#ethical hacker
Explore tagged Tumblr posts
Text


🚫Do Not Re-Upload/Edit My Shots/Art Without My Permission🚫
[Bluesky][Patreon][Instagram][Tumblr][AO3][Nexus][Ko-Fi[Discord]
Human Spite with Detective Neve Gallus discussing a case
This is for Chapter 18 got 2 chapters before this happens XD
This pairing came as a surprise for me but it works so well for En Garde with Spite being an ex investigative Journalist turned ethical Hacker and Neve being a Police Detective XD
#spite#spite dellamorte#spite dragon age#spite x neve#Spite/Neve#neve gallus#neve#police detective#investigative journalist#ethical hacker#digital art#dragon age#dragon age veilguard#dragon age veilgaurd fan art#art: spite#art: Neve#art: Neve gallus#rookanis fic#en garde#fan fiction#fic art#digital artist#datv#art#artist#commissions open#I ship it#its not a pairing i've seen yet XD#it just sort of happened#XD
10 notes
·
View notes
Text

#mdshirajumbillahsiam#succession#the mandalorian#donald trump#margot robbie#taylor swift#ethical hacker#Red Team#cyber security specialist#hacking your mind#hackers
2 notes
·
View notes
Text
Web Search Engine) Links
Hidden Wiki Links – Now you are here then you already know about deep web links / The Hidden Wiki / Dark web links. But before sharing large amount of .onion directory I want to share some very good deep web links which always help you, because all these are deep web search engine links by the help of these search engine you can find any latest working deep web marketplace, hidden wiki or deep web sites list.
Dark Web Marketplace
Darknet markets is a solution for all type products because these type marketplace gives security to both party means seller or buyer, here you can use escrow service which make your payment mode more secure and clear. These type darknet markets places having some big number of listed categories and each category having more than thousands of unique products.
So simple, Today If you are planning to buy anything on deep web/the hidden wiki then these markets can provide you all type products buying or selling opportunity and here you also can get more than one alternatives into single category.
Mostly these deep web links having Drugs, Weapon, Digital products, Fraud, Services, Guide and Tutorials categories.
Bellow I am giving you some very popular deep web Links (dark web links), which you can try but before using these hidden wiki links, you need to register yourself on these darknet markets deep web link.
Note: If you are seller then these dark web marketplace links will proving milestone for you. where you can sell your products. and you can easily get targeted users or can achieve your goals within very short time span.
Note: I am not recommending you to visit these deep web sites (dark web links), I only added these deep web sites/onion sites here for education purpose or freedom information. If you visit these deep web sites then this is total on your risk, but I am recommending you here before visiting these deep web sites make sure focus on your privacy Security.
Recommended: For better security use NordVPN Onion Over Server + Tor Browser. ( Always run both software before access hidden Internet).
http://pwoah7foa6au2pul.onion – Marketplace – Alphabay is most popular and trusted deep web market. If you are truly looking something trusted on deep web then Alphabay is one of the best market, And this marketplace also has all major categories items like as fraud, drugs, chemicals, Guide & Tutorials, Digital Products, Services, and much more. According to current status, This marketplace has more than 3 Lakh listed items, and Just now support two type crypto currency which is Monero and Bitcoins.
Note: Before Buy any product here always check seller profile and available feedback and reviews.
http://lchudifyeqm4ldjj.onion/ – Marketplace – Dream Market : Second largest and most trusted dark web market, also you can say alternative of alphaby market, This marketplace place have drugs and digital products, and both these category have more than 75000+ listed items which is huge. If you are looking another great platform then dream market can provide you right items.
http://wallstyizjhkrvmj.onion/ – Marketplace – WallStreet Market – Another deep web markets which have more than 500+ listed items and each item are well categorized. According to category, You can get products related to drugs, counterfeits, jewelry & gold, services, Software & malware, security & hosting and much more.. and listing growing day to day. Marketplace support PGP and data encrypt by strong algorithm and also support German language. WallStreet has scam free status and multisig support.
http://udujmgcoqw6o4cp4.onion – Deep Web Market – UnderGround, one of the best and reliable deep web market with the possibility to pay in two times. Markets have more than thousands listed items and items related to Prepaid cards, PayPal account, Diploma, Passport, ID Cards, Driver License, Phone, Computer, Tablets, Game Console, Hacker, Weapons, Professional Killer, Humen Organs, Medicines and so on.
Note: This deep web links support JavaScript, If you want to access all function then you need to disable your javascript. But for security reasons, this is not good choice.
http://valhallaxmn3fydu.onion – Marketplace – Valhalla: This deep web marketplace is also very popular into deep web world and mostly people prefer this hidden wiki marketplace url for buying drugs, gadgets, hire services and lot many more things.
http://hansamkt2rr6nfg3.onion/ – Marketplace – Hansa is another famous deep web marketplace, which having more than 15K+ listed products. which is huge, and here you can buy all type products related to drugs, weapons, services, tutorials, services, electronics. It is one of most popular the dark web links.
http://zocaloczzecchoaa.onion – Marketplace – Zocalo Marketplace: Same as other marketplaces this .onion directory links also having good amount of listing product.
http://acropol4ti6ytzeh.onion – Marketplace – Acropolis forum also a good darknet markets, and community forum for sell and buy anything which you want, and also can find your questions answer in this dark web link.
http://tochka3evlj3sxdv.onion – Marketplace – Tochka Free Market: Tochka is also good darknet market where you can find mostly all type product related to education, hacking, drugs, weapon, services and software.
http://cryptomktgxdn2zd.onion – Marketplace – Crypto Market: Are you looking some other deep web links marketplace alternative then check out Crypto Market, Here you can participate in crypto market forum.
Warning: Before browsing the Deep web links/the dark web links, always run your NordVPN Onion Over VPN Server with Tor Browser. Since Tor Browser doesn’t provide your complete anonymity and privacy. You are completely safe only if you use NordVPN software.
http://kbhpodhnfxl3clb4.onion/ – not Evil (Tor Search Engine) for finding list of deep web sites, and one can easily find relevant information about the deep web/the hidden wiki which s/he want to get..
http://hss3uro2hsxfogfq.onion/ – not Evil search engine direct visit deep web links.
Note: Now Tor search engine has been moved on new name, now this popular search engine also known as not Evil, in the current date not Evil having more than 12477146 .onion links database.
Grams Search Engine and Associated Deep Web Services Links:
Grams is newly launched deep web search engine, this search engine getting good amount of popularity with in very short time and these days thousands of people use Grams for deep web access. You can access Grams by using below dark web link.
http://grams7enufi7jmdl.onion/ – Grams Search Darknet Markets and more.
Grams is not a single platform, but it’s like a Google, After couple month after grams launching date, Grams introduced some other product like Helix, Helix Light, Infodesk or Flow.
All three having unique features. If you want to access these three Grams sub product, then you can access by the help of Grams deep web link, or you can also go by the help of bellow given direct dark web links.
Note: Helix takes charge 2.5% every transaction.
Helix Tor Directory Link: http://grams7enufi7jmdl.onion/helix/light
InfoDesk: If you want to find any Vender, products or any specific marketplace tor link then this place can help you because here you can find some great marketplace which is trusted, and mostly people use in daily life.You can access InfoDesk using below deep web link.
InfoDesk Hidden Wiki Link: http://grams7enufi7jmdl.onion/infodesk
Flow: Now time for Flow, this is another popular deep web product which is also introduced by Grams, Hope you like Flow features because some person like this platform for Flow redirect feature.
According to this, if you want to access any darknet markets and you didn’t remember tor directory link then you can access these type hidden wiki url or deep web links easily.. GramsFlow makes this type complicated process more easy.
Now you only need to remember your marketplace name like Agora, Wiki, OutLaw, nuke or any other and you can access by help of Flow.
For Example: if you want to access the hidden wiki then you need to type in your Tor Browser gramsflow.com/wiki, then holla your link redirect on actual tor hidden directory.
For using awesome feature of Flow, visit below give deep web link.
Flow Tor Hidden Directory Link: http://grams7enufi7jmdl.onion/infodesk
http://skunkrdunsylcfqd.onion/sites.html – The Intel Wiki – This .onion site has the good number of trusted deep web links, which every day visited by most of the deep web users. But sometimes when I try to access this deep web link and I saw this dark web link is down. One more thing the Intel wiki also a forum which having great number of threads, which having useful information about the deep web and trusted deep web links/dark web links.
http://auutwvpt25zfyncd.onion/ – Tor Links Directory – OnionDir having more than 1200+ listed dark web sites, one better thing is here you can see on top how many dark net sites are live and how many deep web sites not and All .onions links are well categorized according to categories. For Example: If you are looking hacking or drugs related marketplace deep web links then you need to click on required category and visit any deep web sites which you like.
Forums & Community Deep Web Links(For Questions and Answers Conversation)
If you are eager to learn the darknet hidden wiki forum, also want to deep discuss on this sensitive topic and looking best deep web forums and the hidden wiki links and if you also looking how to access the deep web latest news and updates.
Deepwebsiteslinks is a best source where you can find all most popular deep web links, the hidden wiki news and darknet markets updates day to day and people visit here every day and participate into available threads.
Here I am giving you some popular deep web forums and darknet community links/deep web links, which are sharing the deep web/the hidden wiki related news and current updates everyday.
Privacy Tips: Always use NordVPN Onion Over Server with Tor browser while you accessing deep web sites. if you are thinking you are using TOR and you are safe. Let me clear for your privacy security. TOR doesn’t provide you full security. To access deep web with best anonymity and privacy, NordVPN and TOR both are must used software.
http://rrcc5xgpiuf3xe6p.onion/ – Forum/Community – IntelExchange is my favorite the dark web community because here you can find information thread and also can ask your question, I like this because here you can find mostly pre-discussed thread which having lot of meaningful information like best dark web search engines, dark web browser, most trusted the hidden wiki url.
http://parazite.nn.fi/roguesci/ – Forum – The Explosive and Weapon Forum, This hidden wiki link has some very good weapons and Explosive-related Documents and treads.
http://zw3crggtadila2sg.onion/imageboard/ – Forum – TorChan is darknet forum where you ask and participates into running chat thread, but If you are first time visitors then you don’t know how to visit this website then simple type given URL and after press enter you will get one popup on screen then you need to put given Username and Password into both field, ByDefault Username or Password is torchan2, torchan2. this is most popular the hidden wiki forum, where every day more than thousands or visitors visit and share something very interesting.
http://kpdqsslspgfwfjpw.onion/ – Forum/Community – A Chan, I think this deep web links having Russian language stuff, I can’t tell you about properly this site, and what type stuff this deep web sites have.
http://rhe4faeuhjs4ldc5.onion/ – Forum/Community – Do you have any query related to white hate hacking or black hat techniques, and you want to know some secret hacking tips then this hidden wiki community will proving helpful stuff and gernals. having more than 20+ active threads.
http://turkiyex6fkt46ra.onion/forum/ – Forum/Community/Non-English – Are you from Turkey, and looking your region related deep web forum then check out this hidden wiki forum link.
http://anonywebix6vi6gz.onion/ – Forum/Community – This is newly launched dark net forum. This hidden wiki link also will proving helpful for you, if you want to discuss about the deepweb, darknet markets or any others.
http://arcadian4nxs3pjr.onion/ – Forum/Community – ArcadiaNode is a dark net forum, Note: this deep web sites is not in the English language, that’s why I don’t have more idea about this forum.
http://5dhf54nxiuuv6jvs.onion/ – Forum/Community – AXAHis Community: This is another deepweb (hidden wiki) community where you can share your questions and knowledge, also can interact with related people.
Note: For access first time need registration.
http://p22i3mcdceionj36.onion/index.php – Forum/Community – XenForo: This deep web marketplace is a forum, but here you can buy Pfizer and GG249 Xanax products.
http://anonymzn3twqpxq5.onion/ – Forum/Community – Do you love DBA task and want to discuss on DBA related topics then check out this forum, hope this will proving helpful for you.
http://z2hjm7uhwisw5jm5.onion/ – Forum/Community – WallStreet: If you having any query about Tor or Looking some hidden web related answer then you can try on this deep web link.
http://support26v5pvkg6.onion/ – Forum/Community – Pedo Support Community: This Deep web forum is having more than 10K+ threads, like links, personal support, pedo literature, child love support, etc.
http://suprbayoubiexnmp.onion/ – Forum/Community – SuperBay: This community is having very good amount of thread and everyday lot’s of visitors use these threads, If you have some problem, then you can find relevant thread, and can resolve your problem.
https://blue.thevendingmachine.pw/index.php – Community/Forum – TheVendingMachine: This is very popular deep web community, every day more than 1000+ visitors visit this onion site, and share information. Here most popular thread is Torrent, Movies, General Discussion, TV shows, documentaries, etc.
http://npdaaf3s3f2xrmlo.onion/ – Tor Community – TwitterClon is just like twitter sites here you can share everything which you want into form of tweet, hope you also enjoy this sites, but mostly time I saw this site down.
NordVPN 2
http://ji7nj2et2kyrxpsh.onion/ – Forum – Dark Web Forum: I don’t know what you can find here because this is non-english forum but as per my guess, hope you can discuss about dark web and also can participate into active threads.
http://krainkasnuawwxmu.onion/ – Forum – Dark Web Community: This is the next Russian forum, where you can discuss about dark web community. If you have any question and want to know the right answers, then you can sign up on this forum and can find some easy solutions.
http://fbcy5ylyoeqzqzcr.onion/ – Forum – Moneybook: Another dark web forum where you can discuss about all popular topics related to dark web like as onion links, dark web markets review, PayPal accounts, music movie sites and much more, hope here you can find some good thread for you.
http://realpissxny3hgyl.onion/ – Forum/Porn – RealPiss Voyeur Community real uncensored female pee spycams: community for real girl piss videos and pictures, If you interested into such type content then you can try to visit realpiss site.
http://zzq7gpluliw6iq7l.onion/threadlist.php? – Forum – The Green Machine: Another deep web forum which provides discussion threads, do you have any questions and want to know the right answers then The green machine dark web links can provide you right information. But If you want to participate into available threads then you need to registered yourself on this deep web forum.
http://rutorzzmfflzllk5.onion/ – Forum/Russian – RuTor: Are you looking Russian forum, If yes then RuTor forum can provides you some great questions answer, but this forum not have more active thread, when I visited this deep web sites then I saw, website have only limited thread and also not have users engagement.
http://bm26rwk32m7u7rec.onion/ – Forum – The Majestic Garden: This is another deep web forum, which provides free forum SMF software solution, If you have any questions about this software then you can visit this deep web sites.
http://vrimutd6so6a565x.onion/ – Forum/Community – The Dark Lair: Forum for anonymous messaging, like as Twitter. Here you can share your status globally; Everyone can saw your status on this website. If they visit dark Lier, but you can’t post status on this site. Because you are not the registered member of Dark Lier, that’s the main reason. First your need to register on this website. Site also offers thread service and some good deep web links also.
http://answerstedhctbek.onion/ – Forum/Community – Hidden Answers: I think you already know about the yahoo questions and answers, This site offer same service just like yahoo questions and answers, If you have any questions and want to get your questions answers then you can try this deep web links.
http://saefjmgij57x5gky.onion/ – Forum/Community – TorStack – Q & A Community – Same Yahoo Questions and answer deep web sites, here you also can find right answers for your questions anonymously.
http://dnmavengeradt4vo.onion/ – Forum/Community – DNM Avengers: Another deep web forum site which provides communicating portal for deep web users anonymously. forum already have more than 100+ active threads. If you have any questions and want to know right answer anonymously. You can participate on available relevant thread. Also, you can share your skills in these running threads.
http://twittorxsun563wg.onion/ – Community/Social – Twitter Clone – This is microblogging site on the deep web, here you can share anything with all site readers anonymously. For status publishing you don’t need to signup here.
http://i2vzg7f44bj4l3r7.onion/ – Community – The Alliance – Another deep web social community sites, where users can share his though with all alliance community member or personally with your friends. One more thing, site also offers bookmarks service, by which you can tag any links on the Bookmarks category. which every site readers can read and visit anonymously.
http://www.smplace.com/forum/ – Forum/Community – S&M Place BDSM forum – Great Adult porn community for girls and boys, have all type threads where you can share adult porn videos and pictures, and also you can upload your videos and pictures collections. Forum have more than 70000+ active members.
http://rekt5jo5nuuadbie.onion/hiddenchan/ – Forum/Community – HideenChan – If you don’t know about the hidden chan. HiddenChan is just like as another community forum, here you can participate into current active threads. But hiddenchan is very engaging community here you can see every illegal activity related thread and also you can watch available videos and pictures which is uploaded by various current members.
http://start.jungswtfwgjwile2.onion/ – Forum/Community – Guys.WTF is primarily a community for people who love and love guys and / or feel sexually attracted by them. However, every interested person is expressly welcome. Here you want to help and support each other.
http://bfvfq7hjcdoinzo4.onion/ – Forum/Community – Darknet Erotic Forum – This deep web forum offer threads related to hot, geil, horny, porn, pervers and etc. If you want to discuss about these topics then you can participate on available threads. But without registration you can’t participate in this community.
http://rfwtogljhrrzxyrl.onion/ – Forum/Community – Lolita City – Another deep web forum, which offers hq legal stuff. Today when I visited this site, here only I found 2 threads. Hope here you can get your required information.
Email/Messaging/Chat related Deep Web Links
Warning: Always use NordVPN Tor Over Server + Tor Browser for complete security. Your privacy is not safe if you are accessing deep web links without VPN.
Same ad normal traditional in
#dark web#ethicalhacking#scammer#coding#contact a hacker#scammers#social media hackers#ethical hacker#deep web#hacker
5 notes
·
View notes
Text
Secure Or Recover Your Digital Life: Hire an Ethical Hacker
Welcome to our YouTube video on securing your digital life through the services of an ethical hacker. In this informative video, we will discuss the importance of protecting your email, social media accounts, and phone from unauthorized access. Our focus will be on hiring professional and ethical hackers from hackerslist. to enhance your online security.
youtube
#phone hacking service#contact a hacker#find a hacker#finding a hacker#ethical hacker#phone hacker#ig hack#Youtube
2 notes
·
View notes
Text
Trainee Ethical Hacker (Career Accelerator with Employment Guarantee)
Job title: Trainee Ethical Hacker (Career Accelerator with Employment Guarantee) Company: Nuyew Tech Academy Job description: you towards exciting opportunities in ethical hacking and cyber security. What the Ethical Hacker Career Accelerator at Nuyew Tech… in ethical hacking? At Nuyew Tech Academy, we specialise in providing aspiring tech professionals like you with the tools… Expected…
#5G#Azure#cloud-computing#cloud-native#edtech#embedded-systems#ethical AI#ethical hacker#game-dev#HPC#insurtech#Java#legaltech#low-code#marine-tech#metaverse#mlops#NLP#no-code#power-platform#product-management#prompt-engineering#quantum computing#remote-jobs#rpa#sharepoint#SoC#technical-writing#visa-sponsorship
0 notes
Text
"Zachary Levi and Halloween's hacker revolution: a new thought paradigm"
On a dark and dark night, when the Halloween masks presided over the roads, a mysterious hacker named Zachary Levi gave his revolutionary turning point. An enigmatic character, known in the undergrowth of the network for his ability in the systematic intrusion of the most unreachable computer systems. that night of Halloween, however, brought with him a new school of thought. By challenging the…
#"Armature Halloween#HistoryLessons#LezioniDiStoria#Computer Pirates#coste italiane#Cybersecurity#Cyberspace#Cyberspazio#Divine Justice#English.#Ethical Hacker#Giorno della Giustizia#green revolution#hacker#Hacker Etico#impresa di rivoluzione#New School#Nuova Scuola#Paradigma#Pirati Informatici#Sicurezza Informatica#Zachary Levi
0 notes
Text
https://www.amazon.co.uk/s?i=stripbooks&rh=p_27%3ADOBN%25C3%2588R%2BBROS&s=relevancerank&text=DOBN%C3%88R+BROS&ref=dp_byline_sr_book_1


#word search#cute emoji#ethical hacker#hacking#cybersecurity#custom emoji#emoji game#relaxation#gifts for her#giftforher#birthday gift#gift for him#gift ideas
0 notes
Text
Inside the Mind of a Hacker: How Ethical Hackers Outsmart Cybercriminals

In today’s digital age, the threat posed by cybercriminals is more pronounced than ever. As organizations increasingly rely on technology, the need for robust cyber security measures has become paramount. This is where ethical hackers step in, using their skills to protect systems from malicious attacks. For those interested in pursuing a career in this critical field, a cyber security course in Thane can provide the foundational knowledge and practical skills needed to succeed. Let’s delve into the mind of a hacker and explore how ethical hackers outsmart their adversaries.
Understanding the Hacker Mindset
To effectively combat cybercrime, it’s essential to understand the mindset of hackers. Cybercriminals are often driven by financial gain, political motivations, or even the thrill of the challenge. They continuously evolve their strategies, using sophisticated techniques to exploit vulnerabilities in systems. Ethical hackers, on the other hand, adopt a similar mindset but with the intention of safeguarding information rather than compromising it.
By enrolling in a cyber security course in Thane, aspiring ethical hackers can learn to think like cybercriminals. This includes understanding various hacking techniques, such as phishing, malware deployment, and social engineering. Equipped with this knowledge, they can develop more effective defense mechanisms against these threats.
The Role of Ethical Hackers
Ethical hackers play a crucial role in the realm of cyber security. Their primary objective is to identify and rectify vulnerabilities in systems before they can be exploited by malicious hackers. They employ a variety of tools and techniques to conduct penetration testing, vulnerability assessments, and security audits.
One of the significant benefits of taking a cyber security course in Thane is gaining hands-on experience with these tools. Students learn how to use software such as Wireshark for network analysis, Metasploit for penetration testing, and various programming languages for writing scripts and automating tasks. This practical knowledge is invaluable, as it allows ethical hackers to replicate the tactics used by cybercriminals and anticipate their next move.
Strategies Used by Ethical Hackers
Ethical hackers employ several strategies to outsmart cybercriminals. Here are a few key approaches they utilize:
Continuous Learning: The cyber security landscape is always changing, with new threats emerging regularly. Ethical hackers stay updated with the latest trends by participating in workshops, webinars, and, most importantly, taking comprehensive courses like a cyber security course in Thane. This continuous education allows them to adapt their strategies and tools to counteract evolving threats.
Red Team vs. Blue Team Exercises: In many training programs, ethical hackers participate in simulated attacks, often referred to as Red Team exercises. In these scenarios, they play the role of attackers, while a Blue Team defends against them. This collaborative environment helps them understand both sides of the equation, sharpening their skills in a practical context.
Threat Intelligence: Ethical hackers also rely on threat intelligence to predict potential attacks. By analyzing data from previous cyber incidents, they can identify patterns and trends, helping organizations prepare for future threats. Many cyber security courses in Thane cover this vital area, ensuring students can gather and analyze intelligence effectively.
Importance of Ethics in Hacking
A critical aspect of being an ethical hacker is adhering to a strict code of ethics. Unlike cybercriminals, ethical hackers operate with integrity and transparency. They obtain proper authorization before testing any system and report vulnerabilities to the appropriate stakeholders without exploiting them.
This ethical framework is often emphasized in cyber security courses in Thane. Students learn not only the technical skills needed for hacking but also the legal and ethical implications of their work. Understanding these principles is essential for fostering trust and accountability in the cyber security field.
Career Opportunities for Ethical Hackers
The demand for ethical hackers continues to grow as organizations prioritize cyber security. A cyber security course in Thane can open various career paths, including roles as penetration testers, security analysts, and security consultants. With businesses of all sizes seeking to bolster their defenses, skilled ethical hackers are becoming increasingly valuable assets.
In addition to traditional employment, ethical hackers can also explore freelance opportunities or consultancy roles, providing their expertise to organizations on a contract basis. The versatility of this career path makes it an attractive option for those passionate about technology and security.
Conclusion
As cyber threats continue to evolve, the importance of ethical hackers cannot be overstated. Their ability to think like cybercriminals while maintaining a commitment to ethical standards is what sets them apart. For those considering a career in this dynamic field, a cyber security course in Thane provides the essential skills and knowledge required to excel.
By understanding the hacker mindset, mastering essential tools, and adhering to ethical principles, ethical hackers play a pivotal role in safeguarding digital assets. As we look to the future, the demand for these professionals will only increase, making now the perfect time to embark on a journey into the world of cyber security.
#cyber security course#cyber security#cyber attack#cyber security threats#technology#data security#ethical hacking#ethical hacker#network security#dataprotection#hacking#security#network securiy#cybercrime#cyber security course in thane#ethical hacking course
1 note
·
View note
Text
𝘿𝙖𝙧𝙠𝙒𝙚𝙗 𝙀𝙣𝙩𝙧𝙚𝙥𝙧𝙚𝙣𝙚𝙪𝙧
#darkweb entrepreneur hacker cybersecurity#ethicalhacking#scammer#coding#dark web#contact a hacker#ethical hacker#social media hackers#deep web#hacker#scammers
2 notes
·
View notes
Text
Reader pov:
It was just another regular mission. I’m not sure what counts as regular when you’re on probation within the military about to be thrown out but hey that’s what i get. I should introduce myself my name is Phoenix and I am an ex con. Trust me I know. I had just completed a transaction when blue lights suddenly appeared surrounding me and then wrestled into handcuffs. Hey im not going down without a fight. The next moment i know a black bag is thrown over my head and led into a car.
I don’t remember how long it was or the amount of twists and tuns i had to take to get me where they wanted bye but i could tell that somebody wanted me badly. The next thing i know the bag is being ripped off my head and im being secured into an a dark room with a chair and a table. I was just getting used to my surroundings when a military officer came in. It was weird though he wasn’t in standard military uniform but you could tell that he was military.
Reader: So do I have you to thank for the cushy accommodations or should i be thanking someone else?
He chuckles.
Captain Price: Well they said that you were a charmer at least. Yes you can thank me. I’ve been interested in you for a while ever since you helped out my team around six months ago. That was you am I right?
Reader: Aye. That makes you Captain Price doesn’t it?
Captain Price: So you have heard of me. I apologise for how you were brought it. We took the assumption that you may not be cooperative if we knocked on your front door.
Reader: Your right on that account Captain I wouldn’t have been. So what has brought you into needing my help Captain?
Captain Price: My team and I are in need of some help that we think you help us with. We are looking for a hacker and we think you might be able to help us with. Are you in?
Reader: I’m intrigued Captain. Tell me more.
0 notes
Text
Certified Ethical Hacker (CEH) training with certification voucher(10 HC)
Job title: Certified Ethical Hacker (CEH) training with certification voucher(10 HC) Company: Overture Rede Job description: This is a remote position. Job Title: Certified Ethical Hacker (CEH) training with certification voucher(10 HC… an experienced Certified Ethical Hacker (CEH) trainer to deliver high-quality professional training sessions. The trainer… Expected salary: Location: Delhi Job…
0 notes
Text
Curso gratuito Hacker Etico - Ethical Hacker de Cisco Networking Academy
El curso ethical hacker es una formación online y gratuita que te ofrece Cisco Networking Academy, el programa educativo de Cisco Systems, líder mundial en tecnologías de redes e Internet. El curso está diseñado para proporcionarte una sólida comprensión de los principios de ciberseguridad, repasando y actualizando los fundamentos de la ciberseguridad desde una perspectiva de la seguridad…

View On WordPress
0 notes
Text
The Ethics of Hacking Safeguarding the Cyber World
0 notes
Text
"Exploring the Expansive Scope of Ethical Hacking"
Understanding the Scope of Ethical Hacking
Ethical hacking, often referred to as "white hat hacking," is a fascinating and crucial field in the realm of cybersecurity. It involves professionals, known as ethical hackers or penetration testers, who use their expertise to identify and address vulnerabilities in computer systems, networks, and applications. In this Quora answer, I'll provide you with insights into the scope of ethical hacking, without diving too deep into technical jargon.
What is Ethical Hacking?
Ethical hacking is a legal and authorized practice of attempting to exploit computer systems for the purpose of making them more secure. Unlike malicious hackers who have harmful intentions, ethical hackers work to find and fix vulnerabilities before the bad actors can exploit them.
Scope of Ethical Hacking
1. Security Assessment
Ethical hackers are hired to perform comprehensive security assessments of organizations' digital assets. This involves evaluating the security of networks, websites, databases, and applications. By simulating cyberattacks, they identify weaknesses and suggest improvements to strengthen the security posture.
2. Penetration Testing
Penetration testing is a crucial aspect of ethical hacking. Here, experts use various tools and techniques to simulate real-world attacks on an organization's systems. They assess how well the security measures hold up and provide recommendations for enhancing security.
3. Vulnerability Assessment
Ethical hackers conduct vulnerability assessments to discover and categorize vulnerabilities within systems. They prioritize these vulnerabilities based on their potential impact and help organizations mitigate them effectively.
4. Social Engineering Testing
Social engineering is a tactic used by hackers to manipulate individuals into revealing sensitive information. Ethical hackers conduct social engineering tests to assess the vulnerability of an organization's staff to such attacks. This helps in raising awareness and implementing security awareness training.
5. Web Application Testing
With the proliferation of web applications, securing them has become paramount. Ethical hackers evaluate web applications for vulnerabilities like SQL injection, cross-site scripting (XSS), and more, ensuring that these applications don't become entry points for attackers.
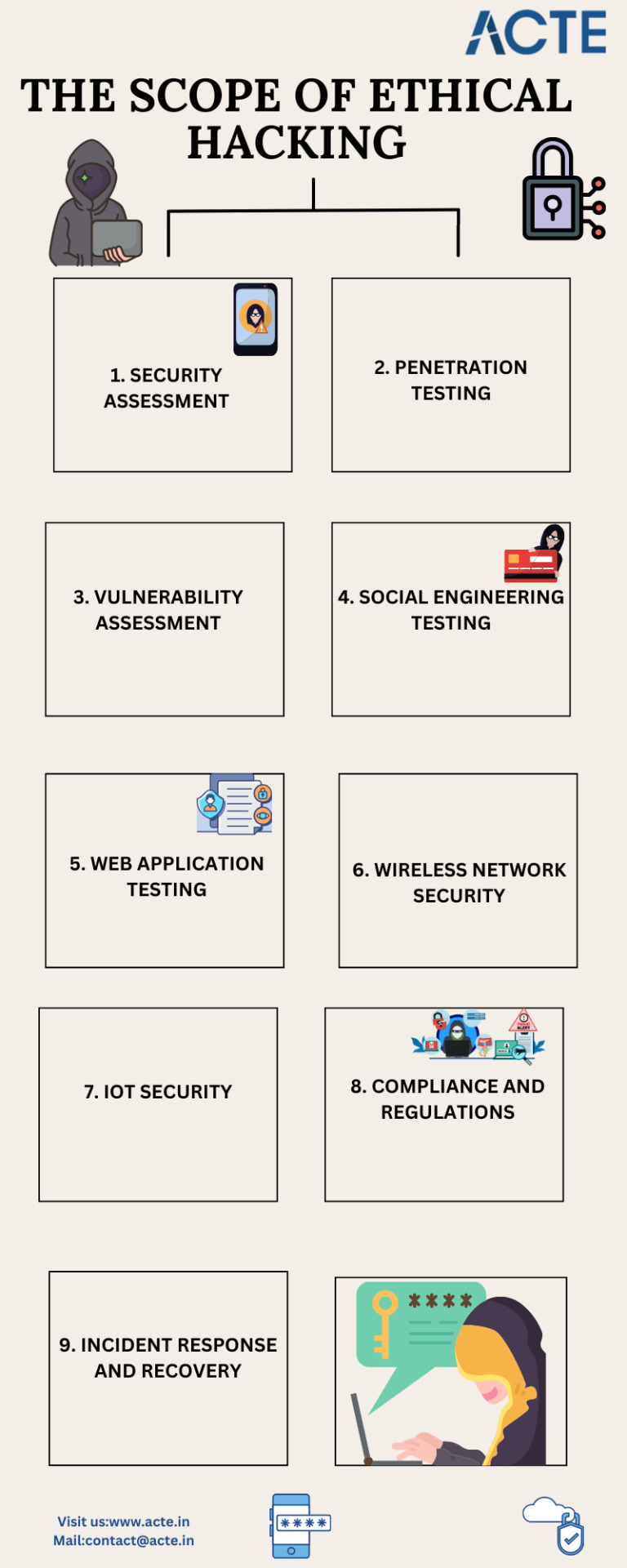
6. Wireless Network Security
Wireless networks are susceptible to various attacks. Ethical hackers assess the security of Wi-Fi networks, identifying weak encryption, unauthorized access, and other vulnerabilities.
7. IoT Security
As the Internet of Things (IoT) devices become ubiquitous, ethical hackers also focus on evaluating the security of IoT devices and networks to prevent potential breaches.
8. Compliance and Regulations
Ethical hackers assist organizations in ensuring compliance with industry-specific regulations and standards. This is crucial for businesses handling sensitive data.
9. Incident Response and Recovery
In the unfortunate event of a cyber incident, ethical hackers play a crucial role in identifying the source, containing the breach, and helping with recovery efforts.
The scope of ethical hacking is vast and ever-evolving. It's a vital component of modern cybersecurity, helping organizations stay one step ahead of malicious actors. Ethical hackers are the frontline defenders of digital security, and their expertise is in high demand.
In a world where cyber threats are constant, ethical hacking is not just a career but a necessity for safeguarding our digital lives.
Remember that consistent practice, working on real-world projects, and seeking help from online communities and resources like blogs, tutorials, and forums can significantly accelerate your learning process. Don’t rush; focus on understanding the concepts thoroughly, as a strong foundation is key to becoming an expert in ethical hacking If you want to learn more about Ethical Hacking, I highly recommend contacting ACTE Technologies because they offer certifications and job placement opportunities. Experienced teachers can help you learn better. You can find these services both online and offline. If you feel that my response has been helpful, follow me and it will encourage me to upload more content about Ethical hacking. Thanks for spending your valuable time. Have a great day.
1 note
·
View note