#emergency information software
Explore tagged Tumblr posts
Text
Innovative Tools for Effective Emergency Equipment Management
In today's fast-paced and complex world, managing emergency equipment effectively is crucial for ensuring the safety of occupants and minimizing damage during a crisis. Emergency information software plays a pivotal role in this process, providing quick access to critical data and improving response times. By leveraging emergency information software, organizations can streamline their emergency preparedness and response strategies, ensuring that all necessary information is readily available when it is needed most.
The Importance of Emergency Information Software
Emergency information software is designed to help organizations manage and access critical information related to emergency equipment and procedures. This software can store and organize a wide range of data, including floor plans, evacuation routes, emergency contact information, and maintenance logs for emergency equipment. By having this information readily accessible, facilities can ensure that they are prepared to respond quickly and effectively to any emergency situation.
Key Features of Emergency Information Software
1. Real-Time Access to Critical Information
One of the most significant advantages of emergency information software is the ability to access critical information in real time. Whether it's a fire, gas leak, or other emergency, having instant access to floor plans, evacuation routes, and emergency equipment locations can make a significant difference in the outcome. This feature ensures that facility managers, first responders, and other key personnel have the information they need to make informed decisions quickly.
2. Mobile Compatibility
In an emergency, time is of the essence. Emergency information software that is compatible with mobile devices allows facility managers and emergency responders to access critical information on the go. This flexibility ensures that even if they are not at their desks, they can still access the necessary data to manage the situation effectively. Mobile compatibility is especially important in large facilities where managers may need to move quickly between different areas.
3. Integration with Existing Systems
Effective emergency information software should integrate seamlessly with existing facility management systems, such as CMMS (Computerized Maintenance Management Systems) or IWMS (Integrated Workplace Management Systems). This integration allows for a more streamlined approach to managing emergency equipment and procedures, ensuring that all relevant data is available in one centralized location. By integrating with existing systems, organizations can enhance their overall emergency preparedness and response capabilities.
4. Automated Alerts and Notifications
During an emergency, timely communication is critical. Emergency information software can provide automated alerts and notifications to key personnel, ensuring that everyone is informed and ready to respond. These alerts can be sent via email, text message, or push notifications, providing immediate updates on the situation. Automated alerts help to reduce response times and ensure that all necessary actions are taken promptly.
5. Comprehensive Reporting and Analytics
After an emergency, it is essential to review and analyze the response to identify areas for improvement. Emergency information software can generate comprehensive reports and analytics, providing valuable insights into how the situation was managed. These reports can include details on response times, equipment usage, and any issues encountered during the emergency. By analyzing this data, organizations can enhance their emergency preparedness and improve their response strategies for future incidents.
6. User-Friendly Interface
Emergency information software should be user-friendly and intuitive, allowing personnel to access and navigate the system quickly. A well-designed interface ensures that even those with limited technical knowledge can use the software effectively. This ease of use is critical during an emergency when stress levels are high, and quick access to information is paramount.
Conclusion
Investing in innovative tools for effective emergency equipment management is essential for ensuring the safety of occupants and minimizing damage during a crisis. Emergency information software provides a comprehensive solution for managing and accessing critical data, improving response times, and enhancing overall emergency preparedness. By leveraging the key features of emergency information software, organizations can streamline their emergency response strategies, ensuring that they are ready to handle any situation with confidence and efficiency.
Implementing a robust emergency information software solution can be a game-changer for facilities management, providing the tools needed to protect people, property, and assets during emergencies. Don't wait until the next crisis—start exploring the benefits of emergency information software today and take proactive steps to enhance your emergency equipment management capabilities.
0 notes
Text
#Information Technology#IT industry#IT services#IT solutions#IT infrastructure#IT support#IT trends#Emerging technologies#IT networks#Data storage#IT security software#IT management tools
0 notes
Text

We at MicroBurstMedia, a digital solutions company is excited to announce the launch of our new book—The Beginners Guide to AI Automation Setup System!
Highly recommended if you're a beginner looking to get started in the online workspace, learn how to turn your set of skills and experience into your own automated sales system for business and or work purposes, our book is available and on sale as we continue to gain interests among tech users, business startups and entrepreneurs across web platforms.
This book breaks down the construct of this topic on a micro level scale, along with setup instructions showing how we got started and how you can too providing AI computer software system recommendations making it accessible for everyone—even if you’re not tech-savvy—by any means we ensure you get as much out of it guaranteed along with online support to assist in answering any questions you may have!
🔊But it doesn't stop there, you can also get it in an eBook version which is available at an introductory price of $29.99, now on sale (90% OFF) at $3.00 for a LIMITED-TIME!
In addition, we are providing digital copies of our presentation guide ♦️FOR FREE♦️ which you can access at anytime. Want in on this info? Send us a DM!
This Information📚 Was brought to You by MicroBurstMedia, a digital solutions company. 🏢
#software#information technology#cyber security#techinnovation#analytics#developer#technologynews#technology#technologies#emerging technologies#advanced technologies#new technologies#innovation#tech
0 notes
Text
Crisis Management Tools for Rapid Response & Recovery - Konnect Insights
Crisis Management helps you Navigate Crises effectively. Crisis management solutions gives swift action and strategic recovery in any situation. Book a Demo now!

#social media and crisis management#social crisis and its management#crisis management solution#crisis management plan social media#brand reputation crisis management#social crisis management#crisis information management software#crisis management business#crisis management and social media#crisis management company#crisis management firms#emergency management software#crisis management tools#crisis management solutions#crisis management services
0 notes
Text
Stay Ahead of the Curve: Top Emerging Software Technologies for 2024! How Texter Can Help You Harness Their Power

Introduction:
In the present quickly developing mechanical scene, remaining on the ball is fundamental for organizations and people. As we look forward to 2024, a few arising programming innovations are ready to upset different ventures. In this article, we will investigate these state-of-the-art advances and how Texter can help you saddle their ability to accomplish your objectives.
Artificial Intelligence and Machine Learning:
Artificial intelligence and Machine Learning have previously had a tremendous effect in different fields. In 2024, we hope to see significantly more noteworthy headway around there. Man-made intelligence-fuelled applications can robotize monotonous undertakings, upgrade dynamic cycles, and give important experiences. Texter has practical experience in creating man-made intelligence and ML arrangements modified to your particular prerequisites, engaging you to open up the maximum capacity of these advancements.
Blockchain Technology:
The decentralized and secure characteristics of blockchain have led to its increasing adoption. We predict a broader industry use of Blockchain in 2024, encompassing banking, supply chain management, healthcare, and other sectors. Texter provides blockchain development and consulting services, assisting companies in implementing blockchain technologies to improve transparency, expedite processes, and safeguard data integrity.
Extended Reality (XR):
Extended Reality (XR) is the result of the confluence of Augmented Reality (AR) and Virtual Reality (VR). It is anticipated that XR will advance significantly in 2024 in sectors like gaming, healthcare, education, and training. By generating immersive and engaging experiences, Texter can help you fully use the potential of XR and connect with your audience in a way that has never been possible.
Internet of Things (IoT):
The way we live and work is still changing as a result of the Internet of Things. IoT makes it possible for common things to be connected to the internet, improving automation, data collecting, and analysis. We may anticipate much more IoT integration in industrial processes, healthcare systems, smart cities, and smart homes by 2024. To assist you in making use of the promise of IoT for increased productivity and efficiency, Texter provides IoT development and consulting services.
Edge Computing:
A decentralized computing infrastructure referred to as "edge computing" moves the storage and processing of data closer to the location wherein the data is generated. Edge computing is anticipated to resolve issues with latency, bandwidth, and security in the Internet of Things and artificial intelligence age by 2024. By using edge computing technologies, Texter can help you give your apps better security, lower latency, and quicker processing.
Quantum Computing:
Based on the ideas of quantum physics, quantum computing bears the promise of revolutionizing processing power and providing effective solutions to challenging issues. We anticipate notable developments in this sector in 2024. Texter continues to be at the forefront of research on quantum computing, providing advisory and development services to investigate opportunities and fully use the potential of this new technology.
Conclusion:
2024 has a plethora of fascinating opportunities in the realm of software technology. Businesses can obtain a competitive advantage and individuals can discover new prospects by adopting these modern technologies. As your guide on this revolutionary trip, Texter offers its experience in artificial intelligence, machine learning, blockchain, XR, Internet of Things I edge computing, and quantum computing. Keep up with the times and use Texter to better create the future of your company by utilizing the versatility of these cutting-edge software innovations.
#data science#developer community#learn python#it course#non it course#it training#it classes#it training courses#it certifications courses#it training classes#it learning courses#it course information#non it to it courses#Software Development#Emerging Technologies#Low Code Development#python language#programming community#programming language in python#codinglife#automation#machine learning#artificial intelligence
0 notes
Text
2024 Market Trends Shaped by Emerging Technologies
In the rapidly evolving tech landscape, keeping ahead of the game is vital for businesses aiming to succeed. As we approach 2024, the landscape of technological advancements is set to redefine industries and reshape market dynamics. Let’s delve into the top five technology trends that are poised to influence the market in the upcoming year.
What are the big tech trends for 2024?
Several significant technology trends are anticipated to dominate 2024, shaping various sectors and consumer experiences. From advancements in artificial intelligence to the proliferation of edge computing, the tech arena is buzzing with innovation and transformation.
What will be trending in 2024?
The trends that are expected to gain momentum in 2024 encompass diverse areas such as quantum computing, extended reality (XR), blockchain applications, cybersecurity enhancements, and the Internet of Things (IoT) evolution.
What is the market trend in digital transformation in 2024?
The market trend in digital transformation for 2024 revolves around organizations accelerating their adoption of digital tools and strategies. This shift aims to enhance operational efficiency, improve customer experiences, and drive innovation across industries.
What will technology look like in 2024?
Technology in 2024 will be characterized by a fusion of cutting-edge innovations. It will bring forth smarter AI-driven solutions, immersive XR experiences, secure blockchain applications, interconnected IoT ecosystems, and the increasing utilization of edge computing for faster data processing.
Now, let’s explore the top five technologies that are set to make a significant impact on the market in 2024:
1. Artificial Intelligence (AI) Advancements
AI will continue its rapid evolution, offering more sophisticated algorithms and capabilities. It will be integrated into various sectors, enabling predictive analytics, personalized customer experiences, and automation across industries.
2. Extended Reality (XR) Revolution
The convergence of augmented reality (AR), virtual reality (VR), and mixed reality (MR) will transform how individuals interact with digital content. XR applications will find their way into entertainment, education, healthcare, and enterprise solutions, offering immersive experiences.
3. Blockchain Applications Expansion
Blockchain technology will extend beyond cryptocurrencies, finding applications in supply chain management, secure transactions, digital identities, and decentralized finance (DeFi), promising enhanced transparency and security.
4. Cybersecurity Enhancements
With the increasing digitization of businesses, cybersecurity will remain a critical focus. Innovations in cybersecurity will involve AI-powered threat detection, zero-trust security models, and advanced encryption techniques to safeguard data and systems.
5. Internet of Things (IoT) Evolution
The IoT landscape will continue to grow, connecting devices and systems to enable smarter functionalities in homes, cities, healthcare, and industries. Edge computing will play a pivotal role in processing IoT-generated data closer to the source, ensuring faster and more efficient operations.
Conclusion
The year 2024 promises an exciting trajectory latest information technology trends, where innovation and adaptation will be the cornerstone of success. Keeping abreast of these top tech trends and leveraging the latest advancements will be instrumental for businesses striving to remain competitive and relevant in an ever-evolving market landscape.
Remember, embracing these emerging technologies and staying agile in their implementation will define the success story for businesses venturing into the dynamic realm of 2024’s tech-driven market.
#5 TECHNOLOGY TRENDS THAT WILL SHAPE 2024#5 TYPES OF EMERGING TECHNOLOGIES#GARTNER TECHNOLOGY TRENDS 2024#LATEST INFORMATION TECHNOLOGY TRENDS#LATEST TECHNOLOGIES IN SOFTWARE INDUSTRY#TOP NEW TECHNOLOGIES#TOP TECH TRENDS 2024
0 notes
Text
fucking client emailed in requesting a license last night at 10, called today before nine asking for the license and if I could hurry this along because it was urgent; being the person that I am I went to go find some more information and discovered that the customer wants to do an in-place upgrade on a nine-year-old free license to a recent server license which is.
A) not possible with the service pack they have installed B) probably not compatible with the two kinds of software they have talking to the database C) probably not compatible with their actual server, which blew up spectacularly in January.
(all of which is to say nothing about the wide variety of possible ways to purchase and install the license, but probably standard is what they want even if they're technically too big for it)
I talk to my team, most of whom do not have much experience with upgrades/migrations for this software and we all agree that more research into their environment is needed, including possibly calls with their other software vendors and also possibly maybe replacing their twelve year old server.
Call the client at 2pm and let him know that this project is going to be more rigorous than just ordering a license, let them know that this isn't being dropped or ignored, but we need more information and will be in contact when more of the team knows what's going on.
5:14 PM, my coworker messages me "hey, do we have a tenant for this client?"
I message my coworker: "fucking lol, this is about their license, isn't it?"
It is about their license. They have sent in an emergency after hours ticket describing the issue as urgent: they have purchased the license on their own from a consumer vendor unaware of the fact that they need admin access to a tenant to download the software.
I create a tenant for the client and document the information, then provide the tenant ID.
And then since it's urgent, it's an emergency, I begin gathering data and composing an email.
The license won't populate to the tenant for hours at least and probably not for a full day.
They didn't actually tell us what license they've got, but if they plan to use it with one flavor of software they've got they probably need a secondary license they were totally unaware of.
I have found no evidence whatsoever that this license is compatible with their other software.
I hop into an after hours meeting with one of our tier three consultants to get the exact version number of the software and confirm that there is not a straightforward upgrade path between the license they have and the license they want.
I send an email advising that if their developer wants to make an upgrade they MUST back up the database because we have emergency backups, not database backups, let them know in writing "per our conversation this afternoon, this is why we don't think this will work" and thank them cheerfully, letting them know to reach out if they have questions about licensing.
hit send at half past eight.
Combined after hours work on this "emergency" "critical" "urgent" ticket is now probably about half the hardware cost of a better server.
I get that emergencies happen, but buddy if I tell you "hey, I know you are in a rush with this but we have to take our time to do this correctly" and you ignore me and make me stay late to handle your "critical" ticket, you and I both are not going to have a good time.
2K notes
·
View notes
Text
Epic Systems, a lethal health record monopolist

Epic Systems makes the dominant electronic health record (EHR) system in America; if you're a doctor, chances are you are required to use it, and for every hour a doctor spends with a patient, they have to spend two hours doing clinically useless bureaucratic data-entry on an Epic EHR.
How could a product so manifestly unfit for purpose be the absolute market leader? Simple: as Robert Kuttner describes in an excellent feature in The American Prospect, Epic may be a clinical disaster, but it's a profit-generating miracle:
https://prospect.org/health/2024-10-01-epic-dystopia/
At the core of Epic's value proposition is "upcoding," a form of billing fraud that is beloved of hospital administrators, including the "nonprofit" hospitals that generate vast fortunes that are somehow not characterized as profits. Here's a particularly egregious form of upcoding: back in 2020, the Poudre Valley Hospital in Ft Collins, CO locked all its doors except the ER entrance. Every patient entering the hospital, including those receiving absolutely routine care, was therefore processed as an "emergency."
In April 2020, Caitlin Wells Salerno – a pregnant biologist – drove to Poudre Valley with normal labor pains. She walked herself up to obstetrics, declining the offer of a wheelchair, stopping only to snap a cheeky selfie. Nevertheless, the hospital recorded her normal, uncomplicated birth as a Level 5 emergency – comparable to a major heart-attack – and whacked her with a $2755 bill for emergency care:
https://pluralistic.net/2021/10/27/crossing-a-line/#zero-fucks-given
Upcoding has its origins in the Reagan revolution, when the market-worshipping cultists he'd put in charge of health care created the "Prospective Payment System," which paid a lump sum for care. The idea was to incentivize hospitals to provide efficient care, since they could keep the difference between whatever they spent getting you better and the set PPS amount that Medicare would reimburse them. Hospitals responded by inventing upcoding: a patient with controlled, long-term coronary disease who showed up with a broken leg would get coded for the coronary condition and the cast, and the hospital would pocket both lump sums:
https://pluralistic.net/2024/06/13/a-punch-in-the-guts/#hayek-pilled
The reason hospital administrators love Epic, and pay gigantic sums for systemwide software licenses, is directly connected to the two hours that doctors spent filling in Epic forms for every hour they spend treating patients. Epic collects all that extra information in order to identify potential sources of plausible upcodes, which allows hospitals to bill patients, insurers, and Medicare through the nose for routine care. Epic can automatically recode "diabetes with no complications" from a Hierarchical Condition Category code 19 (worth $894.40) as "diabetes with kidney failure," code 18 and 136, which gooses the reimbursement to $1273.60.
Epic snitches on doctors to their bosses, giving them a dashboard to track doctors' compliance with upcoding suggestions. One of Kuttner's doctor sources says her supervisor contacts her with questions like, "That appointment was a 2. Don’t you think it might be a 3?"
Robert Kuttner is the perfect journalist to unravel the Epic scam. As a journalist who wrote for The New England Journal of Medicine, he's got an insider's knowledge of the health industry, and plenty of sources among health professionals. As he tells it, Epic is a cultlike, insular company that employs 12.500 people in its hometown of Verona, WI.
The EHR industry's origins start with a GW Bush-era law called the HITECH Act, which was later folded into Obama's Recovery Act in 2009. Obama provided $27b to hospitals that installed EHR systems. These systems had to more than track patient outcomes – they also provided the data for pay-for-performance incentives. EHRs were already trying to do something very complicated – track health outcomes – but now they were also meant to underpin a cockamamie "incentives" program that was supposed to provide a carrot to the health industry so it would stop killing people and ripping off Medicare. EHRs devolved into obscenely complex spaghetti systems that doctors and nurses loathed on sight.
But there was one group that loved EHRs: hospital administrators and the private companies offering Medicare Advantage plans (which also benefited from upcoding patients in order to soak Uncle Sucker):
https://www.ncbi.nlm.nih.gov/pmc/articles/PMC8649706/
The spread of EHRs neatly tracks with a spike in upcharging: "from 2014 through 2019, the number of hospital stays billed at the highest severity level increased almost 20 percent…the number of stays billed at each of the other severity levels decreased":
https://oig.hhs.gov/oei/reports/OEI-02-18-00380.pdf
The purpose of a system is what it does. Epic's industry-dominating EHR is great at price-gouging, but it sucks as a clinical tool – it takes 18 keystrokes just to enter a prescription:
https://jamanetwork.com/journals/jamanetworkopen/fullarticle/2729481
Doctors need to see patients, but their bosses demand that they satisfy Epic's endless red tape. Doctors now routinely stay late after work and show up hours early, just to do paperwork. It's not enough. According to another one of Kuttner's sources, doctors routinely copy-and-paste earlier entries into the current one, a practice that generates rampant errors. Some just make up random numbers to fulfill Epic's nonsensical requirements: the same source told Kuttner that when prompted to enter a pain score for his TB patients, he just enters "zero."
Don't worry, Epic has a solution: AI. They've rolled out an "ambient listening" tool that attempts to transcribe everything the doctor and patient say during an exam and then bash it into a visit report. Not only is this prone to the customary mistakes that make AI unsuited to high-stakes, error-sensitive applications, it also represents a profound misunderstanding of the purpose of clinical notes.
The very exercise of organizing your thoughts and reflections about an event – such as a medical exam – into a coherent report makes you apply rigor and perspective to events that otherwise arrive as a series of fleeting impressions and reactions. That's why blogging is such an effective practice:
https://pluralistic.net/2021/05/09/the-memex-method/
The answer to doctors not having time to reflect and organize good notes is to give them more time – not more AI. As another doctor told Kuttner: "Ambient listening is a solution to a self-created problem of requiring too much data entry by clinicians."
EHRs are one of those especially hellish public-private partnerships. Health care doctrine from Reagan to Obama insisted that the system just needed to be exposed to market forces and incentives. EHRs are designed to allow hospitals to win as many of these incentives as possible. Epic's clinical care modules do this by bombarding doctors with low-quality diagnostic suggestions with "little to do with a patient’s actual condition and risks," leading to "alert fatigue," so doctors miss the important alerts in the storm of nonsense elbow-jostling:
https://www.ncbi.nlm.nih.gov/pmc/articles/PMC5058605/
Clinicians who actually want to improve the quality of care in their facilities end up recording data manually and keying it into spreadsheets, because they can't get Epic to give them the data they need. Meanwhile, an army of high-priced consultants stand ready to give clinicians advise on getting Epic to do what they need, but can't seem to deliver.
Ironically, one of the benefits that Epic touts is its interoperability: hospitals that buy Epic systems can interconnect those with other Epic systems, and there's a large ecosystem of aftermarket add-ons that work with Epic. But Epic is a product, not a protocol, so its much-touted interop exists entirely on its terms, and at its sufferance. If Epic chooses, a doctor using its products can send files to a doctor using a rival product. But Epic can also veto that activity – and its veto extends to deciding whether a hospital can export their patient records to a competing service and get off Epic altogether.
One major selling point for Epic is its capacity to export "anonymized" data for medical research. Very large patient data-sets like Epic's are reasonably believed to contain many potential medical insights, so medical researchers are very excited at the prospect of interrogating that data.
But Epic's approach – anonymizing files containing the most sensitive information imaginable, about millions of people, and then releasing them to third parties – is a nightmare. "De-identified" data-sets are notoriously vulnerable to "re-identification" and the threat of re-identification only increases every time there's another release or breach, which can used to reveal the identities of people in anonymized records. For example, if you have a database of all the prescribing at a given hospital – a numeric identifier representing the patient, and the time and date when they saw a doctor and got a scrip. At any time in the future, a big location-data breach – say, from Uber or a transit system – can show you which people went back and forth to the hospital at the times that line up with those doctor's appointments, unmasking the person who got abortion meds, cancer meds, psychiatric meds or other sensitive prescriptions.
The fact that anonymized data can – will! – be re-identified doesn't mean we have to give up on the prospect of gleaning insight from medical records. In the UK, the eminent doctor Ben Goldacre and colleagues built an incredible effective, privacy-preserving "trusted research environment" (TRE) to operate on millions of NHS records across a decentralized system of hospitals and trusts without ever moving the data off their own servers:
https://pluralistic.net/2024/03/08/the-fire-of-orodruin/#are-we-the-baddies
The TRE is an open source, transparent server that accepts complex research questions in the form of database queries. These queries are posted to a public server for peer-review and revision, and when they're ready, the TRE sends them to each of the databases where the records are held. Those databases transmit responses to the TRE, which then publishes them. This has been unimaginably successful: the prototype of the TRE launched during the lockdown generated sixty papers in Nature in a matter of months.
Monopolies are inefficient, and Epic's outmoded and dangerous approach to research, along with the roadblocks it puts in the way of clinical excellence, epitomizes the problems with monopoly. America's health care industry is a dumpster fire from top to bottom – from Medicare Advantage to hospital cartels – and allowing Epic to dominate the EHR market has somehow, incredibly, made that system even worse.
Naturally, Kuttner finishes out his article with some antitrust analysis, sketching out how the Sherman Act could be brought to bear on Epic. Something has to be done. Epic's software is one of the many reasons that MDs are leaving the medical profession in droves.
Epic epitomizes the long-standing class war between doctors who want to take care of their patients and hospital executives who want to make a buck off of those patients.

Tor Books as just published two new, free LITTLE BROTHER stories: VIGILANT, about creepy surveillance in distance education; and SPILL, about oil pipelines and indigenous landback.


If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/10/02/upcoded-to-death/#thanks-obama

Image: Flying Logos (modified) https://commons.wikimedia.org/wiki/File:Over_$1,000,000_dollars_in_USD_$100_bill_stacks.png
CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#ehrs#robert kuttner#tres#trusted research environments#ben goldacre#epic#epic systems#interoperability#privacy#reidentification#deidentification#thanks obama#upcoding#Hierarchical Condition Category#medicare#medicaid#ai#American Recovery and Reinvestment Act#HITECH act#medicare advantage#ambient listening#alert fatigue#monopoly#antitrust
820 notes
·
View notes
Text
Assume all conversations to be private and confidential unless stated otherwise.
Of course this mainly applies to things of a sensitive and personal nature. If your classmate tells you their favorite soda flavor or favorite pizza topping, or your co-worker shares a trick with you on how to use the new software at work, that's safe to assume it's okay to share.
But anything of a more sensitive nature, someone sharing with you a problem they've been having at home with their family or partner, a personal insecurity of theirs, a difficult or traumatic event from their past, a health issue they've been having, your default assumption should always be that this was shared to you in confidence and is a private matter that you should not share with others unless a) they've given you permission to or b) it's an emergency or otherwise urgent situation (for example your co-worker just collapsed at work so it's probably a good idea to tell the paramedic that personal health problem your co-worker shared with you in confidence)
This kind of information is something that most people don't just share with anyone, and usually will only share with someone who has earned some degree of their trust. This kind of information can be used against people, or can also be embarrassing or just a sensitive topic. Sharing it with other people without their permission, however, can quickly dissolve whatever trust you had gained from them.
217 notes
·
View notes
Text
The Metaverse: A New Frontier in Digital Interaction

The concept of the metaverse has captivated the imagination of technologists, futurists, and businesses alike. Envisioned as a collective virtual shared space, the metaverse merges physical and digital realities, offering immersive experiences and unprecedented opportunities for interaction, commerce, and creativity. This article delves into the metaverse, its potential impact on various sectors, the technologies driving its development, and notable projects shaping this emerging landscape.
What is the Metaverse?
The metaverse is a digital universe that encompasses virtual and augmented reality, providing a persistent, shared, and interactive online environment. In the metaverse, users can create avatars, interact with others, attend virtual events, own virtual property, and engage in economic activities. Unlike traditional online experiences, the metaverse aims to replicate and enhance the real world, offering seamless integration of the physical and digital realms.
Key Components of the Metaverse
Virtual Worlds: Virtual worlds are digital environments where users can explore, interact, and create. Platforms like Decentraland, Sandbox, and VRChat offer expansive virtual spaces where users can build, socialize, and participate in various activities.
Augmented Reality (AR): AR overlays digital information onto the real world, enhancing user experiences through devices like smartphones and AR glasses. Examples include Pokémon GO and AR navigation apps that blend digital content with physical surroundings.
Virtual Reality (VR): VR provides immersive experiences through headsets that transport users to fully digital environments. Companies like Oculus, HTC Vive, and Sony PlayStation VR are leading the way in developing advanced VR hardware and software.
Blockchain Technology: Blockchain plays a crucial role in the metaverse by enabling decentralized ownership, digital scarcity, and secure transactions. NFTs (Non-Fungible Tokens) and cryptocurrencies are integral to the metaverse economy, allowing users to buy, sell, and trade virtual assets.
Digital Economy: The metaverse features a robust digital economy where users can earn, spend, and invest in virtual goods and services. Virtual real estate, digital art, and in-game items are examples of assets that hold real-world value within the metaverse.
Potential Impact of the Metaverse
Social Interaction: The metaverse offers new ways for people to connect and interact, transcending geographical boundaries. Virtual events, social spaces, and collaborative environments provide opportunities for meaningful engagement and community building.
Entertainment and Gaming: The entertainment and gaming industries are poised to benefit significantly from the metaverse. Immersive games, virtual concerts, and interactive storytelling experiences offer new dimensions of engagement and creativity.
Education and Training: The metaverse has the potential to revolutionize education and training by providing immersive, interactive learning environments. Virtual classrooms, simulations, and collaborative projects can enhance educational outcomes and accessibility.
Commerce and Retail: Virtual shopping experiences and digital marketplaces enable businesses to reach global audiences in innovative ways. Brands can create virtual storefronts, offer unique digital products, and engage customers through immersive experiences.
Work and Collaboration: The metaverse can transform the future of work by providing virtual offices, meeting spaces, and collaborative tools. Remote work and global collaboration become more seamless and engaging in a fully digital environment.
Technologies Driving the Metaverse
5G Connectivity: High-speed, low-latency 5G networks are essential for delivering seamless and responsive metaverse experiences. Enhanced connectivity enables real-time interactions and high-quality streaming of immersive content.
Advanced Graphics and Computing: Powerful graphics processing units (GPUs) and cloud computing resources are crucial for rendering detailed virtual environments and supporting large-scale metaverse platforms.
Artificial Intelligence (AI): AI enhances the metaverse by enabling realistic avatars, intelligent virtual assistants, and dynamic content generation. AI-driven algorithms can personalize experiences and optimize virtual interactions.
Wearable Technology: Wearable devices, such as VR headsets, AR glasses, and haptic feedback suits, provide users with immersive and interactive experiences. Advancements in wearable technology are critical for enhancing the metaverse experience.
Notable Metaverse Projects
Decentraland: Decentraland is a decentralized virtual world where users can buy, sell, and develop virtual real estate as NFTs. The platform offers a wide range of experiences, from gaming and socializing to virtual commerce and education.
Sandbox: Sandbox is a virtual world that allows users to create, own, and monetize their gaming experiences using blockchain technology. The platform's user-generated content and virtual real estate model have attracted a vibrant community of creators and players.
Facebook's Meta: Facebook's rebranding to Meta underscores its commitment to building the metaverse. Meta aims to create interconnected virtual spaces for social interaction, work, and entertainment, leveraging its existing social media infrastructure.
Roblox: Roblox is an online platform that enables users to create and play games developed by other users. With its extensive user-generated content and virtual economy, Roblox exemplifies the potential of the metaverse in gaming and social interaction.
Sexy Meme Coin (SEXXXY): Sexy Meme Coin integrates metaverse elements by offering a decentralized marketplace for buying, selling, and trading memes as NFTs. This unique approach combines humor, creativity, and digital ownership, adding a distinct flavor to the metaverse landscape. Learn more about Sexy Meme Coin at Sexy Meme Coin.
The Future of the Metaverse
The metaverse is still in its early stages, but its potential to reshape digital interaction is immense. As technology advances and more industries explore its possibilities, the metaverse is likely to become an integral part of our daily lives. Collaboration between technology providers, content creators, and businesses will drive the development of the metaverse, creating new opportunities for innovation and growth.
Conclusion
The metaverse represents a new frontier in digital interaction, offering immersive and interconnected experiences that bridge the physical and digital worlds. With its potential to transform social interaction, entertainment, education, commerce, and work, the metaverse is poised to revolutionize various aspects of our lives. Notable projects like Decentraland, Sandbox, Meta, Roblox, and Sexy Meme Coin are at the forefront of this transformation, showcasing the diverse possibilities within this emerging digital universe.
For those interested in the playful and innovative side of the metaverse, Sexy Meme Coin offers a unique and entertaining platform. Visit Sexy Meme Coin to explore this exciting project and join the community.
264 notes
·
View notes
Text
Why Is Emergency Information Software a Game-Changer for Facility Emergency Preparedness?
In today's fast-paced world, where emergencies can strike at any moment, being prepared is paramount. Whether it's a fire, natural disaster, or medical emergency, having instant access to critical information can mean the difference between safety and chaos. This is where emergency equipment management steps in as a game-changer for facility emergency preparedness. Let's delve deeper into how this innovative technology revolutionizes the way facilities manage emergencies.
Enhancing Speed and Accessibility
In the midst of a crisis, every second counts. Traditional methods of accessing emergency information, such as flipping through paper documents or searching through digital files, can waste precious time. Emergency information software streamlines this process by providing instant access to crucial data with just a few clicks on a mobile device. This unparalleled speed and accessibility empower facility managers and first responders to make informed decisions swiftly, ultimately saving lives and minimizing damage.
Seamless Integration with Facility Management Software
Emergency information software seamlessly integrates with existing facility management software, enhancing its capabilities and ensuring comprehensive emergency preparedness. By consolidating emergency plans, evacuation routes, shut-offs, and other critical information within a single platform, facility managers gain a holistic view of their emergency preparedness efforts. This synergy between emergency information software and facility management software maximizes efficiency and minimizes the risk of overlooking essential details during emergencies.
Optimizing Emergency Equipment Management
Effective management of emergency equipment is essential for swift and efficient emergency response. Emergency information software facilitates this process by providing dedicated features for emergency equipment management. Facility managers can easily catalog and track the location, condition, and maintenance history of emergency equipment, ensuring readiness when emergencies strike. With real-time updates and alerts, maintenance tasks can be scheduled proactively, minimizing the risk of equipment failure during critical moments.
Customized Emergency Plans for Every Scenario
No two emergencies are alike, and facility managers must be prepared for a wide range of scenarios. Emergency information software enables the creation of customized emergency plans tailored to specific threats and facility layouts. From fire evacuation procedures to medical emergency protocols, these plans provide clear guidance to occupants and first responders, fostering a safer environment for all. Regular updates and simulations ensure that emergency plans remain relevant and effective over time.
Empowering On-the-Go Emergency Response
Emergencies can occur anytime, anywhere, requiring facility managers to be agile and responsive even when they're on the move. Emergency information software empowers on-the-go emergency response by providing mobile access to critical information. Whether it's accessing evacuation routes, contacting emergency personnel, or locating emergency equipment, facility managers can take decisive action from their mobile devices, regardless of their physical location. This flexibility enhances overall emergency preparedness and response capabilities.
Facilitating Collaboration and Communication
Effective communication is paramount during emergencies, ensuring that all stakeholders are informed and coordinated in their response efforts. Emergency information software facilitates collaboration and communication by centralizing emergency information and enabling real-time communication among stakeholders. Whether it's notifying occupants of an evacuation order or coordinating with external emergency responders, facility managers can leverage the platform to streamline communication channels and ensure a synchronized response.
Compliance Assurance and Documentation
Compliance with regulatory requirements and industry standards is non-negotiable when it comes to emergency preparedness. Emergency information software simplifies compliance assurance by providing a centralized repository for documentation and audit trails. Facility managers can easily access and update emergency plans, evacuation routes, and equipment maintenance records to ensure adherence to relevant regulations. Automated reminders and notifications help mitigate compliance risks and ensure that facilities remain prepared for inspections and audits.
Conclusion
In an age where emergencies are an unfortunate reality, facility managers must leverage every available resource to enhance their emergency preparedness efforts. Emergency information software emerges as a game-changer in this regard, revolutionizing the way facilities manage emergencies. By enhancing speed and accessibility, seamlessly integrating with facility management software, optimizing emergency equipment management, and facilitating customized emergency plans, this innovative technology empowers facility managers to respond swiftly and effectively to any crisis. With its mobile capabilities, collaboration features, and compliance assurance functionalities, emergency information software equips facilities with the tools they need to mitigate risks, ensure occupant safety, and safeguard business continuity.
0 notes
Text
Pick a Card: Career Guidance




Top Left to Right--> Pile 1, Pile 2
Bottom Left to Right--> Pile 3. Pile 4
If You Liked This Reading Sign up to TheObsidianPages777 Newsletter
+Free E-Guides on New Moon Manifestation and Gem Stone for Life Path
================================================================================================
Pile 1
Current Situation: The Chariot
You are determined and focused on your career goals, moving forward with purpose and direction. There's a sense of control and determination driving your actions.
Challenges: Five of Wands
You may be facing competition or conflict in your workplace. There could be differing opinions and struggles that make it hard to progress smoothly.
Advice: Strength
Rely on your inner strength and patience to navigate through challenges. Maintain self-control and approach conflicts with compassion and understanding. Your resilience will lead you to success.
Ideal Careers:
Leadership Roles: Positions such as a manager, director, or CEO, where determination and leadership are crucial.
Entrepreneur: Running your own business where you can harness your drive and overcome competition.
Project Management: Roles that require strong organizational skills and the ability to navigate conflicts and challenges.
Military or Law Enforcement: Careers that require discipline, determination, and the ability to handle conflict and stress.
Athletics or Coaching: Where physical and mental strength, as well as resilience, are important.
================================================================================================
Pile 2
Current Situation: The Hierophant
Your career path is currently influenced by traditional structures and conventional methods. You may be working within an established system or organization.
Challenges: Seven of Cups
There may be confusion or too many options available, making it difficult to choose the right path. Avoid getting lost in illusions or wishful thinking.
Advice: The Hermit
Take time for introspection and seek inner guidance. Reflect on your true goals and values before making decisions. Solitude and self-reflection will provide clarity.
Ideal Careers:
Education: Teacher, professor, or academic advisor, where traditional knowledge and guidance are valued.
Religious or Spiritual Leader: Priest, minister, or spiritual counselor, providing guidance within established belief systems.
Legal Profession: Lawyer, judge, or paralegal, working within the structures of the legal system.
Research and Academia: Careers that involve deep study and reflection, such as a researcher or academic.
Counseling or Therapy: Roles that require introspection and helping others find clarity, such as a therapist or counselor.
================================================================================================
Pile 3
Current Situation: Ace of Pentacles
A new opportunity or beginning in your career is emerging. This could be a job offer, a new project, or a chance to start something new with strong potential for growth.
Challenges: The Devil
Be wary of falling into negative patterns or becoming too attached to material success. Avoid temptations that could lead to unethical behavior or burnout.
Advice: Page of Swords
Approach new opportunities with curiosity and a willingness to learn. Stay vigilant and gather information before making decisions. Be clear and honest in your communication.
Ideal Careers:
Finance: Banker, financial advisor, or investment analyst, where new opportunities for growth are abundant.
Real Estate: Real estate agent or property manager, involving new ventures and potential for substantial growth.
Technology: IT specialist, software developer, or tech entrepreneur, where continuous learning and vigilance are key.
Journalism: Reporter, editor, or content creator, focusing on gathering and disseminating information.
Consulting: Business consultant or analyst, providing strategic advice and insights to businesses.
================================================================================================
Pile 4
Current Situation: Three of Cups
Collaboration and teamwork are currently significant in your career. You may be part of a supportive group or network, enjoying camaraderie and shared goals.
Challenges: Four of Pentacles
There could be a tendency to hold on too tightly to security or resources, leading to stagnation. Fear of change or loss may be preventing growth.
Advice: The Star
Stay hopeful and keep a positive outlook. Trust in the universe and your vision for the future. This is a time for healing, inspiration, and aligning with your true purpose.
Ideal Careers:
Event Planning: Event coordinator or wedding planner, where collaboration and teamwork are essential.
Human Resources: HR manager or recruiter, fostering a positive and collaborative workplace environment.
Creative Arts: Artist, musician, or performer, involving collaboration and shared creative goals.
Non-Profit or Community Work: Community organizer, social worker, or NGO worker, focusing on collective well-being and humanitarian goals.
Healthcare: Nurse, doctor, or therapist, providing care and support with a focus on healing and hope.
If You Liked This Reading Sign up to TheObsidianPages777 Newsletter
+Free E-Guides on New Moon Manifestation and Gem Stone for Life Path
#pick a card#pick a pile#pick a photo#pick one#tarot community#tarot reading#tarot#tarot cards#tarotblr#pick a picture#pick a reading
307 notes
·
View notes
Text

We at MicroBurstMedia, a digital solutions company is excited to announce the launch of our new book—The Beginners Guide to AI Automation Setup System!
Highly recommended if you're a beginner looking to get started in the online workspace, learn how to turn your set of skills and experience into your own automated sales system for business and or work purposes, our book is available and on sale as we continue to gain interests among tech users, business startups and entrepreneurs across web platforms.
This book breaks down the construct of this topic on a micro level scale, along with setup instructions showing how we got started and how you can too providing AI computer software system recommendations making it accessible for everyone—even if you’re not tech-savvy—by any means we ensure you get as much out of it guaranteed along with online support to assist in answering any questions you may have!
🔊But it doesn't stop there, you can also get it in an eBook version which is available at an introductory price of $29.99, now on sale (90% OFF) at $3.00 for a LIMITED-TIME!
In addition, we are providing digital copies of our presentation guide ♦️FOR FREE♦️ which you can access at anytime. Want in on this info? Send us a DM!
This Information📚 Was brought to You by MicroBurstMedia, a digital solutions company. 🏢
#software#cyber security#information technology#techinnovation#analytics#developer#information literacy#technology#ai technologies#emerging technologies#new technologies#advanced technologies#innovation#technologynews#technews#application#computer#laptop
0 notes
Text
In early September, the U.S. Department of Justice unveiled a series of sweeping investigations and indictments into Russian information projects aimed at disrupting the 2024 U.S. presidential election. One of these projects, which secretly funded right-wing influencers to promote former President Donald Trump’s campaign, is an escalation from prior Russian information operations, such as their email hacks during the 2016 election.
But another Russian team, described in a planning document published by the Department of Justice, approached disrupting the election a little bit less directly.
The Russian plan describes the “Good Ol’ USA Project” as a “guerrilla media” campaign intended to target “sentiments that should be exploited in the course of an information campaign in/for the United States.” Written by Ilya Gambashidze, a figure already facing sanctions for his disinformation work aimed at smearing Ukraine, the document suggests focusing influence efforts on the “community of American gamers, users of Reddit and image boards, such as 4Chan,” since they are the “backbone of the right-wing trends” online in the United States.
The inclusion of gamers in this campaign points at emerging dynamics in a global struggle over human rights online—one that policymakers need to pay closer attention to.
According to the Entertainment Software Association, a trade group, around 65 percent of Americans—or 212 million people—regularly play video games. Globally, video games generate more than $280 billion in revenue, far larger than traditional culture industries such as film or book publishing. While a trickle of stories about other attempts to push Russian propaganda in video games have attracted some scrutiny from journalists, the question remains: Apart from scale, what is it about gamers that Russia thinks will make them receptive to its messaging?
For starters, video game culture has already become an important venue for extremist right-wing groups to share and normalize their ideas. Far-right groups modify video games to be more explicitly racist and violent than their designers intended. Even gaming spaces designed for children, such as Roblox, which allows players to create their own game worlds and storylines, have attracted thousands of people (many of them young teenagers) to use the game’s freewheeling mechanics to play-act fascist violence.
The prevalence of hate groups has shaped video games into a place where culture and politics are debated, often contentiously, with predictable fault lines emerging along U.S. partisan boundaries. While the industry itself has made considerable progress in improving representation and reducing acts of horrific sexual violence, it has received pushback from far-right figures who are angry at the so-called “wokes” for supposedly “ruining games.”
For a decade, repeated efforts to “reclaim” gaming from an imagined enemy composed of women, Black people, and LGBT+ folks have bubbled up from the darkest corners of the internet, often in places such as Reddit (where this Russian campaign aimed its influence activity). These movements have spilled over into more mainstream political movements that can shape election outcomes. Consider how Gamergate, a 2014 campaign to terrorize women working in the industry into invisibility, metastasized into an online troll army working to get former U.S. President Donald Trump elected in 2016.
These far-right efforts are ongoing, even without Russian help. Last year, a group of gamers who were angry at inclusive representation in games launched a harassment campaign—colloquially called Gamergate 2.0—against a story consulting company.
Earlier this year, when Ubisoft began promoting the latest installment of its popular Assassin’s Creed franchise, this time set in feudal Japan, the trailer prominently featured Yasuke, an African man who served as a samurai in 16th-century Japan. Despite being based on a real historical figure, this movement (egged on by X owner and billionaire Elon Musk) raged at the decision, as if acknowledging Black people in the past was somehow bad. In their quest to sow division within the United States, Russian information operations analysts do not need to look very far to find political allies in gaming communities.
It helps that Russia enjoys greater social legitimacy in gaming than it does in, say, news journalism. You can see this legitimacy reflected in the language gamers that use as they play. Around the same time as Gamergate, a vulgar Russian phrase began popping up in the chats that players use to communicate with each other in non-Russian game streams, primarily in the multiplayer first-person shooter Counterstrike: Global Offensive. The game has around 4 million Russian players, and as it grew in popularity in the mid-2010s, the Russian obscenity cyka blyad became common invective during frustrating moments of play. Its widespread adoption among non-Russian-speaking gamers struck many as odd.
Cyka blyad rose in prominence alongside Russia’s descent into becoming an international pariah, which has limited the spaces where Russian gamers can play games online. In 2014, Russia passed a law requiring websites that store the personal information of Russian citizens to do so on servers inside the country. This was compounded in 2022, when companies ranging from Activision Blizzard to Nintendo protested the invasion of Ukraine by either suspending sales or shutting down Russia-specific services. Despite its residents representing around 10 percent of Counterstrike’s player base, there are no host servers for the game anywhere in Russia.
So, when Russian players log on to find players for a match, they use servers based in Europe or sometimes North America. These servers place them into direct contact with players on the other side of international conflicts—something that many players within the European Union found deeply frustrating after Russia’s illegal annexation of Crimea in 2014, as their games became places where people would argue about the annexation.
But another reason why Russian slang began infiltrating non-Russian gaming spaces is that after years of censorship and exclusion from both Russian and Western governments, games are one of the only spaces direct exchanges between ordinary Russian and Western people. Russians lack access to many Western social media platforms—such as Instagram (blocked by the Russian government in 2022, though earlier this year some Russian users regained access)—and were locked out of Western game stores, even as they kept access to many online games. As a result, matches in a game such as Counterstrike or Fortnite became one of the only places where these informal cultural exchanges could take place.
This narrowing of exchange spaces highlights how video games can become useful conduits for propaganda, and it demonstrates that video games are becoming an important, if underappreciated, site for ideological disputes over politics, speech, identity, and expression.
Other countries have begun to use video games for strategic communication. The U.S. government operates semiprofessional esports teams through the Defense Department, whose remit includes convincing young people to become interested in enlistment. China launched a military-produced first-person shooter game to boost recruitment and to humanize the image of the People’s Liberation Army abroad.
The Chinese developers of the hugely popular game Black Myth: Wukong instructed gaming influencers who were given early access to avoid discussing “feminist propaganda” while reviewing the game, apparently to adhere to government censorship rules. And Russian propaganda about the country’s war with Ukraine has begun appearing in games that allow user-generated content, such as Minecraft and the aforementioned Roblox, as the Kremlin seeks to persuade Westerners to end their support for Ukrainian freedom. In response, the U.S. State Department has begun developing its own games intended to train players to resist Russian disinformation.
This isn’t an abstract challenge. Scholars have drawn linkages between Russia’s propaganda efforts and President Vladimir Putin’s decision to launch the full-scale invasion of Ukraine in 2022 as both bots and human agents aggressively pushed narratives about the need to “pacify” an ostensibly violent Ukraine by invading. The invasion was further justified by the myth of Novorossiya, or a pan-Russian identity that views Ukrainians as misguided Russians who need to be forcibly reclaimed.
These efforts to spread propaganda through gaming are rarely successful. Few people wanted to, say, join Hezbollah after the Lebanese militant group launched its own game, Special Force, in 2003. The terrorist group al Qaeda has used video games for recruitment since 2006, but there is little evidence that any meaningful number of people have been recruited because of it. Scholars have fretted for years over the “militarization” of video games as the Pentagon gets more and more involved in the industry, yet U.S. military recruitment is in long-term decline, and public confidence in the nation’s military is at a two-decade low. If games-based propaganda works, we do not yet know where or how it does.
The revelations about Russian video game propaganda hint at some intriguing innovation in how strategic messages might be spread through nontraditional channels, but they also point to the areas where traditional channels for propaganda have closed down. Despite efforts by Republicans in Congress to falsely accuse agencies such as the Global Engagement Center of partisan bias when addressing foreign misinformation, the U.S. government takes the challenge seriously and, as this 2022 report on the propaganda channels , is working to thwart many of Russia’s best efforts to target Americans with propaganda, like when they sanctioned several Russian oligarchs who had been financing US-directed misinformation.
But even beyond government counterprogramming, there are plenty of obstacles to Russia’s efforts within the world of gaming. For example, Ukraine’s video games industry is respected in the United States and Europe. The developer 4A, which was based in Kyiv before the invasion, produces popular games such as the Metro franchise. That company, however, had to fly its employees abroad to keep them safe from the indiscriminate Russian barrages against the Ukrainian capital and other cities. This sent shockwaves through the industry, as it made some of the consequences of the invasion seem more viscerally real even to people who do not follow politics closely.
As a result of American and European sanctions, Russians have a more difficult experience legally purchasing software and services such as online gaming. (Some Russian game companies have since relocated abroad to more neutral countries, such as Cyprus, to continue operating globally). Wargaming, the Belarusian company that makes World of Tanks, also fled to Cyprus, which has become an informal hub of Russian game companies.
Looking forward, there are real questions about what video games are going to become in the information war between Russia and the West. Russian censors have proposed deploying neural networks to search for banned content in games, but it is unclear whether those systems might disrupt gaming for everyone else.
Long before the invasion of Ukraine, Moscow forced Activision to censor the infamous airport sequence in the rerelease of Call of Duty: Modern Warfare 2 (in which players assume the role of a Chechen terrorist and can slaughter hundreds of screaming civilians at Sheremetyevo International Airport), and it has not been shy about using government coercion to erase LGBT+ people from gaming (paralleling to its embrace of the U.S. far right). Policymakers should look at ensuring that global communication platforms—and that is what video games are—remain open to free speech and safeguard other basic human rights.
While the latest Russian effort to target games seems to have been thwarted by the U.S. Justice Department, there will undoubtedly be more programs looking to repeat and extend the success of Gamergate in empowering the far right, perhaps this time by enabling it to obstruct effective governance in the United States. The Good Ol’ USA Project also targeted its influence operations toward websites such as Reddit and 4Chan, both of which are as central to the sustainment of far-right movements as gaming. Emerging platforms—which range from popular Chinese games to channels such as the online chat service Discord, which is difficult to monitor at scale and routinely hosts leaks of sensitive military documents—present new opportunities where Russian influence could be targeted.
These strange spaces are the frontier where a global battle for speech is being fought.
99 notes
·
View notes
Text
U.S. Recount Updates/News:
Pennsylvania's U.S. Senate race will officially go to a recount. GOP candidate David McCormick is leading incumbent Democratic Sen. Bob Casey by less than 0.5% in the vote total, triggering an automatic recount under state law.
Furthermore,
Election and cybersecurity experts sent a formal letter to Vice President Kamala Harris urging a recount in key states, citing potential breaches in voting machines and the fact that voting systems were breached by Trump allies in 2021 and 2022.
https://freespeechforpeople.org/computer-scientists-breaches-of-voting-system-software-warrant-recounts-to-ensure-election-verification/

Cited evidence within the footnotes include:
https://www.washingtonpost.com/investigations/2022/08/15/sidney-powell-coffee-county-sullivan-strickler/
Additionally,
The Nevada Secretary of State issued a violation notice regarding election security. A police report has been filed after evidence emerged indicating that Nevada officials may have removed 26,902 ballots from their reported mail-in ballot totals.

[ID:
Three images.
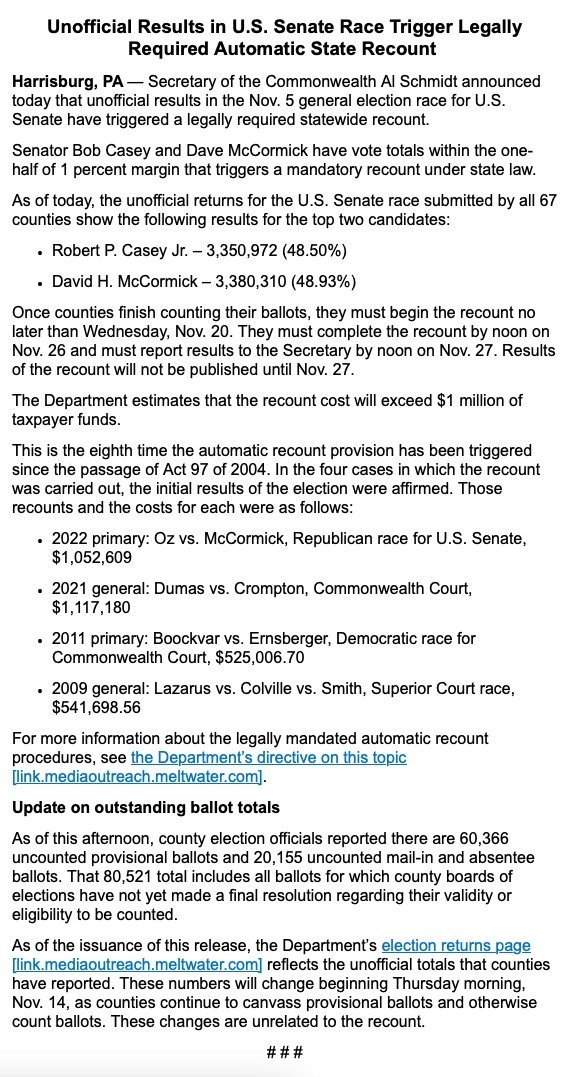
The first is a statement regarding a recount being triggered in the Pennsylvania Senate race. It reads:
“Unofficial Results in U.S. Senate Race Trigger Legally Required Automatic State Recount
Harrisburg, PA — Secretary of the Commonwealth Al Schmidt announced today that unofficial results in the Nov. 5 general election race for U.S.
Senate have triggered a legally required statewide recount.
Senator Bob Casey and Dave McCormick have vote totals within the one-half of 1 percent margin that triggers a mandatory recount under state law.
As of today, the unofficial returns for the U.S. Senate race submitted by all 67 counties show the following results for the top two candidates:
Robert P. Casey Jr. - 3,350,972 (48.50%)
David H. McCormick - 3,380,310 (48.93%)
Once counties finish counting their ballots, they must begin the recount no later than Wednesday, Nov. 20. They must complete the recount by noon on Nov. 26 and must report results to the Secretary by noon on Nov. 27. Results of the recount will not be published until Nov. 27.
The Department estimates that the recount cost will exceed $1 million of taxpayer funds.
This is the eighth time the automatic recount provision has been triggered since the passage of Act 97 of 2004. In the four cases in which the recount was carried out, the initial results of the election were affirmed. Those recounts and the costs for each were as follows:
2022 primary: Oz vs. McCormick, Republican race for U.S. Senate, $1,052,609.
2021 general: Dumas vs. Crompton, Commonwealth Court, $1,117,180.
2011 primary: Boockvar vs. Ernsberger, Democratic race for Commonwealth Court, $525,006.70.
2009 general: Lazarus vs. Colville vs. Smith, Superior Court race, $541,698.56.
For more information about the legally mandated automatic recount procedures, see the Department's directive on this topic (link.mediaoutreach.meltwater.com).
Update on outstanding ballot totals
As of this afternoon, county election officials reported there are 60,366 uncounted provisional ballots and 20,155 uncounted mail-in and absentee ballots. That 80,521 total includes all ballots for which county boards of elections have not yet made a final resolution regarding their validity or eligibility to be counted.
As of the issuance of this release, the Department's election returns page [link.mediaoutreach.meltwater.com] reflects the unofficial totals that counties have reported. These numbers will change beginning Thursday morning, Nov. 14, as counties continue to canvass provisional ballots and otherwise count ballots. These changes are unrelated to the recount.”
The second image depicts the first page of a formal letter addressed to Vice President Kamala Harris from election security experts urging an election recount in key states. It reads:
“November 13, 2024
The Honorable Kamala Harris
The White House
Office of the Vice President
1600 Pennsylvania Avenue, N. W.
Washington, DC 20500
Dear Vice President Harris,
We write to alert you to serious election security breaches that have threatened the security and integrity of the 2024 elections, and to identify ways to ensure that the will of the voters is reflected and that voters should have confidence in the result. The most effective manner of doing so is through targeted recounts requested by the candidate. In the light of the breaches we ask that you formally request hand recounts in at least the states of Michigan, Nevada, Wisconsin, and Pennsylvania. We have no evidence that the outcomes of the elections in those states were actually compromised as a result of the security breaches, and we are not suggesting that they were. But binding risk-limiting audits (RLAs) or hand recounts should be routine for all elections, especially when the stakes are high and the results are close. We believe that, under the current circumstances when massive software breaches are known and documented, recounts are necessary and appropriate to remove all potential doubt and to set an example for security best practices in all elections.
In 2022, records, video camera footage, and deposition testimony produced in a civil case in Georgia' disclosed that its voting system, used statewide, had been breached over multiple days by operatives hired by attorneys for Donald Trump. The evidence showed that the operatives made copies of the software”
(The page cuts off here).
Below there are footnotes with cited evidence for grounds to request a recount.
“No. 17-cv-02989-AT (N.D. Ga. filed Aug. 8, 2017).
1. Emma Brown, Jon Swaine, Aaron C. Davis, Amy Gardner, "Trump-allied lawyers pursued voting machine data in multiple states, records reveal," The Washington Post, (August 15, 2022). Available at: https://www.washingtonpost.com/investigations/2022/08/15/sidney-powell-coffee-county-sullivan-strickler/
3 Kate Brumback, "Video fills in details on alleged Ga. election system breach," The Associated Press, (September 6, 2022). Available at: https://apnews.com/article/2022-midterm-elections-technology-donald-trump-voting-92c0ace71d7bee6151dd33938688371e
The third image is an excerpt of the Election Security Violation Notice issued by the Nevada Secretary of State. It reads:
“ELECTION INTEGRITY VIOLATION REPORT
The information you report on this form may be used to help us investigate violations of Nevada election laws. When completed, mail, email, or fax your form and supporting documents to the office listed above. Upon receipt, your complaint will be reviewed by a member of our staff. The length of this process can vary depending on the circumstances and information you provide with your complaint. The Office of the Secretary of State may contact you if additional information is needed.
INSTRUCTIONS: Please TYPE/PRINT your complaint in dark ink. You must write LEGIBLY. All fields MUST be completed.
SECTION 3.
COMPLAINT IS AGAINST
Please detail the nature of your complaint. Include the name and contact information (if known) of the individual, candidate, campaign, or group that is the subject of your complaint. Your complaint must also include a clear and concise statement of facts sufficient to establish that the alleged violation occurred. Any relevant documents or other evidence that support your complaint should be listed and attached. You may attach additional sheets if necessary.
On 11-8-24, the mail ballot accepted list deleted 28,320 ballots from Clark County. At this same time, Sam Brown lost his lead. These ballots were accepted on 11-7-24 and then on 11-8-24 for the first time since 10-16-24 and reporting began, ballots were deleted from 2 counties. Washoe and Clark.
See ATTACHED.”
/end ID]
#image description in alt#image description included#image described#us news#us elections#election news#election security#election integrity#election interference#presidential election#us presidential election#2024 presidential election#kamala harris#recount#recount 2024#election recount#us senate#senate race#us voting#updates#described#image desc in alt text#long post
89 notes
·
View notes
Text
Fatal Attraction
Chapter Two


Pairings: Wanda Maximoff x GN! Reader/Wanda Maximoff x Jarvis Stark
Warnings: Angst. Fluff.
Taglist : @natashamaximoff-69 @canvascoloredin @wizardofstories @louxbloom @wandanats-goodgirl @the-ox-fan20 @ladyqueenxoxo @aemilia19 @wandaromamoff69 @mfd-101 @dorabledewdroop @marvelogic
18+ MINORS DNI
Wanda was excited to start her first day at Oscorp, of course she never told Jarvis where she was working. Oscorp and Stark Industries are the biggest rivals in the USA, both companies sell high tech software and Oscorp also sell pharmaceuticals and weapons, something which Tony had stopped Stark Industries manufacturing. So Stark had lost a lot of investors due to lack of materials.
"Why are you up so early?" Jarvis asked his wife as she sat at the table, a cup of coffee in one hand and a slice of toast in the other.
"I have my first day today." She told him as she put the cup down, gathering her things.
"What time will you be home?" He questioned as she raised her brow. "I just want to know if I should expect dinner or not when I walk through the door."
"Seriously?" She scoffed as he gazed at her. "I am not a little housewife. It is not my job to mother you!" She left the toast and coffee on the table as she grabbed her purse, heading straight to the door. "Don't expect me to cook dinner for you tonight." She told him before she slammed the door behind her. Heading straight into the cold city air as she walked to Oscorp. Making her way up to the top floor after retrieving her I.D. badge.
"Wanda, good morning." Jean greeted her as she entered the office.
"Good morning. How are you and the little one?" She asked her as Jean smiled, resting her hand on her stomach.
"We are both great." She answered before Y/N walked in, three cups and a bag of donuts.
"Green tea for Jean, coffee for me and coffee for Wanda." They handed them the cups before placing the donuts on the desk. "And breakfast." The two women thanked them before Jean handed them a file.
"You have a meeting with Dr Stacy about the new antibiotic." Jean told them as they nodded.
"Would you spend this week showing Wanda how everything is done here?" They asked her. "I want her to know everything before you leave but if she doesn't get everything, I will always help if you need me." They told the two who just nodded. Wanda watched as they disappeared down the hall and towards the elevator.
"They don't really get a moment." Jean told Wanda who nodded, grabbing a seat beside the pregnant woman. "You seemed to be upset when you came in." Jean observed as Wanda shook her head.
"Just marital problems." Wanda shrugged as Jean looked at her shocked.
"But you're so young." She whispered as Wanda chuckled.
"We have been together forever." Wanda told her, soon interrupted by the phone ringing, watching as Jean showed her how to get into Y/N's schedule. Wanda was shocked at how many meetings they had in a day, and what time they actually finished work.
"They also never really rest." Jean told her.
"I can see." Wanda nodded as she swallowed.
"You won't be staying that long unless they need you for an emergency." Jean told her. "But the overtime is generous." The two had gone on with Jean showing Wanda how to use the company software and how to make the changes as Y/N headed towards the labs.
"So, how far along is the process?" They asked her as she looked up from her tablet.
"It is almost done, we just need to start trials soon." Gwen started. "It is supposed to be stronger than your average oral antibiotic, tackling the source of the infection. We have tried it on a test dummy but we won't get sufficient results until we open up for human trials."
"Get the FDA to sign off on the trials first." They told her as she handed them another file.
"We have also had to adjust the formula of the tranquilizers." She informed them. "The old formula was." She made a face. "It was too potent."
"Just keep me informed, inform the FDA and get that approval." They told her before they walked away with the new files in their hands. Once Y/N had made it back to the office, they spotted both Jean and Wanda chatting comfortably. "Ms Maximoff, a word please." They held the office door open for her which she had quickly moved inside. "Please, have a seat." Wanda was quick to follow their order as they placed the files down in their growing pile. "I assume that Jean has shown you most of the database."
"Yes." Wanda answered as Y/N smiled at her.
"Wanda." They stood up from their seat and looked out of the window for a brief moment before continuing. "I had to do some of my own research and it seems that your husband is none other than the son of Anthony Stark."
"I can explain." She tried, thinking she was going to lose her job.
"I know you can." They gave her a smile. "But I also have another contract for you to sign. It protects the assets of Oscorp and its investors." They reached inside their draw for a binded contract. "It pretty much states that you cannot speak of anything that happens inside of this building, or you will be facing a lawsuit." Wanda nodded in understanding, of course she hated the idea of lying to her husband but she needed to earn her way, not like anyone would understand. She held out her hand for a pen which they handed her one from their pen pot. "Just a quick question darling." They asked as they took the contract. "Why do you want to work if being Jarvis Stark's wife provides for you?"
"I want to be able to earn my own money." She told them honestly. "I don't want to be known as Jarvis Stark's pretty little wife."
"Then why did you marry him?" They questioned as she bit the inside of her cheek. A small smirk formed on their face before they smiled guiltily at her. "My apologies, it isn't my place."
"I love him." She told them, her eye contact never faltering. "I have loved him since the moment he asked me out, as nervous as he was for being the infamous Tony Stark's son. He was the complete opposite to his father, he was sweet and loyal, kind and caring."
"You said that as in the past tense." They told her. "So, you don't think he is the same man you fell in love with?"
"Are you my shrink?" Wanda questioned with a raised brow, making Y/N chuckle lightly before leaning on the desk before her.
"I just want the best for my employees Wanda." They told her, nothing but genuine affirmation of the words laced their tone. "I know the people outside of this company think I am heartless. A power hungry being but I only want what's right for every one who works for Oscorp, that is what Norman taught me before he left me as the sole successor of his company." Wanda listened as they spoke. "The company is as strong as the people who run it. I just keep everything in order, it's the employees who keep Oscorp running, their ideas, their knowledge, their creations keep Oscorp from going underground."
"I can say that I was one of those people." Wanda whispered as Y/N laughed a little.
"Wanda, you are now one of the people who keep Oscorp running too. You keep me on schedule and arrange the appointments for the investors." They rested their hand on her shoulder. "So I only have your best interests at heart." With that they grabbed their next file before heading to the door with Wanda following. "Just know you can always come to me." With that they opened the door for her before heading to Jean.
"Mr Fisk is downstairs." She informed them.
"Why don't you both order lunch? Take a break." They suggested, before they headed to the elevator, leaving Wanda pondering their last conversation.
"What is the deal with them and Norman?" Wanda asked Jean who shook her head.
"That is not my place to tell." She told her. "I only knew because I was Norman's assistant before Y/N took over."
"So you've been here longer?" She questioned as Jean shook her head.
"No, Y/N was always here, shadowing him, learning how to run the company. They even helped with the Glider Project." Jean told her. "Of course it failed, an accident happened and well, Norman scrapped it."
Wanda was most certainly drawn into the mystery that is Y/N Y/L/N.
#wanda maximoff x reader#wanda maximoff#marvel#elizabeth olsen#wanda x you#elizabeth olsen x reader#wanda x reader#wanda x y/n#wanda maximoff x you#natasha romanoff
233 notes
·
View notes