#information protection
Explore tagged Tumblr posts
Text
not romantic not platonic but a secret third thing [what would happen between earth and the moon if the earth stopped spinning as illustrated by xkcd randall munroe]
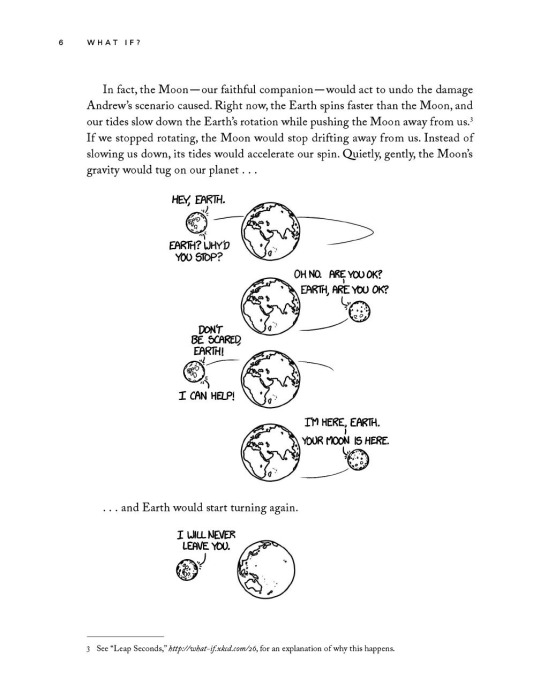
#'your moon is here' things that make me explode like a supernova#UGHHHHHHH what if i was perpetually in your orbit. influencing the tides. protecting you from asteroids. and slowly drifting further away.#then you stopped moving and i was only pulse to your dead heart. orbiting you. right where ive been left. and so you started turning again.#ria.txt#personal#space opera au#(<- not about what you think is about)#hiiii this is gaining traction so glad we're all going insane :D your moon is here is SO fucked up. so good.#xkcd#randall munroe#space#moon#anyways xkcd comics are so good. entertaining witty and informative. check em out!#ok this is about false and ren from hermitcraft#falseren
127K notes
·
View notes
Text
Discover why data security is crucial in data entry and learn effective strategies to safeguard sensitive information. Explore best practices, potential threats, and the role of secure data management in ensuring confidentiality and compliance. Stay informed and protect your data with insights from Zedtreeo.
#Data Security#Data Entry#Information Protection#Cybersecurity#Data Management#Sensitive Information#Secure Data Handling
0 notes
Text
Mandatory Cybersecurity Incident Reporting: The Dawn of a New Era for Businesses
A significant shift in cybersecurity compliance is on the horizon, and businesses need to prepare. Starting in 2024, organizations will face new requirements to report cybersecurity incidents and ransomware payments to the federal government. This change stems from the U.S. Department of Homeland Security���s (DHS) Cybersecurity Infrastructure and Security Agency (CISA) issuing a Notice of Proposed…

View On WordPress
#CIRCIA#CISA#Cyber Incident Reporting for Critical Infrastructure Act of 2022#Cybersecurity#Cybersecurity Infrastructure and Security Agency#Department Of Homeland Security#DHS#Information Protection#notice of proposed rulemaking#NPRM#reporting
0 notes
Text
Securing Communications: The Role of Cipher Machines and Password Cards

In today's digital age, securing communications is paramount to protect sensitive information from interception and unauthorized access. Cipher machines and password cards play crucial roles in this endeavor, offering robust encryption and authentication mechanisms to safeguard data transmission and access.
Cipher Machines: Cipher machines are sophisticated devices used to encrypt and decrypt messages, ensuring the confidentiality and integrity of communications. These machines employ complex cryptographic algorithms to scramble plaintext messages into ciphertext, making them unreadable to unauthorized parties. By incorporating cipher machines into communication systems, organizations can prevent eavesdropping and maintain the privacy of sensitive information.
Password Cards: Cipher Machines and Password Cards serve as physical tokens or devices used to store and manage authentication credentials, such as passwords or PINs. These cards feature grids of alphanumeric characters, each corresponding to a unique password. Users can reference the grid to retrieve their passwords when logging into secure systems or accessing protected resources. Password cards provide an additional layer of security by requiring users to possess the physical token in addition to knowledge of the password.
Encryption Strength: Both cipher machines and password cards contribute to the strength of encryption and authentication mechanisms. Cipher machines utilize robust encryption algorithms and keys to transform plaintext messages into ciphertext, ensuring that even if intercepted, the message remains unintelligible to unauthorized parties. Similarly, password cards enhance authentication security by requiring the possession of physical tokens, mitigating the risk of unauthorized access through password theft or brute-force attacks.
Data Confidentiality: Cipher machines and password cards play crucial roles in preserving the confidentiality of sensitive information during transmission and access. Cipher machines encrypt messages before transmission over insecure channels, preventing unauthorized interception and decryption of the communication. Password cards protect access to secure systems and resources by verifying the identity of users through authentication credentials stored on the physical token.
Authentication Mechanisms: Password cards augment authentication mechanisms by introducing multifactor authentication (MFA) capabilities. In addition to passwords or PINs, users must possess the physical token to authenticate themselves, adding an extra layer of security. This multifactor approach reduces the likelihood of unauthorized access, even if passwords are compromised or stolen.
Regulatory Compliance: Incorporating cipher machines and password cards into communication systems helps organizations comply with regulatory requirements and industry standards for data security and privacy. Many regulatory frameworks mandate the use of strong encryption and authentication mechanisms to protect sensitive information and prevent data breaches. Cipher machines and password cards offer robust solutions to meet these compliance requirements effectively.
User-Friendly Interfaces: Despite their advanced encryption and authentication capabilities, cipher machines and password cards are designed to be user-friendly and accessible. Cipher machines may feature intuitive interfaces for inputting plaintext messages and encryption keys, while password cards provide convenient grids for retrieving passwords during authentication processes. This user-friendly design ensures that security measures do not impede productivity or usability.
Continuous Innovation: Cipher machines and password cards continue to evolve in response to emerging threats and technological advancements. Manufacturers and developers invest in research and development to enhance encryption algorithms, authentication protocols, and physical security features. By staying abreast of evolving security threats and best practices, cipher machines and password cards remain effective tools for securing communications in an ever-changing digital landscape.
In summary, cipher machines and password cards play integral roles in securing communications and protecting sensitive information from unauthorized access. By leveraging robust encryption and authentication mechanisms, organizations can maintain data confidentiality, comply with regulatory requirements, and mitigate the risk of data breaches. As technology evolves, cipher machines and password cards will continue to adapt and innovate to meet the evolving challenges of cybersecurity.
Get More Insights On This Topic: Cipher Machines And Password Cards
#Cipher Machines#Password Cards#Encryption#Authentication#Data Security#Cryptography#Communication Security#Information Protection
0 notes
Text
Recognizing Common Cyber Security Threats

Cyber security threats encompass a wide range of techniques and actions that attackers use to exploit weaknesses in technology and human behavior. These can jeopardize the confidentiality, integrity, or availability of information and resources in an organization. Considering the grave impact such threats can have, we at ITCSS Solution and Staffing find it critical to improve people’s awareness of them.
Learn more: https://www.itcss.net/recognizing-common-cyber-security-threats
0 notes
Text
I don't care about data scraping from ao3 (or tbh from anywhere) because it's fair use to take preexisting works and transform them (including by using them to train an LLM), which is the entire legal basis of how the OTW functions.
#really tired of seeing posts warning people to archive lock their works to protect against scraping#information wants to be free and that includes your second person reader insert#you are of course welcome to archive lock the works#that's a function of ao3 for a reason#but the anti-scraping attitude is exhausting because it tells me#that the broad understanding of 'fair use' is dismal#which is depressing coming from the userbase of a site that is totally reliant on fair use
3K notes
·
View notes
Text
On Thursday, Governor Tim Walz sat down for an interview with author Glennon Doyle, her partner Abby Wambach, and her sister Amanda Doyle during a taping of the We Can Do Hard Things podcast. The conversation touched on key election issues such as abortion and gun violence. However, midway through the podcast, the discussion shifted to queer youth, specifically transgender kids. Rather than shying away from the topic, Walz delivered a passionate, several-minute-long defense of LGBTQ+ rights, including transgender healthcare. He outlined his vision for the administration’s role in protecting these rights.
The question came from Abby Wambach, who turned to the topic after discussing Walz’ founding of a Gay-Straight Alliance at his high school in the mid-90s. Wambach asked, “Well, thank you Governor Walz so much for protecting even in the late ’90s queer kids. And so I have to ask, what will a Harris-Walz administration do to protect our queer kids today?”
Walz discussed positive legislative actions, such as codifying hate crime laws and increasing education, while emphasizing the importance of using his platform to advocate for LGBTQ+ rights. He then addressed the role of judges in safeguarding medical care for queer youth: “I also think what Abby, your point is on this, and I was just mentioning, we need to appoint judges who uphold the right to marriage, uphold the right to be who you are, making sure that’s the case, uphold the right to get the medical care that you need. We should not be naive. Those appointments are really, really important. I think that’s what the vice president is committed to.”
He didn’t stop there. Instead, he directly pivoted to calling out national anti-transgender attack ads which have flooded the airwaves across the United States, often airing besides NFL football games and other major sporting events. The Trump administration has spent upwards of $20 million on such ads, with outside organizations spending $80 million on various races.
“We see it now; the hate has shifted to the trans community. They see that as an opportunity. If you’re watching any sporting events right now, you see that Donald Trump’s closing arguments are to demonize a group of people for being who they are,” Walz said. He continued, “We’re out there trying to make the case that access to healthcare, a clean environment, manufacturing jobs, and keeping your local hospital open are what people are really concerned about. They’re running millions of dollars of ads demonizing folks who are just trying to live their lives.”
He emphasized the importance of representation and the impact of coming out, particularly for parents who may not have been exposed to LGBTQ+ identities and therefore might lack understanding. Walz pointed out, “Look, you’re reaching a lot of folks in hearing this, and for some people it’s not even out of malice and it’s not a pejorative, it’s out of ignorance. They maybe have not been around people. You’ve all seen this, however it takes you to get there, but I know it’s a little frustrating when you see folks have an epiphany when their child comes out to them.”
The strong defense of queer and trans youth came just one day after Kamala Harris participated in a Fox News interview with Brett Baier. Baier, who maintained a hostile tone throughout, pressed Harris on transgender issues with his second question. Rather than adopting the Republican framing, as some Democrats have done recently, Harris emphasized that the law requires medically necessary care for transgender inmates and criticized Trump for spending $20 million on ads focused on an issue far removed from the priorities of most Americans. Her response prompted Baier to quickly shift to another topic.
In back-to-back days, the Harris-Walz ticket has made it clear they will not back down on queer and trans rights, despite the barrage of anti-trans attack ads. This stance is likely reinforced by the repeated failure of similar ads in recent races, including Wisconsin’s Supreme Court election, legislative races in Pennsylvania and Virginia, Georgia’s Herschel Walker vs. Raphael Warnock election, Andy Beshear’s reelection in Kentucky, and the 2023 losses of 70% of Moms for Liberty and Project 1776 school board candidates across the United States. For transgender people, these interviews are likely a welcome relief after some wavering responses from other Democratic candidates in swing states.
#us politics#in support of an informed and engaged electorate#trans inclusion#protect trans lives#protect trans youth#Erin Reed
1K notes
·
View notes
Text

post rescue
#trigun maximum#vashwood#vash the stampede#nicholas d wolfwood#trigun#ruporas art#i love to romanticize the 2 vague short days they got to spend together#2 days bc i know ww dipped the moment marlon informed him his gun was fixed… orz#but in the meantime��. clingy all over each other while they both recover their strength#a feathery embrace in less tense circumstances and a vulnerable display of want and protectiveness on vash’s end
2K notes
·
View notes
Text
we are living in a digital dark age. Export your movies, print your photos, burn CD’s with music. If it isn’t physical it doesn’t exist.
#it doesn’t stop with tiktok#soon we will have nothing#tiktok ban#protect our rights#punks against silence#can’t have punk without politics#stay safe stay informed stay strong
298 notes
·
View notes
Text
Not to be a Style apologist, but I feel like some viewers haven't quite picked up that Style's brand of wooing Fadel is quite literally intentionally designed (by both the writers and the character) to be as annoying and frustrating as possible.
Lets consider:


Style thinks his bff is in love for the first time in his life. He thinks Kant is genuinely down bad for Bison: let’s not forget his clear surprise when Kant agreed to give up the car. As far as Style is concerned, Kant is acting really out of character and it's because Kant desperately wants to be with Bison.


He also thinks the only thing standing in the way of True Love™ is Fadel, who according to Kant is being unreasonably difficult about Kant and Bison dating. He doesn't know that Kant has a secondary motivation, nor does he know about the mind games that Bison is playing with Kant. Worse, he has no frame of reference or context to make any of Fadel's animosity towards Kant reasonable.


Moreover, while I think we all agree that Style made a terrible first impression on Fadel, the same has to be said of Fadel towards Style. Like, yes, absolutely Style was in the wrong, but Fadel came off as not only condescending and impatient, but unreasonable (and very weirdly cagey) when Style tried to immediately offer a resolution. Again, Style has no frame of reference for why Fadel would first demand that he take responsibility for his actions and then immediately after claim to have no time to entertain Style's attempt to take said responsibility.



Also, it doesn't help Style's wounded pride that Fadel keeps 'besting' him at every turn. So at this point I think a significant portion of that initial attraction (in ep 1) has shifted to annoyance when it comes to Fadel. By the time he gets his hands on Fadel's information, I think he's more than a little invested in some payback. While I think Style very much still wants to help Kant (and Bison) out, at least a part of him figures as long as he keeps Fadel busy, he kind of meets his goal. And if he gets to embarrass, frustrate and otherwise harass Fadel along the way, all the better!




You can see him start to have some fun with it. He ramps it up SO much in ep 2. He gets to lean into that wild, brash, playful personality because he doesn't really care if Fadel likes him. Style gets to be dialled up to extremes, and I love that for him because he's honestly kind of justified because he knows so fucking little about what's really going on. I think it's only fair if the other 3 are playing 4D chess while Style only has the Uno game rules in front of him, he gets to be the most Unhinged about it.
So, yeah, while I absolutely agree with all the posts out there that recognises just how reasonable and polite and tired Fadel is, I do think we need to give Style some credit here. He's absolutely SO extra, but he's also the one, arguably, that has been lied to the most and I feel that he deserves some slack for that.
#listen i love him and i just keep seeing so many posts about how terrible he was to fadel#and all of them are so valid! and i agree!! i want to protect Fadel from the world too!!#but i also think we need to acknowledge that Style is working on so much less information than anyone else#also i hope he calls Kant out on the kind of shitty thing he did to not tell Style about Fadel's whole deal#the balance that this show strikes between Unserious and actually honestly kind of Serious is really impressing me#the heart killers the series#the heart killers#thk meta#style meta#fadelstyle#hui talks thk#hui talks thai bl#style sattawat#dunk natachai#dunk continues to impress me so much in this episode#he seemed very believable in the frankly insane breadth of variance his character has in both episodes#i'm so excited to see everything he has to show off in this series
352 notes
·
View notes
Text
I understand the instinct to make Modern Odysseus the type of guy who use's his son/wife's name as a password. he's definitely obsessed with them enough
but Odysseus is smart. he would never make his password something easy to guess and his son/wife's name is super easy to guess, especially since he'd talk about them extensively to every single person he met ever
instead I propose his password is something absurd, like 'olive tree' but using 'Penelope' as a cipher
#this guy PROTECTS his personal information#(except for that one hacker. Cykl0ps got him good)#epic the musical#the odyssey#odypen#odysseus#epic odysseus#nuclear war speaks
215 notes
·
View notes
Text
So, I really love time travel fics and I love the Lucerys cuts out his own eye trope while Aemond watches in horror. That's why my brain conjured up the following plot idea:
What if after their respective deaths, they both travel back in time to the same moment without knowing the other came back too and it's the exact moment where Aemond demanded Lucerys' eye as paiment for his debt on Stormsend just before the fateful flight.
This time though Lucerys does not run. He processes the situation just a second before Aemond does and fueled by his own fear of death does the only thing that seems logical at this moment. He lungs for the dagger and proceeds just as Aemond demanded. Aemond snaps out of his own stupor just as the screaming starts and tries to stop Lucerys but it's already to late. The eye is lost. A meaningless debt which had been paid tenfold in another life had been paid again. And Lucerys looks up at him through tears and blood, his face twisted in agony and asks: "Will you let me leave now, uncle?"
#you may ask why i also want aemond to go back in time and i promise i have a good reason for that#i want him to remember his grief his rage and how powerless he was in the end to protect anything he held dear#i want him to realise that he has the key to salvation right in front of him and yet the timeline already changed again#all while he stood there watching#he doesnt understand what is going on but he knows one thing and that is that he has to keep luke alive at all costs#if he wants to avoid all the suffering yet to come#also remember he has all the information while luke only knows that aemond killed him#lucemond#lucerys x aemond#aemond x lucerys
285 notes
·
View notes
Text
⚠️⚠️IMPORTANT!!⚠️⚠️
If you have an Apple product you need to hear this,
In the latest update Apple has added and insidious Ai to every single one of your apps
You will need to manually turn this off to stop Ai from using your apps as a learning base
First:
Head to settings and find the Apple Intelligence & Siri tab

Second:
if you scroll to the bottom of that tab you should find an option to see your apps and a separate option to see apps clips (these can be done in either order but I’ll explain clips first)
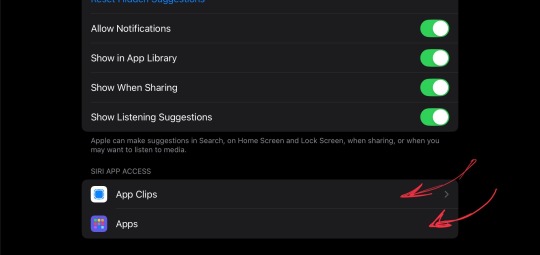
Third:
You should come to this screen with an option of “Learn from Apps Clips”, make sure to turn that off (if it’s green it’s still on)

Fourth:
Head back and click onto the apps section, this should bring you to a screen with all your apps

You’re going to have to click on every single one of your apps and turn it off manually (Apple has deliberately made it as tedious as possible in a way to discourage people doing this)

Fifth:
SHARE THIS INFORMATION!! either via my post or making your own,
Every uninformed person is another source of content for Ai to steal from, don’t let this undermine us
As far as I’m aware that’s everything, but there may be more
I will update this if more information comes out
#important#important notice#important psa#anti ai#apple update#artist struggles#artist help#artist news#protect yourself#protect your information#you need to know this#you need to hear this#valuable information\#ai artists dni#guide with pictures
234 notes
·
View notes
Text
Another Prompt in Memes?! Yes.








#dcxdp#dpxdc#prompts#memes#Knighthood#knighthood ship#Let Jason be a literal Reaper type ghost#Danny is not ghost king but Fright Knight got attached & shall protect his Core as he heals#This can be de aged Danny if you want or not lol#Ghosts deserve to be eldritch#Undead deserve to be eldritch#Crime Alley: Ah yes Undead Punk & Eldritch Knight gotta be my fav genders#Batclan: Please we just want information about the person who dropped off a dufflebag of heads at the GCPD-#Crime Alley: I'm sorry we can't hear you over the sound of our favorite show going live here#Crime Alley is watching their disaster cryptids while munching popcorn like it's their fav sitcom or something lol#Jason deserves to be able to spar with his Allblades#halfa jason todd#star core jason#shadow core fright knight#Space Core Danny#Pfft that can lead to misunderstandings lmao#Stars + shadowy darkness = space lmao#Let Jason be feral- let FK go a lil feral too#Fright Kerian Knight#Also lets be honest they're probably both nerds#And they both bake#LET THEM BAKE TOGETHER#knighthood
631 notes
·
View notes
Text
Listen up please
This is incredibly important.
The united States government has been trying to remove the protections of native children mainly via possibly overturning the ICWA (Indian Child Welfare Act)
This will allow white families to continue to take native children from their lands their family and their culture just like they did for centuries before the ICWA was passed.
This is both incredibly important and incredibly personal as my family was permanently harmed because of children being taken away from their families.
So please spread awareness about this and I have a link below that you can go to the first Nations website learn more about this and and write a response that they can use about how we should be saving the ICWA
3K notes
·
View notes
Text
Peeta recognized the sound of whip on the flesh, don't even talk to me again.
#no you don't understand HE RECOGNIZED IT SO QUICKLY#I can’t get over the fact that his first reflex was to protect Katniss I want to cry#the hunger games#hunger games#Peeta Mellark is the man that every one wants but not deserves because he's just the best#peeta mellark#thg series#thg#It's horrible to re-read a book and be like “HOW DID I MISSED THIS INFORMATION THAT'SSO CRUCIAL”
224 notes
·
View notes