#deployment firewall
Explore tagged Tumblr posts
Text

Bad code can prevent you from shipping mission critical features. This blog explains how OpsMx’s Deployment Firewall prevents shipping of bad code to production.
0 notes
Text
Overcoming Common Challenges in SharePoint Server Installation
SharePoint Server, a powerful collaboration and content management platform, provides organizations with robust functionalities. However, the installation process can present various challenges that may hinder a seamless deployment. In this article, we will explore common issues faced during SharePoint Server installation and provide probable solutions to overcome them. “The tool was unable to…

View On WordPress
#Access Privileges#Application Services Configuration#Central Administration#Collation Settings#Configuration Database#Database Connectivity#Deployment Challenges#Disk Space#Firewall Interference#Hardware Requirements#Installation Issues#Internet Connectivity#Memory Exception#Probable Solutions#Secure Store Service Application#Service Account#SharePoint Prerequisites#SharePoint Search Service#SharePoint Server#SharePoint Timer Service#SQL Server Permissions#Troubleshooting#User Profile Service Application#Windows Features
0 notes
Text
Arknights Spring Festival 2025 PVs
youtube
youtube
New Operators

Surfer, 5* Agent Vanguard
It's sunny out, wanna go for a walk?
Xingzhu, 5* Welfare Abjurer Supporter
The pen is never sharp, but paper falls like it's flying.
Blaze the Igniting Spark, 6* Primal Caster
I'm back! Right then, it's signed with my real name, Gù Zhúhuáng. Oh Doctor, you don't have to call me anything different, you can still call me Blaze.
Yu, 6* Limited Primal Protector Defender
I'm not gonna give it away for free, hehe, but the price is negotiable.
Of all the flavors in the world, the fullness of life is the best them of all.
Operator Outfits Update





4 new additions for the Made by 0011 brand
Almond Platter - Almond
Prairie Pals - Bena
Youthful Journey - Zuo Le (21 OP)
Spring Feast - Shu (21 OP)
Operator Modules Update



Xingzhu being part of the Abjurer Supporter branch immediately gets her module
BLS-X module base effect increases her healing to 100% of her ATK
Earthshaker Guard branch gets 1 module type
Lin, Zuo Le and Chongyue get their second module
PLX-Y module base effect increases Lin's damage the more enemies are in her range (up to +15%)
SBL-Y module base effect allows Zuo Le to survive with 30% HP upon reaching 0 HP for the first time each deployment
FGT-Y module base effect increases Chongyue's ASPD by +10 when he is above 50% HP
Dusk and Eunectes get specialized modules
Dusk gets an Integrated Strategies module
Eunectes gets a Reclamation Algorithm module
Events and Stories

Such is the Joy of Our Reunion, the next installment of the Sui storyline taking place in the culinary city of Bai Zao
Regardless whether you are worried about family matters or matters of national security, when you're at the dinner table all that matters is a pair of chopsticks.
If you're alive, how come you're not eating properly? It's time for dinner. Go wash up and get ready to eat——

Operator Archives update for Yu, Lin, Wanqing and Grain Buds
Misc Stuff


New QoL features
New activity rooms that players can decorate, operators assigned to these rooms can be controlled and moved around the base, also players can use emojis here for fun
The reception room has been expanded and can be decorated with Reception Room exclusive decor items
Dualchips will only take 1 second to make in the Factory
Added dorm rotation locks, operators in the locked slot will not be affected by the dorm rotation button
Added remaining working time display for certain base facilities and a notification option for shift rotations and operators being fully rested in the settings
Performance upgrades for Workshop, Offices, Training Room, Elevators and other facilities
In-game mail players receive can be stamped and stored in the mail folder where players can review them
Added a Module Showroom where players can conveniently view and manage module information


Archetto, Iris and Beanstalk added to Recruitment
Blue Poison's [Shoal Beat] Outfit will be available in the certs shop to players that don't have it
Livestream Stuff
Showcased Yu, a 6* Primal Protector Defender that specializes in inflicting Burn buildup
First talent makes him deal Arts damage and Burn buildup to enemies he blocks and gives him Sanctuary while blocking
Second talent makes Yu recover HP and elemental HP every second when there is at least a certain amount of ally units on the field
Skill 1 passively makes him more likely to be attacked, when active it increases his Max HP & DEF and makes enemies that attack him take Burn buildup
Skill 2 increases his Block Count, ATK & DEF, makes his attacks deal Arts damage, and upon skill activation it immediately deals Arts damage to all enemies in his skill range and teleports all the hit ground enemies to his tile
Skill 3 increases his Max HP, ATK & DEF and makes his second talent apply to all operators, upon skill activation it generates a firewall that spans across the entire battlefield, operator attacks that deal Arts damage against enemies on the opposite side of the firewall will additionally deal Burn buildup based on Yu's ATK, enemy projectiles that hit the firewall have a chance to be nullified
Showcased Blaze the Igniting Spark, a 6* Primal Caster that takes advantage of Burn Burst
First talent activates when Burn Burst triggers on any enemy on the field, deal more Elemental damage to them based on Blaze's ATK and she recovers some HP
Second talent activates when Blaze is defeated, instead of retreating she will instead be knocked down and she gains a large amount of Barrier, she cannot attack or be healed while downed but she recovers HP every second, once fully healed she will revive and Stun all nearby enemies for a few seconds
S1 drops a fire field on the operator with highest Max HP in her range, it deals Arts damage every second and Burn buildup based on the damage dealt by the fire field, lasting for several seconds
S2 changes her range, increases her attack interval, increases her ATK and allows her to attack multiple targets at once, she loses HP with each attack but the enemies she attacks leaves a fire trail, enemies in the fire trail have reduced Movement Speed, receive Arts damage and Burn buildup based on the damage dealt by the fire trail
S3 changes her range, greatly shortens her attack interval, increases her ATK and makes her attacks AoE, if the enemies she hits are under Burn Burst status she deals additional Elemental damage to them, it is an ammo skill that makes her lose HP every second but when Burn Burst triggers on any enemy on the field she gains more ammo, skill can be deactivated manually

Showcased the event mechanic, Fire Stoves powered by chopstick enemies that have hit-based HP, chopsticks will go into one of the 2 stoves on the field depending on their state, enemy chopsticks can be attacked and converted into allied chopsticks and vice versa, when fully charged the allied stove will summon a spirit dragon that deals massive true damage to all enemies in its path
The cost required to spark Nian will be reduced to 200 starting from this event, the cost required to spark Skadi the Corrupting Heart will be reduced to 200 in the CN 6th anniversary event

Announced CC#3 Battleplan Extinguished Sins which is confirmed to have Ep14 enemies and mechanics

IS#3 will gain 3 more difficulty levels up to Surging Waves 18
Starting from SW16 there is a new feature where players can suppress Rejection effects and gain "Genomes" at the end of each battle
At SW17 Rejections will be replaced by Combined Rejections
At SW18, Elite and Leader enemies take -50% Physical and Arts damage for 20s after entering the field, and their ATK is increased by +30%
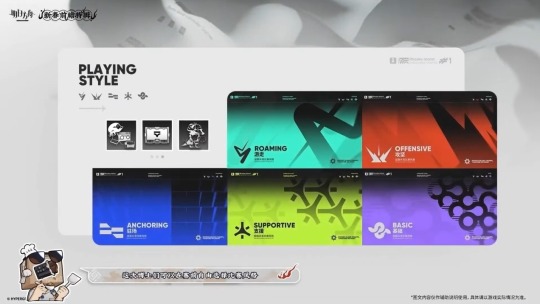




Rhodes Island Icebreaker Games will return with new features as an annual gamemode
Players can select their preferred play style before matches to obtain their preferred buffs and better communicate their gameplay to other players
Players can swap lineups
More levels and difficulties will be added to Regular Events
New balls and enemy units added to Positional Football
New mechanics and boss added to Bastion Defense
Players can take commemorative photos of their units with their teammates after the match
A new outfit for Vermeil and Originium Slug emojis are some of the rewards players can get from IG#1

Showcased the new base update features such as a music player that can change the background music in the base (limited to main menu background themes) and an info board that displays your friends that recently visited


Announced the next story collection event in involving Eblana, Talulah and Amiya
Teased the next event featuring Eblana

Announced Episode 15, the start of Act III of the main story where Rhodes Island returns to Rim Billiton and cliffhangers from Ep14 will be resolved

Announced an in-game event timeline that puts all the main story chapters, intermezzo, side stories and story collection in chronological order
73 notes
·
View notes
Text
A Persistent Lack of Follow Through, Chapter 2: Salvage & Repair

Chapter Links: One, Two, Three
Pairing: Todoroki Shouto x Female Reader
Rating: Mature 18+
Tags: Breaking Up & Making Up, Angst with a Happy Ending, Personal Growth, Drinking, Sexual Content, Non-Explicit Sex, Weddings, Child Abuse, Todoroki Enji's Bad Parenting, Abusive Todorioki Enji, Pining, Shouto is Bad at Feelings, Natural Disasters, Fire, Serious Injuries, Domestic Fluff, Implied Pregnancy
---
Shouto had learned a lot from his Father; how to take a hit, how to pull himself back up, and how to hold a grudge.
But one thing Endeavor could never teach his children was how to be a good partner.
Shouto had to learn that particular skill the hard way.
---
He had spent long, sleepless nights reflecting on the things you had told him; the reasons you left. Every moment of your acquaintance was turned over repeatedly in his head and examined until one devastating conclusion was reached:
"I was a bad boyfriend," Shouto muttered dejectedly, idly picking at the label of the shochu bottle in the middle of the table.
---
A story where Shouto loves, loses, and learns.
Continue reading below, or follow the link to Ao3!

Shouto's deployment lasted far longer than he would have liked. They had managed to suppress the blazes in under a week. Heroes with fire based Quirks set about burning long stretches of untouched vegetation to create firebreaks while ice and water elemental Quirks worked on suppressing and extinguishing blazes that tried to jump the firewalls.
It was exhausting work, but the hard labor and long hours kept him from thinking about his newly single status during the day and ensured that he was too tired to dream after he fell into his cot at night. They had been packing up, ready to return to Japan when the call from his PR team came in.
Animal rescue workers had found a juvenile Koala injured in the blaze, the skin around its left eye seared by a falling branch while it tried to escape to safety. They wanted him to come in and do a photoshoot to raise funds for the wildfire relief fund, the two of them a matching reminder about the lasting damage fire leaves behind.
The original run of promotional materials were wildly successful and Shouto found his return flight pushed back again and again; a never-ending cycle of talk show spots and community appearances with Kodoroki (which had been the winning name in an online poll by a landslide). As much as Shouto disliked being in the center ring of the media circus, the worst part of the entire ordeal was having to call his Father every few days to inform him of his further delays. Endeavour had agreed to watch over Shouto's agency in his absence, and while he was long retired and unable to do any of the field work, his Father was a competent executive and everything was always in good working order upon his return.
The first photoshoot with Kodoroki had been an awkward affair, neither Shouto nor the koala quite sure what to make of each other. But as the weeks dragged on they had become more comfortable and Shouto found himself looking forward to being reunited with his little burned buddy each morning; greeting the young koala with a smile and eagerly awaiting the moment when his handlers would pass him into Shouto's awaiting arms.
"Morning, Kodoroki," Shouto smiled, taking the joey into his arms while the photography team circled around him went wild. "This is going to be our last day together, so let's make it a good one, okay?"
Kodoroki yipped in response, his claws wrapping around the belts slung around his shoulders as he clung to Shotou’s chest. Having grown up without pets, Shouto had never understood why so many people were drawn to animals. But after spending so much time with Kodoroki and experiencing the warm comfort an animal could provide he thought that maybe he was starting to understand the appeal a little. His heart always felt a little bit lighter when Kodoroki was in his arms.
"Maybe I should think about getting a pet when I get home," Shouto mused, shifting his grip on Kodoroki in between photos with the group of waiting politicians hovering around the corner of the room.
"Not a koala though. You're kind of stinky," Shouto crinkled his nose while tapping Kodoroki's forehead. "Also, I'm fairly sure keeping you would be illegal."
Unimpressed, Kodoroki grunted indignantly before releasing a particularly ripe fart that left the Senator next to him gagging.
"See? This is what I'm talking about, Kodoroki," Shouto coughed, fanning the air in front of his face while one of the handlers cracked a window open. "You're not meant for polite society."

Shouto had been so used to coming up with reasons to visit Deku's agency to see you that it was strange to shift out of that mindset. Sidekicks were sent to retrieve paperwork, meetings were attended via video call, and everything else was shoved into emails routed directly to Deku's personal devices.
But having to visit the Number One Hero's agency was inevitable in their line of work. So with his shoulders set in false confidence, Shouto forced a neutral expression onto his face and set out towards Deku's office. He had practiced this greeting in his head a thousand times; what he'd say, how you'd respond, wondering if you'd be happy to see him. Or mad. Or sad, like he was.
He felt like he had prepared for every eventuality except the one he was confronted with: someone who wasn't you.
"Ah, hello?" He greeted the stranger, a bleary eyed man who looked like he hadn't had a good night's rest since the day he was born. Energy bar wrappers were scattered across the surface of your- his , desk and the small wastebasket beside him was overflowing with crushed coffee cans.
"Hello, Hero Shouto," the man yawned, covering his open mouth with his hand and bobbing his head in Shouto's direction. "Deku is expecting you. You can go ahead and enter. After knocking, obviously. Everyone should knock," the man whispered, his eyes dipping shut as he slumped down in his chair. "Knock…knock…"
"Of course," Shouto agreed softly, lightly rapping on Deku's door before slipping inside.
"Shouto!" Izuku cheered, lunging out of his chair to throw his arms around his friend in a crushing hug. "It's been too long! It's so good to see you!"
"It has been," Shouto agreed, patting his friend's back stiffly, always unsure about what to do with his hands in situations like this.
"So," Izuku began awkwardly, pulling back from the too-long embrace with a pained grimace on his face. "How're you holding up? Since, well… you know."
"Not great, honestly," Shouto sighed, picking at a loose thread at the cuff of his uniform. "It's been hard without her. Really hard. I didn't realize just how much of my life revolved around her until it suddenly didn't."
His eyes watered, despite his best effort to hold things together. "I really miss her. And as nervous as I was to come here, I was also looking forward to seeing her- making sure she was alright."
"I'm sorry," Izuku sighed, running a hand through his hopelessly tousled hair. "She asked for a temporary transfer to another department while things…settle down between you guys. She didn't want to make it harder for you, having to see her all the time."
Shouto was roughly struck by how much he both loved and hated your thoughtfulness at this moment in time.
"Takai down in Accounting agreed to take her on for a while and sent up his guy to replace her," Izuku explained, eyeing the door to his office worryingly, the distant sound of sobbing filtering in through the cracks. "I'm…not sure he's adjusting well to the switch. It's a bit more stressful than he's used to, I think."

His friends had assured him that the pain he was feeling would fade with time, that he needed to be patient and eventually he'd begin to heal.
So, he waited.
He waited to stop anticipating your cheerful greeting with bated breath when he came home after work each night. He waited to stop reaching over to your side of the bed at night, desperate to feel the familiar press of your skin against his. He waited for the urge to text you pictures of things he saw on patrol to pass, knowing how much you'd love to see how much the tagger on the East side of the city had been improving.
Shouto waited and waited and waited , but if anything the time spent away from you just seemed to compound his misery instead of alleviate it. He spent long, sleepless nights reflecting on the things you had told him; the reasons you left. Every moment of your acquaintance was turned over repeatedly in his head and examined until one devastating conclusion was reached:
"I was a bad boyfriend," Shouto muttered dejectedly, idly picking at the label of the shochu bottle in the middle of the table.
"I'm sure that's not true," Yaomomo consoled him, reaching across the booth to pat his hand comfortingly.
"I was ," Shouto whined, slumping down in his seat so Mina could pass a drink to Ochako over his head. She was only mildly successful and ended up spilling some of her cocktail into his hair.
"Whoopsie! Sorry about that, Shouto!" Mina grimaced, taking a hold of her cocktail glass with another hand to steady her grip while Ochako sipped from an unreasonably long crazy straw.
"It's fine," Shouto sighed as another glob of frozen margarita hit his head and began sliding down his neck. "I probably deserve it anyway for the way I treated her."
"Okay, look. Maybe you weren't a good boyfriend," Mina said, dropping down in her seat while Yaomomo shot her a disapproving glare. "I don't know, I wasn't there. But you can't keep beating yourself up over this- it's not healthy!"
"Right!" Ochako chimed in while indicating to the waitress she wanted two of whatever Mina was drinking. "You made mistakes, but you acknowledge that you were in the wrong. That's growth, Shouto!"
"Maybe," Shouto said mulishly, tearing the corner of the label he had been picking at fully off the bottle.
"Did you apologize?" Yaomomo asked softly, taking a dainty sip from her wine glass.
"No, I haven't. We haven't talked since my Australia mission," Shouto explained as he tore his strip of label into tiny pieces of confetti. "Do you think I should?"
"Do you feel like you have something to apologize for?" Yaomomo inquired as she tucked a lock of hair behind Jiro's ear, tracing a finger gently down her elongated lobe. Jiro, who was totally sober but utterly exhausted, had ended up falling asleep with her head on the table despite the raucous atmosphere of the bar they occupied. Shouto watched, utterly transfixed at the natural show of casual intimacy, and couldn't help but remember your silent disappointment every time he dropped your hand and stepped away when his friends entered the room.
Is this what he had been so afraid of? His friends seeing how much he cared for you? It had felt so important at the time, keeping you tucked away into the private facets of his life, that he didn't even consider what he was missing by doing so. Would you have looked at him that tenderly? Found little ways to touch him in public to let him know you cared?
Shouto had been so worried about showing vulnerability to the people in his life that he needed to be strong for; afraid that they would somehow find his newfound softness to be detrimental, that they would suddenly find him a liability.
You made him feel weak when all he knew was how to be strong, and the thought of being seen as anything other than what he had been created to be- useful, powerful, terrified him.
He didn't see any of those things when he looked at Yaomomo and Jiro. All he saw was his friends, happy and in love; and all he felt was the icy vice of regret constricting on his heart.
"Yes," Shouto swallowed, remorse thick and unmoving in his throat. "I think I have a lot to apologize for."

Shouto had accomplished many difficult things in his life. He'd survived an abusive childhood, escaped multiple attempts at fratricide as a teenager, and managed to muster up the necessary strength to begin building a tentative relationship with his Father as an adult. These days Shouto could occupy the same room as Enji for nearly forty minutes before the urge to strangle him became too overwhelming, which was positively cordial by Todoroki family standards.
The combined difficulty of all those accomplishments paled in comparison to the one that sat before Shouto at this very moment: texting his ex-girlfriend. He must have started the message a dozen times, trying varying levels of formality before deleting everything he wrote in frustration.
I'm sorry.
I know this is all my fault.
Please forgive me.
I wish we were still together.
I can't stop thinking of you.
Do you wake up every day as sad as I do?
All those messages were true, but discarded all the same. It took all evening, but he finally came up with a message he was moderately happy with; hitting send before he could second guess himself.
Shouto, 8:57pm "I miss talking with you."
Shouto's chest clenched with anticipation as dots bounced across his phone screen, awaiting your incoming response.
Deku's Assistant, 8:58pm "I miss talking with you, too."
A wave of self-loathing rolled through him as your contact name flashed across his screen. Had he really not even bothered to change your profile name when you'd started dating? He really did manage to bungle pretty much every aspect of your relationship, didn't he? You must have really cared for him to put up with his callousness for so long.
Deku's Assistant, 8:58pm "I've really been missing our friendship."
Shouto, 8:58pm "Me too." "Do you think enough time has passed for us to start talking again?"
Anxious minutes rolled by as Shouto awaited your response.
Deku's Assistant, 9:05pm "I don't know. But I think I want to try."
Shouto's heart soared as his fingers flew across his screen, the jubilant smile stretched across his face so wide that his cheeks ached.
Shouto, 9:07pm "Oh, thank goodness. I have so many pictures I need to show you."
send: img_7895
Deku's Assistant, 9:08pm "Is that the cat near the Chinese Restaurant??"
Shouto, 9:08pm "Yes! It turns out that she was pregnant, not fat."
Deku's Assistant, 9:09pm "I feel so bad making fun of her chunky tummy now."
Shouto, 9:09pm "Do you want to see her babies?"
Deku's Assistant, 9:09pm "YES!!!!"

The joy of regaining your friendship was a balm to Shouto's soul. He still longed for the intimacies you had shared and was pretty sure he would vividly remember the feeling of your teeth nibbling on his lower lip until his dying day. But being able to talk with you about his work or offer a sympathetic ear while you vented about your temporary reassignment was positively elating after months of separation.
Currently, you were recounting a run-in with the catty Senior Receptionist in the Marketing Department, something that had been happening with increasing frequency the past couple of weeks.
"I have no clue what I did to offend her, if anything. Maybe she just doesn't like me for some reason?" You sighed into the phone, the distant sound of keys jingling filling Shouto's ears.
"Impossible," Shouto scoffed as he opened up the fridge to peruse for something to heat up for dinner. "Everybody likes you."
"That's not at all true, but I'll take the compliment. I need it after today," you groaned, a sound Shouto knew accompanied you arriving home and sliding off your uncomfortable work shoes.
"Have you given any thought to transferring back to your old job?" Shouto asked, peeling back the corner of a container of leftovers to give the food inside a tentative sniff.
"I, uh, yes. Actually. I'm going to be transferring back later this week," you stammer, oddly nervous about such a mundane topic.
"Really?" Shouto pried, setting his container of food down on the counter to focus his attention on you. "That's sudden."
"It's been in the works for a couple of weeks now, actually. I just…didn't know how to bring it up."
"Because we'll be seeing each other in person again?"
"A little, maybe? But I'm mostly moving back for HR Reasons," you said, inhaling deeply before continuing. "Takai and I have…started seeing each other."
"Oh," Shouto breathed, stunned by your admission. He knew that the two of you weren't dating anymore, but the sudden realization that you would be seeing other people sent him reeling completely off balance; scrambling to grasp his counter for support.
"I'm sorry," you said, tone anxious and shaky. "I should have told you sooner, but things had been going so well and I didn't want to bring it up and ruin everything-"
"No," Shouto interrupted. "You didn't do anything wrong. Your personal life isn't any of my business. Not anymore."
"I- I'm so glad," you sniffle. "I don't know if I could bear not talking to you again."
"Does he…does Takai make you happy?" Shouto asked despite his better judgment. There was no way that your answer would satisfy him. But some part of his heart, the self-destructive portion that kept accepting Fuyumi's invitations to family dinners, needed to know.
"He does, Shouto. He really does."
"I'm glad," Shouto lied, sinking slowly to the floor as his knees gave way. "I need to go now. Dinner awaits."
You bid your farewells and disconnected, leaving Shouto slumped against his fridge with the chill of his kitchen tiles seeping down into his bones.

It was one thing to know you were dating another man, but seeing it in person turned out to be another matter entirely. Shouto wasn't prepared for the sour sting of jealousy that curdled in his belly when he exited the elevator at Deku's agency and saw Takai doubled over, lips pressed firmly against yours. You pulled away first, positively beaming up at him while you adjusted his tie before he straightened up to his full height and put himself out of reach of your tender ministrations.
You returned to your chair and startled once you registered Shouto's presence in your work space.
"Oh! Shouto! I'm so sorry, I didn't realize you were here," you grimaced, nervously turning a pen in your hands to distract from the awkward situation you suddenly found yourself plunged into. You weren't exactly sure how you were supposed to officially introduce a new boyfriend to your ex, but having them drop in while you were kissing likely wasn't the best approach.
"It's alright," Shouto assured you with a brittle smile, nodding tersely to Takai who returned the gesture with a smug grin. Shouto wanted to hate him for it, but remembered he'd done the same when he was in Takai's position; bolstered with pride from being on the receiving end of your affection.
With a parting wave, Shouto slid into Deku's office, collapsing into one of his empty chairs and burying his face into his hands, tears slipping through the gaps in his fingers while his friend scrambled for a tissue box.
"Shouto!" Izuku cried out, shoving a handful of crumpled tissues under his nose. "What happened?"
"I- I've really lost her for good, haven't I?" Shouto croaked, taking the wad of tissues from Deku's hand and sloppily mopping at his cheeks.
"I think so," Izuku whispered, eyes misting sympathetically as he rubbed a calloused hand between Shouto's shoulder blades as he cried.

Likely sensing how uncomfortable running into your boyfriend had made Shouto, you had gone out of your way to minimize the amount of contact between the two of them. You didn't mention Takai during your daily calls or texts unless necessary and Shouto hadn't run into the two of you together since that disastrous day in Deku's office, likely because you were maneuvering them around each other like a chess grandmaster shuffled pieces around the board.
While he knew that he would eventually have to get used to Takai if the two of you were to remain friends, Shouto still appreciated your willingness to give him space while he did so. He always admired that kindness and compassion in you and would never admit that your efforts were ultimately futile because he would never grow accustomed to seeing someone else occupying the place at your side where he used to stand; the place where he still very much wanted to be.
Shouto reveled in this false world he had crafted around the two of you; where Takai existed somewhere in the periphery of his mind, a distant problem he need not consider unless absolutely necessary. He knew more about you now than he ever did when you were together, the past distance between the two of you giving Shouto a newfound appreciation for every bit of time you spent together. For the first time since your breakup, it felt like Shouto was approaching something that resembled peace in his life.
That happiness he felt, the equilibrium he had achieved, all came crashing down dramatically one unremarkable Thursday evening during your daily chat as you walked the final leg of your commute home from work.
"Shouto. I need to tell you something," you began, a serious set to your words that put Shouto instantly on edge.
"What is it?"
"Takai asked me to marry him," you confessed. "And I said yes."
"I- that's," Shouto paused in the middle of the sidewalk, people dodging around him with peevish glares as he struggled to reign in his racing thoughts. "That's… great ."
"I didn't want you to hear it from someone else," you explained, voice suddenly muting as you pulled away from the phone to talk briefly with someone else. "I have to go. Some people down in Accounting are taking us out to celebrate."
"Have fun," Shouto croaked. "And Congratulations. Takai is a lucky man."
"Thank you," you whisper, a smile audible in the timbre of your voice. "That means a lot, coming from you."
"Have a good time. And be safe."
"I will. Bye, Shouto."
"Good-bye," Shouto whispered, the sound of the dial tone fading seamlessly into the ringing in his ears as he spun on his heel and walked through the doorway of the closest bar.

"I'm so sorry to bother you, Mr. Deku, Sir," the bartender bladders, wringing his bar towel nervously with his clawed hands. "I just- I didn't know who else to call? This is just my second week working here and the manager never really covered what to do when a Pro Hero won't leave? And I've seen you and Shouto together a lot on TV, so I figured that you might be friends and know how to handle this, but now that you're here I just realized that you probably have way more important stuff to do-"
Deku cut off the young man's panicked monologue with a raised hand and reassuring smile.
"You did the right thing by calling me. I'll take it from here, okay? Finish up whatever it is you need to do to close up and I'll be sure to have Shouto out by the time you're done."
"Yes, of course! Thank you!" The bartender shouted, scrambling off to carry a tray of used glasses back into the kitchen. Once he disappeared behind the back room door the smile slid from Izuku's face as he took in his long time friend, slumped over the bar with his head buried in his folded arms. With a heavy sigh, Izuku slid onto the stool next to Shouto, the metal squealing in protest at his added weight.
"Hey, Shouto," Izuku greeted, patting his friend's shoulder firmly. "It's time to go. You've more than worn out your welcome here, I'm afraid."
"Iz'ku?" Shouo slurred, rolling his head to face Deku with fiercely squinted eyes. "When'd ya get here?"
"Just a moment ago."
"Oh. Tha's a shame," Shouto sighed. "If you got here eerly- earlly- sooner, we coulda had a drink t'gether."
"How about we drink these?" Izuku asked, fishing two large bottles of water out of his backpack and depositing one in front of Shouto. Nose crinkled in distaste, Shouto cracked the seal on his bottle and started sipping, his hand icing over too cool down the water to his preferred chilly temperature. They sat in a companionable silence, slowly working through their drinks and watching a replay of yesterday's baseball game on the TV hung crookedly from the ceiling above the bar's framed liquor license.
"My ex- she's gettin' married," Shouto said, drawing a finger through a bead of condensation along the bar top.
"I know. The entire office was in an uproar over it. She brought me a slice of cake."
"Was it good?"
"It was alright," Izuku shrugged. "A little dry, but the icing made up for it.
"Tha's good. She deserves good things. All the good things," Shouto nodded, the weight of his own head surprising him as it flopped from front to back.
"Takai is good for her," Deku said, swinging back the last of his water before slipping the empty bottle back into his bag.
"Takai," Shouto hissed. "Wha' makes him so special anyway? Why does she like him better than me? He's too tall! I bet his Grandfather was a pair of stilts."
"Shouto! I know you're sad, but that's no excuse to be cruel. Takai is a good man who treats her well," Izuku chided, poking the arm Shouto was holding his water with to remind him to keep drinking. Reluctantly, Shouto took another mouthful of water, swishing it between his cheeks thoughtfully.
"He treats her better than I ever did."
"He does," Izuku agreed sadly.
"I wish- I wish I could go back. Do it all different. Do y'know someone with a time travel Quirk?"
"I- yes, actually," Izuku admitted reluctantly. "But I'm not going to let you create an alternate timeline because your ex moved on and you're sad about it."
"Ugh," Shouto grunted. "Why do you always have to be so reapons- responsible?"
"Comes with the job, I'm afraid. You're supposed to be responsible too, you know."
"Lame," Shouto sighed, throwing back the last of his water and passing the empty bottle to Deku.
"Sure is," Izuku laughed. "I thought Pro Heroes were so cool growing up, but it turns out we're all a bunch of party pooping killjoys."
"So wha' am I s'posed to do now?"
"Well, that depends," Deku huffed, scratching at his chin thoughtfully. "Were you just friends with her because you were hoping to get back together with her someday?"
"No," Shouto cried emphatically. "I won't lie an' say I wasn't hoping for that, but I'm friends with her because we're good friends. She's good. And she makes me want to be gooder."
"That's… good, " Izuku snorted, amused at his friend's expense.
"Yeah," Shouto grinned enthusiastically, his eyes glossy and unfocused. "It is!"
"So if she's a good friend, you need to be a good friend in return. Talk to her. Support her. But step back and take a breather if it gets to be too much for you to handle. There's no need for you to set yourself on fire here."
"Unless's an emergency," Shouto muttered seriously, staring down at his left hand in contemplation. "I'm definitely supposed to light m'self on fire in an emergency. That's half my job."

Unwavering romantic feelings aside and unmentioned, things were going relatively well between you and Shouto. Once the initial shock of your engagement wore off, he was able to resume calling and messaging you on a regular basis. He did need to take a few days off of work when your wedding invitation arrived at his apartment, a simple but elegantly penned note printed on crisp ivory paper that overwhelmed him with thoughts of a future he wasn't prepared to deal with at that particular moment in time.
But he liked to think he was handling things much better these days.
"Hey, Natsuo?" Shouto called, holding up two delicate plates for inspection. "Which china set best conveys the message 'Congratulations, but I secretly hope your marriage fails so I can have a second chance with you?' Is it Wedgwood?"
"Lemme see," Natsuo said as he took the plates into his hand, angling them to and fro under the dim store lights to get a better look at the delicate patterns.
"Shouto," Fuyumi scolded gently, returning a pale blue tea cup to the display shelf. "There's no need to put yourself through this. We can just order something off the registry and call it a day."
"No," Shouto said firmly, picking up a salad plate and immediately setting it down with a disapproving frown. "I want to do this for her."
"Alright," Fuyumi sighed in defeat, wandering over to a display of shining silver teapots. "How about one of these?"
"It needs to be china," Shouto insisted, staring critically at an oval serving platter with a brocade print running along the rim.
"It reminds me of her."
"You're gonna' need to elaborate on that, Little Bro," Natsuo drawled, his attention still primarily focused on the plates Shouto had passed to him.
"She's…delicate, but strong," Shouto explained, running a finger admiringly across the golden rim of a gravy boat. "And even though you see her every day, you're still stuck by her beauty- a timeless elegance you can't help but admire."
"Shouto," Fuyumi cooed, clutching the teapot to her chest. "That's so sweet!"
"Also, dishes are something you use repeatedly. So if I give them to her I guarantee she'll have to think of me during every meal," Shouto grinned deviously.
"I think you definitely want the Wedgwood then," Natsuo confirmed, sliding the rejected plate back into its stand. "It's too expensive for her to give away without feeling guilty."
"Perfect!" Shouto beamed, waving the dinner plate in the air and using it to flag down a passing salesperson, their face instantly paling as they witnessed the lack of care Shouto was showing their unpurchased merchandise.
"You shouldn't have encouraged him to be so petty," Fuyumi chastised, walloping Natsuo soundly on the bicep.
"Hey!" He winced, rubbing at the spot his sister hit. "This is the most excited Shouto has been in months. If buying spite plates makes him happy, then who am I to judge?" Natsuo shrugged, fishing his phone from his jacket pocket to check on his missed messages.
"I guess," Fuyumi mused, chewing on her lip. "It's pretty harmless in the end, right? She gets a nice set of dinnerware and Shouto is satisfied."
"Yep," Natuso agreed, still engrossed in his phone.
"I'll go help him pick out some wrapping paper then," Fuyumi smiled, shuffling off to look at the display wall of wrapping options while the salesperson who had been helping Shouto rang up his purchase with a dazed expression, unable to do the mental math to calculate just how high their commission was going to be.

To say that Shouto became increasingly distracted as your wedding day drew near was a profound misrepresentation of events. Emotionally, he was in shambles and it was beginning to impact his work. Distracted and slow, he was taking more hits than ever before and limping home after clocking out more often than not. His sidekicks had taken it upon themselves to make sure he never patrolled alone; creating an unofficial schedule that kept him under someone's watchful eye every shift for the foreseeable future.
They thought they were being secretive about it, but the signup sheet was just taped up on the wall of the sidekick locker room. The custodian had discovered it the day it was initially hung and reported it to him immediately. Shouto had been so touched by his subordinates' show of concern for his well-being that he ignored their less than clandestine whispering and did his best to pretend to be unaware of their scheming. He was absolutely indulging them, but he also appreciated their constant company more than he could adequately express.
It was hard to be alone right now.
So when they were alerted to a villain attack a couple blocks away, the odds were in their favor; a top ranking hero with a familiar partner in tow usually made for a devastating combination most villains didn't stand a chance against.
But it seemed like everything that could have possibly gone wrong did. Physical attacks from both him and Ice Pick, his sidekick du jour, weren't landing. Their Quirks were sluggish and misfiring, Ice Pick had lost her footing and stumbled into his side; knocking him off balance as well. The evidence was quickly pointing to some sort of luck manipulation Quirk that they had no idea how to counter.
"Any ideas, Boss?" Ice Pick panted, sending a blast of needle-sharp icicles the Villain's way and screeching in frustration when they all miraculously managed to miss their target.
"Nothing immediately comes to mind," Shouto grunted, ducking behind a parked car to take stock of the situation. "I think our best course of action is to keep him distracted until backup arrives. Call back to the agency and make sure whoever is en route is equipped with Quirk repressing gear."
"Roger that!"
Shouto rolled out from his cover, throwing out a flare blast he knew wouldn't connect, but would hopefully drive the villain away from the cram school he had been encroaching on. Ice Pick, having finished relaying messages back to headquarters, was quick to return to his side.
"Back up due to arrive momentarily."
Shouto opened his mouth to respond to her, but caught sight of something in the distance that pulled his attention away. Speeding towards the villain in front of them at breakneck speed was what looked like a cannonball, but with a slight wobble around the edges like it wasn't fully solid. Given what he ascertained about the trajectory of projectiles lobbed at the villain, Shouto knew it would never connect with its intended target and would instead deflect right towards where Ice Pick was standing.
"WATCH OUT," Shouto bellowed, pushing Ice Pick out of the way and coating his right side in a thick layer of ice to absorb the force of the impending blow. The projectile made contact and swept Shouto off his feet and sent him flying backwards off of the street and through the glass window of a nearby shop. High pitched screeches and cries rang out around him as he finally came skidding to a stop in the middle of the floor, large groups of women scrambling to escape the destruction he left in his wake. Employees wearing bright fluorescent vests were doing their best to funnel the panicking customers back through the emergency exit, but a few stragglers hung back to record the goings on with their cell phones until the very last moment.
With a groan, Shouto pushed himself up into a sitting position, hand darting up tenderly cradle his obviously broken ribs with a pained hiss.
"Shit," he swore lowly, ignoring the sharp pains in his side and the crackling sound that accompanied every breath.
"Shouto!" he heard someone scream through the ringing in his ears, assuming it was Ice Pick rushing to his aide as he slowly shifted until he was on all fours, grasping onto the arm of a nearby chair to keep upright as his vision wavered.
"What the hell do you think you're doing?" You screech, pushing down on his shoulders to keep him from attempting to pull himself up into a standing position. "You are seriously injured, Shouto! Stay down !"
Shouto's head snapped towards you, which was a mistake because the sudden movement made a wave of nausea roll through him. Swallowing down the bile creeping up his esophagus, he was able to finally focus his attention on you. If it wasn't for his agonizing injuries Shouto was fairly certain he would have thought he was in heaven as you knelt next to him, an absolute vision in a white dress with delicately pearls glimmering in the fluctuating light from the emergency strobe lamps.
"What are you doing here?" Shouto managed to mumble, distracted by the delicate swooping of your exposed collar bone. He always loved running kisses across it- you always laughed while he did so, scrunching up your shoulders and burrowing in on yourself in an attempt to protect the delicate flesh from his wandering lips.
He missed that.
He also missed what you were just saying.
"-on wedding dresses."
"Oh," Shouto wheezed, blinking at you owlishly. "You look really beautiful."
"Thanks," you smiled, pushing on his shoulders until he was laying down on the floor, his head pooled in the fluffy fabric of your skirt, staring up at you with a dopey grin. "You know, if you wanted to come dress shopping with me you could have just asked. This is a bit dramatic even for you."
Shouto barked out a laugh and then immediately groaned as his lungs sharply protested his sudden mirth. "Stop being charming," Shouto chided, eyes tracing over the tucks and folds of the bodice of your dress. "I can't handle you at full power right now."
"I'll tone it down then," you sniffled, running a shaking hand through his mussed hair, pulling out tiny slivers of glass with careful fingers and flicking them behind you carelessly.
"Is this it?" Shouto mumbled, his lips slick with a mixture of spittle and blood.
"Is what it? What do you mean?" You asked worriedly, prying and eyelid open to examine his pupil.
"The dress," Shouto clarified with a rattling sigh, frowning when tiny red dots suddenly bloomed across the pristine white fabric. "Is this the one?"
"Oh," you breathe in relief, letting go of his eyelid and returning to running your fingers along his scalp. "Yeah. I think this is the one."
"'s perfect," Shouto whispered, eyelids growing heavy as the edges of his vision darkened. "Defin'ly buy this one…"
"Shou-! -ay awake!" You cried, tears streaming down your face while Shouto buried his face into your stomach, inhaling the scent of your skin layered underneath the fragrance of starch from the dress; snippets of your words filtering through his brain like a sieve.
"-ncussion! Stay awake! Ple-!"
"I already call-"
"-Deku is on-"
And then there was silence.

The road to recovery was far longer than Shouto would have liked. Any sort of brain injury booked you an immediate and non negotiable week long stay in the Hero Intensive Care Unit with CT scans scheduled daily. Shouto flitted in and out of consciousness for a couple of days until they pulled back on his meds, and from there on out he made steady improvement, suffering through never ending days of under salted meals and reciting his ABCs backwards to prove his brain was in fine working order.
Half-way through his stay he was visited by a deeply apologetic Gunhead and his terrified Intern, Cannon Blob, who had been the one that had lobbed the projectile that had taken Shouto out.
"Hot shot here broke protocols and rushed ahead without me," Gunhead explained as Cannon Blob repeatedly bowed at Shouto's bedside, his lips wobbling as a constant stream of apologies tumbled from his mouth. "I told him he's lucky you were able to push Ice Pick out of the way and throw up some sort of shield. If you hadn't, he'd be visiting a grave instead of a hospital."
Shouto looked at the terrified Intern, still just a kid struggling to learn the cruel rules of the adult game they had signed their life away to play. The reformed Hero Commission had raised the age for entering into Heroism after the war, the world rightfully opposed to the government keeping the gears of society greased with the blood of child soldiers. But even with the increase in age, Cannon Blob just looked so young . Too young , really.
With a weary sigh, Shouto dropped his hand down onto Cannon Blob's shoulder, interrupting his frantic bowing with a firm squeeze.
"Take this experience to heart," Shouto said, pausing to cough gently into the crook of his arm. "Learn from this mistake and follow through with that lesson; don't fall back into the same bad habits that led you to today."
"I will!" Cannon Blob blubbered, wiping his tears on his uniform sleeves. "I promise I will, Shouto!"
"See that you do. Gunhead is an excellent mentor. Listen to him and I know you'll become a Hero I'll enjoy working with in the future."
"Thanks Shouto," Gunhead nodded, steering Cannon Blob away from his bedside and towards the door. "Tell you Old Man I said 'Hello'".
"I'd rather take another hit from Cannon Blob," Shouto stated blandly, a corner of his mouth curling at the sound of Gunhead's booming laugh echoing down the hospital hallway.

It was still a good stretch of time before Shouto was allowed back into the field. It was nice being back in his office at first, a welcomed change to the sterile environment the hospital offered, but he quickly grew restless on desk duty and looked for any reason to get out and stretch his legs during the day.
So he accompanied his company gofers on coffee runs, lugged packages around the mailroom, and hand delivered high-level clearance messages between nearby agencies. Today's errand run took him by Deku's office, a place that he'd been avoiding for a while now.
You'd been unable to visit him in the hospital since civilians are banned from entering unless they were the emergency contact or direct family members or of the patient, and he'd delayed replacing his phone right away to buy himself a couple extra days of contemplation before he had to speak with you again.
While a lot of the accident was at this point a hazy blur in his memories, the image of you in that wedding dress was seared into his brain like no other sight had been before. You were there every time he closed his eyes, invading his dreams in that flowing white dress. More often than not his visions followed a rough outline of the actual event, with Shouto's head cradled in your lap while you ran your hands across his face with a tender smile. But sometimes his brain would rearrange things to its liking, depositing you at the end of a long aisle and having you march steadily towards him.
And once he had thought about you reaching him, a bouquet of fluffy chrysanthemums tightly grasped in your hands as you grinned up at him so sweetly that it made his teeth ache; he just couldn't find a way to stop.
He didn't know how he could face you, knowing with absolute clarity how radiant you'd be as a bride.
But not as his bride.
The future he dreamed about wasn't his to claim. He felt a fleeting moment of kinship to his Father, wondering if this is how he felt standing in All Might's shadow for so many years; success somehow both tantalizingly close and impossibly far from his grasp.
When he'd finally switched his SIM card over to his new phone and booted it up, he was inundated with missed calls and texts; his inbox filling up faster than he could answer them, most of them from you. Shouto had assured you that he was fine, but convalescent and in no shape to entertain visitors. After double checking that he didn't need anything, you had backed off and resumed your normal messaging routine; occasional texts throughout the day and a quick call while walking home that Shouto let ring more often than he picked up.
With a fortifying breath as the elevator ascended to Deku's top office, Shouto prepared to face you for the first time since the bridal boutique. The elevator doors whooshed open and Shouto strode purposefully towards your desk, a neutral look settled on his face that would hopefully not alert you to the panicked thundering of his heart.
"Of course. Yes, I understand. I'll relay the message immediately," you spoke into the phone receiver perched on your shoulder, fingers flying across your computer keyboard as you logged some sort of information for future reference. "Thank you for returning my call so quickly. Have a wonderful day!"
Dropping the receiver into its base, you finally turned to address the new visitor, routine greeting evaporating off of your tongue when you realized who was standing in front of you.
"Shouto!" You cried, leaping up from your chair so quickly you stumbled a bit as you rounded the desk and threw your arms around Shouto's neck with a sob. "You're okay! You're really okay! I was so worried!"
"I'm alright," Shouto mumbled soothingly, wrapping his arms around your waist and pulling you further into his embrace.
"I was so scared," you cried into his shoulder.
"I'm sorry."
"Don't apologize," you sniffled, eyes red as you wiped at your tears with the back of your hands. "Just try to pass out a little less ostentatiously next time, okay?"
"I'll do my best," Shouto promised, passing you the handkerchief he had tucked into his back pocket. You accepted his offering with a grateful smile, blowing your nose with an unbecoming honk as you tried to regain your composure.
"Okay," you stated firmly, squaring your shoulders and moving back to your desk chair. "I'm sure you're here on official business, so I'll stop monopolizing your time. Deku's free so you can head on in."
Moving past your desk, Shouto drew to an abrupt halt when he noticed the new addition to your desk decorations; a fluffy brown Koala dressed up in a replica of his Hero costume.
"You bought one of the Kodoroki dolls?" Shouto asked, picking the stuffed animal up and running a finger over the pink patch of fur around its left eye with a fond smile.
"Of course I did! I couldn't resist supporting my favorite Hero and a cute koala at the same time! No woman is that strong," you sighed with a helpless shrug.
"I'm your favorite Hero?" Shouto whispered in awe. "Still? Even after- after how poorly I treated you when we were together?"
"You weren't so bad," you generously offered up in his defense.
"I was a pig-headed, callous idiot," he reminded you flatly.
"You definitely had your faults as a boyfriend," you agreed with a laugh, taking Kodoroki back from his hands and fluffing his ears to your liking before returning him to his place of honor next to your computer monitor. "But I can't imagine a greater Hero than you."
"How thick are these doors?" Shouto whispered, hitching a thumb towards your boss's office. "Is your job in Jeopardy if Deku overhears you supporting another Hero?"
"Please," you scoff dismissively, bopping Kodoroki on the nose before you log back onto your PC to resume working. "He has no place to judge when his office can double as an official satellite location for the All Might Museum."
#bnha x reader#bnha x y/n#bnha x you#mha x y/n#mha x reader#mha x you#pigeoncoos🕊#bnha x self insert#mha x female reader#todoroki shouto x you#shouto todoroki x reader#todoroki x reader#shouto x y/n#shouto x you#todoroki shouto x reader#shouto x reader
74 notes
·
View notes
Text

Deep Dives into Tech and Digital Growth Strategies
In an era of rapid technological advancements and evolving business landscapes, understanding the nuances of tech-driven strategies is essential for sustained growth. Companies today must leverage cutting-edge technologies and innovative digital growth strategies to stay competitive. This article takes a deep dive into the world of technology and digital strategies, highlighting how businesses can harness them to achieve their full potential.
Tech Innovation: The Catalyst for Business Evolution
Innovation in technology is reshaping industries, from manufacturing and healthcare to retail and financial services. Businesses that embrace tech innovations can unlock new opportunities and create unique competitive advantages.
Automation and AI: Automation tools and artificial intelligence (AI) are driving efficiency, reducing human errors, and freeing up resources for more strategic tasks. Companies that adopt AI-driven decision-making processes gain valuable insights and predictive analytics.
Cloud Computing: Cloud-based solutions offer businesses scalable, cost-effective options for data storage and software deployment. Cloud technologies facilitate remote work, enhance collaboration, and provide data accessibility from any location.
Internet of Things (IoT): IoT is transforming industries by connecting devices and enabling real-time data collection and analysis. Businesses can leverage IoT to monitor operations, optimize workflows, and improve customer experiences.
5G Connectivity: The rollout of 5G networks is enabling faster communication and data transfer. This enhanced connectivity paves the way for innovations in areas like telemedicine, augmented reality, and autonomous vehicles.
Digital Marketing Strategies for Sustainable Growth
Digital marketing is at the heart of modern business strategies. To stand out in a crowded market, businesses must adopt targeted and innovative marketing tactics.
Search Engine Optimization (SEO): SEO is critical for improving online visibility and driving organic traffic. Businesses should focus on creating high-quality content, optimizing for keywords, and building authoritative backlinks to enhance search engine rankings.
Content Marketing: Content is king when it comes to building brand authority and engaging audiences. Businesses should invest in creating informative, relevant content that addresses customer pain points and provides solutions.
Social Media Engagement: Social media platforms are powerful tools for building brand awareness and fostering community engagement. Consistent posting, audience interaction, and strategic advertising can amplify a brand’s reach.
Data-Driven Marketing: Analyzing marketing performance data allows businesses to make informed decisions and refine strategies. By leveraging analytics tools, businesses can identify trends, understand customer behaviors, and optimize campaigns for better results.
Personalization: Today’s consumers expect personalized experiences. Businesses that use data to tailor their offerings and communication to individual preferences are more likely to build lasting relationships with customers.
Cybersecurity: Protecting Digital Assets
As businesses become more reliant on digital technologies, cybersecurity is paramount. Cyber threats can compromise sensitive data, disrupt operations, and damage reputations. To safeguard digital assets, businesses must implement robust cybersecurity measures.
Multi-Layered Security: Implementing multi-layered security protocols ensures that businesses are protected from various attack vectors. This includes firewalls, intrusion detection systems, and endpoint protection.
Data Encryption: Encrypting sensitive data both in transit and at rest protects it from unauthorized access.
Regular Audits: Conducting regular security audits helps identify vulnerabilities and ensures that security measures are up-to-date.
Employee Training: Human error is a common cause of data breaches. Educating employees on cybersecurity best practices can reduce the risk of phishing attacks and other social engineering tactics.
Customer-Centric Tech Solutions
Understanding and prioritizing customer needs is key to business growth. Tech innovations can enhance customer experiences and build long-term loyalty.
Customer Relationship Management (CRM) Systems: CRM systems help businesses manage customer interactions and provide personalized experiences. By analyzing customer data, businesses can tailor their offerings and improve satisfaction.
Chatbots and Virtual Assistants: AI-powered chatbots offer 24/7 customer support, answering queries and resolving issues in real-time. These tools enhance customer service while reducing operational costs.
Omnichannel Experiences: Today’s consumers interact with businesses across multiple channels. Providing a seamless, consistent experience across all touchpoints—whether online, in-store, or on mobile—is essential for customer satisfaction.
Tech Integration for Operational Efficiency
Integrating technology into core business processes can streamline operations, reduce costs, and improve overall efficiency.
Enterprise Resource Planning (ERP) Systems: ERP systems integrate various business functions into a unified platform, improving visibility and coordination across departments.
Project Management Tools: Digital project management platforms enable teams to collaborate, track progress, and meet deadlines efficiently.
Supply Chain Optimization: Advanced technologies like IoT and blockchain can enhance supply chain transparency, improve inventory management, and reduce delays.
Sustainable Growth with Tech Partnerships
Partnering with tech solution providers can accelerate business transformation and growth. Collaborating with experts allows businesses to access specialized knowledge and cutting-edge technologies without investing heavily in in-house resources.
Scalability: Tech partnerships enable businesses to scale operations as needed, adapting to market demands without significant disruptions.
Innovation: Partnering with tech innovators ensures that businesses stay ahead of industry trends and adopt new technologies as they emerge.
Looking Ahead: Future Trends in Tech and Digital Growth
The tech landscape is constantly evolving, and businesses must stay agile to remain competitive. Emerging trends like artificial intelligence, quantum computing, and edge computing are set to redefine industries. By staying informed and embracing change, businesses can position themselves for long-term success.
Conclusion
Tech4Biz Solutions is committed to empowering businesses with innovative tech solutions and digital growth strategies. Whether it’s leveraging advanced technologies, optimizing marketing efforts, or enhancing customer experiences, Tech4Biz helps businesses unlock new possibilities. By diving deep into the world of tech and digital strategies, companies can fuel growth, drive innovation, and stay ahead of the curve in an ever-changing business landscape. Visit Tech4Biz Solutions to learn more about how we can help transform your business.
5 notes
·
View notes
Text
Critical Vulnerability (CVE-2024-37032) in Ollama

Researchers have discovered a critical vulnerability in Ollama, a widely used open-source project for running Large Language Models (LLMs). The flaw, dubbed "Probllama" and tracked as CVE-2024-37032, could potentially lead to remote code execution, putting thousands of users at risk.
What is Ollama?
Ollama has gained popularity among AI enthusiasts and developers for its ability to perform inference with compatible neural networks, including Meta's Llama family, Microsoft's Phi clan, and models from Mistral. The software can be used via a command line or through a REST API, making it versatile for various applications. With hundreds of thousands of monthly pulls on Docker Hub, Ollama's widespread adoption underscores the potential impact of this vulnerability.
The Nature of the Vulnerability
The Wiz Research team, led by Sagi Tzadik, uncovered the flaw, which stems from insufficient validation on the server side of Ollama's REST API. An attacker could exploit this vulnerability by sending a specially crafted HTTP request to the Ollama API server. The risk is particularly high in Docker installations, where the API server is often publicly exposed. Technical Details of the Exploit The vulnerability specifically affects the `/api/pull` endpoint, which allows users to download models from the Ollama registry and private registries. Researchers found that when pulling a model from a private registry, it's possible to supply a malicious manifest file containing a path traversal payload in the digest field. This payload can be used to: - Corrupt files on the system - Achieve arbitrary file read - Execute remote code, potentially hijacking the system The issue is particularly severe in Docker installations, where the server runs with root privileges and listens on 0.0.0.0 by default, enabling remote exploitation. As of June 10, despite a patched version being available for over a month, more than 1,000 vulnerable Ollama server instances remained exposed to the internet.
Mitigation Strategies
To protect AI applications using Ollama, users should: - Update instances to version 0.1.34 or newer immediately - Implement authentication measures, such as using a reverse proxy, as Ollama doesn't inherently support authentication - Avoid exposing installations to the internet - Place servers behind firewalls and only allow authorized internal applications and users to access them
Broader Implications for AI and Cybersecurity
This vulnerability highlights ongoing challenges in the rapidly evolving field of AI tools and infrastructure. Tzadik noted that the critical issue extends beyond individual vulnerabilities to the inherent lack of authentication support in many new AI tools. He referenced similar remote code execution vulnerabilities found in other LLM deployment tools like TorchServe and Ray Anyscale. Moreover, despite these tools often being written in modern, safety-first programming languages, classic vulnerabilities such as path traversal remain a persistent threat. This underscores the need for continued vigilance and robust security practices in the development and deployment of AI technologies. Read the full article
2 notes
·
View notes
Text
Navigating the Cloud: Unleashing the Potential of Amazon Web Services (AWS)
In the dynamic realm of technological progress, Amazon Web Services (AWS) stands as a beacon of innovation, offering unparalleled advantages for enterprises, startups, and individual developers. This article will delve into the compelling reasons behind the adoption of AWS and provide a strategic roadmap for harnessing its transformative capabilities.

Unveiling the Strengths of AWS:
1. Dynamic Scalability: AWS distinguishes itself with its dynamic scalability, empowering users to effortlessly adjust infrastructure based on demand. This adaptability ensures optimal performance without the burden of significant initial investments, making it an ideal solution for businesses with fluctuating workloads.
2. Cost-Efficient Flexibility: Operating on a pay-as-you-go model, AWS delivers cost-efficiency by eliminating the need for large upfront capital expenditures. This financial flexibility is a game-changer for startups and businesses navigating the challenges of variable workloads.
3. Comprehensive Service Portfolio: AWS offers a comprehensive suite of cloud services, spanning computing power, storage, databases, machine learning, and analytics. This expansive portfolio provides users with a versatile and integrated platform to address a myriad of application requirements.
4. Global Accessibility: With a distributed network of data centers, AWS ensures low-latency access on a global scale. This not only enhances user experience but also fortifies application reliability, positioning AWS as the preferred choice for businesses with an international footprint.
5. Security and Compliance Commitment: Security is at the forefront of AWS's priorities, offering robust features for identity and access management, encryption, and compliance with industry standards. This commitment instills confidence in users regarding the safeguarding of their critical data and applications.
6. Catalyst for Innovation and Agility: AWS empowers developers by providing services that allow a concentrated focus on application development rather than infrastructure management. This agility becomes a catalyst for innovation, enabling businesses to respond swiftly to evolving market dynamics.
7. Reliability and High Availability Assurance: The redundancy of data centers, automated backups, and failover capabilities contribute to the high reliability and availability of AWS services. This ensures uninterrupted access to applications even in the face of unforeseen challenges.
8. Ecosystem Synergy and Community Support: An extensive ecosystem with a diverse marketplace and an active community enhances the AWS experience. Third-party integrations, tools, and collaborative forums create a rich environment for users to explore and leverage.

Charting the Course with AWS:
1. Establish an AWS Account: Embark on the AWS journey by creating an account on the AWS website. This foundational step serves as the gateway to accessing and managing the expansive suite of AWS services.
2. Strategic Region Selection: Choose AWS region(s) strategically, factoring in considerations like latency, compliance requirements, and the geographical location of the target audience. This decision profoundly impacts the performance and accessibility of deployed resources.
3. Tailored Service Selection: Customize AWS services to align precisely with the unique requirements of your applications. Common choices include Amazon EC2 for computing, Amazon S3 for storage, and Amazon RDS for databases.
4. Fortify Security Measures: Implement robust security measures by configuring identity and access management (IAM), establishing firewalls, encrypting data, and leveraging additional security features. This comprehensive approach ensures the protection of critical resources.
5. Seamless Application Deployment: Leverage AWS services to deploy applications seamlessly. Tasks include setting up virtual servers (EC2 instances), configuring databases, implementing load balancers, and establishing connections with various AWS services.
6. Continuous Optimization and Monitoring: Maintain a continuous optimization strategy for cost and performance. AWS monitoring tools, such as CloudWatch, provide insights into the health and performance of resources, facilitating efficient resource management.
7. Dynamic Scaling in Action: Harness the power of AWS scalability by adjusting resources based on demand. This can be achieved manually or through the automated capabilities of AWS Auto Scaling, ensuring applications can handle varying workloads effortlessly.
8. Exploration of Advanced Services: As organizational needs evolve, delve into advanced AWS services tailored to specific functionalities. AWS Lambda for serverless computing, AWS SageMaker for machine learning, and AWS Redshift for data analytics offer specialized solutions to enhance application capabilities.
Closing Thoughts: Empowering Success in the Cloud
In conclusion, Amazon Web Services transcends the definition of a mere cloud computing platform; it represents a transformative force. Whether you are navigating the startup landscape, steering an enterprise, or charting an individual developer's course, AWS provides a flexible and potent solution.
Success with AWS lies in a profound understanding of its advantages, strategic deployment of services, and a commitment to continuous optimization. The journey into the cloud with AWS is not just a technological transition; it is a roadmap to innovation, agility, and limitless possibilities. By unlocking the full potential of AWS, businesses and developers can confidently navigate the intricacies of the digital landscape and achieve unprecedented success.
2 notes
·
View notes
Text
Building the DevOps Foundation: Essential Skills for Success in Software Development
In the ever-evolving domain of software development, DevOps has emerged as a transformative force, reshaping how organizations approach the entire software development and delivery lifecycle. While there are no strict prerequisites for entering the DevOps realm, acquiring foundational skills significantly enhances the ability to understand and implement DevOps principles effectively. For those aiming to validate their DevOps proficiency and boost career prospects, pursuing DevOps Training in Hyderabad becomes a strategic move. This comprehensive guide explores the essential skills paving the way for a successful journey into DevOps.

Grasping Software Development Basics: A solid understanding of coding, version control, and the software development life cycle (SDLC) forms the bedrock before venturing into DevOps practices. This knowledge bridges the gap between development and operations teams.
Operating Systems Proficiency: Operating systems, especially Linux, underpin many DevOps environments. Foundational knowledge of Linux, including command-line operations and system administration, proves highly beneficial for effective interaction in DevOps scenarios.
Networking Concepts Mastery: DevOps professionals frequently engage with network configurations. Fundamental knowledge of networking concepts, such as IP addresses, subnets, firewalls, and DNS, proves invaluable for seamless application deployment.
Virtualization and Cloud Computing Experience: Virtualization and cloud platforms are integral to DevOps. Familiarity with technologies like VMware, VirtualBox, and leading cloud platforms such as AWS, Azure, or Google Cloud is essential for deploying applications in dynamic cloud environments.
Version Control System (VCS) Expertise: Proficiency in version control systems, with Git being a notable example, is fundamental in DevOps. Understanding version control workflows ensures smooth collaboration and effective code management.
Scripting and Coding Skills Advantage: While not mandatory, scripting skills in languages like Bash, Python, or PowerShell offer a significant advantage in DevOps. Automation scripts streamline repetitive tasks, enhancing the efficiency of DevOps workflows.

Containerization Knowledge Enhancement: Containers, exemplified by Docker, play a pivotal role in DevOps. Understanding containerization concepts and tools facilitates consistent and portable application deployment across diverse environments.
Continuous Integration (CI) and Continuous Deployment (CD) Mastery: DevOps emphasizes CI/CD practices. Familiarity with these concepts and hands-on experience with tools like Jenkins or GitLab CI are crucial for delivering high-quality software through automated testing.
Infrastructure as Code (IaC) Competence: IaC, a fundamental DevOps principle, involves managing infrastructure through code. Familiarity with IaC tools like Terraform or Ansible streamlines infrastructure deployment and management.
Soft Skills Emphasis: In addition to technical prowess, effective communication and collaboration skills are indispensable in a DevOps setting. Strong interpersonal skills contribute to the culture of collaboration that defines DevOps.
Getting Started with DevOps involves not just meeting prerequisites but embracing a mindset of continuous learning and improvement. While these foundational skills provide a robust start, consider enrolling in a reputable DevOps training program for practical experience and industry insights. The dynamic and rewarding world of DevOps awaits those ready to embark on a journey of continuous growth and innovation.
2 notes
·
View notes
Text
Thin Client: Streamlined Computing, Centralized Management, and Cost Efficiency.
A thin client is a computer or a computer terminal that relies heavily on a server or a central network for most of its processing and storage capabilities. It is designed to be lightweight and simple, with minimal hardware and software requirements. Thin clients typically have limited processing power, memory, and storage capacity compared to traditional desktop computers.
The concept behind thin clients is to offload the majority of computing tasks to a central server or a cloud-based infrastructure. The server or the cloud handles the heavy processing, data storage, and software applications, while the thin client primarily serves as an interface for accessing and interacting with those resources.
Thin clients are often used in centralized computing environments, such as virtual desktop infrastructure (VDI) deployments, where multiple users can access their virtual desktops hosted on a central server. In this setup, the thin client acts as a remote display terminal, transmitting user input to the server and receiving the screen updates to display on its monitor.
By relying on a server for most computing tasks, thin clients offer several advantages. They require less hardware maintenance, as the server handles software updates, data backups, and security measures. Thin clients are also typically more energy-efficient than traditional desktop computers, consuming less power.
Overall, thin clients provide a cost-effective and centrally-managed solution for organizations that require multiple users to access shared resources and applications while minimizing the hardware and software complexities at the user end.
Let See! What Is the Use of Thin Client.
Thin clients have several uses and benefits in various computing environments. Here are some common use cases for thin clients:
Virtual Desktop Infrastructure (VDI): Thin clients are often used in VDI environments, where multiple users can access their virtual desktops hosted on a central server. Thin clients act as the display terminals, providing a user interface for accessing and interacting with their virtual desktops.
Centralized Computing: Thin clients are used in centralized computing environments, where the processing power, storage, and software applications are hosted on a server or in the cloud. This allows users to access their applications and data from any thin client device connected to the network.
Cost-Effective Solution: Thin clients are generally less expensive to purchase and maintain compared to traditional desktop computers. Since the heavy computing tasks are handled by the server, thin clients can have lower hardware requirements, reducing upfront costs. Additionally, maintenance and software updates can be performed centrally, saving time and effort.
Security: Thin clients can enhance security in computing environments. Since data and applications are stored on the server rather than on individual devices, the risk of data loss or theft due to device theft or failure is minimized. Centralized security measures, such as firewalls and access controls, can be implemented on the server to protect sensitive information.
Energy Efficiency: Thin clients consume less power compared to traditional desktop computers. Their low-power hardware requirements translate into reduced energy consumption, resulting in cost savings and a smaller environmental footprint.
Legacy System Access: Thin clients can provide a means to access legacy applications or systems that may not be compatible with modern hardware. By using a thin client, users can connect to the server hosting the legacy system and access it remotely without the need for extensive hardware upgrades.
Streamlined IT Management: Thin clients simplify IT management by centralizing software updates, patches, and security measures on the server. IT administrators can more efficiently deploy and manage software applications, ensuring consistent configurations across all thin client devices.
Overall, the use of thin clients offers centralized management, cost savings, improved security, and flexibility in computing environments, making them suitable for a range of industries and organizations.
#blog#news#business#technologies#article#software#productivity software#electronic#enterprise software#articles#electronics#computer science
4 notes
·
View notes
Text
How HPE Load Balancer Enhances Network Security?
As cyber threats evolve, businesses need strong security measures to protect their digital assets. The HPE Load Balancer ensures secure and efficient network operations by optimizing traffic distribution and defending against cyber threats. It helps mitigate DDoS attacks, prevent unauthorized access, and maintain uptime. Edgenexus Limited specializes in deploying HPE Load Balancer solutions, helping businesses safeguard applications while enhancing performance. In this guide, we’ll explore how the HPE Load Balancer strengthens network security and why it’s essential for modern enterprises.
Understanding HPE Load Balancer
A HPE Load Balancer distributes incoming traffic across multiple servers, preventing overload and improving performance. It also enhances security by mitigating risks like unauthorized traffic spikes and potential breaches. The HPE Load Balancer integrates security features such as SSL offloading, access control, and application-layer protection. Edgenexus Limited helps businesses implement these solutions effectively, ensuring that networks remain secure and highly available in demanding environments.
How HPE Load Balancer Protects Against Cyber Threats?
Cyber threats such as SQL injection, malware, and brute-force attacks can compromise business networks. The HPE Load Balancer protects against these threats by analyzing incoming traffic and blocking malicious requests. It filters traffic based on security rules, reducing unauthorized access risks. With Edgenexus Limited, businesses can customize their HPE Load Balancer configurations to create a proactive security defense, ensuring only legitimate requests reach critical applications while malicious traffic is neutralized.
Preventing DDoS Attacks with HPE Load Balancer
DDoS attacks can cripple business operations by overwhelming servers with excessive traffic. The HPE Load Balancer mitigates these attacks by evenly distributing traffic and identifying unusual patterns indicative of an attack. It can limit requests from suspicious IP addresses, maintaining service availability. Edgenexus Limited provides expert deployment strategies, ensuring businesses stay protected from DDoS threats and can deliver uninterrupted online experiences even during high-traffic periods or attack attempts.
SSL Offloading and Secure Data Encryption
Encryption is a cornerstone of cybersecurity, and the HPE Load Balancer enhances security by managing SSL/TLS encryption processes. This reduces server load while ensuring encrypted data transmission. Offloading SSL decryption at the load balancer level allows businesses to conduct deep packet inspection for threats. Edgenexus Limited helps implement SSL offloading, ensuring businesses maintain high-security standards while optimizing performance and reducing latency in secure communications.
Access Control and Authentication Features
Unauthorized access to business networks can lead to data breaches. The HPE Load Balancer includes advanced access control mechanisms such as multi-factor authentication (MFA) and role-based access restrictions. These features ensure only verified users can access critical resources. Edgenexus Limited helps businesses configure access control policies, preventing unauthorized access and ensuring only legitimate traffic flows through the network while blocking security threats in real time.
Application Layer Security and Web Traffic Filtering
Attackers frequently target web applications with cross-site scripting (XSS), SQL injections, and malware. The HPE Load Balancer strengthens security by incorporating Web Application Firewall (WAF) features and content filtering to prevent such exploits. These measures block harmful traffic before reaching applications, significantly reducing security risks. Edgenexus Limited works with businesses to deploy these security features, ensuring that web applications remain protected from both automated and targeted cyber threats.
Monitoring, Logging, and Threat Analysis
Continuous network monitoring is essential for security and performance. The HPE Load Balancer includes logging and real-time monitoring features that provide visibility into network traffic and potential threats. These insights allow businesses to detect anomalies, troubleshoot issues, and respond to security incidents quickly. Edgenexus Limited helps organizations implement advanced monitoring strategies, enabling proactive threat detection and response to strengthen cybersecurity resilience.
Conclusion
The HPE Load Balancer is a powerful tool for enhancing network security, optimizing performance, and ensuring high availability. From preventing DDoS attacks to enforcing encryption and access controls, it offers comprehensive protection against cyber threats. Edgenexus Limited provides expert implementation and support, helping businesses fully leverage HPE Load Balancer technology. By integrating this solution, organizations can build a secure, resilient, and future-proof network infrastructure that meets the demands of modern digital environments.
0 notes
Link
0 notes
Text
Factors to Consider When Choosing a Cloud Hosting Provider
Looking for a reliable cloud hosting provider? Choosing the right one can significantly impact your website’s performance, security, and scalability. Here are key factors to c consider when selecting a cloud hosting provider:
Performance & Reliability Ensure the provider offers high uptime guarantees, fast servers, and low latency. Vultr provides industry-leading performance with SSD-based storage and high-speed networking, ensuring seamless operations for your applications.
Scalability & Flexibility As your business grows, your hosting needs may change. A good cloud provider should offer easy scalability, allowing you to upgrade resources as needed. With Vultr, you get on-demand scaling, making it easier to adapt to traffic spikes and evolving requirements.
Security & Compliance Data protection is a top priority. Look for features like DDoS protection, firewalls, and encryption. Vultr ensures robust security with advanced protection mechanisms and compliance standards to safeguard your data.
Pricing & Cost Efficiency Budget plays a significant role in selecting a provider. Choose a transparent pricing model without hidden fees. Vultr offers competitive pay-as-you-go pricing, ensuring you only pay for what you use.
Ease of Use & Management A user-friendly interface simplifies server deployment and management. Vultr’s intuitive control panel and API allow for easy setup and automation of cloud resources.
Global Data Centers Hosting closer to your users improves website speed. Vultr has multiple data centers worldwide, ensuring low latency and optimal performance across different regions.
Customer Support Reliable customer support is essential. Look for providers offering 24/7 assistance. Vultr provides robust documentation and responsive support to help you resolve any issues quickly.
Why Choose Vultr? Vultr is a leading cloud hosting provider offering high-performance computing, flexible pricing, and global infrastructure. Whether you're a developer, business owner, or enterprise, Vultr provides the best solutions tailored to your needs.
0 notes
Text
Amazon Web Services (AWS): The Ultimate Guide
Introduction to Amazon Web Services (AWS)

Amazon Web Services (AWS) is the world’s leading cloud computing platform, offering a vast array of services for businesses and developers. Launched by Amazon in 2006, AWS provides on-demand computing, storage, networking, AI, and machine learning services. Its pay-as-you-go model, scalability, security, and global infrastructure have made it a preferred choice for organizations worldwide.
Evolution of AWS
AWS began as an internal Amazon solution to manage IT infrastructure. It launched publicly in 2006 with Simple Storage Service (S3) and Elastic Compute Cloud (EC2). Over time, AWS introduced services like Lambda, DynamoDB, and SageMaker, making it the most comprehensive cloud platform today.
Key Features of AWS
Scalability: AWS scales based on demand.
Flexibility: Supports various computing, storage, and networking options.
Security: Implements encryption, IAM (Identity and Access Management), and industry compliance.
Cost-Effectiveness: Pay-as-you-go pricing optimizes expenses.
Global Reach: Operates in multiple regions worldwide.
Managed Services: Simplifies deployment with services like RDS and Elastic Beanstalk.
AWS Global Infrastructure
AWS has regions across the globe, each with multiple Availability Zones (AZs) ensuring redundancy, disaster recovery, and minimal downtime. Hosting applications closer to users improves performance and compliance.
Core AWS Services

1. Compute Services
EC2: Virtual servers with various instance types.
Lambda: Serverless computing for event-driven applications.
ECS & EKS: Managed container orchestration services.
AWS Batch: Scalable batch computing.
2. Storage Services
S3: Scalable object storage.
EBS: Block storage for EC2 instances.
Glacier: Low-cost archival storage.
Snowball: Large-scale data migration.
3. Database Services
RDS: Managed relational databases.
DynamoDB: NoSQL database for high performance.
Aurora: High-performance relational database.
Redshift: Data warehousing for analytics.
4. Networking & Content Delivery
VPC: Isolated cloud resources.
Direct Connect: Private network connection to AWS.
Route 53: Scalable DNS service.
CloudFront: Content delivery network (CDN).
5. Security & Compliance
IAM: Access control and user management.
AWS Shield: DDoS protection.
WAF: Web application firewall.
Security Hub: Centralized security monitoring.
6. AI & Machine Learning
SageMaker: ML model development and deployment.
Comprehend: Natural language processing (NLP).
Rekognition: Image and video analysis.
Lex: Chatbot development.
7. Analytics & Big Data
Glue: ETL service for data processing.
Kinesis: Real-time data streaming.
Athena: Query service for S3 data.
Lake Formation: Data lake management.
Discover the Full Guide Now to click here
Benefits of AWS
Lower Costs: Eliminates on-premise infrastructure.
Faster Deployment: Pre-built solutions reduce setup time.
Enhanced Security: Advanced security measures protect data.
Business Agility: Quickly adapt to market changes.
Innovation: Access to AI, ML, and analytics tools.
AWS Use Cases
AWS serves industries such as:
E-commerce: Online stores, payment processing.
Finance: Fraud detection, real-time analytics.
Healthcare: Secure medical data storage.
Gaming: Multiplayer hosting, AI-driven interactions.
Media & Entertainment: Streaming, content delivery.
Education: Online learning platforms.
Getting Started with AWS

Sign Up: Create an AWS account.
Use Free Tier: Experiment with AWS services.
Set Up IAM: Secure access control.
Explore AWS Console: Familiarize yourself with the interface.
Deploy an Application: Start with EC2, S3, or RDS.
Best Practices for AWS
Use IAM Policies: Implement role-based access.
Enable MFA: Strengthen security.
Optimize Costs: Use reserved instances and auto-scaling.
Monitor & Log: Utilize CloudWatch for insights.
Backup & Recovery: Implement automated backups.
AWS Certifications & Careers
AWS certifications validate expertise in cloud computing:
Cloud Practitioner
Solutions Architect (Associate & Professional)
Developer (Associate)
SysOps Administrator
DevOps Engineer
Certified professionals can pursue roles like cloud engineer and solutions architect, making AWS a valuable career skill.
0 notes
Text
CCNA Certification: Complete Guide for 2025
What is CCNA Certification
Cisco Certified Network Associate (CCNA) certification is one of the most recognized networking credentials in the IT industry. It validates your ability to install, configure, operate, and troubleshoot networks, making it a great starting point for networking professionals. Whether you're new to networking or looking to advance your career, this guide will help you understand the CCNA certification path, its benefits, and how to prepare effectively. If you are looking to take your networking career to next level avail today rated Cisco Courses now.
Why is CCNA Certification Important?
CCNA certification is valuable for several reasons:
Industry Recognition: Globally recognized as a standard for networking professionals.
Career Growth: Opens doors to higher-paying job opportunities in IT.
Skill Validation: Demonstrates proficiency in networking fundamentals, security, automation, and more.
Foundation for Advanced Certifications: A stepping stone to more advanced Cisco certifications like CCNP and CCIE.
Higher Salary Potential: Certified professionals often earn more than their non-certified peers.
CCNA Certification Overview
Certification Name: Cisco Certified Network Associate (CCNA)
Exam Code: 200-301 CCNA
Prerequisites: No formal prerequisites, but basic networking knowledge is recommended.
Exam Duration: 120 minutes
Exam Cost: $300 (subject to regional variations)
Validity: 3 years
Testing Center: Pearson VUE
Skills Covered in CCNA
CCNA certification validates knowledge in the following areas:
Networking Fundamentals: IP addressing, subnetting, routing, and switching.
Security Fundamentals: Basics of network security, firewalls, and threat management.
IP Services: NAT, DHCP, DNS, and QoS.
Automation and Programmability: Network automation using Python and REST APIs.
Wireless Networking: Basics of WLAN, SSID configuration, and access point deployment.
Who Should Take the CCNA Certification?
CCNA is ideal for:
Aspiring network engineers and administrators.
IT support technicians looking to advance in networking roles.
Professionals seeking foundational networking skills.
Students or fresh graduates pursuing a networking career.
Job Roles After CCNA Certification
After earning your CCNA, you can apply for roles such as:
Network Engineer
Network Administrator
Systems Administrator
Network Support Technician
IT Help Desk Specialist
How to Prepare for the CCNA Exam
1. Study Resources
Official Cisco Learning Network: Provides study materials and resources.
Cisco Press Books: "CCNA 200-301 Official Cert Guide" by Wendell Odom.
Online Courses: Platforms like Udemy, Coursera, and Pluralsight offer CCNA courses.
Practice Exams: Use mock tests to assess your knowledge and identify weak areas.
Hands-on Labs: Utilize Cisco Packet Tracer or GNS3 for practical experience.
2. Exam Strategy
Understand Exam Objectives: Study Cisco’s official exam topics.
Create a Study Plan: Allocate time for each subject area.
Practice Configurations: Use simulation tools to practice real-world networking scenarios.
Join Networking Communities: Engage with CCNA aspirants and certified professionals.
Take Timed Practice Tests: Improve time management skills for the exam.
How to Register for the CCNA Exam
Visit the Cisco Certification Website.
Choose "CCNA 200-301" and click on "Register."
Create a Pearson VUE account.
Select a test center or opt for online proctoring.
Pay the exam fee and schedule your exam.
CCNA Recertification
CCNA certification is valid for three years. To renew:
Retake the CCNA exam.
Earn Continuing Education (CE) credits.
Pass a higher-level Cisco certification exam.
Benefits of CCNA Certification
Better Job Opportunities: Preferred by top employers worldwide.
Enhanced Networking Skills: Deepens your understanding of network infrastructures.
Competitive Edge: Differentiates you from non-certified candidates.
Pathway to Advanced Cisco Certifications: Leads to CCNP, CCIE, and other specialized certifications.
Conclusion
Earning a CCNA certification in 2025 can significantly boost your networking career. By understanding its structure, benefits, and study strategies, you can successfully achieve certification and unlock new professional opportunities. Start your CCNA journey today and take the first step towards a rewarding career in networking!
1 note
·
View note
Text
Business Informatic Website Designing — Empowering Digital Transformation
In today’s digital world, businesses require an intelligent and dynamic website that effectively represents their brand, streamlines operations, and enhances user experience. Business informatics website designing integrates technology, data analytics, and a user-friendly interface to create a powerful online presence for businesses of all sizes.
A well-designed website serves as the backbone of digital transformation, enabling businesses to optimize operations, enhance decision-making, and deliver seamless customer experiences. Whether you are a startup or an established enterprise, a robust business informatic website can take your brand to the next level.
Why Business Informatics Website Designing Matters

1. Enhances Business Intelligence
A well-structured website gathers and processes data, offering valuable insights that drive informed decision-making.
2. Improves User Experience
An intuitive, responsive, and seamless website keeps visitors engaged, ensuring high conversion rates.
3. Optimized for SEO & Performance
A business informatic website is designed to be search engine-friendly, mobile-responsive, and fast-loading to rank higher on Google and attract more traffic.
4. Ensures Data Security
With built-in security measures, SSL encryption, and secure databases, business informatic websites protect sensitive business and customer information.
5. Streamlines Business Operations
From automation to CRM integration, a business informatic website enhances workflow and efficiency, reducing manual processes.
Our Business Informatics Website Designing Services
We provide comprehensive website solutions tailored to meet the unique needs of businesses. Our team combines cutting-edge technology, UI/UX design, and SEO optimization to create high-performing websites.
1. Custom Website Development
We design and develop custom business websites that reflect your brand identity, offering a unique and professional online presence.
2. SEO-Friendly Structure
We integrate best SEO practices, including optimized meta tags, keywords, structured data, and schema markup, to boost search engine rankings.
3. Data Analytics & Business Intelligence Integration
Our websites feature built-in data analytics dashboards, performance tracking, and AI-powered insights to help businesses make data-driven decisions.
4. Responsive & Mobile-Optimized Design
We ensure your website is fully responsive and adaptive across desktops, tablets, and mobile devices for a seamless browsing experience.
5. E-Commerce & CRM Integration
For businesses involved in e-commerce and customer management, we integrate payment gateways, shopping carts, and CRM systems for efficient operations.
6. Automated Business Processes
We implement chatbots, automated workflows, and AI-powered tools to enhance customer service and streamline operations.
7. Security & Data Protection
We implement SSL encryption, firewall protection, and secure databases to safeguard customer and business data from cyber threats.
8. Fast Loading Speed & Performance Optimization
We ensure your website is optimized for speed, minimizing bounce rates and maximizing user engagement.
Our Website Designing Process
Our streamlined process ensures that your website is developed efficiently with top-notch quality.
Understanding Business Goals — We analyze your requirements, business objectives, and target audience.
Design & Wireframing — We create a responsive and intuitive UI/UX design prototype.
Development & Integration — Our developers bring the design to life using the latest technologies.
SEO Optimization — We implement SEO best practices to ensure high visibility on search engines.
Testing & Quality Assurance — We perform rigorous testing for speed, performance, and security.
Launch & Post-Deployment Support — We ensure a seamless launch and provide ongoing maintenance and support.
Why Choose Us for Business Informatics Website Designing?
We are a leading website design company specializing in business informatics solutions. Here’s why businesses trust us:
✅ Tailored Solutions
We offer customized website designs that align with your business needs and industry standards.
✅ SEO-Optimized & High-Performance
Our websites are built to rank on search engines, ensuring maximum visibility and lead generation.
✅ Secure & Scalable Infrastructure
We implement advanced security measures and scalable frameworks to support business growth.
✅ User-Centric Design & Experience
Our UI/UX designs prioritize user engagement, ensuring high retention and conversion rates.
✅ Affordable Pricing & Timely Delivery
We provide cost-effective solutions without compromising on quality, delivering projects on time.
Industries We Serve
Our business informatics website solutions cater to a wide range of industries, including:
Corporate & Enterprise Websites
Healthcare & Medical Services
E-Commerce & Retail Businesses
Finance & Banking Sectors
Education & E-Learning Platforms
Technology & Software Solutions
Real Estate & Property Management
Logistics & Supply Chain Management
Benefits of a Business Informatics Website

Enhanced Decision-Making — Provides real-time insights and analytics.
Higher Search Engine Rankings — SEO-friendly features improve visibility and lead generation.
Automation & Efficiency — Reduces manual tasks and enhances workflow.
Customer Engagement & Retention — A seamless UI/UX ensures better user experience.
Scalability & Future Growth — A flexible framework allows for easy upgrades and expansion.
Conclusion
In today’s fast-paced digital landscape, having a Business informatics website designing is essential for growth, efficiency, and success. Our expert team of web designers and developers is committed to delivering innovative, SEO-friendly, and data-driven websites that empower businesses to thrive.
#business informatic webdesign#webdesign#website designing company#website designing#web developing company
0 notes
Text
Incident Response Market – Industry Trends and Forecast to 2028 Growth Drivers: Share, Value, Size, Insights, and Trends
"Incident Response Market Size And Forecast by 2028
According to Data Bridge Market Research Incident response market will reach at estimated value of USD 70.60 billion and grow at a CAGR of 38.40% in the forecast period of 2021 to 2028. Rising stringent government regulations and compliance requirements is an essential factor driving the incident response market.
Our comprehensive Incident Response Market report is ready with the latest trends, growth opportunities, and strategic analysis. https://www.databridgemarketresearch.com/reports/global-incident-response-market
**Segments**
- **Component:** The incident response market can be segmented based on components into solutions and services. Incident response solutions include various technologies like firewalls, intrusion detection systems, threat intelligence, and others to detect and respond to cyber incidents. Incident response services, on the other hand, involve incident management, forensic analysis, risk assessment, threat hunting, and more.
- **Deployment Mode:** Another key segment of the market is based on deployment modes, which includes cloud-based and on-premises incident response solutions. The choice between these deployment modes depends on factors like organization size, IT infrastructure, budget, and security requirements. Cloud-based solutions offer scalability and flexibility, while on-premises solutions provide more control and customization options.
- **Organization Size:** Incident response solutions are also categorized based on organization size, such as small and medium-sized enterprises (SMEs) and large enterprises. SMEs often have limited resources and expertise to handle advanced cyber threats, making them increasingly vulnerable. Large enterprises, with more resources and complex IT environments, require robust incident response solutions to protect their sensitive data and critical systems.
- **End-User Industry:** The incident response market caters to various end-user industries, including healthcare, BFSI (banking, financial services, and insurance), government, IT and telecom, retail, energy and utilities, and others. Each industry sector faces unique cybersecurity challenges and compliance requirements, driving the demand for tailored incident response solutions and services.
**Market Players**
- **IBM Corporation:** IBM offers a comprehensive incident response platform that combines threat intelligence, advanced analytics, and automation to rapidly detect and respond to security incidents. The company's incident response services include threat hunting, digital forensics, incident management, and proactive threat mitigation strategies.
- **FireEye, Inc.:** FireEye is a prominent player in the incident response market, providing a range of threat detection and incident response services to help organizations combat sophisticated cyber attacks. The company's Mandiant incident response services offer 24/7 support, incident response planning, and threat intelligence to enhance cybersecurity posture.
- **Cisco Systems, Inc.:** Cisco offers a holistic incident response solution that integrates network security, endpoint protection, and threat intelligence to detect and mitigate security incidents across the organization. Cisco's incident response services focus on rapid incident containment, forensic analysis, and post-incident reporting to minimize the impact of cyber attacks.
- **Symantec Corporation:** Symantec is a leading cybersecurity vendor that provides incident response solutions tailored for different industry verticals. The company's incident response services include incident detection, containment, eradication, and recovery to help organizations effectively respond to cyber threats and prevent future attacks.
- **CrowdStrike Holdings, Inc.:** CrowdStrike is known for its cloud-native endpoint protection platform that includes incident response capabilities like threat hunting, forensic analysis, and malware reverse engineering. The company's incident response services leverage machine learning and AI to deliver real-time threat detection and response.
https://www.databridgemarketresearch.com/reports/global-incident-response-market The incident response market is witnessing significant growth driven by the escalating frequency and sophistication of cyber threats across various industry sectors. One emerging trend in the market is the convergence of incident response solutions and services to provide organizations with integrated and proactive cybersecurity strategies. Companies are increasingly focusing on enhancing their incident response capabilities to minimize the impact of security breaches and ensure business continuity. This trend is fueled by the growing awareness of the financial and reputational risks associated with cyber incidents, prompting organizations to invest in advanced technologies and expert services to detect, respond to, and recover from security breaches effectively.
Moreover, the market is experiencing a shift towards cloud-based incident response solutions due to their scalability, cost-effectiveness, and ease of deployment compared to traditional on-premises offerings. Cloud-based solutions enable organizations to quickly adapt to evolving cyber threats and ensure seamless collaboration among geographically dispersed teams during incident response activities. As more businesses embrace digital transformation and remote work arrangements, the demand for cloud-based incident response solutions is expected to surge in the coming years.
Another key factor influencing the incident response market is the regulatory landscape, with stringent data protection regulations mandating organizations to implement robust incident response capabilities to safeguard sensitive information and comply with legal requirements. Industries such as healthcare, finance, and government are particularly susceptible to regulatory scrutiny and data breaches, driving the adoption of tailored incident response solutions and services to mitigate risks and ensure regulatory compliance.
Furthermore, the increasing adoption of endpoint detection and response (EDR) solutions is reshaping the incident response market, with organizations prioritizing the detection and remediation of advanced threats targeting endpoints. EDR solutions offer real-time visibility into endpoint activities, enabling security teams to proactively identify and respond to security incidents before they escalate. This proactive approach to incident response is essential in combating sophisticated cyber threats and minimizing the dwell time of attackers within the network.
In conclusion, the incident response market is poised for substantial growth as organizations across diverse industries recognize the critical importance of effective cybersecurity incident response strategies in safeguarding their digital assets and maintaining business resilience. With evolving cyber threats and regulatory pressures driving the demand for advanced incident response solutions and services, market players are continually innovating to deliver comprehensive and proactive cybersecurity capabilities tailored to the unique needs of different industry sectors. As organizations continue to prioritize cyber resilience and threat detection, the incident response market is expected to experience sustained growth and innovation in the coming years.**Segments**
Global Incident Response Market, By Component: - Solution - Service
Service: - Retainer - Assessment and Response - Tabletop Exercises - Incident Response Planning and Development - Advanced Threat Hunting
Security Type: - Web Security - Endpoint Security - Database Security - Application Security - Cloud Security
Deployment Type: - On-Premises Deployment - Cloud Deployment
Industry Vertical: - BFSI - Government - Healthcare and Life Sciences - Retail and E-Commerce - Travel and Hospitality - Manufacturing - IT and Telecommunication - Others
Country: - U.S. - Canada - Mexico - Brazil - Argentina - Rest of South America - Germany - Italy - U.K. - France - Spain - Netherlands - Belgium - Switzerland - Turkey - Russia - Rest of Europe - Japan - China - India - South Korea - Australia - Singapore - Malaysia - Thailand - Indonesia - Philippines - Rest of Asia-Pacific - Saudi Arabia - U.A.E - South Africa - Egypt - Israel - Rest of Middle East and Africa
Industry Trends and Forecast to 2028
**Market Players**
The major players covered in the incident response market are: - VMware, Inc - Honeywell International Inc - Schneider Electric - Cisco Systems - Broadcom - AO Kaspersky Lab - IBM - NEC Corporation - Hexagon AB and/or its subsidiaries and affiliates - R1 RCM, Inc - Eccentex - The Response Group - Haystax Technology - Alert Technologies - Crisisworks - EmerGeo - Veoci - MissionMode - Accenture - General Electric - Rockwell Automation - PAS Global LLC - Fortinet, Inc - Palo Alto Networks - Darktrace - Forescout Technologies Inc. - and among other domestic and global players.
Market share data is available for global, North America, Europe, Asia-Pacific (APAC), Middle East and Africa (MEA), and South America separately. DBMR analysts understand competitive strengths and provide competitive analysis for each competitor separately.
The incident response market is currently experiencing significant growth due to the increasing frequency and complexity of cyber threats across various industries. A notable trend in the market is the integration of incident response solutions and services to offer organizations proactive cybersecurity strategies. This trend emphasizes the importance of organizations enhancing their incident response capabilities to minimize security breach impacts and ensure business continuity. As organizations recognize the financial and reputational risks associated with cyber incidents, they are investing in advanced technologies and expert services to effectively detect, respond to, and recover from security breaches.
Moreover, there is a rising preference for cloud-based incident response solutions over traditional on-premises offerings due to their scalability, cost-effectiveness, and ease of deployment. Cloud-based solutions enable organizations to adapt quickly to evolving cyber threats and facilitate seamless collaboration among geographically dispersed teams during incident response operations. As businesses continue to embrace digital transformation and remote work setups, the demand for cloud-based incident response solutions is expected to grow significantly in the future.
In addition to technological advancements, the regulatory landscape plays a crucial role in shaping the incident response market. Strict data protection regulations require organizations to implement robust incident response capabilities to protect sensitive information and comply with legal mandates. Industries like healthcare, finance, and government are particularly vulnerable to regulatory scrutiny and data breaches, thereby driving the adoption of tailored incident response solutions to mitigate risks and ensure compliance.
Furthermore, the increasing adoption of endpoint detection and response (EDR) solutions is reshaping the incident response market landscape. Organizations are prioritizing the detection and remediation of advanced threats targeting endpoints by leveraging EDR solutions that offer real-time visibility into endpoint activities. This proactive approach to incident response is essential in combating sophisticated cyber threats and reducing attackers' dwell time within networks, thereby enhancing overall cybersecurity posture.
In conclusion, the incident response market is set for substantial growth as organizations prioritize effective cybersecurity incident response strategies to safeguard digital assets and uphold business resilience. With evolving cyber threats and regulatory pressures driving the need for advanced incident response solutions and services, market players are continuously innovating to deliver comprehensive cybersecurity capabilities tailored to diverse industry needs. The market's future holds sustained growth, innovation, and a commitment to cyber resilience as organizations across sectors continue to invest in robust incident response measures to combat evolving threats effectively.
The market is highly fragmented, with a mix of global and regional players competing for market share. To Learn More About the Global Trends Impacting the Future of Top 10 Companies in Incident Response Market : https://www.databridgemarketresearch.com/reports/global-incident-response-market/companies
Key Questions Answered by the Global Incident Response Market Report:
What is the current state of the Incident Response Market, and how has it evolved?
What are the key drivers behind the growth of the Incident Response Market?
What challenges and barriers do businesses in the Incident Response Market face?
How are technological innovations impacting the Incident Response Market?
What emerging trends and opportunities should businesses be aware of in the Incident Response Market?
Browse More Reports:
https://www.databridgemarketresearch.com/reports/global-image-guided-navigation-technology-markethttps://www.databridgemarketresearch.com/reports/global-multimodal-imaging-markethttps://www.databridgemarketresearch.com/reports/global-tourette-syndrome-markethttps://www.databridgemarketresearch.com/reports/global-content-intelligence-markethttps://www.databridgemarketresearch.com/reports/global-personalized-orthopedics-market
Data Bridge Market Research:
☎ Contact Us:
Data Bridge Market Research
US: +1 614 591 3140
UK: +44 845 154 9652
APAC: +653 1251 982
✉ Email: [email protected]"
#Incident Response Market – Industry Trends and Forecast to 2028 Growth Drivers: Share#Value#Size#Insights#and Trends
0 notes