#dataencryption
Explore tagged Tumblr posts
Link
#AndroidSecurity#CybersecurityTrends#dataencryption#digitalrights#GooglePrivacyPolicy#LawEnforcementTechnology#MobileForensics#ProactiveSecurity
0 notes
Text
Decode the Future with Online Cryptography Courses
Explore the world of digital security and encryption with certified Cryptography courses from EasyShiksha. Learn the principles behind secure communication, data encryption, blockchain basics, and cryptographic algorithms—perfect for tech students, cybersecurity professionals, and blockchain enthusiasts.
0 notes
Text
Enterprise File Synchronization and Sharing: How Enterprises are Transforming Data Sharing & Security
The global enterprise file synchronization and sharing market size was valued at USD 9.50 billion in 2023 and is anticipated to grow at a CAGR of 23.2% from 2024 to 2030. The increasing adoption of remote and hybrid work models has necessitated secure, efficient, and collaborative file-sharing solutions, propelling demand for enterprise file synchronization and sharing (EFSS) platforms. Additionally, the growing emphasis on data security and compliance with stringent regulatory standards has underscored the need for robust EFSS solutions that offer advanced encryption and access controls. The integration capabilities of EFSS with other enterprise applications, such as cloud storage, collaboration tools, and enterprise content management systems, further enhances their appeal by providing seamless workflows and improved productivity.
Moreover, the proliferation of mobile devices and the subsequent need for mobile access to corporate data have significantly contributed to the market's expansion. As organizations prioritize digital transformation and agility, the EFSS market is expected to witness sustained growth, driven by the ongoing need for secure, accessible, and efficient data management solutions.
The increasing adoption of remote and hybrid work models significantly drives the EFSS market. As organizations transition to more flexible work environments, the need for secure, efficient, and collaborative file-sharing solutions has become paramount. EFSS platforms enable seamless access to critical data from any location, ensuring remote and hybrid workers can collaborate effectively while maintaining data integrity and security. This shift in work dynamics has highlighted the importance of reliable EFSS solutions, fueling their demand and market growth.
The proliferation of mobile devices and the subsequent need for mobile access to corporate data have significantly contributed to the expansion of the EFSS market. As employees increasingly rely on smartphones and tablets for work, the demand for EFSS solutions that offer secure, seamless access to corporate data on mobile platforms has surged. These solutions enable employees to collaborate, share, and manage files from any device, enhancing productivity and flexibility. Consequently, the growing dependence on mobile technology in the workplace has been pivotal in driving the market's expansion.
Key Enterprise File Synchronization And Sharing Company Insights
Key players operating in the enterprise file synchronization and sharing (EFSS) market include Google LLC, IBM, Open Text, Microsoft, and Qnext Corp. The companies are focusing on various strategic initiatives, including new product development, partnerships & collaborations, and agreements to gain a competitive advantage over their rivals. The following are some instances of such initiatives.
In April 2024, Microsoft unveiled new features for OneDrive for Business, including integration with CoPilot AI assistant and enhanced collaboration capabilities for schools and enterprises. The enhanced search features now include new filters for file types, a date filter for specific timeframes, precise scoping options, and an updated interface with improved metadata. These enhancements help you locate files more efficiently.
In October 2023, Dropbox launched Dropbox Dash, an AI-based search feature currently in open beta. This tool enhances the user experience by providing smarter search capabilities across files and folders. Additionally, Dropbox introduced Dropbox Studio, an all-in-one tool for video content creation, editing, and feedback collection.
For More Details or Sample Copy please visit link @: Enterprise File Synchronization And Sharing Market
#EFSS#EnterpriseFileSharing#FileSync#CloudStorage#DataSharing#CloudComputing#HybridCloud#AIinSecurity#BlockchainForSecurity#DataEncryption
0 notes
Text
#MongoDB#DatabaseManagement#NoSQL#DataSecurity#PerformanceOptimization#TechUpdates#SoftwareDevelopment#DataEncryption#Scalability#LiveResharding
0 notes
Text




Are you aware of SSL integration for your website? 🔐
SSL ensures security, trust, and better SEO, making your website safe and professional. ✅ Syngrid Technologies offers trusted SSL integration to protect your website from cyber threats. Upgrade today!
📌 Visit Us: www.syngrid.com 📧 Email: [email protected] 📞 Call: (65) 6659 3971
#SSL#WebsiteSecurity#SyngridTechnologies#CyberSecurity#SafeBrowsing#SecureWebsite#OnlineProtection#HTTPS#DataEncryption#WebDevelopment#DigitalSecurity#WebsiteProtection#SSLIntegration#SEO#TrustOnline
0 notes
Text
Privacy & Security in Remote Work Time Tracking Tools
#united states of america#PrivacyProtection#TimeTracking#RemoteWork#ClockingInSystem#DataSecurity#WorkFromHome#BestTimeClock#CyberSecurity#EmployeeManagement#WorkTracking#SecureTimeTracking#BusinessEfficiency#ProductivityTools#GDPR#DataEncryption
0 notes
Text
youtube
Importance of Data Encryption for Business
Data processing services with their encryption strategies ensure robust protection against cyber threats, boosting security, compliance, and customer trust. Visit us at: https://www.managedoutsource.com/services/data-processing/
0 notes
Text
Salesforce Data Security
Data security is a critical concern for businesses operating in today’s digital landscape. With the increasing amount of sensitive customer data being collected, stored, and shared online, businesses need to ensure that their data is secure from unauthorized access and breaches. Salesforce, as a cloud-based platform, takes data security very seriously, and offers a range of features and best practices to help businesses protect their data. read more

#SalesforceSecurity#DataSecurity#SalesforceBestPractices#CRMDataProtection#SalesforceAdmin#DataPrivacy#SecureSalesforce#CloudSecurity#SalesforceCompliance#CyberSecurity#DataEncryption#SalesforceTips#AccessControl#SalesforceGovernance
0 notes
Text
Ever wondered how SSL keeps your online data safe? In this quick video, we break down how SSL (Secure Sockets Layer) encrypts your connection to protect sensitive information like passwords and credit card details.
#ssl#HowSSLWorks#cybersecurity#dataencryption#internetsafety#secureconnections#techexplained#websecurity#encryption#techtips#onlinesecurity
0 notes
Text
How does Health Group Insurance software address compliance and data privacy concerns?
Health Group Insurance software ensures compliance and data privacy through advanced security measures and adherence to regulations:
Regulatory Compliance:
Aligns with local and international health data regulations such as HIPAA and GDPR.
Updates regularly to meet changing compliance requirements in the insurance sector.
Data Encryption:
Protects sensitive employee information with end-to-end encryption.
Ensures secure transmission and storage of health policy data.
Access Controls:
Implements role-based access, ensuring only authorized personnel can view or modify sensitive data.
Audit Trails:
Tracks all user activities and maintains logs to ensure transparency and accountability.
Secure Cloud Storage:
Safeguards data with secure cloud solutions that offer regular backups and disaster recovery options.
Employee Consent Management:
Incorporates consent mechanisms for data usage, ensuring ethical handling of personal information.
Discover how Mindzen’s Health Group Insurance software keeps your data secure while simplifying employee benefits management. Learn more here: https://mindzen.com/.
#EmployeeBenefitsSoftware#HealthGroupInsurance#DataPrivacy#ComplianceSolutions#InsuranceCompliance#DataSecurity#HealthInsuranceSoftware#HIPAACompliance#GDPRCompliance#SecureData#InsuranceSoftware#EmployeeManagement#DataProtection#InsuranceTech#BenefitsManagement#MindzenSolutions#PrivacyFirst#DataEncryption#SecureSoftware#HRTech#RoleBasedAccess#SecureCloudStorage#AuditTrail#ComplianceSoftware#InsuranceComplianceIndia#EmployeeHealthManagement#PolicyManagement#SmartInsurance#InsuranceSolutions#HealthDataSecurity
0 notes
Text

#QuizTime What’s your biggest cybersecurity priority?
A) Data Encryption 🛡️ B) User Authentication 🔑 C) Regular Backups 💾 D) Employee Training 📚
Comment your answers below 👇
💻 Explore insights on the latest in #technology on our Blog Page 👉 https://simplelogic-it.com/blogs/
🚀 Ready for your next career move? Check out our #careers page for exciting opportunities 👉 https://simplelogic-it.com/careers/
#quiztime#testyourknowledge#brainteasers#triviachallenge#thinkfast#quizmaster#knowledgeIspower#mindgames#funfacts#simplelogicit#makingitsimple#simplelogic#makeitsimple#cybersecurity#backups#dataencryption
0 notes
Text
Is AWS Elasticsearch Developer’s True Hero?

Elasticsearch is a free open source search engine, which is used for log analytics, full-text search, application monitoring and more. It makes easy to deploy, operate and scale Elasticsearch clusters in the AWS Cloud. We can get direct access to the Elasticsearch APIs. It provides Scalability, Availability and Security for the workload process run.
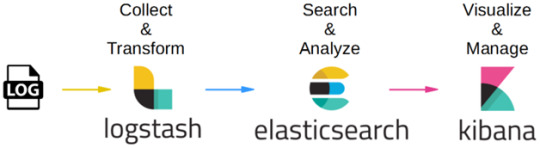
Elasticsearch architecture
The AWS Elasticsearch Service Architecture is very dynamically to allow create instances, remove instances, change instance sizes, change storage configuration and customize to make other changes. This Elasticsearch allows to search and analyse the data log. It consists of three components.
Logstash – is used to collect and transferred to the Elasticsearch.
Elasticsearch –facilitates search and analyze with the logs stored in it. It acts as a database.
Kibana –Kibana enables the data visualization on the dashboard that uses ELK stack. This tool provides a quick insight of the documents using visualization Kibana’s dashboard contains interactive diagrams, geospatial data, and graphs to visualize complex queries that let you search, view, or interact with the stored data. Kibana helps you to perform advanced data analysis and visualize your data in a variety of tables, charts, and maps.
Get started with an Elastic Cluster with AWS
First, create an AWS account and follow the following steps to claim your domain.
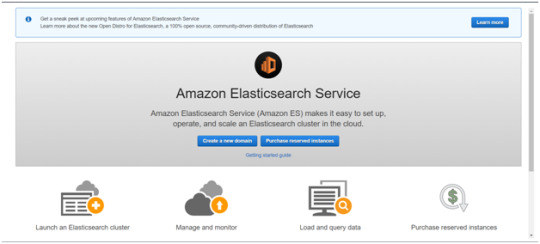
Tap on to “Create a new domain”
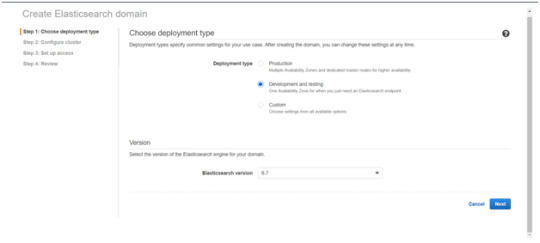
Select on the appropriated Deployment type and select the Elasticsearch version. Click Next.
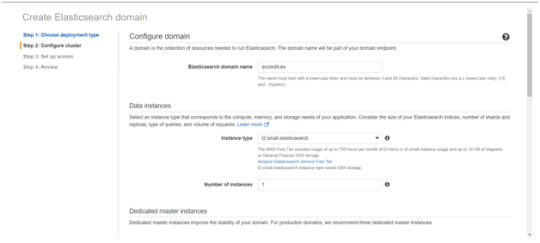
Enter a domain name and choose the Instance type in the prompt page and Click Next.
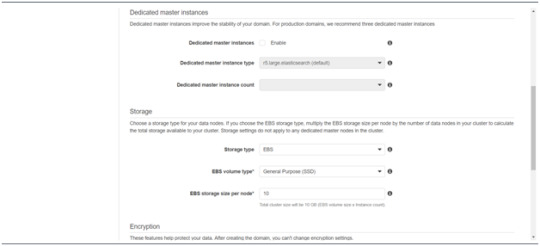
Follow to enter the “Dedicated master instances”
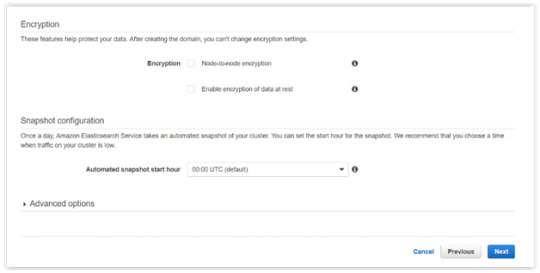
Click Next.
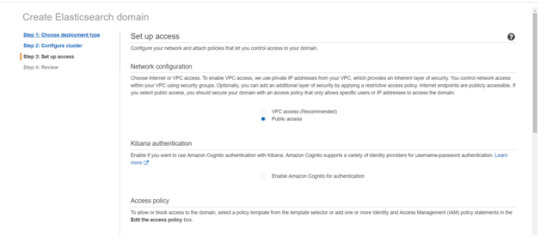
After the Cluster Configuration, you will be taken to the Set up access part. In the Setup access part, enable the specific set of users who can access your ElasticSearch cluster. There are two options — VPC access and Public access. Once you select one of the options and confirm your entries your new cluster is created.
Things to consider
1. Expandable
Amazon Elasticsearch Service provides to monitor your cluster through Amazon CloudWatch metrics.
We can change the cluster in various size from top or bottom within single clicks in the AWS management console or via a single API call.
There is a customizable setting available based on the range of instance types and storage options including SSD-powered EBS volumes.
2.Integrations
Many integrations available in the AWS Elasticsearch such as Kibana for data visualization, Amazon CloudTrail is used to audit API calls configure in AWS ES domains and integrate with Amazon Amazon S3, Amazon Kinesis, and Amazon DynamoDB for loading streaming data into Amazon ES.
3.Guarantee
It guarantees to provide a secure environment and easy integration with Amazon VPC and VPC security groups. There is an availability to access the Identity and Access Management (IAM) control. It provides authentication for Kibana and Data encryption with node-to-node encryption.
4.Availability
Amazon ES supports the different zones in two geographical locations and various node allocations with a large number of zones in the same region itself. It manages the cluster and notifies the damaged nodes automatically.
Conclusion
This article has covered what AWS Elastic Search means, its benefits, what happens between and how you can use it.
#AWS#Elasticsearch#LogAnalytics#SearchEngine#CloudComputing#DataVisualization#Kibana#Scalability#Security#CloudWatch#AWSIntegration#DataEncryption#VPC#ElasticCluster#API#CloudInfrastructure#TechSolutions#BigData#AWSElasticsearch#ElasticSearchService#DataAnalysis#CloudServices
0 notes
Text
Enterprise Key Management Market Future Outlook: Analyzing Size, Share, Growth Patterns
The global enterprise key management market size is estimated to reach USD 9.82 billion in 2030 and is projected to grow at a CAGR of 19.8% from 2024 to 2030. Increasing number of data breaches and loss of confidential data, coupled with increasingly stringent regulations and compliance standards to safeguard sensitive data from malicious users, have led to the implementation of advanced enterprise security solutions across different industries. The shift of organizations toward a digital environment for offering digital services and the need to protect increasing volumes of sensitive data are expected to drive the market.

Enterprise Key Management Market Report Highlights
North America is expected to be the largest market during the forecast period, owing to technological proliferation and accelerated adoption of digital services
Increased online and mobile transactions, along with data security regulatory mandates will drive the market growth
Increasing investments in cloud-based encryption solutions and the need to protect increasing data volume will drive the growth of the enterprise key management market
For More Details or Sample Copy please visit link @: Enterprise Key Management Market Report
Enterprise key management is an essential component of data encryption solutions and involves managing and dealing with generation, exchange, storage, use, destruction, and replacement of cryptographic keys that encrypt different data sources such as emails, databases, disk drives, big data repositories, backup tapes, and data over cloud environments. The key management solutions protect cryptographic keys throughout their lifecycle and restrain unauthorized users from accessing the keys or data.
Organizations are increasingly deploying encryption solutions to protect confidential data, thus, enabling the growth of the enterprise key management market. However, issues related to a lack of skilled key management workforce and standardized key management systems are expected to challenge the industry. Furthermore, the high cost and complex deployment of key management solutions are expected to hinder the market growth.
List of major companies in the Enterprise Key Management Market
Venafi, Inc.
Thales
Google
IBM
Amazon Web Services, Inc.
Oracle
Hewlett Packard Enterprise Development LP
Quantum Corporation
WinMagic
Microsoft
For Customized reports or Special Pricing please visit @: Enterprise Key Management Market Analysis Report
We have segmented the global enterprise key management market report based on deployment, enterprise size, application, end use, and region.
#DataSecurity#CyberProtection#KeyManagement#EnterpriseSecurity#SecureData#DataEncryption#ITSecurity#CloudProtection#DataPrivacy#SecuritySolutions#EncryptionKeys#InformationSecurity#CloudSecurity#DataProtection#SecurityInnovation
0 notes
Text
🔐 Create Secure MD5 Hashes with the MD5 Generator! 🔐
Need a fast way to generate MD5 hashes for your files or text? 🚀 Our MD5 Generator allows you to quickly create secure and unique hashes. Ideal for data integrity and encryption purposes!
Generate your MD5 hash now 👉 https://seotools.report/tools/md5-generator
0 notes
Text

🚨 Did you know? Cybersecurity breaches are projected to cost businesses a staggering $15 TRILLION by 2025! 😱💻
Cybersecurity isn't optional anymore! Protect your business from cyberattacks with Amigoways' next-level solutions: advanced threat detection, data encryption, and real-time monitoring. 🛡️✨
Don’t wait for disaster—secure your digital future now! 🚀 www.amigoways.com
#Cybersecurity#Amigoways#Letsconnect#BusinessProtection#DataEncryption#StaySecure#DigitalDefense#CyberThreats#TechSecurity#FutureReady#CyberSolutions
0 notes
Text
Protect Your Online Privacy with PureVPN and Save Up to 80% on Your Subscription!

In a world where online privacy has become a top priority, having a reliable VPN is essential. PureVPN stands out as one of the best options
Contact Author
Protect Your Online Privacy with PureVPN and Save Up to 80% on Your Subscription!
Protect Your Online Privacy with PureVPN and Save Up to 80% on Your Subscription!
In a world where online privacy has become a top priority, having a reliable VPN is essential. PureVPN stands out as one of the best options, offering not only top-tier security but also an incredible discount that you won't want to miss. In this article, I'll tell you everything you need to know about PureVPN and how you can get up to 80% off plus 3 extra months when you subscribe today.
Why Choose PureVPN?
Over 6,000 Servers in 80+ Locations PureVPN offers one of the largest and most robust networks on the market, with over 6,000 servers in more than 80 locations around the world. This means you can connect from almost anywhere, ensuring a fast and stable connection at all times.
Top-Level Security and Privacy With PureVPN, your security is a top priority. This service uses 256-bit encryption, the same level employed by banks and government agencies, to protect your personal information from any threats. Plus, its strict no-log policy ensures that your online activity remains completely private.
Unblock Content from Around the World Want to access your favorite shows and movies that are restricted in your country? With PureVPN, you can unblock content from platforms like Netflix, Hulu, and BBC iPlayer, among many others. Enjoy unlimited entertainment from anywhere!
Easy to Use on All Your Devices PureVPN has designed intuitive and user-friendly apps for all your devices, whether you use Windows, macOS, iOS, Android, or even routers. With just one account, you can protect up to 10 devices simultaneously, ensuring that your entire family stays safe.
Save Up to 80% + Get 3 Extra Months!
Now is the perfect time to secure your online privacy with PureVPN. By subscribing today, you can get up to 80% off your plan, plus 3 extra months of service absolutely free. This is an offer you can’t afford to miss!
copy this link to take advantage of the offer: http://billing.purevpn.com/aff.php?=49385635
Conclusion
Don't wait any longer to protect yourself online. With PureVPN, you'll get world-class security, the ability to unblock global content, and a server network that ensures a fast and reliable connection—all at an unbeatable price. Take advantage of this unique opportunity and subscribe today to enjoy 80% off and 3 extra months of service.
Protect your privacy and enjoy online freedom with PureVPN!
copy here to get started now: http://billing.purevpn.com/aff.php?=49385635
#OnlinePrivacy#InternetSecurity#CyberSecurity#PureVPN#DataEncryption#VPNDeals#DigitalFreedom#InternetSafety#SecureBrowsing#DigitalProtection
1 note
·
View note