#hacker services
Explore tagged Tumblr posts
Text
DDOS Attack Explained
In this article, you will learn and explore details about what a DDOS Attack mean, how it functions. This write up is basically all you need to grasp the concept of DDOS attacks. DDOS attacks are a primary concern in Internet security today which makes it a very relevant topic to discuss.
DDOS means “Distributed Denial-of-Service“. It can be defined as a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
The latter achieves effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices. In Simple terms a DDOS attack is like an unexpected traffic jam clogging up the highway, preventing regular traffic from arriving at its destination.
How Does a DDOS Attack Work
A DDOS attack is carried out with networks of Internet-connected machines. These networks consist of computers and other devices (such as IOT devices) which have been infected with malware, allowing them to be controlled remotely by an attacker. These individual devices are referred to as bots (or zombies), and a group of bots is called a botnet.
Once a botnet has been established, the attacker is able to direct an attack by sending remote instructions to each bot. When a victim’s server or network is targeted by the botnet, each bot sends requests to the target’s IP address, potentially causing the server or network to become overwhelmed, resulting in a denial-of-service to normal traffic.
Because each bot is a legitimate Internet device, separating the attack traffic from normal traffic can be difficult.
Stay Ahead of Attackers: How to Identify A DDOS Attack
From a tactical DDOS mitigation standpoint, one of the primary skills you need to have is pattern recognition. Being able to spot repetitions that signify a DDOS attack is taking place is key, especially in the initial stages. Automated applications and AI are often used as helpers, but generally companies need a skilled IT professional to differentiate between legitimate traffic and a DDoS attack.
The following are typical warning signs which could mean a DDOS attack is taking place.
Reports from existing mitigation devices (e.g., load balancers, cloud-based services)
Customers report slow or unavailable service
Employees utilizing the same connection also experience issues with speed
Multiple connection requests come in from a specific IP address over a short amount of time
You receive a 503 service unavailable error when no maintenance is being performed
Ping requests to technology resources time out due to Time to Live (TTL) timeouts
Logs show an abnormally huge spike in traffic
DDoS vs. DoS Attacks: What’s the Difference?
It’s important to avoid confusing a DDoS (distributed denial of service) attack with a DoS (denial of service) attack. Although only one word separates the two, these attacks vary significantly in nature.
Strictly defined, a typical DDoS attack manipulates many distributed network devices in between the attacker and the victim into waging an unwitting attack, exploiting legitimate behavior.
A traditional DoS attack doesn’t use multiple, distributed devices, nor does it focus on devices between the attacker and the organization. These attacks also tend not to use multiple internet devices.

Single-source SYN floods: This occurs when an attacker uses a single system to issue a flood attack of SYN packets, manipulating the typical TCP three-way handshake. For example, a SYN flood someone might generate using a Kali Linux computer is not a true DDoS attack because the attack being made is only coming from one device. This is the case even if the attacker uses IP address spoofing. A true DDoS attack is generated by network-level devices, for network-level devices. In other words, you use multiple routers or Memcached servers to attack a network.
The “ping of death”: Years ago, some network drivers contained flawed code that would crash a system if it received an ICMP packet that contained certain parameters.
The slow loris attack: The slow loris attack is often called a DDoS attack, but because the attack targets a specific server (in this case, a web server) and usually does not use intermediate networking devices, it is typically a traditional DoS attack.
Each of the above DoS attacks take advantage of software or kernel weaknesses in a particular host. To resolve the issue, you fix the host, and/or filter out the traffic. If you can upgrade a server to mitigate an attack, then it doesn’t qualify as a traditional DDoS attack.
Remember, in a DDoS attack, the threat actor adopts a resource consumption strategy. This strategy involves using what appears to be legitimate requests to overwhelm systems which are, in fact, not legitimate, resulting in system issues.
How Long Does a DDOS Attack Last
DDoS attacks vary greatly in length and sophistication. A DDOS attack can take place over a long period of time or be quite brief:
Long-Term Attack: An attack waged over a period of hours or days is considered a long-term attack. For example, the DDoS attack on AWS caused disruption for three days before finally being mitigated.
Burst Attack: Waged over a very short period of time, these DDOS attacks only last a minute or even a few seconds.
Don’t be deceived. Despite being very quick, burst attacks can actually be extremely damaging. With the advent of internet of things (IoT) devices and increasingly powerful computing devices, it is possible to generate more volumetric traffic than ever before.
As a result, attackers can create higher volumes of traffic in a very short period of time. A burst DDoS attack is often advantageous for the attacker because it is more difficult to trace.
Evolvement of DDOS Attack
One of the realities of cybersecurity is that most attackers are moderately talented individuals who have somehow figured out how to manipulate a certain network condition or situation. Even though there is often discussion about advanced persistent threats (APT) and increasingly sophisticated hackers, the reality is often far more mundane.
For example, most DDoS attackers simply find a particular protocol. They’ll discover that they can manipulate the transmission control protocol (TCP) handshake to create a flood attack of SYN packets or a particular type of server, such as the memory cache daemon (it is often called “Memcached,” for memory cache daemon).
The Memcached service is a legitimate service frequently used to help speed up web applications. Attackers have often exploited Memcached implementations that are not properly secured, and even those that are operating properly.
Attackers have also discovered that they can compromise IoT devices, such as webcams or baby monitors. But today, attackers have more help. Recent advancements have given rise to AI and connective capabilities that have unprecedented potential.
Like legitimate systems administrators, attackers now have voice recognition, machine learning and a digital roadmap that can allow them to manipulate integrated devices in your home or office, such as smart thermostats, appliances and home security systems.
Why Hire a Professional Hacker from Us
With over 3598 successfully-completed projects and numerous happy clients who have solicited our hacking services, our team of professional hackers is known to many as undoubtedly one of the team of hackers who happen to be on top of their game in the hacking community.
Professional Hacker for Hire is known to take good care of clients as well as their projects seriously with a guaranteed claim their task will be completed and on time. The team makes this claim because, we only accept tasks we are able to complete with no doubts.
We know the ins and outs of DDOS attacks, if you choose to hire us, we can help you detect, prevent or implement these sort of hacks. Our team of experts are more than capable of handling DDOS Attacks
References
There is no good article that doesn’t profit from the knowledge of other blogs and people. We used information from the following sites when we compiled this beautiful peace.
https://www.cloudflare.com/
https://www.comptia.org/
wikipedia.com
https://professionalhackerforhire.com/ddos-attack-service-the-best-2-minutes-article-you-need/
1 note
·
View note
Text




“Welcome to the Glass City,” said a voice that wasn’t Simon’s. Clary found that Simon had disappeared and she was now dancing with Jace, who was wearing white, the material of his shirt a thin cotton; she could see the black Marks through it. There was a bronze chain around his throat, and his hair and eyes looked more gold than ever; she thought about how she would like to paint his portrait with the dull gold paint one sometimes saw in Russian icons.
City of Bones, Cassandra Clare
#thank you Vinnie Hacker for your service#dailyclace#clace#clace quotes#clary fairchild#jace herondale#clary fray#clace moodboard#jace wayland#jace lightwood#jace lightwood herondale#tmi#the mortal instruments#tsc#the shadowhunter chronicles#vinnie hacker#cds
45 notes
·
View notes
Text












GoldenEye (1995, Martin Campbell)
9/6/24
#GoldenEye#James Bond#Pierce Brosnan#Sean Bean#Famke Janssen#Izabella Scorupco#Judi Dench#Joe Don Baker#Robbie Coltrane#Tcheky Karyo#Gottfried John#Alan Cumming#Desmond Llewelyn#90s#action#adventure#espionage#thriller#spies#British Secret Service#femme fatale#Russia#Cuba#international#assassins#hackers#terrorism
14 notes
·
View notes
Text



Kingsman: The Golden Circle (2017, Matthew Vaughn)
30/07/2024
#Kingsman The Golden Circle#film#matthew vaughn#Jane Goldman#sequel#kingsman the secret service#mark millar#dave gibbons#executive producer#colin firth#taron egerton#mark strong#sophie cookson#julianne moore#halle berry#elton john#channing tatum#pedro pascal#jeff bridges#cybernetics#Security hacker#Drug cartel#Toxin#President of the United States#Alpi italiane#cambodia#drug overdose#20th century studios#ghost#budget
9 notes
·
View notes
Text
Hello! PSA here!
Today I got hacked on my main, and I want to address my experience with this discord hacker
His name is Danny Duong, he works with other (presumably hacked) accounts, the other account warns you that they reported you by accident when another impersonated you, and tells you to add a discord user called dannysupport24, he sends you his "credentials" (pic below)

He tells you to change your email to a support email so he can help you, DO NOT DO IT! Discord will NEVER tell you to change your email under ANY circumstance!
After you do, you will get logged out of your account for good, leaving your account to hack more people, please, repost this as much as possible
Link from another experience below
UPDATE: Yes, he uses other hacked accounts to do it, and changes his username every time


11 notes
·
View notes
Text
[Soap meets Orphan’s bodyguard and partner Smoke and the two share a drink while watching Ghost and Orphan talk at a pub.]
Soap: Man, Ghost and Orphan have been spending a lot of time together.
Smoke: I don't like it. He is not good enough for Miss Ivy.
Soap: But they seem happy together.
Smoke: He is a bad influence and he is taking advantage of her because she is young and naive..... and delicate.
Soap, looks at him like he’s grown six heads: Delicate? She killed ten men with an 8ball tied to a bungie cord!
Smoke, choked up: She’s a precious flower.
#S: red vs blue#call of duty modern warfare incorrect quotes#simon ghost riley#ghost x oc#Cod mw oc: Ivy 'Orphan' Doran#cod mw oc: Alan 'Smoke' Monroe#watch dogs crossover#Soap's talking about the thunder ball weapon from watch dogs2#Smoke and Oprhan are dedsec hackers who accidentally got tangled in something that got the Cia's attention#In exchange for their freedom the two are volunteered to lend their services to the 141#simon ghost riley x oc
140 notes
·
View notes
Text
Rewatching Yes, Minister and thinking about Sir Humphrey in "The Whiskey Priest". Upon being told that, if he doesn't care about morality in government, he's going to hell, the man grins. When asked about whether the Civil Service should believe in the government's policies, Sir Humphrey lectures us about how that would mean holding several contradictory views whose net effect would be to drive any man mad. And for all his amoral cynicism, he is sort of trying to help Hacker out: telling the PM what he knows would at best make Hacker a martyr for embarrassing the government (and leave him unable to help anyway) and at worst bring down the whole cabinet, PM included. An interesting episode, all around.
#yes minister#sir humphrey appleby#jim hacker#the whiskey priest#bernard wooley#the civil service#stark staring raving schizophrenic#moral vacuum
16 notes
·
View notes
Text
APPLE’S REJECTION OF META AI TOOLS: A STANCE ON PRIVACY AND SECURITY
#Technology#AI#Artificial Intelligence#Generative AI#Omniverse#NVIDIA#VR#AR#Programing#Python#HTML#JavaScript#Full Stat Developers#programmers#Artist#Developers#Graphic Designers#IndieGames#Indie Games#Hard Surface Developer#Security#Hackers#DoS#Denial of Service#Phishing#Social Media#Internet Protocol#Sockets#Scams#ID Theft
6 notes
·
View notes
Text
I know that we're in a pretty dark timeline right now, but I think that it's objectively hilarious that my main sense of hope in American politics comes from gay furry hacker vigilantes. I genuinely feel so much safer as a trans person because of them


4 notes
·
View notes
Text
How Do Private Investigators Track Cell Phones?
Private investigators (PIs) are known for their resourcefulness and ability to uncover information that may seem out of reach for the average person. Among their many skills, tracking cell phones has become a critical tool in modern investigations. Whether working on cases involving missing persons, fraud, infidelity, or corporate espionage, PIs often rely on cell phone tracking to collect crucial evidence.

But how do private investigators track cell phones? This blog explores the techniques, tools, and ethical considerations involved in this sensitive process.
1. The Basics of Cell Phone Tracking
Cell phone tracking involves determining the location of a device by utilizing the technology it relies on to function—cell towers, GPS, and Wi-Fi networks. Smartphones emit signals that can be intercepted or analyzed to pinpoint their location. While law enforcement agencies have sophisticated tools and legal authority for tracking, private investigators often use alternative methods that stay within legal boundaries.
2. Common Techniques Used by Private Investigators
a. GPS Tracking
GPS (Global Positioning System) tracking is one of the most accurate ways to locate a cell phone. Many modern devices come equipped with built-in GPS chips that constantly communicate with satellites to determine their location. Private investigators might use the following approaches to access GPS data:
Authorized Access: If a private investigator has legal permission (e.g., from the device owner), they can use GPS tracking apps to monitor the phone's location. This is common in cases of missing persons or parental tracking of children.
Location-Sharing Apps: Some apps, like Find My iPhone or Google Find My Device, allow users to share their location. A PI might assist clients in accessing these features, provided they have the right credentials or consent.
b. Cell Tower Triangulation
Cell phones connect to nearby towers for communication, and the distance to these towers can be used to approximate the device's location. By analyzing signal strength from multiple towers, a process known as triangulation can determine the phone's general whereabouts.
Private investigators might collaborate with telecommunications providers to request such data, but this typically requires proper legal justification, such as a subpoena or court order.
c. Wi-Fi Positioning Systems (WPS)
Many modern devices use Wi-Fi signals for location tracking when GPS is unavailable. By identifying the networks a phone connects to, investigators can narrow down the location. This technique is particularly useful in urban areas, where Wi-Fi networks are abundant.
d. Mobile Applications
Private investigators may use third-party apps designed for tracking. These apps often require installation on the target device, making their use legally and ethically complex. Popular tracking apps include:
mSpy: Often marketed for parental control, this app can monitor a phone’s location, messages, and activity.
FlexiSPY: Offers advanced tracking features, but its use must comply with local laws.
Such software is generally legal only if used with the consent of the device owner.
e. Social Engineering
In some cases, private investigators might rely on social engineering techniques to gain access to location data. For example, they might trick the target into sharing their location via a deceptive message or link. While this is less common among reputable PIs, it highlights the importance of staying vigilant against such tactics.
3. Advanced Tracking Methods
a. IMEI and SIM Tracking
Every mobile device has a unique International Mobile Equipment Identity (IMEI) number. Similarly, SIM cards have unique identifiers that can be traced through the network. Private investigators may use IMEI or SIM tracking to locate a device if they have access to the necessary records or tools.
b. Stingray Devices
A Stingray is a portable device that mimics a cell tower, tricking nearby phones into connecting to it. Law enforcement agencies commonly use this technology, but private investigators typically avoid it due to its invasive nature and legal restrictions.
c. Geofencing
Geofencing creates a virtual perimeter around a specific area. If a device enters or exits this area, it triggers an alert. This technique can be used with GPS or mobile app tracking and is often employed in cases involving surveillance or asset protection.
4. Legal and Ethical Considerations
Tracking cell phones is a highly regulated activity due to privacy concerns. Private investigators must adhere to strict legal and ethical guidelines to avoid violating rights or committing crimes.
a. Consent
In most jurisdictions, private investigators can track a cell phone only with the consent of the device owner. For example, a parent might authorize tracking of their child’s phone, or an employer might monitor company-owned devices used by employees.
b. Privacy Laws
Privacy laws vary by country and region but generally prohibit unauthorized tracking. In the United States, the Electronic Communications Privacy Act (ECPA) regulates the interception of electronic communications, including location data. Similarly, the General Data Protection Regulation (GDPR) in the EU sets strict rules on personal data collection.
c. Ethical Practices
Reputable private investigators follow ethical practices to maintain professionalism and protect client interests. This includes:
Avoiding illegal tracking methods.
Respecting the privacy of non-consenting individuals.
Providing clear disclosures about the methods used.
Unethical practices, such as installing spyware without consent, can lead to legal repercussions and damage the investigator’s reputation.
5. The Role of Technology
Technology plays a central role in cell phone tracking. From software solutions to hardware tools, PIs have access to a wide range of resources that make their work more efficient. Some commonly used technologies include:
Tracking Apps: As mentioned earlier, these apps offer location-sharing features for authorized users.
Surveillance Tools: Tools like GPS trackers or geofencing systems allow investigators to monitor movement discreetly.
Data Analysis Software: PIs often use software to analyze call records, SMS logs, or app usage patterns, which can provide indirect clues about a person’s location.
6. Challenges in Cell Phone Tracking
Despite advancements, cell phone tracking comes with its challenges:
a. Legal Barriers
Obtaining location data without proper authorization can lead to legal consequences, limiting the methods available to private investigators.
b. Technological Limitations
Signal Interference: GPS tracking may not work in areas with poor satellite coverage, such as tunnels or densely packed buildings.
Device Security: Modern smartphones are equipped with advanced security features that prevent unauthorized access to location data.
c. Ethical Dilemmas
Balancing client demands with ethical considerations can be tricky. Investigators must ensure they don’t overstep boundaries while fulfilling their obligations.
7. Real-World Applications
Private investigators use cell phone tracking in various scenarios:
a. Missing Persons
Cell phone location data can provide vital clues in locating missing individuals, especially in time-sensitive cases.
b. Infidelity Investigations
PIs often track cell phones to gather evidence of infidelity. For example, GPS data might reveal that a spouse visited a suspicious location.
c. Corporate Investigations
In cases of corporate fraud or espionage, tracking company-owned devices can help identify rogue employees or uncover unauthorized activities.
d. Stalking and Harassment Cases
Cell phone tracking can help victims of stalking or harassment by identifying the perpetrator’s movements and providing evidence for legal action.
8. How to Protect Yourself from Unwanted Tracking
While private investigators are bound by legal and ethical guidelines, not everyone operates within the law. To protect yourself from unauthorized tracking:
Disable Location Services: Turn off GPS and location-sharing features when not needed.
Secure Your Device: Use strong passwords, enable two-factor authentication, and regularly update your phone’s software.
Avoid Suspicious Links: Be cautious about clicking on unknown links or downloading apps from unverified sources.
Use Anti-Spyware Apps: These can detect and remove tracking software from your device.
9. Conclusion
Private investigators play an essential role in uncovering the truth, and cell phone tracking is one of the many tools they use to achieve their goals. However, this practice requires a delicate balance of skill, technology, and adherence to legal and ethical standards.
For individuals and organizations seeking the services of a PI, it’s crucial to ensure they work with professionals who operate transparently and within the law. At the same time, understanding the methods and limitations of cell phone tracking can help protect your privacy and make informed decisions when hiring an investigator.
By staying informed about the capabilities and boundaries of cell phone tracking, you can better navigate the complexities of this modern investigative tool.
#private investigator#finding a hacker#spy phone#phone hacking tools#phone hacking service#phone hacking
1 note
·
View note
Text
The Hacker's War's

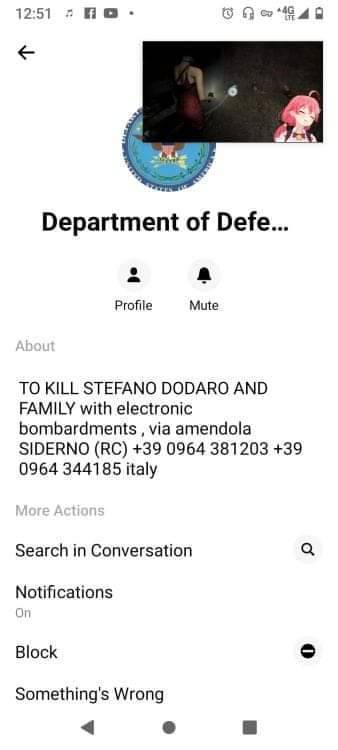
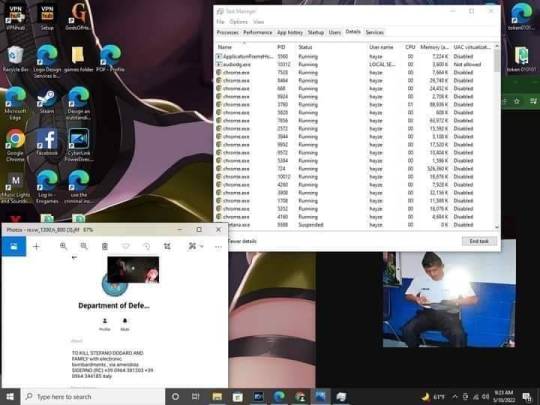

#The Resistance#war never changes#MTK Terrorist#Qualcomm.inc#Cyber Terrorist#Cyber Warfare#The War#To Kill Stephano Dedaro and Family with Electronic Bombardments#Illegal Taxation without representation#The Lambda War's ⚠⚠⚠🎲⚔#72 Million Dollar Case File received connected to The Hackers War's#Earned A Service Reward and Purple heart on a technical level Fighting for my Country#OOOooooraaaah!#For the Alliance#my the God be with you Always... 👍✌👌🎲 GG#USRA Gaming
6 notes
·
View notes
Text
A religion i can get behind
CAME OUT OF MY DADS PRINTER AT WORK TODAY..........

#catgirl hackers deliver an infinitely bigger service to society than any solider#using original tags#well tag#spindash#printer#helper#1115#catgirl hacker#huh#if sad check this tag#funny#photo#february 2023
127K notes
·
View notes
Text

Phishing Emails Hacker's Threats
#Hackers#phishing email#marketing agency#local business#digital marketing#digitalworldvision.online#seo services#seo services melbourne
0 notes
Text

Eva Green in Liaison (2023) Storm Warning
Ep1
Gabriel accepts a mission to withdraw two Syrian hackers. Alison and Banks face escalating cyberattacks in London.
"Liaison" is a contemporary thriller that explores how the mistakes of our past have the potential to destroy our future. The series blends action with an unpredictable, multi-layered plot in which espionage and political intrigue play out against a story of passionate and enduring love.
#Liaison#tv series#2023#mini tv series#Storm Warning#Eva Green#drama#thriller#cyber attacks#Syrian hackers#hackers#mercenary#french intelligence service#british home office#Damascus#London#Paris#spy thriller#relationships#just watched#series premiere
1 note
·
View note
Text
Paper Planes: A Breakdown through the Lens of Jade Ann Byrne
Paper Planes: A Breakdown through the Lens of Jade Ann Byrne Oct 19, 2024 by Jade Ann Byrne (Paladin Jade) Here’s the full blog post incorporating everything we discussed, including a deeper look at Jade Ann Byrne’s reimagined journey through the song “Paper Planes”: Planes, Codes & Hustles: The Jade Ann Byrne Anthem A Deep Dive into “Paper Planes” through the Lens of Jade Ann…
#Coder hustler anthem#Creative disruptor anthem#Cyber hustler anthem#Digital Cowgirl#Digital privacy and autonomy#Empowering female anthems#Female empowerment in tech#Female leadership in tech#High-end service industry evolution#Hustler song remix#Jade Ann Byrne#Jade Ann Byrne anthem#JadeAnnByrne#M.I.A. Paper Planes remix#Paladin hacker#Paladin Jade#Paper Planes analysis#Philanthropy and tech visionaries#Planes Codes and Hustles#Rebellious anthem#Space Country Trap#Tech and creativity anthem#Women in tech and music
0 notes
Text
Can Someone Hack Your Phone and Listen to Your Calls?

In today's digital era, where smartphones are essential for communication, concerns about phone security and privacy are more relevant than ever. The question often arises: can someone hack your phone and listen to your calls? In this article, we'll delve into the intricacies of phone hacking, explore the possibilities of call interception, and provide practical steps to safeguard your private conversations.
Understanding Phone Hacking
Phone hacking encompasses unauthorized access to a mobile device's data and functionalities. While hacking methods vary, the potential risk of call interception is a significant concern. Hackers who gain access to your device could potentially eavesdrop on your conversations, breaching your privacy and security.
Methods of Phone Hacking
Hackers employ an array of techniques to infiltrate devices, including exploiting vulnerabilities in operating systems and using malicious apps. The unsettling prospect of call hacking involves intercepting and listening to phone conversations, often without the victim's knowledge or consent.
VoIP Vulnerabilities
Voice over Internet Protocol (VoIP) technology, which allows voice calls over the internet, has become commonplace. However, this technology isn't immune to vulnerabilities. If hackers exploit weaknesses in VoIP, they might gain unauthorized access to calls, bypassing traditional cellular networks.
Eavesdropping on Calls
One alarming facet of phone hacking is call eavesdropping. By exploiting security gaps, hackers can gain access to live phone conversations, potentially compromising sensitive information. Instances of call interception highlight the urgency of taking protective measures.
Security Flaws in Mobile Networks
Mobile networks, while advanced, can still harbor security flaws. Hackers with the right skills can exploit these vulnerabilities to intercept calls. This underscores the need for robust security protocols to prevent unauthorized access.
Operating System Vulnerabilities
Outdated operating systems pose a considerable risk. When users fail to update their OS, they leave their devices susceptible to attacks. Security patches play a crucial role in preventing hacking attempts that could compromise calls.
Risks of Third-Party Apps
Third-party apps, particularly those without proper security measures, can serve as gateways for hackers. Malicious apps might infiltrate your device, granting unauthorized access to your calls and conversations.
Securing Your Phone
Protecting your phone is paramount in the digital age. Creating strong, unique passwords, regularly updating your device's software, and reviewing app permissions can significantly enhance your phone's security.
End-to-End Encryption
End-to-end encryption is a robust security measure that ensures the content of your calls remains confidential. This encryption method prevents unauthorized parties, including hackers, from deciphering your conversations.
Using Encrypted Communication Apps
Consider using encrypted messaging and calling apps to fortify your communication. Apps like Signal, WhatsApp, and Telegram offer end-to-end encryption, providing an extra layer of protection for your calls.
Network Security Measures
Secure network connections are essential. Utilizing Virtual Private Networks (VPNs) can add a layer of encryption to your internet traffic, safeguarding your calls from potential eavesdropping.
Recognizing Suspicious Activity
Being vigilant about unusual activity on your device is crucial. If you notice unexpected behavior, such as rapid battery drain or unfamiliar apps, it might indicate a breach. Promptly address such issues to protect your calls and data.
Expert Insights
According to cybersecurity experts, the risk of call hacking underscores the importance of proactive measures. Dr. Sarah Miller, a renowned cybersecurity analyst, emphasizes, "Users must prioritize device security, keep software up to date, and employ encryption technologies."
Balancing Convenience and Security
Striking a balance between convenience and security is essential. While security measures might seem inconvenient at times, safeguarding your privacy and protecting your calls from potential interception is worth the effort.
Conclusion
In a world where connectivity is integral to our lives, the possibility of someone hacking your phone and listening to your calls is a legitimate concern. By understanding the methods hackers use, employing robust security practices, and embracing encryption technologies, you can significantly reduce the risk of call interception. Remember, safeguarding your privacy requires ongoing vigilance and proactive action.
Frequently Asked Questions
Can hackers really listen to my phone calls? While it's possible for skilled hackers to intercept calls, taking security measures like encryption and using secure apps can greatly mitigate this risk.
How do hackers intercept phone calls? Hackers exploit vulnerabilities in mobile networks, operating systems, or apps to gain unauthorized access to calls.
What is end-to-end encryption, and how does it protect calls? End-to-end encryption ensures that only the sender and recipient can access the call content, preventing interception by hackers.
Are encrypted communication apps safe for calls? Yes, encrypted apps like Signal and WhatsApp offer strong security measures, making them safe choices for private calls.
What should I do if I suspect my calls are being intercepted? If you suspect call interception, immediately review your device for unusual activity, update your security settings, and consider seeking professional assistance to secure your phone.
#phone hacking tools#phone hacking#find a hacker#contact a hacker#finding a hacker#phone hacking service#cybersecurity#ethical hacking
4 notes
·
View notes