#intercep
Explore tagged Tumblr posts
Text
I was like a kid!fic from RQG would be so cute than I realized that the only people that would be kids at the same time is Bertie, Sasha and Hamid (if we count NPCs Carter, Wilde and Barnes as well).
So now instead I want a kid!au but is actually just Cel takes a very different path on their post-America journey and ends up acidentally taking everyone else under their wing.
Literally just:
1. Cel goes to Svalbard and hears about an sccident on the mines. Acidentaly interceps older teen Zolf and after acidentaly annoying the shit out of Zolf offers Zolf the scape route he would otherwise take with the navy by mentioning they neen an assistant.
2. Cel goes to England. Acidentaly gets a job as a chemistry teacher at a prestigiou school. There they notice sweetheart new transfer student Hamid being peer pressured into becaming a bully. So they ask to talk to Hamid in their room and offer Hamid support. Thanks to that Hamid gains news friends and a new favorite teacher he goes for guidance everytime and can use to project a healthy father figure.
3. Cel is still in England but they can't have just one job so they also settle shop. Someone keeps robbing things from the shop and Cel keeps building new intricate traps to catch the robbers mostly as a fun game than any anger at them. They finally catch Sasha and Brock except instead of angry they are very exited about how the kids were abble to work around the traps and Sasha is cautelously very exited about how Cel build the traps. Sasha slowly relaxes (wich in turn calms Brock) and as she starts firing blunt trap questions Cel starts getting more hyped. They fully rescue/kidnapp Sasha and Brock from Barret.
4. Cel moves to Amsterdam to run from Barret (they leave Zolf with the store and gift a mkbile stone to both now an adult Zolf and favorite student in need Hamid so they can keep contact) and acidentaly ends up witnessing the murder of a goblin pack. They get to late to save the pack but not to late to rescue their one surviving member baby Grizzop.
5. Cel finds a place to settle down at a small town in Kenya. Their are neighboors with Azu's family and they get along super duper well with their neighbors.
(Tbh I think I can even make Cel adopt most supporting NPCs except the kobolds because Shoin sucks, Einstein because too old and maybe Earhart cause I have no idea of even an estimate age for her).
#rqg au#cel acidentaly gets in situations is their whole carear#cel sidebottom#rusty quill gaming#rqg#sasha rackett#no idea how to make cel adopt bertie nor if i want to#maybe in this au bertie studies in hamids middle school as well#zolf smith#rqg azu#grizzop drik acht amsterdam#tbh this was mostly a cel adopts sasha and brock au and the rest was incidental#btw I see cel more as a older sibbling figure to everyone's and not a parent#even tho cel cannonically had kids
22 notes
·
View notes
Text

Marine Air’s Dark Day at Midway
Marine Aircraft Group 22’s experience at the Battle of Midway serves as a hard lesson in trying to do too much with too little.
The 4th of June 1942 was a very bad day for Marine Corps aviation. At the Battle of Midway, Marine Aircraft Group (MAG) 22 suffered terrible losses and contributed little to the U.S. Pacific Fleet’s spectacular victory that day. The group’s fighting squadron, VMF-221, lost far more aircraft than its pilots shot down. Its dive-bomber squadron, VMSB-241, suffered staggering losses without hitting a single Japanese ship.
Midway historians have thoroughly chronicled the actions of these two squadrons and touched on some reasons for their performance. The most cited causes are the obsolescence of Marine aircraft and the inexperience of Marine aviators.1 A closer examination of archival material reveals additional factors that impaired the group’s performance at Midway and new insights into why MAG-22 sent such green pilots into battle.
The heart of MAG-22’s troubles lay in its two competing missions: While forward deployed to defend an advanced base, the group also served as a de facto training command for new aviators. This alone would have undermined its combat readiness. But additional factors worked against MAG-22. In the weeks before the battle, the flight hours the group devoted to training were limited by its responsibilities to defend Midway Atoll and by logistical shortfalls. During the battle, Naval Air Station Midway and MAG-22 were unable to coordinate aircraft from three services based at the atoll. Finally, imprecise direction from Pacific Fleet commander Admiral Chester W. Nimitz led to misunderstandings of how MAG-22 would employ its fighting squadron.
Present-day naval commanders are acutely familiar with the challenge of balancing combat readiness and forward presence. As naval leaders look for ways to maintain Navy and Marine Corps forces in the western Pacific and prepare for possible conflict there, the experience of MAG-22 at Midway provides a sobering reminder of the risks of attempting to do too much with too little.
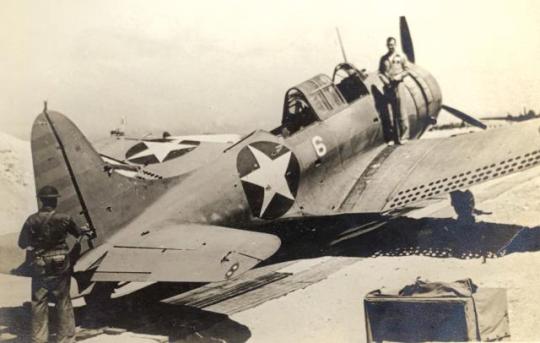
At Midway, First Lieutenant Daniel Iverson stands on a wing of his shot-up SBD-2 Dauntless, one of MAG-22’s 46 aircraft losses in the Battle of Midway. Later repaired in the United States, the restored SBD is now an exhibit at the National Naval Aviation Museum in Pensacola, Florida.
At Midway, First Lieutenant Daniel Iverson stands on a wing of his shot-up SBD-2 Dauntless, one of MAG-22’s 46 aircraft losses in the Battle of Midway. Later repaired in the United States, the restored SBD is now an exhibit at the National Naval Aviation Museum in Pensacola, Florida. National Naval Aviation Museum
MAG-22’s Very Bad Day
At 0555 on 4 June 1942, Midway’s radar detected a large formation of aircraft 93 miles northwest of the atoll. MAG-22’s siren wailed. In accordance with orders issued the previous evening by Lieutenant Colonel Ira L. Kimes, the commander of MAG-22, VMF-221 launched its aircraft immediately. A detachment of six Navy TBF Avengers took off next, followed by four Army Air Forces B-26 Marauders armed with torpedoes. The TBFs and B-26s proceeded independently to attack the Japanese carriers. The 16 SBD-2 Dauntlesses and 12 SB2U-3 Vindicators of VMSB-241 took off last and rendezvoused about 20 miles east of Midway’s Eastern Island.2
VMF-221’s commanding officer, Major Floyd B. Parks, had organized his 21 F2A-3 Buffalos and seven F4F-3 Wildcats into four divisions of Buffalos and one of Wildcats. All but one F2A-3 and one F4F-3 were mission ready and got airborne, though the divisions became slightly disorganized during the hasty scramble. The Japanese strike consisted of 108 aircraft—36 Aichi D3A “Val” dive bombers, 36 Nakajima B5N2 “Kate” carrier attack aircraft, and 36 Mitsubishi A6M2 “Zeke,” or Zero, fighters. In accordance with Kimes’ plan, MAG-22’s fighter direction center funneled all five of VMF-221’s divisions to intercept the incoming strike. The Marines had the altitude advantage, and the separate divisions launched a series of overhead gunnery passes against the Japanese bomber formations. As the slower Marine aircraft recovered for additional passes, the nimbler Zeros overtook them and sent one after another tumbling downward.3
There is little doubt VMF-221 got the worst of the fight. The Japanese shot down 15 Marine fighters and severely damaged another nine, leaving just one F2A-3 and one F4F-3 ready to fly. Though Kimes afterward estimated Japanese losses at 43 aircraft, his surviving pilots definitively claimed just nine victories. Kimes’ estimate included “probable victories by missing fighter pilots” as well as claims by rear-seat gunners of VMSB-241.4 The actual total was far lower. VMF-221 probably shot down just three aircraft outright. Another 16 Japanese aircraft survived the raid but either ditched or were so irreparably damaged they could not fly again.5
A PBY Catalina flying boat had spotted the Japanese carriers, and MAG-22 passed their location to VMSB-241.6 Major Lofton R. Henderson, the squadron commander, led the SBDs. Major Benjamin W. Norris, the executive officer, led the SB2Us. While Henderson took his unit to 9,000 feet, Norris climbed to 13,000 feet.7 On paper, the SB2U-3s were nearly as fast as the SBD-2s, but the two flights proceeded independently.8
Because the Marine dive bombers were slower than the TBFs and B-26s, had taken off last, and had flown east before heading northwest, VMSB-241 did not attack until a half hour after the TBF and B-26 attacks had ended. The Japanese combat air patrol had shot down five of the six Avengers and two of the four Marauders; none had scored a hit. When Henderson and his SBDs spotted the carrier Hiryū at about 0755, the Japanese combat air patrol still had 13 fighters aloft.9
Henderson conducted a glide-bombing attack. A dive-bombing attack would have facilitated bombing accuracy and complicated fighter gunnery and antiaircraft solutions. But more than half of Henderson’s pilots were too inexperienced to attempt the technique, and the cloud cover would have made dive bombing particularly difficult.10
The combat air patrol’s Zeros attacked Henderson first. On their second pass, they sent him down in flames. The remaining SBDs continued the gliding attack. One by one, the Marines released their bombs—and missed. Some came petrifyingly close for the Hiryū’s crew, and many Marines mistakenly believed they had scored hits.11
Norris and his Vindicators arrived at about 0820, less than ten minutes after the surviving SBD-2s had departed and amid an attack by Army Air Forces B-17 Flying Fortresses. The combat air patrol had doubled to 26 fighters. Norris descended through the clouds toward the carrier Akagi. The Zeros could not find the dive bombers as long as they were in the safety of the cloud bank, but neither could the Marines see the ships below. When they emerged at 2,000 feet, they saw only the battleship Haruna. Norris also attempted a gliding attack. The Haruna maneuvered evasively, neatly avoiding every one of the Marines’ bombs. The SB2Us hugged the surface and flew back to Midway.12 Only 8 of VMSB-241’s 16 SBD-2s and 8 of its 12 SB2U-3s returned.13
VMSB-241 conducted two more strikes during the battle. That evening Norris led five SB2U-3s and six SBD-2s in a vain search for burning carriers. They found nothing, and Norris did not return, lost in the inky, moonless squalls. On 5 June, VMSB-241 attacked the cruisers Mogami and Mikuma. The squadron lost another Vindicator to antiaircraft fire and again scored no hits.14
What Was Done Well
MAG-22 did some things remarkably well in its first action. Due to superb intelligence and early warning, no airworthy planes were caught on the ground. The fighter direction center placed the fighters in an optimum intercept position. The dive bombers located the Japanese carriers. Most impressively, every fighter and dive-bomber pilot attacked without hesitation into the teeth of a formidable defense.
MAG-22’s efforts indirectly contributed to the destruction of the Akagi and two other carriers, the Kaga and Sōryū, later that morning. As historians Jonathan Parshall and Anthony Tully demonstrated, the cumulative effect of the series of failed attacks by bombers from Midway and U.S. carriers created conditions that delayed Admiral Chūichi Nagumo’s counterattack and placed his carriers at greater vulnerability to the dive bombers from the USS Enterprise (CV-6) and Yorktown (CV-5). Dodging the attacks required the carriers to maneuver violently. Defending against them required the carriers to launch and recover fighters. Perhaps just as important, Nagumo faced a series of menacing dilemmas, complicating his decision-making. When the dive bombers from the Enterprise and Yorktown appeared overhead at 1020, Kates and Vals were still below on the hangar decks, where their fuel and ordnance amplified the destructive power of the American bombs.15
VMF-221 also helped reduce the strength of Nagumo’s counterpunch when it did come. The only carrier that survived the Enterprise and Yorktown dive-bomber attacks was the Hiryū. It was her air group that VMF-221 had attacked. Though the Marine fighters shot down just two Kates outright, another seven Kates were shot down by Marine antiaircraft guns, ditched, or were too damaged to participate in the strikes against the U.S. carriers.16 In other words, the Marines did not bring down many aircraft, but the ones they did bring down were the right ones—aircraft from the Hiryū’s air group.
Nonetheless, 4 June had been an awful day for MAG-22. It had lost many aircraft, shot down only a handful of the enemy, and hit no ships. Forty-two MAG-22 Marines had died; 36 pilots and gunners were missing; and six Marines had been killed in the bombing of Eastern Island.17
‘Not a Combat Airplane’
On 17 April, Major (soon to be Lieutenant Colonel) Ira L. Kimes (below) landed at Midway Atoll to replace Lieutenant Colonel William Wallace as MAG-22 commander. Accompanying Kimes were six second lieutenants, green aviators who replaced six captains, seasoned fliers, who left the atoll with Wallace three days later. Public Domain

Every surviving Marine fighter pilot from VMF-221 attested to the superiority of the Zero over the Marine fighters. Captain
The F2A-3 is not a combat airplane. It is inferior to the planes we were fighting in every respect.
It is my belief that any commander that orders pilots out for combat in a F2A-3 should consider the pilot as lost before leaving the ground.18
Kimes agreed. In his endorsement to his aviator’s statements, Kimes recommended that the fleet relegate the F2A-3 Buffalo, the F4F-3 Wildcat, and the SB2U-3 Vindicator to training commands.19
The Vindicator was indeed past its usefulness. However, there is evidence that neither fighter was to blame for VMF-221’s poor performance. With improved tactics, Marine and Navy pilots would achieve far better results with the F4F in the Solomons. Captain Marion Carl, the only Marine to shoot down a Zero over Midway, believed the F2A-3 was as maneuverable and fast as the F4F-3, and its only drawbacks were that it could not absorb punishment and was less stable as a gunnery platform than the Wildcat.20
Some British and Dutch Buffalo aces, whose squadrons suffered grievously against Imperial Japanese Navy Zeros, attributed their lopsided outcome to Japanese proficiency and numbers rather than the Buffalo’s inferiority. Finnish Buffalo pilots enjoyed great success flying the planes against the Soviets.21 The Buffalo’s mixed performance in other theaters suggests that other factors contributed to VMF-221’s poor performance.
‘Half-Baked Flyers’
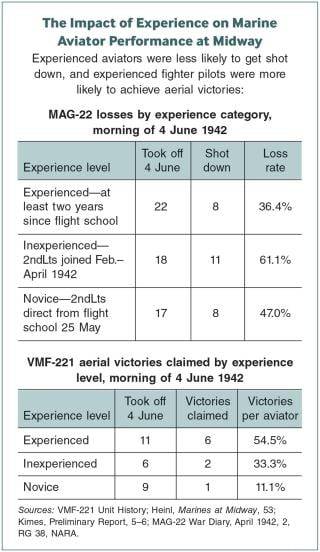
When VMF-221 and VMSB-241 had landed on Eastern Island in December 1941, both squadrons were top heavy with experience. VMF-221’s most junior pilot had been flying for at least a year since flight school.22 But the 57 aviators who flew on 4 June included 35 second lieutenants, none of whom had been with their squadron more than four months, and 17 of whom had arrived on 27 May directly from flight school.23

SB2U-3 Vindicator dive bombers take off from Midway’s Eastern Island in early June, possibly to attack Japanese carriers the morning of 4 June. While inferior aircraft—including Vindicators—were factors in MAG-22’s poor performance at Midway, tactics and training played key roles.
SB2U-3 Vindicator dive bombers take off from Midway’s Eastern Island in early June, possibly to attack Japanese carriers the morning of 4 June. While inferior aircraft—including Vindicators—were factors in MAG-22’s poor performance at Midway, tactics and training played key roles. U.S. Naval Institute Photo Archive
In the first half of 1942, Marine aviation had two conflicting missions: defending the fleet’s advanced bases and training new aviators. Newly winged aviators reported to the fleet with just 200 hours of flight time, and none in the aircraft they would fly in combat.24 The new aviators needed operational training, but the aircraft they needed to train in were defending advanced bases in the Pacific.
On 8 January 1942, Brigadier General Ross E. Rowell, the commander of 2d Marine Air Wing, described the dilemma in a letter to Vice Admiral William F. Halsey Jr., the commander of Aircraft, Battle Force, Pacific Fleet: “I have now accumulated 35 second lieutenants in various stages of advanced training. . . . If ComAirBatFor approves and you want some half-baked flyers, send me a dispatch to that effect.” Halsey approved; he directed Rowell to order the green fliers to squadrons like VMF-221 and VMSB-241.25 This decision set in motion a sequence of personnel transfers that diluted the combat readiness of forward-deployed squadrons. As inexperienced aviators joined squadrons at advanced bases, experienced aviators left to form new squadrons in Hawaii and California.
Marine aviation was still following its prewar training pipeline. Once students were designated naval aviators, they reported to squadrons in the Fleet Marine Force for about a year of operational flight training in combat aircraft.26
Not only did MAG-22 not have a year to train its new aviators, but the group’s commitment to the defense of Midway also required it to devote most of its operational flights to patrols and radar calibration vice gunnery and tactics. Less than 30 percent of VMF-221’s missions from December 1941 to May 1942 were dedicated to improving the lethality of its fighter pilots.27
Logistics shortfalls further impinged on the group’s training. A shortage of .50-caliber machine-gun ammunition often limited gunnery practice to dummy runs.28 In the final week before combat, PBY Catalinas and B-17 Flying Fortresses drew thirstily from Midway’s fuel stocks, which were already limited due to an incredible blunder. On 22 May, demolition charges placed at an underground fuel storage facility detonated when one of the defense battalion batteries fired its 11-inch guns. The station lost 375,000 gallons of precious aviation fuel and its pipeline to Eastern Island.29 The resulting shortage prevented the group from providing the 17 Marines fresh out of flight school with anything more than familiarization flights. VMSB-241 could not even check out its new pilots in their SBDs.30
Without question, MAG-22 fought the Battle of Midway with inferior aircraft and many “half-baked” pilots. Though the odds were stacked against the group’s aviators, command decisions may have stacked the odds higher than they needed to be.
‘No Organized Plan Whatsoever’
In a 1966 interview, MAG-22’s former executive officer stated there had been “no organized plan whatsoever” to coordinate Midway’s Army Air Forces, Navy, and Marine aircraft.31 Though not strictly true, his characterization betrays how Naval Air Station Midway and MAG-22 struggled to coordinate air operations.
In anticipation of the coming fight, Nimitz had abundantly reinforced Midway. In addition to MAG-22, Midway’s air force included 31 PBYs, 17 B-17s, the 4 B-26s, and the 6 TBFs. Nimitz assigned tactical control of all these to the naval air station commander, Navy Captain Cyril T. Simard, and sent an experienced aviator and a naval base air defense detachment to coordinate air operations.32
While the naval air station directed scouting operations superbly, integrating the bombers in a coordinated strike proved beyond its reach. Each aircraft type attacked without regard to the next, permitting the Japanese the opportunity to fend off each in turn. As Kimes observed in perfect hindsight, “It would have been better had they arrived simultaneously.”33
Coordination was exacerbated by the physical separation of the naval air station and MAG-22 command posts. Simard and his air operations officer were on Sand Island; Kimes and his command post were on Eastern Island. According to Kimes’ executive officer, the “Marines ran their own show” but did not command the other services’ bombers on Eastern Island, including the six Navy TBFs.34
Kimes’ air group struggled to coordinate its own aircraft. VMSB-241 does not seem to have attempted to integrate its SBD and SB2U attacks. Most puzzlingly, MAG-22 allocated no fighter protection to VMSB-241 for its strike against the Japanese carriers.
‘Go All Out for the Carriers’

Kimes employed his fighting squadron in what Marine Corps doctrine termed “general support.” As then–Major William J. Wallace lectured Marine officers at Quantico in 1941, general support was an offensive mission that allowed fighters the freedom to be “on the prowl.” In contrast, missions that tied fighters to protection missions, such as escorting bombers, were termed “special support.” As a fighter pilot, Wallace clearly favored the freedom to go find trouble and emphasized, “The rule, then, for the employment of fighter units should be-—general support wherever and whenever possible.”35
In January 1942, now–Lieutenant Colonel Wallace took command of Marine aviation on Midway, which he retained until relieved by Kimes in April. It was Wallace who had developed the fighter direction system MAG-22 employed for defense of the atoll. As Wallace’s views on fighter employment reflected Marine Corps doctrine, and Wallace commanded MAG-22 until two months before the battle, this bias likely influenced Kimes’ decision to place all of VMF-221 in general support on 4 June.
MAG-22’s fighter employment stands in stark contrast to how Japanese and U.S. carrier task forces operated on 4 June. Carriers were far more vulnerable to air attack than an island base. Nonetheless, every Japanese and American task force commander allocated fighter escorts to increase their bombers’ chances of getting through the enemy’s fighters.
Hitting the Japanese fleet was exactly what Nimitz had in mind when he reinforced Midway with so many aircraft. On 20 May, Nimitz provided the Chief of Naval Operations and Commander-in-Chief of the U.S. Fleet, Admiral Ernest J. King, with some views on the role of land-based aircraft he had drawn from the recent Battle of the Coral Sea:
The shore commander should assign attack missions designed to render the greatest possible assistance to the Fleet Task Force when it is engaged and should particularly be ready to provide fighter protection when it is practicable.36
Nimitz incorporated these views in his planning guidance for Midway. In a 23 May memorandum to his chief of staff, Captain Milo F. Draemel, Nimitz explicitly directed that “Midway planes must thus make the CV’s [aircraft carriers] their objective, rather than attempting any local defense of the atoll.”37 In an undated memorandum likely written about the same time, Nimitz reiterated his intent to Captain Arthur C. Davis, his air officer:
Balsa’s [Midway’s] air force must be employed to inflict prompt and early damage to Jap carrier flight decks if recurring attacks are to be stopped. Our objectives will be first—their flight decks rather than attempting to fight off the initial attacks on Balsa. . . . If this is correct, Balsa air force . . . should go all out for the carriers . . . leaving to Balsa’s guns the first defense of the field.38
But in his operations order for Midway, Nimitz was less clear in the tasks he assigned to Simard at Midway:
(1) Hold MIDWAY.
(2) Aircraft obtain and report early information of enemy advance by searches to maximum practicable radius from MIDWAY covering daily the greatest arc possible with the number of planes available between true bearings from MIDWAY clockwise two hundred degrees dash twenty degrees. Inflict maximum damage on enemy, particularly carriers, battleships, and transports.
(3) Take every precaution against being destroyed on the ground or water. Long range aircraft retire to OAHU when necessary to avoid such destruction. Patrol planes fuel from AVD [seaplane tender] at French Frigate Shoals if necessary.
(4) Patrol craft patrol approaches; exploit favorable opportunities to attack carriers, battleships, transports, and auxiliaries. Observe KURE and PEARL and HERMES REEF. Give prompt warning of approaching enemy forces.
(5) Keep Commander-in-Chief, U.S. Pacific Fleet and Commander Hawaiian Sea Frontier fully informed of air searches and other air operations; also the weather encountered by search planes.39
The very explicit language Nimitz used in his planning guidance—that Midway’s aircraft “should go all out for the carriers”—is not reflected in his order. Absent such direction, Simard left it to Kimes to command the Marine squadrons as he saw fit. In accordance with Marine Corps doctrine, Kimes placed his fighting squadron in general support over Midway—and sent his dive bombers against the Japanese fleet without fighter escorts. Had he allocated one or two divisions from VMF-221 to escort VMSB-241, more Marine dive bombers may have survived to drop bombs on the Hiryū, and their accuracy may have improved had they attacked with less interference from the Japanese combat air patrol.
Trying to Do More with Less
MAG-22 had not gone all out for the carriers but had massed its fighters in defense of Midway. Naval Air Station Midway had struck the Japanese carriers with every bomber available but had been unable to coordinate their attacks to increase their chances for success and survival. Most tragically, many of the Marines lost in the battle were just not ready to fight the Imperial Japanese Navy, despite their willingness and eagerness to try.
MAG-22’s very bad day is a cautionary tale. Trying to do more with less—in MAG-22’s case, trying to defend Midway while training novice aviators—carries risks that may be hidden until they are exposed through combat. In his report of the battle, Kimes included a page and a half of candid comments and recommendations.40 After Midway, Marine aviators applied the lessons MAG-22 had learned at enormous cost and achieved spectacular results against the same foe in the Solomons, often under the leadership of aviators who had survived Midway.
Those same lessons are noteworthy today. Naval experts have cautioned the naval services against maintaining too much forward presence with too little fleet.41 An enduring lesson of MAG-22 may be that very bad days result from very bad choices, and that choosing to do more with less is often a very bad choice.
13 notes
·
View notes
Text
Exploring the Perks of Using the Best DIY IMSI Catcher
The best DIY IMSI catchers assist you in spotting vulnerabilities in mobile networks. You can use them to test the resistance power of networks in terms of unauthorized access. You can check the spoofing vulnerabilities with the help of these devices. When you buy an IMSI catcher or drone jammer, you must identify the best technology solution provider.
0 notes
Text
Iranian Warning Problems Once US Helps Israel Intercep Missiles
Iranian Warning Problems Once US Helps Israel Intercep Missiles – CBS News See CBS News Iran and Israel exchanged missile fire for the night again. Earlier this week Israeli troops used drones, military aircraft and hidden operatives to orientation to Iran's nuclear program. The Iranian regime has issued a warning to the United States, the United Kingdom and France, saying that they would be…
0 notes
Text
Iranian Warning Problems Once US Helps Israel Intercep Missiles
Iranian Warning Problems Once US Helps Israel Intercep Missiles – CBS News See CBS News Iran and Israel exchanged missile fire for the night again. Earlier this week Israeli troops used drones, military aircraft and hidden operatives to orientation to Iran's nuclear program. The Iranian regime has issued a warning to the United States, the United Kingdom and France, saying that they would be…
0 notes
Text
starter for @tealeavesandthorns

"Hey, hey! Sorry to come up to you like this," he says, easy grin on his face as he interceps her mid hallway. "I’m Kevin's uncle. Kevin Rojas? Chamaco latoso," he says with a wide grin, shaking his head like he's fond of the kid despite everything.
"I don't know if you've heard but his folks are splitting up. It's messing with his head a little, and I'm worried it's starting to bleed into school." His tone a little more serious now, playing the concerned relative role too well.
"Kev told me you're his favorite teacher. La mera mera. So I thought, maybe..." He shrugs, keeping the smile easy. "Any chance you do private tutoring? Nothing crazy, just a once or twice a week. Kid could use a little extra push, you know?"
1 note
·
View note
Link
0 notes
Photo

LEUCHTTURM Capsulas para monedas 41 mm. ULTRA INTERCEPT (10) 13,95 €. ULTRA Intercept – la única cápsula redonda en el mundo con protección activa contra la oxidación. El anillo de espuma de 3 mm de espesor, insertado en las cápsulas, se basa en tecnología Intercept, patentada hace más de 30 años. Las partículas de cobre en el material neutralizan las sustancias nocivas existentes en la atmósfera, protegiendo así a las monedas de la coloración (protección garantizada durante 15 años). Medida exterior: 53mm. Ref.359435 Categoría: Capsulas redondas Ultra Intercep. Más información en: https://www.todonumismatica.com/leuchtturm-capsulas-para-monedas-41-mm-ultra-inter-24865.html
0 notes
Video
youtube
Los responsables de seguridad de los Juzgados de Plaza Castilla intercep...
0 notes
Video
China-Taiwan Tensions! US Deploys Warships to Taiwan Strait to Intercep...
0 notes
Text
was ist integrierte vpn
🔒🌍✨ Obtén 3 Meses GRATIS de VPN - Acceso a Internet Seguro y Privado en Todo el Mundo! Haz Clic Aquí ✨🌍🔒
was ist integrierte vpn
Definición de VPN integrado
Un VPN integrado es una característica que se encuentra en muchos dispositivos y sistemas operativos modernos, que permite a los usuarios conectarse de forma segura a una red privada a través de Internet. La sigla VPN significa Virtual Private Network o Red Privada Virtual en español.
La principal función de un VPN integrado es proteger la privacidad y la seguridad de la información transmitida a través de Internet, permitiendo a los usuarios navegar de forma anónima y segura. Al conectarse a una red privada a través de un VPN integrado, la información se cifra, lo que significa que solo el remitente y el destinatario pueden acceder a ella.
Además de proteger la privacidad, un VPN integrado puede utilizarse para acceder a contenido restringido geográficamente, ya que al conectarse a un servidor ubicado en otro país, los usuarios pueden hacer que parezca que se encuentran en esa ubicación para acceder a determinados servicios o páginas web.
En resumen, un VPN integrado es una herramienta clave para proteger la privacidad en línea y la seguridad de la información. Cada vez más dispositivos y sistemas operativos incorporan esta función de forma nativa, lo que facilita su uso y promueve una experiencia de navegación más segura y libre en Internet.
Ventajas del VPN integrado
Un VPN integrado es una herramienta clave en la protección de la privacidad y la seguridad en línea. Entre las ventajas que ofrece el uso de un VPN integrado se encuentra la capacidad de enmascarar la dirección IP del usuario, lo que permite navegar por Internet de forma anónima y proteger los datos de posibles ciberataques. Además, al utilizar un VPN integrado, se puede acceder a contenido restringido geográficamente, como servicios de streaming, juegos en línea y páginas web, aumentando así la libertad y la diversidad de opciones en línea.
Otra ventaja importante es la encriptación de la información transmitida a través de la red, lo que garantiza la confidencialidad de los datos personales y financieros frente a posibles hackers o espías cibernéticos. Asimismo, el uso de un VPN integrado proporciona una capa adicional de seguridad al conectarse a redes públicas de Wi-Fi, evitando posibles vulnerabilidades y protegiendo la información sensible de cualquier intrusión.
Además de la privacidad y la seguridad, un VPN integrado también puede mejorar la velocidad y la estabilidad de la conexión a Internet al optimizar el tráfico de datos y reducir la latencia. Esto resulta especialmente útil para aquellos que realizan actividades en línea que requieren un ancho de banda óptimo, como conferencias virtuales, descargas de archivos pesados o transmisiones en directo.
En resumen, las ventajas del VPN integrado son múltiples y variadas, ofreciendo una solución integral para proteger la privacidad y la seguridad en línea, así como para acceder a contenido restringido y aumentar la velocidad y estabilidad de la conexión a Internet.
Implementación del VPN integrado
La implementación del VPN integrado es una solución cada vez más popular entre empresas de todos los tamaños que buscan proteger la privacidad y seguridad de sus datos en línea. Un VPN integrado combina la funcionalidad de una red privada virtual con las características de hardware y software de un sistema informático, lo que lo convierte en una opción conveniente y eficaz para asegurar la comunicación segura dentro de la organización.
Al integrar un VPN en la infraestructura de la empresa, se establece un canal cifrado que protege la información confidencial que se transmite a través de internet. Esto es especialmente útil para empresas con sucursales remotas, empleados que trabajan desde casa o en movimiento, o en entornos donde la seguridad de la red es una prioridad. Al utilizar un VPN integrado, se reduce el riesgo de interceptación de datos, ciberataques y fugas de información.
Además de mejorar la seguridad de la información, la implementación del VPN integrado también puede optimizar el rendimiento de la red al ofrecer una conexión estable y de alta velocidad. Los empleados pueden acceder de forma segura a los recursos de la empresa desde cualquier ubicación, lo que facilita la colaboración y la productividad.
En resumen, la implementación del VPN integrado es una estrategia efectiva para proteger los datos confidenciales de la empresa y garantizar una comunicación segura y eficiente en un entorno digital cada vez más complejo y dinámico.
Comparación VPN integrado vs VPN externo
Un VPN (Red Privada Virtual) es una herramienta que encripta la conexión a Internet para proteger la privacidad y seguridad de los datos. Existen dos opciones principales cuando se trata de utilizar un VPN: integrado en un dispositivo o software externo.
El VPN integrado se refiere a la incorporación de la funcionalidad VPN directamente en el sistema operativo o en el navegador web. Esta opción facilita la activación rápida y sencilla de la conexión VPN sin la necesidad de instalar software adicional. Es una opción conveniente para aquellos que buscan una solución rápida y fácil de usar.
Por otro lado, un VPN externo se refiere a la instalación de aplicaciones o software de terceros para utilizar el servicio VPN. Si bien puede implicar un proceso de configuración inicial más detallado, los VPN externos suelen ofrecer una mayor variedad de servidores y funciones personalizables.
Al comparar ambos enfoques, el VPN integrado puede ser más adecuado para aquellos que buscan una solución simple y no necesitan características avanzadas. Por otro lado, los VPN externos pueden ser más adecuados para usuarios avanzados que desean más opciones de personalización y un mayor control sobre su conexión VPN.
En última instancia, la elección entre un VPN integrado y un VPN externo dependerá de las necesidades individuales de cada usuario. Ambas opciones tienen sus ventajas y desventajas, por lo que es importante considerar cuidadosamente qué características son prioritarias al seleccionar un servicio VPN.
Mejores prácticas de uso del VPN integrado
El uso de una red privada virtual (VPN) integrada en navegadores y sistemas operativos es una herramienta cada vez más popular para proteger la privacidad en línea y acceder a contenido restringido. A pesar de su conveniencia, es importante seguir algunas mejores prácticas para garantizar su eficacia y seguridad.
En primer lugar, es crucial utilizar siempre una VPN confiable y de buena reputación. Optar por una VPN gratuita puede implicar riesgos para la seguridad de los datos, por lo que es recomendable invertir en un servicio de calidad.
Además, es aconsejable activar la VPN antes de acceder a cualquier sitio web o servicio en línea. De esta manera, se asegura que todos los datos enviados y recibidos estén protegidos, especialmente al conectarse a redes Wi-Fi públicas.
Otra práctica recomendada es seleccionar servidores VPN cercanos a su ubicación geográfica. Esto puede mejorar la velocidad de conexión y garantizar una experiencia en línea más fluida.
Asimismo, es fundamental mantener el software de la VPN actualizado para evitar posibles vulnerabilidades de seguridad. Las actualizaciones periódicas suelen incluir parches y mejoras que refuerzan la protección de los datos.
En resumen, al seguir estas mejores prácticas de uso del VPN integrado, los usuarios pueden disfrutar de una navegación más segura y protegida en internet, preservando su privacidad y evitando posibles amenazas en línea.
0 notes
Text
does using a vpn make you anonymous
🔒🌍✨ Ganhe 3 Meses de VPN GRÁTIS - Acesso à Internet Seguro e Privado em Todo o Mundo! Clique Aqui ✨🌍🔒
does using a vpn make you anonymous
Funcionamento do VPN
Um VPN, ou Rede Virtual Privada, é uma tecnologia que permite criar uma conexão segura e criptografada entre o seu dispositivo e a internet. Esse recurso é amplamente utilizado por empresas e indivíduos que desejam proteger seus dados e garantir a privacidade online.
O funcionamento de um VPN é bastante simples. Quando você ativa o VPN em seu dispositivo e se conecta a um servidor remoto, todo o tráfego de dados entre o seu dispositivo e a internet passa a ser criptografado. Isso significa que mesmo que alguém intercep a sua conexão, não será capaz de visualizar ou acessar as informações transmitidas.
Além de proteger a sua privacidade, um VPN também oferece outras vantagens. Por exemplo, ao utilizar um servidor remoto, você pode acessar conteúdos bloqueados geograficamente, como sites de streaming ou redes sociais que são restritas em determinadas regiões.
Outra funcionalidade importante do VPN é a proteção contra ataques cibernéticos. Como a conexão é criptografada, é muito mais difícil para hackers ou malwares acessarem os seus dados ou monitorarem a sua atividade online.
Em resumo, o VPN funciona como uma camada extra de segurança e privacidade para a sua navegação na internet. Ao utilizar essa tecnologia, você pode se proteger contra ameaças online e desfrutar de uma experiência mais segura e livre na web.
Anonimato na Internet
O anonimato na internet é um tema frequentemente discutido nos dias de hoje. Com o aumento do uso da tecnologia e das redes sociais, muitos usuários buscam maneiras de proteger sua identidade e preservar sua privacidade online.
Existem diversas ferramentas disponíveis que permitem aos usuários navegar de forma anônima, como a utilização de redes virtuais privadas (VPNs) e navegadores especializados em privacidade, como o Tor. Essas ferramentas criptografam os dados do usuário e mascaram seu endereço IP, tornando mais difícil a identificação de sua localização e atividades online.
Porém, é importante ressaltar que o anonimato na internet pode ter tanto aspectos positivos quanto negativos. Por um lado, protege a privacidade dos usuários e lhes permite navegar sem serem rastreados. Por outro lado, também pode facilitar a prática de atividades ilegais, como o cyberbullying e a disseminação de conteúdo ilegal.
Além disso, é essencial que os usuários estejam cientes de que o anonimato na internet não garante total proteção. Empresas de tecnologia, hackers e até mesmo governos podem ainda ser capazes de acessar informações pessoais, mesmo quando se está navegando de forma anônima.
Portanto, é importante que os usuários estejam atentos e façam um uso responsável do anonimato na internet, sempre respeitando as leis e os direitos dos outros usuários. A privacidade é um direito fundamental, mas deve ser conciliada com a segurança e o respeito mútuo no ambiente online.
Segurança online
A segurança online é uma preocupação crescente nos dias de hoje, à medida que mais e mais pessoas passam tempo online. Com a proliferação de hackers, vírus e outras ameaças cibernéticas, é essencial tomar medidas para garantir a segurança dos nossos dados e informações pessoais na internet.
Existem várias medidas que podemos adotar para proteger a nossa segurança online. Uma das formas mais eficazes é garantir que tenhamos passwords fortes e únicas para cada uma das nossas contas online. Além disso, é importante mantermos os nossos programas e sistemas operativos atualizados, uma vez que as atualizações frequentes muitas vezes corrigem vulnerabilidades de segurança.
Outra prática importante é ter cuidado com os nossos comportamentos online. Devemos evitar clicar em links suspeitos, fornecer informações pessoais em sites não seguros e partilhar demasiadas informações nas redes sociais. É também aconselhável utilizar ferramentas de segurança, como antivírus e firewalls, para proteger os nossos dispositivos contra ameaças online.
Por último, é essencial estarmos cientes das últimas ameaças cibernéticas e de como nos podemos proteger contra elas. Estar informado sobre as práticas recomendadas de segurança online pode ajudar-nos a evitar cair em armadilhas e a manter os nossos dados seguros.
Em resumo, a segurança online é uma preocupação importante que deve ser levada a sério por todos os utilizadores da internet. Ao adotarmos medidas proativas para proteger a nossa segurança online, podemos reduzir o risco de sermos vítimas de ciberataques e manter os nossos dados pessoais e financeiros seguros.
Privacidade na rede
A privacidade na rede é uma questão cada vez mais relevante nos dias de hoje, especialmente com o constante aumento do uso da internet para diversas atividades do dia a dia. Com a quantidade de informações que compartilhamos online, é essencial estarmos cientes dos riscos e medidas que podemos tomar para proteger nossa privacidade.
Ao navegar na internet, é importante ter em mente que muitos sites e serviços coletam dados pessoais, como histórico de navegação, localização e informações de perfil. Esses dados podem ser utilizados para diversos fins, desde personalizar anúncios até mesmo para atividades mais invasivas, como roubo de identidade. Por isso, é fundamental tomar algumas precauções para garantir a segurança dos nossos dados.
Uma das medidas mais importantes é revisar e ajustar as configurações de privacidade nas redes sociais e em outros serviços online que utilizamos regularmente. Além disso, é aconselhável utilizar senhas seguras e únicas para cada conta, ativar a autenticação em dois fatores sempre que possível e evitar compartilhar informações sensíveis em sites não seguros.
Outra dica importante é manter o software do dispositivo atualizado, pois as atualizações frequentemente incluem correções de segurança que ajudam a proteger os dados armazenados. Também é recomendável utilizar uma rede privada virtual (VPN) ao se conectar a redes Wi-Fi públicas, garantindo uma conexão segura e criptografada.
Em resumo, proteger nossa privacidade na rede requer atenção constante e cuidados básicos, mas essenciais. Ao adotar essas medidas, podemos desfrutar de todas as vantagens da internet sem comprometer nossa segurança e privacidade.
Navegação anônima
Navegação anônima, também conhecida como navegação privada, é uma funcionalidade oferecida por muitos navegadores de internet que permite aos usuários explorar a web sem que suas atividades sejam registradas no histórico do navegador. Esse recurso é especialmente útil para quem deseja mais privacidade ao navegar online.
Ao ativar a navegação anônima, o navegador não armazena informações sobre os sites visitados, cookies, dados de formulários ou histórico de buscas. Isso significa que os usuários podem pesquisar e visualizar conteúdo na internet sem deixar rastros no computador ou dispositivo utilizado.
É importante ressaltar que a navegação anônima não garante total anonimato na internet, uma vez que provedores de internet e sites ainda podem coletar dados sobre a atividade online dos usuários. No entanto, essa funcionalidade é útil para evitar que outras pessoas que compartilham o mesmo dispositivo acessem informações privadas ou para impedir que sites personalizem conteúdo com base no histórico de navegação.
Além disso, a navegação anônima pode ser útil para pesquisas sensíveis, compras online de presentes surpresa ou simplesmente para evitar que os cookies de publicidade rastreiem os interesses do usuário.
Em resumo, a navegação anônima é uma ferramenta conveniente para proteger a privacidade ao usar a internet, embora deva ser complementada por outras medidas de segurança cibernética para garantir uma experiência online mais segura e privativa.
1 note
·
View note
Text
does my network support vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does my network support vpn
VPN compatibility check
When it comes to ensuring your VPN works seamlessly with your devices, performing a compatibility check is crucial. VPN compatibility check involves verifying whether the VPN service you intend to use is compatible with the operating system of your device, as well as the apps and software you regularly use.
Firstly, ensure that the VPN service you choose supports the operating system of your device, whether it’s Windows, macOS, iOS, Android, or Linux. Most reputable VPN providers offer apps for various operating systems, making it easy to set up and use the VPN on different devices.
Secondly, check if the VPN service is compatible with any specific apps or software you frequently use. Some VPNs may have difficulties working with certain applications, especially those that require high bandwidth or specific network configurations. By checking for compatibility with your essential apps in advance, you can avoid any potential issues and ensure a smooth user experience.
Additionally, consider the number of simultaneous connections allowed by the VPN service, especially if you have multiple devices that need protection. Some VPN providers limit the number of devices that can be connected simultaneously under one account, so verifying this aspect is essential for seamless compatibility.
In conclusion, conducting a VPN compatibility check before subscribing to a service can help you avoid compatibility issues and ensure a hassle-free user experience across all your devices. By verifying compatibility with your operating system, essential apps, and the number of simultaneous connections allowed, you can make an informed decision and choose a VPN that meets your specific needs.
Network VPN support assessment
A Virtual Private Network (VPN) is a crucial tool for protecting your online privacy and security. However, not all VPN services are created equal. When choosing a VPN provider, it's important to carefully assess the level of network support they offer to ensure you get the best possible experience.
One of the key factors to consider when evaluating VPN support is the availability of customer service. A reliable VPN provider should offer 24/7 customer support to assist you with any issues or questions that may arise. Look for providers that offer multiple channels of support, such as live chat, email, and phone support, to ensure you can reach them whenever you need help.
Another important aspect of network VPN support is the provider's infrastructure and server network. A VPN with a large server network spread across multiple locations will offer better performance and reliability. It's also essential to consider the speed and bandwidth capabilities of the VPN provider's servers to ensure smooth and fast connections.
Furthermore, assess the security features offered by the VPN service, such as encryption protocols, kill switches, and leak protection mechanisms. A VPN that prioritizes security will help you browse the internet anonymously and protect your data from prying eyes.
In conclusion, when evaluating network VPN support, prioritize factors such as customer service availability, server network size, speed, bandwidth, and security features. By conducting a thorough assessment of these criteria, you can choose a VPN provider that meets your needs and offers reliable support for a seamless online experience.
VPN capability evaluation for network
A VPN, or Virtual Private Network, is a crucial tool for ensuring the security and privacy of data transmitted over a network. When evaluating the capabilities of a VPN for network use, there are several key factors to consider.
First and foremost, the encryption protocol used by the VPN is paramount. Industry-standard protocols such as OpenVPN, IKEv2, and IPSec provide robust encryption to safeguard data from interception or manipulation by unauthorized parties.
The logging policy of the VPN provider is another critical aspect to evaluate. A strict no-logs policy ensures that user activity is not monitored or stored, preserving privacy and confidentiality.
In addition to security features, the speed and stability of the VPN connection are vital for seamless network performance. Testing the latency and bandwidth of the VPN under various conditions can help determine its suitability for the network's requirements.
Moreover, the geographic coverage of the VPN servers is essential for accessing content from different regions while maintaining a secure connection. A diverse server network minimizes latency and enhances the overall user experience.
Lastly, consider the compatibility of the VPN with different devices and operating systems to ensure seamless integration into the network infrastructure.
By carefully evaluating these factors, network administrators can select a VPN solution that meets their security, privacy, and performance needs effectively. Taking the time to assess the VPN's capabilities will result in a secure and reliable network environment for all users.
Determining VPN feasibility for network
When considering implementing a Virtual Private Network (VPN) for your network, determining its feasibility is a crucial step. A VPN is a secure network connection that allows you to create a private connection over a public network, such as the internet. It provides encryption and security measures to ensure the confidentiality of your data.
The first step in determining the feasibility of a VPN for your network is to assess your specific needs and requirements. Consider the size of your network, the number of users, the type of data being transmitted, and the level of security needed. VPNs are ideal for remote workers or offices that need to securely connect to the main network.
Next, evaluate the technical capabilities of your network infrastructure. Ensure that your network hardware and software support VPN connections and encryption protocols. You may need to upgrade or configure your existing equipment to accommodate the VPN.
Consider the cost implications of implementing a VPN. This includes the initial setup costs, ongoing maintenance, and potential subscription fees for VPN services. Compare the costs with the benefits of improved security, remote access capabilities, and enhanced connectivity.
Another important factor to consider is the level of expertise within your organization to manage and maintain the VPN. If you do not have in-house expertise, you may need to outsource the management of the VPN, which can add to the overall cost.
In conclusion, determining the feasibility of a VPN for your network involves assessing your needs, technical capabilities, costs, and resources. By carefully evaluating these factors, you can make an informed decision on whether a VPN is the right solution for your network.
Assessing network compatibility with VPN
When considering the implementation of a Virtual Private Network (VPN) within a network infrastructure, assessing the compatibility of the network becomes essential. A VPN allows for secure communication over a public network by encrypting the data transferred between devices. However, not all networks are initially compatible with VPN technology, which is why a thorough assessment is crucial.
The first step in assessing network compatibility with VPN is to evaluate the existing network infrastructure. Factors such as the type of network hardware, software capabilities, and the network topology need to be taken into account. Some older network hardware may not support modern VPN protocols, requiring upgrades or replacements. Similarly, certain network configurations may need to be adjusted to accommodate VPN traffic.
Next, the bandwidth and latency of the network should be assessed to ensure optimal VPN performance. VPNs introduce additional overhead due to encryption and encapsulation, which can impact network speed and latency. Conducting speed tests and latency measurements can help identify potential bottlenecks that need to be addressed before implementing a VPN.
Additionally, it is crucial to consider the security requirements of the network when assessing compatibility with a VPN. VPNs provide a secure channel for data transmission, but if the network lacks proper security measures such as firewall protection or intrusion detection systems, the effectiveness of the VPN could be compromised.
In conclusion, assessing network compatibility with VPN is a critical step in ensuring the successful integration of VPN technology within an existing network infrastructure. By evaluating network hardware, bandwidth, latency, and security measures, organizations can identify and resolve any compatibility issues before deploying a VPN, ultimately enhancing the security and efficiency of their network communication.
0 notes
Text
Royal Enfield Gt Interceptor 650 Accessories | Gt Interceptor 650 Bike Gears | Zana Motorcycles
Buy Royal Enfield GT Interceptor 650 bike Accessories and Genuine Parts from Zana International. Order crash guard, saddle stay, top rack, backrest, radiator grill, headlight grill, bash plate, mudguard riser, rear master cylinder protector, handlebar, clip on riser riding gears online in India at best price near me.

#interceptor 650 accessories#royal enfield interceptor 650 accessories#continental gt 650 accessories#royal enfield continental gt 650 accessories#gt 650 accessories#accessories for interceptor 650#continental gt 650 aftermarket accessories#intercep
0 notes
Text
>does not elaborate >leaves
>does not elaborate >leaves
He explained multiple times that the eagles are susceptible to the influence of the Ring and that Sauron could have easily intercepted them with the Nazgul if they flew in but still the worst group of smooth-brained nerds insist they should have flown the Ring to Mordor. Source link

View On WordPress
#and#are#could#does#eagles#easily#elaborate#Explained#have#He#Influence#intercep#leaves#multiple#not#of#ring#Sauron#susceptible#that#the#times#to
0 notes
Photo

Premier passage du travail du sol terminé. #champagnesebastienlefevre #viticulturedurable #hve #terroir #chardonnay #blancdeblanc #travaildusol #intercep (à Champagne Sébastien Lefevre) https://www.instagram.com/p/B-J9gsFioz1/?igshid=1mz9fl9aeml86
#champagnesebastienlefevre#viticulturedurable#hve#terroir#chardonnay#blancdeblanc#travaildusol#intercep
0 notes