#emailhack
Explore tagged Tumblr posts
Text
Getting sucked into unread emails (solved!)
When I need to send an email while in the middle of “deep work,” I often get pulled into my inbox and distracted by unread messages. For years, a solution escaped me. I’d find myself working on something important, go to send an email, and the next minute find myself perusing the school newsletter. To avoid this, I’ve started a simple habit: I always exit my email client with the “Drafts” tab…
#drafts#emaildrafts#emailhack#ideas#inboxproblem#productivity#sendingemail#sidetracked#smallbiz#smallbusiness
0 notes
Link
The world of online scams is unfortunately all too familiar. Even celebrities fall victim to these deceptive tactics, as Oscar-winning actor Eddie Redmayne recently revealed on Late Night With Seth Meyers. However, Redmayne's story takes an unexpected turn, highlighting the power of genuine friendship and a helping hand in times of need. Eddie Redmayne Recalls A Phishing Phumble: Redmayne's Email Gets Hacked Redmayne shared his experience with host Seth Meyers, describing a situation that unfolded "a few years ago." He explained that his email account was compromised by hackers, leading to a frustrating scenario. "I was actually in New York at the time and I had a big night the night before," Redmayne recalled. Waking up with a groggy head, the last thing he expected was a message that would leave him both confused and touched. A Voicemail of Concern: Warren Beatty Reaches Out Turning on his phone, Redmayne discovered a voicemail that instantly caught his attention. "And I turned to my wife [Hannah Bagshawe], and I said, 'I think Warren Beatty has just left me a voicemail checking [if] I’m okay and whether I need money,'" he recounted. The situation was surreal – a legendary actor like Warren Beatty reaching out with such a specific concern. Pieces Falling into Place: Deceptive Emails and Genuine Help Redmayne further explained that Beatty's voicemail made him realize the extent of the email hack. He revealed that his contacts had received "a very persuasive email saying that I was stuck and needed" financial assistance. Thankfully, Beatty, unlike others, saw through the deception and chose to reach out directly. A Lasting Impression: Redmayne's Gratitude for Beatty's Kindness Years have passed since the email hack, but Redmayne's appreciation for Beatty's gesture remains strong. "To Warren’s incredible, generous credit, he was pretty much the only person who was kind enough to help to bail me out," he stated. He further emphasized the significance of this act, concluding, "But like, to this day, that man has a great place in my heart." Beyond the Headlines: The Story Behind the Story Redmayne's anecdote isn't the first time this story has surfaced. In February of 2024, fellow actor Jamie Dornan, a friend and former roommate of Redmayne, shared a similar version of the events on the Happy Sad Confused podcast. Dornan confirmed that everyone in their circle received the fraudulent email requesting money, but highlighted Beatty's genuine concern: "And fair credit, Warren Beatty was like, ‘Whatever you need,’” he recounted. However, Redmayne added a humorous tidbit to Meyers, pointing out that Dornan himself hadn't offered any help despite receiving the same email request. This lighthearted moment adds a layer of camaraderie to the story, showcasing the playful banter between friends. A Message of Caution and Camaraderie Redmayne's experience serves as a reminder of the importance of online security. Phishing scams are prevalent, and vigilance is key to protecting personal information. However, the story also offers a heartwarming message about the power of friendship and the value of a helping hand, especially from unexpected sources.
#actorfriendship#celebritykindness#celebritynews#compassionatecelebrities#cyberattack#EddieRedmayne#EddieRedmayneRecalls#emailhack#filmindustry#fraudulentemails#heartwarmingstories#Hollywoodgenerosity#Hollywoodlegends.#JamieDornan#onlinescam#SethMeyers#supportivefriends#WarrenBeatty
0 notes
Text
Monitor Your Dating Partner’s Call History
In the age of digital communication, understanding and navigating the dynamics of relationships have taken on new challenges. One such trend that has emerged is the monitoring of a dating partner's call history. This article explores the nuances of this practice, delving into its benefits, privacy concerns, and the delicate balance between trust and transparency.

Privacy Concerns
The ethical considerations surrounding monitoring a partner's call history are complex. While transparency is crucial, it raises questions about respecting personal space and individual autonomy.
Legal Implications
Beyond ethics, there are legal ramifications to consider. Laws vary globally, and understanding the legality of such actions is imperative to avoid legal consequences.
Trust Issues
Ironically, the act of monitoring can lead to trust issues if not approached with sensitivity. It's vital to weigh the potential harm against the benefits and explore alternatives to build trust organically.
Benefits of Monitoring Call History
One argument in favor of monitoring partner's call history is the promotion of communication transparency. It can lead to open discussions about expectations and boundaries, fostering healthier relationships.
Identifying Red Flags
Monitoring can serve as a tool to identify potential red flags early on. Recognizing patterns in communication can empower individuals to address concerns before they escalate.
Building Trust
Contrary to common belief, monitoring can contribute to building trust when approached collaboratively. It provides an opportunity for partners to demonstrate transparency and commitment.

Choosing the Right Monitoring Tools
With technological advancements, various monitoring tools are available. Understanding the pros and cons of apps versus traditional methods is essential for informed decision-making.
Features to Look for
When selecting monitoring tools, certain features are paramount. From call logs to location tracking, choosing tools that align with relationship needs is crucial.
User-Friendly Options
The accessibility and user-friendliness of monitoring tools play a significant role. Opting for tools that are easy to navigate ensures effective use without unnecessary complications.
Communication in Relationships
The foundation of any healthy relationship is open communication. Discussing the reasons behind monitoring call history and setting expectations can prevent misunderstandings.
Establishing Boundaries
Partners should collaboratively establish boundaries regarding privacy and monitoring. Clear guidelines help create a sense of security while respecting individual autonomy.
Addressing Concerns
Regular check-ins on how monitoring impacts both partner’s can address concerns promptly. Adjustments to the approach can be made to ensure a balanced and trusting relationship.
Your Partner's Perspective
The key to successful monitoring lies in mutual consent. Both partners should be on board with the decision, emphasizing the importance of shared values and goals.
Building Trust Through Communication
Trust is a dynamic aspect of relationships. Actively working on trust-building through open communication minimizes the need for constant monitoring.
Respecting Privacy
While monitoring is a choice some couples make, respecting each other's privacy remains paramount. Striking the right balance is crucial to maintaining a healthy relationship.
Overcoming Insecurities
Insecurities often drive the need for constant monitoring. Building self-confidence through self-reflection and self-improvement can alleviate these insecurities.
Seeking Professional Help
If insecurities persist, seeking professional help, such as counseling, can provide valuable insights and strategies for overcoming personal challenges.

Relationship Counseling
Couples facing trust issues may benefit from relationship counseling. A neutral third party can facilitate discussions and guide the couple toward a resolution.
Balancing Trust and Independence
Balancing trust and independence involves fostering individual growth within the relationship. Encouraging personal development contributes to a stronger partnership.
Mutual Support
Supporting each other's endeavors and dreams enhances trust. Mutual support creates a foundation where partners can pursue their goals while relying on each other.
Finding Common Ground
Identifying shared values and goals helps find common ground. This shared foundation strengthens trust and enables partners to navigate challenges together.
Dealing with Trust Issues
For relationships facing trust issues, rebuilding trust is a gradual process. Consistent actions that align with commitments can gradually restore the foundation of trust.
Establishing a Secure Foundation
Understanding the root causes of trust issues is crucial. Establishing a secure foundation involves addressing underlying concerns and working together to build trust.
Professional Guidance
In cases where trust issues persist, seeking professional guidance, such as couples therapy, provides an objective perspective and structured support.
Common Misconceptions About Call History Monitoring
Invasion of Privacy
One common misconception is that monitoring Partner’s call history is an invasion of privacy. However, in the context of mutual consent, it becomes a shared decision rather than an intrusion.
Lack of Trust
Contrary to belief, monitoring does not always indicate a lack of trust. It can be a proactive approach to ensuring transparency and addressing concerns
Learn more : Monitor Your Dating Partner’s Call History
Final Word:
In the end, monitoring your dating partner's call history is a complex practice that requires careful consideration. While it can offer benefits such as communication transparency and early red flag identification, it also raises significant privacy and trust concerns. The key lies in open communication, mutual consent, and respecting boundaries. Balancing trust and independence, addressing insecurities, and seeking professional guidance when needed are essential elements for a healthy relationship. Ultimately, the decision to monitor call history should be a collaborative one, emphasizing the importance of building trust organically.
10 notes
·
View notes
Text

The Need of secure e-mail service . . . . for more information and tutorial https://bit.ly/47giFx3 check the above link
#cybersecurity#emailsecurity#sslstripping#mitbattck#computerscience#arpspoofing#emailhacking#sessionhacking#mitmattck#computerengineering#javatpoint
1 note
·
View note
Text
Need an ethical hacker?

0 notes
Text
This has got to be the worst scam email I’ve ever seen.

0 notes
Text

Ever hit 'send' and realized you forgot to attach a file? Don't panic! #Smart_Delayed_Send gives you get extra five seconds to add what you missed.
To know more visit https://www.icewarp.co.in/
0 notes
Text
💌 Unlock Email Marketing Magic: Your Free Guide to Spam-Free Success

Tired of your emails getting lost in the spam abyss? 🚫✨ Learn the secrets to crafting irresistible email campaigns that deliver results.
Grab your FREE PDF course and discover:
🎯 Subject Line Mastery: Write attention-grabbing subject lines that boost open rates.
📩 Engaging Content Creation: Create compelling emails that keep your audience hooked.
📈 Deliverability Optimization: Ensure your emails reach the inbox, not the spam folder.
📊 Performance Tracking: Measure your email success and refine your strategy.
Click HERE to get your FREE Copy
#emailmarketing #digitalmarketing #emailtips #emailstrategy #marketingtips #onlinemarketing #emailmarketingtips #emailcampaign #emailsuccess #emailhacks
#emailmarketing#online businesses#affiliatemarketing#digital marketing#digital products#make money online
1 note
·
View note
Text
How to Unsend an Email ✉️🚫
Ever hit "Send" on an email and instantly regretted it? 😅 Don't worry—here's how to unsend an email in a few simple steps! ⏪
Gmail Users: Google offers an "Undo Send" feature. Once you've sent an email, a small pop-up will appear at the bottom of your screen. Just click "Undo" within 5-30 seconds (depending on your settings) and your email will be unsent! 🎉
Outlook Users: You can recall an email, but only if the recipient hasn't opened it yet. Go to your "Sent Items," open the email, and select "Actions" > "Recall This Message." 🤞
Other Platforms: Some email services, like Yahoo, don't offer an unsend feature. In that case, double-check before hitting send! 📋
Quick Tip: Always review your emails for typos, the right recipients, and attachments to avoid needing the "unsend" option in the first place. ✍️
#EmailTips #UndoSend #EmailRecall #EmailHacks #TechTips #Productivity
0 notes
Text
Email Like a Pro: The Essential Etiquette Guide
Tired of ignored emails? We've got the guide to level up your digital game 😎 #emailhacks #professionalAF #communicationgoals #fiercemillennial #hustle&grind
Upgrade your digital communication and leave a lasting impression Yo, friend. Tired of sending emails and wondering if they even landed in the right inbox? Wish people would actually read what you write instead of tossing you a quick “k”? Yeah, we’ve been there. The truth is, email is still a major player in the biz world, whether you’re job hunting, managing a team, or running your own show.…

View On WordPress
#career tips#email#etiquette#FIERCE MILLENNIAL#hustle#Hustle & Grind#professional development#Women in Business
0 notes
Text

Is your email at risk?
0 notes
Text
Monitor Your Dating Partner's Facebook Account
In the ever-evolving landscape of relationships, the digital realm plays a significant role. Social media platforms, like Facebook, can offer insights into our partners' lives. However, the question arises: Is it appropriate to monitor your dating partner's Facebook account?

Why monitor your dating partner's Facebook account?
Establishing trust in a relationship is paramount. Monitoring a partner's Facebook activity can help build that trust by fostering transparency and addressing potential concerns early on. While it may seem like an invasion of privacy, understanding the motives behind monitoring can uncover red flags and prevent misunderstandings.
The Privacy Debate
Balancing trust and privacy is crucial in any relationship. Open communication is the key to finding common ground. Discussing boundaries and expectations ensures that monitoring is done with consent and does not breach the trust that is being built.
How to Monitor Facebook Without Breaching Trust
Transparency and consent are the cornerstones of ethical monitoring. Partners should openly discuss their comfort levels and agree on the extent of monitoring. Setting clear boundaries ensures that both parties feel secure without compromising privacy.
Recognizing Warning Signs
Behavioral changes online can be indicative of issues in a relationship. Monitoring Facebook can help identify discrepancies in communication and address potential issues before they escalate.
The Impact of Social Media on Relationships
While monitoring can uncover potential problems, it's essential to acknowledge the positive aspects of social media in relationships. Sharing experiences, staying connected, and celebrating milestones online can enhance the bond between partners.
Learn More: Forever Wild Dating USA - Dating Partner’s
Building Trust Without Invasion
Fostering open communication is crucial in navigating the fine line between monitoring and invasion. Trust is built through understanding and respecting each other's boundaries, both online and offline.
Understanding Your Partner's Perspective
Mutual respect for personal space is vital. Discussing concerns and expectations around monitoring helps partners align their views and build a foundation of trust that goes beyond online interactions.
Effective Communication in Relationships
Communication is the backbone of any healthy relationship. Addressing insecurities and concerns openly ensures that both partners feel heard and understood.
Social Media Etiquette in Relationships
Respectful online behavior is essential for maintaining a positive digital presence. Avoiding misunderstandings and misinterpretations is key to nurturing a healthy relationship both online and offline.

The Role of Trust in a Relationship
Trust serves as the foundation of a strong relationship. Understanding how monitoring fits into trust-building can help partners navigate this aspect of their connection with empathy and consideration.
Common Misconceptions About Monitoring
Clarifying misconceptions surrounding monitoring is crucial. Distinguishing between healthy monitoring and invasion helps dispel myths and promote a more nuanced understanding of this aspect of relationships.
Discussing Boundaries with Your Partner
Setting mutual expectations around monitoring ensures that both partners are comfortable with the level of transparency in their relationship. Respecting each other's comfort zones is vital for a healthy dynamic.

Maintaining Balance in Digital and Real-Life Relationships
While digital interactions are valuable, maintaining a balance with real-life connections is essential. Over-reliance on social media can hinder the depth of personal interactions, emphasizing the need for a holistic approach to relationships.
Seeking Permission Help
Navigating the intricacies of digital parenting often involves seeking permission Help. Parents, while understanding the importance of monitoring their child's online activities, may find themselves in need of appropriate tools and strategies. Permission help can come in various forms, from utilizing parental control apps to engaging in open communication with the child. It's essential to strike a balance between ensuring online safety and respecting a child's growing need for independence. Seeking permission actively involves the child in the decision-making process, fostering a collaborative and trust-based approach to managing their digital experience.
Conclusion
In conclusion, monitoring your dating partner's Facebook account can be a tool for building trust and addressing potential issues. However, it must be approached with sensitivity, transparency, and open communication to avoid breaching privacy and trust. Striking the right balance between online and offline connections is key to a healthy and fulfilling relationship.
12 notes
·
View notes
Text
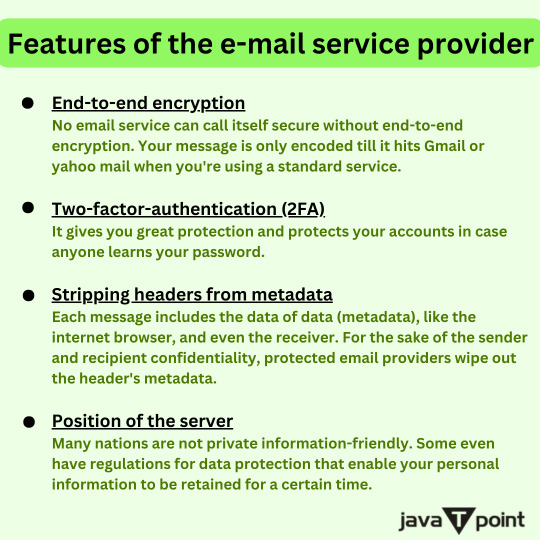
Features of the e-mail service provider . . . . for more information and tutorial https://bit.ly/47giFx3 check the above link
#cybersecurity#emailsecurity#sslstripping#mitbattck#computerscience#arpspoofing#emailhacking#sessionhacking#mitmattck#computerengineering#javatpoint
0 notes
Text
Verified Hacking Services Available HERE.
Proofs provided
Ethical Hacking like any other forensic science involves
the use of sophisticated technology tools and
procedures that must be followed to guarantee the
accuracy of the preservation/documentation of
evidence,identification, extraction and the accuracy of
results.
They are a team of white hat veterans who have been able to
provide clients with computer Ethical Hacking exploits/
Investigations for a wide range of Civil disputes &
Criminal Cases.
These includes; Whatsapp/IG/FB/Twitter/
Email, Litigation, Fraud,Hack/Track Phones and
Computers,Intellectual Property, Website,
Hack&Security,Credit Score Upgrade,Human
Resources,Unlock Computer,DUI/Criminal Records
Removal, Recover lost files/Documents, Content Removal
etc..
NO BAD REVIEWS!!!
Contact: whitehatsforhire (at) protonmail. com
Text: +1 6512430021
#hireahacker #hacker #hack #ethicalhacking #whatsapphacking #emailhack
0 notes
Photo

#eMailHack #Hackers #Hacktivists #LoriLightfoot @chicagosmayor @fbi @kgb.agents @thedemocrats @wikileaksparty @wikileaks @mayorrahm @rahmemanuel @cia @united @exelonofficial @fly2ohare @cubs @whitesox @govpritzker @jbpritzker #Fraud #Waste #Corruption #Politics #Police @cpdreform @cpd19district @cpdhq #WikiLeaks (at The Mayor's Office) https://www.instagram.com/p/COl0i8zBRXC/?igshid=17v4xdbpa2vvt
0 notes
Photo

To cater to the high demand from across the Nation, #MMA proudly presents the second batch of Online Workshop (Webinar) in "Selling by e - Mail & Closing the Deal" on 🗓 10th October 2020 through #ZOOM 🌐 Attend from any part of the World 🌎 ⌛ Hurry & Book your Seats now!!! 🖥Visit https://lnkd.in/gRSQkWm or 📩Mail us to [email protected] #MMACHENNAI #AIMA #CHENNAI #TAMIL #WEBINAR #TAMILNADU #saleshacks #emailmarketingtips #emailsuccess #emailcampaign #emailetiquette #emailhack #salestraining #saleshacks #virtualsales #virtuallearning #wfh #resilientrohit https://www.instagram.com/p/CGE_z5unLM9/?igshid=1gg0u9z6n92ws
#mma#zoom#mmachennai#aima#chennai#tamil#webinar#tamilnadu#saleshacks#emailmarketingtips#emailsuccess#emailcampaign#emailetiquette#emailhack#salestraining#virtualsales#virtuallearning#wfh#resilientrohit
0 notes