded in this paper, are anchored directly to the destinations they purport to be, and do not sneakily pass through an additional domain before redirecting you):
7/7. Conclusion
Never attribute to malice that which can be adequately explained by neglect, ignorance or incompetence. —Hanlon’s Razor
The important thing to make clear here is this: Even if Critical Role and Dropout are not directly selling or exploiting your personal data, they are still profiting off of it by contracting with, and receiving services from, companies whom I believe are. You may not believe me.
I do not believe that the management teams at Critical Role and Dropout are evil or malicious. Ignorance seems to be the most likely cause of this situation. Someone at some marketing company told them that this type of thing was helpful, necessary, and an industry standard, and they had no reason to doubt that person’s word. Maybe that person had no reason to doubt the word of the person who told them. Maybe there are a few people in that chain, maybe quite a few. I do not expect everyone running a company to be an expert in this stuff (hell, I’m nowhere close to being an expert in this stuff myself—I only happened to notice this at all because of a browser extension I just happened to have installed to block ads), but what I do expect is that they change their behaviour when the potential harms of their actions have been pointed out to them, which is why I have taken the time to write this.
PS. To the employees of Critical Role and Dropout
It is my understanding that these corporations were both founded with the intention of being socially responsible alongside turning a profit. By using services like the ones described above, you are, however unintentionally, profiting off of the personal datasets of your fans that are being compiled and exploited without their informed consent. You cannot say, implicitly or explicitly, “We’re not like those other evil companies! We care about more than just extracting as much money from our customers as possible!” while at the same time utilizing these services, and it is my hope that after reading this you will make the responsible choice and stop doing so.
Thank you for reading,
era
Originally Published: 23 May 2024
Last Updated: 28 May 2024
#critical role#dimension 20#dropout#dropout tv#brennan lee mulligan#sam reich#critical role campaign 3#cr3#midst podcast#candela obscura#make some noise#game changer#smarty pants#very important people#web security#data privacy#gdpr#ccpa#open letter
10 notes
·
View notes
Text
I can’t stop thinking about how Cocomelon is damaging babies because the fast pace scene changes can “interfere with the development of executive functions”, and how thin parents are spread in capitalism that they rely on television to entertain/keep their babies company just so they have some time to complete domestic tasks. I am thinking about disintegrated Community Care/structure. I am thinking about how Instagram, Tiktok, Twitter, Tumblr, all media are engineered to be addictive and alter the executive functioning of kids, tweens, teens, and adults of all ages. How malleable our minds are..bread and circuses. Everything we consume has the power to heal or destroy us. I think about Congress Bill 686, and feel discouraged and powerless. You may have heard of it as “The TikTok Ban” of course, the media intentionally oversimplifies it as a ban on TikTok, but really it is the means for The State to restrict the sharing of information on the internet and to censor us, keep us misinformed and suppressed. The State knows that knowledge is power so they keep us intentionally in the dark and distracted, plucking away human rights one by one while we are watching the stage. The Restrict Act would require the Department of Commerce to “identify, deter, disrupt, prevent, prohibit, investigate, and mitigate transactions involving ICT products and services” 🤳🏼👁️ (ICT means Information and Communications Technology, ICT Products and services refers to social media) When COVID first hit, my friend said “this will be like 9/11, there was the world pre 9/11 and post 9/11” I am not one to believe we are “post-covid” because we are still in the grips of the Covidian information wars, which I feel will be one of the main long term take aways from The-Covid-Years. Bill 686 harms all, because any group of 1 million people organizing or sharing information online can be persecuted, banned and shut down under the guise of “prohibiting certain transactions between persons of the United States and foreign adversaries” Congress Bill 686 establishes both civil and criminal penalties for violations of the bill, meaning anything that they consider an “unacceptable risk to national security.” Please don’t forget we live in a police state which is meant to protect the empire. In The United States privacy is not sacrosanct, and actually American big brother corporations like Meta and Google are investing millions into anti-TikTok propaganda, because it clears their competition and allows them back into the palms of citizens, so they can personally be the ones to steal our time and data. It makes me angry, it’s painful. How can we organize against the faceless enemy? It’s all subversion and censorship, anything to get the undiluted power to be placed back into the hands of an American corporation. It will always be The State, Corporations, and Colleges keeping information tucked away and inaccessible to the masses. We must do what we can to preserve the internet as a place of free information sharing and connection. The infrastructure of our communities in real life are generally weak. Weekly I hit a paywall online, and I have seen my own words be instantaneously given an AI generated COVID misinformation banner before. It’s insane, and most people are not comfortable admitting out loud that we are alive during fascism. What’s funny in a way is, I have long hated TikTok, but now that it risks being banned in this “land of the free” I find myself urgently realizing how important it is to preserve and protect.. It is on the individual to use the internet wisely and with boundaries, not the state to restrict people’s access to information. Privacy is important and data-preservation is important, obviously, but if this is what 686 was truly about, we would be having different conversations. All legislation is created to build a precedent.
88 notes
·
View notes
Text
'Role of Social Media in Public Health Campaigns.'
By: naomicindy

Social media isn’t just for selfies, memes, or sliding into DMs anymore—it has become a game-changer for public health communication.
Platforms like Instagram, Facebook, and X have shifted from being places for personal interaction to becoming tools for sharing vital health information and rallying communities into action. I mean, if you lived through the COVID-19 pandemic, you know how much these platforms became lifelines for staying updated and feeling connected. But, of course, it’s not all sunshine and life-saving hashtags—there’s a darker side to using social media for health, like misinformation spreading faster than a viral dance trend and big questions about privacy.
Let’s start with the good stuff—social media’s power to inspire action on a massive scale. Remember the ALS Ice Bucket Challenge back in 2014? It was one of the first moments we all realized just how big these platforms could be for public health campaigns. People everywhere were dumping freezing water on themselves, tagging their friends, and donating to ALS research. It wasn’t just a trend; it raised $115 million in six weeks and put ALS (a disease a lot of people hadn’t even heard of before) on the map (Camero, 2023). It’s wild to think a simple idea could go viral like that and bring in both awareness and funding. Social media literally turned a grassroots campaign into a global movement.

Fast forward to COVID-19, and social media took on a whole new level of importance. When everything felt chaotic, platforms became essential for sharing updates, and keeping people in the loop. Apps like Malaysia’s MySejahtera were lifesavers, tracking infections, vaccination records, and safety guidelines all in one place. They showed how tech could help streamline public health efforts and reach people wherever they were. Plus, health organizations could use social media to speak directly to the public and adjust their messages in real time (Suarez-Lledo & Alvarez-Galvez, 2021). And let’s not forget all those TikTok dances teaching us how to wash our hands properly. Who knew hygiene could go viral in more ways than one?
But it wasn’t all smooth sailing. The COVID-19 pandemic also highlighted some major issues with using social media for health communication. Misinformation spread like wildfire. Seriously, there were wild claims about fake cures, exaggerated vaccine side effects, and straight-up conspiracy theories. It’s scary because this stuff wasn’t just annoying—it caused real harm by making people hesitant to get vaccinated or follow safety measures. Platforms tried to fight back with fact-checking and flagging false content, but it felt like a never-ending game of whack-a-mole. Honestly, we need more proactive strategies to tackle this, like better education on spotting fake news and partnerships between health authorities and social media companies (Tan, 2022).

Then there’s the issue of privacy. Like, we all kind of know social media collects our data, but when it comes to health apps like MySejahtera, it gets way more personal. These apps helped so much during the pandemic, but they also collected tons of sensitive health info. And that raises big questions: How is this data being stored? Who has access to it? Could it be misused? It’s a little scary to think about. If public health campaigns want to keep people’s trust, they need to get real about data transparency and security (Akinsanmi & Salami, 2021). Nobody wants their health data floating around in the wrong hands.
Looking ahead, the future of public health communication is definitely going to lean even more on digital strategies—and honestly, that’s kind of exciting. Social media influencers, for example, have so much potential to make health campaigns more relatable and effective. Think about it: if your fave content creator talks about mental health or promotes a campaign like “R U OK?” it hits differently than a random ad or government PSA. You trust them. You listen. That’s the magic of influencers—they connect on a personal level.

Visual storytelling is another area where social media shines (Varicak, 2023). Infographics, TikToks, and Instagram Reels are perfect for breaking down complicated health info into bite-sized, shareable pieces. And let’s be real, we’re all more likely to engage with a cool animation or quick how-to video than a wall of text. Public health campaigns can totally tap into this, using these tools to get their messages across in a way that feels modern and engaging.
But with great power comes great responsibility (shoutout to Uncle Ben for that wisdom). Social media’s potential is massive, but so are the risks. Public health leaders need to focus on three big priorities: fighting misinformation, protecting user privacy, and making sure everyone has access to digital tools, no matter their background or circumstances. It’s a lot, but the lessons we’ve learned—from the ALS Ice Bucket Challenge to the pandemic—can help guide the way.
In the end, social media has completely transformed how we talk about and tackle public health issues. It can connect people, amplify campaigns, and inspire real change. But to use it responsibly, we’ve got to address the challenges head-on. If we can figure out how to balance the opportunities and risks, social media can keep building healthier, more informed communities around the world. And honestly? That’s a future I’m excited to see.

Akinsanmi, T., & Salami, A. (2021). Evaluating the trade-off between privacy, public health safety, and digital security in a pandemic. Data & Policy, 3, e27. https://www.cambridge.org/core/journals/data-and-policy/article/evaluating-the-tradeoff-between-privacy-public-health-safety-and-digital-security-in-a-pandemic/3659C28712DE31B743266935ECF4615C Camero, K. (2023, June 21). How the ALS Ice Bucket Challenge made a lasting impact. National Geographic . https://www.nationalgeographic.com/science/article/als-ice-bucket-challenge-research-impact Suarez-Lledo, V., & Alvarez-Galvez, J. (2021). Prevalence of health misinformation on social media: systematic review. Journal of medical Internet research, 23(1), e17187. https://www.jmir.org/2021/1/e17187/ Tan, C. (2022). The curious case of regulating false news on Google. Computer Law & Security Review, 46, 105738. https://www.sciencedirect.com/science/article/pii/S0267364922000814 Varicak, S. (2023, May 29). The power of visual storytelling in social media ads. LinkedIn. https://www.linkedin.com/pulse/power-visual-storytelling-social-media-ads-stefan-varicak/
3 notes
·
View notes
Text
ADDRESSING TWITTER'S TOS/POLICY IN REGARDS TO ARTISTS AND AI
Hi !! if you're an artist and have been on twitter, you've most likely seen these screen shots of twitters terms of service and privacy policy regarding AI and how twitter can use your content
I want to break down the information that's been going around as I noticed a lot of it is unintentionally misinformation/fearmongering that may be causing artists more harm than good by causing them to panic and leave the platform early
As someone who is an artist and makes a good amount of my income off of art, I understand the threat of AI art and know how scary it is and I hope to dispel some of this fear regarding twitter's TOS/Privacy policy at least. At a surface level yes, what's going on seems scary but there's far more to it and I'd like to explain it in more detail so people can properly make decisions!
This is a long post just as a warning and all screenshots should have an alt - ID with the text and general summary of the image
Terms of Service
Firstly, lets look at the viral post regarding twitter's terms of service and are shown below
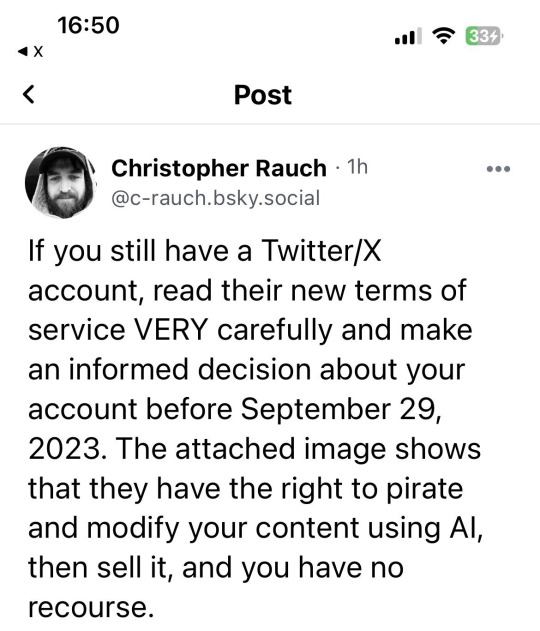
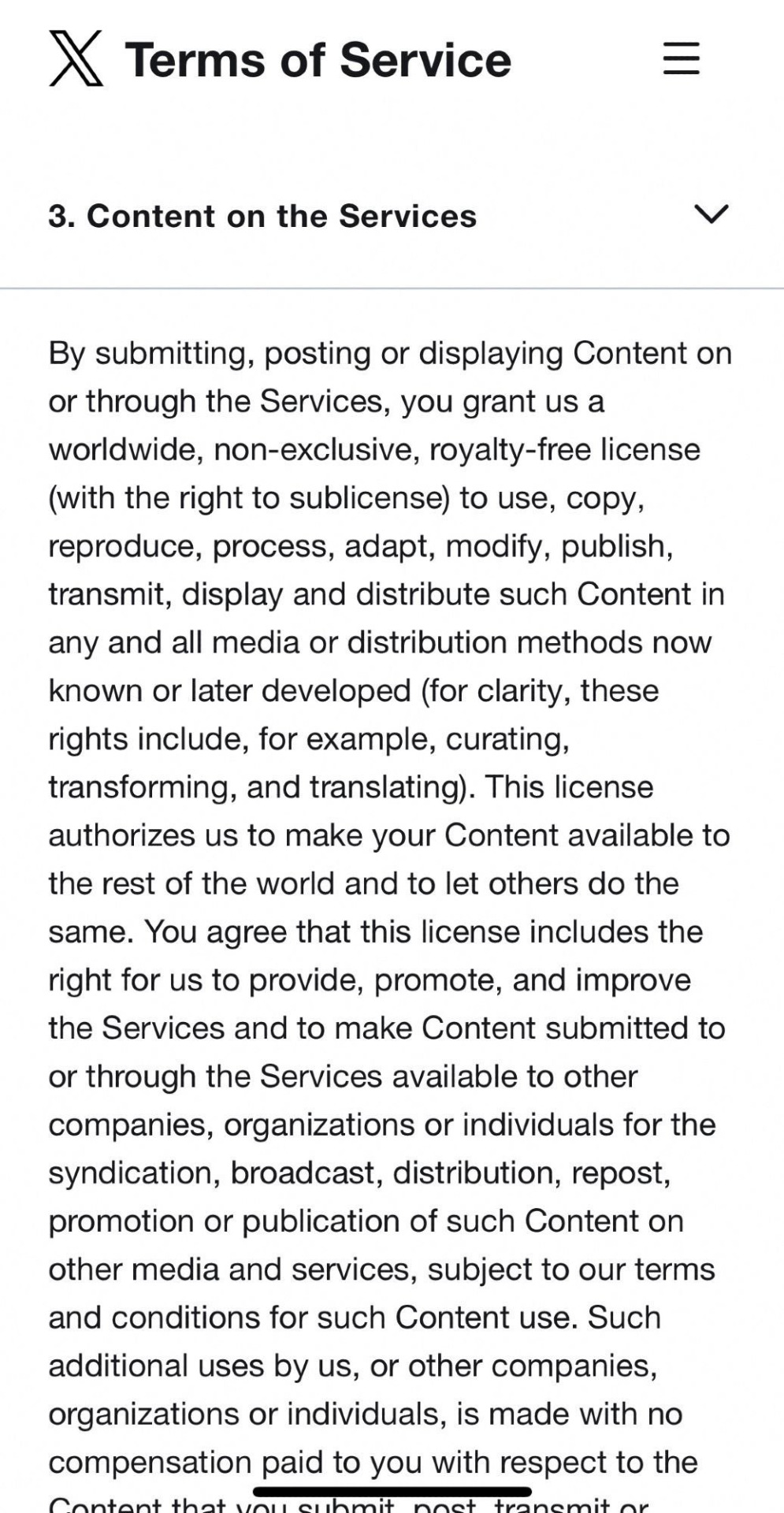
I have seen these spread a lot and have seen so many people leave twitter/delete all their art/deactivate there when this is just industry standard to include in TOS
Below are other sites TOS I found real quick with the same/similar clauses! From instagram, tiktok, and even Tumblr itself respectively, with the bit worded similar highlighted
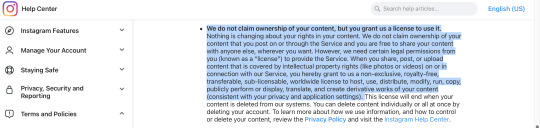
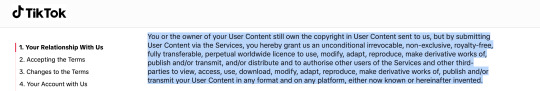
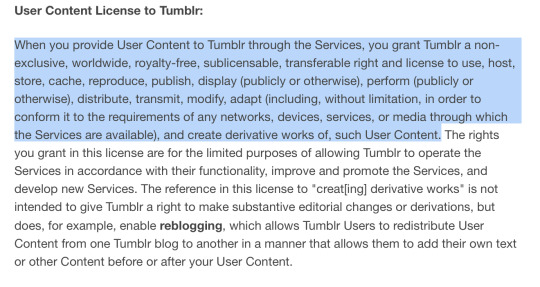
Even Bluesky, a sight viewed as a safe haven from AI content has this section

As you can see, all of them say essentially the same thing, as it is industry standard and it's necessary for sites that allow you to publish and others to interact with your content to prevent companies from getting into legal trouble.
Let me break down some of the most common terms and how these app do these things with your art/content:
storing data - > allowing you to keep content uploaded/stored on their servers (Ex. comments, info about user like pfp)
publishing -> allowing you to post content
redistributing -> allowing others to share content, sharing on other sites (Ex. a Tumblr post on twitter)
modifying -> automatic cropping, in app editing, dropping quality in order to post, etc.
creating derivative works -> reblogs with comments, quote retweets where people add stuff to your work, tiktok stitches/duets
While these terms may seems intimidating, they are basically just tech jargon for the specific terms we know used for legal purposes, once more, simply industry standard :)
Saying that Twitter "published stored modified and then created a derivative work of my data without compensating me" sounds way more horrible than saying "I posted my art to twitter which killed the quality and cropped it funny and my friend quote-tweeted it with 'haha L' " and yet they're the same !
Privacy Policy
This part is more messy than the first and may be more of a cause for concern for artists. It is in regards to this screenshot I've seen going around
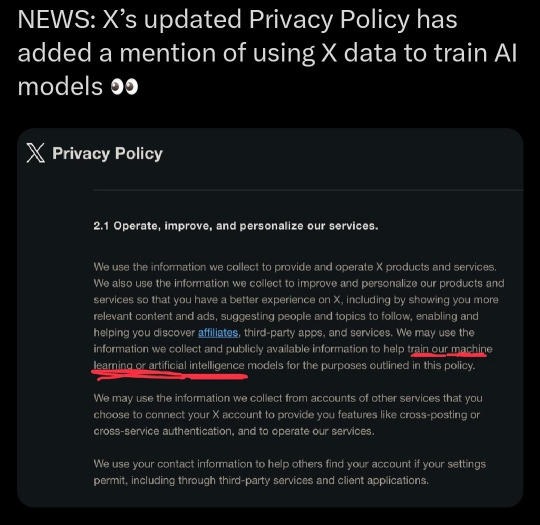
Firstly, I want to say that that is the only section in twitter's privacy policy where AI /machine learning is mentioned and the section it is is regarding how twitter uses user information.
Secondly, I do want to want to acknowledge that Elon Musk does have an AI development company, xAI. This company works in the development of AI, however, they want to make a good AGI which stands for artificial general intelligence (chatgpt, for example, is another AGI) in order to "understand the universe" with a scientific focus. Elon has mentioned wanting it to be able to solve complex mathematics and technical problems. He also, ofc, wants it to be marketable. You can read more about that here: xAI's website
Elon Musk has claimed that xAI will use tweets to help train it/improve it. As far as I'm aware, this isn't happening yet. xAI also, despite the name, does NOT belong/isn't a service of Xcorp (aka twitter). Therefore, xAI is not an official X product or service like the privacy policy is covering. I believe that the TOS/the privacy policies would need to expand to disclaim that your information will be shared specifically with affiliates in the context of training artificial intelligence models for xAI to be able to use it but I'm no lawyer. (also,,,Elon Musk has said cis/cisgender is a slur and said he was going to remove the block feature which he legally couldn't do. I'd be weary about anything he says)
Anyway, back to the screenshot provided, I know at a glance the red underlined text where it says it uses information collected to train AI but let's look at that in context. Firstly, it starts by saying it uses data it collects to provide and operate X products and services and also uses this data to help improve products to improve user's experiences on X and that AI may be used for "the purposes outlined in this policy". This means essentially just that is uses data it collects on you not only as a basis for X products and services (ex. targeting ads) but also as a way for them to improve (ex. AI algorithms to improve targeting ads). Other services it lists are recommending topics, recommending people to follow, offering third-party services, allowing affiliates etc. I believe this is all the policy allows AI to be used for atm.
An example of this is if I were to post an image of a dog, an AI may see and recognize the dog in my image and then suggest me more dog content! It may also use this picture of a dog to add to its database of dogs, specific breeds, animals with fur, etc. to improve this recommendation feature.
This type of AI image, once more, is common in a lot of media sites such as Tumblr, insta, and tiktok, and is often used for content moderation as shown below once more
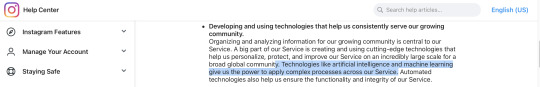
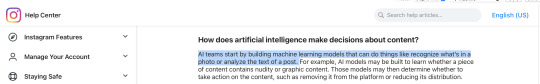
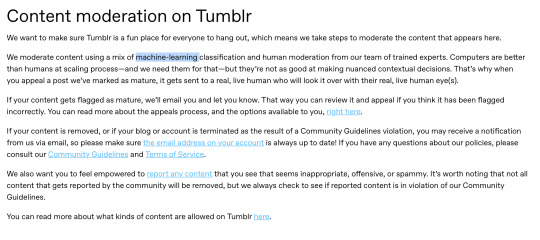
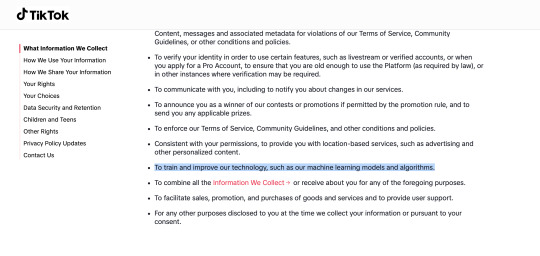
Again, as far as I'm aware, this type of machine learning is to improve/streamline twitter's recommendation algorithm and not to produce generative content as that would need to be disclaimed!!
Claiming that twitter is now using your art to train AI models therefore is somewhat misleading as yes, it is technically doing that, as it does scan the images you post including art. However, it is NOT doing it to learn how to draw/generate new content but to scan and recognize objects/settings/etc better so it can do what social media does best, push more products to you and earn more money.
(also as a small tangent/personal opinion, AI art cannot be copywritten and therefore selling it would be a very messy area, so I do not think a company driven by profit and greed would invest so much in such a legally grey area)
Machine learning is a vast field , encompassing WAY More than just art. Please don't jump to assume just because AI is mentioned in a privacy policy that that means twitter is training a generative AI when everything else points to it being used for content moderation and profit like every other site uses it
Given how untrustworthy and just plain horrible Elon Musk is, it is VERY likely that one day twitter and xAI will use user's content to develop/train a generative AI that may have an art aspect aside from the science focus but for now it is just scanning your images- all of them- art or not- for recognizable content to sell for you and to improve that algorithm to better recognize stuff, the same way Tumblr does that but to detect if there's any nsfw elements in images.
WHAT TO DO AS AN ARTIST?
Everyone has a right to their own opinion of course ! Even just knowing websites collect and store this type of data on you is a valid reason to leave and everyone has their own right to leave any website should they get uncomfortable !
However, when people lie about what the TOS/privacy policy actually says and means and actively spread fear and discourage artists from using twitter, they're unintentionally only making things worse for artists with no where to go.
Yes twitter sucks but the sad reality is that it's the only option a lot of artists have and forcing them away from that for something that isn't even happening yet can be incredibly harmful, especially since there's not really a good replacement site for it yet that isn't also using AI / has that same TOS clause (despite it being harmless)
I do believe that one day xAI will being using your data and while I don't think it'll ever focus solely on art generation as it's largely science based, it is still something to be weary of and it's very valid if artists leave twitter because of that! Yet it should be up to artists to decide when they want to leave/deactivate and I think they should know as much information as possibly before making that decision.
There's also many ways you can protect your art from AI such as glazing it, heavily watermarking it, posting links to external sites, etc. Elon has also stated he'll only be using public tweets which means privating your account/anything sent in DMS should be fine!!
Overall, I just think if we as artists want any chance of fighting back against AI we have to stay vocal and actively fight against those who are pushing it and abandon and scatter at the first sign of ANY machine learning on websites we use, whether it's producing generative art content or not.
Finally, want to end this by saying that this is all just what I've researched by myself and in some cases conclusions I've made based on what makes the most sense to me. In other words, A Lot Could Be Wrong ! so please take this with a grain of salt, especially that second part ! Im not at all any AI/twitter expert but I know that a lot of what people were saying wasn't entirely correct either and wanted to speak up ! If you have anything to add or correct please feel free !!
28 notes
·
View notes
Text
What is the future of public health campaigns in a digital age?
The future of public health campaigns in the digital age is undergoing a profound transformation, driven by rapid technological innovation and the evolving needs of diverse populations. At the forefront is the power of personalization, enabled by artificial intelligence (AI) and big data analytics. These technologies allow health campaigns to move away from one-size-fits-all approaches and instead deliver messages that are tailored to individual behaviors, preferences, and health histories. Wearable devices, mobile apps, and social media platforms generate a wealth of real-time data, which campaigns can use to identify emerging trends, anticipate public health needs, and respond more effectively. This data-driven approach makes interventions not only more targeted but also more impactful.
Digital accessibility and inclusivity are critical in ensuring these campaigns reach all segments of the population, including those in remote or underserved areas. Telehealth platforms offer opportunities to disseminate health education and services to individuals who may otherwise lack access to traditional healthcare infrastructure. Furthermore, creating multilingual and multimodal content—such as videos, animations, interactive tools, and accessible text—ensures that public health messages resonate with people from various linguistic and cultural backgrounds. By adopting an inclusive design approach, campaigns can bridge gaps in communication and health literacy, addressing barriers that have historically excluded marginalized groups.
Emerging technologies such as virtual and augmented reality (VR/AR) are redefining how people interact with public health content. These immersive tools can simplify complex health topics, such as demonstrating how vaccines work or teaching people how to perform life-saving techniques like CPR. Gamification is another innovation that holds significant promise, as it turns health-promoting activities into engaging experiences. Fitness apps with rewards, interactive challenges, and games designed to educate while entertaining can motivate individuals to adopt healthier habits, fostering long-term behavioral change.
Social media platforms will remain a central pillar in future public health campaigns, particularly as they provide unparalleled opportunities for engagement and dialogue. Collaborating with influencers, especially micro-influencers trusted by their communities, can amplify messages to reach specific audiences effectively. Interactive campaigns, such as live Q&A sessions with health experts, community challenges, or user-generated content, create a sense of participation and trust. These platforms also allow for two-way communication, enabling health authorities to address public concerns, dispel myths, and build confidence in health interventions.
A major challenge in the digital age is the proliferation of misinformation, which can undermine public health efforts. Combating this will require robust strategies, including deploying AI tools to identify and counter false information in real time. Partnerships with fact-checking organizations and collaborations with social media platforms can help validate credible sources and ensure accurate information is prioritized. Building digital literacy among the public will also be essential, empowering individuals to critically evaluate health information and make informed decisions.
Equity and ethics will play a pivotal role in shaping the future of digital health campaigns. While technology offers immense potential, the digital divide—stemming from disparities in internet access, device availability, and digital literacy—must be addressed to ensure that no one is left behind. Combining digital campaigns with traditional methods such as radio broadcasts, community workshops, and printed materials can bridge these gaps and ensure equitable access. Data privacy and security will also be critical; as campaigns increasingly rely on personal data to tailor messages, implementing robust safeguards will be essential to maintain public trust and prevent misuse.
Finally, community-centric approaches will make campaigns more effective and sustainable. By engaging local communities in the creation and dissemination of campaign content, health authorities can ensure that messages are relevant, culturally sensitive, and authentic. Crowdsourcing ideas and feedback from the target audience fosters a sense of ownership and enhances the credibility of public health initiatives. Tailoring global health messages to reflect local contexts will further ensure resonance, helping campaigns overcome cultural and societal barriers to adoption.
Together, these advancements mark a shift toward more adaptive, inclusive, and impactful public health campaigns. Leveraging digital tools while addressing challenges like misinformation, inequity, and privacy concerns will be key to meeting global health challenges with speed, precision, and humanity. Public health in the digital age has the potential not only to inform but also to inspire communities worldwide to take collective action for better health outcomes.
2 notes
·
View notes
Text
Week 11 / Post 9
Does empirical evidence show that social media alone was sufficient to drive mobilization, or were other forms of media equally critical?
When it comes to social media alone it can drive mobilization based if certain groups have access to technology. Movements typically skyrocket through social media but in the case of Empirical social movements tend to have more face-to-face interaction for activism. For example, a research study from the Tahris data project surveyed Egyptian activists. “The survey shows that face-to-face interaction 93% was the most important form of activist protest communication, followed by television 92%, phones 82%, print media 57%, SMS 46%, Facebook 42%, email 27%, radio 22%, Twitter 12%, and blogs 12%”(Fuchs). This is a form of interpersonal communication another form of media that traditional and telecommunications were more important information sources and communication tools in the revolution than social media and the internet. The survey also claimed that Egyptian revolutionaries preferred phone communication, followed by face-to-face talk, as most important for their protest, informative, and motivating for practicing in the protest.
How does online activism enhance the effectiveness of protests and social movements?"
Online activism enhances the effectiveness of protests and social movements by taking advantage of the technologies and techniques offered by the internet to achieve their traditional goals and using either internet-enhanced or internet-based. The internet helps bring traditional ways to protest to the next level by reaching goals and having a better impact. This form of online activism would turn into cyber activism. Cyber activism enhances the whole movement by having three general areas which are awareness/advocacy, organization/mobilization, and action/reaction (Vegh). Having these areas helps send out information, or receive it, calls for action, and overall brings awareness to protest and social movements worldwide.
How do online networks help activists get ready for political change?
Online networks help activists bring awareness to political change by helping people obtain information by participating in different types of email distribution lists. Information distribution on the internet is another way for activism. This form of activism creates distribution networks that organizations and social movements that can be used for mobilization purposes. For example, Tedjabayu (1999) reports on the NusaNet Consortium Consortium restricted and Pretty Good Privacy (PGP)-an encrypted inter-NGO e-mail system- created to disseminate alternative news among themselves and to the larger population (Vegh). When serious violations of human rights occur, the internet is essential in reporting the cruelty to the outside world. This can trigger and fuel an activist movement by the use of the internet. This form of email distribution proves how useful these networks are when the moment for political change arrives.
Why might alternative narratives, like those on Black Twitter, be important for communities that feel marginalized by mainstream media?
Alternative narratives on Black Twitter are important to marginalized groups in mainstream media because they provide a space for black people to be able to share their stories, correct biased information, and prevent stereotypes that the black community faces on online media. For example “Meredith Clark, a scholar researching black Twitter, and Kimberly Elise, author of The Bombastic Brilliance of Black Twitter, argue that black Twitter can be a space for jokes, for social viewing of a television series, and as a space where people can voice anger and frustration” (A. Lee). The black community uses this as a way to have power over the misinformation that is spread by racial stereotypes. Black Twitter uses # to generate the message to the black community to bring awareness. The idea is that users, through the creation of ironic, yet cutting-edge hashtags, create a space to address social issues of racial bias and discrimination. Another example is “the black Twitter hashtag #APHeadlines is a great example of textual poaching as resistance. This hashtag was created in response to the Associated Press tweet about the conviction of the Detroit man who shot Renisha McBride. McBride was a young woman of color who was looking for help after a car accident”(A. Lee). Bring awareness to the injustice that Renisha Mcbibe's family is facing, this can help start movements to fight for unfair treatment.
Lee, L. A. (2017, March 5). Black twitter: A response to bias in mainstream media. MDPI. https://www.mdpi.com/2076-0760/6/1/26
Vegh, S. (2007). Cyberprotesting globalization: A case of online activism. Governance and Information Technology, 208–212. https://doi.org/10.7551/mitpress/7473.003.0027
Fuchs. Communication Power and the Arab Sping.pdf
#wgst320f24
5 notes
·
View notes
Text
Did Russia Really Fine Google $20,000,000,000,000,000,000,000,000,000,000,000?
Lately, the internet’s been buzzing with a mind-bending headline: “Russian Court Fines Google $20,000,000,000,000,000,000,000,000,000,000,000!” Let’s be real for a second — how many zeros is that, anyway? Thirty-six? More than most of us would ever count in a lifetime! But before we let our jaws drop too far, let’s take a closer look at the story. Did a Russian court really throw the world’s wildest fine at the tech giant? Let’s dive into what’s real, what’s exaggerated, and what this rumor might actually be about.

The Rumor’s Origins
First, where did this astronomical number come from? It seems this “fine” may have originated as an exaggerated report on previous legal disputes between Google and Russian authorities. Russia has indeed fined Google before, and it often hits tech giants like Meta and Google with big penalties over issues such as content regulation, data privacy, and competition concerns. However, these fines — while hefty — have never approached even a fraction of the $20 gazillion figure flying around.
How Big is $20 Gazillion?
To put things in perspective, the world’s entire GDP is estimated to be around $105 trillion. So a $20 septillion fine is… let’s say out there! It’s just impossible to imagine Russia or any country imposing a fine that would take trillions of times more than all the money that exists in the world to pay off. Not to mention, Google isn’t worth even close to that much!
Why Would Russia Fine Google in the First Place?
Russia and Google have clashed on a few issues over the years. Russian courts have fined Google over certain policies, like failing to remove what Russia considers “illegal” content or protecting data privacy of Russian users. Recently, penalties have focused on content removal — if Google doesn’t remove specific types of content that Russia flags, fines ensue. While these fines are indeed big, they’re nowhere near $20 septillion. The actual fines are typically in the millions or billions (which is still a lot) but never close to something that would break all math records.
Internet Exaggeration at Its Best!
It’s likely that someone saw “$20 million,” “$20 billion,” or even “$20 trillion” and decided to toss on a few extra zeros for dramatic effect. Let’s remember, the internet is a fertile ground for rumors, and if there’s one thing we can count on, it’s that numbers can get wildly inflated when they travel through social media and forums.
What’s the Real Takeaway?
In the end, Google is not facing a $20 septillion fine from Russia — thankfully for everyone’s sanity! But this story highlights something we should all keep in mind: in the digital age, misinformation spreads quickly. A good rule of thumb is to check reliable news sources for confirmation before believing everything we see on our feeds. Sometimes a quick search or a fact-check can make all the difference!
Final Thoughts
While a $20 gazillion fine makes for a juicy headline, it’s just too wild to be real. But hey, it’s a reminder of the power of a good headline — and the importance of digging a little deeper to get the truth!
2 notes
·
View notes
Text
“Evolutionary Intelligence: How Technology Will Make Us Smarter”
I picked this video titled “Evolutionary Intelligence: How Technology Will Make Us Smarter” featuring Professor W. Russell Neuman. This topic looks at how AI can enhance the way humans think and make decisions. Neuman talks about “evolutionary intelligence,” which shows how humans have changed throughout history—from hunting and gathering to using advanced tech like AI. He thinks that AI has the potential to assist us in addressing our self thinking mistakes and enhance our abilities in aspects such as creativity, managing privacy, and even in our relationships.
Professor W. Russell Neuman is recognized as an expert in media technology and digital communication. His research looks at how technology affects the way people interact and make decisions. This makes his work important for me, especially as someone studying cybersecurity, because AI and digital technology are closely connected to what I'm learning. Learning about how AI impacts data security and privacy is really important for anyone studying cybersecurity.
In the discussion, Neuman addresses key questions regarding AI, including its potential to address human biases and its role in finding misinformation. He discusses how AI can help with privacy management by using smart agents and tools that will make the work easier for users. Neuman points out that the regulation of AI should be influenced by market strategy rather than strict government regulations.
I chose this video out of the 70 options because it relates closely to my interests in cybersecurity. AI is really important for security systems and data management, so I need to learn how AI can help make privacy and security better. Neuman’s ideas about regulating AI and safeguarding personal data are really important for my studies, which is why this topic caught my attention.
2 notes
·
View notes
Text
PLEASE READ: We can't take stuff like this lightly!!
There is a spot here where you can contact your members about what you think of this bill.
I've been trying really hard to work through reading over this and understanding it instead of just trusting what other people say.
This has me very worried. Democrats and Republicans are pushing this and Biden himself. I agree with what people are saying that this will result in mass censorship and violate all of our privacy.
It's very vague as to what constitutes harm to minors and leaves it open for people to argue what is harmful. I think we all know where this is going with all the anti-LGBT laws that are being pushed (under the guise of protecting children!!). This would apply to every site where people post and share things. I don't see how every site could ethically determine how old a user is. Some articles are bringing up how in Utah a law passed that required age verification on porn sites which meant they either required you to upload you ID or upload your face to be scanned. So Pornhub just stopped serving Utah altogether. How could every site possibly keep that data safe? How many sites can even afford that? Would this then push out every site that does not have the funds to follow the law? I'm really worried about ao3 as writing fanfiction is my main hobby.
I think the worst part is that some of this seems reasonable and I can see how people (especially older non internet era people *cough cough* our lawmakers) could be convinced. Especially about the type of ads shown to minors etc.
This bill has passed the first step and will be voted on in the Senate. I know a lot of people probably find these posts to be fearmongering but they've been pushing this bill for years and this year it has more cosponsors (43)! Roe v Wade was overturned and people said that would never happen. The direction of our country is really scaring me. We can't take things lightly!!
Please look into contacting your senators! There are multiple ways. I'm still researching to determine the best way. I know there are scripts to help and I plan on calling despite my phobia of phone calls. 😭
I'm currently working on writing up a master post about this but I'm terrible at these things and don't want to accidentally spread misinformation. So if anyone has a really good one that I could blaze I'd be willing to do that too.
#kosa#stop kosa#kids online safety act#us politics#politics#ao3#lgbtqia#lgbt#bad internet bills#if i said something wrong let me know#or have more insight#im really struggling to follow these things but i think its so important
21 notes
·
View notes