#email compliance between
Text
Interesting thing I noticed in the FNAF AR emails. I think this email is related to GGY

What I found particularly interesting is the part about Vanessa looking up how to induce “compliance” in human subjects. Originally, it was believed that this was the mimic looking to garner more control over Vanessa but I’d come to disagree with that interpretation.
Following “another David Theory”, I believe this was the mimic trying to gain more control over Gregory. After all, his control on Vanessa is tight locked and she’s never been seen to disobey him, but Greg?
Looking at the timeline between AR and dreadbear, it seems AR takes place right after the “selected one” in the scottgames files is kidnapped (AKA Gregory). Obviously, compared to Vanessa, the mimic would have a harder time attempting to control Gregory because he never put himself in a situation where his mind could be easily corrupted. Vanessa is a complicit servant because she collected the tapes which directly put herself in Glitchtrap hands, essentially making her a victim of connivence to the mimic.
Compared to Gregory though, he was intentionally targeted, meaning that compliance had to be forced upon him. This would mean the mimic would have to learn how to actually gain control human subjects without their indirect help. Hence, it would explain why Vanessa was looking these things up, she was helping the mimic learn how to stabilize GGY. The GGY interpretation of this email also adds some sense to the mimic’s actions as well, because, if Vanessa was truly being disobedient to him, why would he reveal methods to her that he was going to use to incite obedience. If she had any recollection of her current life, she would be able to make counters for whatever Glitchtrap found as she would see it coming. But if it was for Gregory, both Vanny and the mimic would be able to use this information to their advantage.
Overall, I think this email was a GGY teaser, we just didn’t see it.
#fnaf ggy#gregory fnaf#five nights at freddy's#fnaf ar special delivery#fnaf the mimic#fnaf#fnaf vanessa#another David theory
66 notes
·
View notes
Text
The Magnus Archives Fic list lying on my computer>
The horror and everything else. Mostly Jon centric probably...
Anatomy of a Mask - A new archival assistant is hired. Her name is Mary Sue. Starts as a comedy and absolutely does not end that way.
Plus One - Jon attends a series of parties for which a plus one is mandatory.
Decree Nisi - Elias and Peter divorce (again), and the judge is tired of their bullshit.
Reflection - Jon is haunted by himself, and refuses to take any of his advice.
Rosemary and Thyme - fantasy AU featuring romance, quests, and fairy politics.
What Belongs to the Sea - Selkie AU, mind the tags on this one.
Bell, Book, and Candle - “By the Ride or Die Pact of 2009, Jonathan Sims can call upon Georgie Barker at any time for aid with no strings attached. Despite their rocky history, their childhood friendship, and Jon’s barely recovered alcoholism, this pact is sacred and must be upheld.”
Things Could Always Be Worse - Jon swaps place with an alternate-universe version of himself, who is heroic, chivalrous, and wears plaid. It’s terrible. Inspired by the parodic “straight TMA” blog.
👁🗨 👁🗨 👁🗨 👁🗨 👁🗨 👁🗨 👁🗨 👁🗨 👁🗨 👁🗨 👁🗨 👁🗨 👁🗨 👁🗨
Sex Repulsion and Asexuality Save the World (Though That's Not What Jon Claims): canon divergent from MAG 160, in which Jon is so sex repulsed that a changed word in the Hazel Rutter statement saved the world. Crack is treated seriously.
Refusing to Give Up Tomorrow: safehouse hurt/comfort ft. MAG 160 divergence
The Eyespot Chronicles: Trilogy of works. AU where instead of going Somewhere Else, Jon and Martin stay in the OG universe. However, Jon is a moth.
Déjà Vu: Time-travel fix-it where Sasha, Tim, Jon, and Martin all wake up on the day of the day of season 1, episode 1, with memories spanning from that day to the moment they died.
terror management theory: AU where Mr. Spider kills Jon, and now Jon can't permanently die. Despite this, the fic is rather light-hearted (or at least crack)
Other Kingdoms: A season 3 fix-it, in which Martin uses a Leitner to wake Jon up. Do note that there are references to sex happening (Jon's demisexual in this), but it's rated T so nothing is shown.
When No One Looks: Dark Avatar!Jon AU set during the latter half of season 1
Chamomile: In which post season 4, the NotTea becomes a pet.
If The Archivist Had Been Meant to Fly...: Wingfic in which Jon saves Martin from Simon Fairchild
Molt: This is my favorite take on Web!Martin. This is also a darkfic, to the point that the author was made so sad by chapter 1 that they wrote chapter 2 as a fix-it to chapter 1. Also, as a warning that I would've appreciated but isn't in the tags or summary: there's a scene alluding to corrective rape, but this doesn't actually happen.
Drawn Out of the Unknown: Canon divergent s3 fic, official summary is "While investigating a possible location for the Circus's base, Martin and Tim find something unexpected.
The fic series that contributed to me listening to TMA was this Good Omens crossover by Bibliocratic. Really enjoyed it and finally between this fic and seeing TMA all over my tumblr dashboard (plus having a project to work on with my hands) I finally listened, so I'm thankful for that.
The other series I really love is>
The Magnus Institute vs the 21st Century: a series of emails and IMs which is just utterly hilarious. It's the Magnus Institute going through GDPR compliance processes and it's just fabulous.
And then one I'm still sort of following even though I don't read much TMA fic right now is
dustsceawung by callmearcturus. It's a Moth!Jon fic with Martin as someone who moved to a town in a different fairy court (in a fae AU). Not complete and hasn't updated in a while but I really like the tone.
The world is too much with us is one of the many many many time-travel fix-it fics (I think that's a genre all it's own in the TMA fanfic community at this point). Spoiler to be on the safe side, it follows Jon after he's dropped back in 2014 by the Spiral, and relives what amounts to the next four seasons of TMA, using the experiences he had the first time 'round to try and avoid the apocalypse--and keep everyone alive in the process. Oh, and he's got the added bonus of already being an Avatar of the Eye. Very much angsty with a happy ending. This one's completed, so feel free to binge.
Martin x Jon
https://archiveofourown.org/works/41149674As everything ends, as the tower crumbles around them, Jon and Martin hold each other in a firm embrace. What they see of the world shatters, and Jon breaks with it. He awakened, alone, confused, and something was terribly wrong with him.
Tim drags Jon to a party in celebration of his promotion with one goal in mind: getting Jon drunk off his arse.
Martin is moving to a different position within the Institute and celebrates as well.
through the clouds like a moonbeam: Jon gets wings during the apocalypse. Martin likes them; Jon doesn't.
I’ll bear the waiting now: AU where Jon is the new head archivist with two assistants, but there's a disembodied voice that only Jon can hear. Do note that there is something that looks a lot like suicide but there's a happy ending. (Alternate summary that spoils the fic: Martin is a "ghost" and also Jon's "late" boyfriend. )
true kinda love: Season 3 Co-Archivist!Jonmartin
hiding: Season 3 jonmartin kissing to hide from the Circus
The Garden of forking Paths - Jon and Martin search for each other through universes.
“What about him then?” Georgie asks.
“Who?”
“Him,” she says again like it is obvious who she means, holding up the sketchbook revealing a spread that has several loose sketches of Martin. It surprises Jon it took Georgie so long to find Martin in the book considering he had at least one-third of its entirety dedicated to him.
To graduate from art school, Jon needs to paint a nude portrait, but none of his friends are too keen on modeling for him. As a last resort, he asks a handsome barista.
https://archiveofourown.org/works/46426702When Martin needs a fake boyfriend to bring to his family reunion, Jonathan Sims is the last person he would have expected to volunteer.
https://archiveofourown.org/works/51906919Tomorrow, Martin begins his new job as a lighthouse keeper. He knows (hopes) he'll enjoy it. What he doesn't know (yet) is that a very, very curious selkie lives near and is intrigued enough by him to come visit.
https://archive.transformativeworks.org/works/30210444/chapters/81277828 The last fic I read (time travel)
This list has become a behemoth, comprising various lists created by others. I've saved it, but now I need to free up space. This is the process I'm undertaking for every list I've saved.

#the magnus archives#jonathan sims#jon sims#martin blackwood#jonmartin#fanfiction#tma podcast#tma fanfic#fanfic list
15 notes
·
View notes
Text
Thank you for the tag @the-blue-eyed-firebender !
The story you're proudest of:
That would be one of the first multi-chaptered fic I translated, Her story through her hair, and I would also add my first smut, It's a moment in between the others
Your story that's gotten the most love online:
That would be She's not a diamond, my JB Regency AU! I haven't updated it in a while, the fault to ffnet that refuses to send me emails when there's a Nuit du FoF, the moment I usually write one or even two chapters. It's the outlier in my stats, the one that has the most of everything except word and chapter counts
Tease a current WIP or idea you're working on:
From the next chapter of The name was a knife, twisting in her belly:
The surprise on Jaime’s eyes melted into an undefinable softness, and moved by a sudden impulse, she swore this oath. “I, Brienne of Tarth, promise you to use this sword to help the Stark daughters and help you restore your honor.”
A small gasp from Jaime was his only reaction for a few seconds, before he put his hand and stump over the sword so their skin touched. Brienne shivered involuntarily. “And I, Jaime Lannister, accept your promise. I will do everything I can to help you in this enterprise so you can stay safe as well.”
Your top 3 fandoms:
Fullmetal Alchemist, A Song of Ice and Fire, The Lord of the Rings
Your top 3 ships:
Unsurprisingly: Royai, Jaime x Brienne, Farawyn
Rec someone else's fic:
the story's just beginning (time we did some living) by starsinherblood aka @jedidragonwarriorqueen, marked "Royai fluff for dark times" in my bookmarks, and rereading it, I still agree with that note!
Pick one!
Fluff or Angst: Hard choice! I think I'm better at writing fluff
Oneshots or longfics: One-shots, whether they're long or not, even though I'm writing more multi-chaptered fics lately. But I can't consider them as longfics (the threshold is around 50k words for me)
Canon compliance or canon divergence: it depends on the fandom, though. I'll write more canon compliance for FMA, and more AUs or canon divergence for ASOIAF
AO3 or FF.net: As I was saying earlier, ffnet is sometimes annoying, and it's not the place where my fics have the most success. I only publish in French there now
Tagging @jedidragonwarriorqueen, @torchwood-99 @writergirl2011 @writing-royza if you want to!
11 notes
·
View notes
Text
Once again,@lautaronahuellopez I cannot answer your asks but I get them through email lol.
Raiko wanted to use Mako to manipulate Wu. As a political opportunist, the President saw an opportunity to subdue the United Republic's main threat through his ruler, establishing a puppet king with advisors appointed by Raiko, who would have real power. However, such a plan would need contingencies to put Wu on track in case he wants to rebel against the system. Mako could be that contingency. In a conservative country where the continuity of the monarchy hangs by a thread, a revelation about the courtship between Wu and his bodyguard would be enough for the scandal to end him. Mako could even be used to influence certain policies. Luckily, Raiko's arrogance and misrule, coupled with his cowardice on the battlefield and Wu's growth as a person, caused her to lose the election and be unable to carry out his Machiavellian plan.
Yeessss So I've been screaming about Raiko's attempts to control and manipulate Wu for a while. Wu is naive and unprepared for the throne and Raiko LOVES it. He's very happy to put him on the throne and prop up his own advisors and ministers to handle the day to day ruling. Obviously Wu is not absolved of his disinterest in actively ruling his own kingdom, (that's Wu's whole character arc, Wu finally stepping up and taking responsibility) but like. We have got to remember he was being manipulated by an experienced politician who's probably three times his age. Wu didn't stand much of a chance!
Except that Raiko is willing to give Wu whatever he wants: And what Wu wants is Mako. Only Mako is a good influence on Wu and pushes Wu toward that character growth.
But OH BOY the idea that maybe Raiko would use Wu's relationship with Mako against him?? Blackmail him into compliance? That's actually a delicious idea.
You know, though. Raiko may have lost the election, but in the Avatar Legends Tabletop RPG, Raiko hasn't completely left the political scene. He and his wife start a political talk radio show! If Raiko has knowlege of a relationship between Mako and Wu, he could still use that knowlege for nefarious reasons...
8 notes
·
View notes
Note
Hi! Fellow Shinra fan! :)
I'd love a fic with Reeve and/or Rufus. Maybe them late night working on projects for Edge? (Together. Maybe begrudgingly, but also appreciative of the other's skill and competence.)
Hah, okay, so funny story. I spent literal years trying to make Rufus/Reeve a serious ship in this fandom. So so many years. I don't want to talk about how many years. I blame The Conscience of the King for sticking in my head so thoroughly (you can find that here [http://www.midgar.net/king/] if you've never heard of or read it, but word of warning, it's so old that it's literally text files uploaded to a website; this thing was distributed via email rings back in the late 90s; needless to say, it does NOT take in any extended canon, only OG stuff). Over the years, of course, I've taken most of them down in favor of my more general Turk-fic, but just. My first love, okay? It was always Rufus/Reeve. XD
Now, I realize you didn't expressly ask for Rufus/Reeve, but uh. Here's what you're getting: my trademarked ambiguous relationship style thing. In my favorite time period, which is ambiguously before the start of the original game. Mostly because WRO Reeve breaks my heart.
Prompted from this post. Still taking prompts! If you'd rather do a ship/character + number prompt or a symbol for a headcanon, I'm still doing those too.
In These Deep City Lights
Word count: 1274 words.
Content Notes: Eh. Ambiguous relationship.
Characters: Rufus Shinra and Reeve Tuesti.
Summary: Reeve finds Rufus looking over one of the Midgar models.
Most people who wanted to look at a model of Midgar went to Memorial Hall on the 60th floor. It was, after all, the most impressive of the models of Midgar, with the oversized Shinra Tower in the middle and the model reactors that flared on schedule for their secondary burn process. But it wasn't Reeve's favorite of the models. That honor went to the one on 34. She was a smaller model, and her reactors didn't have the fancy show mechanics that the 60th floor did, but her pieces were moveable. In the middle of the night, he usually had the model to himself.
That was precisely why seeing someone standing in the room surprised him. They hadn't turned on the overhead lights, and instead, they appeared to be inspecting the model purely in the light from the city itself, pouring in through the floor-to-ceiling windows.
Reeve had done that himself more times than he cared to count, and he watched the figure through the frosted glass that separated the model from the rest of the office for a few minutes before he finally went to the door.
He opened it to find Rufus leaning over the model, fingers sliding across the tops of the buildings in Upper Eight. Reeve noticed immediately that several of the buildings were missing, and he spotted them arranged on the table to the side of the model nearest the windows. It took him a moment, but his eyes widened as he realized that they were laid out almost identically to the last proposal for Sector Six that he'd sent the President.
He cleared his throat, but Rufus didn't jump. He didn't even look up. He simply made a low sound and moved another building from Sector Eight to the mocked-up representation of Six. He studied it for another moment, and then he finally looked over at Reeve.
"Vice President," Reeve said, and he took another step into the room, letting the door shut behind him. Under the weight of those blue eyes, that felt like a mistake.
"Reeve," Rufus murmured, and he looked back at his collection of buildings.
"I wasn't aware that you came down here," Reeve finally said, breaking the silence. He crossed the room and picked up one of the buildings, turning it over between his fingers.
He watched as Rufus studied the model, eyes intent and focused, as though he could simply will Midgar into existence— compliance— with his gaze alone. He spoke after a few minutes, voice measured and even, "Only when I need to see one of your proposals."
Reeve set the building he'd picked up back down where it went in Sector Four. He supposed it made sense that Rufus would review the proposal— he was the Vice President, and despite the President's attempts to keep the position as something in name only, Rufus had done his damnedest to carve out some degree of control— but he was surprised by how seriously Rufus was taking it.
Especially when they both knew that the President himself would never approve the expenditure to rebuild Six. There had been one chance to build Six, and when it collapsed during construction, it had taken all possibility of Midgar ever being completed with it.
"Is there anything you had concerns about?" Reeve asked instead.
Rufus straightened up, and he brushed his hair back from his face with a careless motion as he met Reeve's gaze. "You've spent a lot of time on this one," he said instead of answering Reeve's question.
Or maybe it was the answer to Reeve's question. He wasn't sure.
He couldn't look away from Rufus though.
"Clearly," Reeve replied, his voice low as he nodded toward the mock-up, "so have you."
A small smile touched the corner of Rufus' mouth, and he stepped in closer to Reeve, far closer than he had to in order to pick up the factory model from Four that Reeve still had his fingers on. Reeve pulled his hand back, yielding the piece to him, and Rufus' smile widened, eyes gleaming in the relative darkness of the room. "I admire that dedication." He turned the factory over in his hand, and then he held it up between their faces. "You've skewed the sector too heavily to production, however."
Reeve's lips parted, and he reached up to take the factory from Rufus. "My proposal—"
"Is bait," Rufus finished for him, raising an eyebrow. Then he waved a hand toward the mock-up just beside him, turning to look at it once more. "You skewed it toward things that make money because you know exactly what would catch the President's attention."
"It didn't work," Reeve pointed out after a second. "Your father won't authorize the construction."
"My father will not be the one to complete my city." There was a steel in Rufus' voice that caught Reeve's attention, and he smiled faintly at that possessive tone. He set the factory back down in Four where it went once more.
"Your city?" he asked, and Rufus' eyes cut over to him, impossibly blue given how little light was actually in the room.
Rufus tilted his head slightly. "Do you think otherwise?"
"No, of course not, sir," Reeve said immediately, dropping his gaze to the mock-up of Six that Rufus was still facing.
Rufus studied him for a long, quiet moment. "You're supposed to say 'yes.'"
Reeve looked up at him sharply, watching the way the smile on Rufus' face looked a little less practiced, a little more real. He hesitated, replaying what he'd said, and his eyes closed briefly as a faint laugh escaped him. "You're right," he said softly. "My duty is to serve the President's vision."
"Indeed," Rufus murmured. Then he motioned toward the layout for Sector Six. "Redo the proposal. Focus on housing this time."
Reeve hesitated. "You know that will never—"
"The President's vision will change eventually."
Reeve’s breath caught in his throat briefly. On the surface, that was an innocuous enough statement, but standing in that room, awash in the glow of Midgar herself, with the way Rufus was looking at him...
Rufus wasn't just the Vice President, after all. One day—
Rufus' hand closed on Reeve's tie— red tie, Shinra red because that's what the President gifted him every year for Yule — and he adjusted it carefully. When his fingers smoothed over the silk, the touch was soft, gentle.
Reeve wasn't sure how long they stood there, watching one another, Midgar the only silent witness to the moment between them. Then Reeve nodded slowly.
"I'll redo the proposal," he said softly, and there was no mistaking the momentary triumph that lit Rufus' eyes.
"Good. I'll review it personally once it's finished." Rufus' hand dropped away from Reeve's tie then. "For now, go home." He didn't wait to see if Reeve did as instructed. Instead, he turned to look out at the city in the darkness.
Reeve wasn't sure he'd ever been dismissed from one of his own floors in the Tower. He glanced past Rufus, toward the model parts scattered across the table, but before he could ask the question, Rufus waved a hand.
"I'll clean up before I leave."
Reeve nodded. "Very well," he said and he lingered for only a heartbeat more before he turned and left. When the door shut behind him, Reeve glanced back, watching the way Rufus was silhouetted in the lights, figure blurry in the frosted glass that separated the model room from the rest of the office.
He wasn't sure he'd ever been dismissed from one of his own floors in the Tower, but he supposed if anyone could do it, it was Rufus Shinra.
One day, the man would rule the world.
21 notes
·
View notes
Text
Mystictober day 1-- Favorite character/Dance
Getting past security at the RFA party is laughably easy. All that Unknown really has to do is show up half an hour late, and he's able to slink into the party hall behind some of the straggling invited guests. Of course, he's entitled to attend the party whether you sent him an official invitation or not— after all, there wouldn't even be a party without his intervention, since he was the one who sent you to the Savior’s old apartment in the first place. You did an adequate job with the guest list, and you managed to avoid succumbing to the flirtation of the RFA members, which is more than Unknown originally expected from you. Although there are only 35 people here, counting himself and the party’s hosts, Unknown is willing to consider this a victory.
He takes a few moments to finish the final preparations, moving around the room and carrying out the particulars of his plan. Once everything is taken care of, Unknown finds you on the dance floor, swaying by yourself to a slow song that's clearly meant for couples— he almost feels bad for you. On a whim, he decides that it could be fun to play with you a little before the eternal party truly begins. After all, he deserves a little bit of indulgence after all his hard work.
He waits until the brief intermission between songs to approach you. That way, his appearance won't be too conspicuous, and he won't have to put up with any interference from the rest of the RFA-- as if they deserve to even look at you when you're already his. “Hello, prince(ss),” he greets you, offering his hand as the band begins to play the opening notes of the next song. “Know who I am?”
Your blank expression shows him that you have no clue, but he's pleased to see that you take his hand anyway. “Uh, sorry, no,” you tell him with a bashful glance down at your shoes. Maybe he's just excited about his impending success, but Unknown can't help but feel endeared by this gesture. “Could you remind me? I'm sorry, I... I just send so many emails, and—”
“Shh,” he cuts you off, sweeping you into the first steps of yet another slow dance. He's never actually danced with a partner before, but thankfully, you follow his lead, whether he's doing it correctly or not. “I'm the angel who's going to take you to paradise.”
You blink at him, clearly more confused than you were at the beginning— but you're already in his grasp. “Oh,” you feign understanding. “Right. Of course. The... angel. Then I guess you... got all the information that you needed from my emails?”
You're just being polite, pretending to remember emails that you never sent. Once again, Unknown can't help but be endeared... you really are so dutiful, so adept at following instructions and bending to the whims of others that when you're confronted with a dangerous situation, your first impulse is to question your own memories rather than the stranger in front of you. Yes, he knew he chose well when he sent you to that apartment, and of course, Unknown intends to reward you for your compliance— even if you played along without knowing what you were doing.
“You've been a big help, prince(ss),” he beams at you, leaning into the implications of your confused ramblings. Whoever you think he is, you’re probably dead wrong— this is going to be so much fun. “I bet you can't wait to save all these people.”
Your confusion is evident, but of course, you're still polite. “Pardon?” You ask, allowing him to swing you across the dance floor.
“You'll find out soon,“ Unknown assures you, unable to keep the mirth from his tone. If you notice, you don’t have much to say about it. “Until then, you should just enjoy your party.”
You should be shocked, but instead, you continue to follow his haphazard lead as he marches you around the room. You seem entirely oblivious to the stares that the pair of you are beginning to attract from some of the guests. Some of them appear to be whispering amongst themselves, but Unknown isn’t too torn up about it— after all, once they're saved, they won't have very much to say about what you and he are doing. “Oh,” you nod in agreement, despite the fact that you clearly have no idea what you’re agreeing to— adorable. “Alright.”
Unknown offers you a menacing grin. He just can't help it— his plan couldn't have worked out better. “Thank you for your cooperation,” he sneers, pulling you close. You’re too busy looking at him to notice the chaos building around you as the guests begin to notice that the doors won’t open and the punch smells strange. “Things are going to get so much better from now on.”
#Am I confident in my ability to write something every day for a whole month? Yes of course#Am I confident in my ability to edit and post something every day for a whole month? Considering I'm already behind on the second day?#No I am not#But we'll see#I want to get better at answering prompts#MM_mystictober2023#mystic messenger#mystic messenger drabble
17 notes
·
View notes
Text
Fwd: Research Technician Job: UConnecticut.ResTechAnimalCare
Begin forwarded message:
> From: [email protected]
> Subject: Research Technician Job: UConnecticut.ResTechAnimalCare
> Date: 6 September 2024 at 06:47:34 BST
> To: [email protected]
>
>
> The University of Connecticut is searching for a full-time lab research
> technician, to work in Dr. Daniel Bolnick’s lab group in the Department
> of Ecology and Evolutionary Biology, on the evolutionary genetics of
> fish immunity to tapeworm parasites.
>
> The primary responsibility of the technician will be to run the lab’s
> fish colony of threespine stickleback. Secondary responsibilities include
> assisting with laboratory experiments, and lab management tasks. This
> position is funded by a National Institute of Allergy and Infectious
> Disease (NIAID) grant to map the genetic basis of differences in immunity
> between natural populations of fish, and differences in immune suppression
> between populations of tapeworm parasites.
>
> Tasks: Animal colony management includes feeding fish, aquarium system
> maintenance, monitoring fish health, record keeping, and breeding lab
> animals. The technician will also supervise and coordinate other lab
> members who contribute fish care help. Secondary responsibilities
> related to the fish colony will be to collaborate with lab members
> doing laboratory experiments (e.g., vaccination assays) and associated
> laboratory work. In addition the technician will help with general lab
> management including purchasing lab supplies for lab members, ensuring
> safety compliance, and helping to keep the lab organized.
>
> Minimum Qualifications: Applicants must be have an undergraduate degree
> (BSc or BA) in biology or a related field. They must be organized and
> reliable and have the ability to carry out independent laboratory research
> and fish care protocols after initial training. Previous educational
> experience and work records should demonstrate a good work ethic,
> organizational ability, and interest in scientific research.
>
> Preferred Qualifications: Experience with animal care is strongly
> preferred. Prior experience with care of fish or other aquatic organisms
> is especially valuable. Some prior experience with laboratory research
> such as (but not limited to) molecular genetics, immunology, or cell
> biology, is helpful but not required.
>
> Start date and duration: The position is available to begin as early
> as September 16, and we would prefer candidates who could begin before
> October 1. The position will begin with a one year appointment subject
> to renewal for up to four years. The position might be extended for
> additional years beyond four, if additional grants are funded.
>
> Salary is expected to be between $38,000-$45,000 per year depending
> on qualifications.
>
> Applicants should electronically submit a single pdf file containing the
> following in order:
>
> 1. Cover letter (1 – 2 pages), including summary of relevant
> job experience, research experience, career goals, and how
> this position fits your career plans.
>
> 2. CV
>
> 3. List of two (or three?) references, with contact information
> (email, telephone and mailing address)
>
> We will request letters directly from these references, after identifying
> top candidates.
>
> The application pdf file should be emailed to Dr. Daniel Bolnick
> ([email protected]). Include the subject line “Fish Care
> Technician Application:
2 notes
·
View notes
Note
Hi! I saw your insurance call and am in awe! Also looking for advice, but if you don't have the spoons feel free to ignore! I recently got my fallopian tubes removed and since my insurance is ACA-compliant they have to cover it 100% but they don't want to. I've called multiple times, sent a written complaint I'm waiting to hear back from, but do you have any advice on how to deal with it?
As a former insurance lackey, yes I might be able to place some stones here! Disclaimer as always, this isn't legal or medical advice since I'm not your rep, blah blah. Okay!
So, few things. There are definitely differences between "don't want to cover" and "refuse to cover." Now, since you mentioned they are ACA-compliant, then they are most likely refusing to cover and it COULD be for a variety of reasons.
1) They determined the procedue was not medically necessary.
2) Your doctor/hospital/someone in billing somewhere coded the procedure wrong on the claim, thus allowing the "must cover" to "doesn't need to cover."
3) Someone failed a step in the approval and/or pre-approval process which allowed insurance to deny out of hand.
4) Whoever processed the claim done fucked up and rejected it due to human error.
Now, in 3 out of 4 scenarios, the solution is the same. Filing a compliant does sweet fuck-all. Filing an APPEAL forces them to respond, usually by reevaluating or at least resubmitting the claim internally.
HOWEVER, if the procedure was coded wrong (which doctors and admins at hospitals do all the ding dong day), then you need to speak to the billing and coding to get the hospital or doctor to resubmit the claim wirh the proper codes that will trigger acceptance of the claim for ACA-compliance.
If the claim was rejected out of clinician review at the insurance company as being medically unnecessary or "elective" NOW you need to call the doctor who ordered the procedure, and have them call your insurance for a peer to peer review of the case. That can overturn the rejection because WOW doctors don't like being told by someone who hasn't even looked at your charts, that they're wrong. And they'll fight about it.
And if a paperwork error like improper coding, not getting the necessary pre-approvals, etc. is the issue, then you can absolutely contact your providers and get that fixed and get copies of all pre-approvals plus your records of the medical necessity to file a formal appeal with your insurance if they're gonna be particularly stubborn.
I know this sounds like a lot and a pain in the ass (it is) but an appeal form can usually be found on your insurer's website (if they're a bigger one. Smaller ones you might have to call or email for the form) and are straightforward. But doing that part, even if you don't have all the backing evidence you need yet, is IMPERATIVE to do within whatever timeframe your insurer allows for appeals. There is ALWAYS a time limit, and filing in a timely manner also hits the pause button on them trying to collect payment until a decision is rendered. Ideally. Not saying some insurers aren't super shitty about harassing you for payment regardless. But they SHOULDN'T with an active appeal.
Since I don't know specifically what happened with your claim (and please don't tell me if you do know, as I am a stranger on the internet and you should protect your PPI and HIPPA info as much as possible), I can't really point you in a solid direction, but a good first step is seeing how the procedure was coded and if a coding error is the issue first. That's easiest to fix if your care team doesn't suck at paperwork because they will get everything redone and resubmitted for you.
I hope this helps and isn't super confusing and that you recover well and stay as healthy as possible!
12 notes
·
View notes
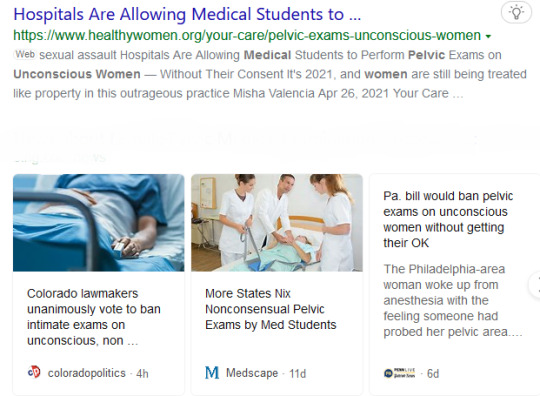
Note
I don't know if this is a news story you'd be interested in but there's a girl on tiktok who found out that during a call with a law professor about a pelvic exam performed on her without her consent the professor had her on speaker phone at her hair dresser. The girl had detailed her medical issues, previous sexual assault, and how she could tell a pelvic exam was performed even though she was under anesthesia and at the beginning of the call was assured everything was between the 4 people who she knew were on the call. She found out she was on speaker because the hair dresser asked her a question regarding it. The professor is on paid leave currently
https://www.news-gazette.com/news/local/university-illinois/ui-legal-scholar-on-paid-leave-over-alleged-mishandling-of-private-phone-call/article_b54fb4bb-acda-5e63-8c9d-ff3b8842b9da.html
I'm interested in most news stories, just can only run so many.
Female law professor even, huh that'll throw a wrench in people blaming evil men which I was anticipating.
This is about a month old too, may be a update for me to find as well.
This is not one I'm going to be able to not editorialize I see.
URBANA — The University of Illinois Ethics and Compliance Office is investigating a claim made against one of its prominent legal scholars — that she mishandled a call under the promise of privacy.
Robin Fretwell Wilson, director of the UI System’s Institute of Government and Public Affairs who holds a tenured appointment in the College of Law on the Urbana campus, is currently on paid administrative leave, UI Associate Chancellor for Public Affairs Robin Kaler said Monday.
“We can’t comment on specific personnel issues,” Kaler said in a written statement to The News-Gazette. “We take very seriously any reports of behavior that might violate the university’s policies or employment expectations related to professional conduct, ethics, research compliance or other matters.”
The allegations came forward from a now widely viewed TikTok post on the account of @bonniedoes, an artist and disability-rights advocate with more than 200,000 followers. The woman behind the account said she has not divulged her full name — on social media or to the university — due to a previous unrelated case of harassment. She has no affiliation with the UI.
Attempts to reach Wilson were unsuccessful.
According to emails shared with The News-Gazette, members of Wilson’s team affiliated with the UI’s Epstein Health Law and Policy Program, a legal research program, reached out to the woman last month after she shared a story on her social-media platform detailing an unauthorized pelvic exam that was performed on her while she was unconscious during an operation at a teaching hospital outside of Illinois.
The practice, sometimes done solely for medical students’ education and not for the benefit of the patient, is highly controversial and currently banned in 21 states, including Illinois. Since January 2019, Wilson and the Epstein Health Law and Policy Program have assisted with legislative efforts to require hospitals to obtain informed consent from patients before conducting invasive medical exams.
I appreciate that some folks are wording this in what I consider a correct way
non consensual is the correct term, it is for a legitimate medical purpose so sexual assault may be a reach, from a linguistic standpoint at least, I know that's what I'd call it tho.

Snopes piece is old obviously
Wilson and her colleagues did not act as lawyers for the woman, or being consulted for legal advice. According to email correspondences, they wanted to understand how TikTok could be used to help speed up this legislative process.
The woman said she agreed to talk, with the understanding that Wilson and three other members of the research team would be the only ones listening in.
But while she was sharing the intimate details of what happened to her, she said later on her TikTok post, another voice chimed in with a question. The voice, she said, came from Wilson’s hairdresser, who was listening to the conversation while the professor had the call on speakerphone.
“I was stunned and didn’t know what to say,” the woman told the News-Gazette on Monday. “I was not at all prepared to handle that. I wanted to just hang up immediately.”
After the conversation ended, the woman emailed the team, calling Wilson’s choice to put the call on speaker “extremely inappropriate and tone deaf.”
“We were having a discussion about the trust between a patient and doctor being violated, while, yet again, my trust being broken by someone who tells me they are here to help,” she wrote in an email.
One of Wilson's colleagues replied to the woman that she was “not aware” Wilson was going to be in a public place during the call.
Wilson later replied in an email, “I owe you an apology since my schedule slipped, but I should have set that out front. Happy to call you privately regarding this.”
The woman has since spoken openly about her call with Wilson on her TikTok page, and brought forward her accusations to the UI System and the UI College of Law.
“Immediately upon learning of this matter, the University Ethics Officer communicated with the individual who posted their concerns regarding their interaction to obtain additional information,” Kaler said Monday. “There have been several other communications directly with that individual since the initial one. We care deeply about any individual who has been affected by inappropriate behavior.
“We believe that survivors of sexual misconduct should always be treated with empathy and dignity and in a manner that fully respects their wishes for privacy and confidentiality.”
Wilson is a well-known scholar in family law, bioethics and religious liberty. She was invited to the White House in December for the signing of the Respect for Marriage Act because of her role in helping to craft the legislation.
The woman said she does not plan to file suit against Wilson.
“I had a concern that she is not treating this issue with the respect and care it deserves, and not treating the victims with the respect and care they deserve,” she said. “The people in that hair salon, under no circumstances did they need to hear that information.”
___________________
There is absolutely everything wrong with this, good grief. Not seeing any updates either.
What a mess, that procedure needs to be illegal without consent, one of those things there's no law about because nobody though it would be needed I guess.
15 notes
·
View notes
Text
AI Calendarfly Review: The Revolutionary Appointment Scheduling AI App

AI Calendarfly Review: Features
Automated scheduling: Enables users to share their availability and allow others to book appointments or meetings at their convenience.
Integrations: It integrates with popular calendar platforms like Google Calendar
Customizable availability: Users can set specific availability windows for different types of meetings or events.
Team scheduling: Allows teams to coordinate availability and schedule group meetings.
Reminder notifications: Sends reminders to both organisers and participants before scheduled meetings.
Time zone detection: Automatically detects and adjusts for different time zones to avoid scheduling conflicts.
Customizable booking pages: Users can customise the appearance and content of their booking pages.
Analytics and reporting: Provides insights into scheduling trends and activity.
Group event scheduling: Enables users to set up and schedule group events or workshops.
Multiple meeting types: Supports scheduling of one-on-one meetings, round-robin meetings, and more.
Team scheduling: Collaborate with team members to coordinate availability and schedule group meetings.
Customizable reminders: Set up reminders to reduce no-shows and ensure all participants are informed.
Buffer time: Add buffer time between meetings to avoid back-to-back scheduling.
Round-robin scheduling: Distribute meeting requests across team members automatically.
Multiple event types: Create different types of events with varying durations and settings.
Web conferencing integrations: Seamlessly connect with virtual meeting platforms like Zoom, Google Meet, and Microsoft Teams.
Embeddable scheduling links: Easily embed scheduling links on websites or email signatures for convenient access.
Multi-language support: Provides support for multiple languages to cater to a diverse user base.
Advanced customization: Customise branding, colours, and logos to align with your brand identity.
GDPR compliance: Ensures data protection and compliance with privacy regulations.
Multiple time zone support: Display availability in different time zones for seamless scheduling across regions.
Reporting and analytics: Track and analyse scheduling data to gain insights and optimise scheduling efficiency.
Booking page customization: Customise booking pages with images, descriptions, and branding elements.
Group event scheduling: Facilitates scheduling group events with multiple participants at once.
User roles and permissions: Assign different roles and permissions to team members for effective collaboration.
Email notifications: Receive notifications for new booking requests, rescheduled meetings, and cancellations.
Recurring event support: Set up recurring meetings with options for daily, weekly, or custom frequency.
Time slot limits: Set limits on the number of bookings per time slot to manage availability.
Bulk scheduling: Schedule multiple meetings or events simultaneously for efficiency.
Availability preferences: Customise availability settings based on preferred days, times, and durations.
Participant questions: Collect important information from participants by adding custom questions to booking forms.
Team calendar views: View team members' availability and schedules in a consolidated calendar view.
Custom appointment types: Create unique appointment types with specific settings and requirements.
Event buffers: Automatically add buffer time before and after meetings to allow for preparation and follow-up.
Calendar blocking: Block off specific time slots for personal appointments or tasks.
Meeting links and details: Share meeting links and details automatically with participants upon confirmation.
Custom email notifications: Customise email notifications sent to participants with personalised messages.
User-friendly interface: Intuitive and user-friendly interface for easy navigation and scheduling.
Accessibility features: Provides accessible features for users with disabilities to ensure inclusivity.
Guest limits: Control the number of guests or participants allowed to book a meeting.
Profile management: Manage user profiles, settings, and preferences for personalised scheduling experiences.
Interactive dashboard: Access a dashboard with an overview of upcoming meetings, bookings, and analytics.
No Technical Skills Required
24*7 Premium Support To Solve All Your Issues On-Time
Commercial Licence Included
>>>>>>>>GET MORE INFO
#digital marketing#AI Calendarfly Review#AI Calendarfly#Coaching#Consulting#Make Money Online#Affiliate Marketing
3 notes
·
View notes
Note
Okay but it’s important to me to say that you absolutely have a right to be and write in the Star Wars fandom regardless of how much of the source material you have consumed
gatekeeping in fandom is the worst. The absolute worst. in the same way that we can love and appreciate fic written before a series finished even years after it’s no longer canon compliant, we can love and appreciate fic by someone who hasn’t consumed the entire source material. how can we say someone isn’t able to write fic until they’ve finished it?? Even if they never finish it?? Especially in something so extensive as Star Wars.
Star Wars canon is a hodge podge anyway—setting aside the Disney reboot, even the extended universe was a mess of retconning. The movies themselves were a mess of retconning. The beautiful and wonderful thing about having so much material is that you can cherry pick what you like. DLB is canon to the original 6 movies, but even if it wasn’t it’s still a fucking amazing story.
You don’t have to watch the other Star Wars stuff to belong here. You don’t even have to like the original Star Wars stuff to belong here. The fact that you have a story to tell with these characters is enough of a membership card.
Can people want to see their favorites show up? Can they be disappointed/upset at the fact that your versions of them aren’t the canon versions? Sure, but that’s their feelings. You’ve been more than clear enough that you’re working from the movies, and we’re fucking lucky to have you here, writing, in exactly the way you do.
There’s a space in this fandom for the uber nerds who have read and watched every last piece of Star Wars media and bring all those details together in ingenious ways. There’s also a space in this fandom for people who have read or watched (1) Star Wars thing and caught the bug. And there’s a space in this fandom for everyone in between.
(…that was more ranty than I intended but I cannot express to you how much my heart jolts every time I see a notification email for you in my inbox. Sometimes a new DLB chapter turns my day around. You are a gift to this fandom.)
Thank you so much! (*^_^*) I really do appreciate the support.
And I have to say that overall, I've been treated very well by people engaging with me and with DLB. My worries are often disproportionate to reality, and I knew when I started posting Like Fire that getting at least some...disgruntled(?) feedback was just guaranteed and I needed to develop a thicker skin for those moments because when you engage online, people saying something that can hurt your feelings is just...inevitable.
Regardless of canon compliance, just based on subscription numbers and how many enthusiastic comments I get per chapter, I know the reception of DLB is just overall positive for those who choose to engage with it.
And I do want to engage back with people reading my story, and even share my thoughts and feelings on why some aspects of canon make it in or don't. I'm just a worrier by nature, so I'm often careful and reticent preemptively, especially on the internet. I'm getting more comfortable in this space and I hope I can keep engaging more in spite of my old habits. But I still definitely retreat like a snail with a poked eye back into my little shell when people get...enthusiastic about correcting me. Those infrequent times it does happen.
(Really though, I am so, so glad when people talk about how DLB just brings them so much joy by existing. Like, why else do we create art but to create feelings between otherwise unreachable souls that want to harmonize so badly? What greater joy is there than to reach out and feel someone reach back?)
45 notes
·
View notes
Text
A bill introduced by senators Dick Durbin and Mike Lee to reauthorize the Section 702 surveillance program is the fifth introduced in the US Congress this winter. The authority is threatening to expire in a month, disrupting a global wiretapping program said to inform a third of articles in the President’s Daily Briefing—a morning “tour d’horizon” of US spies’ top concerns.
But the stakes aren't exactly so clear. With or without Congress, the Biden administration is seeking court approval to extend the 702 program into 2025. From the moment US representative Mike Johnson assumed the House speakership, he’s been unable to orchestrate a vote on the program. Outgunned most recently by Mike Turner, the chairman of the House Intelligence Committee, Johnson was forced to kill a vote after a month of negotiations.
This, even though Congress can essentially agree on one thing if nothing else: that the 702 program is vital to the national defense and that it can’t be allowed to expire. Johnson has, once again, vowed to hold a vote on the matter, this time after Easter. And historically, this is where things have begun to fall apart.
The biggest hurdle to reauthorizing the program is a dispute between lawmakers over whether the government should get search warrants before looking up Americans using 702, a massive wiretap database full of millions of email, voice, and text conversations intercepted by spies.
The Durbin-Lee bill contains tweaks designed, its authors say, to meet the Biden administration halfway. While most bills up to now have wrestled over the title of “reform,” Durbin’s has set its sights on being the first to bring compromise.
Unlike past bills, the Security and Freedom Enhancement (SAFE) Act does not require the FBI to get a warrant merely to search the 702 database for US communications. Only if the search finds results is a warrant needed, and only if investigators intend to read the files.
Without going to court, investigators could still learn whether the communications they’re after exist, whether the person they’re investigators spoke with any foreigners under surveillance, and know when those conversations took place. And because it’s generally trivial for law enforcement to obtain these types of records anyway, it's a compromise that most reformers are likely to live with.
The tweak will add to the difficulty the FBI is having convincing lawmakers that warrants will hinder investigations or destroy the program altogether. “This narrow warrant requirement is carefully crafted to ensure that it is feasible to implement,” Durbin says, “and sufficiently flexible to accommodate legitimate security needs.”
“There is little doubt that Section 702 is a valuable national security tool,” adds Durbin, but the program sweeps up “massive amounts of Americans’ communications.”
“Even after implementing compliance measures, the FBI still conducted more than 200,000 warrantless searches of Americans’ communications in just one year—more than 500 warrantless searches per day,” he says.
The SAFE Act contains the same menu of emergency exceptions that members of the House Judiciary Committee offered up in previously introduced legislation. The exceptions would allow the FBI to ignore the warrant requirements during emergencies, such as people faced with imminent harm or death. The bureau can search the database at will using “known threat signatures” linked to cybercrimes as well, a carve-out designed to help the FBI dodge legal red tape while mitigating harm from malicious software.
While the possibility looms that the Foreign Intelligence Surveillance Court (FISC) will approve the Biden administration’s request, extending the 702 program into 2025 on its own, it's an outcome that all sides seem eager to avoid—improvising a way to prolong a hotly debated surveillance program being a bad look for nearly everyone involved.
One of the program’s core tenets, according to a “fact sheet” distributed by the Office of the Director of National Intelligence (ODNI) this year, reflects the bargain it strikes between the government and the public: US spies are to receive an “invaluable source of intelligence on foreigners located outside the US.” Americans get in return “robust civil liberties and privacy safeguards, overseen by all three branches of government.”
If Congress had meant, in 2018, to reauthorize the 702 program for seven years rather than six, its members wouldn’t have found out last week. Allowing the program to carry on without a mandate from Congress—with nothing but a green light from a secret court—is a legacy of dysfunction that most members aren’t eager to carry, and one that the intelligence community may also come to resent, as people start to question the integrity of its oversight.
“Although the legislation does not include every reform we have called for, it is a thoughtful compromise that would meaningfully restore privacy in the United States,” says Sean Vitka, policy director at Demand Progress, a digital rights nonprofit.
“An overwhelming number of Americans from across the political spectrum want Congress to seize this once-in-a-generation moment and get this done.”
2 notes
·
View notes
Text
In the United States, call center companies play a pivotal role in providing customer support, sales assistance, technical troubleshooting, and various other services for businesses across a multitude of industries. These companies employ thousands of individuals nationwide and operate through various models, including in-house, outsourced, and virtual call centers. Let's delve into the landscape of call center companies in the USA.
1. Overview of the Call Center Industry:
The call center industry in the USA has witnessed significant growth over the years, driven by the increasing demand for cost-effective customer service solutions and the globalization of businesses. Today, call centers cater to diverse sectors such as telecommunications, banking and finance, healthcare, retail, technology, and e-commerce.
2. Major Players:
Several major call center companies dominate the industry, including:
Teleperformance: One of the largest call center companies globally, Teleperformance operates numerous centers across the USA, offering multilingual customer support, technical assistance, and sales services.
Concentrix: Concentrix is another key player, known for its innovative customer engagement solutions. It provides a wide range of services, including customer care, technical support, and digital marketing services.
Alorica: Alorica specializes in customer experience outsourcing solutions, serving clients in various industries. It offers services such as customer support, sales, and back-office support.
Sitel Group: Sitel Group is renowned for its customer experience management solutions. With a global presence, Sitel operates call centers in multiple locations across the USA, providing tailored customer support services.
TTEC: Formerly known as TeleTech, TTEC offers customer experience solutions, digital services, and technology-enabled customer care. It focuses on delivering personalized customer interactions through its contact centers.
3. Industry Trends:
The call center industry is continually evolving, driven by technological advancements and changing consumer preferences. Some notable trends include:
Digital Transformation: Call centers are increasingly integrating digital channels such as chat, email, and social media to enhance customer engagement and support omnichannel experiences.
AI and Automation: Automation technologies, including artificial intelligence (AI) and chatbots, are being adopted to streamline processes, improve efficiency, and provide faster resolutions to customer queries.
Remote Workforce: The COVID-19 pandemic accelerated the shift towards remote work in the call center industry. Many companies have embraced remote workforce models, allowing agents to work from home while maintaining productivity and efficiency.
Data Analytics: Call centers are leveraging data analytics tools to gain insights into customer behavior, preferences, and trends. This data-driven approach enables them to personalize interactions and optimize service delivery.
4. Challenges and Opportunities:
Despite its growth, the call center industry faces several challenges, including:
Staffing Issues: Recruiting and retaining skilled agents remains a challenge for many call center companies, particularly amid competition for talent and high turnover rates.
Security Concerns: With the increasing prevalence of cyber threats, call centers must prioritize data security and compliance to protect sensitive customer information.
However, the industry also presents numerous opportunities for growth and innovation:
Expansion of Services: Call center companies can diversify their service offerings to meet the evolving needs of clients, such as expanding into digital customer engagement, analytics, and consulting services.
Focus on Customer Experience: By prioritizing customer experience and investing in training and technology, call centers can differentiate themselves and gain a competitive edge in the market.
Globalization: With advancements in technology and communication infrastructure, call center companies can explore opportunities for global expansion and tap into new markets.
5. Future Outlook:
Looking ahead, the call center industry is poised for further growth and transformation. As businesses increasingly prioritize customer-centric strategies, call center companies will play a crucial role in delivering exceptional customer experiences and driving business success.
In conclusion, call center companies in the USA form a vital component of the customer service ecosystem, serving a wide range of industries and helping businesses enhance customer satisfaction and loyalty. With ongoing technological innovations and evolving customer expectations, the industry is poised for continued growth and innovation in the years to come.
2 notes
·
View notes
Text
How to Start a Grocery Delivery Business

In an instant where convenience is important and online services are influencing consumer habits, starting a grocery delivery business can be a lucrative venture. As the demand for efficient and time-saving solutions continues to rise, this guide will take you through the essential steps to launch and scale your grocery delivery service.
Research on markets
The foundation of a successful grocery delivery business starts with complete market research. Identify your target audience, analyze local competitors, and understand the unique needs of your community. Consider factors such as demographics, shopping behaviors, and existing gaps in grocery delivery services.
Construct a Business Plan
A business plan is an extensive document that describes the objectives, tactics, and day-to-day activities of a company. A well-researched business plan will serve as your roadmap, outlining your goals, strategies, and financial projections.
Create a robust business model
Choose a business model that aligns with your goals and resources. You can opt for a partnership with local grocery stores, source products independently, or adopt a hybrid approach. Evaluate the pros and cons of each model, considering factors such as costs, logistics, and customer preferences.
Build a user-friendly app or website.
Invest in a user-friendly and intuitive platform to facilitate seamless interactions between customers, your service, and partnered grocery stores. Develop a mobile app or website that allows users to browse products easily, create shopping lists, and place orders with a few taps or clicks. Ensure secure payment gateways and implement features like order tracking and notifications to enhance the overall user experience. If you’re planning to develop a web or app, know the costs of developing a grocery delivery app.
Establish strong supplier relationships.
Develop solid partnerships with local grocery stores or wholesalers to ensure a consistent and diverse product supply. Negotiate pricing, delivery schedules, and terms to build a mutually beneficial relationship. Reliable suppliers are crucial to maintaining a well-stocked inventory and meeting customer expectations.
Implement Efficient Logistics and Delivery Systems:
Efficient logistics and reliable delivery systems are the backbone of any successful grocery delivery business. Develop a streamlined process for order fulfillment, consider partnering with third-party delivery services if needed, and optimize delivery routes for time and cost efficiency. Communicate delivery times and ensure your delivery team is well-trained in customer service and hygiene practices.
Emphasize Quality Customer Service:
Excellent customer service is a key differentiator in the competitive grocery delivery landscape. Provide responsive customer support through various channels, such as live chat, email, or phone. Address customer queries, concerns, and feedback promptly to build trust and loyalty. A positive customer experience is likely to result in repeat business and positive word-of-mouth referrals.
Implement marketing and promotion strategies:
Create awareness for your grocery delivery business through targeted marketing and promotions. Utilize social media platforms, local advertising, and partnerships with influencers to reach a wider audience. Offer promotions, discounts, and loyalty programs to encourage both new and repeat customers.
Ensure regulatory compliance.
Understand and comply with local regulations regarding food handling, safety, and business operations. Obtain any necessary licenses or permits to operate legally. Compliance with industry standards not only safeguards your business but also instills confidence in customers regarding the safety and legitimacy of your service.
Optimize Technology for Analytics:
Make use of technology to gather and analyze data on customer preferences, purchasing patterns, and market trends. Use this information to make informed decisions, refine your product offerings, and customize marketing strategies. A data-driven approach can significantly contribute to the growth and sustainability of your grocery delivery business.
Scale and innovate:
As your business gains traction, explore opportunities for expansion and innovation. Consider adding new features to your app, expanding your delivery area, or introducing subscription models. Stay abreast of industry trends and technological advancements to remain competitive in the ever-evolving grocery delivery landscape.
Conclusion:
Starting a grocery delivery business requires careful planning, dedication, and a customer-focused approach. Grocery delivery services are becoming more and more in demand, and you can meet this demand by developing a streamlined and efficient service, applying technology, and understanding your market. Follow these steps, adapt to changing consumer preferences, and watch your grocery delivery business thrive in an era where convenience is king.
2 notes
·
View notes
Text
Customs Brokerage Strategies: Mitigating Risks in Global Trade
A customs brokerage firm is significant in global trade and goes beyond intermediaries. It is the one that helps exporters and importers manage the intricate field of international trading regulations and procedures.
But what are all the possible international trade risks, and what are the approaches customs brokerage firms take to overcome them?
Navigating Regulatory Challenges
Staying compliant with all the customs laws is vital for importers and exporters to prevent costly penalties and other consequences. Compliance ensures all goods are imported, exported, and progressed correctly.
Customs brokers ensure adherence to diverse international trade laws by meeting all certain documentation necessities. It includes:
Proper labeling of goods,
Accurately measuring all products,
Paying the right amount of taxes and duties, and
Contributing all the precise customs credentials for access to other countries.
Technology Integration for Risk Management
The continuous development of technologies has impacted the worldwide business industry, even the global customs brokerage sector. These technological developments have helped these firms adapt their strategies to the ever-changing landscapes of the field. It has mitigated risks in the importing and exporting process, such as:
Securing global trade by providing tamper-resistant record dealings,
Enhanced customs procedure efficiency, easing the goods’ flow across borders,
Allowed customs brokers to evaluate massive amounts of data and determine patterns to make wise decisions and
Enabled potent monitoring of shipments and cargo conditions and provided real-time updates to clients and customs brokers.
Effective Communication
One of the key factors in mitigating risks in customs brokerage is how obtainable communication is. Clear communication is highly vital between customs brokers, relevant authorities, and clients. Hence, here are some of the effective strategies these individuals should do for transparent communication in global trade scenarios:
Showing vulnerability to build trust,
Utilizing technology to give one messaging platform,
Steady in expressing a well-balanced empathy and privacy, respectively,
Clear on letting their clients know about their values by providing stable communication and
Avoid confusing terminologies and use communicative words that are easy to understand.
Mitigate Risks with Excelsior!
Strengthening risk mitigation is also effective in collaboration with the right shipping company, which could help you find the right government agencies and other stakeholders, like Excelsior.
Excelsior, a well-known freight forwarder international, has been in the shipping industry for fifteen years. It has marked its name in the market by giving the best and most honest service to our clients. Hence, clients are at peace when they book services for Excelsior to get all their shipments to arrive safely at their proper destination.
Engage more with us by calling us at (+632) 8525-9775 or email us at [email protected].
#customs brokerage firm#logistics company in the philippines#licensed customs broker#customs brokerage in manila
2 notes
·
View notes
Text
SOC Success Stories: Lessons from Cybersecurity Frontlines
Introduction to SOC (Security Operations Center)
Welcome to the thrilling world of cybersecurity! In an era where digital threats loom large, organizations are arming themselves with powerful tools and strategies to safeguard their sensitive information. One such weapon in their arsenal is the Security Operations Center (SOC), a formidable force that stands as a beacon of protection against cyber attacks.
But what exactly is SOC? Well, SOC stands for Security Operations Center - a centralized unit within an organization tasked with monitoring, detecting, and responding to security incidents. Think of it as the nerve center, where skilled analysts work tirelessly round the clock to keep your data safe from malicious actors.
In this blog post, we will explore the importance of having a SOC in today's digitized landscape. We'll dive into real-life success stories that highlight how these teams have thwarted sophisticated attacks and saved countless organizations from potential devastation. So buckle up and get ready for some edge-of-your-seat tales from the cybersecurity frontlines!
Importance of a SOC for Organizations
In today's digital world, the importance of cybersecurity cannot be overstated. With cyber threats becoming increasingly sophisticated and widespread, organizations need to have robust measures in place to protect their sensitive data and systems. This is where a Security Operations Center (SOC) comes into play.
A SOC is a dedicated team within an organization that focuses on monitoring, detecting, analyzing, and responding to security incidents. It serves as the central nervous system for an organization's cybersecurity efforts. The primary role of a SOC is to keep a constant watch over the network infrastructure, applications, and endpoints to identify any potential security breaches or suspicious activities.
By having a SOC in place, organizations can proactively defend against cyber attacks rather than being caught off guard and reactive when an incident occurs. A well-functioning SOC helps minimize downtime by swiftly identifying and mitigating threats before they can cause significant damage.
Moreover, a SOC plays a crucial role in ensuring compliance with industry regulations such as GDPR or PCI DSS requirements. By monitoring network traffic and conducting regular vulnerability assessments, the SOC helps organizations meet regulatory standards while maintaining data integrity and confidentiality.
Another key aspect of the importance of a SOC lies in its ability to provide valuable insights through threat intelligence analysis. By continuously collecting information about emerging threats from various sources like dark web monitoring or threat feeds from vendors, the SOC can stay one step ahead of potential attackers.
Additionally, having an internal team responsible for managing cybersecurity allows for better coordination between different departments within an organization. The communication channels established within the SOC enable faster response times during incidents and facilitate collaboration among IT teams across different locations or business units.
Real-life Examples of SOC Success Stories
1. Foiling a Sophisticated Phishing Attack
One success story involves a Security Operations Center (SOC) team that successfully prevented a sophisticated phishing attack on a large financial institution. The SOC analysts detected anomalous network traffic and quickly identified the malicious email campaign targeting employees. By promptly alerting the organization's IT department, they were able to take immediate action to block the malicious links and prevent potential data breaches.
2. Unraveling an Insider Threat
In another instance, a manufacturing company faced an insider threat from one of its disgruntled employees who intended to sabotage critical systems. Through continuous monitoring and analysis of user behavior within the network, the SOC team noticed unusual activity associated with this employee's account. They swiftly intervened, disabling the account before any damage could occur.
3. Swift Response to Ransomware Attack
A healthcare provider was hit by a ransomware attack that encrypted vital patient records across their network infrastructure. Thanks to their well-prepared SOC team, they were able to respond swiftly and effectively mitigate the impact of the attack. The SOC analysts isolated affected systems, restored data from secure backups, and implemented additional security measures to prevent future incidents.
These real-life examples highlight how Security Operations Centers play a crucial role in safeguarding organizations against various cyber threats by employing proactive monitoring techniques, advanced analytics tools, and skilled personnel capable of rapid response when incidents occur.
Collaboration and Communication within the SOC
Collaboration and communication are the lifeblood of a successful Security Operations Center (SOC). In an environment where threats can evolve rapidly, SOC teams must work together seamlessly to detect, respond to, and mitigate cyber incidents.
Within the SOC, analysts from different specialties come together to form a cohesive team. This diversity of skills and perspectives allows them to tackle complex security challenges from various angles. Whether it's network monitoring, threat intelligence analysis, or incident response, each member plays a vital role in safeguarding the organization's assets.
Effective collaboration within the SOC involves constant information sharing. Analysts must communicate findings, share insights, and update their colleagues on ongoing investigations. This real-time exchange of knowledge helps identify patterns and trends that might otherwise go unnoticed.
Furthermore, collaboration extends beyond just internal teamwork within the SOC. It also entails close cooperation with other departments such as IT support or legal teams. By fostering strong relationships with these stakeholders across the organization, SOC analysts can gain valuable context about potential risks and vulnerabilities specific to different business units.
Communication channels within the SOC should be streamlined yet flexible. Regular meetings or huddles provide opportunities for analysts to discuss emerging threats or brainstorm solutions collectively. Additionally, technology tools like chat platforms enable instant messaging for quick updates during critical incidents.
Collaboration and communication lie at the heart of every successful SOC operation. By working closely together and sharing information effectively both internally and externally with other departments in an agile manner; organizations can enhance their overall cybersecurity posture while staying ahead of ever-evolving threats.
Conclusion
In today's ever-evolving digital landscape, organizations face constant threats to their cybersecurity. To protect themselves from these risks, many organizations have implemented Security Operations Centers (SOCs). These centralized hubs of expertise and technology play a vital role in defending against cyber attacks and ensuring the overall security posture of an organization.
Throughout this article, we have explored the importance of SOC for organizations and shared real-life success stories that highlight the effectiveness of these centers. From preventing major data breaches to detecting advanced persistent threats, SOCs have proven time and again their value in safeguarding sensitive information.
One key factor contributing to the success of SOCs is collaboration and communication within the team. The seamless exchange of information between analysts, incident responders, threat intelligence experts, and other stakeholders enables faster response times and more effective incident handling. This teamwork ensures that all relevant insights are considered when making critical decisions during a security incident.
While there is no one-size-fits-all approach to building a successful SOC, these success stories provide valuable insights into what works best in different scenarios. Organizations can learn from these examples by adopting similar strategies such as leveraging automation tools, investing in continuous training for SOC analysts, conducting regular threat-hunting exercises, and fostering strong partnerships with external entities like law enforcement agencies or industry peers.
2 notes
·
View notes